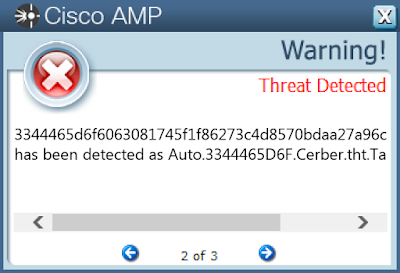
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Dec. 6 and Dec. 13. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net. here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
Threat Name Type Description Doc.Downloader.Emotet-7446804-0
Downloader
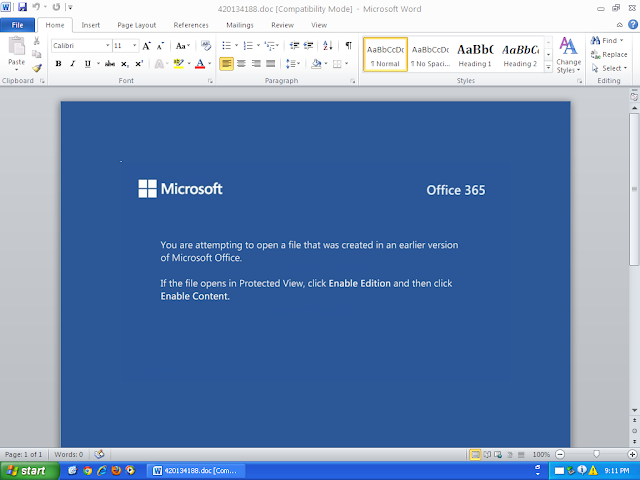
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Packed.Razy-7434602-0
Packed
Razy is oftentimes a generic detection name for a Windows trojan. It collects sensitive information from the infected host and encrypt the data, and send it to a command and control (C2) server. Information collected might include screenshots. The samples modify auto-execute functionality by setting and creating a value in the registry for persistence.
Win.Packed.DarkComet-7433889-1
Packed
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Trojan.Gamarue-7440316-0
Trojan
Gamarue, also known as Andromeda, is a botnet used to spread malware, steal information and perform activities such as click fraud.
Win.Dropper.Fareit-7431743-0
Dropper
The Fareit trojan is primarily an information stealer with the ability to download and install other malware.
Win.Dropper.Tofsee-7440661-0
Dropper
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control.
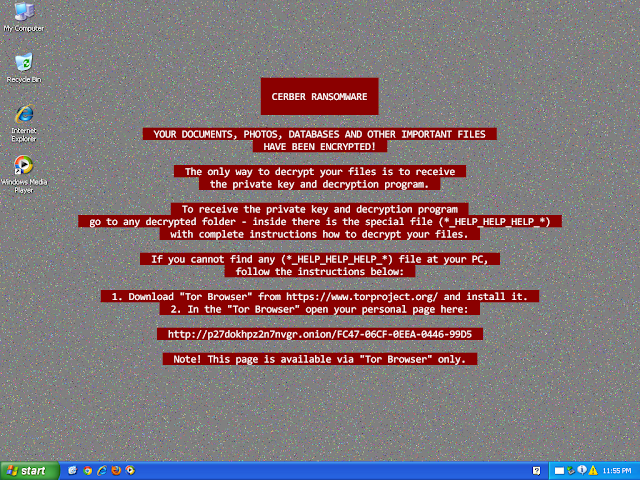
Win.Ransomware.Cerber-7432369-1
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used.
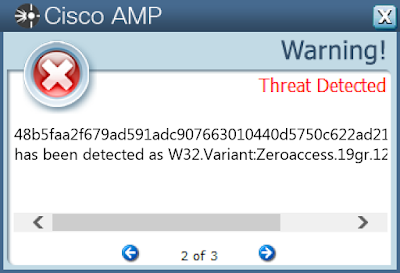
Win.Trojan.ZeroAccess-7432508-1
Trojan
ZeroAccess is a trojan that infects Windows systems, installing a rootkit to hide its presence on the affected machine and serves as a platform for conducting click-fraud campaigns.
Threat Breakdown Doc.Downloader.Emotet-7446804-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\INTERFACE\{BEF6E003-A874-101A-8BBA-00AA00300CAB}
16
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: ProxyServer
7
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: ProxyOverride
7
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: AutoConfigURL
7
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: AutoDetect
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: Type
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: Start
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: ErrorControl
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: ImagePath
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: DisplayName
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: WOW64
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FUNCSITKA
Value Name: ObjectName
7
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}
1
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0
1
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\FLAGS
1
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\0
1
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\0\WIN32
1
<HKLM>\SOFTWARE\CLASSES\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\HELPDIR
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\FLAGS
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\0
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\0\WIN32
1
<HKCR>\TYPELIB\{C4EDCADC-BC75-481F-8A5F-3E2075206B43}\2.0\HELPDIR
1
Mutexes Occurrences Global\I98B68E3C
7
Global\M98B68E3C
7
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 100[.]107[.]68[.]85
9
100[.]79[.]88[.]70
9
100[.]94[.]136[.]45
9
100[.]90[.]27[.]84
9
100[.]112[.]60[.]67
9
91[.]74[.]175[.]46
7
205[.]144[.]171[.]176
7
77[.]90[.]136[.]129
4
173[.]255[.]214[.]126
4
96[.]38[.]234[.]10
3
173[.]194[.]175[.]108
2
82[.]223[.]190[.]138
2
217[.]116[.]0[.]237
2
103[.]6[.]198[.]100
2
54[.]88[.]144[.]211
2
212[.]227[.]15[.]142
2
217[.]116[.]0[.]228
2
62[.]149[.]128[.]210
2
62[.]149[.]152[.]151
2
52[.]96[.]62[.]226
2
185[.]102[.]40[.]53
2
83[.]219[.]92[.]20
2
196[.]44[.]176[.]42
2
41[.]190[.]32[.]8
2
62[.]149[.]152[.]152
2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]4celia[.]com
16
travalogo[.]com
9
miracles-of-quran[.]com
9
capsaciphone[.]com
9
essay[.]essaytutors[.]net
9
smtp[.]secureserver[.]net
2
pop[.]secureserver[.]net
2
mail[.]secureserver[.]net
2
secure[.]emailsrvr[.]com
2
outlook[.]office365[.]com
2
smtp[.]263[.]net
2
smtp[.]aruba[.]it
2
securepop[.]t-online[.]de
2
mail[.]eim[.]ae
2
exmail[.]emirates[.]net[.]ae
2
mail[.]pec[.]aruba[.]it
2
p02-imap[.]mail[.]me[.]com
2
mbox[.]cert[.]legalmail[.]it
2
smtp[.]pec[.]aruba[.]it
2
pop3s[.]pec[.]aruba[.]it
2
pop[.]pec[.]istruzione[.]it
2
pop3[.]itevelesa[.]com
2
smtp[.]mweb[.]co[.]zw
2
mail[.]eitelux[.]es
2
pop[.]realperfil[.]com[.]br
2
*See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%\245.exe
16
%SystemRoot%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
7
%TEMP%\CVRA52.tmp
1
File Hashes 1de08bdcceee9ce5642c85db384163a76e4de953c2e625c944ef1b087c483f4b
24b7af440ef4ac270373b6f5c9514885a3224c046b73cf8ad2f1f43012b2ab79
2b5e8a119ff94422a9b5213562ea161306d91d255b13e8840b8c6e405ca767ca
342e32ccf662f9fdae9df6d332382b5332fd41f47ae970c42197100ccc29bdb2
3c790759a0f56659200ee93697ec8fef684ac4e241545c7e82399cbe5128ce12
47b2096a5d64d83ce0216c4b577d40567e51bdfb7456f2642dbe2222d0fc9ac9
4810b72b5ce022be0b50fb4cc530fa10f8d4351d66c6384eb86ca6a714f697b1
713407b0e97009b83eb112b7c22588ddf4ccc8418fd548ffe8dded8774698894
902d50419ed4b29f175944cd6d1f59d1b06a26b9a659cd04d282c3685cc478d6
adc96e8b0fdb5d977111b124c655a1821d5c9c0810207aaa82ccb5bacc0c6698
b512845fd39f154b9208e59762e4f136838ca52666e4ca598a3e99c90d332061
c5ea35ff71f952e64d69779eb8dfe98d0a8a77f727fae139a66125ad76c3526f
cb03c4ba3c52376950f5924ac4491ddb0afff6e5c5d5d2f1512e042c8116ff2a
cb33e2134b2670a581eaefc1b800721a0c49e96441027948463c32db39e75fbb
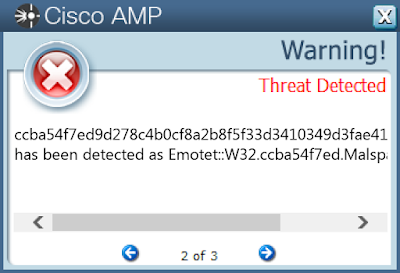
ccba54f7ed9d278c4b0cf8a2b8f5f33d3410349d3fae416fb69388f15874f84d
deb94515bf4c10daa7c26a3c0fa8ed837ee3ad54176a9d4d3d1b5c6230a2447cCoverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
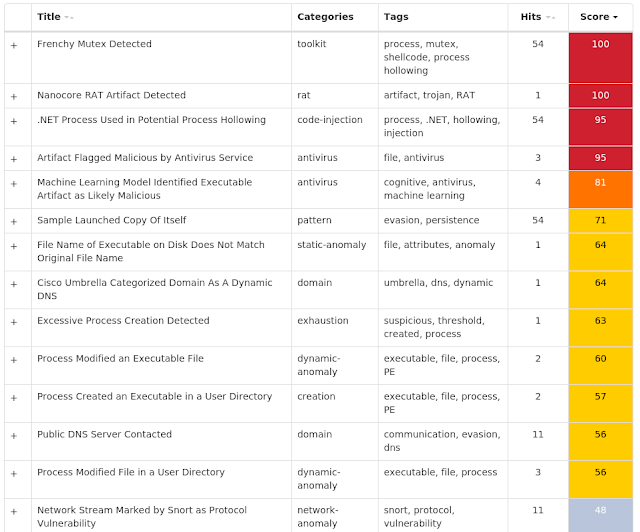
Screenshots of Detection AMP ThreatGrid Umbrella Malware Win.Packed.Razy-7434602-0 Indicators of Compromise Mutexes Occurrences frenchy_shellcode_006
10
Startup_shellcode_006
10
Global\{b0cec92d-4b6c-4178-94fb-bf6cc1add43d}
10
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 107[.]172[.]83[.]151
10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dec8973[.]duckdns[.]org
10
Files and or directories created Occurrences %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5
10
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs
10
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator
10
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat
10
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\HJdyTuap.exe
10
%HOMEPATH%\ophan.exe
10
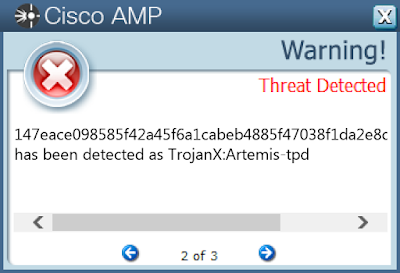
File Hashes 02252b22b7b50a36851f97a612057c61a8aeed4a2d7cc18258fe2ba6d70fe6a5
147eace098585f42a45f6a1cabeb4885f47038f1da2e8dbf700795b7f5176165
472334c6964fa75128a812e1f819693c4a3b19d43466fb01e88d16a04366487b
5928dd708f5190db002c2ac530f61b994ef6667e59894ae7f085296e451cb06d
59ef7cbae939ff16e921afa54d76b2ed960a7c982fd1b41b318e2e840fa67690
8f5d1ed403153ce043daabd92c15452f01142a829ebaa0530a690ca7bf16d8b1
9708566442ccfc689c110efa436095f21a6d2e15ab1a5a5d5bf35d9ce1063768
a9844ac5e8f56a958e42500b31d6e902120d385f373599eeafc9d4316c6ff2e7
c7b1a3495bb7fb1f8f4016952f6ee68873bd6d4c39468602bc97e59eb8cc9177
d9e7d0ae7bacf011c0abfee024872bb7662b06b4f5faa87efc8eccb7ad02a633Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
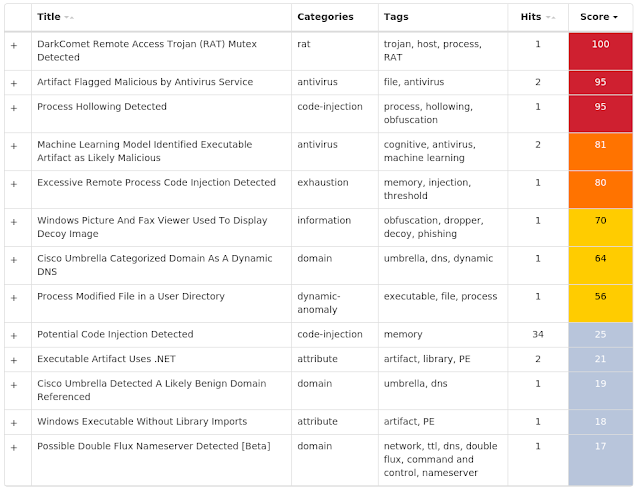
Screenshots of Detection AMP ThreatGrid Win.Packed.DarkComet-7433889-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
6
<HKCU>\SOFTWARE\DC3_FEXEC
Value Name: 12/6/2019 at 1:01:19 PM
4
<HKCU>\SOFTWARE\DC3_FEXEC
Value Name: 12/6/2019 at 1:01:20 PM
4
<HKCU>\SOFTWARE\DC3_FEXEC
Value Name: 12/6/2019 at 1:01:18 PM
3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicroUpdate
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: UserInit
3
<HKCU>\HKEY_CURRENT_USER
2
<HKCU>\HKEY_CURRENT_USER\SOFTWARE
2
<HKCU>\HKEY_CURRENT_USER\SOFTWARE\MICROSOFT
2
<HKCU>\HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\ACTIVE SETUP
2
<HKCU>\HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Java Updater 12.02.3
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: Java Updater
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: Load
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: IE Per-User Initialization utility
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: IE Per-User Initialization utility
2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
2
<HKCU>\SOFTWARE\DC3_FEXEC
Value Name: 12/6/2019 at 1:01:24 PM
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
1
Mutexes Occurrences DC_MUTEX-<random, matching [A-Z0-9]{7}>
12
DCPERSFWBP
4
Paint
1
Administrator5
1
zRfBoxVQtvcwCKzfoomrPWdIUUjnqiHWPygjEgky
1
cbebf6a3c30e189f1791a07b91284eaf
1
UNwehCeiwHcpcPqMLnVm
1
Global\c8760b20-185a-11ea-a007-00501e3ae7b5
1
wHcpcPqMLnVmYcCcnhzwUpOGDOftPDMkeIKqqMLnVmYcCcnhzwUpOGDOftPDMkeIKqqMLnVmYcCcnhzwUpOGDOftPDMkeIKqqMLnVmYcCcnhzwUpOGDOftPDMkeIKqqMLnVmYcCcnhzwUpOGDOftPDMkeIKq
1
yzxDnuCSssIxBsSuZXFtOFvJTDCppRZlOhNkDPDB
1
NSaQvFFEJfmtYlkBEHyXmfPxzUwCPMuIhhJReGZF
1
IRojNPvPVdSxHIGLipwanmDHJBaphSzCXzESOwLj
1
orHcdnwrVlEYrlbHQQOTFxFjvvLPSKixqaILfIMa
1
myCQlnwHCfuNhBukQZZY
1
Global\c923cf81-185a-11ea-a007-00501e3ae7b5
1
uoHEavVNJUlBWJTqlPRxRXfUzJKINkqxcpoFJLDc
1
bQvFGEJgmtYlkBFHyYnfQxzUwCPMuIhhJSeGaFdv
1
JwuoGEavUaWilBWXgqlPew
1
HusmFCYuTZVgjyUVfojNcvPidSxHIGLvpwan
1
xXXyHTvPuSkKkvpIrOxJOL
1
vkhbtqNjIOKVZnJLUdYCSkFYSInwwvzlelQcc
1
iRfFFfoBdwczSrSdXpZvfpvrEUjqsCZUxzgmGOEj
1
Global\f44dbcc0-185a-11ea-a007-00501e3ae7b5
1
QXCcOehkcBeJsodxoboyhhVHiFRfNeQUu
1
ewtQmLRNYbqMNXgbFVnIbVLqyzxDoho
1
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]159[.]135[.]230
4
94[.]73[.]36[.]254
2
104[.]16[.]155[.]36
1
94[.]73[.]32[.]235
1
94[.]73[.]33[.]36
1
173[.]194[.]175[.]108/31
1
54[.]231[.]48[.]43
1
109[.]220[.]205[.]220
1
90[.]197[.]55[.]134
1
25[.]109[.]69[.]178
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences simond[.]zapto[.]org
4
laloutrecam[.]no-ip[.]org
2
botofvps[.]no-ip[.]biz
2
whatismyipaddress[.]com
1
s3-1[.]amazonaws[.]com
1
s3[.]amazonaws[.]com
1
zcitizen[.]no-ip[.]org
1
server-49[.]sytes[.]net
1
bbdl[.]ddns[.]net
1
who-is[.]ddns[.]net
1
update[.]imagineyourcraft[.]fr
1
123[.]105[.]12[.]0[.]in-addr[.]arpa
1
alaka[.]no-ip[.]biz
1
Files and or directories created Occurrences %APPDATA%\dclogs
11
%TEMP%\AdobeARM.exe
10
%TEMP%\resman.exe
7
%TEMP%\dw.log
4
%TEMP%\<random, matching '[A-F0-9]{4,5}'>.dmp
4
%TEMP%\<random, matching '[a-z]{4,9}'>.exe
4
%HOMEPATH%\My Documents\MSDCSC\msdcsc.exe
3
%HOMEPATH%\Documents\MSDCSC
3
%HOMEPATH%\Documents\MSDCSC\msdcsc.exe
3
%APPDATA%\pid.txt
2
%APPDATA%\pidloc.txt
2
%TEMP%\garrys mod robot.jpg
2
%TEMP%\holderwb.txt
1
\Paint
1
%ProgramFiles%\Java\jre8\bin\rmiregistry.exe
1
%ProgramFiles%\Java\jre8\bin\servertool.exe
1
%ProgramFiles%\Java\jre8\bin\tnameserv.exe
1
%ProgramFiles%\Java\jre8\bin\unpack200.exe
1
%ProgramFiles%\Java\jre8\bin\vjava.ico
1
%ProgramFiles%\Java\jre8\bin\vjavacpl.ico
1
%ProgramFiles%\Java\jre8\bin\vjavaw.ico
1
%ProgramFiles%\Java\jre8\bin\vjavaws.ico
1
%ProgramFiles%\Microsoft Silverlight\5.1.30514.0\coregen.exe
1
%ProgramFiles%\Microsoft Silverlight\vsllauncher.ico
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Paint.lnk
1
*See JSON for more IOCs
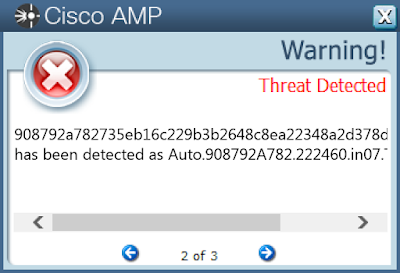
File Hashes 2d6da6399671b08e28a10df9bcf76061f4c98a1f65202fb0dffccd918a5554fc
3a7644b928b85c1e448fe7bb7ddf51056e63f49b9455aae7b2e38fb179559066
6001c594a9e3454fb9359b140dc22e106c5946c323029783e9f122ec285e0c65
79a1576d14b171ce34915fe40b021f73a9d607c2ada2be53e335f330b6cb858f
879c8524b93f3699c02ca366b15677c03df4d5e4e8ba03b43907618adde5627f
908792a782735eb16c229b3b2648c8ea22348a2d378d428d4798fbb21cdca541
918928629a8e0059e82aaa4fe2f226f66a334ead2b8f85dd8eef6e5d288325dc
92729ba8ef8eabfc9b4e88443d94fba225c6a643871fddfc6bf9d8d173d4c7f6
a0f6ffb10dd497d92d870642f2ba86639b170486cbaead79d0a82bd2d7e5edf3
a1999cf773b35ebab2b29acc4d0c0fe92de4bea83e4ee118a2b9a2474b19956c
af47feb292bf865a7d0fbf2a8da31f8d04b38c759f5850ef3510a5f2ecaedae1
b1a9a49194c72fe92df017167c753625a80173c81b8a17cb1b20c84093d10c02
bb7b89751f70e99fe62c1edaba821bb95dfab8b0c6d268b845f3f936f09113df
bc49d905ffd3203d51e3684755fd2412fdc75ee977350da40db2cae357419bd9
bd9e2ff72624901bf190a22ba2a9419395024d280e7f9d140918ffaecf96065a
de59098d7862ae86da6c3159093f1afd4aa72dfc7f6b2826e270e94b272fb7fb
df237e6044ad335081f455ce70e0288453ce74c371016def916462e0d93d124e
e8f164fe292feef26582e9af9d8e0fec11768a72fcb2202af7180a5a8efa46fa
f893532e35d7503e3685c70aaf7a23ce371acc1d0e3779297aba47ae65e9e949Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
Screenshots of Detection AMP ThreatGrid Malware Win.Trojan.Gamarue-7440316-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: {77E00C05-FC14-92FB-C64D-2FAE1577C98A}
8
<HKCR>\CLSID\{B1D503C8-F3D9-54CE-C64D-2FAE1577C98A}
8
<HKCR>\CLSID\{EBF02436-D427-0EEB-C64D-2FAE1577C98A}
8
<HKCR>\CLSID\{EBF02436-D427-0EEB-C64D-2FAE1577C98A}
8
Mutexes Occurrences Santiv18
8
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 217[.]23[.]1[.]27
8
212[.]8[.]242[.]104
8
Domain Names contacted by malware. Does not indicate maliciousness Occurrences v1[.]eakalra[.]ru
8
v1[.]op17[.]ru
8
Files and or directories created Occurrences %ProgramData%\{DA12294E-A996-195C-0CAA-A4200A7998ED}\77adf9d1.exe
8
%SystemRoot%\Tasks\{4602017E-81A6-854C-0CAA-A4200A7998ED}.job
8
\{c78b9d89-a44c-8958-2fb4-20d7a387d6e3}\a7c25200-afe3-483f-5c47-c10c3cf1e73a.exe
8
%ProgramData%\{EBF02435-D424-0EEB-C64D-2FAE1577C98A}
8
E:\{c78b9d89-a44c-8958-2fb4-20d7a387d6e3}
8
E:\{c78b9d89-a44c-8958-2fb4-20d7a387d6e3}\a7c25200-afe3-483f-5c47-c10c3cf1e73a.exe
8
%ProgramData%\{EBF02435-D424-0EEB-C64D-2FAE1577C98A}\464ff4aa.exe
8
%System32%\Tasks\{77E00C05-FC14-92FB-C64D-2FAE1577C98A}
8
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\779425.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\743768.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\888608.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\577671.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\898551.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\569993.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\281727.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\469268.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\502020.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\569087.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\630040.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\825247.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\400602.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\445144.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\223566.exe
1
%ProgramData%\{D73F619F-E147-1471-0CAA-A4200A7998ED}\688135.exe
1
File Hashes 0c56ea50a45505f406a4feddcb3b4c055c0d52ca1aa4ca7d8254267fe1e75e52
0f4e733dcf95c9b026b2a081c0bc8883bdcdf8799a31ae2afff8aa12fa980c3f
46e382dadb24dc1dfd6c5ff7faeb088d56a70150ec44015a8370900251b3024e
86251f8acfcf6f5adb20ef8cfb4def27ff42b8248aae488f3a4d3650dda87364
8ffb2571c279e05205e55b169d306f54a574a73c596475f0738593c34dfbb3be
900547463b112df48191a8a950a7375be9c20fb33de917bf5af6d31aa5e5b700
943bdb5be04e4dd27ebf28532a8639eafd6dc7df5e471f733697220a1aee9c93
ab2d58efd6a9c50bfab5b0143009dc25ab0f92d7a9d7bcad39f4edbf1ff6b835
b291fe03d64db56f2dbd01d71364ed39b2a7b83b61161673bea57ab33c27c7e8
bf1a4d2ab6c500f55a8e5d8e9667fc6bfce7cdbd79b2bf9ebbf7a1392ff3956e
c865ae6939ddc9a42481a4f2d410a928f11837e807dbd8d6dad867c13b58019e
ca47206563a8eb9e402d5f5f957e15bf73d6193985281c38127cc2cdd63bcb64
cf5e15aa7027ca86fc3ad768f1684fd619f367c521231970db5a3024230b34f1Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid Win.Dropper.Fareit-7431743-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\WINRAR
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: WindowsMonitorConfigs32
10
<HKCU>\SOFTWARE\WINRAR
Value Name: HWID
10
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9
Value Name: F
10
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5
Value Name: F
10
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC
Value Name: F
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS
Value Name: WindowsMonitorConfigs
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS
Value Name: WindowsMonitorConfigs32
10
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\NETWORKLIST\NLA\CACHE\INTRANET
Value Name: {9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
7
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 37[.]10[.]116[.]208
10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences loqapeek[.]pw
10
xistoons[.]pw
10
Files and or directories created Occurrences %APPDATA%\SystemDriversReserved
10
%APPDATA%\SystemDriversReserved\rynuqeny.exe
1
%APPDATA%\SystemDriversReserved\filarifi.exe
1
%APPDATA%\SystemDriversReserved\miqonagy.exe
1
%APPDATA%\SystemDriversReserved\xuminazy.exe
1
%APPDATA%\SystemDriversReserved\qeremuvu.exe
1
%APPDATA%\SystemDriversReserved\vywivama.exe
1
%APPDATA%\SystemDriversReserved\cuzuluqa.exe
1
%APPDATA%\SystemDriversReserved\dufenuxu.exe
1
%APPDATA%\SystemDriversReserved\cutypiwu.exe
1
%APPDATA%\SystemDriversReserved\rikicuzo.exe
1
%APPDATA%\SystemDriversReserved\tihupono.exe
1
%APPDATA%\SystemDriversReserved\xomytevu.exe
1
%APPDATA%\SystemDriversReserved\xotadyry.exe
1
%APPDATA%\SystemDriversReserved\zytecufo.exe
1
%APPDATA%\SystemDriversReserved\myciloby.exe
1
%APPDATA%\SystemDriversReserved\kebyqyha.exe
1
%APPDATA%\SystemDriversReserved\fufolely.exe
1
%APPDATA%\SystemDriversReserved\rysopyly.exe
1
%APPDATA%\SystemDriversReserved\zazanyge.exe
1
%APPDATA%\SystemDriversReserved\niwalefu.exe
1
File Hashes 10491d1ce14e3c36f1ff822ff1053604043836d94925de6054482c9ae4673359
15901d3d72c05adea149a9b23a03240e84827ee199119beca4bae58d0f2cf292
28495c8cd716b9047bbdecdeb9acb5883a57dcb887db0aa10d72345c25cccf01
2afda0e3c48ea37e936b0ef7d7efbfc5a6e487f1dee0dd89ec83cba2c054ddd0
31f651b56867fe2a75041c5c053977414f33285d1a8294875ef4082269103f59
4629248f320c9fd7d3b2d9b01e3b0e705a07c52ed8c40baa63395ae95b4e6e43
91a2d95ddf43ee9a47c0b2f781d9aa6752ada642cbd826fc8c0ec2c31932870d
b831abbd0734bcd7cf2262400d70c32b5909d3a38044327b841b5f05cba93567
d27a710d945ee916fa7ab557e3a360f907d06ca37c34aff86133074ddfed9090
ee3cf9966f84454415d0dda42e29ccf65e14f964daef8233077c2509aa84b305Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid Win.Dropper.Tofsee-7440661-0 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES
2
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
2
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
2
<HKCU>\SOFTWARE\MICROSOFT\IAM
Value Name: Server ID
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\kdrxwekz
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KDRXWEKZ
Value Name: Description
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\piwcbjpe
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
Value Name: Description
1
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
1
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: apiMPQEC
1
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
1
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\75E0ABB6138512271C04F85FDDDE38E4B7242EFE
Value Name: Blob
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\PIWCBJPE
1
Mutexes Occurrences Global\syncronize_URN0LVA
2
Global\syncronize_URN0LVU
2
A16467FA7-343A2EC6-F2351354-B9A74ACF-1DC8406A
1
Global\9776ba01-1ac7-11ea-a007-00501e3ae7b5
1
Global\990ba241-1ac7-11ea-a007-00501e3ae7b5
1
Global\95700cc1-1ac7-11ea-a007-00501e3ae7b5
1
{<random GUID>}
1
Local\{<random GUID>}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]55[.]5[.]250
2
13[.]107[.]21[.]200
2
43[.]231[.]4[.]7
2
104[.]47[.]54[.]36
2
172[.]217[.]7[.]164
2
85[.]114[.]134[.]88
2
172[.]217[.]12[.]164/31
2
68[.]178[.]213[.]37
1
94[.]100[.]180[.]104
1
93[.]158[.]134[.]89
1
81[.]19[.]78[.]66
1
77[.]88[.]21[.]89
1
46[.]4[.]52[.]109
1
96[.]114[.]157[.]80
1
94[.]100[.]180[.]31
1
94[.]100[.]180[.]180
1
104[.]47[.]9[.]33
1
104[.]47[.]36[.]33
1
213[.]209[.]1[.]129
1
87[.]250[.]250[.]89
1
211[.]231[.]108[.]46
1
104[.]47[.]5[.]33
1
213[.]180[.]147[.]146
1
212[.]227[.]15[.]41
1
208[.]89[.]132[.]199
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
2
microsoft-com[.]mail[.]protection[.]outlook[.]com
2
smtp[.]secureserver[.]net
1
mx[.]yandex[.]ru
1
yandex[.]ru
1
list[.]ru
1
mx-eu[.]mail[.]am0[.]yahoodns[.]net
1
mxs[.]mail[.]ru
1
rambler[.]ru
1
smtp-in[.]libero[.]it
1
mx1[.]comcast[.]net
1
libero[.]it
1
mail[.]ru
1
comcast[.]net
1
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
1
mx[.]yandex[.]net
1
inbox[.]ru
1
eur[.]olc[.]protection[.]outlook[.]com
1
aol[.]com
1
hotmail-com[.]olc[.]protection[.]outlook[.]com
1
emx[.]mail[.]ru
1
yahoo[.]it
1
mx[.]poczta[.]onet[.]pl
1
charter[.]net
1
inmx[.]rambler[.]ru
1
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\D47F.tmp
5
%TEMP%\CC4F.tmp
3
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\desktop.ini.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\FilterTransforms\1033\StarterKitsFilterTransform80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\CSharpLangFilter20.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\ControlsTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\HelpTopicsTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\InfoPathTechFilter12.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\KBTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\NetFxTechFilter20.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\SamplesTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\ServerEntTechFilter20.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\SnippetsTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\StarterKitsTopicTypeFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\VBLangFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\VBScriptLangFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\VS2005TechFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\Win32TechFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\WinFormsTechFilter20.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\WindowsTechLonghornWinFx60.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Filters\1033\XmlLangFilter80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%CommonProgramFiles(x86)%\microsoft shared\VS Help Data\8.0\Pages\1033\VSTAHowDoI80.xml.id-98B68E3C.[admin@sectex.net].bot
2
%APPDATA%\Microsoft\Internet Explorer\brndlog.bak.id-3C28B0E4.[admin@sectex.net].bot
2
%APPDATA%\Microsoft\Internet Explorer\brndlog.txt.id-3C28B0E4.[admin@sectex.net].bot
2
%HOMEPATH%\Cookies\index.dat.id-3C28B0E4.[admin@sectex.net].bot
2
*See JSON for more IOCs
File Hashes 1a2997b0927ee1931765cf9b971ee5fd20ca9509f25eed7f2ece2f9b39ec30ec
1b7f2a5950d2d2c9f012c8aa7bb8a7611a19bea54e2ad3a11aaeeb178de91229
45e58500cc320316f3ab9cb9f9bde14446ae10f5ac37c93061b2bfad97b1026d
51fb27ab74d127a6cef6b1aaf416bc28020c93cc62926c25a0aabd64eadd51f0
63bbfc542016858d070ae21bc75f4f507273343ed7552b0fb1041b353891c943
6ac190612aeca2cf29bc2c403afd7ff4f6bd0978611b9879feed907a43d7a44e
7a6ca98d05b91859a323aeb8aa95cea2465223095963a56edd053ea2144d2949
8bd815aac414de71c6c9e8d98af6f3ea99f8f7d9eb99b24bd65aefc6fae62564
9adc16c0e94ecca0bd3bfb7a6913bc439fbeb59ae70ec264b49dc74bf92de628
a3397387c72d6215fbe3d976c0d2a2a96ada6526a1e939326e0a009c1469c748
ac1195f32c230290268c6ac144d386aaa1be9889ed4ba899bbd2078d1985a296
c909a47cc3169954c962a7bba2911694345cca7ecbe809a8e9ae737df9ee1c24
d59f8aa651ab5015619a62efde293097facdabd1a11c019cc0a0748009628126
f05b7128fd81fb67061ede7c279807ab347505762245f77f1ab0180bb4655cb2
fccdacfaf67834441250a0713534ef2d1047e7af6424a09df88a6ee132a3fe86Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid Umbrella Win.Ransomware.Cerber-7432369-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\SPEECH\VOICES
Value Name: DefaultTokenId
33
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\VOICES
33
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
32
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
31
<HKCU>\SOFTWARE\MICROSOFT\DIRECT3D
Value Name: Name
1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
33
Local\MidiMapper_modLongMessage_RefCnt
33
shell.{<random GUID>}
27
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 91[.]119[.]216[.]0/27
33
91[.]120[.]216[.]0/27
33
91[.]121[.]216[.]0/25
33
150[.]109[.]231[.]116
22
54[.]209[.]0[.]191
18
34[.]193[.]185[.]171
15
178[.]128[.]255[.]179
11
104[.]24[.]105[.]254
7
104[.]24[.]104[.]254
4
54[.]87[.]5[.]88
2
52[.]21[.]132[.]24
1
104[.]16[.]150[.]172
1
104[.]16[.]149[.]172
1
104[.]16[.]152[.]172
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com
33
bc-prod-web-lb-430045627[.]us-east-1[.]elb[.]amazonaws[.]com
25
hjhqmbxyinislkkt[.]1j9r76[.]top
22
bitaps[.]com
11
chain[.]so
11
btc[.]blockr[.]io
11
hjhqmbxyinislkkt[.]1a8u1r[.]top
1
Files and or directories created Occurrences %TEMP%\d19ab989
33
%TEMP%\d19ab989\4710.tmp
33
%TEMP%\d19ab989\a35f.tmp
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\03809a07-348b-48cc-b08d-f7b8472c133c.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\07a5080e-becd-4719-9a79-fe50b59eb55b.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\0d984a6a-e70e-4747-bded-b92173e85c21.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\0ec91619-5478-4e5c-aa1b-8da00a066091.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\115556d6-ba8b-4b18-8439-8e9c81ff63a4.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\1e81fb27-0aa3-4b11-a764-0d9e7e3272ea.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\3c6a9801-329c-4eba-9524-2165ac426bef.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\52c39d7c-6d6b-4ad3-b5e5-c417949d335d.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\5318eba9-773d-4fec-9366-6e84f8dfbbc5.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\5394c05d-dc33-4d24-bd45-2d8954648f28.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\62e3dfa2-4350-445b-8693-d1d04a74543c.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\6a8b0e06-e9a5-4761-afda-29391149e64d.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\70c3a864-35fa-4245-802a-dbda1e3f4c00.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\70d1f452-966e-4e28-8da5-8b2eeadbe078.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\7b168dd1-e39e-4b39-918c-53b9e78365e9.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\7dceec06-0991-43f4-8af3-601c0ebeb910.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\8339d228-5ca6-486f-8793-633aa6af18d8.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\a4fbc2bf-8cc2-4a6d-b3c7-0ef749399e7f.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\a507cd65-0038-49e4-8cdb-b6082f566351.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\a6f0f9a9-e50d-4612-9e8e-f5640793680c.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\a9e6bb3f-0b62-4410-86f7-68bb36989df7.png
33
%LOCALAPPDATA%\microsoft\onenote\14.0\onenoteofflinecache_files\b1503304-9b12-4d90-89e7-df30e304e6c2.png
33
*See JSON for more IOCs
File Hashes 00d8580b7de2d5cfcdeb6d896153cb43aeb8086ad87c320a20528fb0ab382c83
0156cd32b9647dcd19ef44503aa99dfcfb891365a6a1e0a4f364e1b882563a77
049e95486dc15591857897db7e038204ad7669afc52f6e413ad8eef6a042a3f3
0543292cf63218e40d9785a1e6e0b9cc0dddd34cd6cfdbd6e6735e7b2cd7767e
05e6572e963ec98373c94748dba580a9d4c99ced95d2c4e455cf2e952973404c
06d5ae8d97a7b3bb50330f566130ce3b0ceced3a9b92ff1b5be9b2a3b08dec89
09e5adc6762e13f50bbc4b3e233c00c44c77cab958bd3e30212034fe0a2471be
0af56173b6a8d920e8f42c564d590373d8a8c55edda2476deff5013a39d76d87
0cfb5e263ca7a4f5b38cd79c111eeeb7cb6e2e3150fc07996fd7b74a739452e8
0dccb9d4f1369026b350c848d98e0aadddd063ed231c9682419735b25d4cd1e0
0e2f515b821c6995dff04862e4808609e3ebfcb7dbf4cbd2884dc3b737657580
15f59c6041fbb1a8f54e083a4f501076efa61941f5064db404c2914be4973e2f
16f2a805ea445edf5c9cdab4d530235204acccaa50cda907dbb84177f71eda57
179ecfd3969f0f2aef94a99467064e60ef737bac9819439bcbe1b3ca2dffee08
183bad8c045acadaa5cdd8542fae8f05539249c0df2448816b3895a6d949caf3
1860ec3f04583312079795ca661360e723092217e0880ddc7e48345829f571a8
19e65785549059911db9ad54bbdbb8c4f86d6a4cc6710d8572b81afed213250b
1d44d8a762ee2f1f9813482b862428add0c081fab9bb27a4bad082a118b5e509
20122bc23fc55bbc44a920e8b9c06829a13e78258356798a64c224a534e06faf
2070face5382b738dda8e2a42c56b233793a9751fb6722e970d77da207d52f1f
20842d1ad99423e0412187f7f365ce5b9d93c2499df5bcb9da16a8d196b3e94c
244820be643b64929d14af90218aa67f2e9b2cb07d8654c5ead2d60a25f8ead3
2c670078bda065d704ed155173fc59438a15e71244c0f47ccf95d12225e27eaa
2f29ed32c90581269668e03216169207478721f2b9d59ebfb389a647c6a1f51a
2f3bf21023544bc5ade37a16588cf51aa6ac8327685de3953f44de57a3068a8d*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid Umbrella Malware Win.Trojan.ZeroAccess-7432508-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: Start
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: DeleteFlag
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: DeleteFlag
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: DeleteFlag
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BROWSER
Value Name: Start
31
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
Value Name: ThreadingModel
31
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
31
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
31
<HKLM>\SOFTWARE\CLASSES\CLSID\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\INPROCSERVER32
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Type
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: ErrorControl
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: Type
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: ErrorControl
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: DeleteFlag
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Type
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: ErrorControl
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Type
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: ErrorControl
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000010
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000009
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000008
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000007
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000006
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000005
Value Name: PackedCatalogItem
31
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK2\PARAMETERS\PROTOCOL_CATALOG9\CATALOG_ENTRIES\000000000004
Value Name: PackedCatalogItem
31
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 68[.]58[.]140[.]128
38
180[.]254[.]253[.]254
31
166[.]254[.]253[.]254
31
135[.]254[.]253[.]254
31
117[.]254[.]253[.]254
31
119[.]254[.]253[.]254
31
134[.]254[.]253[.]254
31
206[.]254[.]253[.]254
31
222[.]254[.]253[.]254
31
182[.]254[.]253[.]254
31
190[.]254[.]253[.]254
31
184[.]254[.]253[.]254
31
197[.]254[.]253[.]254
31
183[.]254[.]253[.]254
31
158[.]254[.]253[.]254
31
204[.]254[.]253[.]254
31
24[.]149[.]4[.]58
29
97[.]95[.]231[.]238
28
50[.]68[.]78[.]41
26
188[.]26[.]185[.]40
26
111[.]250[.]107[.]91
26
173[.]175[.]25[.]91
26
184[.]166[.]16[.]43
26
24[.]98[.]179[.]133
26
79[.]115[.]11[.]4
26
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences j[.]maxmind[.]com
31
Files and or directories created Occurrences \RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\@
38
\RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\n
38
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\@
38
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\n
38
%SystemRoot%\assembly\GAC\Desktop.ini
38
\systemroot\assembly\GAC_32\Desktop.ini
31
\systemroot\assembly\GAC_64\Desktop.ini
31
%System32%\LogFiles\Scm\e22a8667-f75b-4ba9-ba46-067ed4429de8
31
%SystemRoot%\assembly\GAC_32\Desktop.ini
31
%SystemRoot%\assembly\GAC_64\Desktop.ini
31
\$Recycle.Bin\S-1-5-18
31
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f
31
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\@
31
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\L
31
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\U
31
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\n
31
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f
31
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\@
31
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\L
31
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\U
31
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\n
31
%ProgramFiles%\Windows Defender\MSASCui.exe:!
31
%ProgramFiles%\Windows Defender\MpAsDesc.dll:!
31
%ProgramFiles%\Windows Defender\MpClient.dll:!
31
%ProgramFiles%\Windows Defender\MpCmdRun.exe:!
31
*See JSON for more IOCs
File Hashes 0157ed115b5bf4c7be57c400db2d0565f5ad1b6df2bb63d85ca04932d190f83a
02deef08e12b0ca6d311bd47d984587fc2eacee659bccd5b03f470d04baf7fda
05e354a637fc39a732a2042d70be6d4ff0d7250f746a89bda5833787b1d73f77
05e9764e72fd580377b26682b329ede539bab36a7c651f17e78bfed628f29236
070a5d1c0a35171169531caa0583f46ef8ce39d8e8a5f4806ea0060a8311e3c2
08a22538c4474de9d510516b31169eb4bbcb111333f45463387540ee1c802094
094f81ace5dc69455869040c8306a5c89ed318a0209feb9883c65dedfaa1607a
1078cbea870ad246012c3e5d7383a34b73b71d743b8a7814b916afb22dafc052
12092b610aec4b3a4abd1704aa5ca7796afb88ed2d62813f64e69813179bf17e
13297a1a4dae8afcae7683ca66825a041fde54b3a34347c5ae9cd1ca540bfe65
15c92af968516aa50e2434d678099993d616322ed64c28fbedbdf9f58f688cfe
1ccece616c3bf43763c2f4159894df3170e8e017359a432fcf574df86ed4d9c9
1ddede2f503ec591648dee15162794cc8c44bc39b40aaa209a344c4d8741b59e
1e40c41b83c1dfdcf4f62b52a3248f7de7d14e9d20c622f3d58b56e873e90ada
1e6bd842bc6e5a5a27e4c9124f4f8d0cb99bf13fe07f33ae4ebddeaeccddc065
1f213cb034864518007496d9f81834a202e2fbb24f60685c0d38af4127230b7e
23095a64ad977a038141d7a51d9b16fffb690671c4cba65f4aa9cab1ead68d9d
245aa365f4df9a087650d523cfb5685f5e0a22faf3948de28e4516ff7574daec
26fc9dad694e24ab9f22f40ecae7b5ce436d3e7f0fdc7c0dc91a33967ed3bcb3
2afc92a8de98e29db880f1bbd0cde81e4cc2e49dce0bdafb5d992511be97dbca
2fbc30feb2a4a8c926b69b762e898bda305d5333a198b2a1304644a1bff6176a
352d14133cb2f89223d15a81fa44442ef7b033b3646b12a92f69d82d27718f67
38257554ec967969a8e114bb6588b63210b83a0a76a7f1cbf0eb17b6e10ab91f
3852da85c0d4541fea5bb3812eaec3b7247aae76c57c6a4ad7271b76d50acb8d
3be059379396caf75330c4f1fa97adc8f5683cba16eeaabcbdd9ccbd8055b748*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. CVE-2019-0708 detected - (24000)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP) request. Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Process hollowing detected - (246)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Kovter injection detected - (209)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Dealply adware detected - (191)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.
Gamarue malware detected - (159)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Excessively long PowerShell command detected - (101)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
Installcore adware detected - (88)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
Special Search Offer adware - (25)
Special Search Offer adware displays unwanted advertising in the form of popups or by injecting into browsers and altering advertisements on webpages. Adware has also been known to download and install malware.
Fusion adware detected - (20)
Fusion (or FusionPlayer) is an adware family that displays unwanted advertising in the form of popups or by injecting into browsers and altering advertisements on webpages. Adware is known to sometimes download and install malware.
Corebot malware detected - (20)
Corebot is a Trojan with many capabilities found in other prominent families. It features a plugin system to enable it to load a variety of features from the C&C server at any time. Known plugins include RAT capabilities such as taking desktop screenshots, as well as being able to intercept and modify browser communications and steal data, especially data related to banking.