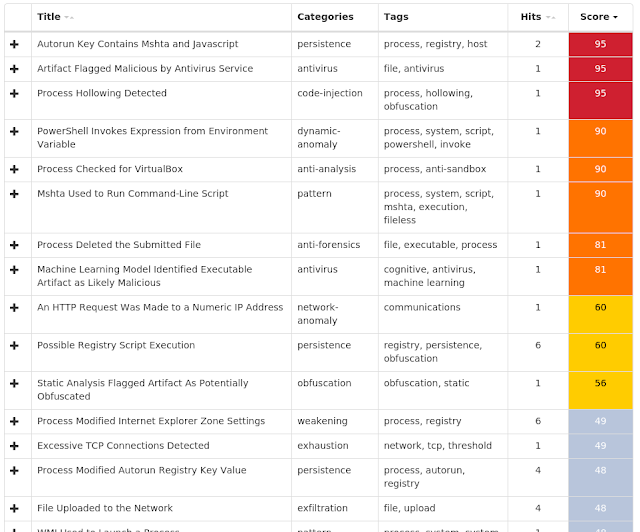
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 24 and May 31. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
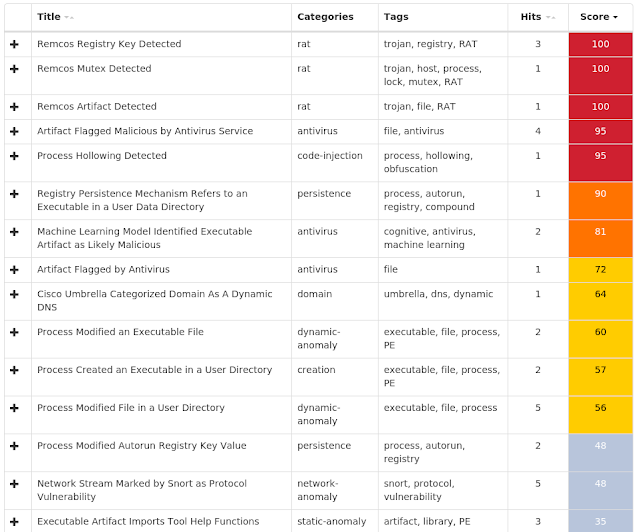
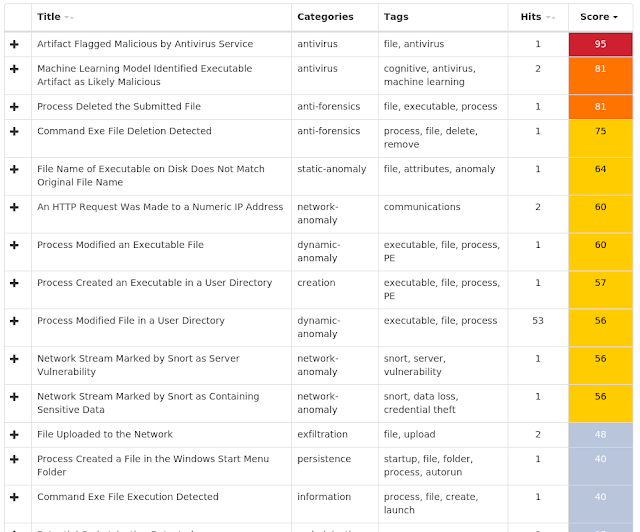
Win.Malware.Remcos-6978637-1 Win.Dropper.LokiBot-6978650-0 Win.Dropper.Kovter-6978831-0 Doc.Downloader.Emotet-6978977-0 Txt.Downloader.Nemucod-6979968-0 Win.Dropper.Qakbot-6984556-0 Win.Malware.Kryptik-6983260-1 Win.Ransomware.Gandcrab-6984356-1 Win.Malware.DarkComet-6983986-1 Threats Win.Malware.Remcos-6978637-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Mozilla
9
<HKCU>\Software\Microsoft\Windows Script Host\Settings
1
<HKCU>\Software\Remcos-8L6ET9
1
<HKCU>\SOFTWARE\REMCOS-8L6ET9
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-8L6ET9
Value Name: licence
1
<HKCU>\Software\Remcos-DMGAK8
1
<HKCU>\SOFTWARE\REMCOS-DMGAK8
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-DMGAK8
Value Name: licence
1
<HKCU>\Software\explorer-N7CBD4
1
<HKCU>\SOFTWARE\EXPLORER-N7CBD4
Value Name: EXEpath
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: explorer
1
<HKCU>\SOFTWARE\EXPLORER-N7CBD4
Value Name: WD
1
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\34ONMET3ZF
1
<HKCU>\Software\Remcos-LMBBE5
1
<HKCU>\SOFTWARE\REMCOS-LMBBE5
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-LMBBE5
Value Name: licence
1
<HKCU>\Software\Remcos-A2GPXU
1
<HKCU>\SOFTWARE\REMCOS-A2GPXU
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-A2GPXU
Value Name: licence
1
<HKCU>\Software\Remcos-4ACKPE
1
<HKCU>\SOFTWARE\REMCOS-4ACKPE
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-4ACKPE
Value Name: licence
1
<HKCU>\SOFTWARE\REMCOS-4ACKPE
Value Name: FR
1
Mutexes Occurrences Remcos_Mutex_Inj
6
3749282D282E1E80C56CAE5A
1
A16467FA-7343A2EC-6F235135-4B9A74AC-F1DC8406A
1
eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-21-2580483871-590521980-3826313501-500
1
\BaseNamedObjects\Mutex_RemWatchdog
1
\BaseNamedObjects\3BA87BBD1CC40F3583D46680
1
Remcos-8L6ET9
1
Remcos-DMGAK8
1
explorer-N7CBD4
1
Remcos-LMBBE5
1
Remcos-A2GPXU
1
Remcos-4ACKPE
1
\BaseNamedObjects\explorer-N7CBD4
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 91[.]193[.]75[.]9
2
184[.]75[.]209[.]157
1
91[.]193[.]75[.]115
1
46[.]105[.]127[.]143
1
185[.]244[.]31[.]63
1
47[.]254[.]172[.]117
1
185[.]247[.]228[.]210
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences uaeoffice999[.]warzonedns[.]com
2
ml[.]warzonedns[.]com
1
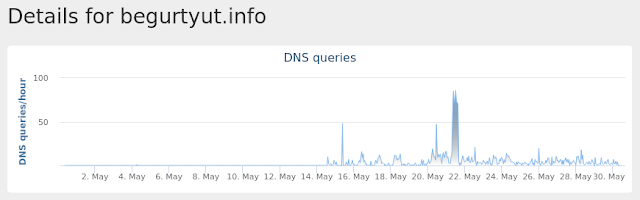
begurtyut[.]info
1
ableyahweh[.]ddns[.]net
1
kingmethod111[.]duckdns[.]org
1
amblessed[.]ddns[.]net
1
kobiremcos2[.]punkdns[.]top
1
bio4kobs[.]geekgalaxy[.]com
1
kobiremcos3[.]punkdns[.]top
1
kobiremcos[.]punkdns[.]top
1
Files and or directories created Occurrences %LOCALAPPDATA%\TVcard.exe
9
%LOCALAPPDATA%\Mozilla\StatsReader.exe
9
%LOCALAPPDATA%\Thex.bmp
9
%APPDATA%\remcos
5
%APPDATA%\remcos\logs.dat
5
E:\TVcard.exe
5
\TVcard.exe
5
%HOMEPATH%\Local Settings\Application Data\TVcard.exe
5
%HOMEPATH%\Local Settings\Application Data\Mozilla\StatsReader.exe
5
%LOCALAPPDATA%\Mozilla\MiniConvert.exe
5
%LOCALAPPDATA%\Sys.ocx
5
%HOMEPATH%\Local Settings\Application Data\Thex.bmp
5
%ProgramData%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
3
%LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
3
%HOMEPATH%\Local Settings\Application Data\Mozilla\MiniConvert.exe
3
%HOMEPATH%\Local Settings\Application Data\Sys.ocx
3
%APPDATA%\D282E1\1E80C5.lck
1
%APPDATA%\D1CC40\0F3583.hdb
1
%APPDATA%\D1CC40\0F3583.lck
1
\??\E:\explorer.exe
1
\explorer.exe
1
%ProgramFiles%\Microsoft DN1
1
%APPDATA%\D1CC40\0F3583.exe (copy)
1
%LOCALAPPDATA%\Microsoft Vision
1
%TEMP%\install.vbs
1
See JSON for more IOCs
File Hashes
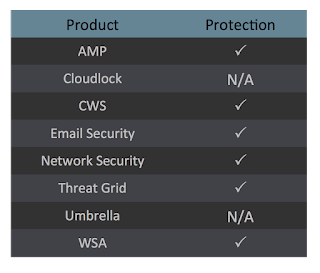
254cc60f64f6db8b54b2033d95f57f6a7f5c8ceea890ccc85f74570eab725b565246657574c87126f2bd268b17f5a4bc44e4dd256cf6eff493c2250c7b1c3d3e5325269f4a381c1c7815863de0dd50b208944993d1f61c38a9f521be609827de585f0d663b32f025514e3740e5ac8dd007f777ce0c384fe664b3266c4159289d9484de151f507a81bb04f24b8bccbe4a63bfe0a1df7ea40ba5a076a52599af63a233e5ce1fc0df70599f3fe8de20d512aac0b59d9d99df58894a34bba89ec81fa969c6228f0de0426084c36c27615dbfa864c71a61c7c4f413fd862fc821db95c71a6c05644b6fa09da4dc8c8d808bc7b0eaa3cac989d5f414cbbb79abea9b37c916075ef74d579828ecb7fb1805076ac3929daac5b43b3c9d22c36d2239cbbad8b92e14d57fb295a1102e9e89c2bdee0e332d87a003d3721b76e1e9eeaa7eb5d9b94599e186e1c3a2507f1672a4a1b9492b4eb3c1a3547b3498c54275306765 Coverage
Screenshots of Detection ThreatGrid Umbrella
Win.Dropper.LokiBot-6978650-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\WinRAR
1
<HKLM>\http://45.67.14.182/slk8/b/cat.php
1
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9
Value Name: F
1
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5
Value Name: F
1
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC
Value Name: F
1
<HKCU>\SOFTWARE\WINRAR
Value Name: HWID
1
Mutexes Occurrences A16467FA-7343A2EC-6F235135-4B9A74AC-F1DC8406A
6
3749282D282E1E80C56CAE5A
5
\BaseNamedObjects\3BA87BBD1CC40F3583D46680
4
\BaseNamedObjects\A238FB80-2231ABE6-BF235135-4DF622E2-F156829B3
1
\BaseNamedObjects\A238FB80-2231ABE6-BF235135-47749B25-DB14F8DE1
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 185[.]79[.]156[.]24
3
185[.]79[.]156[.]18
3
185[.]79[.]156[.]23
2
45[.]67[.]14[.]182
2
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %ProgramData%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
6
%LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
6
%APPDATA%\D282E1\1E80C5.lck
5
%APPDATA%\wfsgsybinp\spflmbuwjdxpyke.exe
5
%TEMP%\2fda\api-ms-win-core-heap-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-interlocked-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-libraryloader-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-localization-l1-2-0.dll
4
%TEMP%\2fda\api-ms-win-core-memory-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-namedpipe-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-processenvironment-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-processthreads-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-processthreads-l1-1-1.dll
4
%TEMP%\2fda\api-ms-win-core-profile-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-rtlsupport-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-string-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-synch-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-synch-l1-2-0.dll
4
%TEMP%\2fda\api-ms-win-core-sysinfo-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-timezone-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-core-util-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-crt-conio-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-crt-convert-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-crt-environment-l1-1-0.dll
4
%TEMP%\2fda\api-ms-win-crt-filesystem-l1-1-0.dll
4
See JSON for more IOCs
File Hashes
1efb2130e792e899d3fee5b0582e61b54f9bdafd00ae43e727d618d462a64a42316522e4f97f2d4f6d568093a043624cbb02d46eb5a7e0f6accfdb188cf1528f319d22b549bcbabce103c5d1359ac65f8e8ae49bff6287de21f3f9ef3138646d36ba85a2d278fb599de9dd36adbe289c39264055996b764d8979f45bcf12353539b14c7b01c68dbd67963156b813ff89c3755b4f12643e6bc92f6ff4b14f40ee680d1d8de9f13d9763a6bc8b2585840b70b7ca6c0f45470bed65f0ce5ca8f908737b0f10471e7d73ec2227dba9250c5130f16b083bc34773e112d72ded4f9e8b7ccb34bd9651f6f27d531128d839d8d0c1853f2b6f29fed69b7e19448bfd30248772387a55e177ff01fa20b6941dddde054c594eee8098cdf96a57e2ccb78b7d8a4d4491deaea94a51586c5098055c335831b37c17f3d8449fba197dfe73a83d98ece7de8b60e356d6a965c8fecc089b86e67e2c29faa941f7cae0a64537abb9ba11b9b4c9e0084e5ae5d0de45761b6bd6ebbb62d41c93c7a23ceeda8461d4b1bda55e17c599b80c688e93249375fb027754aef373ecf8a05f205f1ff4bbf21de650008c2c991f8064942ff5609617d07b4589d40a3e9e37c3c4885898f29f54ea123c9b6299186b1319ec6572bd16fb6a28185f2e9ddb9aa1bf3e52f1911b5defa28604a547613b68480f7e8ac59f8d02931f5b8d4be6971ea96aff253d5d1a Coverage
Screenshots of Detection ThreatGrid Win.Dropper.Kovter-6978831-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
Value Name: DisableOSUpgrade
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
Value Name: ReservationsAllowed
25
<HKLM>\SOFTWARE\WOW6432NODE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUpgrade
25
<HKCU>\SOFTWARE\3a91c13ab1
25
<HKLM>\SOFTWARE\WOW6432NODE\3a91c13ab1
25
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 656f27d6
25
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 656f27d6
25
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 96f717b3
25
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 96f717b3
25
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: ffcfae7b
25
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: ffcfae7b
25
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 01b2a448
20
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 01b2a448
20
<HKLM>\SOFTWARE\WOW6432NODE\RDAW2P1XI
Value Name: tnzJBB
1
<HKLM>\SOFTWARE\WOW6432NODE\XBZ0H3
Value Name: Emk9DIqKS
1
<HKLM>\SOFTWARE\WOW6432NODE\RDAW2P1XI
Value Name: yw6yqsnsb
1
<HKLM>\SOFTWARE\WOW6432NODE\765B49A5A77BF31D
1
<HKLM>\SOFTWARE\WOW6432NODE\byvWyhji
1
<HKLM>\SOFTWARE\WOW6432NODE\765B49A5A77BF31D
Value Name: D347D67C3DAC5505
1
<HKLM>\SOFTWARE\WOW6432NODE\BYVWYHJI
Value Name: aL0JVbstG
1
<HKLM>\SOFTWARE\WOW6432NODE\BYVWYHJI
Value Name: ESqO4Lrhe
1
<HKLM>\SOFTWARE\WOW6432NODE\062D56AB77939C4FB63
1
<HKLM>\SOFTWARE\WOW6432NODE\1ZBB6iJuv
1
Mutexes Occurrences B3E8F6F86CDD9D8B
25
A83BAA13F950654C
25
EA4EC370D1E573DA
25
Global\7A7146875A8CDE1E
25
\BaseNamedObjects\408D8D94EC4F66FC
15
\BaseNamedObjects\Global\350160F4882D1C98
15
\BaseNamedObjects\053C7D611BC8DF3A
15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]170[.]60[.]26
1
144[.]193[.]156[.]187
1
88[.]105[.]164[.]83
1
169[.]202[.]2[.]58
1
208[.]229[.]136[.]68
1
186[.]120[.]237[.]204
1
28[.]237[.]185[.]18
1
216[.]21[.]9[.]183
1
217[.]156[.]137[.]119
1
11[.]136[.]96[.]41
1
90[.]235[.]33[.]244
1
189[.]30[.]93[.]102
1
85[.]82[.]241[.]240
1
87[.]213[.]1[.]121
1
42[.]75[.]114[.]211
1
204[.]6[.]62[.]16
1
112[.]78[.]74[.]19
1
163[.]112[.]153[.]66
1
17[.]210[.]26[.]114
1
27[.]3[.]105[.]38
1
100[.]27[.]228[.]124
1
130[.]139[.]163[.]141
1
128[.]215[.]237[.]245
1
23[.]138[.]20[.]236
1
167[.]165[.]229[.]191
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]cloudflare[.]com
1
demo[.]wylynx[.]com
1
aviators-auth[.]coxhn[.]net
1
Files and or directories created Occurrences \InitShutdown
18
\winreg
18
%SystemRoot%\SysWOW64\tzres.dll
1
File Hashes
0715f9f01ebbe56625dd3e970d7437d97564648e85990c9bdf142b4ecdaca3f107285e9593636743a333a3338ab93bf095fa0907451e471084cd609e7c938281097d7d04e897eca987e28fa7f65a0c3ade12a71de1c758a9a4f5f925c5c602d80a297b9d84a638e994b2c7fec6df3b3847404731fb7c71562f1ccc0ae75506ab0c8b9fa3bbdce9c015b000de00360c16203166088f2e7221af3e790e7309540311bc7f1f1a3cda33e2f6240ab1e88e468c3a63e5ea3a329946992b737e29613616e7c3a7b2a49e61db54ac870d796c37f9e671f64647887f1489ad3bd5ff626c260572ea7138b64d15936143a9a547bab095151cc4d2ee8e2e9b7daf305fb2be26f53bfdf087e36f3d13e5277b12e38ddb1b4989dd009f3f092d1954da0b871728766b46246a485e4c226ff90d93392cf2c706ed3bc60aa0d67fd2772130a9852c32a26d84981b540b5fac0d466092c9a72c93723c2a36d643e6ff8cb8a8067d2cfaede6d177df3e4eff37f5f99cb6a3353d76eac59a708f553abf8269dd2aca30ae1dda31fe6473f13e54e01ad124ad3ea919ceaf196cb9f240ca1dfd79ed4a3509a633922b3ede20640ffff30ffa13785f3972c4228bce33d631458825fe2437bc5d2235c55b03d1b3270f88dac6f210400a192d85c85405593424af5c4c603a105a570eab21e12a4895a0ccf65b0d4b2bff313567e3e52119b1c14e8ea7503c3166135909f4e982f313d6f28cbd44057f96a9ace0b1ffc9fd085d577fc4aa3ea71c0fcc071c4eb5195f17a6b35156a5cc3602b2e1f5a6e90f9cb2ea315a073eb27755726ae476869cd8054527c1d0f6f49365c9efda8887013af895146c0542561fe7ca1b2322cbe4d910d4c6d7d74a7089a33974a0bef7a45f7235267cd642ac2333962667d01a4296c64cfd907880c64dfbb9439a3a471f8080024e9d0753dc0aee9d383c234bf9ffd2a49a25ae2affc2275b8806a72e343744f0a9e2ad56ac99cd20dce48020e300dd3b46e9813552ad890b5e52e3d1c46247f6bb8cae5700b5bfde766173f1dce5ccceb7ba015c22cb327f9591e700b8ebacfd158ed5597f778320e6a1a30ab8905f7abdc796c490bd0a87f09c0a02f7849eb0b80585See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Doc.Downloader.Emotet-6978977-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\sourcebulk
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Type
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Start
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ErrorControl
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ImagePath
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: DisplayName
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: WOW64
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ObjectName
38
Mutexes Occurrences Global\I98B68E3C
38
Global\M98B68E3C
38
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 115[.]71[.]233[.]127
35
74[.]207[.]227[.]96
28
23[.]95[.]95[.]18
28
172[.]217[.]6[.]211
24
65[.]55[.]72[.]183
23
74[.]6[.]136[.]150
21
69[.]147[.]92[.]11
18
74[.]6[.]141[.]50
17
212[.]77[.]101[.]141
17
69[.]147[.]92[.]12
17
196[.]25[.]211[.]150
16
212[.]227[.]17[.]168
16
212[.]77[.]101[.]1
16
172[.]217[.]12[.]211
15
159[.]127[.]187[.]12
15
173[.]194[.]207[.]108
15
72[.]167[.]238[.]29
13
104[.]131[.]11[.]150
13
64[.]91[.]228[.]45
13
200[.]27[.]156[.]230
13
64[.]4[.]244[.]68
12
200[.]27[.]156[.]160
12
207[.]204[.]50[.]10
11
68[.]178[.]213[.]203
11
213[.]165[.]67[.]108
11
See JSON for more IOCs
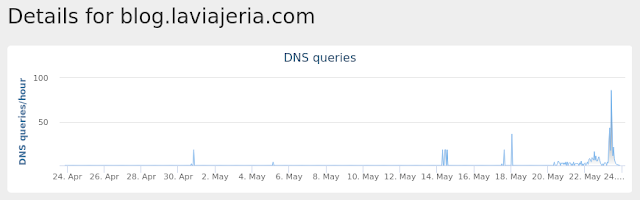
Domain Names contacted by malware. Does not indicate maliciousness Occurrences blog[.]laviajeria[.]com
25
smtp[.]aol[.]com
17
mail[.]wp[.]pl
17
smtp[.]wp[.]pl
16
mail[.]aol[.]com
15
mail[.]paypal[.]com
15
smtp[.]telkomsa[.]net
14
pop3[.]telkomsa[.]net
13
golfingtrail[.]com
13
smtpout[.]secureserver[.]net
12
smtp[.]mail[.]ru
12
mail[.]web[.]de
12
smtp[.]paypal[.]com
12
imap[.]secureserver[.]net
11
smtp[.]orange[.]fr
11
mail[.]secureserver[.]net
10
smtp[.]1und1[.]de
10
smtp[.]outlook[.]com
9
smtp[.]yahoo[.]co[.]uk
9
smtp[.]secureserver[.]net
8
mail[.]rochester[.]rr[.]com
8
mail[.]ccsu[.]edu
8
premium68[.]web-hosting[.]com
8
mail[.]gmx[.]de
7
mail[.]msn[.]com
7
See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%\905.exe
25
%HOMEPATH%\985.exe
13
%SystemRoot%\Registration\R000000000005.clb
1
%SystemRoot%\SysWOW64\sourcebulka.exe
1
%SystemRoot%\SysWOW64\RaIsI.exe
1
%SystemRoot%\SysWOW64\b7CLyYeMYOz.exe
1
%SystemRoot%\SysWOW64\JAfDaABdFwDwQOmU.exe
1
%SystemRoot%\SysWOW64\XsURGMXS03AY8k5H.exe
1
%SystemRoot%\SysWOW64\B3G3HJkHw.exe
1
%SystemRoot%\SysWOW64\OACv5sbfWOqW.exe
1
%SystemRoot%\SysWOW64\vQPrd2DqNc.exe
1
%SystemRoot%\SysWOW64\eZctuX442LBnjCR.exe
1
%SystemRoot%\SysWOW64\G4gruKLDsT8Hqq.exe
1
%SystemRoot%\SysWOW64\H2TI.exe
1
%SystemRoot%\SysWOW64\0UiKEdt.exe
1
%SystemRoot%\SysWOW64\lI7hCDdPp88lp9wc9FI.exe
1
%SystemRoot%\SysWOW64\jvfRQuzTShGWsLy.exe
1
%SystemRoot%\SysWOW64\pFZeNxzUSolEMyg5jlf.exe
1
%TEMP%\CVR99F.tmp
1
%SystemRoot%\SysWOW64\s5nWep8.exe
1
%SystemRoot%\SysWOW64\OBG55Zcwc0ZIAIzMsrO.exe
1
%SystemRoot%\SysWOW64\rrLgU5ygLqi.exe
1
%SystemRoot%\SysWOW64\Bbnxe2ZT28fYyG.exe
1
%SystemRoot%\SysWOW64\4CrV663kwXBhNO.exe
1
%SystemRoot%\SysWOW64\rnrtEbeM2u.exe
1
See JSON for more IOCs
File Hashes
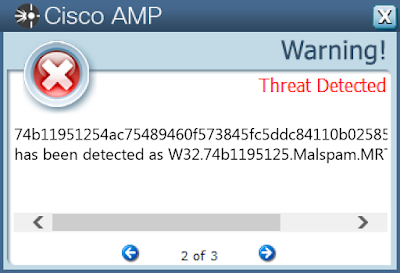
08891649a39702f90e11f8ff3035fd16c8f2431d16eeb4919382414735a342be10b5e211a2e7f00f87d2074a183f9870459e588772f2434ae2e597f800f8522a173f2078c872504912c5878cac192ab6e7aee9da8f2b76505a7c201eec5af2f217dbcd96af456b87e928609743c3a232e438e3b7f31be3f82d9912605a17e7e51a1c4b3314857aed3c55053968fa6260693577ee18e59f29be78e9add0e528401afd12fda74676381f591b7e2dd6dd2510e603308504a73c880ab6990bd49d3228398ed10fb49cc49f2cf4559ccbd2b5ce7213c0d62694dd637a5ec8d304352b286d190e59b9fea171a55e2d99f2c4c5a66560c2e919199a67a6a960f5acd0792875510d0044c059a8f554aa8401cacd69f806a46205632a11c02096ecb6a0e829a3ee36c05e27f07958695833e5f49f2579ce005fabd6048d74285b9dfc40e940abbe8ec1e3c31efdedfabaeadc4cdcb88e918f7a0ed7dd3092e26fb2dd676e4e82b20ca98af17b4361fe688bce991cd907e25c139b9da39340fd758a6bd22b4f65fb3713b36e2c0eb64e8e77a3aa6bd3e4367ffd3184b179da869ff094cacc510f007b77f469f04508b716ab447ce6b2bdcb592aaf4854d236410e61009ee4598ec9fc1bede336d31abbeaa17ee90fec033e46ca742d16e17b25efa2bfe8dc5a217e950f27df7da794e729b22980c2aa1417696ffa1ee861ce9e657fd35bbb5c0a12520509cc3dced61c92a635e06dc369f5fe537f6dd74cde28a383beaaf86850221b3ed9b438b4959fac2fa86ef2731267ecef2c539e128621a145f8f0b1720d9323f66abad23ddc1a0274f13ada330575fa1566fc87c81faad0983b2a7274b11951254ac75489460f573845fc5ddc84110b02585520cc175b02162c212e74bf67c7c1ed3eafd43b099b40d537ea115190c49e4e3e956e42702ea9aa904b7db9895829ef195f34659278d7f47618703cb2c535183f41dfc51a8263c7b4c583b3bc37bf99bc56096c76ecfd19cb34a70d0d9656f926598625417b5c425fc78691ab6505118b9ca2818db4e3ece4edcd40cedc4ba3b5a00dfbc7a1c12d58e686a50c8e8f5d300f3731ebdce8b98be02696e2ff1d7e979abd873354bfd87006See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
Txt.Downloader.Nemucod-6979968-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\System32
18
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\Configuration
18
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xi
18
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Client Server Runtime Subsystem
18
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xVersion
18
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xmode
16
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xpk
16
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xstate
16
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xcnt
16
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\DAC9024F54D8F6DF94935FB1732638CA6AD77C13
Value Name: Blob
14
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: shst
14
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: sh1
14
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xmail
9
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: shsnt
9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]109[.]206[.]212
9
95[.]216[.]12[.]141
9
104[.]18[.]35[.]131
9
104[.]16[.]154[.]36
8
104[.]16[.]155[.]36
8
86[.]59[.]21[.]38
7
104[.]18[.]34[.]131
7
208[.]83[.]223[.]34
6
154[.]35[.]32[.]5
6
171[.]25[.]193[.]9
6
128[.]31[.]0[.]39
5
193[.]23[.]244[.]244
5
76[.]73[.]17[.]194
5
62[.]173[.]145[.]104
3
85[.]93[.]145[.]251
3
131[.]188[.]40[.]189
3
138[.]201[.]169[.]12
2
78[.]129[.]150[.]54
2
82[.]192[.]94[.]125
2
134[.]19[.]177[.]109
2
109[.]234[.]165[.]77
2
173[.]254[.]213[.]13
2
94[.]73[.]147[.]165
1
148[.]251[.]155[.]108
1
212[.]237[.]210[.]8
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com
16
opengraphprotocol[.]org
16
wsrs[.]net
16
whatsmyip[.]net
16
aff[.]ironsocket[.]com
16
cmsgear[.]com
16
www[.]zagogulina[.]com
2
api[.]w[.]org
1
gmpg[.]org
1
t[.]co
1
www[.]lagerpartner[.]dk
1
adasnature[.]rodevdesign[.]com
1
toolingguru[.]com
1
specialsedu[.]com
1
tuttyguru[.]com
1
hoiquanarsenal[.]000webhostapp[.]com
1
stakesedu[.]com
1
techjoomo[.]com
1
tbuild[.]2tstelecom[.]com
1
fruityytech[.]com
1
techyoun[.]com
1
www[.]adasnature[.]rodevdesign[.]com
1
trutthedu[.]com
1
essexweldmex[.]com
1
ashleyharrison[.]tech
1
See JSON for more IOCs
Files and or directories created Occurrences %ProgramData%\Windows
18
%TEMP%\6893A5D897
18
%TEMP%\6893A5~1\lock
18
%ProgramData%\Windows\csrss.exe
18
%TEMP%\6893A5~1\state.tmp
18
%TEMP%\6893A5~1\unverified-microdesc-consensus.tmp
18
%TEMP%\6893A5~1\cached-certs.tmp
17
%TEMP%\6893A5~1\cached-microdesc-consensus.tmp
17
%TEMP%\6893A5~1\cached-microdescs.new
17
%TEMP%\6893A5~1\unverified-microdesc-consensus
17
E:\README10.txt
16
E:\README2.txt
16
E:\README5.txt
16
E:\README6.txt
16
E:\README7.txt
16
E:\README8.txt
16
E:\README9.txt
16
\README1.txt
16
\README10.txt
16
\README2.txt
16
\README3.txt
16
\README4.txt
16
\README5.txt
16
\README6.txt
16
\README7.txt
16
See JSON for more IOCs
File Hashes
01446b1b8130f7e962e12ff9a50d5da8acb394be437f000d77f54e39527b7ab80aa15df3fca9a49cf616d6ee3dbc9d29fde8f272466788a217e15c28ec6ef3f519c6c4e0d94e88f3460549dca47715ba9f0f0e928f127eb45706c38d9979163b1e91a7eb97063517cb8798dafe93fb2f20eec7f4100b4175ec26c7f975aa69651ed50005b56e0fd4828799e74bc5f78d2cc887934b891c23eb28d5b5cff1413937134b5f952e7c0108685d16963663687637ec006a86a15feee1afca36e8b76538be93101842cd74079121d4864d37f971cbad305c993ef2d465bb2bb6706d3d43d78a497d4fc7a500e33d09bda1b93097727c703b7a0ed698bda3b417efd7c4467be08133e9e2c683444bb21eef42864df9603cf22cde4ddf777a7d1c24236247b28eea9dc3aea93a1c361b3e5db6d1cf88021225c43ba364f11959a834049e54a6d6b359a4119a0009c2fec6f430a06df2aa6a0793b79feafe1a89b0e09010640f7ee70f167a82e02a174c8f084ecec19b7a5481b6f7e399dfd25ad64f4da57b1d29992c3c9be33294af41981d48ba92a773f2d6bab6142d625aa5b7d96a7d856b8aed7661ec632ccdba1e738e990703a53dd241c99a1627df99ad5bd3a478869daf9d7e0ba9da47e604ca310022fa7aeb7a3a2ca7c1dc976958b634ab9cc594c3139cb64e42264c87afd46f879702b45c33e6711d1777a4ce3faa134faecf986a7e2a2199640a2b156ad35a9313070bab0f89402bf9f6daff03c76748c76ea3c8f9e92437fc83ad502f12eeb5aa97828b060168e50914aef6504961c82263ab05542f803dfe04d1941ca646a3c9f10d04037475655bb1b9495dc82279fcd3af66d0c9ab90be7dee01a389e351dc52a025be4579a7ef9cb290c4348c499cb6be77578b063aeb67fa49b17d0474229e4573ab79e48d9d68e4250a063884d7c6c22bb64479d12c5322e20c8cf88d7ddd68157d81b9211764a7f46e9096c56594cf86b58dcc90b88df0f81d7e4db87e2c687baae11058924a74e91594ee8a0965d6b029b0280f7c3e1a9be0dff1d9ce58e173b4fca568a80e62c69248398eed53d93ad8604d87827ce1312c1640df2a49ba9f3c592ef9f779ae38eb76a9d95739See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Dropper.Qakbot-6984556-0 Indicators of Compromise Registry Keys Occurrences N/A
-
Mutexes Occurrences ocmwn
36
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences N/A
-
File Hashes
0416a1f1118ca4e50afdee9c1e76cdca0b19e374d2be21ed1ea6cf96eadc60330f70dc9c66a9bc37b7edfa1cb2d3566c53b63d67b8e8fd4c78f0f9ac08fc7a7b0fbd8df6ea3398aa3c7a139679fe60ab90766a4dd81e3ae6feface7a24061b310fc09554d5f6f9059e6c251108caf5921db41ce23e791d418b4587108aae62db122f88c01202cc59a9cbb11b8eff11e4b1ff98b8a9e7956db2c0161bd633e4511df18b6c34f6eab5ba1de274793f94f6168016cfe00008db3a38d79031936b8125194a4d3d7b860d1c2a722eeccd45d7c6bedb3fe2967e83bd28e9b3ea6bb0332c738330714e592259d090d03400fa3cc4f2ae7f16b2e3616a5b8bc16e29c72e2de648c80d9122fc3081aabf4d6257e03fecb57d9fe6e1b98b4e79f28516b8a22f769a70e02699e161593dc619e354028e3f3b23ea76cb8b493ef68595bc2b673b24ecd81735aaa4c459aa8e5378595eb6bc043d607eeb90b56ba89a962f56a840a186d85f12a21d4b65650ab513e723d0ebac79256307b6772257d4d936418843b8424bdd21dfbfd81cfc4b2f31706f2bfd21c5d5dd99b17be2b78ceb3a98e247d0d80d31c6b02e009585b97702fac60a958c5443a07ac62a68ef24b39bfcf44a961cc37b6f6c9e650d4aefa99de46a564679783b5ebaf631b10ac0e891191d4ac3ceb7094c7c2a5edd95bb21a5b87e6f644cb03b0b72bb9f436623ec2b11d14af9db7adad64a3ccffb37a051672cbd119524999968837300763d1f0143d2184b1becbe4702e8e370a3c0ba0d1ae6c3b0794de26b1db1730c609d2675f7edbd4c36e499054de9b6a674a54d809083b90ffef539a33f76ef49d7a1bfe89ddfd256d8a1d419389fc826ca627bd62b90d8c1c78c1de9c906d73cc2f9a90aace0a65931e1ea80e1b82dbf84db29d4bcdf01feecc7a0efb3fac05bc187abf29a588c61e2e922cae2ebed761d7ebc4e43e48821097821213216a17ec7690325c18f6f62679544133ce6ec6a09ac7b374cb3c51e82ad5486499467ad58b4115850f11066ef03a7d4628f9c40801b5ffd192376dce602214947e29f32d676f908c41d1870d91dbb7fb60dfcee3cfa585eed0efcdd25620bdb5ffffd8431e02876ee65ddSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Kryptik-6983260-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: drippt
25
Mutexes Occurrences 3G1S91V5ZA5fB56W
25
8AZB70HDFK0WOZIZ
25
ATYNKAJP30Z9AQ
25
JKLSXX1ZA1QRLER
25
NHO9AZB7HDK0WAZMM
25
OMXBJSJ3WA1ZIN
25
PJOQT7WD1SAOM
25
PSHZ73VLLOAFB
25
VHO9AZB7HDK0WAZMM
25
VRK1AlIXBJDA5U3A
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences N/A
-
File Hashes
037a8cc036ef9b395300b6e56deb931f411d1fb498aefa1417fc5905f5a355b70e699ed4adcd822951f647d9d34873eb45436d8e08f273c6edc271b3a28a63b31693124dbb76c552ea96d94aeb56bcf673b29a4207be877743bc8e5b7404a9c51c3eb8b78b435fb261296e5afe7eca9d2f898e75a953edad8eb4b8788875e5b61cc0c215b78bc42e9926e822e8b3c05fca8dddfa23e6cbd245087309a9ac114c233dd554a6e99d66c3c5b03a60c25c5737b1da6a6fa13b3e594da1deb5c47dcd337b52e708905c51d83d570edd07379322270d6ef25a981a801776b2e60cf82a37ae2b35640423e3074277bf9c6f6e0f25d47251418b66ce9b37c761541640233d2017ed5b3f99c43cc17ea72e95a4209be22d7cd0ed8c6b9d43add50628d6cc432ce20272510c1a6112aa246b0cb321976a299b054d2b82b94598ed59ee7f444ac6c836b35945108c53f863e441e659baaf099279f06e0aa01d41f1739a980d4f2333d05cdb8293b85e64bbb891eb5a8ad1ab322babf8993b854e37135a8677513171233ab20f2e5f474ec0e00498a7e800c8c6d31f575ace21677e9a834667571cfa598f094ad73ff6237ae66c938cb2832bf04196442608107fc3b46a967f59010e05103e93fcb5bd33a0f13b8780720ac23694a1d12e4a5d59e3e8aa09846067621b4ecf4018e42e5ed195a8e179a3e6c259025b6f248e6b8bbd2b2057046a73e94427c84a3e16e9c2c7ee4404ae93137cd08852fbb33dda67bacebbf0a66c2c7bab2520d774d6054b789047916f59f741b561db2710351b96e36b10f000710436e038f3406ba539b2fdf91478ba44b4ac14e4738ef9dbc25fc0b2fe7105712119bcb97d93941e5668fe8977fdbf5a06eb435d7b611094a87caf54fffb72747c08074c51758e03b550d571830cbcdaaf0ce6ad6721d7d07de7f0f3df0b628662a730cdb3d3303e5ae5ef9beafd74473487fac7f06542f0154cbbe56284f98a5f573dd497c0d1adc337bf71f6a37b9b9cb0ba79607950c7fc92cc45508c1694bceae74cc733290eaa6830bfc61bfdeeafaf1d609439d5d9bc718b8ffc668a989eaa8e832dee1ea28452e91c30556ed1b84cb38d1381361770469c599db4ceSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Ransomware.Gandcrab-6984356-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\CONTROL PANEL\DESKTOP
Value Name: Wallpaper
3
<HKLM>\SOFTWARE\WOW6432NODE\ex_data
3
<HKLM>\SOFTWARE\WOW6432NODE\EX_DATA\data
3
<HKLM>\SOFTWARE\WOW6432NODE\keys_data
3
<HKLM>\SOFTWARE\WOW6432NODE\KEYS_DATA\data
3
<HKLM>\SOFTWARE\WOW6432NODE\EX_DATA\DATA
Value Name: ext
3
<HKLM>\SOFTWARE\WOW6432NODE\KEYS_DATA\DATA
Value Name: public
3
<HKLM>\SOFTWARE\WOW6432NODE\KEYS_DATA\DATA
Value Name: private
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\Notify
2
<HKLM>\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\Windows\system32\rundll32.exe
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\gctilof
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\GCTILOF
Value Name: Impersonate
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\GCTILOF
Value Name: Asynchronous
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\GCTILOF
Value Name: MaxWait
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\GCTILOF
Value Name: DllName
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON\NOTIFY\GCTILOF
Value Name: Startup
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: gctilof
2
Mutexes Occurrences A16467FA7-343A2EC6-F2351354-B9A74ACF-1DC8406A
20
Global\8B5BAAB9E36E4507C5F5.lock
3
Global\XlAKFoxSKGOfSGOoSFOOFNOLPE
3
A9MTX7ERFAMKLQ
2
A9ZLO3DAFRVH1WAE
2
AhY93G7iia
2
B81XZCHO7OLPA
2
BSKLZ1RVAUON
2
DRBCXMtx
2
F-DAH77-LLP
2
FNZIMLL1
2
FURLENTG3a
2
FstCNMutex
2
GJLAAZGJI156R
2
I-103-139-900557
2
I106865886KMTX
2
IGBIASAARMOAIZ
2
IGMJIA3OX
2
J8OSEXAZLIYSQ8J
2
LXCV0IMGIXS0RTA1
2
MKS8IUMZ13NOZ
2
NLYOPPSTY
2
OLZTR-AFHK11
2
OPLXSDF19WRQ
2
PLAX7FASCI8AMNA
2
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]31[.]71[.]122
10
192[.]42[.]119[.]41
4
185[.]62[.]170[.]1
3
52[.]17[.]9[.]185
3
217[.]26[.]54[.]189
3
83[.]166[.]148[.]69
3
217[.]26[.]53[.]37
3
213[.]186[.]33[.]5
3
136[.]243[.]162[.]140
3
195[.]201[.]207[.]213
3
188[.]165[.]40[.]130
3
46[.]32[.]228[.]22
3
185[.]58[.]214[.]106
3
185[.]51[.]191[.]29
3
149[.]126[.]4[.]15
3
193[.]200[.]231[.]4
3
194[.]51[.]187[.]23
3
83[.]166[.]138[.]8
3
5[.]144[.]168[.]210
3
136[.]243[.]13[.]215
3
83[.]138[.]82[.]107
3
192[.]185[.]159[.]253
3
193[.]246[.]63[.]157
3
149[.]126[.]4[.]89
3
194[.]51[.]187[.]22
3
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences electrumscoin[.]org
10
PALKANKA[.]SITE
6
doa[.]wolexsal[.]at
5
www[.]cantinesurcoux[.]net
3
www[.]pizcam[.]com
3
www[.]hotel-blumental[.]com
3
www[.]arbezie[.]com
3
www[.]holzbock[.]biz
3
www[.]disch[.]mehrmarken[.]net
3
www[.]alpenlodge[.]com
3
www[.]hotelolden[.]com
3
www[.]hotellido-lugano[.]com
3
www[.]petit-paradis[.]com
3
www[.]hotelrotonde[.]com
3
www[.]2mmotorsport[.]biz
3
www[.]flemings-hotels[.]com
3
www[.]hardrockhoteldavos[.]com
3
www[.]bnbdelacolline[.]com
3
www[.]arbezie-hotel[.]com
3
www[.]mountainhostel[.]com
3
www[.]lassalle-haus[.]org
3
www[.]alimentarium[.]org
3
www[.]bellevuewiesen[.]com
3
www[.]kroneregensberg[.]com
3
www[.]waageglarus[.]com
3
See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\pidor.bmp
3
%HOMEPATH%\98b689da98b68e3f316.lock
3
%HOMEPATH%\AppData\98b689da98b68e3f316.lock
3
%APPDATA%\Media Center Programs\98b689da98b68e3f316.lock
3
%APPDATA%\Microsoft\98b689da98b68e3f316.lock
3
%APPDATA%\Microsoft\Internet Explorer\98b689da98b68e3f316.lock
3
%APPDATA%\Microsoft\Internet Explorer\Quick Launch\98b689da98b68e3f316.lock
3
%APPDATA%\98b689da98b68e3f316.lock
3
%HOMEPATH%\Cookies\98b689da98b68e3f316.lock
3
%HOMEPATH%\Desktop\98b689da98b68e3f316.lock
3
%HOMEPATH%\Documents\98b689da98b68e3f316.lock
3
%HOMEPATH%\Documents\My Music\98b689da98b68e3f316.lock
3
%HOMEPATH%\Documents\My Pictures\98b689da98b68e3f316.lock
3
%HOMEPATH%\Documents\My Videos\98b689da98b68e3f316.lock
3
%HOMEPATH%\Downloads\98b689da98b68e3f316.lock
3
%HOMEPATH%\Favorites\98b689da98b68e3f316.lock
3
%HOMEPATH%\Links\98b689da98b68e3f316.lock
3
%HOMEPATH%\Music\98b689da98b68e3f316.lock
3
%HOMEPATH%\My Documents\98b689da98b68e3f316.lock
3
%HOMEPATH%\NetHood\98b689da98b68e3f316.lock
3
%HOMEPATH%\Pictures\98b689da98b68e3f316.lock
3
%HOMEPATH%\PrintHood\98b689da98b68e3f316.lock
3
%HOMEPATH%\Recent\98b689da98b68e3f316.lock
3
%HOMEPATH%\Saved Games\98b689da98b68e3f316.lock
3
%HOMEPATH%\SendTo\98b689da98b68e3f316.lock
3
See JSON for more IOCs
File Hashes
0056173ac7818058a9ef3025473fceff24386f8dd61c23b3ca53f332b7b8b756010dd10aebe976dbf2473a656f0449c0a91aff6732d82fa605974d5452a1f8820c3a00f9adfbb35f60aa3a67e02ee7fe5f01464d08825c2a0b181c55538094840cd7b76e663ef841a0468a4542f9594a212f682bda4fd13ac596c8dc375a70a10dd538728ed3de4c0f112e503825028c6de6a19d176093b4f8ee2aba784e96e412a9b70fb4e43716b450c37120a63c2da29e7a3c8657a95a1f318a4853550968157f96de23735d1c41df83f0a4deba3a4c64d7d0b15d4cce28a9166131e085bc19d7bab5cc8305e6fa1b248ceda3fb40dfe9d5256b1f8897350ccd2110c235d5259220ed0a5fadd095aee079bf2fb8fa27f2204f3ebe95b588014bf4654d925d411d66336a7a62138158211a0c9d47760cf072a86ea27cddfb173a59a4839a6e4446a42ec66656956467df28df5c1e587d4c4cfd804201ba9912fd5729bb8f644b4f963ed8910f44f75ca75a2c21f7a31f600761bd97517246f7aa8f2ab5c4ff4c9cb943f1efb719c8bb4907d89fa296bb53f010e53fd8f1da09667be0055aaf50e6406dd568defee6835b152a2af2b82956004a87011d9da202648197dfaafe510fd9535d75bf55e09028dc6f015798c7050d39f60b9ed86f7ce392d08ccc3653248110e4f2ffb57520d2bbedc2cd4efe486c2a05243eb60807242bbfcbdd0e5a70e3f4169bfc369c5d6686eb5f6a3170b39dc4fa5196d39d2d9409075665cf5c562a47c8bb34f90f70377862dad9f134d6d5ae2d01595ea8225f51f8c7ed99618d93da49f253e9ece275eaf87c9639489d5f876dec9b1ce6fb14fc22d1c17566ef34785cdbbccb9cc46e69902d4e4f227134ddd2f8275430e3656480d79caa729c6ae5d8415d8b49c646807a4b95ddef38626bce3303cf08c4cdcc505196cf76151d8b9598ed85a90c04ce2b8c19fb93efc435b9982dd37565bdc92a494ad37872ffcf0a320ec62c57954bb55158876958adf3c9a41ff470da476a13cbbef7796b0898478bb8ba453d4d974ab43aacf5c7e85bafa8e86133a284f47ab214d98775ce35c810ebe3d2e0f8a9c84b77e38bd5d2d682a4e65a3fc9f9a86df52aa1See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.DarkComet-6983986-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
1
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
1
<HKLM>\Software\Wow6432Node\Microsoft\Active Setup\Installed Components\{16E11FA4-EASQ-57E4-QPP4-4B4EE7V76IQ4}
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: system32
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: system32
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{16E11FA4-EASQ-57E4-QPP4-4B4EE7V76IQ4}
Value Name: StubPath
1
<HKLM>\Software\Wow6432Node\Microsoft\Active Setup\Installed Components\{0D285L58-7O12-HSU1-C880-04J8UU718520}
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: WinUpdate
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: WinUpdate
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{0D285L58-7O12-HSU1-C880-04J8UU718520}
Value Name: StubPath
1
<HKCU>\SOFTWARE\Cofer2
1
<HKCU>\SOFTWARE\COFER2
Value Name: FirstExecution
1
<HKCU>\SOFTWARE\COFER2
Value Name: NewIdentification
1
Mutexes Occurrences \BaseNamedObjects\_x_X_UPDATE_X_x_
13
\BaseNamedObjects\_x_X_PASSWORDLIST_X_x_
13
\BaseNamedObjects\_x_X_BLOCKMOUSE_X_x_
13
\BaseNamedObjects\***MUTEX***
4
\BaseNamedObjects\***MUTEX***_SAIR
4
\BaseNamedObjects\***MUTEX***_PERSIST
4
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences loucao22[.]no-ip[.]org
1
Files and or directories created Occurrences %TEMP%\UuU.uUu
4
%TEMP%\XX--XX--XX.txt
4
%TEMP%\XxX.xXx
4
%APPDATA%\logs.dat
4
%System32%\install\server.exe
2
%SystemRoot%\SysWOW64\install
1
%SystemRoot%\install
1
%SystemRoot%\SysWOW64\install\explore.exe
1
%System32%\install\explore.exe
1
%SystemRoot%\install\flashplayer.exe
1
File Hashes
001dadb87b55db69aaab1edcbf7c38bba929732e83c16d84278c992687d157fc4ca9b2f8018dd2789f91fca2ad5a2281875bd3a6239a56ec29ff3ce366265d985780956f6411277398daf452baa75bdfcad2bd93c4a97af4e07ac0e20fbb9f0c7ad5f208199b49bd14cbb26a1d8888c07692830d84b9be29920bc1db37c0b1e18a006d694bf6d30e2f711fce6e612d2880fba6d95085e41c57d0b76b88392b4495728734cc57a788f44b2c8a7cf6601b0f4b7b2c05b85aa893a926d1c4c799d7a9a09f58cc3dc6d6d097ee2ffcab7ec256c157d778979f5e80c1212ff68f3eb3d2211069cc40d43f81d9c81274976aff64ff52e5858ed573d26cd5503dd563eed90b4a4ade207ebf768af252cf8d9b032158122670c50eb6bfafeec74d695f58eb914c411fdc043c690ed0d1361d82d73dca6e764150c0bce4a20d9439df9c8bef2dae7f7d3a706a766ac41478adb9dd2dd871f88d458ace41e9813670cc99bdf094dbe9dc2bbc7337e2aa1317317f1a7833bad9d966f01ebb582d51ce8d3b23f1a0dda889f3af093b9092b8652fd7847de05015dee0914d36937c2ef641fa46f51b96ebe4242a34754e14d0d2bc0dcd5ccd446f0eeb5fcdb9b7e03686dc40cc Coverage
Screenshots of Detection AMP ThreatGrid
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (3512)Kovter injection detected (1779)PowerShell file-less infection detected (513)Process hollowing detected (478)Gamarue malware detected (288)Dealply adware detected (285)Atom Bombing code injection technique detected (60)Installcore adware detected (59)Suspicious PowerShell execution detected (55)Excessively long PowerShell command detected (54)