Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 22 and April 29. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
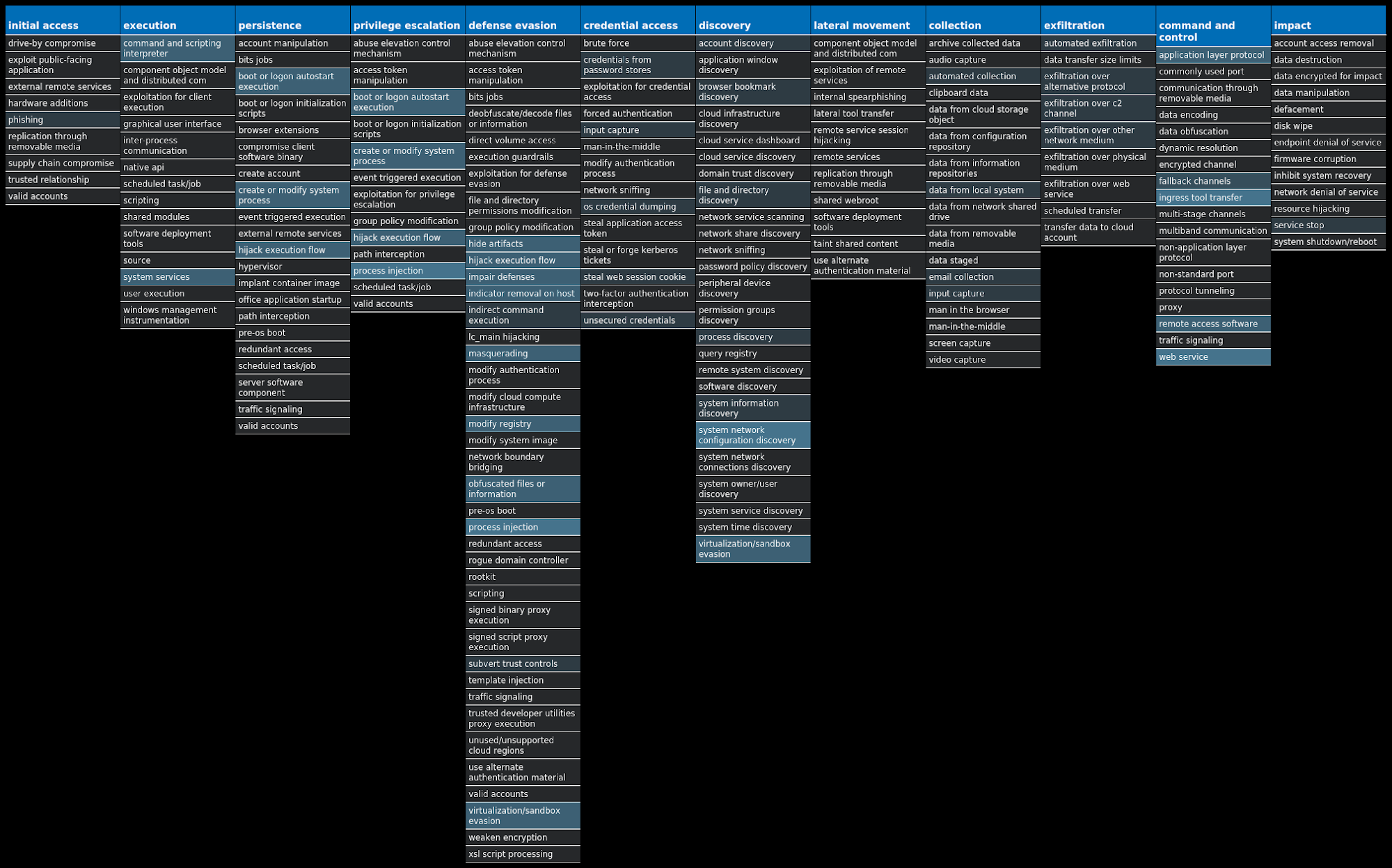
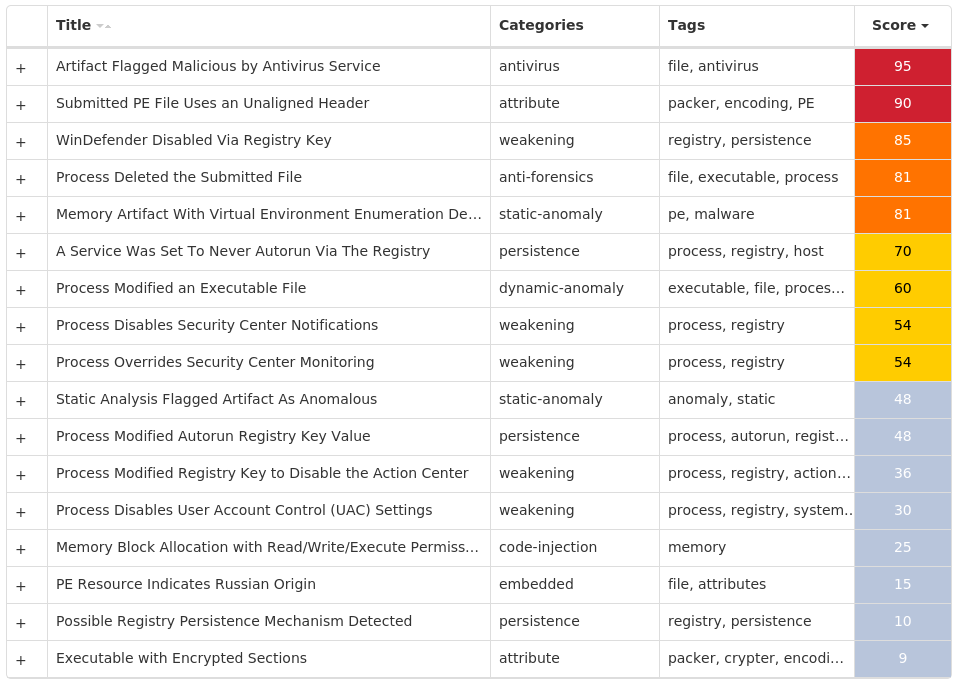
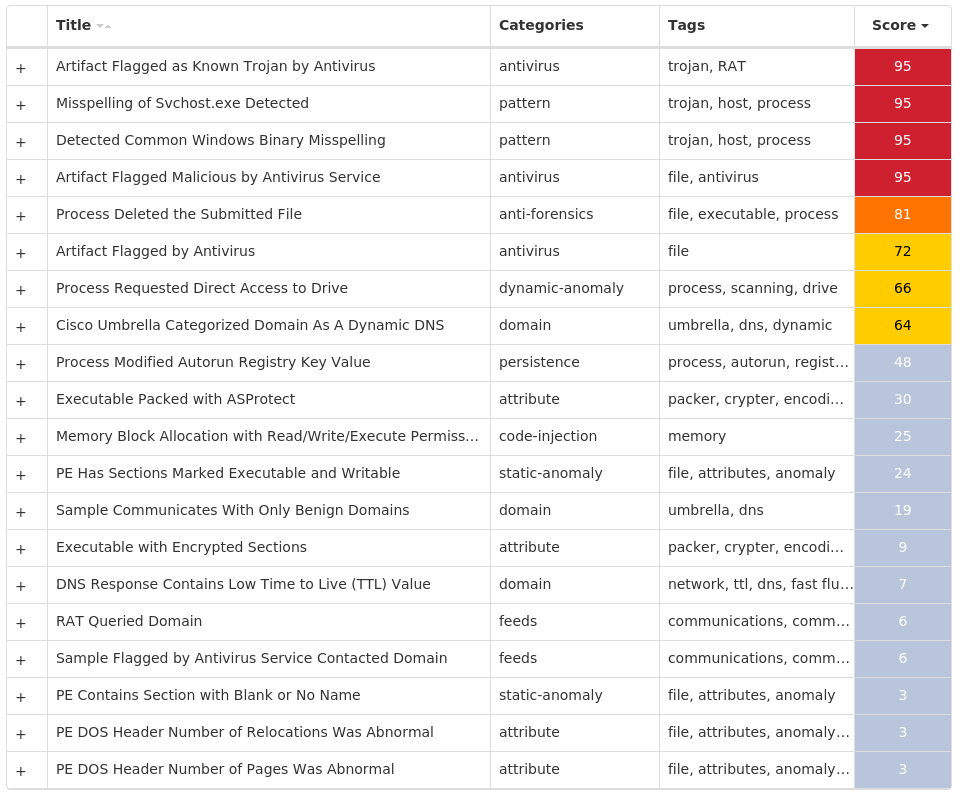
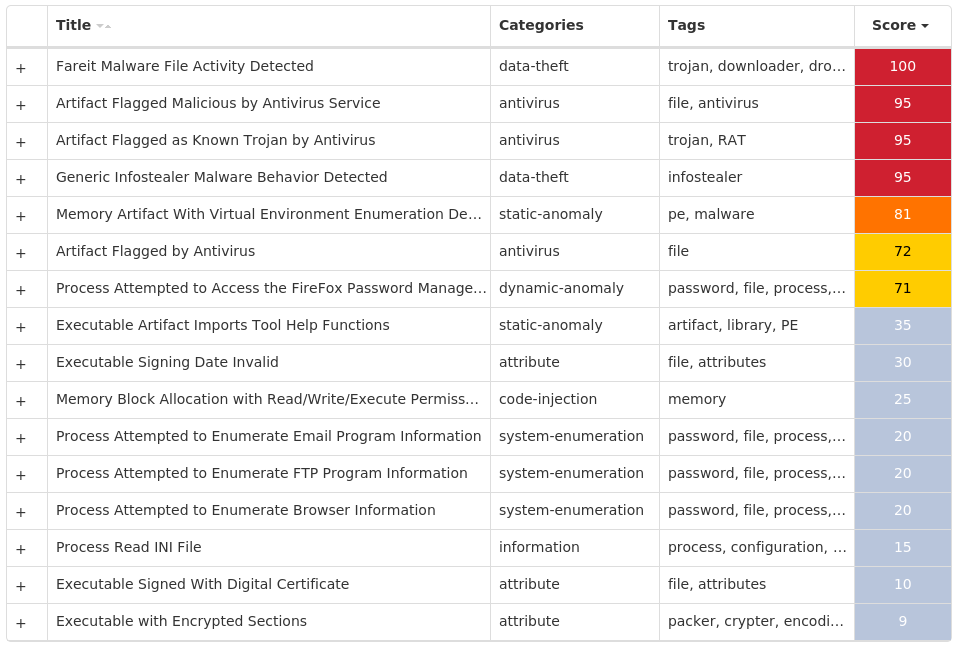
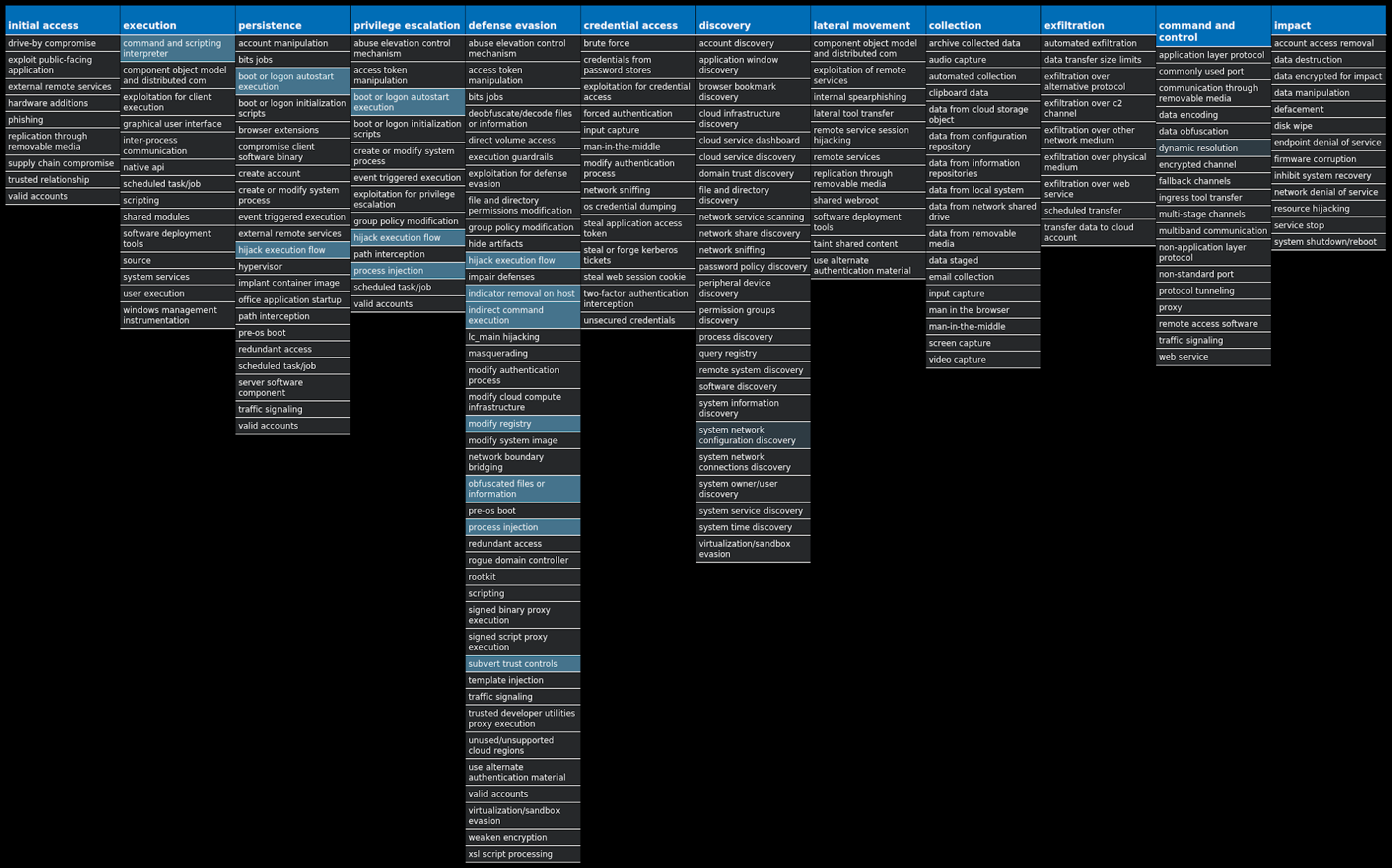
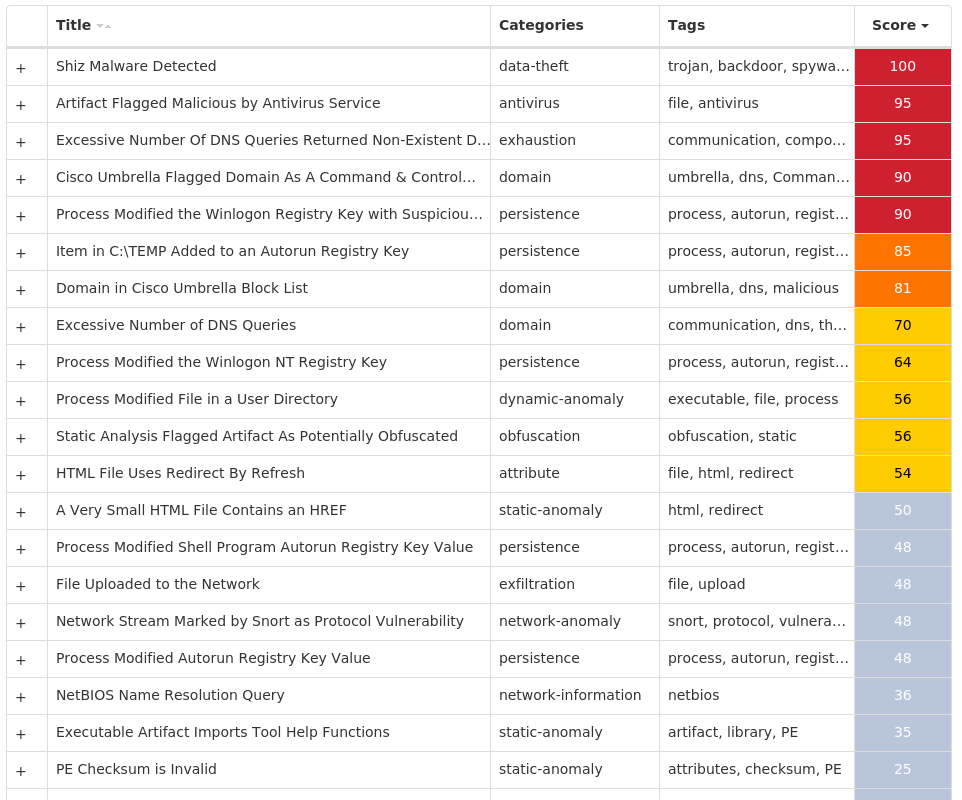
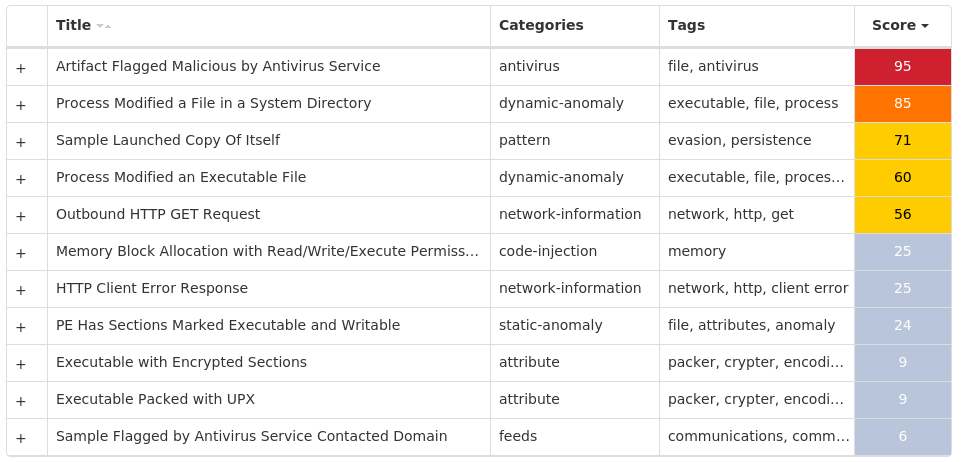
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Dropper.Kuluoz-9946000-0
Dropper
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
Win.Dropper.Tofsee-9946510-0
Dropper
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control.
Win.Trojan.Zbot-9947109-0
Trojan
Zbot, also known as Zeus, is a trojan that steals information, such as banking credentials, using methods such as key-logging and form-grabbing.
Win.Dropper.Zusy-9947443-0
Dropper
Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Win.Packed.Fareit-9946200-1
Packed
The Fareit trojan is primarily an information stealer with functionality to download and install other malware.
Win.Trojan.Gh0stRAT-9946565-1
Trojan
Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the Internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks.
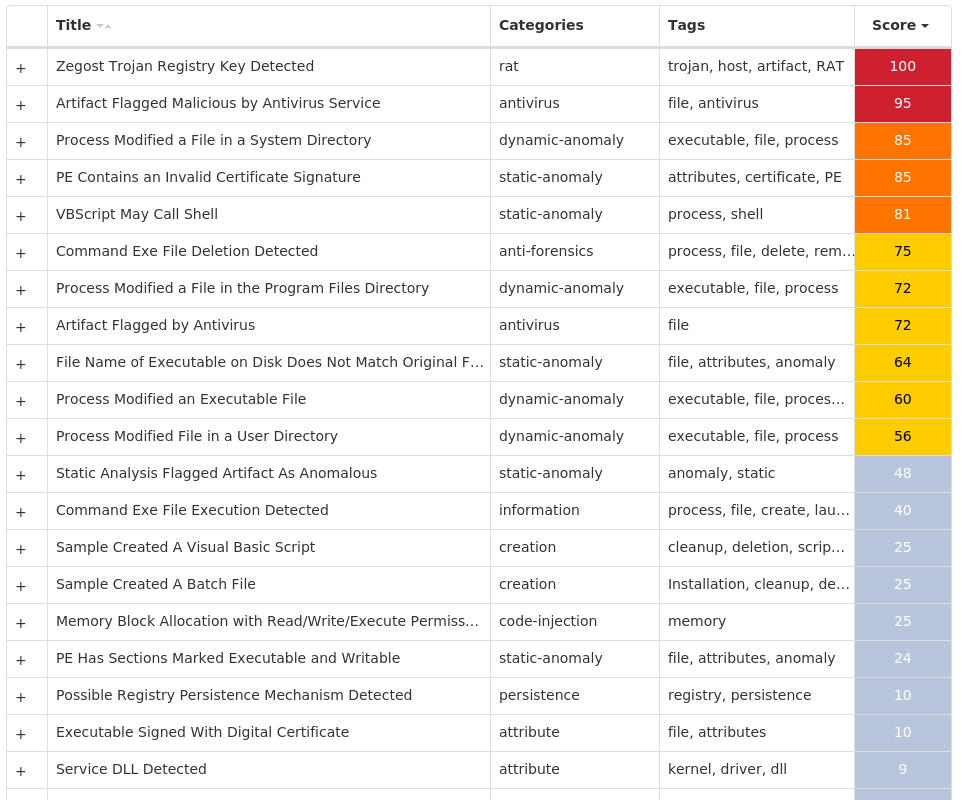
Win.Worm.Zegost-9946550-1
Worm
Zegost is a remote access trojan designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. Zegost appears to be derived from Gh0stRAT, which is a well-known remote access trojan that had its source code leaked, thus significantly lowering the barrier to entry for actors looking to modify and reuse the code in new attacks.
Win.Dropper.Shiz-9946469-0
Dropper
Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site.
Win.Malware.Swisyn-9946568-0
Malware
Swisyn is a family of trojans that disguises itself as system files and services, and is known to drop follow-on malware on an infected system. Swisyn is often associated with rootkits that further conceal itself on an infected machine.
Threat Breakdown Win.Dropper.Kuluoz-9946000-0 Indicators of Compromise IOCs collected from dynamic analysis of 84 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 84
<HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'> 84
<HKCU>\SOFTWARE\CJRBCQCV Value Name: rvkansdn 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: npnwqpol 1
<HKCU>\SOFTWARE\XHPHJIMH Value Name: flhbwrfp 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lsqoaghj 1
<HKCU>\SOFTWARE\CSLGMSBM Value Name: xplljtsk 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fpkauvlb 1
<HKCU>\SOFTWARE\NXPSFQVQ Value Name: trxoobco 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jgtjmhnx 1
<HKCU>\SOFTWARE\SNJDFBDD Value Name: bvtqjugm 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: aajklswe 1
<HKCU>\SOFTWARE\WGLGFAVE Value Name: qowsrtcf 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: paqomfhq 1
<HKCU>\SOFTWARE\KKCGPLBT Value Name: wgtwcska 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hmqmjbix 1
<HKCU>\SOFTWARE\PMKHQRBA Value Name: qkisqvpi 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tjqgsbbq 1
<HKCU>\SOFTWARE\AUJKXNRB Value Name: rqapoojk 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ixkdxkvu 1
<HKCU>\SOFTWARE\TCQEXEIW Value Name: bdrnvonm 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: iujdubcx 1
<HKCU>\SOFTWARE\WMRJVRVS Value Name: cbaittwb 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: imxhsefn 1
<HKCU>\SOFTWARE\QHBWDLEW Value Name: ltsaoqje 1
Mutexes
Occurrences
aaAdministrator84
abAdministrator84
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
198[.]57[.]165[.]4653
69[.]64[.]36[.]24452
16[.]156[.]201[.]23748
110[.]77[.]220[.]6646
130[.]60[.]202[.]7144
85[.]12[.]29[.]25143
5[.]249[.]139[.]13241
5[.]175[.]166[.]3538
Files and or directories created
Occurrences
%LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe84
File Hashes 010767ccc41595d706b6058de836341530e00ec432497f4e0e5d16a28069adea
044d40b02598856b94da0e7dca80befe4fd0e159736c2b7d669eb8dc3e046792
04bf922e68819dbe3d4449b75884d82b9252fec514f71beb1cdb66b5e77fb3a3
06a14d0277052b5c274c56f2c9f10484a9c5868cbfcb88d94e500d64d684f637
07f5f195e1906928b423c671b5d54f8a16d0d0624081a431f6488383d2c03606
0c405ad2641fb3da5cfd9671149e37a7c95fcdcad47ac27fe38caa8b957d08a4
101100330c3dad13b1391321cc3e1771cecd7887569f06d7b4b9066b2624a3dc
10a57eabf280362f14370d783d31361d433bf254f53d9ef915d9b215f6944205
228a4398715087fb1b9e5da6b04f5bee23a4cbf96fad6f834efc3e57f5688409
2321ca11a8ee8aeef480ed870f947b47c7e6678b51b18e421212ca23f61d1c27
280921144c834717afbc32a4cf91aa02150203c2ac2f01a78a335b9cc9367f32
28fc4c69afe168b97ffc97563f7b7b6631f59092d3cb933723f8e057d01a80e0
2b852b7411dafff60a32ad9962bea7737cd03532890108f130032085c15a6c60
2ebba35eaf1e15a72d508b673b5426576cbc1f199baa8c1a520f8f252403fac1
2f21d38280507ea4de0b18f526bd069df15124e249982bd0e639e98d15d06a48
2f590ec580ca909919c30d339b5a88975d1c72425d1da28a5cba0d0ab3a8955d
336475cb4d327e0bb436427e13c6c83324bdeec82ac64c19cb93d76638456525
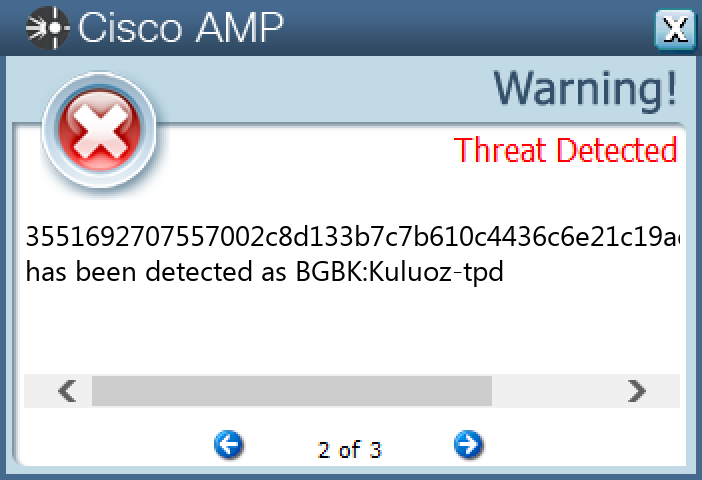
3551692707557002c8d133b7c7b610c4436c6e21c19ae70a7ea4c5ebf2f803ee
36eb65e638c7a5c543004783253c18decfdc1d86daf1a73e6af78d21cbf892a3
3a256c739632d72e3fa95b7779ede95aa60909c74be183195103e27cf38aba49
3ac4979856f6284800bab9799f3aee430c15eb24010557dfb89e32fcb3a856fe
3db97701a3e5a207c025873cbb0bec4bb76f8b2dcfee39cdfe9eefc2c12a4055
3e10388eb7c9a63691460ef914b411951f4bb6fcdeb48f4730595294ddda289b
43aab8ab7d7b025fa8d1787e2d908ffcdab28b92a3c0088cf40bf3bd475e165d
48444a67228011b09f30763a731737151256c5b3d65671823b7aa87a3392578f*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
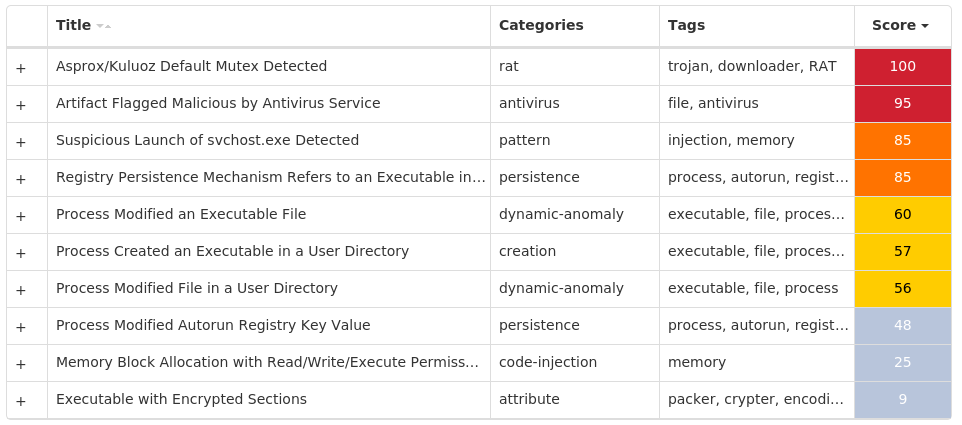
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-9946510-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKU>\.DEFAULT\CONTROL PANEL\BUSES 12
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 12
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 12
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 9
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\ktmkeuza 3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\udwuoejk 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\oxqoiyde 2
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup0 1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SESSIONENV Value Name: Start 1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CERTPROPSVC Value Name: Start 1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\TERMSERVICE Value Name: Start 1
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 1
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 1
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup1 1
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 1
Mutexes
Occurrences
3749282D282E1E80C56CAE5A1
d19ab989-a35f-4710-83df-9d20-806e6f6e6963Administrator11
Global\515dd0c1-c197-11ec-b5f8-00501e3ae7b61
Global\50e42c21-c197-11ec-b5f8-00501e3ae7b61
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
91[.]243[.]33[.]512
62[.]204[.]41[.]4812
62[.]204[.]41[.]4512
62[.]204[.]41[.]46/3112
62[.]204[.]41[.]21212
62[.]204[.]41[.]21012
142[.]250[.]80[.]10011
45[.]8[.]124[.]9910
31[.]13[.]65[.]1748
31[.]13[.]64[.]1747
213[.]91[.]128[.]1336
31[.]13[.]65[.]525
157[.]240[.]2[.]524
157[.]240[.]2[.]1744
34[.]98[.]127[.]2264
148[.]251[.]234[.]834
172[.]64[.]146[.]744
13[.]107[.]21[.]2003
104[.]47[.]53[.]363
149[.]154[.]167[.]993
104[.]47[.]54[.]363
142[.]250[.]176[.]1953
185[.]25[.]20[.]2103
40[.]93[.]212[.]03
142[.]250[.]65[.]2063
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org15
249[.]5[.]55[.]69[.]bl[.]spamcop[.]net12
249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org12
249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net12
249[.]5[.]55[.]69[.]in-addr[.]arpa12
249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org12
249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org12
microsoft-com[.]mail[.]protection[.]outlook[.]com12
microsoft[.]com12
www[.]google[.]com12
niflheimr[.]cn12
www[.]instagram[.]com7
fastpool[.]xyz6
www[.]bing[.]com5
9[.]116[.]131[.]216[.]in-addr[.]arpa5
9[.]116[.]131[.]216[.]zen[.]spamhaus[.]org5
9[.]116[.]131[.]216[.]cbl[.]abuseat[.]org5
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com5
9[.]116[.]131[.]216[.]sbl-xbl[.]spamhaus[.]org5
9[.]116[.]131[.]216[.]bl[.]spamcop[.]net5
9[.]116[.]131[.]216[.]dnsbl[.]sorbs[.]net5
i[.]instagram[.]com4
m[.]youtube[.]com4
iplogger[.]org4
z-p42-instagram[.]c10r[.]instagram[.]com4
*See JSON for more IOCs
Files and or directories created
Occurrences
%SystemRoot%\SysWOW64\config\systemprofile12
%SystemRoot%\SysWOW64\config\systemprofile:.repos12
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>12
%TEMP%\<random, matching '[a-z]{8}'>.exe11
%System32%\config\systemprofile:.repos6
\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F80085063
\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E0F5C59F9FA661F6F4C50B87FEF3A15A3
\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F80085063
\Users\user\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E0F5C59F9FA661F6F4C50B87FEF3A15A3
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\fw3[1].exe3
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\PCALSGUV\fw4[1].exe3
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\XN0IX3V7\fw5[1].exe3
%ProgramData%\JMQSZR50GEQHSB1XIUK\files\Files\Wallet.zip1
%ProgramData%\JMQSZR50GEQHSB1XIUK\files\History\Mozilla Firefox_1lcuq8ab.default.txt1
%ProgramData%\JMQSZR50GEQHSB1XIUK\files\information.txt1
%ProgramData%\JMQSZR50GEQHSB1XIUK\files\temp1
%HOMEPATH%\Documents\Cdpw8sGeOjrLOii_YNrAi.ls1
%HOMEPATH%\Pictures\Adobe Films\5A4H_jZev7nlbhJsWeTONMQd.exe1
%HOMEPATH%\Pictures\Adobe Films\6d3FTmwA33nDcosimMWAzfr1.exe1
%HOMEPATH%\Pictures\Adobe Films\7G3I0uSMWF3bzDycgsuA6ozU.exe1
%HOMEPATH%\Pictures\Adobe Films\9OWNjoSwOBYCFSDiS3tkji38.exe1
%HOMEPATH%\Pictures\Adobe Films\IV8irYSJLHICjg_CPa4GSTzj.exe1
%HOMEPATH%\Pictures\Adobe Films\OyHyN99cAOMn2mkEhxmsDqSE.exe1
%HOMEPATH%\Pictures\Adobe Films\QyVxzuagunbE6jL6GoqilBAX.exe1
%HOMEPATH%\Pictures\Adobe Films\VDNe4RxRGwTemQHwlaDCAY7u.exe1
*See JSON for more IOCs
File Hashes 00cb3dc51238994b915035596b6d03cb9466aee7ff5057c1e5d43dc78720e171
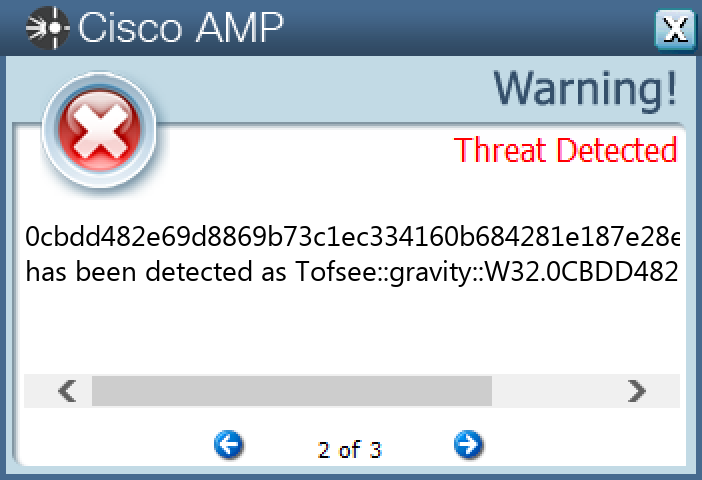
0cbdd482e69d8869b73c1ec334160b684281e187e28ee448df51c64dd523fbef
1fc2f4b80c02776854ca3b7c88fdb27adf381794ea618b8effc5dcca9aad3a92
284b9cc29d11ae1baa476d1a73583c029862d22399d101fedf8658daece8714c
29d04d6ce6bcc56d514f4245fb9cf89078a759103edfb4d7ce7641807b34f3aa
3235698114e95e3bb3b7176bf9c0d3bc1480d91675f4df381cd55ea0707dfc6d
336b95e1279ff5b7208e70c409fe6e05cc9577c93852edcd5d9e3edd389a4003
35f5b9b19f8cbd2dac42c538e82d882d8e95a116c20b90cdf3ee1107f51db230
58c46755dfcc39c07a2bf1c72fc53f96e3fdca0ed56d9d1420f31b0267ef5dce
5f4bc2e7d0f47176e32bc9ec8c42b291a6bb25d499bd73863005d4d1109d3093
775597428d5390ebb2084822a7a927e118ccdfd2985b1a93e821e73f1662744f
871b2e65b8cfb829f4494320a5c22c25c91b857562a290b048c3b6104680a09a
97fa6cf3876cef47104344dce4b523f55bc50e00b05eccc1106700fb64e807cd
9c930ec0e93c3a395f355049ddae45578fa9a8c364b5434bcffe7947ef60dc24
a080d62575420a3c99623a19788ca9e952f4a4e52be5b1f313e558cb9f2c038b
aea4c9d9f1f4ff6732d19308f92ab0b8203452473f90799d2a9665a131bfdceb
b036c7939c408de1297d6fbcc4da5c3713c86a4dc3f5b7be1d3377af3981e555
b1e82a612e672773e1ad354f4bba71e5195408647ef3568f4f0bd1c4d7a476f7
ba19d1876f0063a79e954905435d30003d908400d10c2042cd795e49d889c5bd
c4940e652e5ffe1e8bb760a70a906a46ccf3ae889b70f698cc4143b30b8dd017
d6a716eae4eac9ebe83fc7e15e06622e0cb216f235dc4f6dd8582b5cfaab055f
e5fcd724bb93e4c8a75a838edba9ad04d962e963f7c740fca6dc8904ba751e0f
e95247066fcd9471c148e987d45af91ff943c204c58ebe9ffe647c6ebb98a765
ea8439297f16407bbc15ec1200668585a583a6a9f8a1510ba97b9041f3671077
f6221f215ed77c7058e664aeeae78ff476a610881fbb6ac78d7d9a8de821eb37Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
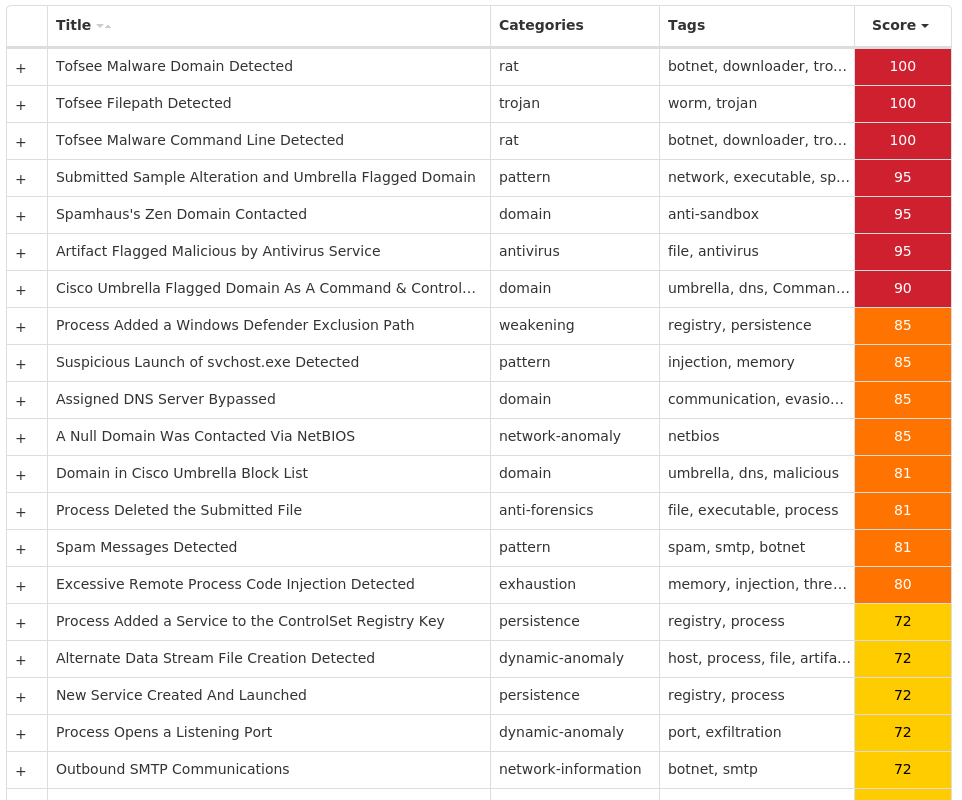
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Zbot-9947109-0 Indicators of Compromise IOCs collected from dynamic analysis of 72 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 63
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 63
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 63
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 63
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER Value Name: HideSCAHealth 63
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 63
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LUAFV Value Name: Start 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SYSTEMRESTORE Value Name: RPSessionInterval 63
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 63
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: 98BE0FA9BB7E8E3C000098BD76F2948C 63
Mutexes
Occurrences
98BE0FA9BB7E8E3C000098BD76F2948C63
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
103[.]4[.]225[.]4163
Files and or directories created
Occurrences
%ProgramData%\98BE0FA9BB7E8E3C000098BD76F2948C63
%ProgramData%\98BE0FA9BB7E8E3C000098BD76F2948C\98BE0FA9BB7E8E3C000098BD76F2948C.exe63
%ProgramData%\98BE0FA9BB7E8E3C000098BD76F2948C\98BE0FA9BB7E8E3C000098BD76F2948C.ico63
File Hashes 01112ab17cdd52c29fd0a35d22345faa5f0b91c29303ed9b99547483ff577903
01acc1f52288fac7c701d5afa808becda7707191074ae9b2713a044f56d4ce19
02482d109bb4e0fbaea2e49669161d245841475462a5147016653831bcb95122
04fc6cbb85c821b65784e731d842a3e8eef7f4b4c923f4a48c2797c3f30b5a32
05153cd09ca86f8170814e9673fa6e3b5b35e37130d02d06bb49de8a5edb07e3
0754948534520b90e6a39713bda4a837fa085e93dca711f5e6c45c1c7e500e71
08c4363e2fbf1ebf5c1044ad8b10f0b70b3fa4fb41aaa659ecf852541bdd5fd0
0d23a377c074b9e9384552f10e6559ba40b602dc640a4c00a8b8e4c89e30b2e1
14694bc56f5708667f76a9411b12ab1061e6258ed2cab19e07cccbc5b79233d9
16d5b01348c73778c7b38729765c0199ae35c80ba4c338f7804bf2dd7a4e9da9
197fe1f217ce695313116a6a4b8fe7a4864c4ebbf4a4d66aa5d3436eb9133068
1b0e354d7028943828958614c6dd1f5a4eeb0140acd5c621b66eac7f02cf8634
1dddee46a74dc4418474fab0503624868ce2d2f3f55d99dd9b19ec856c0ac6f0
22979d43efabf9f7f363c872327fa009502987c2760a55d54ba8e7e2d2f4f3ba
26303c95badff347180218326295d61de119fff41c6ccde72b213d1ba1f64c73
264a7d364707e7a253ce99b662dc919438e5028916635f548d99dffc79f975d8
2651496839f347a66017659a2640c093dde97e89a4b9aae204d2a1f3d6f8fc09
270e6ae8490a9f28295880ed5d83e50efb60d9f3d1688bce08213ae5a3643325
274dcecd716456e18f68397ab9e0edfa431715041edd1b8d1c6620b083a84b9f
27c827425ba98ebcac8f6b2f5788c75201fbd86d87749fcd90e5154b61914f71
2928ef396805e65f076e7270483e82227b55161592f3d7f598ba2472cb01f903
2a872938741cdae8b12d042a67a5b7e38cd4474a405f3893a0a8cb0a23f3b528
2c2f4799233126b6b05543941f4c8fd35878fc5f9389495f04864182a3cd25d7
2c72b937ff6be3a0961296118b27f5b6aad265d7401c1330f3bc33420dbbdb0a
2d14e797c438c9c9a0d01530d5df50c9831b987fa3822c1e5a17dee01a1ed2c5*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zusy-9947443-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: XXXXXXACF01C77 18
Mutexes
Occurrences
AAAAAABP785vz9BPP+9r2wsLGxvfzxBKmxr66xnw==18
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
183[.]236[.]2[.]1818
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
gaoyongtai[.]3322[.]org18
Files and or directories created
Occurrences
%SystemRoot%\XXXXXXACF01C7718
%SystemRoot%\SysWOW64\ACF01C777
File Hashes 03bc4384c090f38ebb07e6499fceae4acb034d68388c1c4136fcd0c6750b6dec
0648d892df0ad0a5c96825376025240e497f143566a0003b474e6934f3fa2f68
14c9909132c664a0ef8db2b81995d4614ce88eaa731851a00c826318f731efba
16155edc50d2c90e7879a225288bca50b341e1131f6a11504c578d39178b63ae
26fd2aa4373648e041066a37ed83b838ef1b1869b51770c46633b323368d9d6a
3a501fb85e886e57b90263211579dcad0e46f49ed0b05ba1560baf51f3b6b443
5170042543c7a51b92f442f4b56946066f57f561be872a9bea49ea12851f9b6e
588af18424dcf877e25d7312299cbaa1676ccc50cdf22f45ebe92af8668320dd
63793c860ac2672b539dcfe05796386cd4e89a023151d298931a9b39a8de0c9a
7dd061b6e0007406db200c88f02f467f2557c2fba53f493061919a19aeaacb38
8e7d3a59a5c3aa668b0c0e0579577c4c485e9c5d54c6d7ca471a9584ab92a72b
915ea0232e14efed3a097798cc33a9b288be7d7ecb18750e15d3e265350cada3
9d5505d43e46d4fcc8c356f5fdde07e4e2d126e33062062d671efa25c132621f
c4dd4e8698c8b4c8fae1452aa6faaf0b45b72b66b2964033d5ba297d400fdb61
e7ef29db18c227c09d3beff5945d2bbbc6359589de46e28b9dc9a7c4d74ad6b2
eabf05d03a9720d5e3a8fa6c3945c769a6010d7256585637d882c0e7ddaae355
f23efeff6ae4f341e42c44ffd98f0177b3d278b0d97d47d83224c8712bf32dae
fcb2786fa5bb3877ff6ec460f26c8c98946d2b53b133e33b660664246bd5960fCoverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
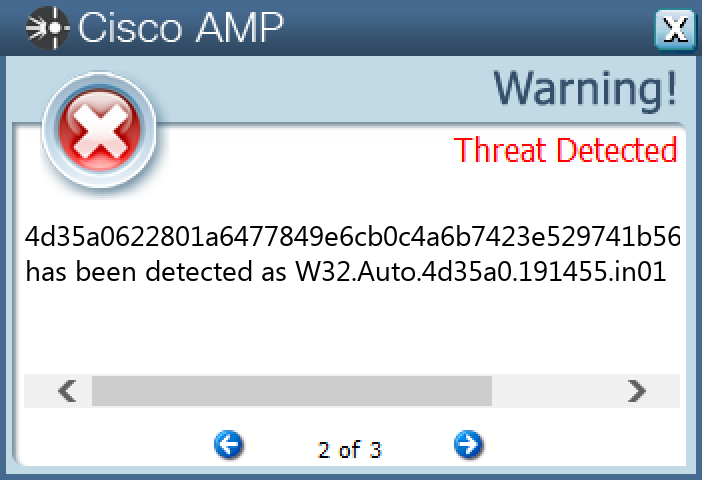
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Fareit-9946200-1 Indicators of Compromise IOCs collected from dynamic analysis of 12 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\WINRAR 12
<HKCU>\SOFTWARE\WINRAR Value Name: HWID 12
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 5
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 5
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 5
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
173[.]246[.]103[.]1247
192[.]155[.]83[.]1915
80[.]211[.]33[.]514
104[.]21[.]56[.]2253
172[.]67[.]133[.]773
198[.]185[.]159[.]1441
198[.]49[.]23[.]1441
174[.]140[.]168[.]2481
104[.]21[.]13[.]2211
172[.]67[.]156[.]621
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
4[.]dlevo[.]com7
5[.]chinottoneri[.]com5
5[.]estasiatica[.]com5
saginawmasoniccenter[.]com4
juaki[.]com4
world-teenies[.]net4
www[.]bestfreecams[.]club4
4[.]e-why[.]net1
flaggenundfahnen[.]com1
jodisandler[.]com1
www[.]jodisandler[.]com1
mhrs182[.]org1
Files and or directories created
Occurrences
%TEMP%\abcd.bat5
File Hashes 3911b2cd6bf58d9a7757e6c81ee6008ba8a261cf167c76338d8c44c812778251
482f784ba47354fdf1772fa031b16d04caece7d94d4791c40db23f81f3843662
4d35a0622801a6477849e6cb0c4a6b7423e529741b5654df4870fe4b58344542
500335ac560795fbff8ec19963f91e7b3af5d60dc9c253263c47e9211048cc8d
5f4c7785fa15da5bff379986e8267424ccc1743b9b5973a1effc7c25b3607648
6dd5b6c87a1568800974e950e8240f9cd858b14ae1feb76379b57b89e710fd7d
a93040a0dbb2629c17284e48bb96b59a27adb343ec1af3a73296c63f382512ab
c8efd9ea7b1fcbbfb53875159150528864c06a892de351b974ecba19a26de0e4
cdb1c0deddb60ce0e67427053252b80a912ac67b88e845fa9d7aab07ea758623
e3c94ca3aac23c52f1b0a629d9bd5d571ec535e3cc509d1f9669c04a310d6b45
e9273e8a75b2181855cdd0f307ff8e1acc35c30043583046047aa9a55aa2fe5e
e9d7abd1750a12fcdf83782ee4b0915261ed22a24011e7502c9b7314ccd9447aCoverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
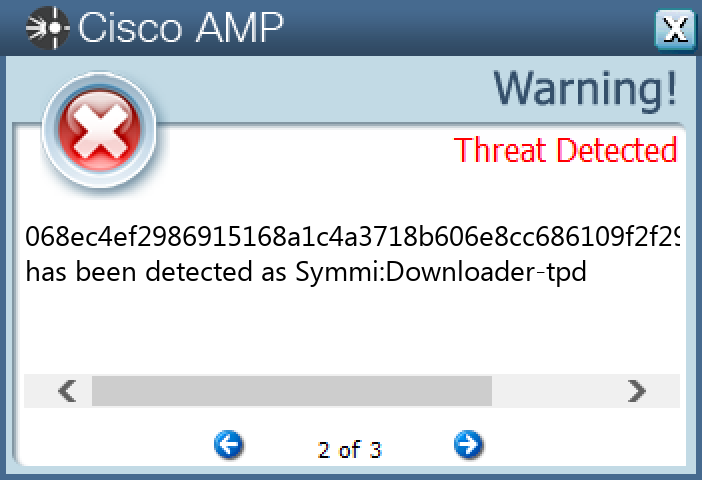
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Gh0stRAT-9946565-1 Indicators of Compromise IOCs collected from dynamic analysis of 37 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: Start 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: DisplayName 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: WOW64 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: ObjectName 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: Description 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: Type 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: ErrorControl 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: FailureActions 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR Value Name: ImagePath 8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: Description 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: Type 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: Start 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: ErrorControl 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: DisplayName 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: WOW64 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: ObjectName 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF Value Name: FailureActions 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MNOPQR TUVWXYAB DEF 7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: Description 3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: Type 3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: Start 3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: ErrorControl 3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: DisplayName 3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VWXYAB DEFGHIJK MNO Value Name: WOW64 3
Mutexes
Occurrences
<original file dir>\<original file name>.exe36
C:\Windows\raxhss.exe7
C:\Windows\nwjpoq.exe5
senlin1996.3322.org:20135
sszhuan.3322.org:20134
black123.gnway.net:95964
C:\Windows\nanpoq.exe4
C:\Windows\cyqyqe.exe3
222.186.24.213:20133
C:\Windows\vipzwu.exe3
C:\Windows\ccuyqe.exe3
hao.2sqj.com:80803
shiyong.8866.org:20132
C:\Windows\gcequg.exe2
l.emp666.org:20142
1sf.8800.org:20132
C:\Windows\rebhss.exe2
C:\Windows\ggiqug.exe2
yangzihouyuanhui.6600.org:20141
one2ada.f3322.org:38001
vip.523sew.com:38001
yplinfo.gnway.net:4431
ddos.zhanglianlian.com:19891
ip.caobile.com:20131
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
222[.]186[.]24[.]2137
23[.]89[.]5[.]604
59[.]24[.]3[.]1742
93[.]46[.]8[.]902
106[.]114[.]182[.]1982
14[.]108[.]240[.]642
118[.]5[.]49[.]61
77[.]4[.]7[.]921
197[.]4[.]4[.]121
54[.]76[.]135[.]11
183[.]38[.]222[.]2041
216[.]24[.]187[.]1741
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
senlin1996[.]3322[.]org5
sszhuan[.]3322[.]org4
black123[.]gnway[.]net4
hao[.]2sqj[.]com3
shiyong[.]8866[.]org2
l[.]emp666[.]org2
1sf[.]8800[.]org2
yangzihouyuanhui[.]6600[.]org1
one2ada[.]f3322[.]org1
vip[.]523sew[.]com1
yplinfo[.]gnway[.]net1
ddos[.]zhanglianlian[.]com1
ip[.]caobile[.]com1
Files and or directories created
Occurrences
%SystemRoot%\raxhss.exe7
%SystemRoot%\nwjpoq.exe5
%SystemRoot%\nanpoq.exe4
%SystemRoot%\cyqyqe.exe3
%SystemRoot%\vipzwu.exe3
%SystemRoot%\ccuyqe.exe3
%SystemRoot%\gcequg.exe2
%SystemRoot%\rebhss.exe2
%SystemRoot%\ggiqug.exe2
File Hashes 04ebbba021908a307ec940f3ed13ffb17381ea13d6380016b9412fdabad434ca
068ec4ef2986915168a1c4a3718b606e8cc686109f2f29ddf248d4f164658f77
0a7d86b170a972915d84bdaf7872a956c72cacd2d2006fceeda51546f549daa7
0f1dc60719ff68dd7017a9611c6a4f6307c8b995f6979e41875863df0b97ec9c
1095d7ebdc1028f721cceee67e7061f19b852579a95f0c7ec4295213ecf28f83
143a93ed9f3201005951153115e9c5a9509832e71df0fb8753c4d3a74f653a0e
1634b94075b35bfb9b4963353a2434d416c72a99792c746b4c8a7a2e25496927
180ad4cd4d3fd57965db3a28460d2aaadd43ef016f81f321224b05c483ac5187
19637314063bdfb97ee2b16c01a6fade6bb753a1f4b62971b69da0e16d9e367b
1f700d543397aa0e2c665726fafd7e4308c2f66469ab08e4d126032754d8ba80
20a5ca42b895317279f748cdaf9645540f61476094a99b8e2aa640e7a28a2292
21d3488d3cb041fced95389ef70954924184ca26ddd81d28536614c8957e270c
221175c5a6fbeda144b61ffdcfea57abf386a6264147cc28ed53bbd5d927fbe6
22801fbacb065dfededa6b71c82878f20fddcf55c1ab47860863c1f0a78e86dd
258af2d035aa5b1485a2dab0611c4be5242cd9c032214108488360de947f232c
26f5aba25a4504d19371653a7ee13ff278041ab3fce4c76f393e0cf66df1e297
2a8bebc5acd6bf6a4feec62b7a6ccf4dcd3e978a63473d560335fec48845aea6
2d44f5ad3da4f27296ecf96ad759bd02973091eda8cbbb092fbfc48b30b5f5a8
2f127e3a56aca1f7bfdbf33beb95300bc260e6083497eb044edb53d8b1809452
33550ba8c95a2e712b37f8b4a1f63e96d68429cef3dfa79ac38b3f78e135176c
34c852bf132d37efba5dc6ba2b4751da14e42f200d53116bf67a88e19a170742
3787dcd4636dbd0a70acdf072f787375b34e4de0a1e409f4b757d773caad5247
39e624e07ede8b4e00f99f7baaeb7a9c1d24d53367e91d139a57ea1a8c47aaeb
403551b8142ba37e0d35ec9661c8604452f0395cddf555a69a14ee1fbf7820c6
4a21501030634432303ddf43a5ee52231f52b54a39fea4cd34fa338245e6828c*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
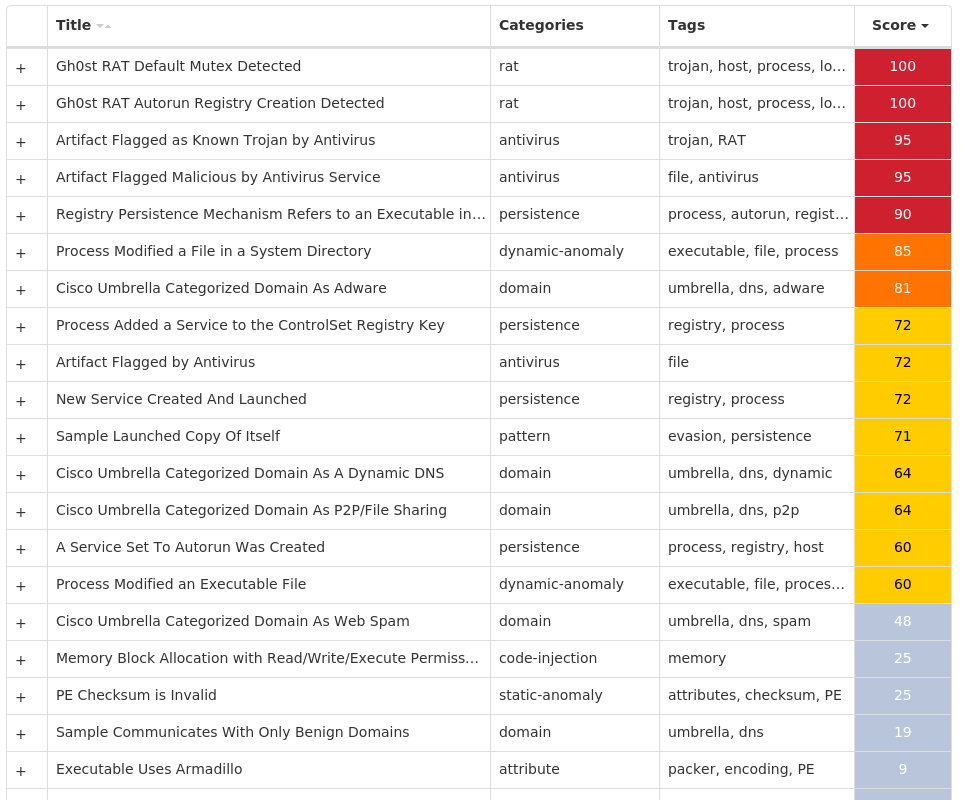
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Worm.Zegost-9946550-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK Value Name: MyVerSion 25
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK Value Name: InstallModule 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSOCK Value Name: ConnectGroup 25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN 22
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\APPMGMT Value Name: Start 22
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\APPMGMT Value Name: Type 22
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\APPMGMT\PARAMETERS Value Name: ServiceDll 22
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ADVANCED INF SETUP\IE COMPLIST Value Name: IE.HKCUZoneInfo 3
Mutexes
Occurrences
QQQQQQAOawsa+9sLCxsb388QSpp6+np58=5
QQQQQQ+/musa+xvbCwsbG9/PEEqbCusbCf4
QQQQQQr/UC8b2wsLGxvfzxBKmup6ewnw==3
QQQQQQBfIA+L39/efw7r0A/Pqpsa+urp8=2
QQQQQQ5/Cvrr2wsLGxvfzxBKmupqexr58=1
QQQQQQ6ff88uf2/a69sLCxsb388QSpsK+vpp8=1
QQQQQQ9PwDAvbvrrGwvbCwsbG9/PEEqaevp6+f1
QQQQQQ9Pz+9vv28ubyvbCwsbG9/PEEqbGvrq6f1
QQQQQQ8fH07r2wsLGxvfzxBKmnrqeunw==1
QQQQQQ8/P457W9BPYA7739AvOpp6+nr58=1
QQQQQQ5/CuvQT99P7mvf0C86mnr6+vnw==1
QQQQQQBbOvr6envbCwsbG9/PEEqbGvrq6f1
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
183[.]236[.]2[.]1811
59[.]42[.]71[.]1786
157[.]122[.]62[.]2051
118[.]5[.]49[.]61
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
cy320[.]3322[.]org5
lj1202[.]3322[.]org4
0ver[.]3322[.]org3
fuck[.]nnxsq[.]com2
xs01[.]3322[.]org1
wodeip123[.]3322[.]org1
woailiuyu[.]3322[.]org1
rrwq[.]3322[.]org1
zhouxin1[.]3322[.]org1
ttkx6[.]gicp[.]net1
xs1[.]gnway[.]net1
f40088[.]3322[.]org1
Files and or directories created
Occurrences
\%Program Files%25
%ProgramFiles%\%Program Files%\363.VBS25
%ProgramFiles%\%Program Files%\Cest.bat25
%ProgramFiles%\%Program Files%\Wdcp.dll25
%ProgramFiles%\%Program Files%\laass.exe25
%ProgramFiles%\%Program Files%\~25
\ntldr.SYS25
%SystemRoot%\362.vbs25
%SystemRoot%\best.bat25
%TEMP%\TMP4352$.TMP3
%TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp3
File Hashes 08e765dff942e0073c7bfc9b62067b64d1d6fefec6eae577effd1f514c2bb575
20951335c4c6454f5e4e0aa8b319ae70fbea7ed301f69aa7e6d5ed337352098c
589778f28203eadf943dd83b450778727d26c4027fa4fb293cf4a003800e9800
5a169f3a282052f21b04e6d9af4fa4c1e869c0408e2a05a27b04f185414b0b12
5cfa2ddb2331b8541da48dffb35c7518928fd60f065c05269cd3ce5e3ab8ebd4
67c21234b86ce7eceeafe1d0ec150ed4e91eeeaba2b6537a34ecf3298769275e
78b8d9227ed3ca1abbe32311edc1f31cbc77a5cc526e141f8922eb52dd2db6ad
7b5fae9b19a7c3a4dc0757ed693148ae4640a1571d93c79e34b7b20ed49835a2
93038f211273160908d018042797d69379981225dc1d7b569ead8adb409f78ab
a52abbe79663e0b4b869fdcb8c51351ff6b900703d15093166d694c0b10eb7ff
ad16d94357db7fcb2b0fc10e01da9c79dd5bdd5fe667064f47b296a1250b56e2
af44b8cca1ab8f9724e9b120d5ac4a8dd2d4577a25fd2f5da5e7386b8901016e
b3d3b4d847e0a93adadf99c165df2a8724f1660516a1f9298aec83c07f6d4a33
b84a2ff26be573aaa3bfe7d45cb07c9bce925ed65e8a69a4c76a8958d3a621d3
c363c34d5c8b77615f72442c8ff70b885e035876d0cb40e45d8462f99a38cdd4
d763aa74c89fbea50a2575bc9655e1bc9e53242fc725ef131c3831d7f553f847
d8e2dc1f10e2a5ea7ecc4a3fa4145c658cd1cbade634ebca790fd682dfd30969
dc5140b9b97dcd6a2f207fa73e73164f2a585eb59ad0f333dd1b8577a1984dfc
dc9dd044b7b7880c32e62dbf1e26bb9f417edc90129fa5a2d4f7adb1bc02a823
e3e857f6ec202c9834f00ed0d243dd0a1b40a23d159e7c091a14b631559073fe
e79b668b743bc69bf4fd4ebf5e6405d4b62794d1db30aa724550a722a1cd55e2
e8b051700d4b04424bf0fc2f8d74aa71e85552da946d8bd82f7e615c433495a1
eeacf5a00b076fc6a013b374f73a8d0750e9e858271c602a0b037865d464a1e7
f1d74a7a6485d312e203119e414aa5f9611d6e1edc0ba8ebf29d286374499e5a
f81b183119e1ef4a9fbfc8b198d5d5145ad83b92075c3910ec02a1f64f7524ad*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Shiz-9946469-0 Indicators of Compromise IOCs collected from dynamic analysis of 48 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 48
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 48
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 48
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 48
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 48
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 48
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 48
Mutexes
Occurrences
Global\674972E3a48
Global\MicrosoftSysenterGate748
internal_wutex_0x000000e048
internal_wutex_0x0000038c48
internal_wutex_0x0000044848
internal_wutex_0x<random, matching [0-9a-f]{8}>37
internal_wutex_0x000007d011
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
147[.]75[.]63[.]8726
13[.]107[.]21[.]20022
147[.]75[.]61[.]3822
45[.]79[.]19[.]19611
45[.]56[.]79[.]2310
45[.]33[.]2[.]7910
96[.]126[.]123[.]2449
45[.]33[.]23[.]1839
198[.]58[.]118[.]1678
45[.]33[.]18[.]448
72[.]14[.]178[.]1748
173[.]255[.]194[.]1345
45[.]33[.]30[.]1975
72[.]14[.]185[.]435
45[.]33[.]20[.]2354
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
ryloqulebih[.]eu48
kezituraxep[.]eu48
jecygyrogec[.]eu48
lykonurymex[.]eu48
pufyjulogih[.]eu48
tujaculurim[.]eu48
voporitevet[.]eu48
disisizazim[.]eu48
mamylotifat[.]eu48
gaqecizupun[.]eu48
norebituwez[.]eu48
jenujoxojug[.]eu48
qebifopalaz[.]eu48
kevopoxecun[.]eu48
rycaropynar[.]eu48
lyxemoxyquf[.]eu48
tulyboputal[.]eu48
pujulapohar[.]eu48
cihihacakuf[.]eu48
tuwyjyvymuq[.]eu48
xugelurisep[.]eu48
fotaqizymig[.]eu48
cidufitojex[.]eu48
xukuxaxidub[.]eu48
puvacigakog[.]eu48
*See JSON for more IOCs
Files and or directories created
Occurrences
%TEMP%\<random, matching [A-F0-9]{1,4}>.tmp48
File Hashes 025ad02329bf16e3ff9d580361f6da949b822983f605ec522b2a856c1d653e06
0598c224a75129a911074f9f5ba57ef25b7141f0a40e1ae8ba709ccd8b52b2e9
0b6c36cf0fa1cd710db9a068fa74af3a8a8861d69b25a1cab1c3d53078a70265
196dee6604a4416d660ba4e3d311c7acff390316dc4a17f45102254f8fb6f526
1ec1dfb1e60929f25e7798727457fc9bdc60f434707041c0bf17d0921eaa694f
21537d7c1e99933e60f9f97e970f98ed09dae47f678a17747d4b4f2682143f25
23d2b48c1eac61b0ac8634be7827a5e9a807766b2981038cf41e065a4657a46a
312349a46c279cf8415b8bd59605bf364bd9794b002ce6e76f78fa05c5aeeb75
381d5e84889d8e4916887bb567a9e5f6e6f30cb8a8094f9996e5a52e8be78711
45227368b923a383f7c35178121306b76460055fb5217d24d569e965688d4b38
51d46da5fdb5c3d3659fbb199e0907d5cf5b0d54a6df6c9609ed38de6dba6c2c
5d2d1bb2b9f27f54cd9fbe6fdaea4282ad12794accdca72c727fbee00c236a49
6055e4bc99dcb0bd2ca99adfa0b0523a9d4a9600ea5db6e5b97d1304db73a0e7
63e22ce0d32d928c777d23de94e9a80fbe5588d9a54d4a1655305d4d69304af7
64190ed6121e52587928c762166834550f08bca7fab43a50cc20356a8ea35f9e
649f829114bb1e400b634f8b4a5531fa9234af0367821437fb512a1a3d55cce7
6b46067476de652641633d7477ace746c5f44d46673f4451913f470a745f64d7
76f7a282d03c1a1ffcfe4efd2303657e62138053d16c93db32badb9e8ef53571
79d2631be00b13f7115a66bbed9fa78e4451254f423a4eda1d8b2214fbba2e65
7eeef7b6512243b9c3b7a95178bf4e379b17fda8bd5d90c1b0435882b2cd214f
8675e1048bc2b4296762bb5ae8aef1bf218a4f1634f09b50812498dc097e97a6
93b752f254046451fc7f4f6cd071536f179858a69b902b2c71999b152fb8d2fd
9df32eb0e5a38723aed16970fe220d8eaa40c5d6beb71d4a15092f961d6b8fcc
a3b96c986db7f0a94ef4b7bcf09614daf926f82ce0f5862051f5facb680615c4
a72672de4fbc0b024996b46c03061e6c9cef1e212be0aaa21a7d75d6bbe55a3d*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Swisyn-9946568-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 3
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 3
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 3
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
164[.]88[.]45[.]18710
13[.]107[.]21[.]2007
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
www[.]bing[.]com11
www[.]m2pk[.]com10
m2pk[.]com8
jipiao114ai[.]com1
Files and or directories created
Occurrences
%SystemRoot%\winlogon.exe11
File Hashes 0a5cdd69571e204fe37a0178a2d41e2153a2efa806cd076c5af3ea2cae38942a
0ee44f83ac5df91896f433f8acac397cdf964e187f296127fc7e340800d4971e
19811699cd73b72fb2b8d1ef3253032f327590ed3ca16e7534eb9a26d24f5f86
2b09069a3e6f47836d07d92868a71243970a4ef854a46874d695ab79464ea6ba
3c99a848cba6f618328ca277346a4d6909e01acae9e2bbd6f71fbf6a626c6a19
4dbaa76744b64561fc96e5ab34077bb53dba351c98d4d7fc375b23be89b53a33
4dd8f1e1ede64ccda57c019a0f50c7b619109850e9101b576414cb2f24edda55
5491a30bc56ddd6542af90afc1d41847c377b6b7d3b251503042d5c9dac11cfd
9506b7aae42b099156c0c5b32e2770561968a0169504c1ae46284aa76290154c
ae68f92992d1a8e072107b0ad437dbc4da3acaf35cabb11e825f8882abf1da50
fa23bbe2e3bd5b0b41c2c726890f317b72d901385362f61d93a2a5348d95f78fCoverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK