Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Aug. 30 and Sept. 6. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
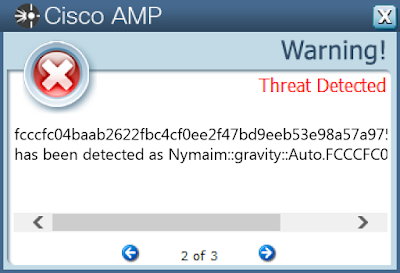
Threat Name Type Description Win.Malware.Nymaim-7149347-1
Malware
Nymaim is malware that can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control (C2) domains to connect to additional payloads.
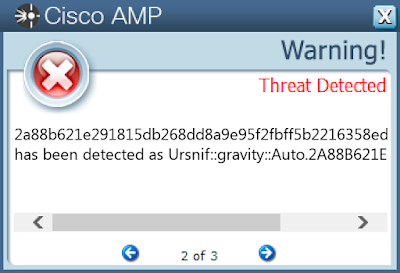
Win.Malware.Ursnif-7149254-1
Malware
Ursnif is used to steal sensitive information from an infected host and can also act as a malware downloader. It is commonly spread through malicious emails or exploit kits.
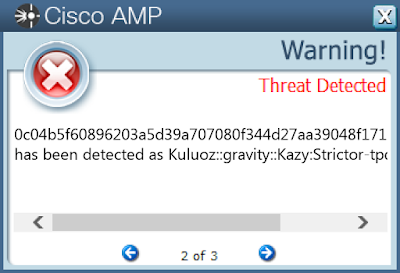
Win.Malware.Kuluoz-7149209-1
Malware
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
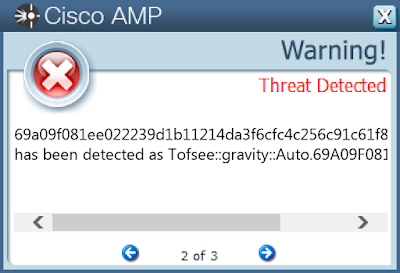
Win.Dropper.Tofsee-7147648-0
Dropper
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities, such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
Win.Trojan.Dorkbot-7146944-0
Trojan
Dorkbot is a worm that spreads itself through social networking sites and messaging apps. Once installed, the infected computer becomes part of a botnet, allowing the controller to control the machine remotely.
Win.Ransomware.Gandcrab-7145847-0
Ransomware
GandCrab is ransomware that encrypts documents, photos, databases and other important files typically using the file extension ".GDCB," ".CRAB" or ".KRAB." GandCrab is spread through both traditional spam campaigns, as well as multiple exploit kits, including Rig and GrandSoft.
Win.Malware.Phorpiex-7145044-1
Malware
Phorpiex is a trojan and worm that infects machines to deliver follow-on malware. Phorpiex has been known to drop a wide range of payloads, including malware that sends spam emails, ransomware and cryptocurrency miners.
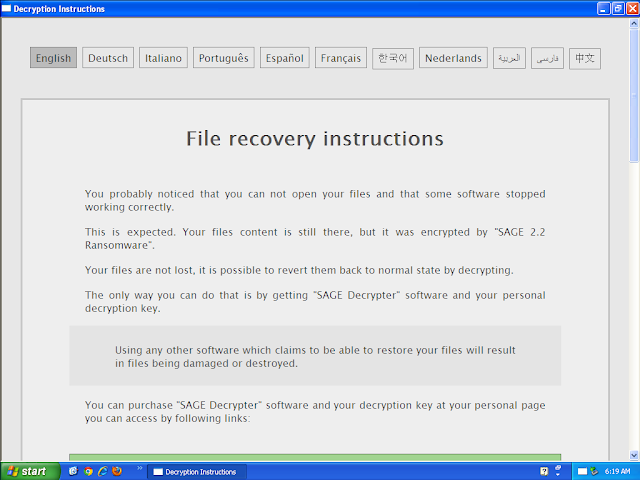
Win.Ransomware.Sage-7144073-1
Ransomware
Sage ransomware encrypts files and then demands a payment for the files to be recovered. Sage typically spreads via malicious email attachments, and the encrypted file extensions vary.
Threat Breakdown Win.Malware.Nymaim-7149347-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\GOCFK
16
<HKCU>\SOFTWARE\MICROSOFT\KPQL
16
<HKCU>\SOFTWARE\MICROSOFT\GOCFK
Value Name: mbijg
16
<HKCU>\SOFTWARE\MICROSOFT\KPQL
Value Name: efp
16
Mutexes Occurrences Local\{369514D7-C789-5986-2D19-AB81D1DD3BA1}
16
Local\{D0BDC0D1-57A4-C2CF-6C93-0085B58FFA2A}
16
Local\{D8E7AB94-6F65-71DE-8DA1-FE621BE2E606}
16
Local\{F04311D2-A565-19AE-AB73-281BA7FE97B5}
16
Local\{F6F578C7-92FE-B7B1-40CF-049F3710A368}
16
Local\{0F53A50D-AEA8-402A-580B-3C32A490301E}
16
Local\{42FDAA48-39A4-4464-9CC4-6F1A48111B12}
16
Domain Names contacted by malware. Does not indicate maliciousness Occurrences gokxyba[.]net
15
bkigzfz[.]com
15
UPOEPRPAA[.]NET
15
WJXVRSFRYJQ[.]PW
15
gfjtjjgx[.]pw
15
YZOBVXEI[.]NET
15
DZLYHSMMLUL[.]PW
15
EMKWQU[.]PW
15
TQTZRZKIIID[.]COM
15
MJWHLRF[.]NET
15
tbblpqejav[.]pw
13
fseqigbfr[.]in
13
pscjvmzmy[.]in
13
scvkmktqksu[.]pw
13
ibypya[.]in
13
hkfyto[.]pw
13
qvrghscpr[.]in
13
sbuhudow[.]pw
13
yqofd[.]in
13
luwjudefo[.]net
13
uqzbwfz[.]net
13
oangztra[.]com
13
qanefmpvo[.]net
13
chtugnzdw[.]com
13
jcggrdthx[.]net
13
*See JSON for more IOCs
Files and or directories created Occurrences %ProgramData%\ph
16
%ProgramData%\ph\eqdw.dbc
16
%ProgramData%\ph\fktiipx.ftf
16
%TEMP%\gocf.ksv
16
%TEMP%\kpqlnn.iuy
16
%TEMP%\fro.dfx
13
%TEMP%\npsosm.pan
13
\Documents and Settings\All Users\pxs\dvf.evp
13
\Documents and Settings\All Users\pxs\pil.ohu
13
File Hashes 037d05e6a51414ff22c6f27f5758bab12a237fae5a8da61b3d9579e77cf68cc9
04f91d0532ceec2b0455ab9745dff5b423f34e8f32cee261db68ad28db024a08
123573d7840dccbc368911be620c2c839fcb81642abeaed5a67316c003bb67a4
2f485d4cf77a8079c75d584aed08d769b864ba76373250e583b7268a444fc2b4
6f7ef5eaa16f360e0ce570fe2196bc91ee133cb954a1d62ff9d4a72a1f0e2c45
78838c78442dd1afb4d1806e0eb81ddb4931a1f51dd021a24109a461105232c0
79158026c4d06723c530813c1e2a90024e88dddac9aa84cf0314f004eb49062c
792daabd16b1ceb49a85bccc8cdd8fcf8c21a9a0df3eb909e06df9cd81f786c7
7a06a8e0fc5ee2416369f3638bb42a7b4994fd2e74b89b6a533636de6f8a4a86
7c8ff85a4e95716c990a60b5f5a5992c0fe530e7a366f80bafbc6621ffff0fbb
ac1887855401066432456e2890c97b7b303e08b7b65e20a8fd004052175a5b18
c19036fc9959e2003d48bb68b2cd6c95a6423b6fa7a434c7ce96d77d69c6e532
c1d686b25508f66fd32aaaeb1caccf0fd233f5303418a3658088205f543182a3
ca3a1e4d93207501cd2911bf88a92431ec5ef877b7b1a7200072c976339a07ae
fc5b7ae3747c98d4658a0599130d5374c71bf2aa88483fab28d2e643e6283164
fcccfc04baab2622fbc4cf0ee2f47bd9eeb53e98a57a9754286805c0580ff79fCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
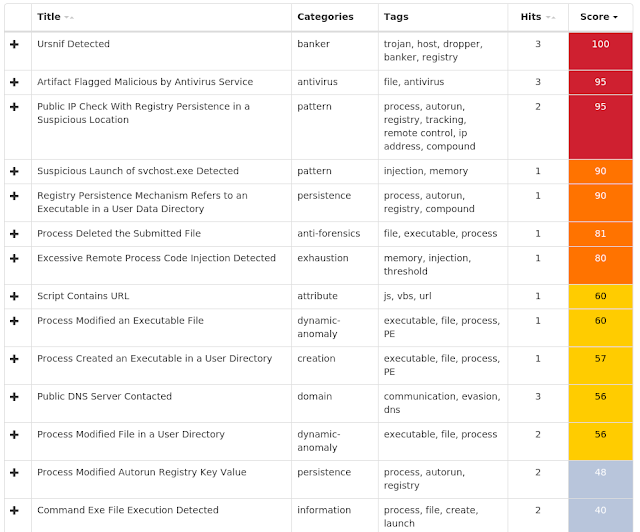
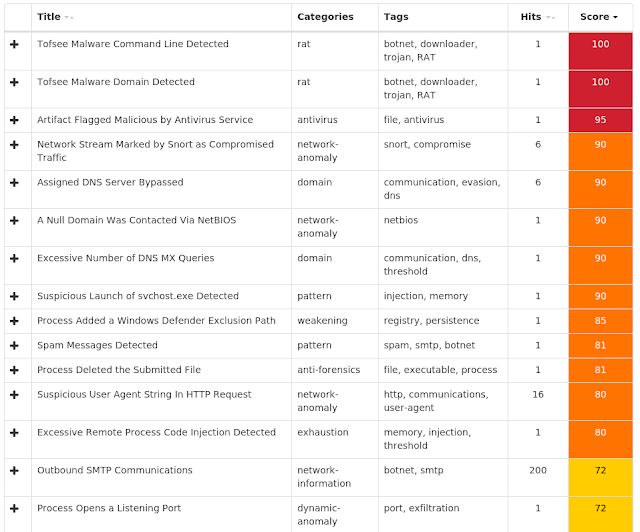
Screenshots of Detection AMP ThreatGrid Umbrella Win.Malware.Ursnif-7149254-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: api-PQEC
10
<HKCU>\SOFTWARE\MICROSOFT\IAM
Value Name: Server ID
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
10
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: Client
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: {F50EA47E-D053-EF14-82F9-0493D63D7877}
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: {6A4DAFE8-C11D-2C5C-9B3E-8520FF528954}
10
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
10
Mutexes Occurrences Local\{57025AD2-CABB-A1F8-8C7B-9E6580DFB269}
10
Local\{7FD07DA6-D223-0971-D423-264D4807BAD1}
10
Local\{B1443895-5CF6-0B1E-EE75-506F02798413}
10
{A7AAF118-DA27-71D5-1CCB-AE35102FC239}
10
{C3863B40-467D-ED33-68A7-DA711CCBAE35}
10
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]67[.]222[.]222
10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences resolver1[.]opendns[.]com
10
222[.]222[.]67[.]208[.]in-addr[.]arpa
10
myip[.]opendns[.]com
10
jiauwnehbtqiwjeqwe[.]net
10
Files and or directories created Occurrences \{4BC230AC-2EB3-B560-90AF-42B9C45396FD}
10
%APPDATA%\Microsoft\Dmlogpui
10
%APPDATA%\Microsoft\Dmlogpui\datat3hc.exe
10
%TEMP%\<random, matching [A-F0-9]{4}>.bi1
9
%TEMP%\8A4.bi1
1
File Hashes 055f5a38fca8e55adb9e46bfc7dfe3b9094ad659bb473553881b0c72cc580120
2a88b621e291815db268dd8a9e95f2fbff5b2216358ed24eab198917fe65742b
3b306bbe5aaabdd008259ac755b50ac5c53144bd2f79b90d1f29c3c576172661
7cbc76561f75ead55fd3a776ba7b44d253783da767f4fb20b09616fa1039ac8b
b2939cb18525d202ec9af8629b4ba0aaaab24e7b81bd5abd00fbb69d34a1dea5
c23a3dcbe61fb4877322c6f0e24476d9fd433ca013f62cc9f42a9cb62acf02f1
cd83db4c5a03f1fae1fa4183e70ea6a6acfc0657e45fbecabc48adfb281f39fe
cf10ee7467a9ee13fe44e9ea9c2833dde4c5270909a75c5fd8b3ec3627a17af5
d257e0242bc63f343d6712fe05e5b8c9d9be84645e5a2063a1d12820aae450fa
fb1eac4151a47e030a0d372c40fc3c70cd4ba76bc40571fa69d60f398196726aCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
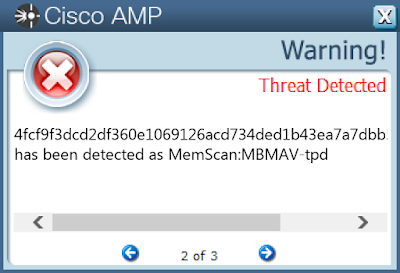
Screenshots of Detection AMP ThreatGrid Win.Malware.Kuluoz-7149209-1 Indicators of Compromise Mutexes Occurrences 2GVWNQJz1
188
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 87[.]106[.]4[.]78
129
95[.]141[.]29[.]195
128
50[.]57[.]99[.]160
126
188[.]116[.]23[.]96
119
178[.]33[.]227[.]11
114
91[.]227[.]26[.]178
114
78[.]46[.]92[.]70
110
91[.]220[.]215[.]29
105
Files and or directories created Occurrences %LOCALAPPDATA%\etxaxetj.exe
1
%LOCALAPPDATA%\eopjtjwg.exe
1
%LOCALAPPDATA%\tfugpetb.exe
1
%LOCALAPPDATA%\tjdsucos.exe
1
%LOCALAPPDATA%\uxfuuarq.exe
1
%LOCALAPPDATA%\lspsvmef.exe
1
%LOCALAPPDATA%\addakgil.exe
1
%LOCALAPPDATA%\gdsfuent.exe
1
%LOCALAPPDATA%\kesjxiuw.exe
1
%LOCALAPPDATA%\rvdhhicw.exe
1
%LOCALAPPDATA%\odjotitr.exe
1
%LOCALAPPDATA%\apferdrh.exe
1
%LOCALAPPDATA%\mxdmpmxp.exe
1
%LOCALAPPDATA%\jujldfjk.exe
1
%LOCALAPPDATA%\lwmwmfsv.exe
1
%LOCALAPPDATA%\sauuvxpt.exe
1
%LOCALAPPDATA%\rvrsnrcv.exe
1
%LOCALAPPDATA%\libwmqqa.exe
1
%LOCALAPPDATA%\sfvadtvv.exe
1
%LOCALAPPDATA%\cswmofrn.exe
1
%LOCALAPPDATA%\hngjmrve.exe
1
%LOCALAPPDATA%\jkqgumia.exe
1
%LOCALAPPDATA%\cqeelolf.exe
1
%LOCALAPPDATA%\ipatebes.exe
1
%LOCALAPPDATA%\xmcejvax.exe
1
*See JSON for more IOCs
File Hashes 01412a2d6877375f88d6b502600e45a26197396a1f0b019d8d10437729f52257
02205537e0ac5c8b8b66f53e8d2993b706a8f7fa5757346a7312db646a471143
0364c9b75b03b9ed56059c9bea7f8a8f81f13d2cfc061c0b6e13525dcc3bd7dd
0383d381bf8f010ebfe0215528a7289429052487a2fe90ce35eae0f7f11e1fea
05fa1a824e573e2db9dfbf4e3358a5f2c88956ae6a669f6336c42812a67a524f
06de3f442bfeee18831cebef86194b8166a188af312b739fb628c203e4d5f2ea
078e7fba23d21250e959935ba3ab9559dddad02240443543616eab37547ddd86
07b13ab67c36b30dc081deebdd0bc5a9319a3ddf05e17a5d4552c16ded433d4e
087d4788799c0e935673ef2572bebf8f86ca61e8966b2404e20432a417e73894
0909060506cdf2d77307b2ae36380fc7f85de0a9c1c103ca629d3089ba507df3
091b1cb41a31ffd75781295ec748bb6b82bc6624dd7853405304a08a322c51ec
0a482d15c908dd7b8936e0900fcabef622708b79cd2020c730376aec9c7ca388
0c04b5f60896203a5d39a707080f344d27aa39048f171e9284d6d8b665e226e5
0c86168150197d12329c57ad9c8d616a15f285483ba3cec4a9bb4ede46e4d234
0ce022144a2b3d712579d8a63c9c73109ac74eff4ad68f1b6fbd8f593c706aa6
0ce6ae758bdc6f4c44b249f4ecf327f5a00a238ebed3bbe8b06f317b91335f1c
0d3ce20b680e2dbf203a10e9c8ed97c4f7006be9b3a6fddbeb443937480d98b5
0de776cb80503f7daa3effefbb2739f9c927f028df4445fa051cb33377de359f
109a6498f4d7b51f0ede104d4bd8f78782913d641147930e07c6dc236dc04a94
126266edb2a41407ba26f72e127430dd5932b07ab2e312dfd09285bc9f5db40b
12e80c62f20986a8abe96df7be0c1b91d5fd32bef9781bf669d7a5d538af778c
13705e3f984dc79824e22fa9349c3704dbe5d67a606f59029622887379eeb302
14e13631f15fc311ef20c9e87ef28675dc14cd83ed871f44266811e103b45284
15381012927b9852633c0943aab2d0522dbf3d3d0a326e4b0e18e21ba29f6065
168c0dd6882307664579943b5786594e94435ccab43618aee5b04d6f974bda2c*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
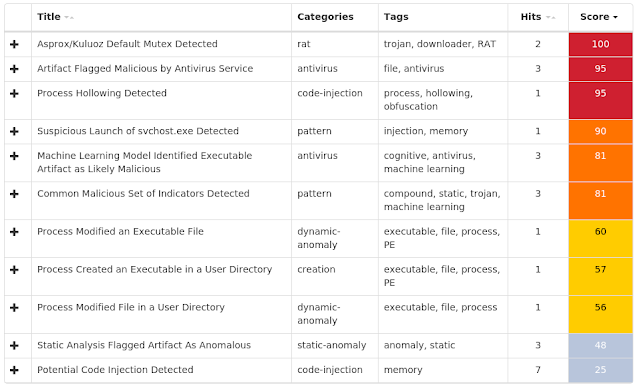
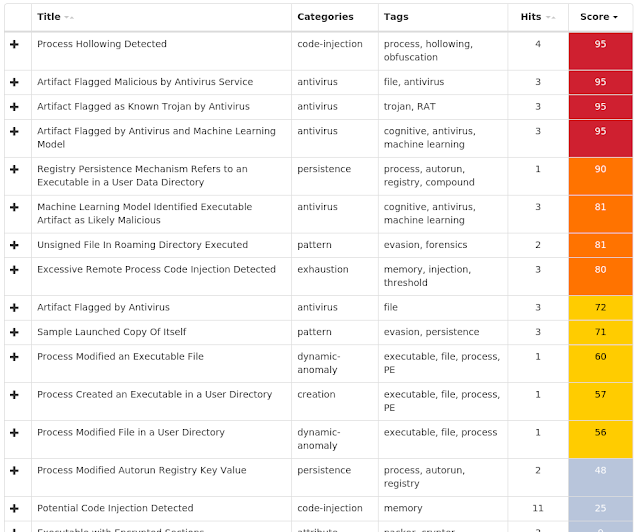
Screenshots of Detection AMP ThreatGrid Win.Dropper.Tofsee-7147648-0 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
13
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
13
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
13
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
12
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
7
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\jcqwvdjy
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\unbhgouj
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\nguazhnc
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\zsgmltzo
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\yrflksyn
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\dwkqpxds
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\rkyedlrg
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\vocihpvk
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\fymsrzfu
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\mftzygmb
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\xqekjrxm
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
13
69[.]55[.]5[.]250
13
172[.]217[.]3[.]100
13
46[.]4[.]52[.]109
13
176[.]111[.]49[.]43
13
85[.]25[.]119[.]25
13
144[.]76[.]199[.]2
13
144[.]76[.]199[.]43
13
43[.]231[.]4[.]7
13
192[.]0[.]47[.]59
13
95[.]181[.]178[.]17
13
172[.]217[.]197[.]27
13
67[.]195[.]228[.]111
12
172[.]217[.]10[.]227
11
64[.]233[.]186[.]27
11
23[.]160[.]0[.]108
10
172[.]217[.]5[.]228
10
168[.]95[.]5[.]117
10
188[.]125[.]72[.]73
10
209[.]85[.]203[.]27
10
213[.]209[.]1[.]129
9
216[.]146[.]35[.]35
9
77[.]75[.]78[.]42
9
77[.]75[.]76[.]42
9
98[.]136[.]96[.]74
9
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
13
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
13
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
13
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
13
whois[.]iana[.]org
13
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
13
whois[.]arin[.]net
13
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
13
microsoft-com[.]mail[.]protection[.]outlook[.]com
13
honeypus[.]rusladies[.]cn
13
marina99[.]ruladies[.]cn
13
sexual-pattern3[.]com
13
coolsex-finders5[.]com
13
super-efectindating2[.]com
13
mta5[.]am0[.]yahoodns[.]net
12
hotmail-com[.]olc[.]protection[.]outlook[.]com
11
www[.]google[.]co[.]uk
11
mx-eu[.]mail[.]am0[.]yahoodns[.]net
10
video-weaver[.]fra02[.]hls[.]ttvnw[.]net
10
smtp-in[.]libero[.]it
9
libero[.]it
9
eur[.]olc[.]protection[.]outlook[.]com
9
tiscali[.]it
9
etb-1[.]mail[.]tiscali[.]it
9
www[.]ebay[.]com
9
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile
13
%TEMP%\<random, matching '[a-z]{8}'>.exe
13
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
12
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
10
%SystemRoot%\SysWOW64\config\systemprofile:.repos
7
%TEMP%\tsielhm.exe
1
File Hashes 07cbb12e22655ae68bae25e8aedee6bea64d0d430d77afb86227758740b1dfcd
1ef2f6a958ffc7e4c2733100f10b53baec777d197d345012d464c2e9987cdd43
461f7cb0c6be901935666279cc26d155df22ddffbd4d65372b6ffe9aa3f4ff31
4b57c99f86103e7b26c7bee052f5c5c92c6ac82c34f21ac1b8aa333887a51068
4f734c7197b0c73e62e042cdef1cb4dfb056bc5e144a44ec00f8239796b203a9
564e5e2f864ce52b923daf130c30efd97ba3eab872e04cc8849ed6133ed7abe8
69a09f081ee022239d1b11214da3f6cfc4c256c91c61f806faa71d1997ca31d9
a0738035727d477bae527df884eb986a9c8e6aea75a354782038e3840b6fa3af
a2a94ca3039111688fe1304a3fd4ad245b79d0b6d2ce58bcecdcfdb1b34c0208
ad601c1a9bc018b918cbc9eb6c4ccd625f9096c01115a2eb4a7c1387f2bf1d10
afc2ab3eb8b9a23623603c03e7b7d1f0fca18b7b64f33976dd102681eb2a217a
b1f1d675c5d97b3ecf4085f1326bf67e5b1ee0b30ed1499df1552283d5fde731
b2ba1ec34c107072d07a962d8ce3fbaefe195969c03be6a3d0dda19aef4665a2Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Trojan.Dorkbot-7146944-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Znawav
25
Mutexes Occurrences hex-Mutex
25
s5rBKCUVfOF8JLVi
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]200
25
13[.]107[.]21[.]200
15
212[.]83[.]168[.]196
13
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]wipmania[.]com
13
update[.]jebac[.]net
13
Files and or directories created Occurrences %APPDATA%\Znawav.exe
25
%APPDATA%\Pwoiox.exe
13
File Hashes 1b7787bd1726468e25ab200665e57b1b470b7ba531d60cee8642646443725cf8
1f2f1041c73af88cc46eb86719cf66e3b51da1c4d7ac70a80cc5b6e7ee4ad73a
20f7f4a0bd9e9e531df4c14276eb290f5cb7efc37156ec9ba46fa2a7891206f1
31012f9ba68cf7e8ac73561fee2c8b2e2a538196d264f3d4c3d89341e77e2495
33f4666ed81d7e61ccdae3a895aa21d670b714727ae68639aeb064f58e387744
39a3a1ccf3c4f36cc72bd45985058d31b02ee345fc844be3b94da5a4c5a03bb6
3d8aa371276f3f11f2640c559dc5edbc792f8126604cb0e8d0ac3c7e521d4f24
4388646391e39334c69e5ff223f0a17d8f3dd11e34921344a30f78772550ca03
4fcf9f3dcd2df360e1069126acd734ded1b43ea7a7dbb5912db0d23eea505bc9
53d77cbc31d6ada99bd858417c8a8ec67907a82e6bc20e8641a3f71cbcfbe4f3
642106449fb781a3f5de12b52b54c97961e61f76160ef8c169bd2b0615e98a2c
738a68fc7864cd87bfaa8336f87b8cdc888fe9fb918de29114b419e2944d29dc
791b43d7009c8bceb849274e51607d89283bddfa94d215ede8cc3bc76953f7a7
a2c072ec77e1736120ff202bfd7f23495921f04375e09fcedc43be1e61ce4a18
a4f42f84cb704690aa10a2ebdce33e964b67a57cee554019d33f1a7cd9d3f4f3
b5bc85bf00d89cc18ffd0749f4783e5c4dd855fa37ce6c37a97ac6e8aa0a10e7
bf1102d0fb6cff725e38c7a6f6ca0e538aebcc546b711f9a2d5fac84fdb981f4
cb95aedf7037adb0c4d756ca1ddb3038341ca20cb276156b782726eff3dfca99
def2ba6dc7842c6b35f09283b68aaa9558e7339ba4b4aa53da83bfed57188ecd
e5cbafb8ceee5d6573f199acdff34ab85d2dcd0d0d8e4eb34bd1afed33fe405a
ea0479b081905b195d7dc9f37f81cd07945691ab84b395013e2653594e40522e
ee10cd27e27378d4ad3f6122168c3e60270031b337e90683481c061d192401f7
ef4abe8f4692c99b8d9bdc30b458d830905e6149ae1ae50bf7eb494f0c8bd229
f31763a353bf7a525e14f500f70c1924948db63d0bde94567dd908917f69133f
f71e42635ad5e9c0edac076a736ee15dd705ee119e2d485cb27db7c203bd0e0bCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Ransomware.Gandcrab-7145847-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: pmoywyfxuah
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: timdnedsfpy
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: gygyxbzlyev
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: faopdrnwmix
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: zpkiquyxsdb
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: lqerbrodiev
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: hspjekelvqt
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: mmdbduldnwd
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: rwsrrtanpih
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: ukyzgbixnjn
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: bnsxxppkywd
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: wuanhvperbe
1
Mutexes Occurrences Global\pc_group=WORKGROUP&ransom_id=4a6a799098b68e3c
12
\BaseNamedObjects\Global\pc_group=WORKGROUP&ransom_id=ab8e4b3e3c28b0e4
10
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]171[.]248[.]178
12
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ipv4bot[.]whatismyipaddress[.]com
12
ns1[.]wowservers[.]ru
12
carder[.]bit
12
1[.]1[.]168[.]192[.]in-addr[.]arpa
12
ransomware[.]bit
12
ns2[.]wowservers[.]ru
12
1[.]0[.]168[.]192[.]in-addr[.]arpa
10
Files and or directories created Occurrences %APPDATA%\Microsoft\<random, matching '[a-z]{6}'>.exe
12
File Hashes 067cdd8df478938f229dcedc5f65fd4cf92c66d3c516ba60ae4355d5cfd06a4b
2d6a8bbf44f9459a31692b826a86be3ec55a2fae943b01f1dbfe78bf033ff7ed
32c22604944c7f284fdd4495613bb7d0f7cf274677df9f2d4fb2c38369dba438
4135c6461d7866f9b1841bc7ecbc3e4ff58681e2b80f79e9a7daade0ca014678
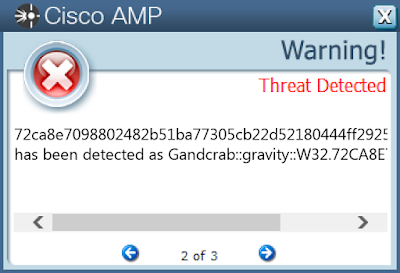
72ca8e7098802482b51ba77305cb22d52180444ff2925ed20d8eb1ca0dac5c56
7deada88e32db501dfcfb1aa0b9328c94b8a92561477d01e6b1a3b74e092e56f
a10f24291658cec5c7674d2a0a28ce019a69db9af92f3ce8b5b5a8c01c166e5f
a2f4c15b34be976d49f35e8363e220f88d59e17ab056b9049d872c6eec04f27f
b2526566d9c11b59d36b80c035653ec56a23c5aac8c49c6d7ce3657441e357b2
d2ec413f2c120332e05f71f899094794a9c0092b220ef86633d499bcdcf997ee
f8a6408e3a5a75772246c8dba4a39311ef82a5c5e5445fd817375610606bac66
f8d8c881aa3b875216dff9aad38648fe95ad99ee53b3b6652d3172187eded48fCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Malware.Phorpiex-7145044-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusOverride
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallDisableNotify
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallOverride
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SYSTEMRESTORE
Value Name: DisableSR
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesOverride
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AutoUpdateDisableNotify
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Driver
9
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Driver
9
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS
3
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\SORTANDLIFE
2
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\SORTANDLIFE\RECENT FILE LIST
2
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\SORTANDLIFE\SETTINGS
2
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\75E0ABB6138512271C04F85FDDDE38E4B7242EFE
Value Name: Blob
1
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\HEXEDITOR
1
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\HEXEDITOR\RECENT FILE LIST
1
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\HEXEDITOR\SETTINGS
1
Mutexes Occurrences 5069403
5
5070508
4
rc/Administrator
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 185[.]176[.]27[.]132
9
7[.]5[.]7[.]7
9
208[.]100[.]26[.]251
7
35[.]225[.]160[.]245
7
193[.]32[.]161[.]73
5
68[.]178[.]213[.]37
1
66[.]218[.]85[.]151
1
96[.]114[.]157[.]80
1
64[.]136[.]44[.]37
1
212[.]227[.]15[.]9
1
104[.]47[.]44[.]33
1
173[.]194[.]66[.]27
1
212[.]54[.]58[.]11
1
104[.]47[.]9[.]33
1
104[.]47[.]6[.]33
1
172[.]217[.]197[.]26
1
24[.]201[.]245[.]37
1
64[.]98[.]36[.]4
1
202[.]137[.]234[.]30
1
69[.]168[.]106[.]33
1
64[.]8[.]70[.]104
1
34[.]212[.]80[.]54
1
212[.]227[.]15[.]10
1
209[.]17[.]115[.]10
1
104[.]20[.]17[.]242
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences eguaheoghouughahse[.]top
9
rzhsudhugugfugugso[.]io
9
daedagheauehfuuhfp[.]co
9
aeifaeifhutuhuhuse[.]top
9
bfagzzezgaegzgfaik[.]su
9
huaeokaefoaeguaeho[.]io
9
aeoughaoheguaoehdl[.]cc
9
gaohrhurhuhruhfsdk[.]su
9
gaoehuoaoefhuhfugl[.]cc
9
afaeigaifgsgrhhafo[.]io
9
befaheaiudeuhughgl[.]cc
9
aeufuaehfiuehfuhfe[.]top
9
afaigaeigieufuifie[.]top
9
aeoughaoheguaoehde[.]top
9
gaghpaheiafhjefijo[.]io
9
aegohaohuoruitiiep[.]co
9
eaeuafhuaegfugeude[.]top
9
eguaheoghouughahsp[.]co
9
gaoehuoaoefhuhfugk[.]su
9
rzhsudhugugfugugse[.]top
9
afaigaeigieufuifik[.]su
9
eaeuafhuaegfugeudo[.]io
9
urusurofhsorhfuuho[.]io
9
rzhsudhugugfugugsp[.]co
9
bfagzzezgaegzgfail[.]cc
9
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp
10
\autorun.inf
9
\.lnk
9
\__\DriveMgr.exe
9
E:\$RECYCLE.BIN
9
E:\autorun.inf
8
E:\__\DriveMgr.exe
8
E:\.lnk
8
E:\__
8
%APPDATA%\winsvcs.txt
8
E:\__\$RECYCLE.BIN
7
E:\__\System Volume Information
7
%TEMP%\20402.exe
1
%TEMP%\27375.exe
1
%TEMP%\14527.exe
1
%TEMP%\13598.exe
1
%TEMP%\26079.exe
1
%TEMP%\25060.exe
1
%TEMP%\37440.exe
1
%TEMP%\39807.exe
1
%TEMP%\10643.exe
1
%TEMP%\16693.exe
1
%TEMP%\11927.exe
1
%TEMP%\29428.exe
1
%TEMP%\14209.exe
1
*See JSON for more IOCs
File Hashes 0d338324cf835af918aeb90f63e3d3e96f1f21136005162bff9eb7dff51d5efb
1924bd8e0c2679662f36c52fb7c1acb170e9ad71c55d1b53b70e55f3db71d644
48eac3b34c05886e1338554f54ca7022fa15215dd22d4a6bf62d6c531ba1a3f7
5e1d7375f3e2bb793908e0fa30b5d50e330024be2482f1d6be2c17395bd3b104
65ebf8cd6280fc0c6d3261ecb07e928dec08a6c3a9a814008faeb9053da5485e
6d65ccab03a62d84f12ac21fd02f44805c34696951e3dfb79ca042d8b832cd89
8a60f95d39f7255e1fd83aac66e0d922ca0a235069d7fca74a4ca07aa5ff5f96
c9d8bbeecb57aa0e4f59bad6e574470fe3ff8cc1685f38b16b6fa5435791231f
de730a7cf6d436b4e93c0a857cd72074bb2bc1dfd5fda10e25125773711526a9
e0af9dcc27483bcdad52558aa19224a0338343e0456ad1e663e0b42fdd53520fCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Ransomware.Sage-7144073-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER
Value Name: GlobalAssocChangedCounter
14
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: Wallpaper
14
<HKCR>\.SAGE
14
<HKCR>\SAGE.NOTICE\DEFAULTICON
14
<HKCR>\SAGE.NOTICE\FRIENDLYTYPENAME
14
<HKCR>\SAGE.NOTICE\SHELL\OPEN\COMMAND
14
<HKCR>\HTAFILE\DEFAULTICON
14
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
14
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
14
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\##PC#USERS
Value Name: _CommentFromDesktopINI
6
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\##PC#USERS
Value Name: _LabelFromDesktopINI
6
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\##PC#USERS
6
<HKCR>\.SAGE
1
<HKCR>\SAGE.NOTICE
1
<HKCR>\SAGE.NOTICE\DEFAULTICON
1
<HKCR>\SAGE.NOTICE\FRIENDLYTYPENAME
1
<HKCR>\SAGE.NOTICE\SHELL
1
<HKCR>\SAGE.NOTICE\SHELL\OPEN
1
<HKCR>\SAGE.NOTICE\SHELL\OPEN\COMMAND
1
<HKCR>\HTAFILE
1
<HKCR>\HTAFILE\DEFAULTICON
1
Mutexes Occurrences zHUoNUQ7
14
\BaseNamedObjects\PFShggN3
13
\BaseNamedObjects\adX9ZN6Z
13
\BaseNamedObjects\nkB7lqma
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 5[.]45[.]17[.]36
14
5[.]45[.]100[.]133
14
5[.]45[.]107[.]161
14
5[.]45[.]107[.]167
14
5[.]45[.]208[.]36
14
138[.]197[.]5[.]51
14
138[.]197[.]17[.]156
14
138[.]197[.]90[.]36
14
138[.]197[.]90[.]40
14
138[.]197[.]90[.]60
14
138[.]197[.]100[.]51
14
138[.]197[.]107[.]13
14
138[.]197[.]223[.]99
14
139[.]59[.]5[.]191
14
139[.]59[.]17[.]80
14
139[.]59[.]46[.]45
14
139[.]59[.]107[.]91
14
139[.]59[.]125[.]8
14
139[.]59[.]125[.]154
14
139[.]59[.]183[.]4
14
139[.]59[.]183[.]170
14
139[.]59[.]184[.]137
14
139[.]59[.]198[.]12
14
139[.]59[.]198[.]48
14
139[.]59[.]198[.]116
14
*See JSON for more IOCs
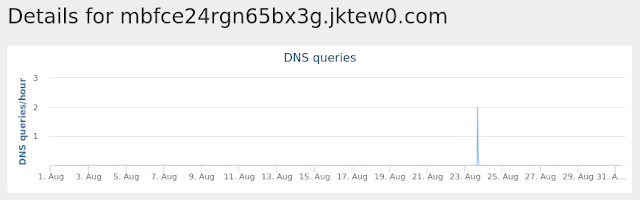
Domain Names contacted by malware. Does not indicate maliciousness Occurrences mbfce24rgn65bx3g[.]jktew0[.]com
14
mbfce24rgn65bx3g[.]jpo2z1[.]net
14
Files and or directories created Occurrences %HOMEPATH%
14
%System32%\Tasks\N0mFUQoa
14
%TEMP%\__config252888.bat
14
%APPDATA%\Rj3fNWF3.exe
14
%APPDATA%\s1qoaKDO.tmp
14
E:\!HELP_SOS.hta
14
\!HELP_SOS.hta
14
%TEMP%\DDx.bmp
14
%APPDATA%\f1.hta
14
%HOMEPATH%\Desktop\!HELP_SOS.hta
14
%HOMEPATH%\Documents\!HELP_SOS.hta
14
%HOMEPATH%\Documents\Outlook Files\!HELP_SOS.hta
14
%PUBLIC%\Desktop\!HELP_SOS.hta
14
%PUBLIC%\Documents\!HELP_SOS.hta
14
%TEMP%\f1.vbs
13
File Hashes 0558a89422c627ed31af6d34293b1de99ebd9f8538d8c29bf830b9302dd9aa56
25fd8664218cae1ca68b42245729c6cd00bbf3033704adf66c3ed56604d7e49c
42266cea4387c3bfa085ead6686fb91936a65bf8110c328b4e898771240e7b00
785c3dde4d85cd5ff2e1a826801c3813c2dd08fd547628aaf83bd9baeaf1f9c9
91a103e0a3a93dc681e7de5af18850933d2435a1d6cef35f85e7855f14c3ec02
9dd1839b1090c0467211f689214df91e5eb8e73830f2a2ea9e3408e527fe4096
a462ea6b325c5b91513498401fe7213cee84b61f04278616c51cae7238e57225
adf288cbaea7fadb2b2f152ebccab141a94cccce33d343fd9c5d42bfe65e57eb
b238d1eb5e3ef4e3f5c93ead5032ad0bd67716ff555cf1a3649397ad2e3dcaef
b5678f253a2c15a3caa25840b16421b4458928d0ddffaf1fb941a4aff1061f38
b61628da0124170e6bfeb5f282da74d06c5a6cffcd05681ce8cd069ec7831404
d59ec8d355d30d035faf50a342e1f1b67b44764db114a373c503098847718db3
d7e794446a774f9f3cacdbd58345a1a52f988eaff24c122800a9aa9b0e094e08
f44c64cc3c06ebb0c2e3333227e82568a14e7cc4400679cd85228f8882f0a416Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
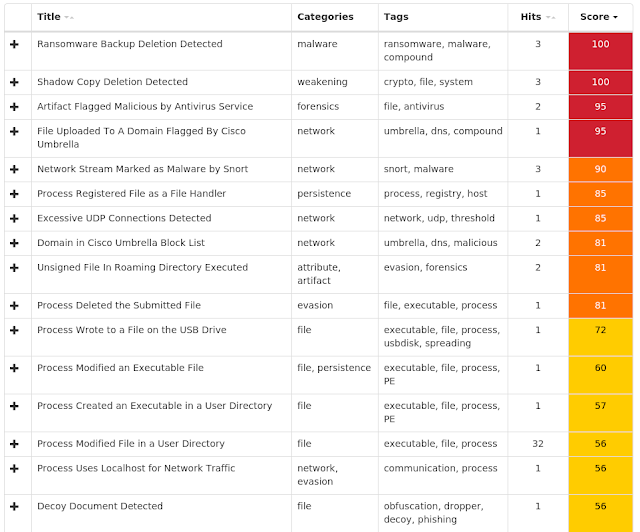
Screenshots of Detection AMP ThreatGrid Umbrella Malware Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. CVE-2019-0708 detected - (5286)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP request). Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Madshi injection detected - (2638)
Madshi is a code injection framework that uses process injection to start a new thread if other methods to start a thread within a process fail. This framework is used by a number of security solutions. It is also possible for malware to use this technique.
Kovter injection detected - (1427)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Process hollowing detected - (1081)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Trickbot malware detected - (220)
Trickbot is a banking Trojan which appeared in late 2016. Due to the similarities between Trickbot and Dyre, it is suspected some of the individuals responsible for Dyre are now responsible for Trickbot. Trickbot has been rapidly evolving over the months since it has appeared. However, Trickbot is still missing some of the capabilities Dyre possessed. Its current modules include DLL injection, system information gathering, and email searching.
Gamarue malware detected - (193)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Installcore adware detected - (97)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
Excessively long PowerShell command detected - (65)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
PowerShell file-less infection detected - (49)
A PowerShell command was stored in an environment variable and run. The environment variable is commonly set by a previously run script and is used as a means of evasion. This behavior is a known tactic of the Kovter and Poweliks malware families.
Dealply adware detected - (30)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.