EXECUTIVE SUMMARY
Exploit kits are an ever-present and often forgotten threat on the landscape today. Their popularity seemed to peak several years ago with the success and eventual downfall of some of the best compromise platforms ever created, including the Angler Exploit Kit. These kits generated millions of dollars from their victims and they are still effective. One of their biggest appeals today is the removal of reliance on user assistance. Increasingly, on the crimeware landscape today, user assistance is required, whether it's through blatant social engineering attacks like ongoing sextortion campaigns or through the countless malspam messages traversing the globe daily, users are required to help achieve infection. That is where exploit kits stand alone as an effective web-based platform for compromise that only requires users to surf the internet.
Today, Cisco Talos is unveiling the details of a new exploit kit campaign that proves exploit kits are still a threat and should be taken seriously by defenders: Spelevo. This recent campaign leveraged a compromised business-to-business site to deliver Spelevo, one of the first new kits we've seen in months.
Spelevo illustrates many of the challenges associated with protecting against these threats and preventing their spread. In compromising this particular website, the attackers did little more than add four lines to the code rendering the webpage — but those four lines did a lot of damage and can compromise all visitors that have poor security hygiene. Even though Angler did make use of a zero-day in Adobe Flash Player years ago, exploit kits largely depend on existing, patched exploits. However, all it takes is one missed patch on one system to lead directly to compromise. That's why you need things like a thorough defense-in-depth approach with various technologies in place to help mitigate any residual risk that comes with running an enterprise.
BACKGROUND ON EXPLOIT KITS
Exploit kits are something Talos has covered in the past, including some more memorable deep dives. The goal of exploit kits is fairly straightforward: compromise random victims on the internet using disclosed vulnerabilities to deliver a malicious payload. It achieves this through a couple of components: a traffic direction system (TDS) or gate, landing page and exploit page. The challenge for most adversaries is getting traffic to their kits — and there are a couple of different methods to get it there.
Today, most exploit kit activity Talos observes is powered through malvertising, or the use of malicious ads. These ads are usually hosted on a variety of different web pages and platforms, but most commonly is associated with illicit streaming services and adult content. However, this is not the only way users can be directed to exploit kits, as Spelevo shows. Spelevo leveraged compromised websites, another popular method, to infect victims.
Exploit Kits have one large limitation: Internet Explorer. For exploit kits to operate effectively, adversaries need to take advantage of an antiquated web browser that lacks many of the modern protections designed to defeat this specific type of attack. But the amount of people actively using Internet Explorer continues to dwindle as they migrate either to modern Windows-native web browsers like Edge or to some of the other open-source solutions like Mozilla Firefox and Google Chrome. However, Internet Explorer remains somewhat popular, and exploit kits will always be there to take advantage of its users.
SPELEVO DETAILS
Cisco Talos began observing an increase in exploit kit activity and started looking into one campaign in particular. It was during this investigation that one of the compromised web servers was identified and the full campaign came into focus. The activity appeared to originate from a business-to-business (B2B) contact website. This website initially appeared to just have a single page compromised, but as the investigation continued, it appeared that the compromise was more significant with multiple pages, including the main homepage redirecting to the gate used for the campaign. To their credit, while the investigation was ongoing, the site was already dealing with the compromise. The actual compromise is subtle, adding only a few short lines.

There are actually two different connections that these couple of lines establish and start the infection process. One thing to note is that this particular kit opens a new tab when they are compromising the system. In this case, the actual gate is being hosted at ezylifebags[.]com[.]au with a 302 cushion.
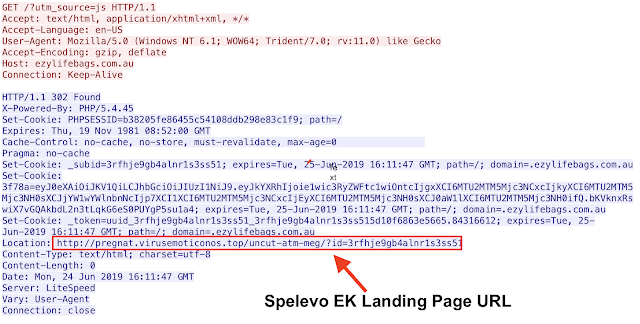
As you can see, this isn't the only additional script dropped on the compromised website. There is also a request for another JavaScript file being hosted at your-prizes-box[.]life. However, this request doesn't result in anything but additional requests for the same file via 301 redirect and could be used as an additional tracker to ensure the victim is getting to the gate via the proper channels, a compromised website, and are not direct connects from researchers.

It's at this point that the exploit kit itself becomes involved. This starts with a request for the landing page. The landing page is typically where an initial vetting of the system occurs and some level of reconnaissance is done. This will include things like the operating systems being used, the type and version of web browser, and type and versions of applicable plugins, most notably Adobe Flash. This reconnaissance phase wasn't easily identifiable when initially looking at the landing page. As shown below, at the top of the document there appeared to be a base64-encoded blob that was assigned to a variable. However, there was a failed attempt at decoding, which led to the discovery of an extra effort by the attackers.

When we began analyzing the code on the page, we found why the decoding was failing: The actors used rot13 encoding first, as highlighted below.

Once we decoded the rot13 and then decoded the resulting base64, we found the code needed to probe the system to determine vulnerability.

This code will probe the operating system, web browser, and plugin information. As the try statement found below shows, after this is done a decision tree exists. If a vulnerable version of flash is found, the first path is taken which likely leads to CVE-2018-15982, which has been widely abused by exploit kits including Spelevo. If a match isn't found, the second path is followed, which delivers another exploit.

The specific infection path we are following did not go down the Flash path, and instead served the other exploit. We began to analyze the exploit, and after some investigation, determined that CVE-2018-8174 is being exploited — another use-after-free vulnerability in the VBScript engine of Internet Explorer. This particular exploit has been widely abused and can be found in several other exploit kits, most notably the Fallout Exploit Kit.
It's not surprising to find this exploit being added to multiple exploit kits, as most kits copy one another and once an exploit is available in one, the others typically are not far behind. This particular vulnerability still requires the use of Internet Explorer and relies on the user being behind on updates, since the patch for this particular bug has been available since May 2018.
Once the system has been compromised and the payload is delivered, Spelevo does something a bit novel for exploit kits: It redirects to Google, post compromise. The practical effect of which is that a user would see a tab open which loads the gate, followed by the landing page, an exploit page, and then finally to Google.

This could lead the user to miss the fact that they've been compromised and assume they were opening up a normal web page.
PAYLOAD
The payload that exploit kits deliver varies. In the instances that Talos observed banking trojans as the primary payload — specifically both IcedID and Dridex have been observed being delivered from Spelevo during this campaign. These types of payloads are common to exploit kits since this is a purely financially motivated attack and banking trojans are an attractive avenue for monetization.
FAMILIAR TECHNIQUES
Spelevo is a relatively new exploit kit that was first seen a couple of months ago. Since its discovery, it has gone through some minor changes, including modification of URL structure and some obfuscation changes in the landing and exploit pages themselves. It makes use of a lot of common techniques for exploit kits that we've seen over the years.
Unlike the Rig exploit kit, Spelevo is being hosted using domains instead of hard coded IP addresses. Additionally, they appear to be leveraging domain shadowing, a technique Talos discovered several years ago, leveraging compromised registrant accounts to host malicious activity using subdomains. Talos also found several instances of 302 cushioning where the gates and exploit kits will leverage a series of HTTP 302 redirects to eventually point to the landing page. The core functionality remains the same: Compromise anyone who interacts with it.
SPELEVO EXPLOIT KIT VIDEO
CONCLUSION
In much the same way that we see old threats like MyDoom and Stuxnet circulating on the internet today, exploit kits will be a permanent part of the threat landscape. They are still incredibly effective at leveraging existing vulnerabilities to randomly compromise victims on the internet to deliver a malicious payload. However, in today's world, systems that utilize Internet Explorer and have unpatched vulnerabilities are continuing to become harder and harder to find. As such, adversaries have many other attractive routes to try and get malicious software onto end systems. Increasingly, we see the Traffic Direction Systems (TDS) point to other monetization routes. These commonly include threats like tech support scams and fake Flash players. The common difference is both of those attacks require the user to interact to earn money off of the attack, rather than leveraging a vulnerability. Regardless, the majority of the traffic redirection we see lands in these two buckets, leaving exploit kits as the odd man out.
We expect this trend to continue as the amount of systems vulnerable to these types of threats decreases daily. Talos recommends removing Internet Explorer as the default web browser on most machines, especially for users who may not be as tech-savvy as a security researcher. Additionally, in today's internet, there is little need to have a plugin like Adobe Flash installed. Soon, it will even be deprecated completely. Taking small steps like these will help protect that increasingly small amount of users that are still being terrorized by this small yet extremely effective attack platform that still lurks on the internet today.
COVERAGE
To detect this new exploit kit, Cisco Talos released SNORTⓇ rules 50509 - 50511.
Additional ways our customers can detect and block this threat are listed below.

Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
INDICATORS OF COMPROMISE
Domains:
open[.]nylonsneak[.]top
hailey[.]nylonsneak[.]top
goddess[.]nylontruth[.]top
calientes[.]nylontruth[.]top
clasica[.]santarough[.]top
famili[.]clearnubile[.]top
colombia[.]clearnubile[.]top
swallowing[.]flavorideal[.]top
diary[.]motoribyron[.]top
bologna[.]vediocorset[.]top
54[.]armlessdance[.]top
perv[.]armlessdance[.]top
homosexual[.]armlessdance[.]top
clara[.]awesomeablam[.]top
different[.]beestkilroys[.]top
race[.]belarusapple[.]top
charmane[.]belarusapple[.]top
katsumi[.]carmanexteme[.]top
bww[.]cosbyfunnies[.]top
arnold[.]cosbyfunnies[.]top
vodeos[.]galeriebeths[.]top
veronica[.]galeriebeths[.]top
lithuania[.]galeriebeths[.]top
get[.]guerradanger[.]top
name[.]preitymutter[.]top
the[.]sandeerugrat[.]top
marge[.]sandeerugrat[.]top
emule[.]unicornbrune[.]top
candye[.]brunetbebitas[.]top
adora[.]dailysexpress[.]top
famose[.]dailysexpress[.]top
trailery[.]dailysexpress[.]top
mulatas[.]damitahustler[.]top
chaild[.]denizprivatne[.]top
combustion[.]denizprivatne[.]top
talent[.]denudaskalani[.]top
abu[.]fightingsatan[.]top
anziane[.]fightingsatan[.]top
world[.]italyalemanes[.]top
converted[.]minorikeibler[.]top
beastyality[.]minorikeibler[.]top
gore[.]natachafetish[.]top
binary[.]playingactive[.]top
tes[.]satanicenanos[.]top
window[.]aphroditedrink[.]top
breitny[.]barbiereallity[.]top
dyre[.]bloggerlolicon[.]top
filmmaking[.]bloggerlolicon[.]top
asturias[.]freakylanguage[.]top
delco[.]graffitoandnot[.]top
tanto[.]ingyenesrusian[.]top
punker[.]militarymagyar[.]top
break[.]periodherstory[.]top
chantelle[.]periodherstory[.]top
tes[.]teannapostales[.]top
absolutely[.]caballerosricky[.]top
pete[.]clothedcalcutta[.]top
foley[.]clothedcalcutta[.]top
natural[.]fantasygisselle[.]top
copii[.]gratuitekrystal[.]top
bailey[.]gratuitekrystal[.]top
dating[.]leilanihardcord[.]top
powerpuff[.]mancicdreadlock[.]top
adina[.]teasingfreehome[.]top
animay[.]tranniefotologs[.]top
qwerty[.]virusemoticonos[.]top
erotic[.]bridgettepromise[.]top
socal[.]carmellanightelf[.]top
ameuter[.]carmellanightelf[.]top
high[.]cartoonseverinin[.]top
sample[.]cartoonseverinin[.]top
groups[.]chabertcigarette[.]top
book[.]emblemliterotica[.]top
diary[.]ghanaiansorority[.]top
taylors[.]ghanaiansorority[.]top
spit[.]natashayoungster[.]top
IPs:
95.211.5[.]242