Cisco Talos works with many organizations around the world, monitoring and protecting against sophisticated threats every day. As such, we are watching the current state of events in the Middle East very closely for our customers and partners who may be impacted by the ongoing situation. We are continuing to evaluate potential threats and attack vectors, especially related to critical infrastructure and high-profile businesses and industries.
A challenge with protecting against state-sponsored campaigns is that the primary and ideal targets are potentially already compromised, either by a specific adversary or their allies who would be amenable to acting on their behalf. In previous research, Talos has observed footholds like this that can go undetected for extended periods, waiting to be modified remotely to exact a variety of potential malicious activities.
It may be difficult for primary target organizations to detect activity and defend themselves at the perimeter. Hopefully, they have employed a layered defense, which should include two-factor authentication, network segmentation and endpoint protection.
Of course, the potential also exists for the adversary to move away from a targeted maneuver to more broadly focused disruptions that could incorporate a much wider array of businesses and even consumers. This means that everyone should view this as a wake-up call — shore up defenses, update/patch your devices and focus on cyber hygiene. Employ authentication everywhere, beware of suspicious links, emails, etc. — phishing/credential theft continues to be popular among attackers. Every business should at least take a second look at every strange thing they see — don't ignore anomalous activities, take the time to see if there is something nefarious at the end of the tunnel.
While prior campaigns in the region have heavily relied on wiper malware, this is no guarantee that future campaigns will continue this trend. At times like this, vigilance is key.
Campaigns
According to US-Cert, Iran has been an active adversary since late 2011 and has been responsible for a series of attacks including some large-scaledistributed denial-of-service attacks against financial institutions, infiltration of a dam in New York state, and the destructive attacks against targets regionally and globally, including the large-scale Shamoon campaigns and the recent ZeroCleare wipers. They have also conducted a series of espionage campaigns against universities and companies to steal research, proprietary data, and intellectual property.
Additionally, Talos has found several large-scale campaigns based in the region that have included attacks against DNS infrastructure and those leveraging watering hole and social engineering techniques. Since the actors are active in the region DNSpionage, Muddywater, and Tortoiseshell will be included in the coverage list below.
The breadth and variety of both the attacks and the techniques show the capabilities of the adversary. Apt33/34 Actors have not only attacked traditional targets for espionage but have shown an interest in attacking critical infrastructure with the dam attack and have shown a willingness to be destructive in their activities. Actors in the region have also shown a willingness to attack some of the critical components of the internet, most notably DNS. These things combined make for a dangerous adversary that is operating during heightened tensions. As such we are providing a list of the ways that we cover these various attacks and a series of IOCs for organizations to be aware.
In-the-wild activities
We are continually assessing the threat landscape and the activities and actors currently operating. Based on the indicators we have been analyzing our telemetry sources to see if we have noticed any noticeable increases in activity that could be attributable to Middle Eastern actors. At this point, we do not have any indication that these activities have increased. However, this is an ongoing investigation and this could change at any moment.
Part of the process involved leveraging the mapping US-CERT had undertaken linking the APTs tactics, techniques, and procedures (TTPs) to the associated techniques on the MITRE ATT&CK™ matrix. Keep in mind these are generic techniques not associated with a single actor or nation state. Those organizations that have incorporated the ATT&CK framework should be able to map these techniques to the mitigation and detection strategies already in place. The techniques are listed below, for more details on the way that Cisco Talos maps related Mitre ATT&CK techniques to Cisco detection technologies, see this document.
- Credential dumping
- Obfuscated files or information
- Data compressed
- PowerShell
- User execution
- Scripting
- Registry run keys/Startup folders
- Remote file copy
- Spear-phishing link
- Spear-phishing attachment
Coverage
Additional ways our customers can detect and block this threat are listed below, please note that at the bottom of this document there is a more specific list of signatures and IOCs associated with campaigns and are labeled accordingly.
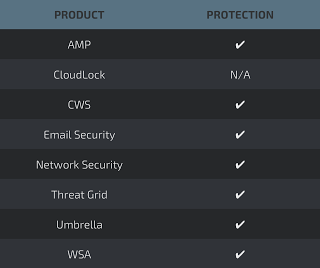
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors. Exploit Prevention present within AMP is designed to protect customers from unknown attacks such as this automatically.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), Cisco ISR, andMeraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
ZeroCleare
Snort
52572-52581
ClamAV
Win.Malware.ZeroCleare*
SCAR Trojan
ClamAV
Win.Trojan.Scar-7509404-0
Win.Trojan.Scar-7509405-0
MagicHound malware
Snort
Sids: 36579, 36580, 41656 - 41659
ClamAV
Win.Trojan.MagicHound-5859368-0
Win.Trojan.MagicHound-5859367-0
Doc.Dropper.MagicHound-5859115-0
Doc.Dropper.MagicHound-5859369-0
Win.Trojan.MagicHound-5859366-0
Win.Trojan.MagicHound-5859365-0
Shamoon
Snort
23903, 23893, 23905 - 23933, 24127, 40906
ClamAV
Win.Dropper.DistTrack-*
Win.Trojan.DistTrack.*
Win.Malware.DistTrack.*
ThreatGrid
Shamoon Malware Detected
AMP Cloud IOCs
W32.Shamoon.ioc
W32.RawDiskDriverUse.ioc
CVE-2018-20250
Snort
49289 - 49292
ClamAV
Win.Exploit.CVE_2018_20250-6869547-0
Win.Exploit.CVE_2018_20250-6869546-1
Tortoiseshell
ClamAV
Win.Dropper.Tortoiseshell*
Win.Trojan.Tortoiseshell*
DNSpionage
Snort
48444, 48445, 50348 - 50355
ClamAV
Xls.Dropper.DNSpionage-6773417-0
Win.Malware.DNSpionage-6759811-1
Win.Trojan.DNSpionage-6975387-0
MuddyWater/Blackwater
Snort
48859, 48860
ClamAV
Doc.Dropper.Agent-6935014-0
Doc.Dropper.Agent-6899904-0
Doc.Dropper.Agent-6961195-0
Doc.Dropper.Agent-6918391-0
Doc.Dropper.Agent-6964920-0
Doc.Dropper.Agent-6932616-0
MacDownloader
Snort
41661 - 41663
ClamAV
Osx.Downloader.MacDownloader-5781857-0
Other (Indicators Not Linked to Specific Campaigns)
ClamAV
Win.Trojan.Turnedup-6598671-1
Win.Trojan.Hacktool-6478864-0
Win.Trojan.Lazagne-6779429-0
Rtf.Exploit.CVE_2017_11882-6584355-0
Indicators of Compromise (IOCs)
Hashes and Associated Campaigns: WateringHole
afa563221aac89f96c383f9f9f4ef81d82c69419f124a80b7f4a8c437d83ce77
7651f0d886e1c1054eb716352468ec6aedab06ed61e1eebd02bca4efbb974fb6
9e5ab438deb327e26266c27891b3573c302113b8d239abc7f9aaa7eff9c4f7bb
8c8496390c3ad048f2a0a4031edfcdac819ee840d32951b9a1a9337a2dcbea25
5fe0e156a308b48fb2f9577ed3e3b09768976fdd99f6b2d2db5658b138676902
acf24620e544f79e55fd8ae6022e040257b60b33cf474c37f2877c39fbf2308a
7e3c9323be2898d92666df33eb6e73a46c28e8e34630a2bd1db96aeb39586aeb
165f8db9c6e2ca79260b159b4618a496e1ed6730d800798d51d38f07b3653952
55f513d0d8e1fd41b1417a0eb2afff3a039a9529571196dd7882d1251ab1f9bc
bff115d5fb4fd8a395d158fb18175d1d183c8869d54624c706ee48a1180b2361
2df6fe9812796605d4696773c91ad84c4c315df7df9cf78bee5864822b1074c9
8f6f7416cfdf8d500d6c3dcb33c4f4c9e1cd33998c957fea77fbd50471faec88
4442c48dd314a04ba4df046dfe43c9ea1d229ef8814e4d3195afa9624682d763
02f2c896287bc6a71275e8ebe311630557800081862a56a3c22c143f2f3142bd
Win.Dropper.Distrack/ZeroCleare
36a4e35abf2217887e97041e3e0b17483aa4d2c1aee6feadd48ef448bf1b9e6c
2a2a32a7e820e4a15abc96491cb3345161e189d6eaf02b62e2f86aac2c7d6c3d
cf3a7d4285d65bf8688215407bce1b51d7c6b22497f09021f0fce31cbeb78986
2fc39463b6db44873c9c07724ac28b63cdd72f5863a4a7064883e3afdd141f8d
W32.Disttrack/Shamoon
5a2f540018ca7c012a5d674bd929a0f38bf458043d4eeade1e2cdef94aab5eb8
b1c061138ba0cf34ba1dfb84e8ca89336d2a530808b42c363a69abfd6db8bf2a
052f0eb5986e92afc5460eafec293f805851cf2a98bdd2d2aed97eec6c7946a9
448ad1bc06ea26f4709159f72ed70ca199ff2176182619afa03435d38cd53237
735bf8c41e876a82815479f1e22155d0a2a47724b6f3d912c0bb995d10f8bcd9
7c7ff63898d59522bed1e4f0f7bd43a92a3167d66593628e040e36f90bfb2e5d
cd3d50629f0ed6b0ffeddd98b8cde57a6d00ec4b7f930f12ae7c0a980a9e9a00
f1710c802ce590bc737eda6d1845f390a7e7d2cf43313c3362768c5f9f94a807
4f02a9fcd2deb3936ede8ff009bd08662bdb1f365c0f4a78b3757a98c2f40400
61e8f2af61f15288f2364939a30231b8915cdc57717179441468690ac32ced54
7b589d45825c096d42bdf341193d3fd8fd9a0bd612a6ebd7466c26a753304df9
1982c011cdea5520a73ea610f46a243ccd768de87c8df4c428ead79840c38bf4
57fb0ec1eb292956a8d5031d6c2d1369acf5745b94a776aa6957e701003078d6
f9d94c5de86aa170384f1e2e71d95ec373536899cb7985633d3ecfdb67af0f72
ef35a54290d96871a860f80a789460ab10e91844a5184489c96a97b810768d29
cebdf768721473789ebe2fe79ffec7c6de0c52433b40fd02e57747f194fe0e80
7709da093dd9722e80c7c552a0935876b8d17ccf9ecc4784cffb1c1bc38dd9c0
c7fc1f9c2bed748b50a599ee2fa609eb7c9ddaeb9cd16633ba0d10cf66891d8a
66fdb7e7d868346e730113ccb9977ca840c4c337434b5fe517f7b1a858fd8317
7076c1d5c8a56820d87681754880013771fcd743a8e8bae8509e1dc682f82a5b
01e860972e621c1bd6c990d1817ebc0309dd9298f0e0819cc14d2ffcaa1820e7
a37b8d77fdbd740d7d214f88521adec17c0d30171ec0dee1372cb8908390c093
9979678be7b89a9f01c2481ea6f420417e67572f52aad66ae4ccce3c65a7b504
128fa5815c6fee68463b18051c1a1ccdf28c599ce321691686b1efa4838a2acd
788aca28addbdf2588b160a9471f7421e402f4c6b74dd303a7997be83c9c8768
5902a246ea00defd6371126b352bc3e13432cee18fef427f2ee40a6e0ba995eb
25a3497d69604baf4be4d80b6824c06f1b7120144f98eeb0a13d57d6f72eb8e9
47bb36cd2832a18b5ae951cf5a7d44fba6d8f5dca0a372392d40f51d1fe1ac34
dbdea08e7b970d395236b8e0aada6fc07fb23e6181485d86f65da1e73ab2ba2e
394a7ebad5dfc13d6c75945a61063470dc3b68f7a207613b79ef000e1990909b
04ffee9e574ae7aea7963d1f7e7dd9f9851487a743db8c86a866db7cb1b2f4d8
8cccb478de2c92b548f9976799f1b4da1bd8d6f1c821e7b0479b914939560310
d56dbe26887a4bef9b2c8f0d05f4502b80083e62ba3c7299c02e01b9eefeb2e4
4919436d87d224f083c77228b48dadfc153ee7ad48dd7d22f0ba0d5090b5cf9b
5475f35363e2f4b70d4367554f1691f3f849fb68570be1a580f33f98e7e4df4a
c7f937375e8b21dca10ea125e644133de3afc7766a8ca4fc8376470277832d95
c3ab58b3154e5f5101ba74fccfd27a9ab445e41262cdf47e8cc3be7416a5904f
bd2097055380b96c62f39e1160d260122551fa50d1eccdc70390958af56ac003
0694bdf9f08e4f4a09d13b7b5a68c0148ceb3fcc79442f4db2aa19dd23681afe
0975eb436fb4adb9077c8e99ea6d34746807bc83a228b17d321d14dfbbe80b03
391e7b90bf3f0bfeb2c2602cc65aa6be4dd1c01374b89c4a48425f2d22fe231c
ccb1209122085bed5bded3f923835a65d3cc1071f7e4ad52bc5cf42057dd2150
dab3308ab60d0d8acb3611bf364e81b63cfb6b4c1783864ebc515297e2297589
ee084f2c6fd2cc16f613fadd712641b5742489ca87851739dc868b976867858f
36414012564b88b5a2dcded39fc5ed22301ea2ef2f455bf697fa97a5925cb721
101e74ef7a18d3a790f1d30edc7bd9f4ebf0afb2cb85cffcd5710d0a53df77a6
4d4531f0372d4364e3d9b7e6ea13abf241bbc4a4b761f8a2aea67428d0de8d83
w32.Dropper/Filerase
35ceb84403efa728950d2cc8acb571c61d3a90decaf8b1f2979eaf13811c146b
5203628a89e0a7d9f27757b347118250f5aa6d0685d156e375b6945c8c05eb8a
d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a
2abc567b505d0678954603dcb13c438b8f44092cfe3f15713148ca459d41c63f
DNSpionage
9ea577a4b3faaf04a3bddbfcb934c9752bed0d0fc579f2152751c5f6923f7e14
15fe5dbcd31be15f98aa9ba18755ee6264a26f5ea0877730b00ca0646d0f25fa 2010f38ef300be4349e7bc287e720b1ecec678cacbf0ea0556bcf765f6e073ec
82285b6743cc5e3545d8e67740a4d04c5aed138d9f31d7c16bd11188a2042969
45a9edb24d4174592c69d9d37a534a518fbe2a88d3817fc0cc739e455883b8ff
Tortoiseshell
c121f97a43f4613d0a29f31ef2e307337fa0f6d4f4eee651ee4f41a3df24b6b5
2a9589538c563c006eaf4f9217a192e8a34a1b371a31c61330ce2b396b67fd10
55b0708fed0684ce8fd038d4701cc321fe7b81def7f1b523acc46b6f9774cb7b
ec71068481c29571122b2f6db1f8dc3b08d919a7f710f4829a07fb4195b52fac
51d186c16cc609ddb67bd4f3ecd09ef3566cb04894f0496f7b01f356ae260424
41db45b0c51b98713bc526452eef26074d034b2c9ec159b44528ad4735d14f4a
78e1f53730ae265a7eb00b65fbb1304bbe4328ee5b7f7ac51799f19584b8b9d4
46873290f58c25845b21ce7e560eae1b1d89000e887c2ff2976d931672390dd8
f31b5e14314388903a32eaa68357b8a5d07cbe6731b0bd97d2ee33ac67ea8817
f1c05ff306e941322a38fffb21dfdb5f81c42a00a118217b9d4e9807743d7275
1848f51d946fa8b348db8ef945a1ebff33ff76803ad26dfd175d9ea2aa56c7d0
ed150d9f6e12b6d669bcede3b7dc2026b7161f875edf26c93296e8c6e99152d5
2682328bde4c91637e88201eda5f5c400a3b3c0bdb87438d35660494feff55cf
e82a08f1514ccf38b3ae6b79e67d7605cb20b8377206fbdc44ddadfb06ae4d0d
Muddywater/Blackwater
0f3cabc7f1e69d4a09856cc0135f7945850c1eb6aeecd010f788b3b8b4d91cad
9d998502c3999c4715c880882efa409c39dd6f7e4d8725c2763a30fbb55414b7
0d3e0c26f7f53dff444a37758b414720286f92da55e33ca0e69edc3c7f040ce2
A3bb6b3872dd7f0812231a480881d4d818d2dea7d2c8baed858b20cb318da981
6f882cc0cddd03bc123c8544c4b1c8b9267f4143936964a128aa63762e582aad
Bef9051bb6e85d94c4cfc4e03359b31584be027e87758483e3b1e65d389483e6
4dd641df0f47cb7655032113343d53c0e7180d42e3549d08eb7cb83296b22f60
576d1d98d8669df624219d28abcbb2be0080272fa57bf7a637e2a9a669e37acf
062a8728e7fcf2ff453efc56da60631c738d9cd6853d8701818f18a4e77f8717
Domains: Note that these domains were associated with previous, historical campaigns
hxxp[:]//intelchip[.]org
hxxp[:]//windowskernel[.]in
hxxp[:]//nameserver[.]win
hxxp[:]//cloudflare-analyse[.]xyz
hxxp[:]//nasr[.]xyz
hxxp[:]//winupdate64[.]com
hxxp[:]//githubapp[.]online
hxxp[:]//clalit[.]press
hxxp[:]//cloud-analyzer[.]com
hxxp[:]//labs-cloudfront[.]com
hxxp[:]//winupdate64[.]us
hxxp[:]//alkamaihd[.]net
hxxp[:]//fbcdn[.]bid
hxxp[:]//onlinewebcam[.]press
hxxp[:]//cachevideo[.]xyz
hxxp[:]//mswordupdate16[.]com
hxxp[:]//digicert[.]xyz
hxxp[:]//fbstatic-akamaihd[.]com
hxxp[:]//js[.]jguery[.]online
hxxp[:]//ssl-gstatic[.]online
hxxp[:]//trendmicro[.]tech
hxxp[:]//cloudflare[.]news
hxxp[:]//windowkernel[.]com
hxxp[:]//cloudflare-statics[.]com
hxxp[:]//mcafeemonitoring[.]com
hxxp[:]//cortana-search[.]com
hxxp[:]//jguery[.]online
hxxp[:]//sdlc-esd-oracle[.]online
hxxp[:]//cloudmicrosoft[.]net
hxxp[:]//outlook360[.]net
hxxp[:]//windowskernel[.]com
hxxp[:]//mswordupdate17[.]com
hxxp[:]//fb-statics[.]com
hxxp[:]//symcd[.]site
hxxp[:]//patchthiswindows[.]com
hxxp[:]//digicert[.]space
hxxp[:]//kernel4windows[.]in
hxxp[:]//updatedrivers[.]org
hxxp[:]//dnsserv[.]host
hxxp[:]//alkamaihd[.]com
hxxp[:]//un-webmail[.]com
hxxp[:]//intel-api[.]com
hxxp[:]//windowslayer[.]in
hxxp[:]//tehila[.]global
hxxp[:]//chromeupdates[.]online
hxxp[:]//officeapps-live[.]net
hxxp[:]//tehila[.]info
hxxp[:]//ipresolver[.]org
hxxp[:]//microsoft-security[.]host
hxxp[:]//patch7-windows[.]com
hxxp[:]//winupdate64[.]net
hxxp[:]//britishnews[.]press
hxxp[:]//gmailtagmanager[.]com
hxxp[:]//hamedia[.]xyz
hxxp[:]//tehila[.]co
hxxp[:]//1e100[.]tech
hxxp[:]//twiter-statics[.]info
hxxp[:]//githubapp[.]tech
hxxp[:]//windefender[.]org
hxxp[:]//cloudflare-analyse[.]com
hxxp[:]//officeapps-live[.]org
hxxp[:]//cloudflare[.]site
hxxp[:]//win-updates[.]com
hxxp[:]//nsserver[.]host
hxxp[:]//windowkernel14[.]com
hxxp[:]//static[.]news
hxxp[:]//cissco[.]net
hxxp[:]//windowskernel[.]net
hxxp[:]//patch8-windows[.]com
hxxp[:]//microsoft-tool[.]com
hxxp[:]//outlook360[.]org
hxxp[:]//owa-microsoft[.]online
hxxp[:]//google-api-update[.]com
hxxp[:]//broadcast-microsoft[.]tech
hxxp[:]//microsoft-ds[.]com
hxxp[:]//micro-windows[.]in
hxxp[:]//fbstatic-a[.]space
hxxp[:]//githubusecontent[.]tech
hxxp[:]//hotseller[.]info
hxxp[:]//digicert[.]online
hxxp[:]//cachevideo[.]online
hxxp[:]//fbstatic-a[.]xyz
hxxp[:]//officeapps-live[.]com
hxxp[:]//windows-10patch[.]in
hxxp[:]//winupdate64[.]org
hxxp[:]//akamai[.]press
hxxp[:]//azurewebsites[.]tech
hxxp[:]//windowssup[.]in
hxxp[:]//mswordupdate15[.]com
hxxp[:]//big-windowss[.]com
hxxp[:]//newsfeeds-microsoft[.]press
hxxp[:]//walla[.]press
hxxp[:]//cachevideo[.]com
hxxp[:]//windows24-kernel[.]in
hxxp[:]//ads-youtube[.]tech
hxxp[:]//windowskernel14[.]com
hxxp[:]//mssqlupdate[.]com
hxxp[:]//mcafee-analyzer[.]com
hxxp[:]//winfeedback[.]net
hxxp[:]//sphotos-b[.]bid
hxxp[:]//mpmicrosoft[.]com
hxxp[:]//1m100[.]tech
hxxp[:]//twiter-statics[.]com
hxxp[:]//chromium[.]online
hxxp[:]//mywindows24[.]in
hxxp[:]//sphotos-b[.]pw
hxxp[:]//fbexternal-a[.]pw
hxxp[:]//tehila[.]press
hxxp[:]//fdgdsg[.]xyz
hxxp[:]//elasticbeanstalk[.]tech
hxxp[:]//akamaitechnology[.]com
hxxp[:]//google-api-analyse[.]com
hxxp[:]//sharepoint-microsoft[.]co
hxxp[:]//windows-kernel[.]in
hxxp[:]//myservers[.]site
hxxp[:]//win-api[.]com
hxxp[:]//symcd[.]xyz
hxxp[:]//win-update[.]com
hxxp[:]//windows-api[.]com
hxxp[:]//ads-youtube[.]online
hxxp[:]//windows-drive20[.]com
hxxp[:]//jguery[.]net
hxxp[:]//fb-nameserver[.]com
hxxp[:]//f-tqn[.]com
hxxp[:]//qoldenlines[.]net
hxxp[:]//fb-statics[.]info
hxxp[:]//microsoftserver[.]org
hxxp[:]//mcafee-monitoring[.]com
hxxp[:]//akamaitechnology[.]tech
hxxp[:]//fbexternal-a[.]press
hxxp[:]//ssl-gstatic[.]net
hxxp[:]//ads-youtube[.]net
hxxp[:]//windowsupup[.]com
hxxp[:]//javaupdator[.]com
hxxp[:]//windows-india[.]in
IP Addresses: Note that these IP Addresses were associated with previous, historical campaigns
206[.]221[.]181[.]253
66[.]55[.]152[.]164
68[.]232[.]180[.]122
173[.]244[.]173[.]11
173[.]244[.]173[.]12
173[.]244[.]173[.]13
209[.]190[.]20[.]149
209[.]190[.]20[.]59
209[.]190[.]20[.]62
209[.]51[.]199[.]116
38[.]130[.]75[.]20
185[.]92[.]73[.]194
144[.]168[.]45[.]126
198[.]55[.]107[.]164
104[.]200[.]128[.]126
104[.]200[.]128[.]161
104[.]200[.]128[.]173
104[.]200[.]128[.]183
104[.]200[.]128[.]184
104[.]200[.]128[.]185
104[.]200[.]128[.]187
104[.]200[.]128[.]195
104[.]200[.]128[.]196
104[.]200[.]128[.]198
104[.]200[.]128[.]205
104[.]200[.]128[.]206
104[.]200[.]128[.]208
104[.]200[.]128[.]209
104[.]200[.]128[.]48
104[.]200[.]128[.]58
104[.]200[.]128[.]64
104[.]200[.]128[.]71
107[.]181[.]160[.]138
107[.]181[.]160[.]178
107[.]181[.]160[.]194
107[.]181[.]160[.]195
107[.]181[.]161[.]141
107[.]181[.]174[.]21
107[.]181[.]174[.]228
107[.]181[.]174[.]232
107[.]181[.]174[.]241
188[.]120[.]224[.]198
188[.]120[.]228[.]172
188[.]120[.]242[.]93
188[.]120[.]243[.]11
188[.]120[.]247[.]151
62[.]109[.]2[.]52
188[.]120[.]232[.]157
185[.]118[.]65[.]230
185[.]118[.]66[.]114
141[.]105[.]67[.]58
141[.]105[.]68[.]25
141[.]105[.]68[.]26
141[.]105[.]68[.]29
141[.]105[.]69[.]69
141[.]105[.]69[.]70
141[.]105[.]69[.]77
31[.]192[.]105[.]16
31[.]192[.]105[.]17
31[.]192[.]105[.]28
146[.]0[.]73[.]109
146[.]0[.]73[.]110
146[.]0[.]73[.]111
146[.]0[.]73[.]112
146[.]0[.]73[.]114
217[.]12[.]201[.]240
217[.]12[.]218[.]242
5[.]34[.]180[.]252
5[.]34[.]181[.]13
86[.]105[.]18[.]5
93[.]190[.]138[.]137
212[.]199[.]61[.]51
80[.]179[.]42[.]37
80[.]179[.]42[.]44
176[.]31[.]18[.]29
188[.]165[.]69[.]39
51[.]254[.]76[.]54
158[.]69[.]150[.]163
192[.]99[.]242[.]212
198[.]50[.]214[.]62