Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 8 and Jan. 15. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Packed.Glupteba-9819426-0
Packed
Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and steals sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information.
Win.Dropper.Bunitu-9819420-0
Dropper
Bunitu is malware that establishes a persistent foothold on an infected machine and turns it into a proxy for criminal VPN services.
Win.Dropper.BazarLoader-9819187-1
Dropper
BazarLoader is used to drop follow-on malware on an infected system, most commonly the Trickbot banking trojan or Ryuk ransomware. BazarLoader is named in part because its command and control communications typically occur to domain names using the .bazar top-level domain.
Win.Packed.Dridex-9819209-1
Packed
Dridex is a well-known banking trojan that aims to steal credentials and other sensitive information from an infected machine.
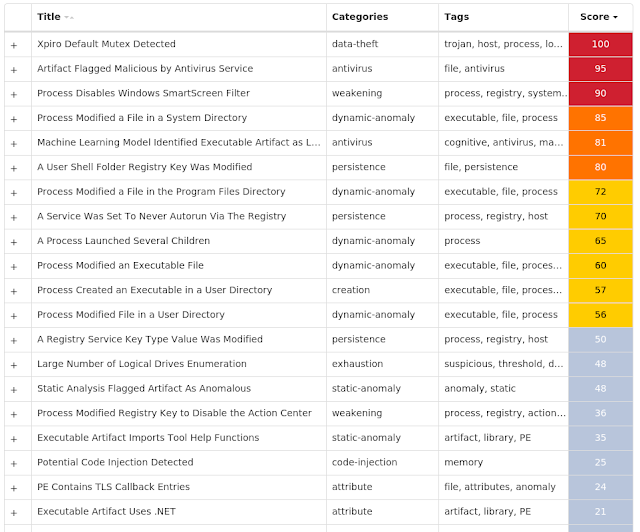
Win.Virus.Expiro-9819253-0
Virus
Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Malware.FickerStealer-9819303-1
Malware
FickerStealer is a commodity infostealer malware written in Rust and sold on Russian-language hacking forums.
Win.Malware.Tofsee-9819431-1
Malware
Tofsee is multi-purpose malware that differet modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages to infect additional systems and increase the overall size of the botnet under the operator’s control.
Win.Malware.Redline-9819608-1
Malware
Redline Stealer is an information-stealer written in .NET and sold on hacking forums.
Win.Malware.Zegost-9819547-0
Malware
Zegost, also known as Zusy, uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Threat Breakdown Win.Packed.Glupteba-9819426-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: DeleteFlag
16
<HKLM>\BCD00000000\OBJECTS\{9DEA862C-5CDD-4E70-ACC1-F32B344D4795}\ELEMENTS\23000003
Value Name: Element
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\16000048
Value Name: Element
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\25000020
Value Name: Element
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\16000009
Value Name: Element
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\14000006
Value Name: Element
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMONFS
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMONFS\INSTANCES
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMONFS\INSTANCES\WINMONFS
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\22000011
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\16000009
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\12000002
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\14000006
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\16000048
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\25000020
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\22000002
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\21000001
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\11000001
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\DESCRIPTION
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS
16
<HKLM>\BCD00000000\OBJECTS\{71A3C7FC-F751-4982-AEC1-E958357E6813}\ELEMENTS\12000004
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMON
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMON\SECURITY
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMONFS\SECURITY
16
Mutexes Occurrences Global\SetupLog
16
Global\WdsSetupLogInit
16
Global\h48yorbq6rm87zot
16
Global\ewzy5hgt3x5sof4v
16
Global\xmrigMUTEX31337
16
WininetConnectionMutex
16
Global\wpsSerMutex2
3
Global\sswxstats
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]214[.]40[.]16
16
204[.]79[.]197[.]219
12
104[.]28[.]30[.]17
9
104[.]21[.]26[.]241
9
172[.]67[.]168[.]157
7
172[.]67[.]170[.]134
7
172[.]67[.]128[.]242
6
104[.]28[.]2[.]216
6
172[.]67[.]170[.]203
6
104[.]18[.]47[.]206
6
104[.]21[.]1[.]88
6
104[.]27[.]150[.]210
5
104[.]27[.]151[.]210
5
131[.]253[.]33[.]219
4
104[.]28[.]31[.]17
4
204[.]79[.]197[.]200
3
104[.]28[.]3[.]216
3
104[.]18[.]46[.]206
3
172[.]217[.]197[.]102
2
173[.]194[.]175[.]138
2
173[.]194[.]175[.]95
2
94[.]130[.]204[.]130
2
195[.]201[.]243[.]176
2
148[.]251[.]238[.]14
2
104[.]27[.]187[.]4
2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences easywbdesign[.]com
16
vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net
16
vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net
16
fotamene[.]com
16
pioncker[.]com
16
myysuper[.]com
3
server13[.]easywbdesign[.]com
3
thirdptop[.]com
3
server7[.]easywbdesign[.]com
2
a1815[.]dscr[.]akamai[.]net
2
www[.]adobe[.]com
2
googlehosted[.]l[.]googleusercontent[.]com
2
swebgames[.]site
2
translate[.]googleapis[.]com
2
redirector[.]gvt1[.]com
2
setbird[.]site
2
clients2[.]googleusercontent[.]com
2
server1[.]easywbdesign[.]com
2
r3[.]sn-p5qs7nsr[.]gvt1[.]com
2
r3---sn-p5qs7nsr[.]gvt1[.]com
2
server12[.]easywbdesign[.]com
1
server3[.]easywbdesign[.]com
1
7d681903-73ec-4d85-94b8-fca3aa28a136[.]easywbdesign[.]com
1
5cd92230-7319-4080-ba3f-be595046b199[.]easywbdesign[.]com
1
4f40063b-290b-4ee1-8af3-77d545a7b1c3[.]easywbdesign[.]com
1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\Logs\CBS\CBS.log
16
%SystemRoot%\rss
16
%SystemRoot%\rss\csrss.exe
16
%TEMP%\csrss
16
%TEMP%\csrss\dsefix.exe
16
%TEMP%\csrss\patch.exe
16
%System32%\drivers\Winmon.sys
16
%System32%\drivers\WinmonFS.sys
16
%System32%\drivers\WinmonProcessMonitor.sys
16
%TEMP%\Symbols
16
%TEMP%\Symbols\ntkrnlmp.pdb
16
%TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02
16
%TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error
16
%TEMP%\Symbols\pingme.txt
16
%TEMP%\Symbols\winload_prod.pdb
16
%TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361
16
%TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361\download.error
16
%TEMP%\dbghelp.dll
16
%TEMP%\ntkrnlmp.exe
16
%TEMP%\osloader.exe
16
%TEMP%\symsrv.dll
16
%TEMP%\csrss\DBG0.tmp
16
%System32%\Tasks\ScheduledUpdate
16
%System32%\Tasks\csrss
16
%TEMP%\csrss\collectchromefingerprint.exe
3
*See JSON for more IOCs
File Hashes 0ab9a985f16a8fd8cfd31574180e2109ebf6f88e75fb2e16d966fca13a8f969f
1f8b0dac5cb2e3ba0a1341333e702ba11a276e3ef5e9cb17070921dffefd5734
3ae41434c248ba674a1bbf93a7302962b7845dcb63fd1dbbd085cecd9dea1243
4a30172b43ba3b77ce944e245369fe1f8d1bad742a448d626f0f36100841dff5
60d1bd8c47f122e5cfe9b3a02a09684d08bc85f8223f83de98a49b230ee8e189
66b63477620a1a540b65322e48c8de7bbcaf9b417d80a43bc89662ac19f1f1b4
6ad76dd2ae941604a6ae26ed2c41033efbf16a04a7fc82f682d9a66d07f76a3b
78354a477af61648620b4b2f44f3a28477aa2f86a199ac88548f84212fb16767
81b146b0e1bb17861f4cf6e823b96690d78032f2f69128aa50034951943bd3af
8bf465b3670c7c1e541d848eb4f2c4ba730e309caed3c22038e1457746632f7b
96fee0eabe5b07d1b2441698327069823c2b308e215d30b32a24263bdaea22ae
a0f74dff52e0c5e868fe5e242a15c121dab7e0a986f1a9afab9f7fa8ff0955b7
b0d0f56625c4ec6ccf9cf013897cba690d1b490ce1bb619dc8eca6cbcc503764
e5b16d78857c729001b060d22708f93d2bc4664c0f9e8891e296c307ba09072e
f316f9c9f635457b330e76e1f5dcc2f3c1b2522bfa280c1d99eede9f71894e89
f78e42d31ef6a91b65d74fdeacd34419c8f1804a19a11996ec15c91c8ccf6351Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Dropper.Bunitu-9819420-0 Indicators of Compromise IOCs collected from dynamic analysis of 61 samples Mutexes Occurrences fe711d65-f31a-4c22-a12f-cec65d231941
29
55731fe5-97ad-47dc-953f-37a8aca1451b
29
3c159c86-0e90-47d1-ad37-788c00ba2948
29
1cce886d-1841-4e18-963b-15f2e90a3c44
29
069e4409-bd54-4a1f-8e37-49da2cf6a537
29
9b765102-98e7-43e2-a003-f8cbdfab8a64
29
0ca9a8d3-01bf-4f9e-bfc7-7eb51e67e0c4
29
d86a1229-2cb7-409b-a3de-5366eec3db90
29
16ed8dab-ee6b-44ea-8cea-31c66d6864b9
29
1a379834-6135-41e7-9cf7-e79a9f705fbc
29
2c0c5f0d-6ad7-4c97-b1a8-2c706d03a4f8
29
f967041f-20dd-4d31-a34a-f5e04bdfdf7b
29
5440d9f2-2c16-411f-8204-a206c9c20cd4
29
9f093bf8-480b-414c-a8e8-5d9c6da83576
29
056c197d-b3e0-4bae-b639-97cccbc504ef
29
6a833436-8b37-450b-9753-8cc18364fa88
29
ad0482d7-c686-4267-8b7b-352cdf811081
29
ee67405a-96ab-46be-b946-ec5875d07506
29
0e22932c-5c83-43e2-9133-8de798150a45
29
2af4e2d5-a194-4fda-9f51-273b7773809a
29
248c3593-c2fb-4734-84f8-5847c460f1d9
29
661f7562-d95a-47d4-866d-09e98860b559
29
d483fc17-c43d-4259-81c4-1668415ee2c5
29
e0e6ea1b-d3d8-4802-abd2-bf6c69f72b6f
29
049a72ba-fac1-4970-baea-d08d0abf0a99
29
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]199[.]229[.]251
8
5[.]61[.]40[.]13
8
5[.]61[.]42[.]235
8
216[.]58[.]206[.]107
8
172[.]217[.]197[.]138/31
6
204[.]79[.]197[.]200
4
172[.]217[.]197[.]102
4
172[.]217[.]197[.]100/31
3
5[.]199[.]174[.]223
2
45[.]153[.]240[.]65
2
194[.]109[.]206[.]212
1
172[.]217[.]197[.]113
1
205[.]185[.]216[.]10
1
178[.]79[.]169[.]193
1
159[.]69[.]36[.]3
1
128[.]31[.]0[.]34
1
199[.]58[.]81[.]140
1
23[.]21[.]42[.]25
1
54[.]235[.]189[.]250
1
23[.]21[.]140[.]41
1
18[.]133[.]158[.]66
1
165[.]22[.]5[.]30
1
195[.]189[.]99[.]121
1
51[.]38[.]147[.]96
1
93[.]228[.]169[.]237
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences b[.]myvlownsnow[.]com
8
r[.]myvlownsnow[.]com
7
admex175x[.]xyz
2
api[.]ipify[.]org
2
servx278x[.]xyz
2
cds[.]d2s7q6s2[.]hwcdn[.]net
1
ctldl[.]windowsupdate[.]com
1
elb097307-934924932[.]us-east-1[.]elb[.]amazonaws[.]com
1
yan0212[.]com
1
Files and or directories created Occurrences %APPDATA%\MasterTok
29
%LOCALAPPDATA%\frunkuf\frunkuf.dll
8
%TEMP%\CC4F.tmp
5
%TEMP%\9E5E.tmp
4
%ProgramData%\ptaq
1
%ProgramData%\ptaq\afpi.exe
1
%SystemRoot%\Tasks\afpi.job
1
%System32%\Tasks\afpi
1
%ProgramData%\iwhwwk
1
%ProgramData%\iwhwwk\ctbx.exe
1
%SystemRoot%\Tasks\ctbx.job
1
%System32%\Tasks\ctbx
1
%ProgramData%\mnlomki
1
%ProgramData%\mnlomki\ahcqcl.exe
1
%SystemRoot%\Tasks\ahcqcl.job
1
%System32%\Tasks\ahcqcl
1
%ProgramData%\xuol\aleaj.exe
1
%SystemRoot%\Tasks\aleaj.job
1
%LOCALAPPDATA%\nitasfa\nitasfa.dll
1
File Hashes 01b9f7dc34a07b72ab789c9ac8f281d667ce662f4135bc76ff90a7da856f5add
041f205d037f64240995ce8445e2d6a08df0e072cc4f6584ec1e99eeb68e9e47
053e03f95369487d35ce6bd9d4c6c470909a4f9b1b2a62c05b1e2922f0c0e292
07d630cc0ec09159c95cd0e143814ae882d81587b7be146a4ca76a9de08e0215
0ac23547fbef3ba4e1406b9a7d3df6d084d58a91a7d203efb9646b75ca27d7f3
0b5157e7be4ca8cbdae9474238e767631422ff6d46c93de5b08247f153aa9c18
0f125189072bfb8379b79645abc69f19cb3e5a6ee0ccf0fd716b2ff25ca9dc43
0f3dbd4ed64c00c733fba9b66a09b82272e0add84c6c79c26f0d24454c83939a
133b9577b9297ce3d9330fb2dba4c904d765d7de608cae491f4297376ad67e63
1727aedcbeff54ddbfe28715273b392e5a6ce0e57ee61ecbb124c1111a41430e
1a52788602e6cd8128c8f520c7fe1d8f4d0def477f466f421f51cec1c7596800
1ba243aef62b1c6feed908ffc4acbcc69a9c5187fd9c500d2191d283ca475385
294e517fa8c82e31042801d9e979811a125b0f225cd0a69adb41d607de72f1c6
2a6acfe4f845e47435d6584c0e475ef734019d6ac8ce6013b60a6869087d5b00
2c204bb06e4a59eb7edf50ae87e99b08857e362ff625e8cc51696e2979bf8281
36c4ab1110858033bc056186bab5c9112300c51d3740fcb660c30a81860a53e5
36f12d7f9dd7490fdca202d2a0a353933cd8e5b41bb733d565f071f1b17a9577
373d9fe298e314a18963d440266466535130b6fde3c4ba8708fd60a36c9c6093
3b24746ab542c90734a45a72d0ca9d4c2e2846ec2201ecc6321908380a80a537
3f1e1aaaaf845c3449962b2fa397b9dd576a825cfc4338ab21ad558d3d14117b
413ba9b7fe6678399136439c229aca5e91c215b110b667e2131998858a4da768
47f7b6dd760728ac7b3e9866b0a0320cb543066d38999316e28448b7942cf009
4ea7b6b8257b4719ae70e5312eb99ccfd1efa178e368f710ccc5fab55b644014
5ec5f731eacf9816979494df0295f77415e659e8f9e306fbc3b1ed098a48ff32
613f577ad18d6a4d4db4af89f6ce5f1cc2d898875a7dbb278688722c0092b00f*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Dropper.BazarLoader-9819187-1 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Mutexes Occurrences {98821448-3638-4f11-831f-edbf359cd4ad}
5
{b54b793c-ee44-4b0a-99bf-2954404ad218}
5
K9PM2Z2XQO5YDC3ETDFDM8XVPV47T
5
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 185[.]82[.]127[.]115
7
94[.]140[.]114[.]152
5
107[.]152[.]32[.]121
5
192[.]236[.]155[.]212
5
192[.]119[.]171[.]165
5
185[.]244[.]151[.]185
5
185[.]121[.]177[.]177
4
208[.]67[.]222[.]222
4
208[.]67[.]220[.]220
4
5[.]135[.]183[.]146
4
169[.]239[.]202[.]202
4
69[.]164[.]196[.]21
4
217[.]12[.]210[.]54
4
5[.]45[.]97[.]127
4
82[.]141[.]39[.]32
4
162[.]248[.]241[.]94
4
172[.]98[.]193[.]42
4
192[.]99[.]85[.]244
4
142[.]4[.]204[.]111
4
176[.]126[.]70[.]119
4
142[.]4[.]205[.]47
4
172[.]104[.]136[.]243
4
163[.]172[.]185[.]51
4
51[.]255[.]211[.]146
4
89[.]35[.]39[.]64
4
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences impactpsychcoloradoo[.]com
7
freekaratee[.]com
5
birch-psychology[.]com
5
elevateyoga-denver[.]com
5
flourish-psychology[.]net
5
busybjjj[.]com
4
flux-psychology[.]com
4
noservers
4
cubiibek[.]bazar
2
ektuuded[.]bazar
2
ibufuded[.]bazar
2
qeliudom[.]bazar
2
wyufeluh[.]bazar
2
owfionew[.]bazar
1
owolibqe[.]bazar
1
owoltoew[.]bazar
1
owoludqe[.]bazar
1
owostoca[.]bazar
1
owtiibca[.]bazar
1
owyktoew[.]bazar
1
owymsoqe[.]bazar
1
owyxsoew[.]bazar
1
tuogonyw[.]bazar
1
tyahsoem[.]bazar
1
tyisibca[.]bazar
1
*See JSON for more IOCs
File Hashes 0e809ef68d85e730190db2663ab914dfd6ccb4c355a051841366b3a5c91ada63
102dca8d268dbbba33770459009d4d67e0d714b44523c28fce57ee83fe186a31
21df8a331f272ed9b6b72509028af31612292c9f3c0776a4472b2b585c142648
2be628add2ab1be6120026893c6a7a51dc0b3f81c7421349504a6010581aa427
2c6b49185dea80c48dcdd1c316a0de3413ff52a67819a720419c630093b5e638
392c73ffa3b1513cd8de9435d7e76320eff7f98db884eb6bc776c3b2bea7c77e
3941242436e943fbfb7b1767aa2615bcc5637da3d939d3b06a1572de8bf044a1
3985648d781de545cf1209469454b88f7f6e54696b6a050dbb7ba2ba1eae2cec
436301cb89dadecb6c6cefc043b8a4d8f47de2054b1e84e1612cf061cd14dc15
44075e5eb7ee76b006a8f4cf2bfee30dec3c5007c02f8657f956429bb976ea4b
4be75ecc81192ea74d09a2d60a3dd629426fcb988800784112a1d7877344a503
4c4b00621d0e57bcdf188174a539ca3c92a4fc96647eabe6d79c17ae04bd519d
67da5b6ab704468511385140553e23d9481bb7865bddf87d9b333cc7990d7504
6aefd19d41aa2a2584d25b5b89230c33bc13e9b55c73896e94b661546073dd81
74d757a4cabf26009ab5f1064939c54ceea43a8399419a7c965b2edb7e0ed648
82dbcaa7694a6e763300cee1d4b2ef6e65f6a65fd93663365ce032823984cb21
90a51557f3438fec9b2ffab5828751cb43fa9eeb1fa84468effe95a9f13f12d0
b8d852655caae079b534ff0f058dc3843a7d38c5ca646d78423bf40bdc9d6d91
bbe896ab541c703d699f97311a30c2e07be98be1ebf7eed9a9a1fd7dfa2efb5b
bed288ad6037546ecfb9e912518583fefbb7685681a8ecfd5b27502735de20bd
c422ea456bf322b5033f2d8a968e8cd7b1be47a6e310612c90840e2df76fbc49
e1841e78c6dace694cc5172bac1068b9ede38a3623c5429a877eb1190d90a14d
f088236bb9ad5bffd42b6328ae966344444311f79f9d679d8256ce3656fa6ad9Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Packed.Dridex-9819209-1 Indicators of Compromise IOCs collected from dynamic analysis of 83 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: trkcore
83
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableTaskMgr
83
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0
Value Name: CheckSetting
83
Mutexes Occurrences QwfpZjePnU
1
aPsTj6VuEa
1
311Mkr7VEd
1
uM2op9CoOl
1
D9s3f7uTP8
1
7IWGS8xVSK
1
5UNwjs08pW
1
tilsevyDm1
1
3Vd3jMXCQX
1
DRu3Sh5gdu
1
UoPPnHjG8C
1
dZuTID11Mz
1
puOK1waZHz
1
RdyHdMSjZt
1
fIdRIvDpxc
1
el9rzspeWr
1
154PDLu0Ly
1
UDozcoidFa
1
eoQAqaQr7s
1
X0Des9pz0v
1
TSjcc3p9fB
1
la9yxJSgEV
1
JtBjxsI6IW
1
VCHG6rkcVW
1
i0txY7uR76
1
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]217[.]12[.]206
68
104[.]23[.]99[.]190
40
172[.]217[.]10[.]78
6
72[.]21[.]81[.]240
6
104[.]23[.]98[.]190
6
172[.]217[.]7[.]14
5
205[.]185[.]216[.]10
5
173[.]194[.]175[.]139
4
142[.]250[.]64[.]78
4
173[.]194[.]175[.]100/31
3
173[.]194[.]175[.]102
2
204[.]79[.]197[.]200
1
205[.]185[.]216[.]42
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com
83
ctldl[.]windowsupdate[.]com
12
cds[.]d2s7q6s2[.]hwcdn[.]net
6
cs11[.]wpc[.]v0cdn[.]net
6
www[.]79otjy24xk[.]com
1
www[.]bnyuwmkw6o[.]com
1
www[.]fcn4uyhfin[.]com
1
www[.]ftbtlvr2s6[.]com
1
www[.]ibxa6gy5sn[.]com
1
www[.]lggglkzaia[.]com
1
www[.]53uuqwro9b[.]com
1
www[.]et0wbgprfg[.]com
1
www[.]i67uljtaxm[.]com
1
www[.]kojspnmyqr[.]com
1
www[.]owjmdbkr6e[.]com
1
www[.]qb61cfv85k[.]com
1
www[.]sxmorqgytc[.]com
1
www[.]t9pb4oeyjo[.]com
1
www[.]yn4uwob8mf[.]com
1
www[.]zgil5ledvy[.]com
1
www[.]1cctewxjyp[.]com
1
www[.]nreyta6cwu[.]com
1
www[.]awr6zkq2hs[.]com
1
www[.]qfzyebsybv[.]com
1
www[.]v2kht7we14[.]com
1
*See JSON for more IOCs
Files and or directories created Occurrences <malware cwd>\old_<malware exe name> (copy)
30
%TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp
11
%ProgramData%\Microsoft\Windows\SystemData\S-1-5-18\ReadOnly\LockScreen_Z\LockScreen___1024_0768_notdimmed.jpg (copy)
5
%ProgramData%\Microsoft\Windows\SystemData\S-1-5-18\ReadOnly\LockScreen_Z\~ockScreen___1024_0768_notdimmed.tmp
5
\Temp\HncDownload\Update.log
3
%LOCALAPPDATA%\Microsoft\CLR_v2.0_32\UsageLogs\HncCheck.exe.log
3
%LOCALAPPDATA%\Microsoft\Windows\Explorer\ExplorerStartupLog_RunOnce.etl
3
%APPDATA%\Microsoft\Windows\Themes\CachedFiles\CachedImage_1024_768_POS4.jpg
3
File Hashes 0235205e1d9636a0212eeb08c8f4440a2b2cea3199c15b3e028a5ba2df9b89b7
0260d9ee215c86c1a2510f93293ec03c31af5c849a2d7782765ada9e3b073bba
06049be088c3e16f6466db4c9db36750b120017ce56f602f02001f80c43defe8
06dc7541d25c3bb8d6c06b3699273989d931399660430497cf2104be962e69b2
07b319c358717257f94a8847aa5871a5cf385468fef9aa862f4a4ebe85bd27e0
09351b5ea74e8aff44ec6ea78f1858d65b40122fdf0e49785d94c7a395f51d72
09a059c0af0fff338f88de6097d49bf98059b3af9a8a53d3ff05e5583f938b6e
0bda655e36e76c74eea73ed3cf5514a2eed04f79b336c94c7b8da9e60527eb43
0cbb84597e5fdf76cbc16fa6a162ca83dc58b3790fa4fe97b4a810eb86ba249f
0eaee28da99f8119a2a657a975d526c5145d70adb1dbd3fd0cf02d0787d0db8a
13f0005573bbb598472171ce1b805a59d861ea8be1497f619d525af829dd1a96
1518bf354a6294bc73b3306ae6ee82ce2ea87c6d958c4b4df6b536992702d4d5
157ca7deeec5d7d2175cbac88b87fb8b2226646470976dfda465e4ad4dc471cf
158c6cc9463c87524162549eb4763d6a1a6678356678d50f9a7a5a3b85936b6e
16c67593a4238afae9d159aee0e75d0f4d5413338acba8dbb708d6240e032fc4
17136a99f935a72f7fe7b5aa486f4c27d5348cbd28c2925bdb638235466ae810
184de8e4ae9093ed129feb26ca81792f9e2707b5a1f5c89383788f10c53f62f4
192033da234e1f5fd76cc774fe4ed4a9059b343984acbcc0743fbe157790ee16
1be901d747349de5ac0d9e6f3fdf7a37dd2f260b70cd5cd5d61c6991089ba1b8
1c8b98ca9bda4e72ec5dd588d8b7a1bbf839ef49007c360b25c7bd7966ff25a5
1cfba48ee57f732ae3831bffb449483a5651c126553b87240a86816f7e212743
1ec9bc3a47a431f966c75675113167edf15b4e2f09ec978de1a8cae2ef8336da
21fc207a10dac9c4f424a97461eec17ec33e2c79f9259e1bd9a9c417617b2c2a
24917890f07c86e438add11172b9500e47d30f0ac0e13bf0a3563cb4387fdebc
2769715955f85e336e2c9091f575b5b70457ae39a30bc16113e761016fba449e*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Virus.Expiro-9819253-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Start
16
<HKLM>\SOFTWARE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500
16
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM
Value Name: EnableSmartScreen
16
<HKLM>\SOFTWARE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500
Value Name: EnableNotifications
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHRECVR
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE
Value Name: Start
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\SHELL FOLDERS
Value Name: Startup
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\USER SHELL FOLDERS
Value Name: Startup
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64
Value Name: Start
16
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE
Value Name: AccumulatedWaitIdleTime
16
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE
Value Name: RootstoreDirty
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\ACCESSIBILITY, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=B03F5F7F11D50A3A\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\CUSTOMMARSHALERS, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=B03F5F7F11D50A3A\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\MICROSOFT.VISUALBASIC, VERSION=10.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=B03F5F7F11D50A3A\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\MSCORLIB, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=B77A5C561934E089\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\PRESENTATIONCORE, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=31BF3856AD364E35\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\PRESENTATIONFRAMEWORK, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=31BF3856AD364E35\1
Value Name: RuntimeVersion
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\ROOTS\PRESENTATIONFRAMEWORK.AERO, VERSION=4.0.0.0, CULTURE=NEUTRAL, PUBLICKEYTOKEN=31BF3856AD364E35\1
Value Name: RuntimeVersion
16
Mutexes Occurrences Global\mlbjlegc
16
Global\Media Center Tuner Request
14
eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-18
13
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
11
Files and or directories created Occurrences %CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE
16
%ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE
16
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe
16
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe
16
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe
16
%System32%\alg.exe
16
%System32%\dllhost.exe
16
%SystemRoot%\ehome\ehrecvr.exe
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log
16
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log
16
%SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog
16
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngen_service.log
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenrootstorelock.dat
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat
16
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenrootstorelock.dat
16
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenservicelock.dat
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat
16
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.lock
16
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngenservicelock.dat
16
%LOCALAPPDATA%\rqboqelc
16
%LOCALAPPDATA%\rqboqelc\cmd.exe
16
*See JSON for more IOCs
File Hashes 01f092156a79e974530a99d5698711279acf9f73e322c6ea9da1544eed06e550
06a8da750a8deba5cb4df7bc69173dcf9e9e05f3872c6ee6975c5b4fd2f3db50
0db81bfc08d9cf6a02fa97d7b7384774840ce979c62be17c2f5e0089897164e1
23b16b3fe5a962c2282c097f02f0061fe38b60827fde49d2fe78341712b797a6
36f702a33e824babd5e1838e9b2a589d75778cb66368b3ac2055da3519661b39
52b305111828c5637dbc74738aa89d55abcbe4ac70a14c70f38a7f1373f3fe55
6014b7ccc366123c5b73f6d615d1abd2e8f01f50a7aa677301cc71b03f634d31
672334067e99cf9861c7e78631f8a2ab5c74b5172c82120d6bc47a305e7f2bfb
6b94b49ef54089c0bbf8eb4610332521e94fa7f6ae84449df3f3f86d4243d07b
700f2beedab087e9c7876adbb5c37a01dfcf71c47dadeed0e3adea63e6ad6a3c
8816c73995b821633bd60feff641fa15f58799e5b299f477bcaf8785e5a56e1f
9e6defed8098dfe5654fc4b9c10bd852a76b560ae1d3044a6d06d8c09e7408d0
9e782c6f64a63b1c0e8751fe6185234c6deacca0a8bebbc1b0996f040c645485
e123b1fa253faced17dae411ccb97d88ebb9812b9863fb099ad900d28b265f5a
e8c70cf85c5824504ee91d028a3827b019b9a52c2d533308bc1e25b426ab901b
fe0a57e614cae59e3cbe3057073f96b2342f7abbbad6ac003d66a7efd7490f04Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Malware.FickerStealer-9819303-1 Indicators of Compromise IOCs collected from dynamic analysis of 30 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: LanguagePack
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: LanguagePack
1
Mutexes Occurrences hrth
8
whoareyoutellmeandilltellwhoyou
8
ah;waeh;jftyjftyjfiftfdgaf
8
hotyjftyj;afdh
8
ijlhlkwaftyjftyjftjftyh;joi;i
8
o;jtfytyjftyjftyjftyj;ijo;
8
whftyjftyjftyjtfyjtfyjtfyj;ijo;h
8
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 195[.]2[.]74[.]126
14
195[.]2[.]81[.]120
4
50[.]19[.]243[.]236
3
192[.]0[.]47[.]59
2
199[.]71[.]0[.]46
2
104[.]26[.]13[.]31
2
54[.]221[.]253[.]252
2
93[.]115[.]18[.]170
2
93[.]114[.]128[.]19
2
194[.]99[.]20[.]177
2
172[.]217[.]12[.]206
1
199[.]212[.]0[.]46
1
192[.]0[.]32[.]59
1
54[.]225[.]66[.]103
1
178[.]237[.]33[.]50
1
54[.]235[.]83[.]248
1
172[.]67[.]75[.]172
1
23[.]21[.]27[.]29
1
54[.]243[.]164[.]148
1
23[.]21[.]42[.]25
1
54[.]243[.]119[.]179
1
185[.]150[.]117[.]41
1
54[.]235[.]189[.]250
1
195[.]2[.]92[.]125
1
23[.]21[.]140[.]41
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org
8
elb097307-934924932[.]us-east-1[.]elb[.]amazonaws[.]com
4
api[.]ip[.]sb
3
whois[.]arin[.]net
3
whois[.]iana[.]org
3
checkip[.]amazonaws[.]com
1
www[.]geoplugin[.]net
1
lmdfdmserv275[.]xyz
1
oribba[.]xyz
1
jennante[.]xyz
1
tallipere[.]xyz
1
Files and or directories created Occurrences %ProgramData%\kaosdma.txt
8
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp
2
%APPDATA%\Microsoft\Protect\Once
1
%APPDATA%\Microsoft\Protect\PREFHIST
1
%ProgramData%\s7r8y2v9v8r8y2v9v8\softokn3.dll
1
%ProgramData%\s7r8y2v9v8r8y2v9v8\vcruntime140.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\freebl3.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\mozglue.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\msvcp140.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\nss3.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\softokn3.dll
1
%ProgramData%\s8v0x2v3v8v0x2v3v8\vcruntime140.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\freebl3.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\freebl3.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\mozglue.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\mozglue.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\msvcp140.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\msvcp140.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\nss3.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\nss3.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\softokn3.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\softokn3.dll
1
%ProgramData%\s8p4p5w8r0p4p5w8r0\vcruntime140.dll
1
%ProgramData%\s8y8w9x3p5y8w9x3p5\vcruntime140.dll
1
%ProgramData%\s9w4r2q7v7w4r2q7v7\freebl3.dll
1
*See JSON for more IOCs
File Hashes 0b2912254415369ba173ffd6cc6fd7e36f36213af815f742ef7355cf2b90de70
0cf759e84869d51a965c314d25d91910812381f44503de2fe00186cc137c7d81
108565e95c7741954e78ba0d9a4d4f5c2802354468acd4ebf40cdbcdc4cc5297
156e73756bf43eb9ee514dfb4258129f2c5f8890e960023ea9fcd148d73486c4
15759d1074ad9603fe637e83e453f4fc0d44f5983887d23b17d2236ccf8215cf
16948f00f5875f5e7440922233d4a0aa02236c829a6ebc3b19853cc3a91f21c1
1f6d0a74e3c9ab7b4fa94960b61f0abd81a9545273389a482f396c7a77c20a19
2250e4939f282894313e84ea1595dc312791a5301f0452f55a573039cf3815c3
2ba751611d815dc342a32712610f7fabe78e34780c35e4145879645529810ab5
4fe78a3eac1b4a1dce616b3fc39fa174c8b112d681edb5985243be24cd0724de
5106598337fc2af29e0d03cd72651dc0373e390453e26100f9d3cfbd52387d18
63d1f8f4ca47893ca7638bc49e5ab48cfd14203a9c7acd8774c497bdc9887e6c
63d4fa397b3b294e145968a0f90dd6237e557ece059a2b78547a1f862af83147
64eaa2aa7b575c37c74dbff88a0e4b67c3f2aed7f6b89bd107f39141f0cf02c2
674f30cc21a0790ebf32af6876c8eef7efbba7daf458ba8aef719408832c9338
6912e997963c1e8c93d3272be7f0b09b8036e12ea112663888ea3a94cd1777b0
7482f5805808c17c3d8224a0854f25fd79f90bcda5321ae49c6c9810c9605160
7920398ae747e67aca018921e6c1584abb3cd6f7ad4bf4d47f51bff071bf8287
7e4f06d93d9bb99cc6b3c893f1b3eb406bb62a3326bfed89d76b6eabdcde990b
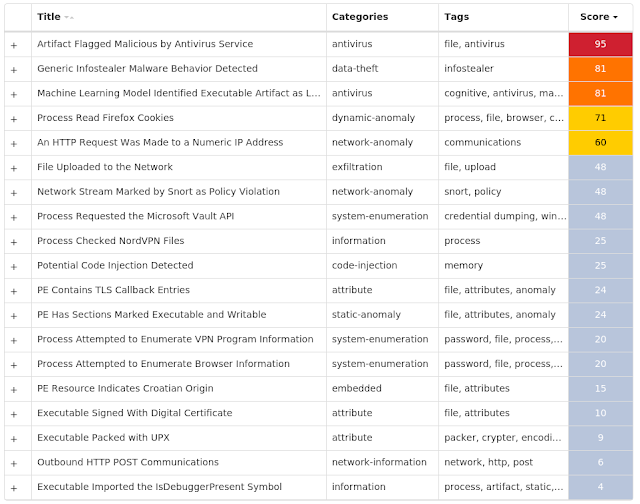
7eea90f98488448767a72df890cb7f23ed40aeac937a32642bd72cf60f202352
831447cbcd8817ded39594bfc10383e3cd8b4d0efa7e5346d3bec67543a8e566
8536077bc00de4f9544abb3c3b299cf6cc11e813f649dcc53c382306bd0a5278
8ef14192d1a811a59e27bb697dbece52b3f630b5c0d69910c9d4540cfaa118db
90609ab4a6ca57cfef46702d027a94733ffdb7ad35c6aeeae5d4beede3033de7
97a267b363b9621d1cc69fa705f89cb0f353ebda1b117f2ed4edd39dc342ee50*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Malware.Tofsee-9819431-1 Indicators of Compromise IOCs collected from dynamic analysis of 34 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
34
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
34
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
34
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
34
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
34
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
23
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\gzntsagv
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\jcqwvdjy
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\xqekjrxm
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\unbhgouj
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\haoutbhw
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\athnmuap
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\tmagfnti
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\piwcbjpe
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\slzfemsh
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\qjxdckqf
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\ohvbaiod
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\exlrqyet
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
34
69[.]55[.]5[.]249
34
104[.]47[.]53[.]36
19
157[.]240[.]2[.]174
19
5[.]9[.]72[.]48
19
217[.]172[.]179[.]54
19
130[.]0[.]232[.]208
19
144[.]76[.]108[.]82
19
185[.]253[.]217[.]20
19
45[.]90[.]34[.]87
19
31[.]13[.]71[.]174
18
176[.]9[.]119[.]47
18
43[.]231[.]4[.]7
17
185[.]254[.]190[.]218
17
69[.]31[.]136[.]5
16
104[.]47[.]54[.]36
15
172[.]217[.]197[.]106
15
172[.]217[.]197[.]147
15
172[.]217[.]12[.]196
14
157[.]240[.]18[.]174
14
47[.]43[.]26[.]7
14
163[.]172[.]32[.]74
14
87[.]250[.]250[.]22
13
67[.]195[.]204[.]72/30
13
172[.]217[.]197[.]103
13
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net
34
249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
34
249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
34
249[.]5[.]55[.]69[.]in-addr[.]arpa
34
249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
34
249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
34
microsoft-com[.]mail[.]protection[.]outlook[.]com
34
schema[.]org
24
msr[.]pool-pay[.]com
17
api[.]sendspace[.]com
16
ip[.]pr-cy[.]hacklix[.]com
14
market[.]yandex[.]ru
13
work[.]a-poster[.]info
11
www[.]amazon[.]com
11
119[.]151[.]167[.]12[.]in-addr[.]arpa
10
d3ag4hukkh62yn[.]cloudfront[.]net
8
iv0001-npxs01001-00[.]auth[.]np[.]ac[.]playstation[.]net
5
www[.]google[.]es
5
www[.]google[.]de
5
www[.]google[.]nl
5
www[.]google[.]co[.]in
5
www[.]walmart[.]com
5
www[.]google[.]se
4
www[.]google[.]it
4
www[.]google[.]ca
4
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile
34
%SystemRoot%\SysWOW64\config\systemprofile:.repos
34
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
34
%TEMP%\<random, matching '[a-z]{8}'>.exe
33
%System32%\config\systemprofile:.repos
25
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
22
%TEMP%\tvqwpcm.exe
1
%TEMP%\cezfylv.exe
1
%TEMP%\ikflerb.exe
1
%TEMP%\gidjcpz.exe
1
%System32%\beyeagh\gidjcpz.exe (copy)
1
%System32%\vtrnuzt\omvwfbqm.exe (copy)
1
%System32%\sbrjqyv\ulhofeim.exe (copy)
1
File Hashes 003f4e0f105169a5cf0e772718728b430c897fc83b9f5738b35dd7163680707a
0fc78609bf9010369a7ce4af472363a3fd4f0f5236e1e286d890ef44681e36b7
190e4a1584728b3e1ba15794530ca6927d338e5a5ede8e0c54f8ffea706affc8
2359f3547a13a3cfc5c91a1f96cecb789fe9c0348ed5d28d4e27cc27c905413f
28802e8e05dffead15c34bfefc62f292edf1aef2296e61b8cef5f1a0c77c6799
2cc9f1ddcedc781d039edac5a9f5389b65b0b7faaf50da0322ccbebc16b84d2b
359c52e1098060c7931ce5d336f636f8ee7499d863d4bcc7bd77c2b7c0289ff3
36f13ba2e0ac7c19e0594cb0f48ebabbf0ca2690def1564e0a0d23b36d2fda7f
36f9410a9790af54b0c9a890fc2bb9158212f92663c12179aaf0d7cda28cce8a
3be1a6c30364eeeac74e64b281a524749aa8dce908bffe41d7f5b3113975ba75
54af3997de833515af5de6eaa0f7244595161e1826ee3e6b545fad5ffaec12b9
591bf1855957fbbf960c547186d7b645b7676c6cc883798230190d2da49c19e0
64b46abeca0ad9e783811a9fffd330229e5b43fcd44d80d9bd2f4ab3cb8f5325
68e52283e52ad93b8769cce40a9d948908ba3276a26037160163bfc76aed6730
694d0d490e1ec0a1ab62d962ddb13f8e008843ccf3f292dfac2b8f1d45eaf156
6c02a2a3672cc18a30d542e5882ff82767ff34c181efbb709ebdbd2fc707cf3a
6cee45ce3d918a417a8ef184309c08ae7db537bcc05e38a2ff0c9b8a536b864a
6d85bbed5fafd7b15e04e4378e85bf95a34ae6628f75810fe8af0f6ced2d1ff8
714d78ce37a800894ccabb97de96b493d175e4e2c0be9690c27e6db1962b407a
715dfee4ece1c24ef3b17957e3af3ca8e880e1afe8eed38c8f62e22f996e63e6
725b286a9d16d2a077f8188930c0ed225ad7801746bd94994884085a69f231d9
7304fa5629bacc1356b2d56e3a594f6e938b89b8e51197b8c9572babff57d868
79aa9ba38068ca0b1eb6882e28c8169bd1fbac1ae691a8665a53d95cc71f51a0
7a1c23fefa1f7679186400d168d1d39a3e3b969521af9eedf20eec7c50b8dfb7
7a9606c0f24b92126ef2f3d9b618f3ab9314b479d58c8525c1046c4f6cf21e1e*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Malware.Redline-9819608-1 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]67[.]219[.]232
9
104[.]21[.]24[.]187
7
Domain Names contacted by malware. Does not indicate maliciousness Occurrences longwhitelice[.]cyou
16
Files and or directories created Occurrences %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp
16
File Hashes 11bcab49e564310f5137a9b638bb1ead9ea4028e67ec802d45c811686987ab23
3af849f44fc729ecb867eefc88181ed5675a72d5cbfe736e5dc63e129e51e2a3
4b615d44ac84e330135132d0ff062ba98cb8fe732f2e2b6d2e6020012f0fc2f2
542e8b2a3dc3d972ba5cfb92c44858513c520581a95eeb92d1597707554531a0
8be12c2f0a37e68f263de19b06095020562903c83426babb1e724034e3db8c36
96831d9c6375ec9b80ef3fa55342320442b8517830858c41d548fc0f7891cc7e
99906bef27e8c3ad2639430c820319224742e5bf8f72338de3767be5812ebe20
a411474abab8d40856f636addf0d619dda7f38524bbbcbd441dec955189eba74
ae8d0276030d8012703f9f0a8a6a1bd04d5eb9265f77eaf5e230c62807fc8c2f
b6602a904550cc5d953aaa241665e10f402c74c3ba0ddd5219360d5d8704dac0
bed7057aaac834046123cff7d683ed732af201c890b68fc40901a9e1af2a86ae
ce38bed65320a0149f1792d5667a3a5c60939f34aee97717167ccb9b504dfde2
e6d402a709bcbfec6628b8e4ecdc8828ff28f8ef1f9ecc041d17160cc8b5a859
e99a3bab431d695d60e2a588c24424e5c9de525c774f8ae09ecc85f495ddcf20
f6e29141a3a658983b3ea700f34cb10d1231e9781e2fe26206883f783cc95d0a
f90e4be8b5208be16eac10a9287f33422f869fecf036011a73fd0001a8caa063Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
ThreatGrid
MITRE ATT&CK Win.Malware.Zegost-9819547-0 Indicators of Compromise IOCs collected from dynamic analysis of 40 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSQQWK WWQCQSEM
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSQQWK WWQCQSEM
Value Name: ConnectGroup
3
<HKLM>\SYSTEM\CURRE
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSQQWK WWQCQSEM
Value Name: MarkTime
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSTRBX RDPNRKXQ
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSTRBX RDPNRKXQ
Value Name: ConnectGroup
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSTRBX RDPNRKXQ
Value Name: MarkTime
2
<HKLM>\SYSTEM\CURRE
Value Name: ConnectGroup
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: ImagePath
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: FailureActions
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: ConnectGroup
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: MarkTime
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSIWOA WMGKUSMM
Value Name: Description
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSACGJ PROLVJNR
Value Name: ConnectGroup
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KEFRAP VLSEXWFC
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KEFRAP VLSEXWFC
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KEFRAP VLSEXWFC
Value Name: ImagePath
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KEFRAP VLSEXWFC
Value Name: DisplayName
1
Mutexes Occurrences Global\ec134b81-56cd-11eb-b5f8-00501e3ae7b6
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 174[.]128[.]255[.]252
3
118[.]102[.]11[.]13
3
101[.]254[.]149[.]206
3
204[.]79[.]197[.]200
2
61[.]142[.]176[.]23
2
118[.]193[.]233[.]10
2
47[.]111[.]82[.]157
2
219[.]235[.]1[.]7
2
61[.]147[.]125[.]184
1
123[.]56[.]41[.]200
1
35[.]244[.]181[.]201
1
34[.]107[.]221[.]82
1
103[.]214[.]170[.]249
1
103[.]212[.]33[.]244
1
59[.]56[.]72[.]201
1
118[.]126[.]16[.]84
1
66[.]117[.]8[.]164
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences tribeboy[.]eicp[.]net
3
qq2209458045[.]f3322[.]org
3
813305377[.]f3322[.]org
2
17v0o99672[.]iask[.]in
2
xmchz[.]f3322[.]org
2
yao709[.]vicp[.]cc
1
jcsb[.]f3322[.]org
1
www[.]qpf001[.]com
1
hclm110[.]f3322[.]org
1
lbaabb123[.]f3322[.]org
1
bybug521[.]3322[.]org
1
hkchenxi[.]meibu[.]net
1
Files and or directories created Occurrences %ProgramFiles(x86)%\Microsoft <random, matching [A-Z][a-z]{5}>
8
%ProgramFiles(x86)%\Microsoft <random, matching [A-Z][a-z]{5}\[A-Z][a-z]{6}>.exe
8
%ProgramFiles%\Microsoft <random, matching [A-Z][a-z]{5}\[A-Z][a-z]{6}>.exe
7
%ProgramFiles%\Windows NT\Yeeskam.exe
2
%ProgramFiles%\Windows NT\Wewkymk.exe
2
%ProgramFiles(x86)%\Windows NT\Wewkymk.exe
2
%ProgramFiles(x86)%\Windows NT\Yeeskam.exe
2
\6618.vbs
1
%ProgramFiles(x86)%\Windows NT\Iyyesms.exe
1
\268.vbs
1
%SystemRoot%\Txgcvxe.exe
1
\2980.vbs
1
%ProgramFiles(x86)%\Windows NT\Mib
1
\5075.vbs
1
%ProgramFiles(x86)%\Windows NT\Cksasos.exe
1
\4448.vbs
1
%ProgramFiles(x86)%\Windows NT\Osefzqh.exe
1
\1444.vbs
1
\9412.vbs
1
\8798.vbs
1
\9607.vbs
1
\6440.vbs
1
%SystemRoot%\SysWOW64\Sumiemu.exe
1
\5106.vbs
1
%ProgramFiles(x86)%\Windows NT\Suggece.exe
1
*See JSON for more IOCs
File Hashes 003bf1d2e2213bef6d1d2437045dd868722c0046caa2b8b8e02ec782f284f021
0b822644516bfcef097cd9d85fb2b5dba7f1fd655fc4e4d3cbbe264fc216d271
0e4e60751074fa387946051f6e604d8727b55e7180d607d9b22242e2a85e92a4
1249727b2bed9ec5abda7995602457ccc308b4eeb398cc905e6a95d7db6feed4
1b2723f06c8e0341d2a0462128f345a03b3f64c77a7ade133c5fa3a973eb01e9
1c831609051813f8a5f53999db590270c9126b2875bb47025810c9890cb6ffb0
1f3cb94fe40d095029ebb84a13baf98e0a471c48aa8595f549106526dbddadd8
231ee6de5b09fe471d9dffacde6302e7617ff5df8518fde3d8f13b34c10a8abd
2ae5c5b742586bcf88cb1d7c8df12c72a6a49a3df281fc5a2dd0bdbc8a365177
2b9d28dc19015ebe9155de796d6ce68b65cac0986561a394e4ea4da1b0ea6d42
30e104213ad9b49b07f5c7d9186894557ee547a8ab711fb08d905f185c367168
324435ae3d162ab6de8c125c20079a0315e1d12da9f7c6cf602aaf750fcccbde
3626136fa08df12a480f0b4e2e3fcbf725feaec3c5d7b50c2bcca5a590f15812
370c3bdd6fe3df390349a1d9a5250fa38d92f284cf4cdd0d401620c728ac6bb1
38f99a66469a1a96ce0d42971fa9cff2933ff445c5b67f5ab6ef451def0bb908
3ae01359a4c5f12482b4b86278b8b2300a3b3deeb2222be3a8f48127ac5a87d9
3c83d0237d6bd96e1018cc14167b2eb43b6939b5a219ffdc849da3c540f9457e
3d9fce2dfc530299ebae2fb1662861bdc5e7f79f06e536d9e28a3b3c88f8f577
43f2a67a245863acb3b433b64ee7e1271a704114c6ae1162a9d38875625d46ae
44e43d97579f393ac0c98cc4803e147c4ec196cc8a815bf977aefcc2d73a7942
4a264b2825a10f61ccff7c10e9e4f81997324467cfdf6419cc48b17d272cf2a3
4dc64b9529c284be07c723553bfa28f011ea9e62dc4e03b555a7328ca69be438
4fa0e49145197258e2d90caa6a17d67daaab9c05061b9a89f43b297126e72bf3
503542ac2746b3016cad1db027acf0b3b5641fcd41aa44101aab3e7a8133549d
522ed8df43739cf35d5ea2a883aba86054b1f16e27c6ba8667e0906daa22c295*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP
MITRE ATT&CK Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities.
Dealply adware detected - (4613)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.
Process hollowing detected - (3453)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
A Microsoft Office process has started a windows utility. - (1214)
A process associated with Microsoft Office, such as EXCEL.exe or WINWORD.exe, has started a Windows utility such as powershell.exe or cmd.exe. This is typical behavior of malicious documents executing additional scripts. This behavior is extremely suspicious and is associated with many malware different malware campaigns and families.
Kovter injection detected - (860)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Squiblydoo application whitelist bypass attempt detected. - (713)
An attempt to bypass application whitelisting via the "Squiblydoo" technique has been detected. This typically involves using regsvr32.exe to execute script content hosted on an attacker controlled server.
Installcore adware detected - (390)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
Excessively long PowerShell command detected - (388)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
Crystalbit-Apple DLL double hijack detected - (345)
Crystalbit-Apple DLL double hijack was detected. During this attack, the adversary abuses two legitimate vendor applications, such as CrystalBit and Apple, as part of a dll double hijack attack chain that starts with a fraudulent software bundle and eventually leads to a persistent miner and in some cases spyware deployment.
Gamarue malware detected - (115)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
CVE-2019-0708 detected - (112)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP) request. Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.