Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 14 and June 21. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
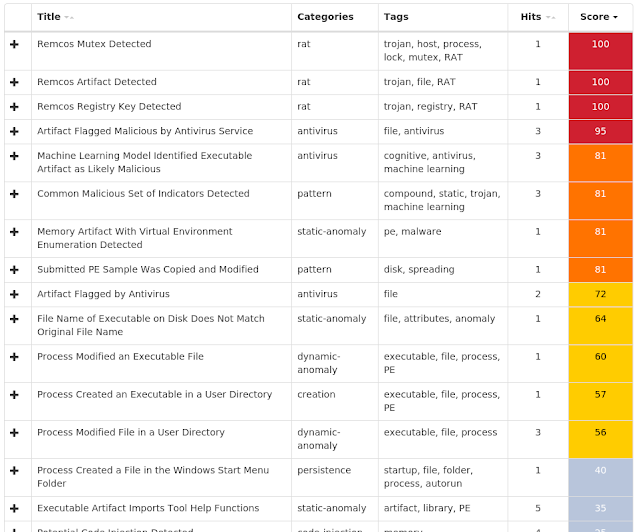
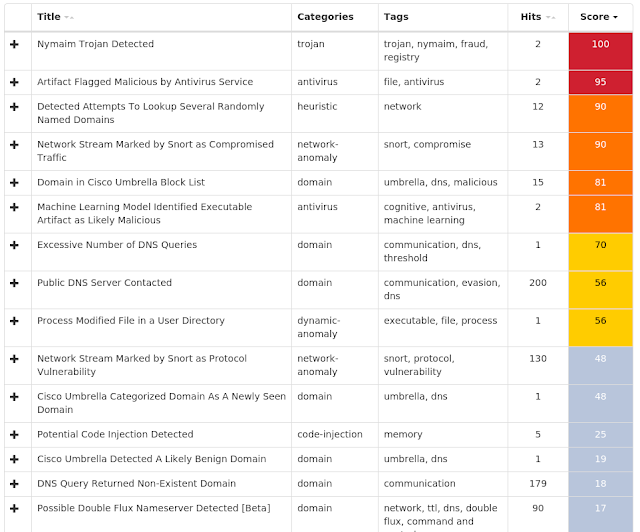
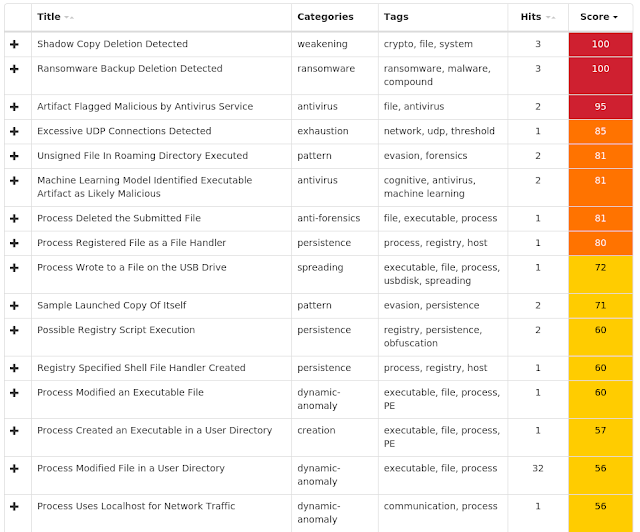
Win.Malware.Remcos-6996918-1 Win.Dropper.Nymaim-6996892-0 Win.Ransomware.Sage-6995951-1 Win.Malware.Ursnif-6995948-1 Win.Malware.Zusy-6995723-0 Win.Ransomware.Sodinokibi-6995593-0 Win.Malware.Dridex-6995476-1 Win.Trojan.Shiz-6994953-0 Win.Virus.Expiro-6994921-0 Threats Win.Malware.Remcos-6996918-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\remcos_gerjisumsvyvegw
25
<HKCU>\SOFTWARE\REMCOS_GERJISUMSVYVEGW
Value Name: EXEpath
25
Mutexes Occurrences Remcos_Mutex_Inj
25
remcos_gerjisumsvyvegw
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 185[.]84[.]181[.]90
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %APPDATA%\remcos
25
%APPDATA%\remcos\logs.dat
25
%APPDATA%\Machree1.exe
25
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Machree1.vbe
25
%HOMEPATH%\Start Menu\Programs\Startup\Machree1.vbe
24
File Hashes
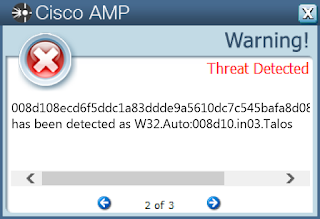
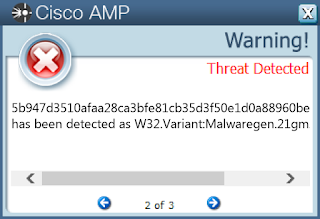
008d108ecd6f5ddc1a83ddde9a5610dc7c545bafa8d08a5f334cf6c18b8f8c480532cb4b98868c1ca8c6679a128649ef4db64ce7aa495c43b43a1c63622e9fb305914740255f1e48bd2267145f374d982a6d84a52666a51064f3a4a2d53ca667061345d5cb07ed337651b14172d5881c7f940225f777e97162d3bb5d13b9f303061699059a6bb9fe01566d062f1425eab0a8b67f47b088f45f4ac2b44c04bbe006cb29e96868854c02e5121d9c72e8ea17ed97a519bc7d2c8cc4fc55d56cb6210771087cc5d55f25b3ef398fbe3303e46fca47c4b56a84a611f567b5d299939008242c0494c9cedf45cb27f447848661ea57f1598734ced8d0ac6e529a52eb0d09dfabb291531d5d9b5250bce1b0e53a4ac318d9c16712190ff0197f42b051170e30994864e21d987ef62a0d26d280c35680c151853c93d7b591dc5b711a859c0f11daf971e9e8777a01b3892de3cf14d4f2eb8ba3bee6c589832e42e512e23f15a34dc9368201767521a71133fc51442bbaf87b5f7449895f32e9dd6860e5b915fa9cfaaba597d539b6037789bab5817e878c391a684fe24226b085822a5f5c18e4d4f751a9b0dd98c1d44f5ee6a711850074244b452541a1807bf06dfaebcf1d608c4f6f5461bd282fa372a7142214aac8581b767f8c961bcfd1e0b67a777322586b36679b18e7f560cb3382c4d5b10e173dcce3f9c038d6cb6c0bdb30021e26952825987d9fa2ecbf59acf74cc46f546acafc9212130b77c66d442a8884682c707b9f5c691c03a36e0b77b83572abd481197aa9d4ad075a8921b54a0e2ac22d1286793d988e5f5fb49857d40ed6fc6626b81a7fc15436611230b03b8cb23638fb84780fe10c9d89765365cf3a7e96b992a9efb8e049605139fb75da1971d53aa207171befd54d8d3e1c4cabd692c6a59c9dfc24e2ad1be15e66cfe972c6313ae0b911a9934ad510b86b86cb74c891754fdecf26bb537d603869e559cf6f803e662b8b705b1d3d6f7d731bf341d0c328cab969d36b9c1d7ed36941f5c1d2e63ec95e210408d3e195af15058ea02b93abe0be5d88364da0927921deaced8fdc3ee483a19e47433b5b36b6df2456d713d9737083652300651b19e5d56d803526See JSON for more IOCs Coverage
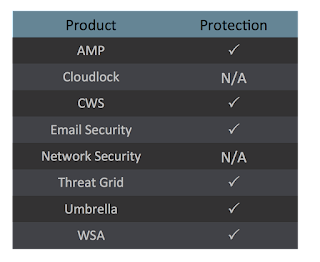
Screenshots of Detection AMP ThreatGrid
Win.Dropper.Nymaim-6996892-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\GOCFK
26
<HKCU>\SOFTWARE\MICROSOFT\GOCFK
Value Name: mbijg
26
Mutexes Occurrences Local\{369514D7-C789-5986-2D19-AB81D1DD3BA1}
26
Local\{D0BDC0D1-57A4-C2CF-6C93-0085B58FFA2A}
26
Local\{F04311D2-A565-19AE-AB73-281BA7FE97B5}
26
Local\{F6F578C7-92FE-B7B1-40CF-049F3710A368}
26
Local\{306BA354-8414-ABA3-77E9-7A7F347C71F4}
26
Local\{F58B5142-BC49-9662-B172-EA3D10CAA47A}
26
Local\{C170B740-57D9-9B0B-7A4E-7D6ABFCDE15D}
26
Local\{B888AC68-15DA-9362-2153-60CCDE3753D5}
26
Local\{2DB629D3-9CAA-6933-9C2E-D40B0ACCAC9E}
18
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 34[.]227[.]185[.]153
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences olmcehndmyhb[.]in
25
thxwvxr[.]pw
25
wjztocdw[.]net
25
gxmxojjk[.]com
25
mmyuf[.]in
25
dlycu[.]net
25
oxkkvlewktdt[.]in
25
hlexdsgcio[.]com
25
yayksuheo[.]net
25
fjfrix[.]pw
25
rqpdg[.]com
25
sqbxpxuhgs[.]in
25
wmimqpx[.]pw
25
nnhquzhcvm[.]in
25
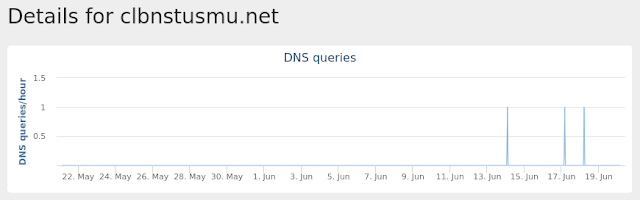
clbnstusmu[.]net
25
kttasj[.]in
1
qthupu[.]net
1
bqdkoibgkrw[.]in
1
rakacljgisdb[.]in
1
nefhn[.]in
1
bkbyvpcgbcnc[.]net
1
xabzrrutxu[.]com
1
yckmgwft[.]com
1
deueijrnywe[.]pw
1
tazhibvbczf[.]com
1
See JSON for more IOCs
Files and or directories created Occurrences %ProgramData%\ph
26
%ProgramData%\ph\fktiipx.ftf
26
%TEMP%\gocf.ksv
26
%TEMP%\fro.dfx
24
\Documents and Settings\All Users\pxs\pil.ohu
24
%LOCALAPPDATA%\7z2
10
%APPDATA%\s269
10
%LOCALAPPDATA%\2870
6
%APPDATA%\710i5v8
6
%ProgramData%\05n3
5
%ProgramData%\0m2
5
%ProgramData%\pj57siq
4
%ProgramData%\02zs
4
%ProgramData%\j91z
3
%LOCALAPPDATA%\9b8
3
%APPDATA%\mb31
3
%LOCALAPPDATA%\lnt0
3
%LOCALAPPDATA%\uhs
3
%ProgramData%\hm94p64
2
%ProgramData%\9qa3
2
%LOCALAPPDATA%\4y343
2
%APPDATA%\h65
2
%APPDATA%\3084
2
%LOCALAPPDATA%\c5a
2
%LOCALAPPDATA%\q0n0
1
See JSON for more IOCs
File Hashes
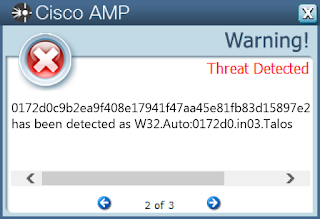
00e353db4270f10024bfecdb87176625a79fe79c8fc5447c117cf65231df3dc20172d0c9b2ea9f408e17941f47aa45e81fb83d15897e2a49c1213abb725387d6069f16f2659e165ff2b29f2e539af61e986955738187d987b83fe36dd18ce721082e25b44250cb9eb2771c72ab79acda6bd6846090d4ac3d839e201b0782a2e20cc0e127d86659ecf3fcbcdf04fcf72217a3ce12081b48831e739e5001dd2e040fac2d86d39cc022dea6a0ba072ac88985fc9f0bd9dcd7246f3395daea9d5c2b17094de48ed74622c81a08504bc65c32c518784ac791197a8fe40f315a5db41d1753a38b2c5f994198409c1f706d61a7e3059502a40fe577cc2071e7765ffdd51d04d5db2cee469d6a6de02bddb26a0ebd648ecac8a8437e700c448d48f4a4bd1f8ded1f7ff186d6cf02db9a9fb32837cf32afc2c9cce54862ed8332e8f7afed3611e930dff5d525411c09b000d4c3f39e4ca3c3de408222e32efeef36f6bee9388fd291540103637daaca22f40ed1219e60713e01d00943e57b56c50b8bb0af4cf78bec349135e62405097f3c7ecbc496d9ac82357ba36563cbb0dc77ef73ea578ac45673bbf7516027b31626390893dc95e9646fd5860f23562c660c23ebf86557ecfaa38148a9b4f6652b5f0f0dabe2fb9c27ad44b86e2fe9db38baf2e9446fd12db488909e16ad2bbfddc8cd1ea8a405e3846a3f08d2ef17b9abce598840743acd3870df235c506231e1da30d55549b878b950d0a7e31b9a1b2299c2172c779f163a69ad38fe61dab7bfcea1a2fedaa951c7f957774acf4f3d5e1ed4487a783ad0bb502ddba1fc42383b34bd8252568fff178dcb387b25984a36f3801ff579c279315079c1307b73a49591b441e8ba19f169321d343b129d374b0f10d37d7a3a5142c6d45c5bbf24a6a841cd494487ab83561a7e3f8221ac1a6f019e3a68901a670c01ef2f5b81eb5b2914d6f642aa513adae76e7714e5bf49ccd1a4386c9cd58d1690a4dd35c764097538edd119e5ed4a6ebea2bf08054c7e6fb43b599cab8eef993a40335c73bd970654e1342a1c0c1e9081b59c45027e6db608971e6faf527cf0ab22c9d7acaf33ceec3996185c0aef59bd9fa2784dd9ac602d85fa19See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Ransomware.Sage-6995951-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
25
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}
18
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
Value Name: CLSID
18
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
18
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
Value Name: Generation
18
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER
Value Name: GlobalAssocChangedCounter
18
<HKCU>\Software\Classes
18
<HKCR>\.sage
18
<HKCR>\sage.notice\DefaultIcon
18
<HKCR>\sage.notice
18
<HKCR>\sage.notice\FriendlyTypeName
18
<HKCR>\sage.notice\shell\open\command
18
<HKCR>\SAGE.NOTICE\shell
18
<HKCR>\SAGE.NOTICE\SHELL\open
18
<HKCR>\htafile\DefaultIcon
18
<HKCR>\htafile
18
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: Wallpaper
18
<HKCR>\.SAGE
18
<HKCR>\SAGE.NOTICE\DEFAULTICON
18
<HKCR>\SAGE.NOTICE\FRIENDLYTYPENAME
18
<HKCR>\SAGE.NOTICE\SHELL\OPEN\COMMAND
18
<HKCR>\HTAFILE\DEFAULTICON
18
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}\FILES
Value Name: Datafile
18
Mutexes Occurrences zHUoNUQ7
25
Local\30F1B4D6-EEDA-11d2-9C23-00C04F8EF87C
18
\BaseNamedObjects\PFShggN3
16
\BaseNamedObjects\adX9ZN6Z
16
Local\{3AE0DB4C-C01E-4DAE-8FDC-24ACF3B28941}-Mutex
15
Local\{609C30CE-E266-4A73-A27F-BD103B3FA847}-Mutex
2
Local\{7C86DD40-D457-4186-A852-0F98388A1834}-Mutex
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 5[.]45[.]6[.]138
25
5[.]45[.]159[.]19
25
5[.]45[.]140[.]6
25
139[.]59[.]93[.]181
25
5[.]45[.]226[.]237
25
138[.]197[.]136[.]196
25
138[.]197[.]105[.]68
25
211[.]114[.]30[.]7
25
5[.]45[.]247[.]22
25
138[.]197[.]196[.]19
25
138[.]197[.]122[.]68
25
139[.]59[.]227[.]172
25
211[.]114[.]64[.]63
25
5[.]45[.]129[.]52
25
138[.]197[.]22[.]151
25
211[.]114[.]47[.]80
25
211[.]114[.]28[.]235
25
138[.]197[.]109[.]79
25
5[.]45[.]242[.]197
25
139[.]59[.]219[.]237
25
5[.]45[.]24[.]236
25
139[.]59[.]185[.]4
25
5[.]45[.]238[.]90
25
211[.]114[.]135[.]136
25
211[.]114[.]84[.]142
25
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences mbfce24rgn65bx3g[.]we0sgd[.]com
25
mbfce24rgn65bx3g[.]y8lkjg5[.]net
25
Files and or directories created Occurrences %TEMP%\__config252888.bat
25
%APPDATA%\Rj3fNWF3.exe
25
%APPDATA%\s1qoaKDO.tmp
25
%HOMEPATH%\Documents\!HELP_SOS.hta
25
%System32%\Tasks\N0mFUQoa
25
\!HELP_SOS.hta
22
%TEMP%\f1.vbs
22
%APPDATA%\f1.hta
22
%HOMEPATH%\Desktop\!HELP_SOS.hta
22
%TEMP%\DDx.bmp
18
%PUBLIC%\Desktop\!HELP_SOS.hta
18
%PUBLIC%\Documents\!HELP_SOS.hta
18
File Hashes
002681facd1401892d38d6b2fb8a4a601cb6097e2036807d960088e3a11518bd07ea28b71fa40819e50c191eeb968029564ea50c1be7f9fa9c60c9e0949c238b0866e68a80127122197155713e6a88ee77833f5a309ee5a78f172fcda338ad420c022132886217e726f6c199a7336da8153b17477740dbbfb381c246253e98b80c2c36fb7443677b044a0d9802caced6ef9ed367ad8d22941d22ce5b7c62015b0d873b512bb9419c70d5d9a173de936a4fb88e78e62cea33f8e7588efb13a9860f05b4134b3474c2c3f9f715ab625515e4dc74d175f224dbd743034ca7fd5f0c19c7fa10cdb6af0a317b898fca0c2f8dec17766ee7c486be6d2d4e8151943cc3277a53be722f0af119fe7ec952391fce2ba5dffe53499b6b066a0a7760c549f427f2a66812448c1a9e157d6814c1622a15ef098ddc5bd79c5ed5c0faa1fb683c2cf2814a79c30a107bf7b765f7fbd8f7f12fd7feceed7d7948c777ef4862a2bf4264426561ed818abc86cadef408e0501efd8a377d668d5ba08e7634aef1ee4e484afc576a95445933cdee2304f015758a3f1979460a7fabffdc7680be48f6f64c78e95297bd4e39c874b5405db0cabc9543bd586db72d7396a4854e57b4ccf45069703a5f06e1ca23ea7ae6cf5b12d1e8a22c38b71712927491633541cae49654791783603a6ac3e74a6d64276b6f6160da289130d42fc7c6a58632c6b7bccd5b947d3510afaa28ca3bfe81cb35d3f50e1d0a88960be5ea3da634599337deb75dd1cb4b4f8a339024c010d10343093671db5cbac4b9653789488843434a16bc65a1582b598001becc4c95c429097481b4572d5e012991912a0269db77dad1376b8921856dfbc5ae21bb2cca0def18769ed855f3d9a2d0e90b2a9776bdb0e7096cd837db9ee3984c5bbeb23ec892a4fa298cd10d698ebcfbf8379f944fce39f373573450b01ab7f8da715315f5bfca23fb80c1c6be629f36a68f0ba70beb78857e0aa71c458ed642ed6d210aac13b088bc4e0ab15c73699dc279d0a0c6af0637805f4e981b4f67c65492734466d6089a44a56cd7555cb7e01513f2a318fd4632878156061f18393a0889e3fd6eba8138d33f29ac1dc3f39ec3e54e5693c966b6See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Malware
Win.Malware.Ursnif-6995948-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\IAM
Value Name: Server ID
15
<HKCU>\Software\AppDataLow\Software\Microsoft\02BAB7FD-7931-84AC-1356-BDF8F7EA41AC
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: aclutxml
15
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\02BAB7FD-7931-84AC-1356-BDF8F7EA41AC
Value Name: Client
15
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\02BAB7FD-7931-84AC-1356-BDF8F7EA41AC
Value Name: {D7908994-4AF8-210B-0CFB-1EE5005F32E9}
15
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\02BAB7FD-7931-84AC-1356-BDF8F7EA41AC
Value Name: {344BD002-037D-867E-2DA8-E71AB15C0BEE}
15
Mutexes Occurrences Local\{31F7CC8D-DC06-8BF4-6EF5-D0EF82F90493}
15
Local\{73A713E4-3646-1D08-D857-CAA18C7B9E65}
15
Local\{C955B29C-9464-E306-E60D-08C77A91BCEB}
15
{D647E266-3DDD-787D-776A-C12C9B3E8520}
15
{EA4B00BD-410A-AC5E-1BBE-05A07FD209D4}
2
{5E33275E-2503-40DA-9F72-297443C66DE8}
1
{9AA3B82F-319E-DC81-8B6E-F5D0EF82F904}
1
{B2A0D287-6908-B436-8306-AD28679A31DC}
1
{16F26DB9-7D02-B8E1-B7AA-016CDB7EC560}
1
{2EBBEFAB-B5C8-9042-AF42-B9C45396FD38}
1
{6618B948-8DD4-88EC-47FA-113C6BCED530}
1
{C6705878-6D91-E8C3-275A-F19C4B2EB590}
1
{C6978AC4-6D8C-E882-275A-F19C4B2EB590}
1
{F2232C8E-A932-F4DB-C346-ED68A7DA711C}
1
{82016989-F9D2-04E0-93D6-3D78776AC12C}
1
{F6025C5D-DD1D-9885-178A-614C3B5E2540}
1
{2AB58D90-81E2-ECD9-5BFE-45E0BF124914}
1
{22C3958C-1968-A432-B376-5D18970AE1CC}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]67[.]222[.]222
15
52[.]58[.]78[.]16
15
87[.]106[.]18[.]141
15
62[.]149[.]142[.]160
15
62[.]149[.]142[.]166
15
Domain Names contacted by malware. Does not indicate maliciousness Occurrences schema[.]org
15
api[.]w[.]org
15
gmpg[.]org
15
maxcdn[.]bootstrapcdn[.]com
15
resolver1[.]opendns[.]com
15
222[.]222[.]67[.]208[.]in-addr[.]arpa
15
myip[.]opendns[.]com
15
ogp[.]me
15
themeisle[.]com
15
www[.]addthis[.]com
15
atomi[.]org
15
www[.]capoverso[.]info
15
capoverso[.]info
15
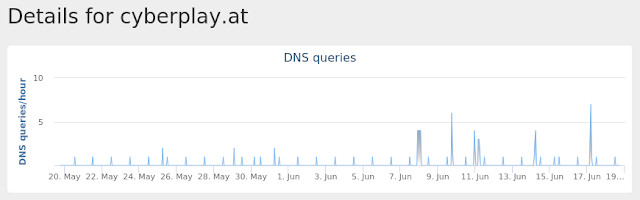
cyberplay[.]at
15
smashballoon[.]com
15
www[.]azzurrabiagi[.]com
15
Files and or directories created Occurrences %APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\prefs.js
15
%APPDATA%\Microsoft\Cicprov
15
%APPDATA%\Microsoft\Cicprov\api-draw.exe
15
\{5D9E0C27-180C-9720-0AE1-CCBBDEA5C01F}
15
%TEMP%\70B2.bi1
1
%TEMP%\E304\10.bat
1
%TEMP%\716D.bi1
1
%TEMP%\E536\F29B.bat
1
%TEMP%\6E32.bi1
1
%TEMP%\E110\10.bat
1
%TEMP%\90EE.bi1
1
%TEMP%\F56C\FAB6.bat
1
%TEMP%\8E8E.bi1
1
%TEMP%\F490\10.bat
1
%TEMP%\A143.bi1
1
%TEMP%\520C\2906.bat
1
%TEMP%\9DD9.bi1
1
%TEMP%\3F66\1FB3.bat
1
%TEMP%\89BD.bi1
1
%TEMP%\1460\A30.bat
1
%TEMP%\99A5.bi1
1
%TEMP%\3BDC\10.bat
1
%TEMP%\81B2.bi1
1
%TEMP%\B7A
1
%TEMP%\B7A\5BD.bat
1
See JSON for more IOCs
File Hashes
03acbc64c9b3989a76dd27df76ce1d8cbe73ecb9b44b3573db48dc1f68812009092491d78943b29e6fd44893c945ff8fc4ac6915288c91e63ea9995fbcbf076e0a7fdfc7765dc8c7b1b7163ac790eabd225565110ae21ca6459cdae3174802371673c7630dba0d13ddf37fd41d3df713716636d6e17a0783339688928c0094cb189a2e65781d3f026a1a8a19b21fbf2e305504e7e8317865ad4e538e055f5571306c7d52c2c6d02bc243dbdaea2084f9b32346dd48f6bb436b947fed783744de32b005dbb3c48e6aa483c078b4a67361bf913d6204549f635a8a88e42097d9ea741a2e9f54703f4b79bae3d2824e0b675817bbdaf3c9863bbe1457584edc25017e97b034ba57094f287acac4a02bfa379db09366aed17f0dc12dd63b32e4cb5885ca78bd8452b966c035a15c9cdad1822f252e4fa89373d249927951c16ac3058abd4e0b76d245ea7d3f05bb4c51a67aebdbc3acef4d9f2f4724397d9c3cccd9a0f4837e429db7efdbdaa6cdbedd4a8c2af20b995aecfdecaf6438651d6c4a55c139ae8e6b92853d8c2d189ef3bb100782e4bb820cbd16cd6901067d4187ad96c523e34ec9d8af73d08cb1208e31e22f0de9a32c7d0dc57a7fe96311fcbabac4da646594016fbbf3eeaf875fb01c4d35ab8c72837a99152a8cd696eeb32863d7 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Zusy-6995723-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: EEFEB657
16
Mutexes Occurrences EEFEB657
25
\BaseNamedObjects\4A60888F
24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]185[.]162
24
216[.]218[.]206[.]69
1
104[.]238[.]198[.]190
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences brureservtestot[.]cc
19
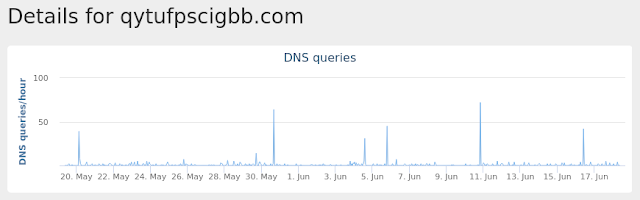
qytufpscigbb[.]com
3
Files and or directories created Occurrences %APPDATA%\4A60888F\bin.exe
24
%LOCALAPPDATA%Low\EEFEB657
16
%APPDATA%\EEFEB657
16
%APPDATA%\EEFEB657\bin.exe
16
File Hashes
028d11679340a1b6c63a10553cb3d3eefd898994d8abb6555c2b516976def7af02cfd52d13be87eb03002bb503650e9039fa30322f43ca6e7df23596b4e791290584391d84c0d39e853958be9a3a01d6a2c77513c5731ab50f81a0f7234381e30634e2abbcc9e55b84c1f144b381c3e0f7ea5f5f2cff8e5f9a8f07b4407bbd2f0e12e7bed943fdbffe284ff143034204f1473dccbb3605526988972f88d227e80ec0197b47f0585471b4121a1b84dde9c50fcb4265cdf30b4da57a4a408c854311e972658b8649e229fcd4272bcf68ee7c52b99ee11b91a08231faef4d554eeb15ac577f5b198fc6db81c854fb08beabe75f3dbba190375058192c06faa1635e16be38687d00e7c50c4f6b68d9d52ecdb9b7f195ff7c96250aa54de9b8483a92177c118622bcd7ce78f740dc7ae6501bed20fa581c9d75b9f183e065badb89b01cc2fb4f39d0b5991c9d2a9f85fc61a359d7f53105325b53dfd70ec807be09041cc93e8839a9cdc79a9165baa61b43065210b6204fb43e8dd66479d8fe0b5a371d34ffabc85ec962b3c2ff8b4107154e7d56debf9723cf6466bfa1552a8035de20b1b90aa72891d632067d92b5aff513219b46ae0166a275f979f0a8553882de24a906c73eb7e2fd33ea90f714e0950d267dd852cb38232162a9cfd4bd9b43ea27a6628ffadf218081c50c05b098956f83c54dfc0820d4216851a9cfb85b7c4229d7b8cab5b08106a011bc74908638168f91578dec2478b2f245e091eb44c3d92a5b2b31e2aca479bff24922f4170a74cfe70914589af4b1f30ac931039339732d29e10bad213d8eb768b306d24dc3bc40af3127e39af12934c13b69b2a50cb32dc9fcb48596f3660e37b004504dd4cdd147a317f1d91c4f1af0858798ee63503d665290548cb0ca8bb65daf166c8fa5781bdccb6854f658749becb84f1de7313e1d13408d35361b3880ed7081c4cad0cc8af48e3fa72e57c9fd00b33cb3e1d7477b06ead8877f7b3dfffc7263d2a3740ed978797730cedcbe2274ba783c4c0147d6ff0d66e8a2aa608682894f37e3fac9504f499eba421ee7f921896b622ffe48484ab467c9a716ce6d0fbd9cfed614657ff1e7f317bfe40849bcf1f92b2736See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Ransomware.Sodinokibi-6995593-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\Wow6432Node\recfg
15
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: pk_key
15
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: sk_key
15
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: 0_key
15
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: rnd_ext
15
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: stat
15
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: Wallpaper
14
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\DAC9024F54D8F6DF94935FB1732638CA6AD77C13
Value Name: Blob
11
<HKLM>\SOFTWARE\WOW6432NODE\RECFG
Value Name: sub_key
6
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\490A7574DE870A47FE58EEF6C76BEBC60B124099
3
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\490A7574DE870A47FE58EEF6C76BEBC60B124099
Value Name: Blob
3
<HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CERTIFICATES\A9CE8E8879AB0CCB17A1FEEED83E720F3D925DF8
3
<HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CERTIFICATES\96002650CC3818ADB7BC358B15AF098A0BD0AEB6
3
<HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CERTIFICATES\A9CE8E8879AB0CCB17A1FEEED83E720F3D925DF8
Value Name: Blob
3
<HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CERTIFICATES\96002650CC3818ADB7BC358B15AF098A0BD0AEB6
Value Name: Blob
3
Mutexes Occurrences Global\206D87E0-0E60-DF25-DD8F-8E4E7D1E3BF0
6
Global\FDC9FA6E-8257-3E98-2600-E72145612F09
5
Global\6CAC559B-02B4-D929-3675-2706BBB8CF66
4
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]35[.]177[.]64
12
87[.]98[.]154[.]146
7
50[.]116[.]71[.]86
6
141[.]138[.]169[.]215
6
213[.]186[.]33[.]3
5
52[.]28[.]116[.]69
4
213[.]52[.]129[.]248
4
109[.]73[.]231[.]100
4
193[.]124[.]179[.]13
4
46[.]30[.]215[.]77
4
188[.]213[.]19[.]167
4
109[.]237[.]212[.]70
4
80[.]158[.]2[.]41
4
185[.]197[.]130[.]80
4
159[.]203[.]88[.]13
4
46[.]45[.]134[.]70
4
107[.]180[.]57[.]28
4
185[.]103[.]16[.]188
4
188[.]165[.]53[.]185
3
213[.]186[.]33[.]24
3
185[.]52[.]2[.]154
3
66[.]228[.]32[.]51
3
85[.]214[.]26[.]104
3
198[.]71[.]233[.]104
3
52[.]9[.]200[.]151
3
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com
13
apps[.]digsigtrust[.]com
12
kellengatton[.]com
7
ziliak[.]com
6
matthieupetel[.]fr
4
bd2fly[.]com
4
jefersonalessandro[.]com
4
silkeight[.]com
4
the-cupboard[.]co[.]uk
4
lovetzuchia[.]com
4
stabilisateur[.]fr
4
fskhjalmar[.]se
4
atma[.]nl
4
naukaip[.]ru
4
bundan[.]com
4
iactechnologies[.]net
4
oscommunity[.]de
4
www[.]acibademmobil[.]com[.]tr
4
ronaldhendriks[.]nl
4
activeterroristwarningcompany[.]com
4
acibademmobil[.]com[.]tr
4
LSNGROUPE[.]COM
3
funworx[.]de
3
taulunkartano[.]fi
3
energosbit-rp[.]ru
3
See JSON for more IOCs
Files and or directories created Occurrences N/A
-
File Hashes
0aebc3c9dd12779c489012bf45a19310576ec0e767ac67d1c455839302465afa1501f261a66eefce47dc47cb8a426107c4b694a41b5b9fd000d0ad2ea76d8e3417d153a225ea04a229862875795eeec0adb8c3e2769ba0e05073baaf868504671937098609fbbda1b470811a7ffe5fa044058655722d84bd029050d54f2b14962ea781140f7e86c63b636249b5fdba9828661bdd846fd95c195c5b986b84a50736fa3f72afc2dd6f206a295fc618038fef5e241bc48bd5451ac9bab9128734dd4748e9729f2e0b1bb151950cdaa75d51ad74612a1c12ff124a492a9a67c2f49b6727edbb5d6abee908851a8c5fd7b4aca6d664634fdcdfc15e04502b960abbc56efd9aae5e112418bd43ab48ec4a1fce191c7503fcd11fdb95e89ad0217adb7a7bafd5de1b6724962ab920f71031978a101055f061ae3cc21db8bb9fa64c5829861bc212241bcac9f8095c8de1b180b398057cbb2d37c9220086ffaf24ba9e0889d80016ff4c6600e8dd8cfad1fa6912af4d21c5457b4e9866d1796939b48dc49fa3a004576f357b5174dd1c29ef7d13005d996d5f9fb4b86d6d978d1a4a84aea389e24bf0af9bc81b8133a600a2b6c875d32aa0885964d0b9f3ac6db5fee762e281347d6faf8fa17e9bcd79d0f815187506c89e8bca9ffae78170e31ff07438 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
Win.Malware.Dridex-6995476-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: trkcore
21
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableTaskMgr
21
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0
Value Name: CheckSetting
21
Mutexes Occurrences onXWzc331S
1
x1I78jI7dI
1
3BudAKaa5l
1
IY1oUapMVy
1
LAme40hNU1
1
PqPmiKaxbT
1
VlpnDSgg3g
1
oW2bMc607G
1
rzHJChsIaJ
1
uKmWBwWy5R
1
2kGkONAtb2
1
GPTOF7ZR0p
1
JRfp790lHH
1
K4EN0HOyBN
1
QiWTz8nBr0
1
hvUL9X1ymZ
1
kaqW5ROCus
1
w4Ith2QyiY
1
7flTFqBJ2g
1
A7OrpJ4YZw
1
Jjcx5gKyG4
1
SV3OytSaAP
1
kKOjeZFyh3
1
lBeTaukWiI
1
p74m9DtouU
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]217[.]12[.]174
21
104[.]20[.]208[.]21
17
104[.]20[.]209[.]21
4
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com
21
www[.]0kgr0svsdw[.]com
1
www[.]11exvnzpds[.]com
1
www[.]tqzvsormbw[.]com
1
www[.]egntxfch2f[.]com
1
www[.]p8o6adliq7[.]com
1
www[.]1di9yqmr4e[.]com
1
www[.]ahzu9hhyqj[.]com
1
www[.]x6n5szq1jb[.]com
1
www[.]0hox6fnkju[.]com
1
www[.]ahy9qgaqjw[.]com
1
www[.]uxnyhqblpm[.]com
1
www[.]1ohvaomcea[.]com
1
www[.]v2xeifg35d[.]com
1
www[.]wzykyninkd[.]com
1
www[.]tkhrjexxyn[.]com
1
www[.]u6vpjfufqz[.]com
1
www[.]05p60clujw[.]com
1
www[.]ijzuyfo6m9[.]com
1
www[.]nnd9bsodkx[.]com
1
www[.]ikzjlvrxat[.]com
1
www[.]ejglgrlsfv[.]com
1
www[.]49jucwch3k[.]com
1
www[.]dpnrq4kpe7[.]com
1
www[.]3rw4hwziej[.]com
1
See JSON for more IOCs
Files and or directories created Occurrences \388987352.exe
1
\old_388987352.exe (copy)
1
File Hashes
147861778f0693429684b6d52fddf6e8b5f1c09901aecf8da095d4e011813d612fcd0b9a9bd223ba0a04490a631b3bf92b537a006e060fbf4a0bb0541573c3ae450e7f78b43b060e3b55fb82ad75a914ce440ed365a3c74c5d9905bca3871f1e4b8384d3b9ba817e2c139fff74f289a2f9c75af1fb805d85d5fc798e8546a0f051e29a5685b27518cfc295d6f978c38d4c8a035f87f09d3c65a6e0c3ef8a5cf959397962406f67de80d7c4c98caf8253541b0707504facdc752bd1f1a35a834b6c9b8580f46ce7548254f1aa2e809a2e94cf41be58921c19f8d08a431c12ff3a6f8329e22dfeecb70fbe230e66cb4007e88e1dc3ef225d3207fff8046b26e3bf713a7b0b36eba38c569c59f337198d21860e04fd8277b7f2eb27cc071c97d6e288ed47a4401efef21a0f4168a04912f5577a2edb2ee14c4e8f77a9618e42d92896b4d6688b0d482ba1230fb3198bd9c79a43faea6f861e430f52b250da2745d2a2eb8d64d5dc33f8f89345b8574eb12d3122f6a32ee87d0935288e9650c76a37a8329c903e0d9d3f41301e110b490a3986260169c73adc539eaea21b155d3346af9428d1830d0e4b676000732ea0d99284f1db6a972ee6f776709491b85b5c16b64e8a3d377c8e16581540721c068c2d65d78e33254475a848fe23f1d6646c23bee09de2744b8ce8e11ab8d0eba4668d22a7083e4648835cc77f3742f3d4d8bccea99fa3855ef7bfe2651bd1e2ba1ab9725b2af7d07a70f70848348ad0993a71d3515980b07364781e8105a155009bcd7902380a74a9a4c81ed7f429c53b2074dd0bb344ab3e9de4812af9bc80c32fac182a31a6d144bb6c193bcc91628ee53bdf342abf5940fb9a6dfb7013b3766af13899873c7725fd43f8f4b115550eb8fbed9f38d2128c8d621140760571953d9d26bfba041309491cd6bc08d477f9326a Coverage
Screenshots of Detection AMP ThreatGrid
Win.Trojan.Shiz-6994953-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT
Value Name: 67497551a
27
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: 98b68e3c
27
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: userinit
27
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: System
27
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: load
27
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: run
27
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: userinit
27
Mutexes Occurrences Global\674972E3a
27
Global\MicrosoftSysenterGate7
27
internal_wutex_0x00000120
27
internal_wutex_0x00000424
27
internal_wutex_0x00000474
24
\BaseNamedObjects\Global\C3D74C3Ba
21
\BaseNamedObjects\internal_wutex_0x000005b8
6
internal_wutex_0x000004a0
5
internal_wutex_0x00000210
4
\BaseNamedObjects\internal_wutex_0x0000069c
4
\BaseNamedObjects\internal_wutex_0x00000384
4
internal_wutex_0x00000620
3
\BaseNamedObjects\internal_wutex_0x000000e0
3
\BaseNamedObjects\internal_wutex_0x000000dc
3
internal_wutex_0x000003b4
3
internal_wutex_0x00000138
3
internal_wutex_0x000006a8
2
\BaseNamedObjects\internal_wutex_0x000006a0
2
\BaseNamedObjects\internal_wutex_0x000005b4
2
\BaseNamedObjects\internal_wutex_0x000005b0
2
\BaseNamedObjects\internal_wutex_0x000000ec
2
internal_wutex_0x0000017c
2
\BaseNamedObjects\internal_wutex_0x000000f4
1
\BaseNamedObjects\internal_wutex_0x000002d4
1
\BaseNamedObjects\internal_wutex_0x000003e4
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 23[.]253[.]126[.]58
27
208[.]100[.]26[.]251
27
104[.]239[.]157[.]210
27
198[.]187[.]30[.]249
27
35[.]229[.]93[.]46
18
204[.]79[.]197[.]200
15
13[.]107[.]21[.]200
12
35[.]231[.]151[.]7
8
Domain Names contacted by malware. Does not indicate maliciousness Occurrences TUFAMUGEVIH[.]EU
27
tupazivenom[.]eu
27
qeburuvenij[.]eu
27
rytahagemeg[.]eu
27
tunarivutop[.]eu
27
GANAZYWUTES[.]EU
27
KERABORIGIN[.]EU
27
nojepofyren[.]eu
27
LYKEMUJEBEQ[.]EU
27
XUXETIRYQEM[.]EU
27
nozapekidis[.]eu
27
CILYNITISEG[.]EU
27
NOVACOFEBYZ[.]EU
27
lyvoguraxeh[.]eu
27
xubifaremin[.]eu
27
DIKUVIZIGIZ[.]EU
27
JENUPYDACES[.]EU
27
QEGEFAVIPEV[.]EU
27
NORUMIKEMEM[.]EU
27
xukafinezeg[.]eu
27
FODAVIBUSIM[.]EU
27
PUPUCUVYMUP[.]EU
27
vocupotusyz[.]eu
27
gaherobusit[.]eu
27
MAGOFETEQUB[.]EU
27
See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%\NTUSER.DAT
27
%HOMEPATH%\ntuser.dat.LOG1
27
%TEMP%\C.tmp
3
%TEMP%\1F.tmp
3
%TEMP%\E5AB.tmp
2
%TEMP%\E689.tmp
2
%TEMP%\5702.tmp
2
%TEMP%\D26E.tmp
2
%TEMP%\C6C5.tmp
2
%TEMP%\C6D6.tmp
2
%TEMP%\5742.tmp
2
%TEMP%\BB8D.tmp
2
%TEMP%\E56C.tmp
2
%TEMP%\EAA7.tmp
2
%TEMP%\6021.tmp
1
%TEMP%\BA52.tmp
1
%TEMP%\6920.tmp
1
%TEMP%\D079.tmp
1
%TEMP%\BEA3.tmp
1
%TEMP%\E11F.tmp
1
%TEMP%\D59F.tmp
1
%TEMP%\CBAF.tmp
1
%TEMP%\4915.tmp
1
%TEMP%\214C.tmp
1
%TEMP%\5EBA.tmp
1
See JSON for more IOCs
File Hashes
056d3a8dae02d04ba1312003791e46fe1ddaf1e850d1b847ad736637367fc718071b2028f9ddc54cf5bd04b3439c3937fd05d62c5ef70e6b5b07f81579e5806d0877c2c5e086884cd5654375483d6944286cb6351b0de2b2b8115daede3a440a09302a98d751e7b8097e2f98be7e747c42ae54e7906e8e7cbc1e5f273d793d120c214a0484f1e1d9197ca13159f71248dcf5f2576a93a6326471f2d02f9944de14ec15d83bb6ec592a7ef19d8b6d8d6e1a56475c512200721af9214c765f4b0516f65725e09cf3d55347eab4252481e65db4bbfae3113fac140f724c6eb94a1f182b84454c4674dc61e3215c6f07d0f546c4197ae688987e30a2fadb77898f751f10bb3822d7bf6dbe6cc2dfd72bc60e00197db5819d098e0e75c3ac2b4baaf6214ead8b6a5ba4205258abd256934c05316b4c02a0ec20f92e4415f36ca4f72324f43e78a195f256f4802e02851cc4dd69e912d92dcd7d2e33d6590716c86f03271f96ac65a9b97c4aecc1eee799a29a6244306e1e027df541f277a03fc66b7e32abd7d95eb9018ce1618fa0e48c3173dae0d0590c73b3200641b01d2897bf9d33bc6b06e7d06133c1872fc9fe3d734e382bc6577f2094ec60ab00d456a9ed443424ab4d70f930cd177b2ccdd96d81601efb6b51bb9bc51d64f913f8af5e960e34bebadd666db3fcfac273330324da52f1ac0c4fc794139be0e4d96504c34715353bb53dbcf5965e2d3afb933564dfb97b404327ad38a57d7cecbbd2013f357636d6f0252c5b39edd7784c048b14cc4e8b890274f9583bc91b79f2d45ca141283cee73fa5fb4bfe11d8eb751476a68e49222763b22dc3e35a13eaaf6af855ede3e4007511f5cd14c58fe373e3d78cb3c34e5cd5a16cce5a6aae1b8db373bfd0d41a4e635fb0542ebff2a9e533f3f7b10a6b6bed30dd7a67199d285e90bcd3a83431755f57af0005b3a27561c423cdbbfdcad11c18c709c2dead91a29b3a45f284332e8161e092aa143ac96b0e40241ba332fa300469f74329f43e7f83bbbd2e444671196bb73250589214bea72307d928d62cdef74877113e550b5fbdf59b95848117ef8d2fc9fc72e9529012eff094a1792915fd7e3147d52d4fedc7d596514See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
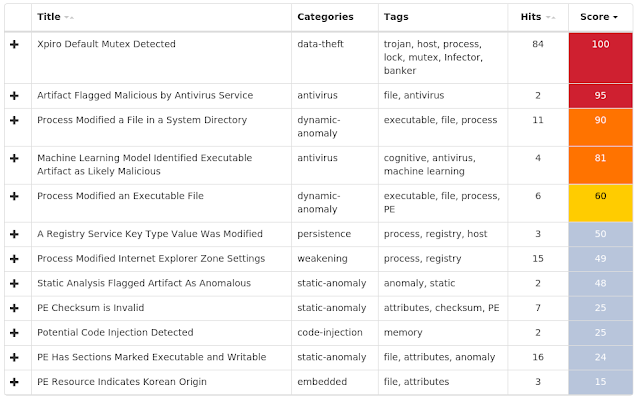
Win.Virus.Expiro-6994921-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Type
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Start
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Type
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Start
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC
Value Name: Type
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC
Value Name: Start
23
<HKCU>\Software\Microsoft\Osk
23
<HKCU>\SOFTWARE\MICROSOFT\OSK
Value Name: Setting
23
<HKCU>\SOFTWARE\MICROSOFT\OSK
Value Name: Stepping
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting
23
Mutexes Occurrences kkq-vx_mtx1
23
gazavat-svc
23
kkq-vx_mtx75
23
kkq-vx_mtx76
23
kkq-vx_mtx77
23
kkq-vx_mtx78
23
kkq-vx_mtx79
23
kkq-vx_mtx80
23
kkq-vx_mtx81
23
kkq-vx_mtx82
23
kkq-vx_mtx83
23
kkq-vx_mtx84
23
kkq-vx_mtx85
23
kkq-vx_mtx86
23
kkq-vx_mtx87
23
kkq-vx_mtx88
23
kkq-vx_mtx89
23
kkq-vx_mtx90
23
kkq-vx_mtx91
23
kkq-vx_mtx92
23
kkq-vx_mtx93
23
kkq-vx_mtx94
23
kkq-vx_mtx95
23
kkq-vx_mtx96
23
kkq-vx_mtx97
23
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog
23
%SystemRoot%\SysWOW64\dllhost.exe
23
%SystemRoot%\SysWOW64\msiexec.exe
23
%SystemRoot%\SysWOW64\svchost.exe
23
%SystemRoot%\SysWOW64\dllhost.vir
23
%SystemRoot%\SysWOW64\msiexec.vir
23
%SystemRoot%\SysWOW64\svchost.vir
23
%SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{9161210E-9C65-434F-8957-2AD799206FF1}.crmlog
23
File Hashes
0a5bc7465c0efc59aee85312a1abba14d691b3345d4b6630c3bb83dbae749dc712bd3e823cbb4a3e56ec5c17f69e28261f8cb39212c89e910780e7372a018c3617c037d9e0cbf4f6e11dc5f61c341484abcc28f9bb86e9052b6504af9d6dd5ae1f8a91163a60b9969ab43b6229c3715373f3a3974d74a74c08457a2af25d5ccb203ee856844e57afef69c3be268efb92ce466ba0ec541b0f56b8bdb336bdefc12a5ebd020ca217c6062d94212f3a47f229d24eb39a8b538795b04bba6749963141d9bb9c11ecadd28283770fc6a8580bd5ad9ba86df2e58e72672bced2a558f7445086ca6b9015865a25d5fb21d651153cab0e80b4b8958ee927803f7100417f4df7f7733ba6cc1d43683d036f2107eb909d07fb1f074ec6a8ebf595daedda18560ef4c5743def36e9b820378ad8dbf1f50d1cba83e1803db8931b734786de085ab01f91a3fe2c14e6a91098ac901502ddf68d676ed8317608c8f774c9df093e684f5c54d43bd1ef6bbd5b4781238e7d4d2411df9891240f5ec0a6e78d4921917aa38eac44171d5f764b58b1a5fe92334b5de3f8e187389405526362ee7f80be8d8b6d6b7269115b1aa4ab705b23a0fe890a75de5c56e91100d97bff1aaf885e90a43627c9897dd6f6e4ddc43bf2c911911f97dc7815955dd83855d0077862f5bb7cce3ef02d2a64fd37406f9e23975a7ac6fafab26669c908e369d872664010bfda0bc4f6756125e4a6fc0f3395bf1571ec00f2076a0480fcae7ba9a840c7dccab81316437f0ae434102ca0c5468688ed96cb802dc7db6f7d0786ff4824d57dd0e57c67a026d8d3e88997fff1e763b0747f1e770e19deabb3c52580213558d2e282f45eeac6018884c47130708572f962452e5c3db37dade2b8f2e292ad0276ea062e5dd432ffd64454bbb56566ea196d16df63ace79a59b59b727bae9eae63ebe6a5d9838b97702e6bd5c26bed23856f606514403e2d9cf8464f929fd10b87faebeeed682999de6f01135e8032fa377b6f1e54bd965ea79fb91d1590743b11 Coverage
Screenshots of Detection AMP ThreatGrid
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Excessively long PowerShell command detected (2608)Madshi injection detected (2504)Kovter injection detected (1026)Process hollowing detected (952)Dealply adware detected (264)Atom Bombing code injection technique detected (262)Gamarue malware detected (188)PowerShell file-less infection detected (153)Fusion adware detected (64)Installcore adware detected (50)