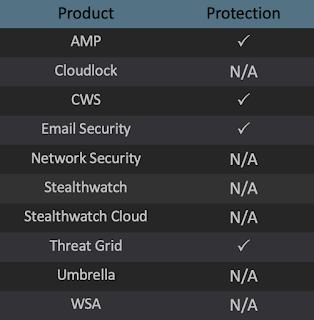
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 21 and June 28. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
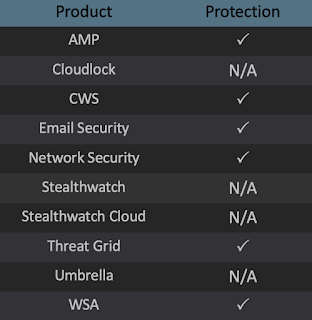
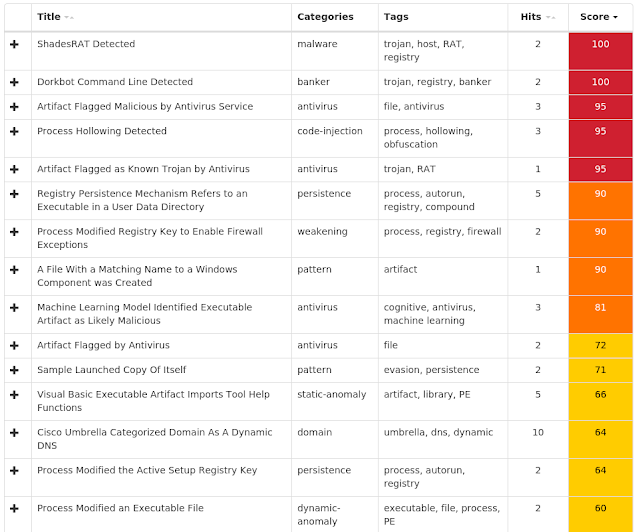
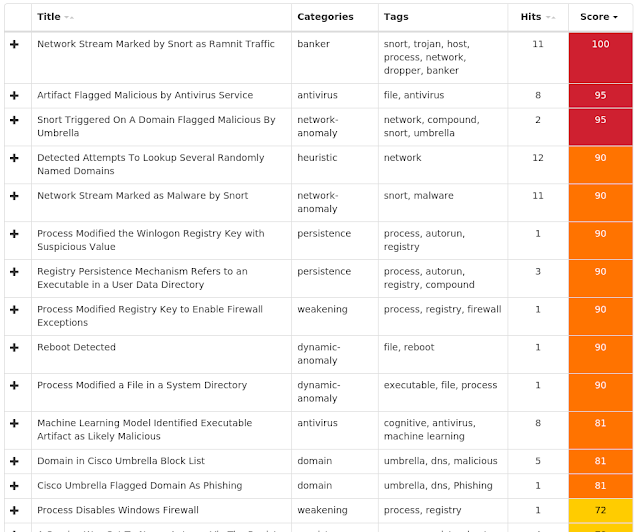
Win.Trojan.Zeroaccess-7002138-0 Win.Packed.Blackshades-7002008-1 Win.Malware.Gamarue-7001972-0 Win.Trojan.Lokibot-7001391-1 Win.Malware.Ponystealer-7001707-0 Win.Malware.Upatre-6997681-0 Win.Virus.Ramnit-6997840-0 Win.Dropper.Kovter-6998646-0 Win.Dropper.Gh0stRAT-7003005-0 Threats Win.Trojan.Zeroaccess-7002138-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: DeleteFlag
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\Epoch
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BROWSER
Value Name: Start
25
<HKCU>\Software\Classes\clsid
25
<HKCR>\CLSID\{fbeb8a05-beee-4442-804e-409d6c4515e9}
25
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\InprocServer32
25
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
Value Name: ThreadingModel
25
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
25
<HKLM>\SOFTWARE\CLASSES\CLSID\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\INPROCSERVER32
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: DeleteFlag
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000010
Value Name: PackedCatalogItem
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000009
Value Name: PackedCatalogItem
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000008
Value Name: PackedCatalogItem
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000007
Value Name: PackedCatalogItem
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 88[.]254[.]253[.]254
21
92[.]254[.]253[.]254
21
71[.]254[.]253[.]254
21
87[.]254[.]253[.]254
21
180[.]254[.]253[.]254
21
166[.]254[.]253[.]254
21
135[.]254[.]253[.]254
21
117[.]254[.]253[.]254
21
119[.]254[.]253[.]254
21
115[.]254[.]253[.]254
21
134[.]254[.]253[.]254
21
206[.]254[.]253[.]254
21
222[.]254[.]253[.]254
21
182[.]254[.]253[.]254
21
190[.]254[.]253[.]254
21
184[.]254[.]253[.]254
21
83[.]133[.]123[.]20
16
130[.]185[.]108[.]132
9
68[.]43[.]104[.]31
9
143[.]106[.]5[.]242
8
69[.]73[.]14[.]56
8
65[.]25[.]8[.]238
7
174[.]50[.]46[.]17
7
50[.]4[.]85[.]69
7
198[.]91[.]176[.]53
7
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences j[.]maxmind[.]com
25
Files and or directories created Occurrences %System32%\config\AppEvent.Evt
25
%System32%\config\SysEvent.Evt
25
@
25
L
25
U
25
\$Recycle.Bin\S-1-5-18
25
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f
25
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f
25
n
25
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\@
25
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\n
25
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\@
25
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\n
25
\systemroot\assembly\GAC_32\Desktop.ini
25
\systemroot\assembly\GAC_64\Desktop.ini
25
%System32%\logfiles\scm\e22a8667-f75b-4ba9-ba46-067ed4429de8
25
%SystemRoot%\assembly\GAC_32\Desktop.ini
25
%SystemRoot%\assembly\GAC_64\Desktop.ini
25
\RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\@
25
\RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\n
25
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\@
25
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\n
25
%SystemRoot%\assembly\GAC\Desktop.ini
25
File Hashes
076954251dae552c90215a067aac007bf0ad679029fbb1b82a698d3de09e730008d7b4f347a16b79a62d245459cf9ab131c2df9fc1838e02802bfb9a6aca61121181cc286159851699c0e9c1390dfca7006c8d6d4c92108c34c082941f8481291ebcb2ef3bf9c2ed7375b7948e3a0dec8b0ff0be6e059e8922c4b1547bb52e1851fdc7e0e25ecf5d90ae3c95c1c16187f2dfda8491bdd0ab9ef1378c2150c76458d8666816aad58ab24ef3ec21216266f96a3173ee8e3113ba7844b70bdd8d0d7738ac853462f4e1ed29d9d3a55319be75b952feacbb68ce1ecc21e5e3c3351e813358d1ceafa1065613f42c7f78a432c4a72f267d7a0340090d7651785bc32e84b1758b4545308192ce7ef2ea44b808fdc208bfe0d119e46e3c9a2e2a492c359a93a769b759fd3e562b7dbd6c981e8c70942b5b9216589e57f11362af662fd0a00d8e76a72f9ff877de789727c1e95b356e4fd2191445fcfc039903bd3e88d1b7c20720b36e4c882c933ebb02793d40da26fa31a81b34b2ddc888c9ede3ae97ba957b265fd5c148f3bbb6f8bdbbdd1a4f0559d3dd9bf35d31f1d3a4d4f7a5efbf4e99cdf812b134bba7a56bca65f17916eb8fff3b9827f71c7de8d00bc37e4ec16a37d1a3f20d45179658151aacecec34708951c0de088d2038f7e5f9543f5ec74110419cab5a72722b929492a9df2a236d71053b5d2198f7da1084fa50b1c8ccdf01be4f8b32eb501ca6a521ae08275cc10391b0d653b4cfc2e0ddbd105df6d6a15841b35a33683e7d47e9237a5011a1d66d08900b9238e2352bcc4d361fe4dc2e56ce69095d93fb0a64f6c337572136dd90325908b1d273a6fda47a155047df6455604ab4475f164609b573cdc60bf0f0cc0df507a2101b764b15113193c6e30a7c87a93dcf2d1620e0e96fe8d4c419df59bc35ec00b5da835281546015ece52780b7e43765cff93f396b7a6721f5d41e30a169cc2beff2c0e33814a51594ea07d6c283c6230f60ba73481c6304b42435a129814bbe28ad22d413af23db02ea2aef3063a846658ab0e44cc2061117a9253e4d2f450f484660d671b162cce2ebe860b9c6041c0704c54da28f09d82f86fd6af142c3db365fb380c54a706aa6See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Packed.Blackshades-7002008-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DoNotAllowExceptions
15
<HKLM>\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile
15
<HKLM>\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
15
<HKCU>\Software\VB and VBA Program Settings\SrvID\ID
15
<HKCU>\SOFTWARE\VB and VBA Program Settings
15
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SrvID
15
<HKCU>\Software\VB and VBA Program Settings\INSTALL\DATE
15
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\Users\Administrator\AppData\Roaming\svchost.exe
15
<HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\policies\Explorer\run
15
<HKLM>\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components\{E94B570B-EA1A-7B9E-DDDE-F6ADFD39B3EB}
15
<HKCU>\SOFTWARE\Microsoft\Active Setup\Installed Components\{E94B570B-EA1A-7B9E-DDDE-F6ADFD39B3EB}
15
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: Manager
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Manager
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Manager
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{E94B570B-EA1A-7B9E-DDDE-F6ADFD39B3EB}
Value Name: StubPath
15
<HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{E94B570B-EA1A-7B9E-DDDE-F6ADFD39B3EB}
Value Name: StubPath
15
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID
Value Name: BRQY4LY7WY
15
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE
Value Name: BRQY4LY7WY
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\b426eed44205d22b31ddc9bba93777d66418725cc7389e33e94eaf82ed5a9eb5.exe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\93fdc3817676fae502836a274aa2444aac753f0295324c6ee1a6ba9456122323.exe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\f488d4abe7e53940581174ee39fa0bba3e101dcd1014e17b83eaf46ef524cd3a.exe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\c35c172e3ec61d1c9295eefc369e6364071b3e242bd0b7e3fe1d53e8598e5267.exe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\cbdc183665f526d08d30f2b9d58ecb9263d896ef89bf350354436e4ac9e084b1.exe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\TEMP\e514982ad751e1c4d206e29300afa21d80ec2d4ab9975ef1e4fe4a0282ad1d7a.exe
1
Mutexes Occurrences \BaseNamedObjects\BRQY4LY7WY
14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 212[.]117[.]50[.]228
14
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 8synnanonymous[.]no-ip[.]info
15
9synnanonymous[.]no-ip[.]info
15
3synnanonymous[.]no-ip[.]info
14
synnanonymous[.]no-ip[.]info
14
2synnanonymous[.]no-ip[.]info
14
4synnanonymous[.]no-ip[.]info
14
5synnanonymous[.]no-ip[.]info
14
7synnanonymous[.]no-ip[.]info
14
6synnanonymous[.]no-ip[.]info
14
1synnanonymous[.]no-ip[.]info
14
4synnanonymous[.]no-ip[.]info[.]example[.]org
1
1synnanonymous[.]no-ip[.]info[.]example[.]org
1
5synnanonymous[.]no-ip[.]info[.]example[.]org
1
7synnanonymous[.]no-ip[.]info[.]example[.]org
1
2synnanonymous[.]no-ip[.]info[.]example[.]org
1
synnanonymous[.]no-ip[.]info[.]example[.]org
1
6synnanonymous[.]no-ip[.]info[.]example[.]org
1
Files and or directories created Occurrences %APPDATA%\svchost.exe
15
%APPDATA%\sysinfo
15
%SystemRoot%\Temp\scs1.tmp
11
%SystemRoot%\Temp\scs2.tmp
11
%TEMP%\6JUNY.exe
1
%TEMP%\IC12M9RR.exe
1
%TEMP%\FJR17ZE.exe
1
%TEMP%\2A7HNDZJJJ1Q15.exe
1
%TEMP%\CVFV5OH.exe
1
%TEMP%\IH53AYOW.exe
1
%TEMP%\DWWWW46.exe
1
%TEMP%\MJXXI5LRM.exe
1
%TEMP%\YB5JQ8UA2LW2C.exe
1
%TEMP%\GGZD9TW0.exe
1
%TEMP%\WUHWJ6WIC603.exe
1
%TEMP%\04RP9MOSL3GEBE.exe
1
%TEMP%\Q9JX06QPQW7.exe
1
%TEMP%\EJ1ENZ6.exe
1
%TEMP%\EO4KXVJ.exe
1
%TEMP%\SBK2S44SS10.exe
1
%TEMP%\21T4BJS31T30T0.exe
1
%TEMP%\GBST7SCK.exe
1
%TEMP%\840AG7.exe
1
%TEMP%\XYNVF6Z8GZ52.exe
1
%TEMP%\DRSSEYO.exe
1
See JSON for more IOCs
File Hashes
89cec5949ed0d34c5e4acdff49fd25899aa99935fab559007b5e7f74eea114498eeb0e3d9cce9b3cd1d3cff8747905d083ae4e8c3139b8b48fbcee00289960b1923a9f3de724c4b19dfd4915d65cb7e185e2b6e3174a6d60839b456bc87f4aa693fdc3817676fae502836a274aa2444aac753f0295324c6ee1a6ba9456122323ae44c2d406dd0d76dfb26776ba7e085a34d57b1565ac81c78fa0f0d3c1de55dfaf5e730507faf8fa7d8f14fc2daa6d253a1a947e8227cb46fb0549cba5bd1483b426eed44205d22b31ddc9bba93777d66418725cc7389e33e94eaf82ed5a9eb5b8be6562a523ed101548cee88735f16778294ac8f8404d2fdf84c0353cf39987c35c172e3ec61d1c9295eefc369e6364071b3e242bd0b7e3fe1d53e8598e5267c4611e26199efce41b4a3daced46fbdc8e6f6cd19163f401334dc7d0086c900fcbdc183665f526d08d30f2b9d58ecb9263d896ef89bf350354436e4ac9e084b1e3306af770fd17f779fa3579656ffc1279e4c6a4ffb4fb317d5257070f25c39be514982ad751e1c4d206e29300afa21d80ec2d4ab9975ef1e4fe4a0282ad1d7af488d4abe7e53940581174ee39fa0bba3e101dcd1014e17b83eaf46ef524cd3affe5d67e939edc9ff1543f61e395451af223654dd14eb33b9d6a3b106ebfa5d0 Coverage
Screenshots of Detection AMP ThreatGrid
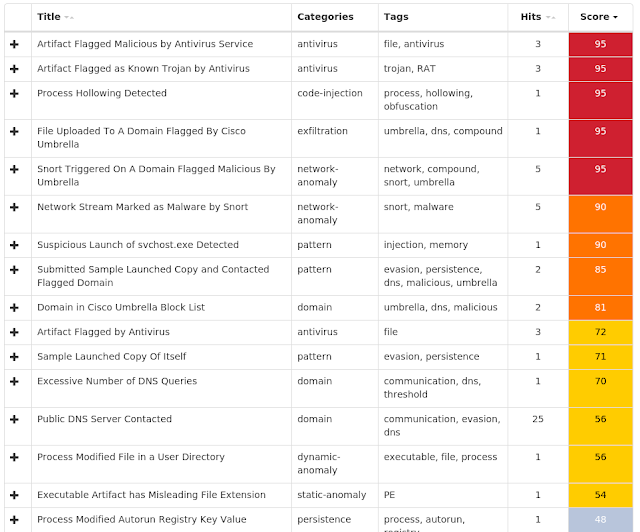
Win.Malware.Gamarue-7001972-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\software\Wow6432Node\microsoft\windows\currentversion\Policies\Explorer\Run
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: 36412
25
Mutexes Occurrences 2562100796
25
\BaseNamedObjects\1009299684
24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]95[.]103[.]184
25
71[.]209[.]210[.]64
25
71[.]209[.]248[.]201
25
52[.]249[.]24[.]103
7
104[.]45[.]185[.]175
6
40[.]91[.]94[.]203
5
52[.]230[.]217[.]195
4
20[.]186[.]50[.]83
4
40[.]81[.]11[.]194
4
Domain Names contacted by malware. Does not indicate maliciousness Occurrences amnsreiuojy[.]ru
25
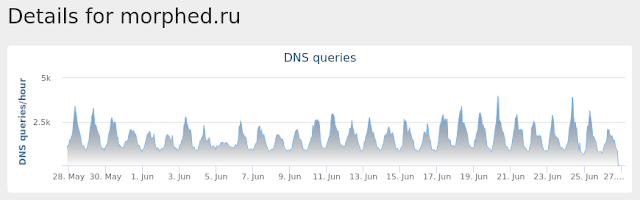
morphed[.]ru
25
www[.]update[.]microsoft[.]com[.]nsatc[.]net
24
Files and or directories created Occurrences %ProgramData%\Local Settings
25
%ProgramData%\Local Settings\Temp
25
%TEMP%\ccudefqw.com
2
%TEMP%\ccpaittr.scr
1
%TEMP%\ccvcbrqp.scr
1
%ProgramData%\Local Settings\Temp\ccaohaqb.scr
1
%ProgramData%\Local Settings\Temp\ccioodfy.pif
1
%ProgramData%\Local Settings\Temp\cccyokze.exe
1
%ProgramData%\Local Settings\Temp\ccfahy.exe
1
%ProgramData%\Local Settings\Temp\ccceirah.exe
1
%ProgramData%\Local Settings\Temp\cckyaew.com
1
%ProgramData%\Local Settings\Temp\ccauqse.scr
1
%ProgramData%\Local Settings\Temp\cclrzzfm.pif
1
%ProgramData%\Local Settings\Temp\ccokzu.com
1
%ProgramData%\Local Settings\Temp\ccablfq.scr
1
%ProgramData%\Local Settings\Temp\ccidop.cmd
1
%ProgramData%\Local Settings\Temp\cceazb.exe
1
%ProgramData%\Local Settings\Temp\ccraqi.exe
1
%ProgramData%\Local Settings\Temp\ccipousa.scr
1
%ProgramData%\Local Settings\Temp\ccacqvoes.pif
1
%ProgramData%\Local Settings\Temp\cciacuqeh.exe
1
%ProgramData%\Local Settings\Temp\ccyaykc.com
1
%ProgramData%\Local Settings\Temp\ccfayx.exe
1
%ProgramData%\Local Settings\Temp\cclygipzk.pif
1
%ProgramData%\Local Settings\Temp\ccuqhey.com
1
See JSON for more IOCs
File Hashes
88b83d7940351d57a7415257a5c764c250796735b84dac723227090cd158360490de0eb62d02f63a793ee83399dca3a0a26ef5778561127cdc3b7a12fdd14c209a557649beffab5fa440fe296b033302019f588fd2a2a55f96424247ab503d5a9dbfc5901b71f9329d1df2304c04a5dc23f841fbc23ab93f1b5162bbfbd17d19a5b91c4a675620e083a2469ec7e6835f4f0aeb5f8080fc86e06acf51c46af45fa6e33529f62b1a06b6ebb82d262b7c271db69436cd0147bbe78b668046f14c0bae51fd15c7b341e451607a0c451b8dc202b20a4f07f9698ae03db3fc10a9b7b8aeb375b2ec7bedb7cd130419135de45182b2472c854315142b237b7f458b5a3ab6e98593c8e5bcafaffc7d08f59f5dce7e31248f44901a5b96977e0a93a5cf9ebf272f51af40e07225731aa1ef5b558a92eca5a170b27d6830d096a10dbe5387c06e2844838c870cab80f096ec83674a94a3630232eae7fd7094b83c944aad1cc4968a5878f0ca3c5486b46b02ee12bb162070771acd199c1c0ae153a8b5f893c50836bcdb9bd118afa149c9fa69f522cb5cd73cfafca6e39dee9c0da9fc041bc543cbb30540aa3fb12bc61d2c389e0243e0cb71209e5737200403888c6c4170c5dc3ca6227c7cba83899d74f040de24a681a5e4ae14563a22e3575ca26782ddcd31b2573b597e43cfb6a5d83083457d01d260326d5ff50649cf7fb7facebc98d26052594814c437cdef01ba6ae431f6dddb03d0e091498b4a724f555b883796db657ca04f33f4a4923663d90e0b53bfab9616fea6c1b023170ac4eb2437f145e4030fe726df1c3b36b5819d8189eba5ceca082d6768349d97d0f9a89ec63d3ce6ba8ddeb72c376ac8bdb707fa1cf1d7afa3783f040e7ff186d3ddf2e73214abe70ed5d11dc4820b873be149df9ba68a884b03631e4b5c931698d4eb11e51213ecbce2866468b9d94c979a8b947d943682846c439f76b65880f6606bd6f8141eedf58c5f3dc245b7f12ecfb376f30e2be4dffaa8e4e7cfe519d521d12d70d80befc850ea39ff6f82b21d1a1036c065bd65ee251e6ef66134be6cf6aab3b27aa6f054a006bb89514411ae9e9611c9acf8979e9d3ab2365d059e61eb59f6c04440See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Trojan.Lokibot-7001391-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\VB and VBA Program Settings
13
<HKCU>\Software\VB and VBA Program Settings\yl6S81871663781\Cm4RF771904693
13
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\yl6S81871663781
13
<HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\YL6S81871663781\CM4RF771904693
Value Name: dvQ6A283412628
13
None
3
None
3
<HKLM>\http://tmjchange.com/Aw_/Panel/five/fre.php
2
Mutexes Occurrences 3749282D282E1E80C56CAE5A
13
\BaseNamedObjects\3BA87BBD1CC40F3583D46680
13
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 212[.]1[.]211[.]48
4
193[.]29[.]187[.]29
3
85[.]187[.]128[.]8
2
78[.]135[.]65[.]20
1
161[.]117[.]85[.]207
1
47[.]52[.]60[.]150
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences stcatherinescollegeug[.]com
4
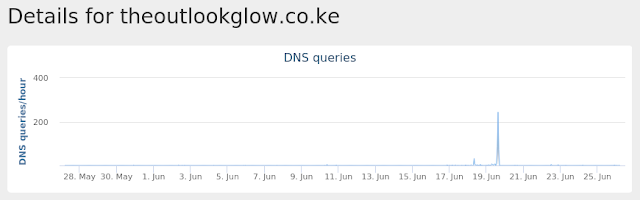
theoutlookglow[.]co[.]ke
3
matbin[.]com
2
api[.]w[.]org
1
tmjchange[.]com
1
bteenerji[.]com
1
Files and or directories created Occurrences %APPDATA%\D282E1\1E80C5.lck
13
%ProgramData%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
13
%LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
13
%APPDATA%\D282E1
13
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
13
%SystemRoot%\win.ini
13
%APPDATA%\D1CC40\0F3583.lck
13
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-1258710499-2222286471-4214075941-500\a18ca4003deb042bbee7a40f15e1970b_8f793a96-da80-4751-83f9-b23d8b735fb1
13
%APPDATA%\D1CC40\0F3583.hdb
11
%APPDATA%\D1CC40\0F3583.exe (copy)
4
%APPDATA%\Microsoft
1
%System32%\winevt\Logs\Microsoft-Windows-Resource-Exhaustion-Detector%4Operational.evtx
1
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500
1
File Hashes
0accf0fcb86d4fb3367ac3f7c70665a67ce8c83f564db604759cb3836b7f4ac818723bb19eebe8e4e6e01c1a652b85e7359aaadcbd0ec0c57d073426b26b036d1fd0f0bb055544d562e8f44675ff0e8205149af12ce68d4ab74e2800e84618d53f589cd475b1211115dd0acea7483819d6e6d78f3d9a9e9b389374c9afdbaad042af756837b1c4213219b7deda4c4432dff3b35e09483f63a3acc9211e08cae651d37cda477215a5da7872f8a178d82279f652023be289c70cd2ae983e6a24609c71815e65a5717ab07352f76960cebd49a16c376c0853d6ac7685fbfca8e38e9c9b0cfbd7a7b04f11611f60c7f2defdbe5db81e30a7cc01cfd123f0a6b97174b3c350aaeae1b1b066fd23002a3732130b3cfdf57d39a11f04112382a0594d7fd0fe5eee1cfe7b595c9d69362de5d4b823ef35933f5bfbe38b19d3488a040220d110960c25e29d8b687ef5000aa3761721af5510d1d7c8a72355485d82c5ce89d8c181a8be250796f8ad9583393b326c3d76f6e86a81c89225660cc7bed38e61ef69508adf938a083db4f91b3c40c67338623dc192983f03385a4510d3826e58 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Ponystealer-7001707-0 Indicators of Compromise Registry Keys Occurrences N/A
-
Mutexes Occurrences MUTEX_s2azEwonPXfon4JrAD
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]195[.]146[.]130
25
213[.]183[.]40[.]31
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ip-api[.]com
25
Files and or directories created Occurrences %System32%\Tasks\svchost
25
%APPDATA%\Logs
25
%APPDATA%\SubDir
25
%APPDATA%\Appelinstansen0.scr
25
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Appelinstansen0.vbe
25
%APPDATA%\SubDir\svchost.exe
25
%APPDATA%\Logs\06-26-2019
25
%HOMEPATH%\Start Menu\Programs\Startup\Appelinstansen0.vbe
24
File Hashes
176d0695e5f9bba1761b1288d40c70381a607474edefa4b96bfdae58097775a51f44ab287b2068f0cd7f179ae8a9fc749f54a4b75c02c1a19289820a4c5abfde20e65a6e2ef74c18fd2ec2c0df19c972cfe5271b53fbaca72f2b276e07f4c9b330ff31bdea7abfada4022dfc4a7ff283d8d280d1778229d994924df95edf6db23140b0c479fd50ccabe59d2a687bcd30c8d8c358e8097a3ae74b97510cc33c86321bc48ccceaa8fd3492c9713d457db00670f336e26857055e0e2c1009069032329d9e96a9dd0b45592e948cc691eee9a5b0d55f6129f25507e1f5fb40a3e02c36018abd322d8b0cf3a2e9264046a544b6ef58fe48ebd22f7df0db20b9a40ab645e8bc09f684e9d83abab87b8f8cc6d1a498968d0aca65f0ef668f8541f8a82647d1a8a70c173cba1dcc36e26bf38b206b738eb93493a0c9d9a3d09b235e97404dda62fdee6cdb3b592956fba1326f1b418c9d81ba2577a3ec00011fa17487e44df99361addca5c1c414fbddf48181ff65db954bd940fd0f6a1c87fa9961edf55143e2500885ee10fa43369052dcc02576210e566e7d26102307f554b348d23153a0d0a143bf9c4e6fa96873643d1c3d148a02180664bfe575ffaabccb9ac45c61b2848c773403ccee8ebaf8b3e72ded01728ea958f1461c72442dd84fcf29a765bb863b0e339f8f5d97e40f0ff2883bbb3d5fc9fe8b31c1d712384da7eb7aec6730bba3452b7b977186d80c34abd839dcaf731ff0b9befdb8323254c22c4fc2707d60c52242ddb3676a351faf3f96af40b547e548b32ef4c8f6751ab3cb5ffb7117534af19394d2d394c0d39005c2a06b97326b0e51f75ec53fab2f9b76c96371708c36ae65505b44dd9bdf9e7a01a3899eb5a68015c584474bc1888d2badfe7d51854e8e23a3458d9babe9f30395161256e614c0083e9adc9da561432f837f859c8e53eeba8e4ea3721673e7beefdfff3139fcc248b118a8a6c06c17594d03937ec4452c22ae6e45ea0b2d6d75442984dc2fcf2f087ba9c7d082639ee399519ca2236b18368afca7c75b8eebda5b64eb0d98f30351ad9eb49210a63dbb12d79df66dd5010ff85999d78be0345b529dc1ca197fb327b42e1d6d9593f708177bSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Upatre-6997681-0 Indicators of Compromise Registry Keys Occurrences N/A
-
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]239[.]157[.]210
9
23[.]253[.]126[.]58
7
Domain Names contacted by malware. Does not indicate maliciousness Occurrences rockthecasbah[.]eu
16
electriciansdublinireland[.]com
3
dcmsservices[.]com
3
Files and or directories created Occurrences %TEMP%\budha.exe
19
%SystemRoot%\SysWOW64\secur32.dll
14
%SystemRoot%\SysWOW64\api-ms-win-downlevel-advapi32-l2-1-0.dll
13
%SystemRoot%\SysWOW64\webio.dll
10
%SystemRoot%\SysWOW64\winhttp.dll
10
%SystemRoot%\SysWOW64\api-ms-win-downlevel-shlwapi-l2-1-0.dll
2
%SystemRoot%\SysWOW64\dnsapi.dll
1
File Hashes
05e4fbd158d8b712eb2293bd7a8586ff451d50a4336de23277837e94ba56e8e11dd50c279fa213938cc50b7e8d52b74598c86edcc33fdcbf7555eb529f35d7cb3198e6958489e008a41f72821b311d9e6611f33ce387f1114d6ad82bf85e25bd3d9fa6ff93769c89a6bd7cf0ab136eefe350231f433a16289f21edd1bb6adcb05d38cb5ad7bbee701da5987a516d446ec6664e91c6f24ca01a94b19a6ecc60dd65378641d80eeec0caf4a616d2526ecdf8013c521d3f80fabceb0bbd11588da8668c8706dd4a85a2a92a04e47034faf3627a68985c2017ad76c3261c38f98cab6b78d89491561dc032767651a7fd7e4fc365ddbb3f30a61247160c5ccac569826d61d43ea9fbb883c0eb2b18a4fdba086dc74946af12947f9cfdbddb0cbbaef66ee66ed2e08789b99387238c1a96306e8ee9d18c16e4a3e64258ed5e03da6634810e29feb32471fb3b003f719ecf4332ac155ad4ad915a7cf78499cdc05cb85b8a18b650ec0d0dfb38d93b0504ac777a794de50b83d702b381906dd2b91c20558e8214b61c2f9b5146541703c7c7fb176701f70bf7797d5be3202892268f817495c3d556aa3cc4ce02a64457e948434b66727b85379b7f575e45a936420833a4a0762390da8246251848bb0bddae2cfdea3b1511cba5b428b74073809c67c42da893d80022e464d48589d7a76f94108e42ac583c235ea3abd18cc6202fb15357cb9857baaba1d49fdff5a644acc7bd0781d69fb3d74b3d62a17e3e9e3cdbf1dae144eaf549ee6641f2689917057b6d8acf44179c0b7606961a157dd136edb715e333d13bb84a89a53c7f69ebb4c435558291ead7df9acdd17ff12f5017771ec3 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Virus.Ramnit-6997840-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusOverride
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallDisableNotify
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallOverride
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UacDisableNotify
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DoNotAllowExceptions
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: jfghdug_ooetvtgk
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: JudCsgdy
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{509D0DCA-5840-11E6-A51E-806E6F6E6963}
Value Name: Generation
5
<HKLM>\SYSTEM\CONTROLSET001\ENUM\PCIIDE\IDECHANNEL\4&A27250A&0&2
Value Name: CustomPropertyHwIdKey
5
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{509d0dca-5840-11e6-a51e-806e6f6e6963}
5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\{509D0DCA-5840-11E6-A51E-806E6F6E6963}\shell\Autoplay\DropTarget
5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\{509D0DCA-5840-11E6-A51E-806E6F6E6963}\shell
5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\{509D0DCA-5840-11E6-A51E-806E6F6E6963}\SHELL\Autoplay
5
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}
24
{79345B6A-421F-2958-EA08-07396ADB9E27}
24
\BaseNamedObjects\{137A1518-4964-635A-544B-7A4CB2C11D0D}
20
\BaseNamedObjects\{137A1A2C-4964-635A-544B-7A4CB2C11D0D}
20
\BaseNamedObjects\{137A2419-4964-635A-544B-7A4CB2C11D0D}
20
\BaseNamedObjects\{137A1A2D-4964-635A-544B-7A4CB2C11D0D}
20
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB3B51D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB9291D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB61D1D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB4BD1D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB5111D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB58D1D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB91D1D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB7391D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB7211D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB9411D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB3751D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CBA451D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB4711D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB9A51D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CBFD91D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CBA691D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB4911D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB9F51D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB9351D0D}
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]100[.]26[.]251
22
172[.]217[.]12[.]174
22
87[.]106[.]190[.]153
22
46[.]165[.]220[.]145
22
89[.]185[.]44[.]100
21
172[.]217[.]164[.]142
17
35[.]224[.]232[.]239
4
172[.]217[.]7[.]238
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wstujheiancyv[.]com
22
kbivgyaakcntdet[.]com
22
yrkbpnnlxrxrbpett[.]com
22
qislvfqqp[.]com
22
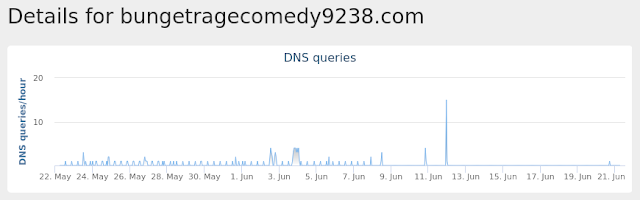
bungetragecomedy9238[.]com
22
oeuwldhkrnvxg[.]com
22
kbodfwsbgfmoneuoj[.]com
22
wdgqvaya[.]com
22
ypwosgnjytynbqin[.]com
22
jlaabpmergjoflssyg[.]com
22
ausprcogpngdpkaf[.]com
22
fmsqakcxgr[.]com
22
OAWVUYCOY[.]COM
21
GFARONVW[.]COM
21
dvwtcefqgfnixlrdb[.]com
21
citnngljfbhbqtlqlrn[.]com
21
Files and or directories created Occurrences \Boot\BCD
24
\Boot\BCD.LOG
24
%LOCALAPPDATA%\Microsoft\Windows\UsrClass.dat
24
%LOCALAPPDATA%\Microsoft\Windows\UsrClass.dat.LOG1
24
%HOMEPATH%\NTUSER.DAT
24
%HOMEPATH%\ntuser.dat.LOG1
24
%LOCALAPPDATA%\bolpidti
24
%LOCALAPPDATA%\bolpidti\judcsgdy.exe
24
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe
24
%SystemRoot%\bootstat.dat
24
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\e6944fe95a45c918aa3f2953cd29d8f6_d19ab989-a35f-4710-83df-7b2db7efe7c5
24
%TEMP%\yowhywvr.exe
21
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-1258710499-2222286471-4214075941-500\e6944fe95a45c918aa3f2953cd29d8f6_8f793a96-da80-4751-83f9-b23d8b735fb1
21
%TEMP%\guewwukj.exe
20
%HOMEPATH%\Local Settings\Application Data\hmqphkgx\pseqpmjy.exe
20
%HOMEPATH%\Local Settings\Application Data\jpnfmrvn.log
20
%HOMEPATH%\Start Menu\Programs\Startup\pseqpmjy.exe
20
%ProgramData%\wtvakgao.log
20
\nBm4h9I
4
nBm4h9I
4
\TEMP\nBm4h9I
4
oTKCR23
3
\TEMP\oTKCR23
3
\oTKCR23
3
\Device\HarddiskVolume3
2
See JSON for more IOCs
File Hashes
020eb6da1196582c52e823a5bb222b4bfeff859c1007404e146694be17b79c0a15d31a8b30de2cc620bfaee8377fb8c2542e1fc8b3ad3ab8a19ee6d12dd0d7e8227a7a24686b80036eb0bbb6d42dc8f22c629889284dbc086c43a375b8aa4bcc2904815a1c7eccacf480673b7deb8e4f5fd0a6bd4dcc69fc2ef42e9059595b732e324aa5b5c88f484ec89457a3d586ee17291249a053342252327876322f7ea538dbc28e1a410c4d5b7740c2c5ad12abc72c5c4eb26961365313edee3808dc2d3e939542ad68cf7d18c4638b4ebc8f721f5d1357f8fa6068f03a5dd2f1c15a394052f05c6345ef6306d1122f478d241ce395b6abec43af1230ad110a1fde53334ce65aba2b6f06cb625374eb55eab94391f44f98acae5e62d38676312fb9fd235e9441f982564e65ec1b0ddde1a164ba5d72ed18d93c28bc91d909f31134fc6c6503c9a444c480014378fc6dcc0d2bade62d0ee0a6dc9af2f8fa4e4261e5f7c16d39754a92431ff4462ef5f4355b8f06aa371be911159507b774ee3dbfdf4bc28b80167746d58c26a133e5f30ab82d4c295b6c2332d72b25dafedf61243e6a5b90d91197518a0e66012b8dfa52583f49968736187018ae7c821d0014184be0b59a60fb85f32d6c9adfeaa27e2cd07752109aeaab22f9745f74de26f0eeda3cf29e65eb141fd680acb220134c3ba615c83cc4a8d4368f0d5e659b17d5fdf3c102a847ef0c0091cc8c75336551dc64bd02e21f2bcc843df68bcaeb1cfd7051e0f0d58f75aa97d0bb3e3d8933f6b568bd28775f7a315d1d9f4e86fa233b3abbf32adab8c5868ad964e90df10ea1470f660076ec93532a0d5bb2e31310669c799e05e7c461cba22f92a1082995142d9371d062a1788f587075c6ec3358a03f32dba9e8e5366efa6d00f9a21620a3f74d65ee9eb68bced11461886c789392627ef1cff0827924286a0aaf731f2c0b8734798c42601250c12364878661d9cc8ccdc47efad70a7a283976a5409bf17038c091947bfdaa45e17e83302a1fc843c5f75f27fb94f2d201e2eeaae73c43f6299225eb31d888018d2931d7385023385f455dab Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Dropper.Kovter-6998646-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: internat.exe
10
<HKCU>\SOFTWARE\07771b47
10
<HKLM>\SOFTWARE\WOW6432NODE\07771b47
10
<HKLM>\SOFTWARE\WOW6432NODE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
10
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: explorer.exe
10
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: iexplore.exe
10
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: explorer.exe
10
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: iexplore.exe
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: 956299e5
10
<HKCU>\SOFTWARE\07771B47
Value Name: 956299e5
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: 18f8f764
10
<HKCU>\SOFTWARE\07771B47
Value Name: 18f8f764
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: 8de2c2e8
10
<HKCU>\SOFTWARE\07771B47
Value Name: 8de2c2e8
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting
10
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: dllhost.exe
10
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: dllhost.exe
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: 412841e8
10
<HKCU>\SOFTWARE\07771B47
Value Name: 412841e8
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
10
<HKCU>\SOFTWARE\07771B47
Value Name: e1616c62
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: e1616c62
10
<HKCU>\SOFTWARE\07771B47
Value Name: 921a72e2
10
<HKLM>\SOFTWARE\WOW6432NODE\07771B47
Value Name: 921a72e2
10
Mutexes Occurrences C77D0F25
10
Global\07771b47
10
244F2418
10
906A2669
10
\BaseNamedObjects\A146B82F
9
\BaseNamedObjects\20D5C1BD
9
\BaseNamedObjects\Global\7df04eda
9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 96[.]17[.]191[.]121
10
23[.]218[.]40[.]161
9
23[.]196[.]65[.]193
9
104[.]215[.]148[.]63
4
40[.]113[.]200[.]201
2
40[.]76[.]4[.]15
1
110[.]19[.]64[.]9
1
46[.]17[.]33[.]57
1
192[.]79[.]201[.]18
1
110[.]165[.]194[.]202
1
75[.]129[.]131[.]245
1
14[.]252[.]183[.]4
1
43[.]234[.]203[.]246
1
51[.]202[.]78[.]227
1
64[.]43[.]110[.]160
1
102[.]186[.]146[.]107
1
220[.]120[.]41[.]19
1
105[.]10[.]131[.]34
1
40[.]39[.]16[.]104
1
33[.]239[.]167[.]136
1
79[.]87[.]240[.]45
1
101[.]144[.]113[.]42
1
176[.]37[.]192[.]106
1
64[.]128[.]116[.]36
1
171[.]137[.]160[.]184
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fpdownload[.]macromedia[.]com
10
e13678[.]dspb[.]akamaiedge[.]net
9
clipsource[.]com
1
Files and or directories created Occurrences %TEMP%\install_flash_player_18_active_x.exe
10
File Hashes
0405d046f18b12fa283aae775dfc86b7f37b3c9187c478b408b1d1df56e4946e0f7d26164358095c5e09500102a4fffd4bcabd86f8a8da20ce6d4b1257c6cfe73579e91f3bbe9c7f0930e1ae804ed334d7cc7e5edea3477cc1d725cfc9721e6a4ae693d59ba77b5de104649fa4b0fbfcd4863910253219358e0b60534373d73662190bdab2b81d6af487289107c0ae880b6f4ac005c81feeefad042fd5cdd86463ab82c5bb8e3105847973879c43fc754c886bf713a3d2377efd2832ee103e997fc0a306813ca939ecb32640b534a3686cad7146930edd8f0b947b490e97641999f3b3710f26b15d3b9e1363bd12de968651c4a6266838a0d51212dcfd80898ab2859d76620c0dabaed848832f08be73e78cd4deddf9bf34c80ddd243c887f87f3f4621e74ef38c9c05f34fb33fe092db859f16efbff734022617ad72ed2ddf0 Coverage
Screenshots of Detection AMP ThreatGrid
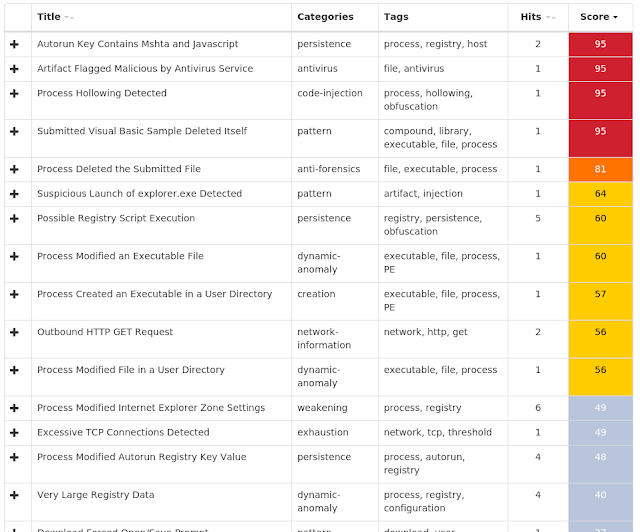
Win.Dropper.Gh0stRAT-7003005-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CurrentControlSet\Services\BITS
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
Value Name: InitTime
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
Value Name: Group
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
Value Name: Version
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\Stuvwx Abcdefgh Jkl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DirectX jrq
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: Description
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: Description
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: SVCSHOST
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIRECTX JRQ
Value Name: ImagePath
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\STUVWX ABCDEFGH JKL
Value Name: ImagePath
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NQUFHIVF
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NQUFHIVF
Value Name: ObjectName
1
Mutexes Occurrences C:\Windows\SysWOW64\hevtam.exe
3
wenxiaoyan.3322.org
2
xiaocheng780.3322.org
2
sjj184901537.wicp.net
2
a009188.f3322.org
2
C:\progra~1\Common Files\svchost.exe
2
tcjzzf.f3322.org
2
xinshoutouliezhe.vicp.net
1
\BaseNamedObjects\944413269.3322.org
1
104.194.20.12
1
wytcn.com
1
liwtao.f3322.org
1
182.92.223.28
1
C:\Windows\SysWOW64\akqukc.exe
1
C:\Windows\SysWOW64\lijlio.exe
1
103.40.100.191
1
C:\Windows\SysWOW64\wgccga.exe
1
C:\Windows\SysWOW64\eoemoe.exe
1
C:\Windows\SysWOW64\scokyy.exe
1
mama520.f3322.org
1
108.171.243.19
1
23.94.244.17
1
23.94.244.18
1
C:\progra~1\Common Files\SVCH0ST.EXE
1
125.46.39.66
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 61[.]142[.]176[.]23
3
123[.]249[.]34[.]172
2
125[.]109[.]109[.]30
2
27[.]54[.]252[.]252
2
174[.]139[.]226[.]178
1
42[.]236[.]77[.]185
1
104[.]194[.]20[.]12
1
182[.]92[.]223[.]28
1
103[.]40[.]100[.]191
1
198[.]13[.]108[.]245
1
108[.]171[.]243[.]19
1
23[.]94[.]244[.]17
1
23[.]94[.]244[.]18
1
125[.]46[.]39[.]66
1
154[.]95[.]54[.]46
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences sjj184901537[.]wicp[.]net
2
wenxiaoyan[.]3322[.]org
2
xiaocheng780[.]3322[.]org
2
tcjzzf[.]f3322[.]org
2
a009188[.]f3322[.]org
2
xinshoutouliezhe[.]vicp[.]net
1
944413269[.]3322[.]org
1
wytcn[.]com
1
liwtao[.]f3322[.]org
1
lbaabb123[.]f3322[.]org
1
sjj184901537[.]xicp[.]net
1
mama520[.]f3322[.]org
1
westexpired[.]dopa[.]com
1
Files and or directories created Occurrences %SystemRoot%\SysWOW64\hevtam.exe
3
%System32%\tgvbgq.exe
2
%CommonProgramFiles%\svchost.exe
2
%System32%\ggiogq.exe
1
%System32%\jwzvwy.exe
1
%System32%\hufzuk.exe
1
%System32%\kkwgks.exe
1
%SystemRoot%\SysWOW64\totbau.exe
1
%System32%\ycuuyi.exe
1
%SystemRoot%\SysWOW64\akqukc.exe
1
%SystemRoot%\SysWOW64\lijlio.exe
1
%SystemRoot%\SysWOW64\wgccga.exe
1
%SystemRoot%\SysWOW64\eoemoe.exe
1
%SystemRoot%\SysWOW64\scokyy.exe
1
%CommonProgramFiles%\SVCH0ST.EXE
1
%SystemRoot%\SysWOW64\wgccca.exe
1
%System32%\dqrhqi.exe
1
File Hashes
0403e7f8d9892722756918c24801cad3d661815f5c306c8c5391f1ab8a630ec404d45c30a242afecf9a8d9e6cbf583029f794f13b22c22108cc0f5a6d79aff1f0a18fd63c2489ee27c7f4802ef60011cf270fd035ca3153ff0587fb201683c070b88e2e952e057d1e67eb9aced20ed79cdb4ec00b4de5c306394d5996f6c1cb30d9854cb571a8ef781ef4ebfd82bd461b47273fb637e80b8863388eaa7325c3719268cf4f3d3e6f37cea8d3eb6c67bd4f9abbe0dee6cba4c5ee623904e7815743464e90e1b93df7d1bf837fa799be811665b1d12d5320a2419d5cdb354cfe6c8429cca47e464202273ccf9a33f2e08aa366fe1bb59cee9ebbb1735b401b72be34675518e7355804e0134dbb26889ae2fa0e3857110645076082087fd0c9d75174f64ef87e5b5094f0f3b501f46f8029f0ddb47054a2d1810b50b149d6f179ae64fcfea79eaf6fcb55cf0fdf5feab7217f949af742f52a6e12ed8e6590b19494b51b8854b75c9c928ef77a2d76ecdab13ff6aab4399960005acd4a9dd8ed4df18526e31726b1a3109312721f5d210db6e384a799951fbb9b2170a34672cd15f18553d09ad92a5abcb4987335fba0ca0fda30ceef2c33e8f72747dcc1de969ae325ba1e4767e5e9f9d0c10d64d5399e13f83e727b96d68c68413a40773f11d16905c2d5a7e9fe0721c8c00bc61b8b32db9bdfdd874cf2cdc3542c719b289535f875c9a6cded235870fc95ca7e3a2aea98d642da688a7fdef40391bcd52435723ca5fb34b0666b3e21e5835c2f7d05ccab2b076e462c6982175eb638d9c08b9f13864f8a4a03ed33a6ce0b19e52411ecb58a834840db6f1fbaa46ee815a667cd362681e1d899c9342f6cf5a2600b1af723f1ea0216467050f023ed7f33da078ec726cf9e25edd01d958328923af88edfc9224d26e1ce72a677f6f0f4c64cff1160070bb286abdffddf3137e5f8c2f3fde94fbb3c58dacc9bd7ac5c2e816829429a6712e9f3f962722317243c52aec1edeaecc59d53180873b67b108eeacc27ba84c7433255788cf4f6761369a89313ed5786b32049c7bd48c50fb8f62328744f5aa77e44b92cd3403248e82b31b16efa7b4114e872c5c1206600c2222d8020cc2b7See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
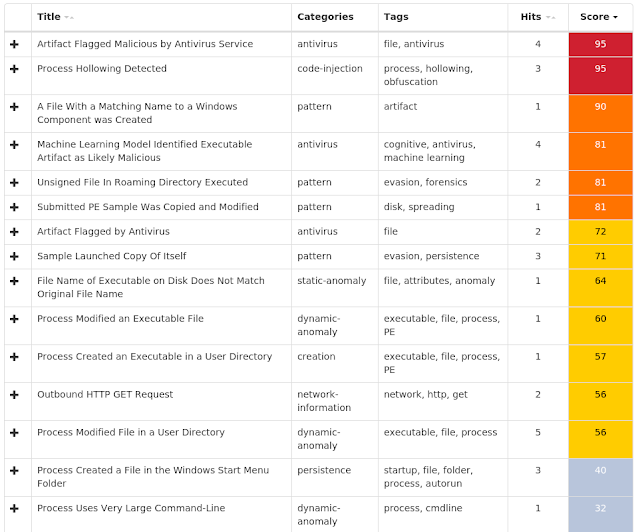
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Atom Bombing code injection technique detected (10876)Madshi injection detected (1932)Trickbot malware detected (1694)Process hollowing detected (941)Kovter injection detected (727)Dealply adware detected (605)Gamarue malware detected (231)PowerShell file-less infection detected (61)Fusion adware detected (45)Excessively long PowerShell command detected (43)