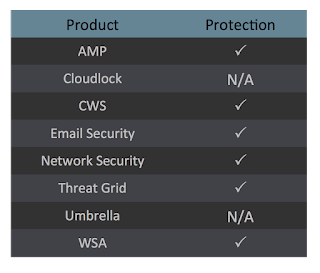
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 31 and June 07. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
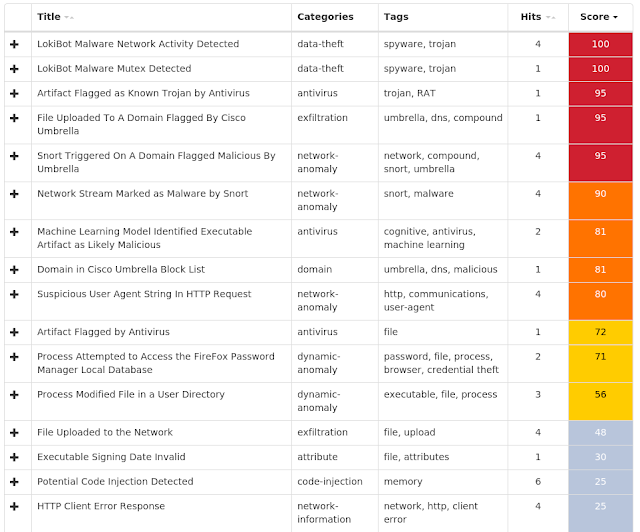
The most prevalent threats highlighted in this roundup are:
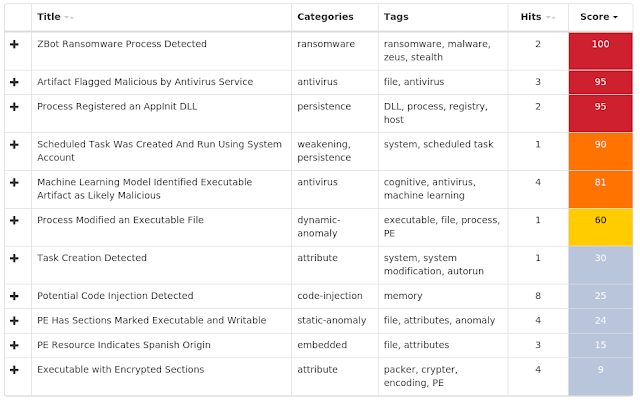
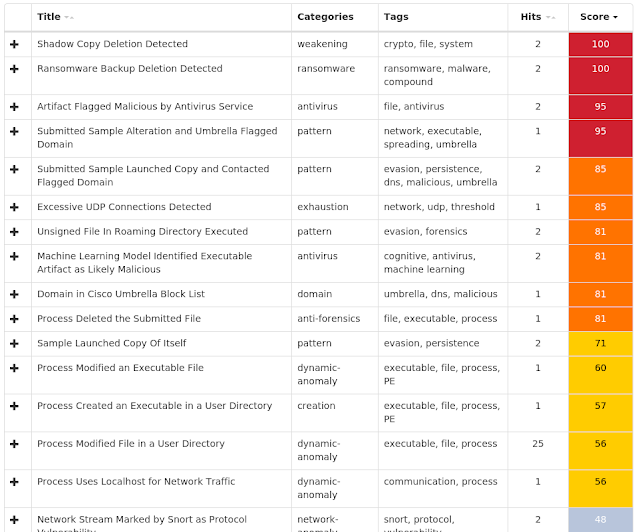
Win.Malware.Cerber-6984447-1 Win.Malware.Ircbot-6984710-0 Win.Malware.Kovter-6985541-0 Win.Malware.Lokibot-6987581-1 Win.Malware.Remcos-6985941-1 Win.Malware.Tofsee-6988429-1 Win.Packed.Zbot-6986485-1 Win.Ransomware.Sage-6987538-1 Win.Worm.Vobfus-6986418-0 Threats Win.Malware.Cerber-6984447-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
21
<HKLM>\BCD00000000\OBJECTS\{926583E4-EF64-11E4-BEED-D6738078AD98}\ELEMENTS\16000009
19
<HKLM>\BCD00000000\OBJECTS\{926583E4-EF64-11E4-BEED-D6738078AD98}\ELEMENTS\16000009
Value Name: Element
19
<HKCU>\Printers\Defaults\{21A3D5EE-E123-244A-98A1-8E36C26EFF6D}
19
<HKCU>\PRINTERS\Defaults
19
<HKLM>\BCD00000000\OBJECTS\{926583E4-EF64-11E4-BEED-D6738078AD98}\ELEMENTS\250000e0
19
<HKLM>\BCD00000000\OBJECTS\{926583E4-EF64-11E4-BEED-D6738078AD98}\ELEMENTS\250000E0
Value Name: Element
19
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: Run
19
<HKCU>\SOFTWARE\MICROSOFT\COMMAND PROCESSOR
Value Name: AutoRun
19
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: SCRNSAVE.EXE
19
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MuiUnattend
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: MuiUnattend
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: takeown
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: EhStorAuthn
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: EhStorAuthn
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntoskrnl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: ntoskrnl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: UserAccountControlSettings
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: UserAccountControlSettings
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: pcaui
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: pcaui
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: w32tm
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: w32tm
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: eventvwr
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: eventvwr
1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
19
\BaseNamedObjects\shell.{5B5347A7-9806-3802-3FD9-E106D6283088}
2
\BaseNamedObjects\shell.{2DA495A3-711D-597E-268E-77F8D29EB324}
1
\BaseNamedObjects\shell.{A90EDFAB-A502-430E-BDBC-2A277AABA37D}
1
\BaseNamedObjects\shell.{5B932A48-D5E6-DC9D-1CCC-8C4A4EFDFAEB}
1
\BaseNamedObjects\shell.{641070EF-FED1-8B40-20B1-757459DEA0E7}
1
\BaseNamedObjects\shell.{85890FA8-4651-7F6B-96B4-C1A19F5B4623}
1
\BaseNamedObjects\shell.{1095E0BC-41F3-CF2A-1232-3CB5F90C4677}
1
\BaseNamedObjects\shell.{F1DB17FA-39DB-DA6E-6E05-AC596D3CADD5}
1
\BaseNamedObjects\shell.{298948D1-70B9-FF20-23B0-FFCF5A6170CF}
1
\BaseNamedObjects\shell.{6B756908-BAD6-5676-BEB4-1AF11E0335F1}
1
\BaseNamedObjects\shell.{31C26804-8082-BCD2-AE9A-2E0E343C4A11}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]93[.]0[.]38
19
85[.]93[.]0[.]39
19
85[.]93[.]0[.]36
19
85[.]93[.]0[.]37
19
85[.]93[.]0[.]34
19
85[.]93[.]7[.]234
19
85[.]93[.]0[.]32
19
85[.]93[.]0[.]33
19
85[.]93[.]6[.]24
19
85[.]93[.]6[.]25
19
85[.]93[.]5[.]10
19
85[.]93[.]5[.]11
19
85[.]93[.]6[.]244
19
85[.]93[.]6[.]16
19
85[.]93[.]6[.]17
19
85[.]93[.]6[.]18
19
85[.]93[.]6[.]19
19
85[.]93[.]6[.]20
19
85[.]93[.]6[.]21
19
85[.]93[.]6[.]22
19
85[.]93[.]6[.]23
19
85[.]93[.]6[.]169
19
85[.]93[.]5[.]72
19
85[.]93[.]3[.]20
19
85[.]93[.]2[.]71
19
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ipinfo[.]io
19
Files and or directories created Occurrences %HOMEPATH%\NTUSER.DAT
19
%HOMEPATH%\ntuser.dat.LOG1
19
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}
19
%System32%\Tasks\MuiUnattend
2
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\MuiUnattend.lnk
2
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\MuiUnattend.exe
2
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\UserAccountControlSettings.exe
1
%System32%\Tasks\UserAccountControlSettings
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\pcaui.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\pcaui.exe
1
%System32%\Tasks\pcaui
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\w32tm.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\w32tm.exe
1
%System32%\Tasks\w32tm
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\eventvwr.lnk
1
%System32%\Tasks\eventvwr
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\wuapp.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\wuapp.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\bitsadmin.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\bitsadmin.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\certreq.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\certreq.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\mtstocom.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\mtstocom.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\autochk.lnk
1
See JSON for more IOCs
File Hashes
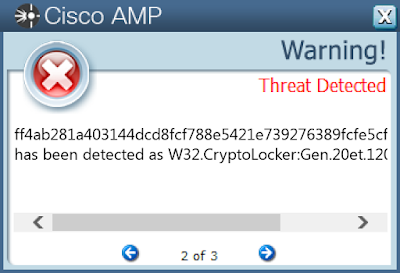
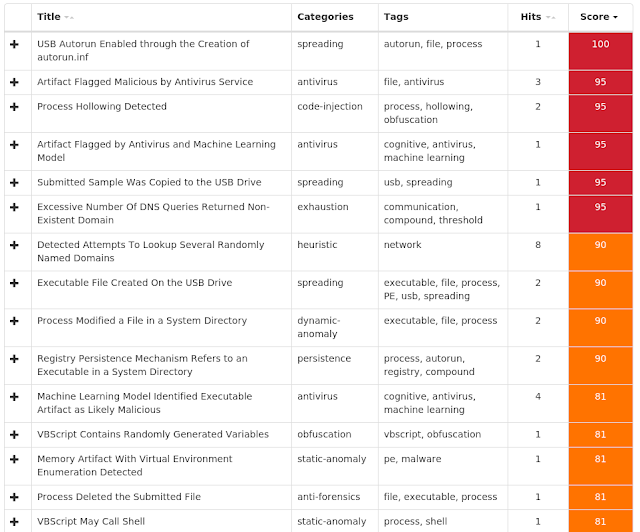
12c882e47ae5e2ef9e3621b1d8a719458041ce6f1ed38b370c45c821a5e8c59b12ec0e3ccef67f877fefce823785ac7d7dbb0f85f8ad001bdf7fc6bfe46e398118ca84623943190fa4ac1f756742b2ae30666d74acc7deee679b3a91bbd75e6f20b9ff24148baa96dbe1a0a7a48bbbeada81598988ee10605ebb21b139359e0924e2f47a00dba0b61b7ef2994f56318cc775c6fab40ad232598cebf0410b3da830731c843ed73bf36620d943ddce0a0237d8694b7afb212541e2e91416096b2b33b70cc445e8fa02e56ea688be53f7c2993826388539adf7bf48fef3c45995a7341e0f811782bc5c95e195f6f4d88de2aece469919de8c2c7b61794f99f40d824c3c95c99f5d583e2bbf8fb237e55aee3595dcdf24096dc0336190a067487e154f5e962ece139e2478863ad05e2d92ed0f8d37c98616faa2338adb84efe997445b54c5a4b56149231c5b2c0b9f0f40e226a4a198c9081068d245320f502fb4396179ede1ad0a80f932189cf1035fe8fe2329b4bde4ccdfcc1d3cbec15179d2b7692772293eb858cc1aa0bc9844448d3330a057992453e6a75e0a20e528ee4c6b734e3caad97e6edc7e62687d5a8a4628348ee24726938204779f3f5eb7a0f40080616c2ddd1a8c4e8be8c6053a905c9687e1f83336cc5661dca04c5ffb056afe825848fa43ac2ea280104225d930c7c85f33700c51528113295e75c8dc160aec9721c8e97b3ba15a00de9ab4dbcc0d3236253b5bb73f2b3e9d4f57c7ed3dd922c381125d95a755659683f75fbf32b57546d7ef099e266ca1c00a305a1938736fd9cf96f1f2dd702e618982028129009100e88e30c325775f98e77df4bf907af1dc7f0f8206c6b155e04cca65f269b7f2a2238297e9782c4605ecd5cf5eb5d8a7f378761bf7237c3355845ae18cc335b384e4ea7ba5f8ec1deea3fc59e3880050fa754655007b7b726ede666f2838940ea89d3349dd9c1278a8c998e2eecda3e3ff4ab281a403144dcd8fcf788e5421e739276389fcfe5cf31c708257d0474799 Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Ircbot-6984710-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
43
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Manager
43
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Manager
43
Mutexes Occurrences b2
43
\BaseNamedObjects\b2
3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 220[.]181[.]87[.]80
43
64[.]70[.]19[.]203
43
216[.]160[.]207[.]10
43
35[.]231[.]151[.]7
26
35[.]229[.]93[.]46
17
69[.]49[.]96[.]16
2
216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ageihehaioeoaiegj[.]su
43
aefobfboabobfaoua[.]ru
43
oeihefoeaboeubfuo[.]su
43
eghoabeogbuaeofua[.]su
43
abvainvienvaiebai[.]ru
43
eghoabeogbuaeofua[.]ru
43
iapghahpnpnapcipa[.]ru
43
oeihefoeaboeubfuo[.]ws
43
goiaegodbuebieibg[.]ru
43
iapghahpnpnapcipa[.]ws
43
ageihehaioeoaiegj[.]ru
43
siiifibiiegiiciib[.]su
43
oeihefoeaboeubfuo[.]ru
43
aefobfboabobfaoua[.]su
43
abvainvienvaiebai[.]su
43
rohgoruhgsorhugih[.]ru
43
rohgoruhgsorhugih[.]su
43
siiifibiiegiiciib[.]ru
43
oeabocbeogoaehgoi[.]ru
43
rohgoruhgsorhugih[.]ws
43
oeabocbeogoaehgoi[.]su
43
iapghahpnpnapcipa[.]su
43
goiaegodbuebieibg[.]su
43
murphysisters[.]org[.]murphysisters[.]org
2
www[.]murphysisters[.]org
2
Files and or directories created Occurrences \??\E:\autorun.inf
43
\autorun.inf
43
\??\E:\_
43
\.lnk
43
\??\E:\DeviceConfigManager.vbs
43
\??\E:\_\DeviceConfigManager.exe
43
\DeviceConfigManager.vbs
43
\_\DeviceConfigManager.exe
43
\??\E:\DeviceConfigManager.bat
43
\DeviceConfigManager.bat
43
%SystemRoot%\M-5050720597279729037972350920
43
%SystemRoot%\M-5050720597279729037972350920\winmgr.exe
43
\??\E:\.lnk
41
%TEMP%\phqghumeay
30
%TEMP%\edakubnfgu
29
%TEMP%\rgjqmvnkyr
26
%TEMP%\gwhroqkhwu
25
%TEMP%\tubjrnmzyu.bat
2
%TEMP%\eakjohgdtz.bat
1
%TEMP%\roomnvjngg.bat
1
%TEMP%\ynyfoqgvhz.bat
1
%TEMP%\sypfjdusmt.bat
1
%TEMP%\inwumejvuz.bat
1
%TEMP%\euywrsbhrm.bat
1
%TEMP%\jorljhwyxb.bat
1
See JSON for more IOCs
File Hashes
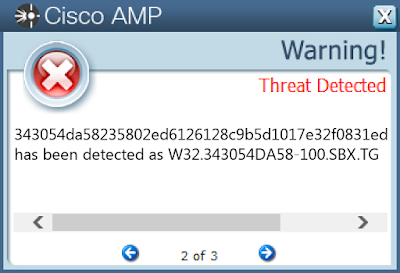
02fb71eb8559f95fd9d1bc2a31b119306c15a0921ab79101bc35e5ee1729e8730373f392e0cf0ec8a14fdf48a157cbbca1554960b0475724f45a80aae88932f30851ddc919f0ea470c3c23e296b6a76b378678364d63a119f6ebab2779e75c000b30c46cb7774dfa26d40809d4a665ba733364f3e9768314f5ac258c1ca2b2130e455cc4d487203ed86f96707ddcf09546c523b14238b003959d29db80db022a1538cc3c6f059ee7b734150f5e8eab97739c226119edd8b07c543ac77fc68ca515647f00761bb8ff63128c4af1e1277e69b4f51c627779259833c6e2d474aea0168070acbb2cb5200981e8d0dbed8255bb389feef078162f1ba140dc3ea3355316eae34bfa90161d7948d421636687c4b2e7cd4bf66d33dc27da05370f1f1cdd1b0cff388754655704d76af041b56978edd261dd7c2bb8a64a7a79a808312e001db1f2b0cf7c31206624f21c76587f97e41797d4b034e60577167c751a41c9d71f9c1401a3d5279386e59811bd6a916fd555d0ce2701f955110cf548219f64f81ffc4c395bbb6a3a25b17845a5bf7d897e7c9455c29a7d930607dddb1539f72e22e62621d215f605a6ad76325c08c8ade8a78a55411fad1e4081e0406069404d2a9836c84b839afa60b4fec08b0285404b065a596458237bdbadd9937b637ae22d2d8936c9f938e60799545e538bc2397f1c2db0d5bf6a8e8afbb7cd561a81f52d32b4679e6550adb81a453813e8a820f9d61133d946a32035a4ec3ab566e4212d5beaf3e2779270c8b6c3c9d288a64f53e4065104d6806438178f1283ed1c212da6a2799761b83b1206e7dab4d590dfb689af837cf3ac66fa3e58bb8484ee21343054da58235802ed6126128c9b5d1017e32f0831ed5bc09748c0c3707d54333451ccb4bdf160e6150d3f1f4ed55dc943544780edcef3098283e41502c8b4ab368ff13ab0807019f61b3ab0ee083c2ab701151582fd59e3b055be3f4e2c63ed36dc719c3e47172a121189c734406055df92e986d1e202769a2432191f028bf1386fdf3836ad5b3bf1588e6b40700abdc69eb793cfe7c6f36895da751944d2bb3a6e2efe8331037681da5ee01f8deb8aa7cd9960b21f5975aef7d876f7e82b86See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Kovter-6985541-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
Value Name: DisableOSUpgrade
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
Value Name: ReservationsAllowed
25
<HKLM>\SOFTWARE\WOW6432NODE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
25
<HKCU>\SOFTWARE\fc6a75be78
25
<HKLM>\SOFTWARE\WOW6432NODE\fc6a75be78
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUpgrade
25
<HKLM>\SOFTWARE\WOW6432NODE\FC6A75BE78
Value Name: 0521341d
25
<HKCU>\SOFTWARE\FC6A75BE78
Value Name: 0521341d
25
<HKLM>\SOFTWARE\WOW6432NODE\FC6A75BE78
Value Name: b5e001e3
25
<HKCU>\SOFTWARE\FC6A75BE78
Value Name: b5e001e3
25
<HKLM>\SOFTWARE\WOW6432NODE\FC6A75BE78
Value Name: bca7705c
25
<HKCU>\SOFTWARE\FC6A75BE78
Value Name: bca7705c
25
<HKLM>\SOFTWARE\WOW6432NODE\FC6A75BE78
Value Name: 0905afc0
23
<HKCU>\SOFTWARE\FC6A75BE78
Value Name: 0905afc0
23
<HKLM>\SOFTWARE\WOW6432NODE\E75950E48E5A494D2B
1
<HKLM>\SOFTWARE\WOW6432NODE\0oCEoq
1
<HKLM>\SOFTWARE\WOW6432NODE\98LFDHTIH
Value Name: FeWPlOewHO
1
<HKLM>\SOFTWARE\WOW6432NODE\E75950E48E5A494D2B
Value Name: 7CAC0591BC7764C7382
1
<HKLM>\SOFTWARE\WOW6432NODE\98LFDHTIH
Value Name: p6gawa3
1
<HKCR>\RATHF\SHELL\OPEN\COMMAND
1
<HKCR>\.XJJWQ8S
1
<HKLM>\SOFTWARE\WOW6432NODE\0OCEOQ
Value Name: YcaGv7s
1
<HKLM>\SOFTWARE\WOW6432NODE\0OCEOQ
Value Name: gG1npQtvrW
1
<HKLM>\SOFTWARE\WOW6432NODE\5C8B173AEDDAD6407C3D
1
Mutexes Occurrences C59C87A31F74FB56
25
Global\42EDC1955FE17AD4
25
0D0D9BEBF5D08E7A
25
1315B41013857E19
25
\BaseNamedObjects\BAD24FA07A7F6DD9
24
\BaseNamedObjects\863D9F083B3F4EDA
24
\BaseNamedObjects\Global\EE662FBC96CBCB1A
24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 99[.]19[.]28[.]150
1
33[.]162[.]102[.]125
1
152[.]71[.]205[.]88
1
25[.]4[.]98[.]57
1
180[.]222[.]21[.]248
1
125[.]197[.]146[.]126
1
1[.]75[.]211[.]46
1
164[.]202[.]251[.]11
1
149[.]126[.]117[.]212
1
6[.]104[.]211[.]114
1
169[.]78[.]132[.]23
1
46[.]130[.]20[.]79
1
187[.]185[.]88[.]9
1
217[.]134[.]228[.]74
1
156[.]244[.]226[.]39
1
70[.]181[.]27[.]114
1
142[.]72[.]113[.]250
1
187[.]78[.]253[.]202
1
46[.]171[.]247[.]91
1
146[.]148[.]18[.]137
1
51[.]145[.]9[.]51
1
190[.]43[.]97[.]88
1
152[.]195[.]236[.]164
1
191[.]169[.]221[.]13
1
213[.]55[.]97[.]176
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cpanel[.]com
1
etp[.]adilet[.]gov[.]kz
1
Files and or directories created Occurrences %LOCALAPPDATA%\epobuj
1
%LOCALAPPDATA%\epobuj\0qIkSdDC.V0Eq5OI
1
%LOCALAPPDATA%\lyza
1
%LOCALAPPDATA%\lyza\CdxtVr.frbnvz
1
%LOCALAPPDATA%\zamem
1
%LOCALAPPDATA%\zamem\tOLe1R7o.SeYQX
1
%LOCALAPPDATA%\jyde
1
%LOCALAPPDATA%\jyde\OAws9tY.gXnWQL7wx
1
%LOCALAPPDATA%\umove
1
%LOCALAPPDATA%\umove\tX0S.dyCX7y
1
%LOCALAPPDATA%\ojoc
1
%LOCALAPPDATA%\ojoc\zurK74.xJjWq8s
1
%LOCALAPPDATA%\pyrul
1
%LOCALAPPDATA%\pyrul\Mo3j.DWTa0cV
1
%LOCALAPPDATA%\bebet
1
%LOCALAPPDATA%\bebet\iIKL9U.DGsvEB
1
File Hashes
00bd28d59cb4b7018516410c9664eec2eefe7adba447a37edb587d4829eb760d037385b8865ee894bf36cdce3b370265b7da03447b3b4e18dd72d114330e9942039c52e2bd728ba1ac902a0f4af7363d28aced0ba6f5622fbd0e118d959f59b2065d2473aa32a471228eba99fd58773ee61a634e4f2466b69f6f9c2c94ae56d308e337c9f049aa7529aa727fcb8898d1eb2bf14d4b656af95d740e07d7ef9b670adc56352600d4dd0a413986ffa45cbeaf04b973abdbd86c9b0c87a53440e29410f8c098454c63c90a986d037d571d055f5174a00e1f380931157a84ecdc2c0118b1f735465a3b6fba65570dbe125f10b8489587410a872973216ec853cb125b1e663349f267cef450ab939b3904bdd33e0809f9080235241929e09fb7b770ae270d791b5a9c8f7723563afffcb54932ee840920c7b68bed13d8c7aa689190ff2ca4a4be4d6975d74bb50303fa61c453ae539c6982f88ac38553b7a7ca5128133057b5a29b5ef78d36bce0c6c31ec2300f8c0ffdd67fc9f5efd7e3b1f00aa04a334afefc5c14d97cd3af6ab570691d73c23b2c257fd988502a08fec02fc6f7b733a640afd9288415aff6de8ef74b85c1879784be2b73dd0900ab00d06dd519c03680469ac286cfb7a9ef01f31b5703cfdb965550dba9170d0d60a93ab316cb9a36d13de18cddc5dcfb7bb8bb9e946c6c77a26be5e7098c1303e70db9f24511fd39af3ab5ef14b0dd3adc7b2bffa4a344bf19caf9b3d9e9d4c78afab321466f8d39c7f1118753de1bed52953ab491652c807970d42eff5f5366c3936a297f92203b7be616a488f39465e822097aedc82aec3b05e730bcd22e1d5d57e64227439e3e653e5fbeda3f17ea2e35f2456769710d3210940f157fe25a18026943cef6433ed50e60a4117ffb607a4843f95df60f6cacbc29498f05371073ae06a562dfc33fea545cce296bbbeb27176f2ce630493d3b680f789effa6d9dc26478d5f00cb449d58bad679912feee287ed8e17ce6221bc61432707e9f189490119bcb9a76d5263e898133a652e1e0ff1c94919d31c4c3da2bb1bf2fdbf876ba1dd18a0150256b0d6771543530d8a49ff3e8581f0a81330500ca9e6794a15f6876a394285f7See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Lokibot-6987581-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
2
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASAPI32
2
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASMANCS
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableFileTracing
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableConsoleTracing
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileTracingMask
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: ConsoleTracingMask
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: MaxFileSize
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileDirectory
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: EnableFileTracing
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: EnableConsoleTracing
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: FileTracingMask
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: ConsoleTracingMask
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: MaxFileSize
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: FileDirectory
2
<HKCU>\SOFTWARE\Microsoft\Protected Storage System Provider\S-1-5-21-2580483871-590521980-3826313501-500
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: internat.exe
1
<HKCU>\Software\Microsoft\Windows Script Host\Settings
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: deaqsdegdd
1
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\U6T0UXHWPB
1
Mutexes Occurrences 3749282D282E1E80C56CAE5A
19
-
1
eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-21-2580483871-590521980-3826313501-500
1
d19ab989-a35f-4710-83df-7b2db7efe7c5{846ee340-7039-11de-9d20-806e6f6e6963}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 87[.]251[.]88[.]30
5
87[.]251[.]88[.]27
4
93[.]158[.]134[.]38
2
47[.]254[.]177[.]155
2
87[.]251[.]88[.]28
2
87[.]251[.]88[.]19
2
69[.]195[.]146[.]130
1
104[.]16[.]154[.]36
1
104[.]16[.]155[.]36
1
192[.]185[.]129[.]109
1
185[.]29[.]9[.]246
1
5[.]253[.]62[.]214
1
149[.]129[.]242[.]147
1
104[.]31[.]83[.]247
1
37[.]120[.]146[.]124
1
37[.]120[.]146[.]122
1
84[.]234[.]96[.]91
1
145[.]239[.]202[.]109
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences doosantax[.]com
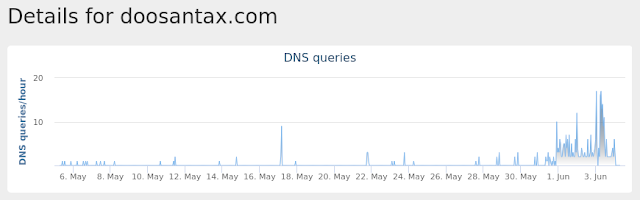
4
bridgecornenterprises[.]com
3
smtp[.]yandex[.]com
2
whatismyipaddress[.]com
2
unimasa[.]icu
2
ip-api[.]com
1
OK
1
sas-agri[.]ml
1
SIBARZZ[.]XYZ
1
plutonav[.]ru
1
bestbtcchange[.]com
1
officialhillcoms[.]ga
1
beatfile01[.]ml
1
freecaps3[.]ml
1
flmates[.]com
1
www[.]dlamaqperu[.]com
1
lronman4x4[.]com
1
apollocapitalp[.]com
1
Files and or directories created Occurrences %ProgramData%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
23
%LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
23
%APPDATA%\D282E1
19
%APPDATA%\D282E1\1E80C5.lck
19
%APPDATA%\pid.txt
2
%APPDATA%\pidloc.txt
2
%TEMP%\holdermail.txt
2
%TEMP%\holderwb.txt
2
%ProgramData%\freebl3.dll
1
%ProgramData%\mozglue.dll
1
%ProgramData%\msvcp140.dll
1
%ProgramData%\nss3.dll
1
%ProgramData%\softokn3.dll
1
%ProgramData%\vcruntime140.dll
1
%TEMP%\deaqsdegdd\deaqsdegdd.exe
1
%TEMP%\deaqsdegdd\deaqsdegdd.vbs
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Soft\Authy
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\ElectronCash
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\Electrum
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\ElectrumLTC
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\Ethereum
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\Exodus
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\JAXX
1
%ProgramData%\4O1XVHRT01HDEJRSE1PVNWXU7\files\Wallets\MultiDoge
1
See JSON for more IOCs
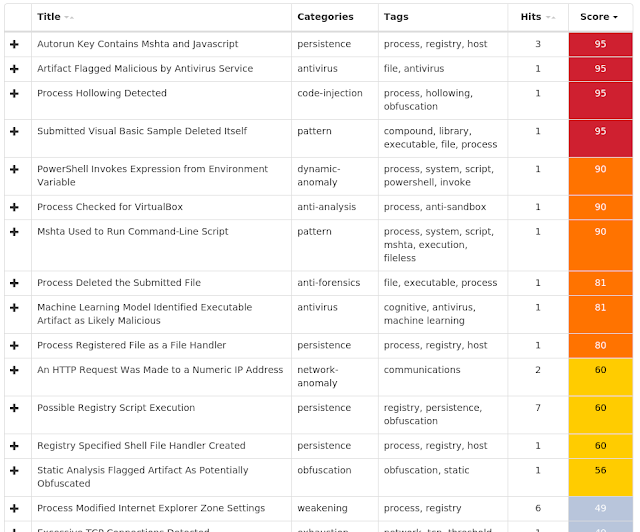
File Hashes
21ea64cf87a724414eaaa6cc7a69a38cebef6b5507084f036b486adb3f80541725fa58e7d7821ca2c5cdb947422289eae7d3909efc9455a7a5ef4e476947f4ce30120ab8f904030dcd4748b4b5edc38f9437ee18d582ffd86c63882ef0afc1e533527e13eaf4f1ad749a5d00e5f2f8c06e55503a492cdd3a2a01bebc79360aa339bd8e2feb6ff6b4b8d25f5e8f9e2e413d7df9241c9effde6cf5c074b0360964425b00366b5e0bbcbecaa17a6f3767ce182d10cb54d14b8146d60795e0a91b4a45332fc059e1f72e4c9c27bd61e33b9af765299f3685bc1e33e31dae5206311b46773272beedf1cbcd61b41e399df8c437d8c915e3f942115eaa48c5a44af0254e59cb8c79d9dd7964e5319be30a91b8dee1744054e6e7c470717dab91c95905527eee4d3d2df6305545a95c33e17524a22464ba921f5091489bc776287e9082618c7974abfa637082c14b741cab9c859f0ea5ef9cb7517824d5c956886b99596f86b9a80e340cae7b6ce7c70b06f7237c54019c37faa9dd888b57fe15568d6c72394394c1b0b5d02fe6e362fd07940a6d69551fa7fcacef03c0d82f41fc8fbc83ad9a9b79964ccec70ccf12c7e01c0ea6ea0dcf391dd2ac014d2381e1ba42f190836122fddbc258f491d097e53e155258999cee41fe1550c78354aa3c8f2e0498a3e55133d7a23d343f2d690650e5579e485500447f0fff3e0e23f29c9fa86f9ad80c24445040b882abd94406f5bd389ab83b400ac4177687e653277788d7f3a493e9a4662dabc9083cde701821e1df98e499dd9404f49dbedbe3f55fedd764c6605ed53413e717e788b8f551455a1f9e94a313ebd00613fac0c63f7bfb920fcce98d91043e66d5b85e536b8864e604d2b26566a8d875dda21e93f51efc6f71dc9c4bb8db7e3b0d26dab3572df9ab97cd0218c14a17621104c2a6c095a61f40dd33d5c467751e8f531bd557cc74f91619d43e3c8ebd1a516c339f33d3be9ac3e25beccc8caa3518794a0ba5edbdc99916a66cee94fd55e25d9d34a23420bbe0 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
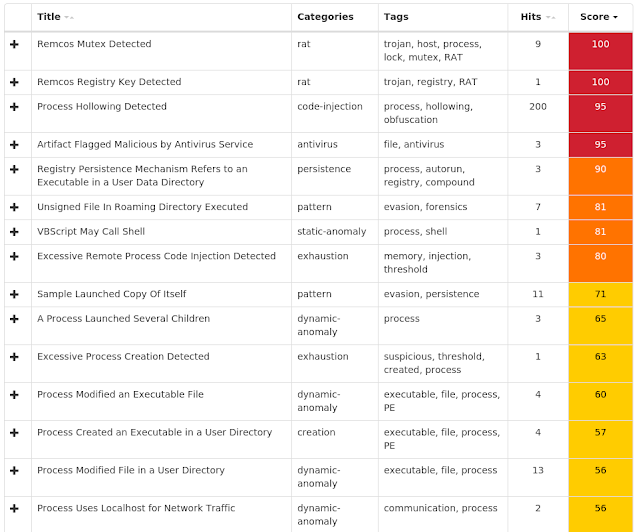
Win.Malware.Remcos-6985941-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\remcos_jpetmoenqu
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: srvs
21
<HKCU>\SOFTWARE\REMCOS_JPETMOENQU
Value Name: EXEpath
18
Mutexes Occurrences \BaseNamedObjects\remcos_jpetmoenqu
25
Remcos_Mutex_Inj
21
remcos_jpetmoenqu
21
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 213[.]208[.]129[.]213
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %TEMP%\install.bat
25
%HOMEPATH%\MdRes
25
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\RmClient.url
25
%APPDATA%\WindowsApp\logs.dat
25
%APPDATA%\WindowsApp\srvs.exe
25
%HOMEPATH%\MdRes\RmClient.vbs
25
%HOMEPATH%\MdRes\klist.exe
25
%HOMEPATH%\Start Menu\Programs\Startup\RmClient.url
25
%APPDATA%\WindowsApp
21
File Hashes
2d0c8f189df656a4eb6e0352bd32fb21c3afbce9ea7c345550386ce0127c320a30f9c76cd44a579c337269351ab40daf575e5996769cf23ab9a004766359380933baecfca9dcc0ad6c662a1df86a3ee2e97a9c042e6951145a1139674ee040ad430d466c1c81f8b680b5e8d57eb696a1c09efc0727009ee3412698bdbd77cede4ee4c01b513f59cef746c45b14b8211597937dfba27fb58b5e003fe97b7c87ce516aee696300bb4b56085134b659caa5800a89badc46fc6611864ff5e79ca872561a586d20b38ac2bac223d970186c02bacfdca09c96fe7d41125483b0a583d06319c58313ab6b8172994320d5ae1c16dc3e0cd1462d10eddc1244dc2573b98768df7e2ac8625213080dad97fb015f78d0a7cbcf560e1d118879a7c949cf2eb47f3e2f8ba14f4f08655e53d1e4daf2fd581e58a444c8c66c57292e28fdde1afc876ba61de5a3feb2e34181bc9a6e1197e70215b51cc169126c2d0bf0bb7588d48eca101db0d90f835dce7436a4e36f786694950a27eef3bfcbc458a347118f3f9d3547fe7517b3a9cd60eb408e9233273433bcd1bf86093ee7040f8162e54b9aa280c5a73c7388441c7b06d600fd0237cce304d02b93a80a88dff73e1e1fbcc8abd1175388917b260096ca11cc3a8c3e56425abd0dc04650f528ad1669214923b67255713feb497e145187f505da1cb42becbc0684f2b23efb1bbeff2f2f7431b95ea3839a21dfeac94eb4f21efd35d2f1652a7e4c7f65b08bdc846685a7de44c5f806ef8bdaec76e4b022eac1386fd7954522542e7ce21afbc7f7e848d35e12cc5535a4f201268e7a60692d4b21f2da0478771f6fd3379b43f36dbd13d0a2d3d47300165d3868f3b9ad434e8256a950ba2d83a5b71a684000fda9bdbd673585e3fa269a38eea19a1d0e8fbdf9432347109a365378afe16a77fe5956e825ae53effec65407157ad26d5bea08a1def289630078e9c88e4fc70b1e11f83836476df601204c1446b69b8a5606eb6bfe4e8bded5287513a1beab99160d0495e79f4ff67262db3cd9ff311c83c274b4498a60147316ba82b8e91b16bd2292082c3ff5fa6030698b41b7d260a55312fd83746df4c79d3f86e4c565ae170414d79b1642See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Tofsee-6988429-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
17
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
17
<HKU>\.DEFAULT\Control Panel\Buses
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
17
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\dwkqpxds
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\dwkqpxds
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DWKQPXDS
Value Name: Description
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\rkyedlrg
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\rkyedlrg
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\RKYEDLRG
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\RKYEDLRG
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\RKYEDLRG
Value Name: ErrorControl
2
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
17
69[.]55[.]5[.]250
17
46[.]4[.]52[.]109
17
176[.]111[.]49[.]43
17
85[.]25[.]119[.]25
17
144[.]76[.]199[.]2
17
144[.]76[.]199[.]43
17
43[.]231[.]4[.]7
17
192[.]0[.]47[.]59
17
94[.]23[.]27[.]38
17
211[.]231[.]108[.]46
14
213[.]209[.]1[.]129
13
173[.]194[.]207[.]27
12
188[.]125[.]73[.]87
11
199[.]212[.]0[.]46
10
104[.]47[.]53[.]36
10
104[.]47[.]5[.]33
9
104[.]47[.]124[.]33
9
98[.]137[.]159[.]24
8
216[.]239[.]36[.]21
7
104[.]47[.]8[.]33
7
104[.]47[.]0[.]33
7
62[.]211[.]72[.]32
7
213[.]205[.]33[.]61
7
148[.]163[.]156[.]1
7
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
17
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
17
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
17
mta5[.]am0[.]yahoodns[.]net
17
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
17
whois[.]iana[.]org
17
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
17
whois[.]arin[.]net
17
eur[.]olc[.]protection[.]outlook[.]com
17
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
17
hotmail-com[.]olc[.]protection[.]outlook[.]com
17
microsoft-com[.]mail[.]protection[.]outlook[.]com
17
sweety2001[.]dating4you[.]cn
17
honeypus[.]rusladies[.]cn
17
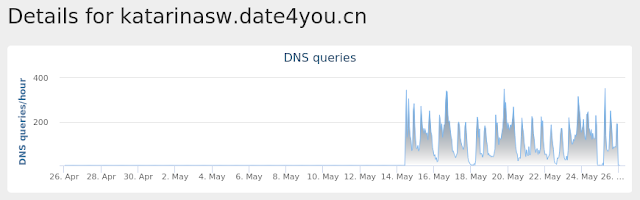
katarinasw[.]date4you[.]cn
17
marina99[.]ruladies[.]cn
17
mx-eu[.]mail[.]am0[.]yahoodns[.]net
16
tiscali[.]it
16
etb-1[.]mail[.]tiscali[.]it
16
hanmail[.]net
14
mx1[.]hanmail[.]net
14
ipinfo[.]io
13
smtp-in[.]libero[.]it
13
libero[.]it
13
tiscalinet[.]it
13
See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%
17
%SystemRoot%\SysWOW64\config\systemprofile:.repos
17
%SystemRoot%\SysWOW64\config\systemprofile
17
%SystemRoot%\SysWOW64\dwkqpxds
2
%SystemRoot%\SysWOW64\rkyedlrg
2
%SystemRoot%\SysWOW64\athnmuap
1
%SystemRoot%\SysWOW64\nguazhnc
1
%SystemRoot%\SysWOW64\wpdjiqwl
1
%SystemRoot%\SysWOW64\piwcbjpe
1
%SystemRoot%\SysWOW64\qjxdckqf
1
%TEMP%\euatucsb.exe
1
%TEMP%\bvxuokuz.exe
1
%TEMP%\baqmtpu.exe
1
%TEMP%\idkhgdza.exe
1
%TEMP%\irjirdhy.exe
1
%TEMP%\mgifzvfk.exe
1
%TEMP%\kmhypjqj.exe
1
%TEMP%\tryutcar.exe
1
%System32%\sflmyjon\mgifzvfk.exe (copy)
1
File Hashes
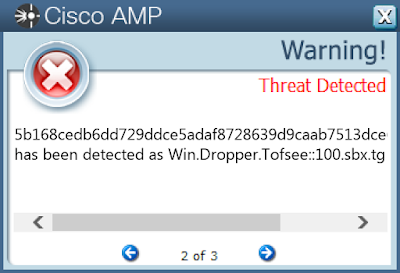
1d7dce1a75f19e02b554764e116205833fc300e13e407a1424aee1f7efcef4912896e3d9e7e10b9faa9254c44f78b7bc7005fa008090234eb5d92ddc55415f1233906a7062f316e0683753977c6018675877c19755d830bbca04e6c87cd7d7273b902891e76a3efe254aaa04071bee804576585be3324f1938001827e817f3a1478f07fdb1dcd3672ff5d290c70d5f372f5f5eb31ecdd7d9d5eba82cc316b7f2490867ad1a8bea080a54486696c32aeeb614900e2af12f2766789267b9c842925b168cedb6dd729ddce5adaf8728639d9caab7513dce660cfa85f77b2d3a2fb16bff144513b6bca96b1a1681870f114bcdffaaca0aa23e1f523ef01ee81b4a3fa448406f2e0e9583c0fe8f8366b55bb36e73ee3ef2d2258a13045be87488fecbb66ab4ace074418791a4aa3b22d467087b3f72106844724d50ad8429867b9f27bebc1ca1106ef7f9ab3773cb50dbfac77057d2ac485930ddde418734a30dcea6d65a714eacd52d80ae4d81f7c3f0439b1eed742a91d8e18e351306a8e9a7d56add949e91c747449bc0cf3271378e86160a4caba277441237f5854133b5b63e37e0a341fb6e766d58f954fc9801b8c9b2e3b76dea4987b051673c9c9fbfb1bd5bebd599453987fc52d3783dfcb4b7cd93bd7d1cad864da460ea4fabd4340ddd09f867deb777721ceec1e0da73c4f7599e20d041030e42bdc07e90b0ee58f171f5fb1da0632e8f438ef9b22e13ccf98fc6cda8cbc79276a179f4e00a18fbc24554 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Packed.Zbot-6986485-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: LoadAppInit_DLLs
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: AppInit_DLLs
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %ProgramData%\Mozilla\thfirxd.exe
25
%System32%\Tasks\aybbmte
25
%ProgramData%\Mozilla\lygbwac.dll
25
%HOMEPATH%\APPLIC~1\Mozilla\kvlcuie.dll
22
%HOMEPATH%\APPLIC~1\Mozilla\tfbkpde.exe
22
%SystemRoot%\Tasks\kylaxsk.job
22
File Hashes
75a96e041086cc1af7696888b0519dcfdba518234345f55746ef5a3c5b7db5547f0d74475cce26ef072c23f5788e56688d280645a5eed19537cdc66feed7d2237f22ccfdfb24939537763a2f265979c540ef674e0f29101f57d63573863a4ebc87aef6c3658a5e31c59df0dbd604d1309cff42b84cbe2761634e8e5f8add3cba8fc42bf42753de20f7f8a889146d5ac3f81b1498b8de4695ed759d930c55a81e9a3dab606f2bfa91bc7b4e1a6ddf2fde1a579daeea10d273c5d92ed5400ee72e9f47c7fb5108b7802a9721115563d8485389e29d08082e747e5317e4b85a93b9a8ccd6f1a376356ec6a54a0f233d495183d52bfbe0da041403c32717d5321853b16564e7e63b6761a2a307d0f03b5eb8725b7f688693df8d4cea881f09b2d959bbab6e4862965c729645b63b2dd3a73fde02cecb960a03169196ae409dcf424dbe492dd9101569320491e515e195d7679aa67e3d293ba551aa47724b5298a957c2a7bd7b3f15334856a1631683490dce70db66ea8aea2b82589cf16e6a566829cbaba36a158d6be04f18de282f77db026b1fcd82451a28e93aaaaedb363b9691d8d3e9b08507ce57c428b0dcfad69ef8c9e303d7c89a14a44dd0a2b0fd14583cda185a973d7add8f69eb42818c9783f0608f77e63036ec0014228ab9a2cefee9dc5d91b1c9767f8920b8803266e6c8443f6c416c3a45c0321ba7124d9dca0d4dde68595f96cae94bb027659485fe9dc90c92f1de376c2206ae351d397ffffcbbe6efee10de9b5ae15896cd35f87ca6e108823f00857e6c4c6cdc97aae0a0e8aae8818da0e728731d74779bb9c8328ba40cf2331703a250f4f1369aaa996b9f79ea45d1af873f9b6ba50a5c7e4e96bf7f62948ede9777391e1558530c02f3c3eceadf0dd3d9bb9c60c00328d43ae8b52657af58cce0794ecb31bff77b8a6eff8bed8653b1e049258b58ece93559603a0fdb998003c6ae3a0f9930bccf21bbcdf0edd63bc56a1a477e20d52a7931177a65e4ab7f78f4f807a8eed1f3785a7fe704ef7f834b58f201bc59b17a7a3e45e9cab4f0426a1c084506acb5be97c03fd376efd021314885ae49896a01c9244a4ca301cfe74e72a3ad6ca35afc8dcbbc01f0See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Ransomware.Sage-6987538-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Control\Session Manager
25
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
25
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\##PC#Users
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\##PC#USERS
Value Name: _CommentFromDesktopINI
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\##PC#USERS
Value Name: _LabelFromDesktopINI
25
Mutexes Occurrences wj6qbq4X
25
\BaseNamedObjects\PFShggN3
3
\BaseNamedObjects\adX9ZN6Z
3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 5[.]45[.]6[.]138
25
5[.]45[.]159[.]19
25
5[.]45[.]140[.]6
25
139[.]59[.]93[.]181
25
5[.]45[.]226[.]237
25
138[.]197[.]136[.]196
25
138[.]197[.]105[.]68
25
211[.]114[.]30[.]7
25
5[.]45[.]247[.]22
25
138[.]197[.]196[.]19
25
138[.]197[.]122[.]68
25
139[.]59[.]227[.]172
25
211[.]114[.]64[.]63
25
5[.]45[.]129[.]52
25
138[.]197[.]22[.]151
25
211[.]114[.]47[.]80
25
211[.]114[.]28[.]235
25
138[.]197[.]109[.]79
25
5[.]45[.]242[.]197
25
139[.]59[.]219[.]237
25
5[.]45[.]24[.]236
25
139[.]59[.]185[.]4
25
5[.]45[.]238[.]90
25
211[.]114[.]135[.]136
25
211[.]114[.]84[.]142
25
See JSON for more IOCs
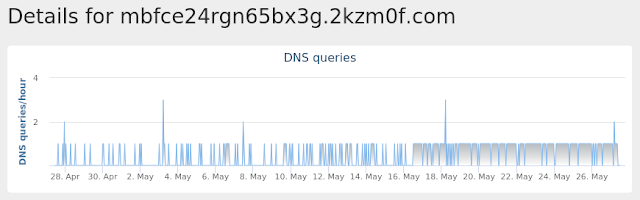
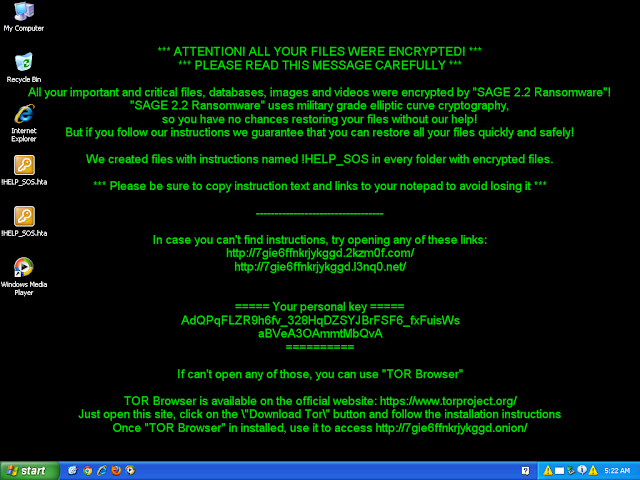
Domain Names contacted by malware. Does not indicate maliciousness Occurrences mbfce24rgn65bx3g[.]2kzm0f[.]com
25
mbfce24rgn65bx3g[.]l3nq0[.]net
25
Files and or directories created Occurrences %TEMP%\__config252888.bat
25
%APPDATA%\1SKJ4BcT.tmp
25
%APPDATA%\h7Ph24Fx.exe
25
%System32%\Tasks\NuqH5Wz3
25
%HOMEPATH%\Documents\!HELP_SOS.hta
20
%HOMEPATH%\Documents\Outlook Files\!HELP_SOS.hta
20
%TEMP%\__config16184093.bat
3
%APPDATA%\qh78RMdu.exe
3
%APPDATA%\vpiuxHWP.tmp
3
%HOMEPATH%\Start Menu\Programs\Startup\TLkOeWe7.lnk
3
File Hashes
1160b42660eafdbaa7e8eb963f3bb9ae17058c06248965265df0fe8b3d39fda0239d51f57e2cb6b6dd712deeef8d87a4a1f78b10269424edf028f79eccf70bec3599109b2d20e97baaec09e11e917058dc902158a377015c425a7371ff5840545d62a735a26a9c4494ad3abefd99287889264451798948b8e3dd2a83370312c35e9e35441ce1473fedd37ca2356cb4932d47f62a9125903383706dba1c3568966c4aa0ea8d6828c79bfc6e973ed1b03f88cf311dd7cd5b0ca2982221a29317d57aec11754a7a9c23b313376a188c4231e1d6f1e5110b689de56236d891f956d57f89228c94c44ab61cc5ba06ce6dad7524343a0c50dc394a39b0066a8378a34980e3c7ad157c9b87a49817973591df737a0d1399bdc9c0a0093acecb7d50d21a901ff9ae67350d0d294b9b666a7b1fc5612df5fa7e15acf78561716f5a6567f797c9f82d70fb957f74e31413b9ac00e56bdab268727f11189c781e7ac93b547998cc91e7d693e7b41f471f256ecf7f780847d37576696c94f005203a614be6169c7b75a7daae70019419abd51ce4c2bea8e383bd7e618b45d640b08a5f07b99ca24fef8d4b55e29dec0b57011e4aa605a39b0ce3d6f207d94ca6e83cd11edaa6a5d950f3e43db37527ed31959ffeecb5fb8e7b96d5caae1356577b16dccf183ba9ed29372780e5c7c43144308475457df9bc9767c5bdcc294a41eb4fb18a5ac1bc584c0d484c2f772bfdfe5afce3860f8de64fc3f7a147aa731c48e62b8f895fc039c4ba185062fd62b7033dbf3b323f15ee8ec385029c7e91560dab1e1b6a4bc771267b2194218e3e8c81795f9e13382415cefea5809260acc7f2a2a0ff8838ccf5439e4290e97bb501bf81b8e2c868fd602799dfaaf45254454bb796ffe8a5dc0eddac68e6ef891133b6992bdacf4993b49a1a23d3b279ce3092588cb8d1c1e4fe560783615e0fc7b410b7c951095749f15dbcb54dd05d1f20fc56da90cb70e6a535eaf2e4d37287a4dde09528a29095daa74f05378239b4786b3f90f42192ec49a254c5bc7d07d346d5821483cd10ad166b2b96ffd59aa9038bace5fc82e8fddf11ffb5c70acf8f0d0c4de1cc352948c263a8646ced62248fd689f4555756 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
Win.Worm.Vobfus-6986418-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: ShowSuperHidden
24
<HKLM>\SOFTWARE\WOW6432NODE\Policies
24
<HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\AU
24
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
24
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
Value Name: NoAutoUpdate
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: xyyiaf
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wdciac
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tioguh
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: xaone
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: goatia
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: muunai
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: woiotin
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: xanix
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: diozog
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: jkxab
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hakol
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: baualof
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: leaewi
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: yiiepi
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: dooreab
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: boebit
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: liuolum
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: yifeg
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: kuawea
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ns1[.]boxonline2[.]net
24
ns1[.]boxonline3[.]com
24
ns1[.]boxonline1[.]com
24
ns1[.]boxonline3[.]org
24
ns1[.]boxonline2[.]com
24
ns1[.]boxonline3[.]net
24
ns1[.]boxonline1[.]net
24
ns1[.]boxonline1[.]org
24
ns1[.]boxonline2[.]org
24
Files and or directories created Occurrences \??\E:\autorun.inf
24
\autorun.inf
24
\??\E:\System Volume Information.exe
24
\System Volume Information.exe
24
\$RECYCLE.BIN.exe
24
\??\E:\$RECYCLE.BIN.exe
24
\Secret.exe
24
\??\E:\Passwords.exe
24
\??\E:\Porn.exe
24
\??\E:\Secret.exe
24
\??\E:\Sexy.exe
24
\??\E:\x.mpeg
24
\Passwords.exe
24
\Porn.exe
24
\Sexy.exe
24
%HOMEPATH%\c
24
%HOMEPATH%\Passwords.exe
24
%HOMEPATH%\Porn.exe
24
%HOMEPATH%\Secret.exe
24
%HOMEPATH%\Sexy.exe
24
%HOMEPATH%\c\Passwords.exe
24
%HOMEPATH%\c\Porn.exe
24
%HOMEPATH%\c\Secret.exe
24
%HOMEPATH%\c\Sexy.exe
24
%HOMEPATH%\c\autorun.inf
24
See JSON for more IOCs
File Hashes
0223f31be057b76cc3c77463a5ac362dfb164d921865d6fac45bc0b342a24987116a453c9f33b2471e3e4f688e65d9a816039ed8978e4bf9419e0e74d3e4c956184c4a17e81a3b8628401cec2c3153c8d447427612b0015689e63eb57c6d29293d51dc56d04b6b1a770191d01ebd25a8f461e906cbcc4a3c5e95d37c7b117d1a5050ea8a4fc19652186b7bd5d2376c5772cf7fdcd8f9075731e2c7ece560afc883a2a54dfd89718b6f949e79a21b697288197422655c1eef52d410df9583c96a9aa53a3a52c40afe47a531badf1df6c812c985e5d0d345f00fabf8fad53319b79cf7815a0c7da0d55dd202dcbe171d7109a24857ccea16a7ab21827e3fce8386a1cdaec71cd76dcf37b43c55d7ae9c33dc4d2a6baf55cae35d3214e582c1f9f3a20512d57c5d82b8df044ac5bfb0f7f345290e8b6e388b3a17ea88671766f9c4a5cf7dc6a3c6b2fce41a4fcf0f0d98ef1cdd91af9d0e292c6e9142eae0b06b82afc01f079aec32874f62926770d6cdf74eb19289954fdfe830d0ac17160698bfb9845e32db4bdf3fc5f795fa7979f092116c3b9b39c364b96bcada6921a81918b990b6dd7a5bfde334b246c100a95b7dd52611d7167a81e9399f1f191be172e9ba9f10b7ac5e09f0137206341a4a7ab36e74f6d2d12f84f4057adccbc9d2ea3ebbbb74ba16e46156f476676ba8e24de3b7b13ee363188a8252f7b2784e9b5e55be56ffcee4c9fb35af3ba72afb1b4be47ae841390e2ea2966cced4af7dad46d5c54174b6e003481ce059f05fe0c33d8bdabc5d49cdf82eb3f52436c87ba886e3cc8cc46b4932f6ec383699a14776bbc573f366a5f3db87e1cd0edafd1b36303fdae1aa0ccf8af9b1ea58d81097f09ea3af90f7c9bf0bf4d6e03f93fa0224e0f9edb225e13b85e2680eaf3379f1902afe8059a23b475642076e0b4b3558dd738cf43b29ce77ef694b43467fd0e69956e46ee69805abd2963bab7d33bbcd0ad4effd17a474fedafc167118316dbad93648c63365e645a1233b9f8ef0aa5d7aa127ffdd606b64c51d5ec950dee14328c97cac84b75090f77ad7e77c5bf9da20ce08 Coverage
Screenshots of Detection AMP ThreatGrid
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (3872)Kovter injection detected (2952)PowerShell file-less infection detected (1443)Process hollowing detected (356)Dealply adware detected (243)Gamarue malware detected (194)Excessively long PowerShell command detected (106)Installcore adware detected (61)Fusion adware detected (40)Possible fileless malware download (31)