Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Dec. 31 and Jan. 7. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
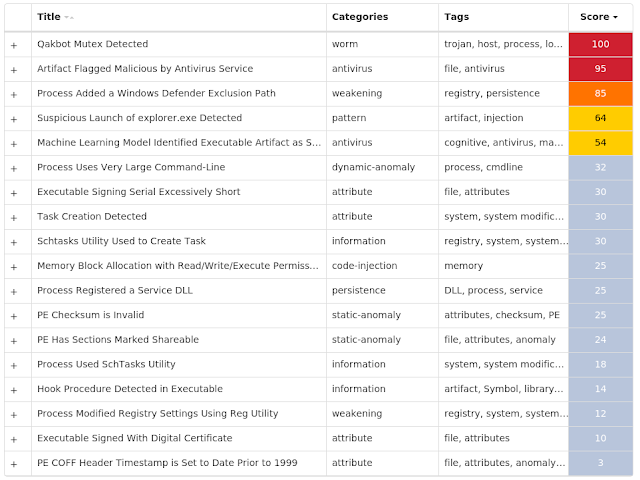
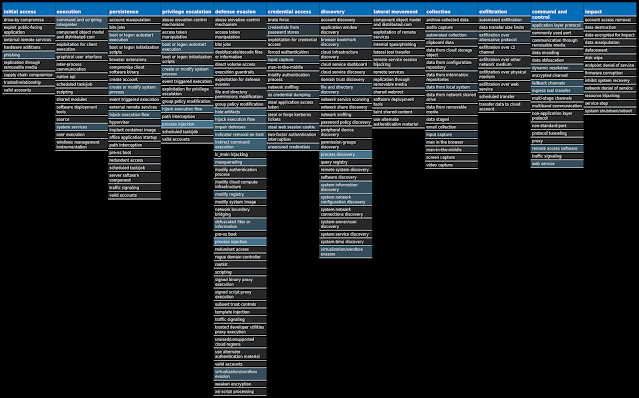
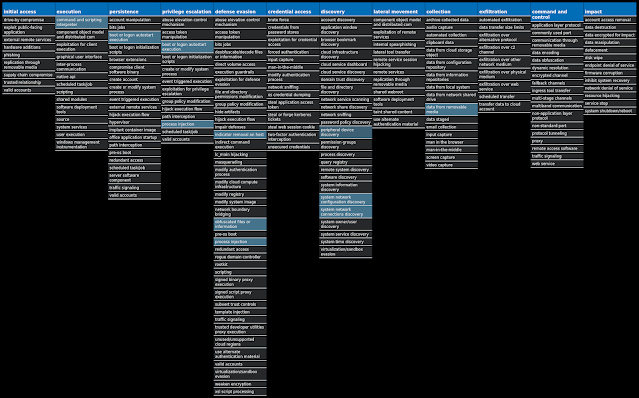
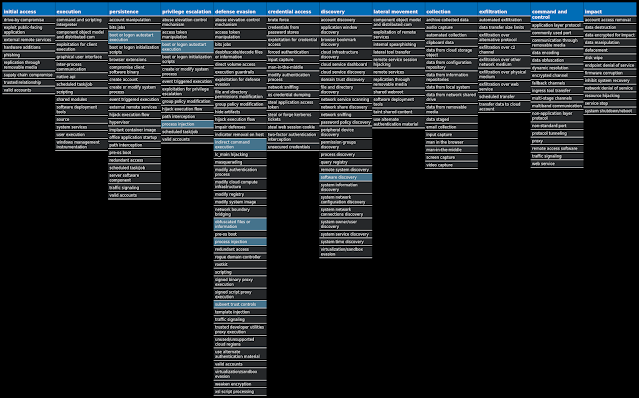
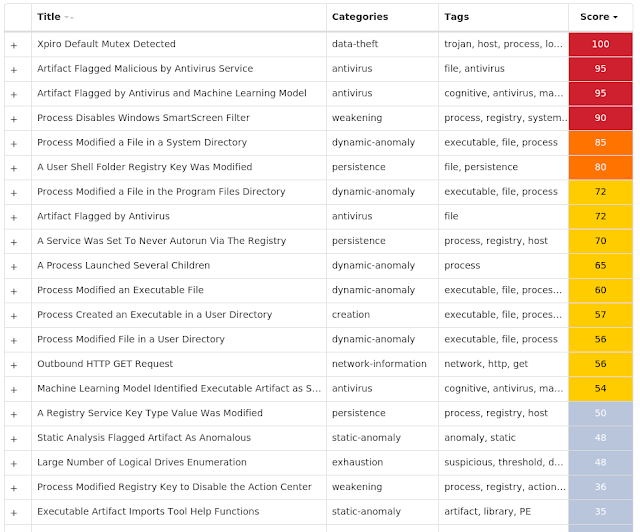
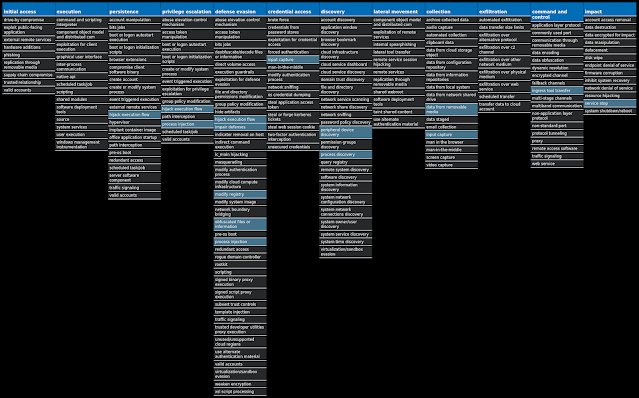
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Trojan.Qakbot-9924229-1
Trojan
Qakbot, aka Qbot, has been around since at least 2008. Qbot primarily targets sensitive information like banking credentials but can also steal FTP credentials and spread across a network using SMB.
Win.Malware.Tofsee-9933691-0
Malware
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control.
Win.Trojan.Gh0stRAT-9928675-1
Trojan
Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks.
Win.Downloader.Upatre-9934126-0
Downloader
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. This malware downloads and executes malicious executables, often banking trojans.
Win.Packed.Zusy-9932471-0
Packed
Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Win.Dropper.DarkComet-9932930-1
Dropper
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include downloading files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Virus.Xpiro-9932984-1
Virus
Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Dropper.Remcos-9933257-0
Dropper
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Dropper.Kuluoz-9933836-0
Dropper
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. It often is delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
Threat Breakdown Win.Trojan.Qakbot-9924229-1 Indicators of Compromise IOCs collected from dynamic analysis of 37 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bd63ad6b 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bf228d17 37
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: f7b512d3 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: ff0b3567 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: fd4a151b 37
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\ProgramData\Microsoft\Ecrirfryzd 37
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Users\Administrator\AppData\Roaming\Microsoft\Xtuou 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: b5dd8adf 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: 80425a91 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: c22ac29d 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: ca94e529 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 79eea72 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 7a96a5f8 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: 45f6727e 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: 38fe3df4 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 5dfca0e 37
<HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 88fc7d25 37
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\AIWIGKCO Value Name: 47b75202 37
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\\SIGNATURES Value Name: bybpxju.job 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\\SIGNATURES Value Name: bybpxju.job.fp 1
Mutexes
Occurrences
Global\{06253ADC-953E-436E-8695-87FADA31FDFB}37
{06253ADC-953E-436E-8695-87FADA31FDFB}37
{357206BB-1CE6-4313-A3FA-D21258CBCDE6}37
Global\{280C5EDE-5A47-4F1C-97D3-B8CFE4CF258D}37
{280C5EDE-5A47-4F1C-97D3-B8CFE4CF258D}37
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org17
isatap[.]example[.]org5
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com2
computer[.]example[.]org1
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com1
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com1
Files and or directories created
Occurrences
%APPDATA%\Microsoft\Xtuou37
%ProgramData%\Microsoft\Ecrirfryzd37
\TEMP\sample.dll1
%System32%\Tasks\uzzfcfeja1
%System32%\Tasks\rgpagsnkum1
%System32%\Tasks\nqlhmsvvr1
%System32%\Tasks\rulrpoq1
%System32%\Tasks\atedfbcijx1
%System32%\Tasks\aniqbhus1
%System32%\Tasks\ztzqhswde1
%System32%\Tasks\vbtliwae1
%System32%\Tasks\bvgluvp1
%System32%\Tasks\eyevaabnzx1
%System32%\Tasks\najlnxj1
%System32%\Tasks\jvayiiiax1
%System32%\Tasks\hdkofgb1
%System32%\Tasks\ietqzlmnk1
%System32%\Tasks\fhkjrymy1
%System32%\Tasks\ysldzei1
%System32%\Tasks\dniinjqzy1
%System32%\Tasks\mqxdiwzkep1
%System32%\Tasks\xjecbugqmj1
%System32%\Tasks\bybpxju1
%System32%\Tasks\bhioelzycq1
%System32%\Tasks\iluzaryx1
*See JSON for more IOCs
File Hashes 01e16f0b3d9a51d8d5ec1d955e1acbbb17cbb29b7272634ea7941331135e07ae
02241908fb5bb63858807d8b307cce9d6b03227958f3b401196239d8c6f19253
0297be18782977e4555405f89616c266f5f8e5640c49c4bda4785ffba10ae324
032550997e4a1487a526d92f0b3c42e3abe23784806d10b0e4f7ee0f180f4a5b
072b6c7647e7335b870392b325d44799c84bf99ea96dc904991e40656bf2c187
0870c2af5a5aae70c9aaf87156e8804411a42c06d6ffb06f25bc25a3bf4ed7ef
0baf6ecbcbb90241bf60015cf14b95945ae4b82125743a6aa486fd83aaca54df
0d43a3c205e8f0afab98b54c370837ceec490a11874a90d7589bd15e65f1901c
0d715e6881533e18a77c86f1a950e50cff677e9cd3078b895ac8aec98352b3c9
11713306b39ec65d73b1edc64aaab89546e881b3aece4edebbc0f056e7b62487
1736547c85a4702779713a248ced337011d5a4c47639535e98e98177896397da
17d57c8aa7536959e45dd55a6cae0b9b0c64c02f7a6b7545c2b5b1e350e70bd7
1c93d8de51131599bec513a1575f24bd858a490dccc724239984f8bf4882034e
1cb5a596781b8b41d6e7e6c2ede7e021dc7557b6a9207b7e6c918dfe1baf5fce
1d50fb2a219b8ad5901474cf59f1598832d1d89b208729803272d7cbf9231623
1f0b854919f8101ccd0d9f4b8073d3b4fcf7119a3e40389f25e74cea9f140553
1f7192c63a108a20f5d9021ef852ac26700290e05f9080ca1c915a4a2095530e
20212e75b0fc6545eb885e91a52c95566263ead049252e4ab3f6b9d304c43486
20359e35c0ecac74b431d40e0ab9b887947b00d14e1f6c65e093dc5e354e1e79
2075b7757cec5c14f3861042a302617c41deec3c5e181446259a9ae7cc64a45c
210b54b61ac8e02c786ece5df62a7fd47f5c86f958fbf9e19bd25c0a8f486b33
23ab8e0e718a7829cd0e73e6b626fadac4cf3d1064809f97604c9833dccf3105
25eb013528689123dbad237eb7f7e2477c96e22a4bc604d8b0d54f161ebeb08f
279a0df573e692a0a7f8f525d48e5ddd83a47c3b7bb1f139189dd825f4ddd027
2912768470005f80a6ff8cacb72e52ed6c2a929f65685188f5d6381e5d60ec51*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
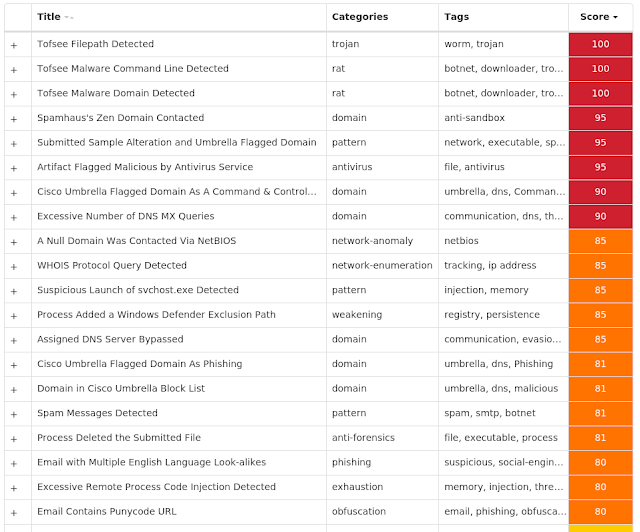
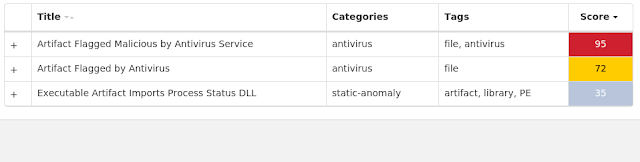
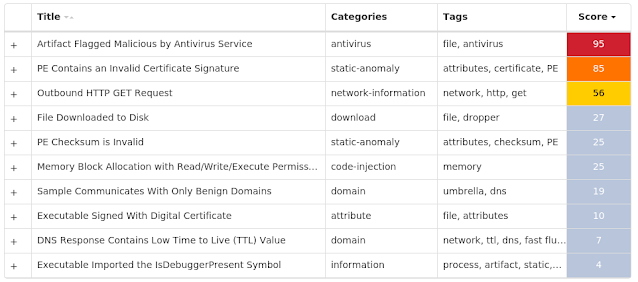
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Tofsee-9933691-0 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 28
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config4 7
<HKU>\.DEFAULT\CONTROL PANEL\BUSES 7
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 7
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 7
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 7
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config3 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 7
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\tuawzulg 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\fgmilgxs 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\jkqmpkbw 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\wxdzcxoj 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\yzfbezql 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\mntpsnez 1
Mutexes
Occurrences
Global\551d9b41-6d47-11ec-b5f8-00501e3ae7b61
Global\53648161-6d47-11ec-b5f8-00501e3ae7b61
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
67[.]199[.]248[.]10/3110
54[.]38[.]220[.]8510
67[.]199[.]248[.]14/3110
213[.]91[.]128[.]13310
185[.]186[.]142[.]16610
194[.]180[.]174[.]5310
86[.]107[.]197[.]13810
89[.]223[.]65[.]1710
104[.]215[.]148[.]639
211[.]231[.]108[.]46/319
117[.]53[.]116[.]159
96[.]103[.]145[.]164/319
194[.]180[.]174[.]419
74[.]208[.]5[.]20/318
144[.]76[.]136[.]1538
91[.]219[.]236[.]188
159[.]153[.]191[.]2397
67[.]195[.]204[.]72/307
142[.]250[.]81[.]2287
185[.]7[.]214[.]1717
185[.]7[.]214[.]2107
185[.]7[.]214[.]2127
185[.]215[.]113[.]717
142[.]251[.]33[.]2067
185[.]7[.]214[.]517
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org11
isatap[.]example[.]org8
computer[.]example[.]org8
249[.]5[.]55[.]69[.]bl[.]spamcop[.]net7
249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org7
249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net7
249[.]5[.]55[.]69[.]in-addr[.]arpa7
249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org7
249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org7
microsoft-com[.]mail[.]protection[.]outlook[.]com7
microsoft[.]com7
www[.]google[.]com7
whois[.]arin[.]net7
whois[.]iana[.]org7
aspmx[.]l[.]google[.]com7
mta5[.]am0[.]yahoodns[.]net7
mx1[.]hanmail[.]net7
host-data-coin-11[.]com7
patmushta[.]info7
www[.]instagram[.]com6
mx01[.]oxsus-vadesecure[.]net6
hanmail[.]net6
mx37[.]mb5p[.]com6
park-mx[.]above[.]com6
mail[.]h-email[.]net6
*See JSON for more IOCs
Files and or directories created
Occurrences
%System32%\config\systemprofile:.repos16
%SystemRoot%\SysWOW64\config\systemprofile7
%SystemRoot%\SysWOW64\config\systemprofile:.repos7
%TEMP%\<random, matching '[a-z]{8}'>.exe7
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>7
%ProgramData%\freebl3.dll3
%ProgramData%\mozglue.dll3
%ProgramData%\msvcp140.dll3
%ProgramData%\nss3.dll3
%ProgramData%\softokn3.dll3
%ProgramData%\vcruntime140.dll3
%APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\places.sqlite-shm3
%APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\cookies.sqlite-shm3
%APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\cookies.sqlite-wal3
%ProgramData%\sqlite3.dll3
\Users\user\AppData\Local\Temp\dxvpqfnc.exe2
\Users\user\AppData\Local\Temp\ibqvoqnw.exe2
\Users\user\AppData\Local\Temp\grwwarcd.exe1
\Users\user\AppData\Local\Temp\qbcuhfxi.exe1
\Users\user\AppData\Local\Microsoft\CLR_v4.0_32\UsageLogs\9A36.exe.log1
\Users\user\AppData\Local\Temp\pixcvxud.exe1
\Users\user\AppData\Local\Temp\sqodvieh.exe1
\Users\user\AppData\Local\Temp\odjdyomb.exe1
\Users\user\AppData\Local\Microsoft\CLR_v4.0_32\UsageLogs\968C.exe.log1
\Users\user\AppData\Local\Temp\cemlbbvs.exe1
*See JSON for more IOCs
File Hashes 0ae852bbe8c30fa41de11c94daf008bc96c80be4230e91215b6c17c1f0a37fa6
0b769ae3a1ab07b3414b2fe5808b662237e8d3ea8d87c4550952f2adb4cfdfee
0cc22a85732d6748f0936c79e68c730bde531da31baebb6b1c8dd6e7f755a186
1108a10b143d94353cd0cad6bcc2f8bd57a9ea56945291fabcff56efe81ad910
124b3ea6d0e14ae41d0759bf0c34919f88417fcf4feccdd74de3bfbb56ed846e
12fb3b2deb9d723e2da17673475fe9e502f24b06b2cd194b1aa5d3f212f53058
18814124ba5985e9dfe57b3ce63e93c15a559e1d07dbaacb67ca461935d6d813
1955cce2e7bc2519db00d207e78d56f229515999e01e8b5ab40ea7a9a7d193c1
1a9573072e9afe029c6b702e4e0a29da0e71ed75c11b7f3a2c949047160f0bd1
1b77f4ff31294559619df3adfbfccab8980992764e63377f70c9c5b96ee618b1
46033bd204315a883f599a40dc6e27c86af574e05af915d39915f3840f8c07d3
4c9df4e198cfbbe3d19a2254614da33e5ac2658ade06f068c733b5118393cfac
594971e3c6eccf37a499985467286e0ac176f20ede2c87fd2c6d0ada3964429d
5a7434856e1ebc9505c879344c548105bfb31ddfe5a3931e90436ad90405db6a
7caa4a9307034a4315d31c23a9b8311274e9b822a15a724eb18363e74eada362
8c9b2c8c4f8ba33d638615bc3377ad4ef8f5eb8e508b532a0fd3eab1f960779b
a81b000c8092297045fc9e4747c27c633a3b25555a51f04785a136dd1a4f689a
b9355ca00910baf8db38b01ae66a211b5895a061ee27d715de210c3ba915bece
bcf64b263f8c0756d94a325b3a726f7eeb167b53c512d1dd973fd60f960b3853
c493f6064d4e5a6f5ba15457d4c4801376ed77cae36b71e988c3fc9d86dad1fb
c4d175ee93dac83fb8046a40f24a848a15a55040de3c30caa4126b194cde077f
c798a56771dd93d5cff37370f67394767a6027cf491a85e4997f9629386bb789
d6df00041280e81d38662a7bebaeeaa0d4175cd7b0043a7d00ed369b8a57ca47
e29d07c397855222a340994afe624e659864eead2b6eed5654360ecfd94f8495
e2e0fcbe61bd5439f825ed3f7f997ecae0e7674a154654b2c3f76b87f2bf190c*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
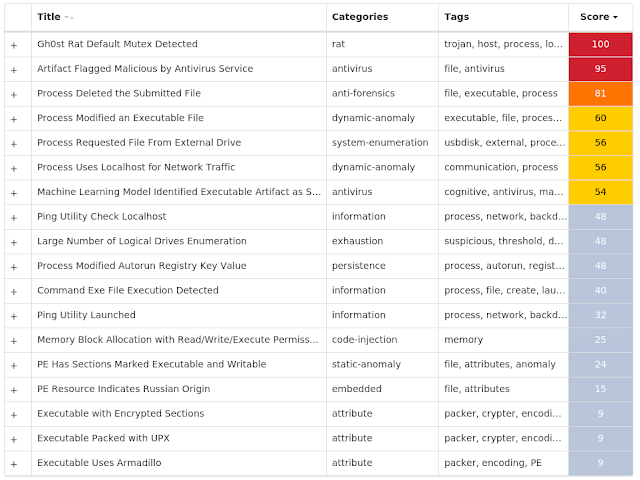
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Gh0stRAT-9928675-1 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: EvtMgr 26
Mutexes
Occurrences
67.198.215.213:320426
M67.198.215.213:320426
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
67[.]198[.]215[.]21426
67[.]198[.]215[.]212/3126
123[.]126[.]45[.]9221
127[.]0[.]0[.]121
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
blogx[.]sina[.]com[.]cn21
blog[.]sina[.]com[.]cn21
wpad[.]example[.]org21
isatap[.]example[.]org14
computer[.]example[.]org13
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com11
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com5
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com4
Files and or directories created
Occurrences
\1.txt26
\<random, matching '[a-z]{4,7}'>.exe25
\<random, matching [a-z]{7,15}>7
\unripft\xivhs.dll1
\ccdcv\yspjgpw.dll1
\etvduqkmd\nqvwmce.dll1
\bfbqa\ynhdf.dll1
\xlovl\dhvbqozo.dll1
\mnqbgefzl\ihdxjewa.dll1
\ccvefudy.exe1
\jiqtj\mzbjz.dll1
\smhmieb\rdhnee.dll1
\qwhhw\xvozelqjz.dll1
\lcmgxjlx.exe1
\xpqbwm\rynae.dll1
\vrbbr\wpdbq.dll1
\pfdxkdiz.exe1
\atpnv\bjklg.dll1
\ertpt\vbwblka.dll1
\tiblue\ayorce.dll1
\xotiz\deblgig.dll1
\dpokjp\uyvhx.dll1
\kldyl\fkoyn.dll1
\oodcm\sevjht.dll1
\pzqqbwtkd.exe1
*See JSON for more IOCs
File Hashes 030362794d0bd7ae6d968d3e1889bbfeb66f58ee0db67704469eedf9094d7871
0e0a0b46185e77f645b74e18b696e65aeca2089851db1b11ca9dfe13ce5ea0e7
0fb28ad4d4f0fa49d50e1e771b93330ec9a0be4aa6a4b8a4b55844df94eaa25c
2a7462cee6e834c3e5171bd94767fed3b58cc8e2d005d07cdb353d42594031ba
2c6a238df36443e93bdac060a6b3123f4f474c3b7b15baa672f1b14ff22f5b7a
35b0477ded22ab5b75de86f81cabae2f38557e8b99ee7d8c15feb71329d5afcb
3d8d8a0358fae0ed84f2c888be7debc97bf358920a7ef5be45a59e01dde2c96f
40c70bfe876c3cd2aae6b334885a34f5311cccd4ef1f00035935b83e4ee58e1d
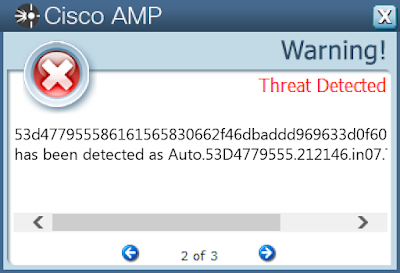
53d477955586161565830662f46dbaddd969633d0f60245273667b6acd592dd6
5535c38614da6a5d19f18ecf4bfae1a839e133bb7ef263f613ae5cf069fdbde1
69a46f75ceb96cf6dbabc145ef2de4f2e0869915bd5fd902ade2891b3f14ce3d
6a4512becd91eb633c6618f6ea5ff11ad6b848377148515c979dc172c761ea79
6bbffe220f31d756c56484c6d8bdde65587b14f96670bbc269d6528645b6f726
6e12fe6cfea60ea1a62a27c4f58531ce95dc13d43b616e340cd406cd510b5307
708c9ce952229721ca3dbd0335314c130e1f8b14fd5ad4dfe345c53caff8e218
78af44d3e04c6f2ae327dcdc5d9dd515aeef9a5303accf728907f329df4ad1b1
8e4d4e4453d0fc449144b7bc95236b7e26383fd1c040cebc4733778721cbc89f
9577670a22f61939447e571eeddd6dc9cb3591d6249b227ec65a2290a9cef45c
a5b72bd2367be139b7c97f9599e49007e3dd1d49eec4693cfdd45f99580c1f34
b687a09b8ed0ac267b1fce38d1859e1a2e920beabeba8436c76d82ddc3324f3f
c9e2a16f1eed9770131953d73fe95c274827195dbb6ed2b31bceed993d433e65
cc15221bb779b96813ba6e125bcd5b668d43d2cdc1b21f6ea8c0bb054bb75a19
d0fbdaba4ff55a8a55a13a68154a77a5eafed027798b7bcc52ea7ef79b6a326c
d16d0152fdb6250c3c036a065ccabac5ea4c11f75c37b6cfc2d97e7840c35f6c
d410c5c55b60b38e6529e1c834e16312ebee734ade55deccf2c6e01ea9092961*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Downloader.Upatre-9934126-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
204[.]44[.]192[.]7625
72[.]22[.]185[.]20114
72[.]22[.]185[.]20811
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
apps[.]identrust[.]com25
leisuremaintenanceltd[.]com25
Files and or directories created
Occurrences
%TEMP%\bhfsrfgs.exe25
%TEMP%\pgengh.exe25
File Hashes 0a80730a2ae557047a01cc6e827fe32a59013b03f6e58b2a2bfd1efea47d1a24
172a9b83bd59358801ff9c6523b373dc5347768dc11302ce536f03bd1dd596de
1782c42db8c20a8dd5bbf950a2d6d42010da4fe35a80aef175a0f48ceac54717
1c2212536e3a873021f62a091baaf1d79bae8fb24c7dfffcc764978548ab24c1
1d7edf1e37ea7b11167eb318fcc1acb94070757ca25bd11e84be8c2d8fe0154a
1e9a1e783678319854c65d8d3c334744553db83acdaf9d91cfaf738ffdebc1d2
2348e2111667d2f566f2bd35480eadb6e7abd2fe65961033cab774dd45a34ea2
2abcd9a59f3c69b297ef985fed980703a92da4bc39fb2c5fea33fb8d607e59bb
2e6633143345a549af8b11593e7c71311a8b8def13608c7b58dd3882dd35cdef
31b0f36ddce0eed570dcaf34e950856695ab0e487b4d6f7d0e29dcd57a296f13
32524ea5235bca3898a25d8a957caf807706ff7ba6f90ded68eaada47669223e
3bf006d46763841336b120412e60f7775fae2a413dcac49b4d459c93a978e9e2
3e02ce8274df79e15cf45c17435356238aaa13f7ae64cc7d26794b9bc60dcdc9
4013176e317de33e6128d8b1dcc307c785dd3d2c7cdf7c863b6d9c38cf78a76c
4eb73b5a36004c90aeb8c6ffe9b05e906495642fc4db52dff1a7e32459b650ea
4f1f60abc469669a8dc15a8e7c4d226a1bac5588f81c5a66eabed97081f15202
52c4868c8228abdd13a5776e89db2f076d4e06b04282ed1b24e9c4360dbb3078
602ba48eef6e4a667c0ed7e7fb8d050a569d90dc3abd0bb7c7be8a09133787db
608963dd078baa521fc0b70284d48745d223c1077b30e299abe2a7592bcc1fe7
61fdc16290150fcd7ec2e0cfed8b3fc564313d3cf6d9f5cbd138edb5e777f2b6
62e545097ed02c498f94adeef634bf3cddeb829421e5f511acfdd59ce68fb445
69119f039ccdb064b7bcdf48bc150061028dd2c79aa99519810388d49d3956ab
6f58f8cff540be89791a7ce777c897b84d4980dd7e543ba7f0d1c62725a1239e
77a45e959977fcfa67a86a6c9ad0ebf73850aa3a755daec14097990cb736ca68
7dafa943159f67d6b04e09723f320ae809d81df97e69ee03a49a8c3d37ad2011*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Zusy-9932471-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 23
Mutexes
Occurrences
ashot_st23
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
104[.]208[.]16[.]948
52[.]182[.]143[.]2123
20[.]42[.]73[.]293
20[.]189[.]173[.]223
52[.]168[.]117[.]1732
20[.]189[.]173[.]201
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org23
clientconfig[.]passport[.]net21
onedsblobprdcus16[.]centralus[.]cloudapp[.]azure[.]com8
isatap[.]example[.]org7
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com7
computer[.]example[.]org5
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com5
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com4
onedsblobprdwus17[.]westus[.]cloudapp[.]azure[.]com3
onedsblobprdcus15[.]centralus[.]cloudapp[.]azure[.]com3
onedsblobprdeus15[.]eastus[.]cloudapp[.]azure[.]com3
www[.]msftncsi[.]com2
onedsblobprdeus16[.]eastus[.]cloudapp[.]azure[.]com2
windowsupdate[.]s[.]llnwi[.]net1
onedsblobprdcus17[.]centralus[.]cloudapp[.]azure[.]com1
onedsblobprdwus15[.]westus[.]cloudapp[.]azure[.]com1
Files and or directories created
Occurrences
\Users\user\AppData\Local\Temp\WERE723.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_034ce6f4\Report.wer1
\Users\user\AppData\Local\Temp\WERD70A.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0e501105\Report.wer1
\Users\user\AppData\Local\Temp\WERBB15.tmp.WERInternalMetadata.xml1
\Users\user\AppData\Local\Temp\WAXD81.tmp1
\Users\user\AppData\Local\Temp\WERE7C.tmp.appcompat.txt1
\Users\user\AppData\Local\Temp\WEREDA.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_02c82f1c\Report.wer1
\Users\user\AppData\Local\Temp\WERD41C.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_09913b63\Report.wer1
\Users\user\AppData\Local\Temp\WERCC6D.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0d157521\Report.wer1
\Users\user\AppData\Local\Temp\WER4A0F.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0739b4ec\Report.wer1
\Users\user\AppData\Local\Temp\WER5B14.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0b2e9b87\Report.wer1
\Users\user\AppData\Local\Temp\WER692D.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0a650fd8\Report.wer1
\Users\user\AppData\Local\Temp\WERAA19.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0ef069b4\Report.wer1
\Users\user\AppData\Local\Temp\WER16E1.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_0a2b952f\Report.wer1
\Users\user\AppData\Local\Temp\WER67F5.tmp.WERInternalMetadata.xml1
%ProgramData%\Microsoft\Windows\WER\ReportArchive\AppCrash_loaddll32.exe_cf32f5149196789a81fecd6e57fad0fcb71e1b_b175e38d_033eac42\Report.wer1
*See JSON for more IOCs
File Hashes 0aeb8bb69d4e8a6d4223693dc353f62430c0f4c16f1278f20042a9908a884420
174867d04fa7f99695368904f0e4b83994e2c72b231e4e39cebec3648d3878ae
17aebd0c16bd81bb37e7f0d398d909c50638b6d70b2181e4ac7ee35b6b23cfb6
1af1f7f5baf654eeb7cf885d9a83354804dffb364bd450ab0e919cb87d963421
307ae88c9bfc701c47db16e952ac930a19d84fc53f6246444264a41ca53c0c1c
488463853079ebd42263015cb085617c657598e5321583460b1b1dc2fca7684a
4d6aeee0e6a13420ccb4948646a9709b4a43bc8adcfdb682b881d88d2deac641
66064ce541047d9ffc659bdb5cd891032739040eb63b1f2c71dafa69251e5cb0
75d0e8c3cad8908948055ae798fe413ee9d0bd1b50865be47869ea8308cb3909
7b9a940f9dfe586dffe998ed13ad540c037ec3eccbdf804e5375fd580c1cd14f
7bac8ccfe2f46e859101851ba7fa3750c345fc3b2bdce2f99f6abd32c7a6e888
9d3875d4f8f4645d713a08e1b4beffb9ef3997892d75376e9d508b44a1f1e272
a0a1660a5d388b79ccc34f357754f088c8740109bc2347cb53d2ae06d5c6587e
a311dff286a0997be3a75a8bd3c09381c7b9be77c397636ce96fff38f4789224
a45b2a2c438ec83610c82eef0912a80dac39658d975f5a9aef3fd5b207f1e93a
aa3f81e3e9437fc2e214b7b5a445b7b04a7696848b6224833a75b829e1daf2c1
b66e3af15e2855c1080b841af82e7885086993933b494ba7d2ce73d830a85429
c31aa6a54c3e41f7a018f53d19e34f66458fbb83bb317c2207ed2666effc3cac
ca34ecd3ed96a2c89785ca8661fa814fd3dd0ea5b5c3abf12c468de1ceb56996
dfd3d7688d88fa9552a28af2f5b76b5cafb5fff87407b8ec0b15fa751edd91ec
e23667ff62e045397bb2a402df274edfefc6bf1a25d2e246f0472e2dc859e30c
e34a312ed5d22190d1b4240a8bcd83086b220fdeded228ab825697d6df3de176
e9b23d0f2b89494469738f1eb971603cc10a1600965e327928821bf3d1d38729Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
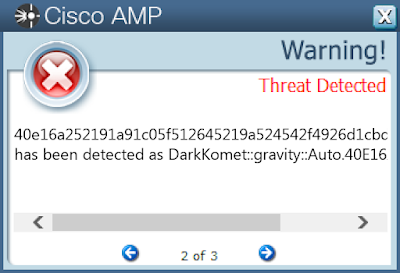
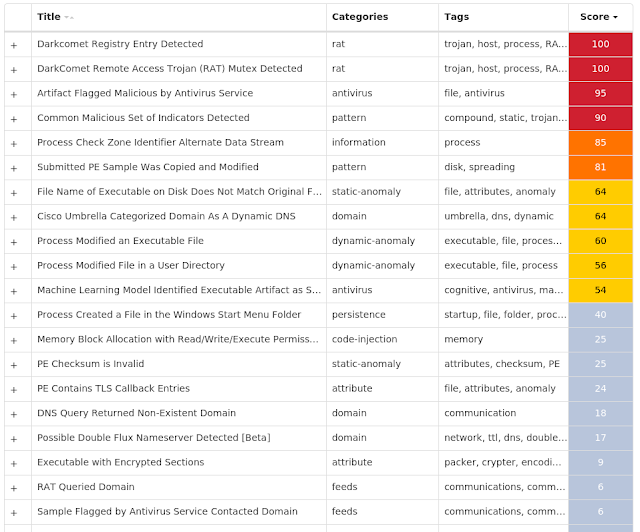
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkComet-9932930-1 Indicators of Compromise IOCs collected from dynamic analysis of 49 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\DC3_FEXEC 49
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 49
Mutexes
Occurrences
gcc-shmem-tdm2-global_lock_spinlock49
DCMIN_MUTEX-BNUVM5R49
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
sure052[.]hopto[.]org49
wpad[.]example[.]org1
Files and or directories created
Occurrences
%APPDATA%\dclogs49
%ProgramData%\Script Code49
%ProgramData%\Script Code\ScirptCode.exe49
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ScirptCode.org.url49
%SystemRoot%\ServiceProfiles\LocalService\AppData\Local\Temp\MpCmdRun.log1
\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ScirptCode.org.url1
\Users\user\AppData\Roaming\dclogs\2022-01-02-1.dc1
File Hashes 00ebc35361fe5684426a5c8b7c3d35c6258dfef425183e2599eea3e6258d555a
01962cc2da397d3d22f0efa3266094b5f115743345082349ceda7607250e573d
01e87628396262c96d858c73b9bacb8bed8ff66c963454594f70d856930a4c96
03c34a84b9a5218fdb8e4289b60f59ed82f0c31971b412106eeb11cf2aa0d9f1
0c1cd086912d10be794a8d600a7e58cfd8af3d4c84b73663630f600ecee358ae
0ef90630cc4c188568a6d41c6dffa382c70d5a0fa5cb33168fb22827886f8045
0f54fe7ea39aca5ea3adfc919a2eb1aa49e7eff8670463c58d0883c0260bad17
19c9226fa78491ea9c737c0641b2dc328ff4db05eb16e7cadc81ae3e4a87eae7
1e03d8aeed562585a2068fa2f6c89434eeb832c2b97a5b90c21ecaeec73a8660
200a9ad4c35e5b86a40203181239dd808540c6a1a4fcf482ff7cb815beb1524c
22ad2eb6af7ad4829e5e5ba2b57b74dfe9cc5f4df08659b978554450961ff153
2bd6201844d5e8bb11de482f3af321aee77fea3843ef3bc56d41e3851c70b8c0
2c6355caaff8d1a6a22f194205c13c69c8ef9d42f8581fb582f52f885e3cc57f
2c721d02e7bc49b5fa732bb8d04696b6268386b18e3b96237beba8d7f03a90ef
32a06f0808a79accc801ae855fd37a8e16158708d94017fb297e73394dd5dec9
336e70f824c8b75b7af305a30d7a30951230f7b9620db472f5b9e3b6b498ac65
343fcc60e38c1029dd47987989013c25c9f94777a3fde06d55fdd7f18687da50
34711eb40ed68a7c4bb0aa5854dd83cf4dc5b241ac51c4b911cd61e16bc0dc67
39b18030395e6fedf7fafa9a4dd9a4cc4f0b39b73bc77ba29d6ba9878d16ceaa
3a6a64646baea4c118e22d54ebaac75368c7fd200acf29776769700e05142569
3f38e55e17238844b9cffed80231074f946373717e2df5b308133fb3baab3294
404d69ad873e280aab7c640312c0cc54e39bd77daf1b91f4b9b617a8ad752449
40e16a252191a91c05f512645219a524542f4926d1cbd3707f593f18e002ec43
429fa9f299eb2a772aa2a110007b50c95300b495d052ce68aaecac5e40734f44
4384740f417019f446c16a1b3753290aff90fe68163ff934971731d10f81d1f1*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Xpiro-9932984-1 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHRECVR Value Name: Start 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: Start 19
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\SHELL FOLDERS Value Name: Startup 19
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\USER SHELL FOLDERS Value Name: Startup 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Start 19
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 19
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 19
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 19
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: ObjectName 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: Type 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: ObjectName 19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: Type 19
Mutexes
Occurrences
Global\mlbjlegc19
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
20[.]36[.]252[.]12919
104[.]18[.]11[.]3912
104[.]18[.]10[.]397
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org20
cacerts[.]digicert[.]com19
g[.]live[.]com19
isatap[.]example[.]org17
computer[.]example[.]org12
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com10
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com5
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com5
Files and or directories created
Occurrences
%CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE19
%ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE19
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe19
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe19
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe19
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe19
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe19
%System32%\alg.exe19
%System32%\dllhost.exe19
%SystemRoot%\ehome\ehrecvr.exe19
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log19
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log19
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngen_service.log19
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log19
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat19
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenrootstorelock.dat19
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenservicelock.dat19
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock19
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat19
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.lock19
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngenservicelock.dat19
%LOCALAPPDATA%\rqboqelc19
%LOCALAPPDATA%\rqboqelc\cmd.exe19
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenofflinequeuelock.dat19
%SystemRoot%\Microsoft.NET\ngenservice_pri1_lock.dat19
*See JSON for more IOCs
File Hashes 1c274f2fd7723cb45f0291b2133f2039268620cc56350f282ad8df4745f162d9
263e898f8887a4b29bf9967e7cbbc4715ea4a66b542425ea35a7005b93eeabf0
292e736944678b2c8e12b02848803dc045fe3ad35ff9a2082a3efe6f629b0f40
305ff0ca1e7b01f179ae3d24b22b9d6658218eac9675288de1c2e088964c5c7b
34bbf8f00daf0369aa27ba7894041ae6aa5e34464b40e3a73194d507322f6abf
549c81447bbf0374a09494e50c310ad4a642816f0d079a21cd447a49e59b09fa
57c947a131966a2e297e8e0d237f67984cc22fa8672b879b893afe60c6a383e6
5bcd32596530cafb7239bf7f768f1fe361ea4199c2358b8f14300143f0a6468e
6b894476e61687cdee381dcae921eb71f37c856e931d81cbc11227ac2f615993
780c2bd0e4bbae90adb2f77a06097431cc8774770a7dba4e84011969f7e1d5dc
7eaa0aad3ddf0d6e124581b1aa4c2b9762f576e8637493dd122ec2e9c670ca9f
8888b3c34cdb5a777c09746d0bc4be2578480f73b201ada7f7144f008afce606
9084355a3acbb14e2cb5f8f5f200040c3b07b7c6d923b39ac1636c29342cadcd
960f3d585fa14c93d343d662d6e89f3d26ef3a7f6974a910a89e98054ed06ec0
a3446721087c18519f408f50d7775d8033d9a8e3267b7dabb21141e81d06a7d4
a7341a6fd6ca44a43982558461f1e3309fb9fab6fd17103f648247ecc16a8e74
aaa9bc6679655f6295e6e278acf2cb47d05d42e7a466c4a1a96f4cd1b7e52a2b
f440562aed34967e7be0c63bd0dbc6e9faf85eac7af8a95327c0a8e93749a410
f6b99c6e972a798bd45d6140020735992a2f6de18f7b09776f3503c883fd88d8
fb25f0ae22545094cbea3ce5996365c81c7565bee6b78ce60ad1a1d2da60d613Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Remcos-9933257-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 17
Mutexes
Occurrences
7BmKnW0JUV99OHo4kyukabIU17
VcR4^@&2XJ1cx2&(450x-4GP23C2
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
51[.]91[.]236[.]19316
72[.]22[.]185[.]2089
72[.]22[.]185[.]2017
192[.]35[.]177[.]641
205[.]185[.]216[.]421
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
apps[.]identrust[.]com16
www[.]royerconseil-finances[.]ch16
newpkmdhhsddg[.]xyz1
File Hashes 181ab75f2bdae575e5542a13b1522ad692f38af0856657dc9b976ef8582f647e
2df20feb158d1fd59acc38775a791ac1ee3093bffe2add9e568825b4e6700cb3
39f305a03168b3cca7605f3f99424437f1e328703a7c7ffa6db12342402e1f7b
44f6f2bb5311838d857aa4e0271d1f1292ad116d5428185249b827b744023a45
77648eecce4bc3c7ba51115391fddcaf87b85eaaf39d7f52e8db67a265467d0a
8a834f4e2a840c91d06290c8dd64bc17b003706829c208c439d8270ce683d18b
8ca2f44a3e92a7a6ac1d5f67d8faa2bb811ace96513e8f489b3ea206f27b3971
8d329c068bd720cbc781d32f5b18037ad52fef296ce6bcbe14a462c9f1071661
98c8ac6434ebca027b504274f032810f113141869f0723d9ee14b41ce5687cec
a8e39f0c32e61bb63d407b62042fa2e63602ee3efda145acdb939644850dac31
a8f8da85066d1c19257135bd264d5373ebb151fe330d16fedb093d441ecc1989
c23f82d2083cc69a7510f4ae7d321c3d5a22ae58132eb2461111986d9b7c61c9
defd887bca57c8169f8b613e0368f63627cc65437abd9e094d8b0587870c2f29
e46e6196ab59cc732a35998900b6008b6629b515c7666d83ee053cc3c2ef8aa4
ecfc7d6cf284dc8cdd7fd02e7193319c0ec75e3c0e38be530c21bc0c01d36728
f58667964733c487833e7d7e506db5c1dbf21a0f0aef3a93fee6be52cf47a12f
fcac3792d1de7bac9a6dc38dfffa35717cec2ac4d867210a647ab0a2d49035b9Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
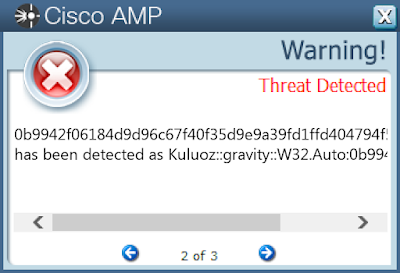
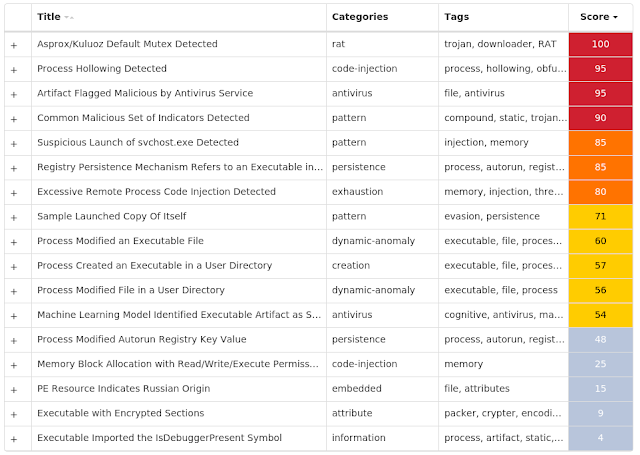
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kuluoz-9933836-0 Indicators of Compromise IOCs collected from dynamic analysis of 296 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'> 294
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 293
<HKCU>\SOFTWARE\RJPEUNNT Value Name: tksadhql 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: qntkmrgf 1
<HKCU>\SOFTWARE\PLDRDUJG Value Name: qgpvxdew 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kpxncbnv 1
<HKCU>\SOFTWARE\HFJWFKRT Value Name: cpidsppg 1
<HKCU>\SOFTWARE\JUFXXQNQ Value Name: bjndblob 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vtvscuku 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hbpscdtd 1
<HKCU>\SOFTWARE\VSQSKALW Value Name: xkudedwt 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pvmkkhpt 1
<HKCU>\SOFTWARE\KTCNFHAK Value Name: jgopihal 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: mpmivkbw 1
<HKCU>\SOFTWARE\OQLRUIHD Value Name: rulopwsa 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: nrwadbro 1
<HKCU>\SOFTWARE\MTCUUATK Value Name: akenqcjl 1
<HKCU>\SOFTWARE\ETNPQCGM Value Name: cmhsegcd 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vqvejfug 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: euqlmwfj 1
<HKCU>\SOFTWARE\TMQVEIXX Value Name: akiccmar 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: haiqbmtd 1
<HKCU>\SOFTWARE\CUCUXKTL Value Name: xvwdqfoq 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tpxxxphg 1
<HKCU>\SOFTWARE\JHQMKJCB Value Name: fjifcswx 1
Mutexes
Occurrences
aaAdministrator3
abAdministrator3
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
64[.]91[.]226[.]48167
198[.]57[.]205[.]18164
80[.]93[.]28[.]65160
109[.]68[.]191[.]186159
103[.]27[.]108[.]199153
216[.]250[.]125[.]3019
111[.]67[.]14[.]1918
65[.]181[.]127[.]12515
192[.]163[.]219[.]18315
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com8
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com8
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com7
wpad[.]example[.]org4
computer[.]example[.]org3
isatap[.]example[.]org1
Files and or directories created
Occurrences
%LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe294
%HOMEPATH%\Local Settings\Application Data\xknjctgm.exe1
%HOMEPATH%\Local Settings\Application Data\dphhlajg.exe1
%HOMEPATH%\Local Settings\Application Data\rlwfnogd.exe1
\Users\user\AppData\Local\jhpqfmat.exe1
\Users\user\AppData\Local\uekmeaxo.exe1
\Users\user\AppData\Local\cimfjovj.exe1
\Users\user\AppData\Local\ujntigkx.exe1
\Users\user\AppData\Local\mkpfcqoi.exe1
\Users\user\AppData\Local\bspcovtb.exe1
\Users\user\AppData\Local\fvrwacwq.exe1
\Users\user\AppData\Local\enraxmii.exe1
\Users\user\AppData\Local\vkxqgkdo.exe1
\Users\user\AppData\Local\ggiqquda.exe1
\Users\user\AppData\Local\udarbmmk.exe1
\Users\user\AppData\Local\pvbgvxog.exe1
\Users\user\AppData\Local\akpfgmxe.exe1
\Users\user\AppData\Local\bqbidpmd.exe1
\Users\user\AppData\Local\ghiulumw.exe1
\Users\user\AppData\Local\mmajgwmj.exe1
\Users\user\AppData\Local\ndoanhcd.exe1
\Users\user\AppData\Local\etslkokr.exe1
\Users\user\AppData\Local\vpbuxipr.exe1
\Users\user\AppData\Local\wluwmjno.exe1
\Users\user\AppData\Local\pjhtddap.exe1
*See JSON for more IOCs
File Hashes 00821b577f7436541761c9ba039087b88054ebdc64445a63940c62119ec0c368
01f9a0a5cc46be71f9d14f679a8dfbad9a82aa5727a1fdbca7802b2d4d890ca5
039e8d3046195c432e932e7c79e56d82eccc3f413e1e350540ac9339c69b9166
04052884207b2ff302cdcc73fc8997278d4ca3d505b82a96d9f5c0ebe39c3327
0483261bfc9791b6866efbc506390aadc901056a5e73c142b192f8336c596d03
04b27a851e607b2845e488e4e41a0d5e85187e11c1585e92392607751152927f
0644c40a3bb058c6fb64f3d57c83624e1a90db440f0122ec5eda0c9798f53369
09d2a012e974436dc8d767368512e7b1ee5425d7d3d6ed2c9ba753a1335fcade
0a783435ad220b4432e4b0e1af38af98e89d42aa3c9193e48ce1e5cc04251d0c
0ab99b6c5ad749a602354b6525fcbce76b109c12d25bd4983384cc141a60da55
0b932135b31b8de131eabfc23bbaf57af505fc5c492b59486f66aa227c1e3ab1
0b9942f06184d9d96c67f40f35d9e9a39fd1ffd404794f5bc269e35111c8a852
0c96d07fbeaf26651fd3522856bd547e3a0eb7d9d3071dfa263055afde6e19cd
0d16279827f8590217c26fcd71df64db85cbe59c9586957d55bd8608aaa47094
0d650e473de170caf6cb66d90fa03f58bafb0a9011e99d76bf05d045d615e2b6
0db8f23e7d335575756e93958fb75d716ad6d44f04e7bc0595540638fa3a7f26
0e650fd74e9358b8fdedf27d05ebb2db7eafd903c3d16e0c3f3f7fa57ba531d0
113b2ac10b0ea7a4a91b874d27c5f51545d81f561755cb1e29861ee7b76cdd78
13b0ebb6ab2cd8ec71b7ad1b626d88db253300faabfadee288765cde290c91c8
1414657fa4d9190fe64fa69d9790a24e54757189bb1ba3a243ae7471bc4904c3
143688ae9ac7b8a95e0dc714ae4d2df925c399d2fe2a9d0bd5105e38eb929eb3
1447b894dcabff4299275bf3ebe64c963e2f90fe6f114d64c60e46a5ff99cee9
14733d3ff31310695f39dc6792befdd25f92de6ba0a98f76b11da6f5cb55ad89
14e251578492927e95d99b39405db2ebfea8eccd9da372f14adfa5c5f0167a9d
1621e3da2f4a25a71d402afa336230c2671518aec5945eb5418a8e0ff38274e7*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK