While major attacks like ransomware and COVID-19-themed campaigns made headlines across the globe this year, many attacks were prevented through simple practices of finding, disclosing and patching vulnerabilities. Cisco Talos' Systems Vulnerability Research Team discovered 231 vulnerabilities this year across a wide range of products. And thanks to our vendor partners, these vulnerabilities were patched and published before any attackers could exploit them. Each vulnerability Talos addresses is an opportunity lost for attackers. Mitigating possible zero-day breeches in your defenses is the easiest and fastest way to prevent wide-ranging and business-critical cyber attacks.
Like everything else, COVID has changed the threat landscape. The global workforce shifted to a largely remote working environment and remote communication software has skyrocketed in popularity. Although there is no clear timeline on when the current pandemic will subside, fully remote and connected workforces are here to stay. This is reflected in the increased attention that Talos gave to library, web/mobile and driver vulnerabilities this year. In this post, we'll give an overview of all of our vulnerability work from 2020 and fill you in on patches you may have missed.
Philosophy
Cisco Talos' Systems Vulnerability Research Team protects our customers and the broader online community by investigating software, operating systems, internet-of-things (IoT) devices, service, web and mobile vulnerabilities. Talos fosters coordinated vulnerability disclosure via a 90-day default timeline. Working together with any vendor to responsibly close and address any vulnerable attack vector that our research uncovers which ensures timely patch and mitigation strategies. Our research provides detection content which protects our customers during the vendor response window. Upon coordinated disclosure, Talos detection content is made publicly available as well as a detailed report that you can find for each vulnerability on the Talos vulnerability information page here.
Talos also regularly releases Vulnerability Spotlight blog posts which feature an in-depth technical analysis of vulnerabilities discovered as well as a brief summary highlighting the possible impact of exploitation. You can find these Vulnerability Spotlight blog posts here.
Talos' timeline of reporting and disclosing a vulnerability, per Cisco's Vendor Vulnerability and Disclosure Policy:

In fiscal year 2020, we published 231 advisories resulting in 277 CVEs, in a wide range of software including operating systems, IoT devices, Microsoft Office products, browsers, PDF readers and more. This is a marked increase in both advisories and assigned CVE's from 2019.
While we do our best to increase coverage and thus the overall security of the Internet, bulletproof software just doesn't exist. Even vendors with large security teams make mistakes, and many don't even have those. Cisco Talos strives to increase our coverage of vulnerabilities in a landscape of insecure software and hardware. This is not an indictment of vendors - everyone makes mistakes, and not everyone has the same resources to devote to secure coding and development.
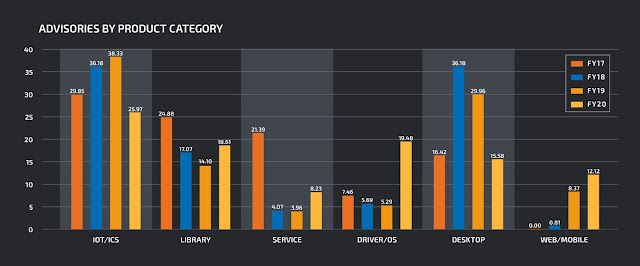
|
| Advisories by percentage |
Some highlights of this year:
- Multiple vulnerabilities in major PDF apps, including Adobe PDF, Foxit PDF, NitroPDF and Google PDFium.
- Multiple vulnerabilities in graphics drivers from Intel, Nvidia and AMD. These graphics drivers vulnerabilities resulted in Microsoft deciding to deprecate and disable RemoteFX in Windows and will fully remove it in February 2021.
- Multiple vulnerabilities in Pixar OpenUSD, a library that is used by default on Mac OS X and iOS for USD files.
- As part of our participation in Microsoft's Azure Sphere research challenge, we also found another 16 vulnerabilities in Azure Sphere.
- Multiple vulnerabilities in major web browsers such as Firefox, Chrome and Safari — including the WebKit system used by many of these browsers.
- Other major applications that we found issues include Synology's SRM and DSM firmware and Microsoft Office and Windows.
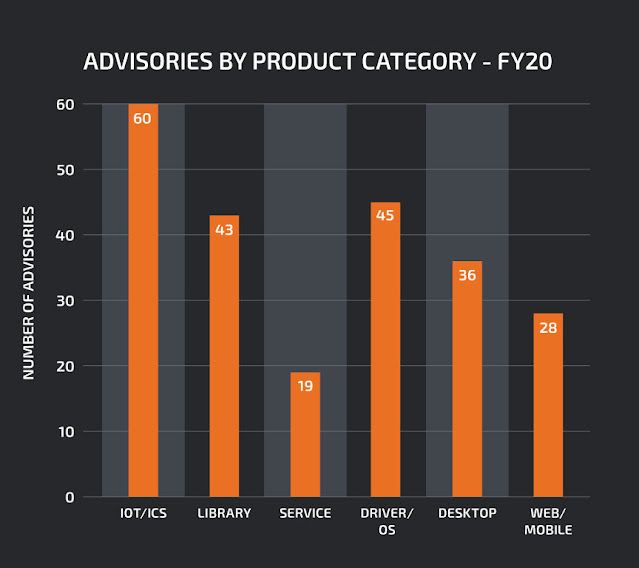
|
| Advisories by total numbers |
We work closely with all vendors under our coordinated disclosure policy, while ensuring our customers and communities are protected with detection content until patches are issued. This proactive research and content advances security for everyone, as we all benefit from more secure software and hardware.
For vulnerabilities Talos has disclosed, please refer to our Vulnerability Report Portal here.
To review our Vulnerability Disclosure Policy, please visit this site here.
