Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 15 and July 22. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
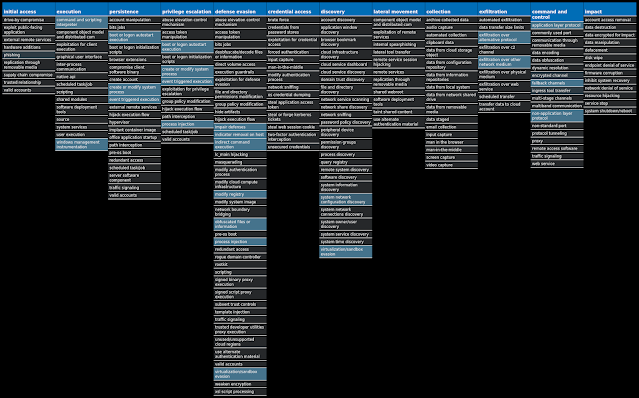
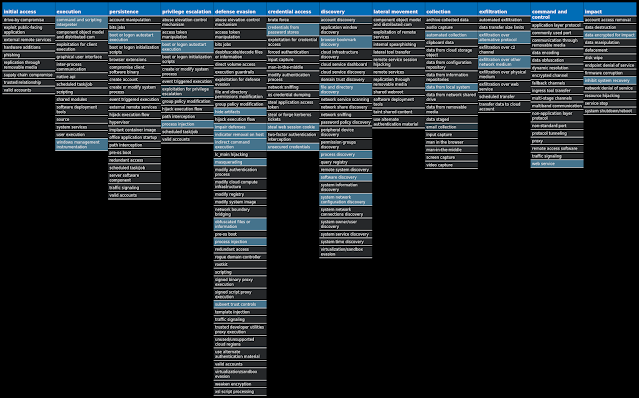
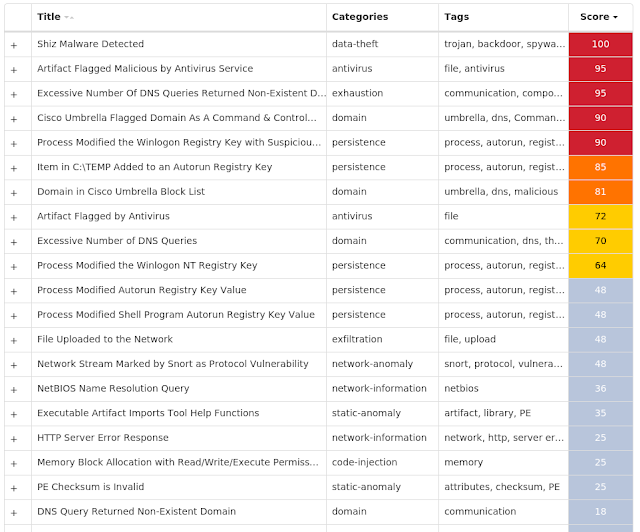
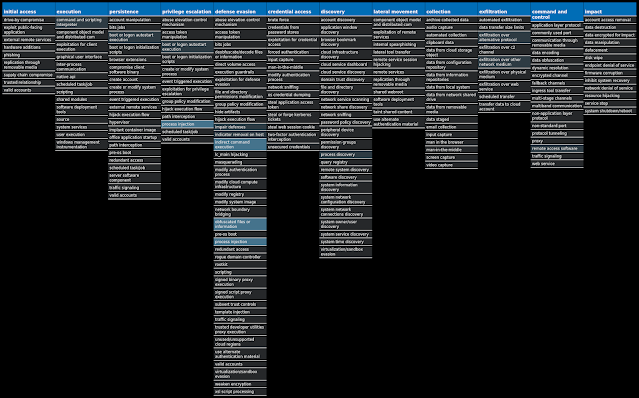
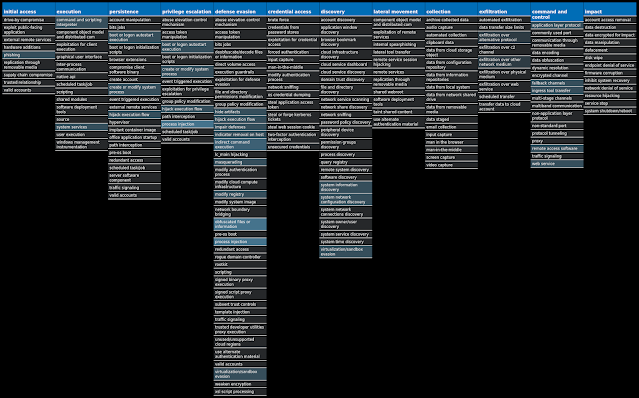
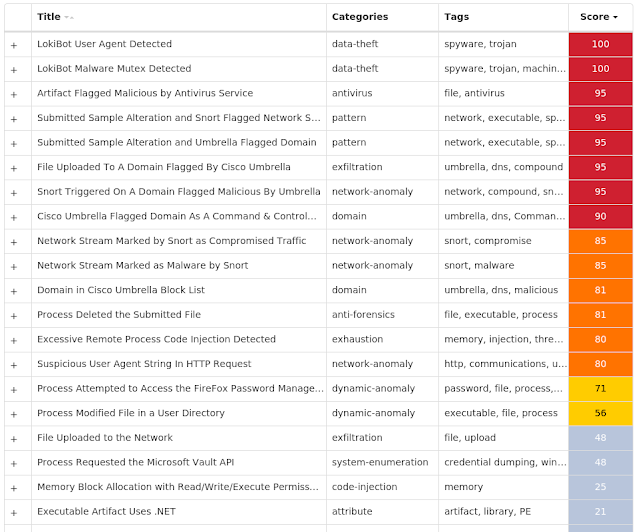
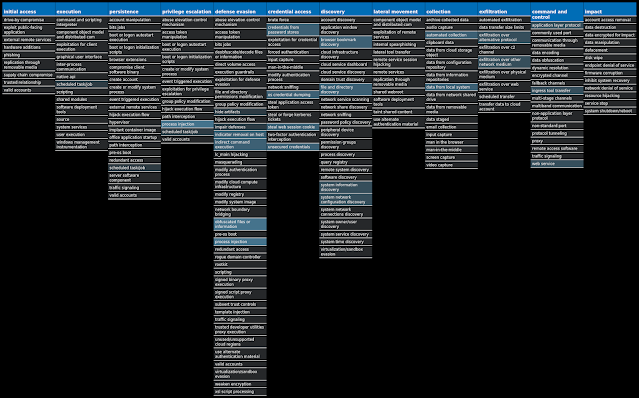
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Virus.Ramnit-9957454-0
Virus
Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It could also steal browser cookies and hides from popular antivirus software.
Win.Malware.Kovter-9957371-0
Malware
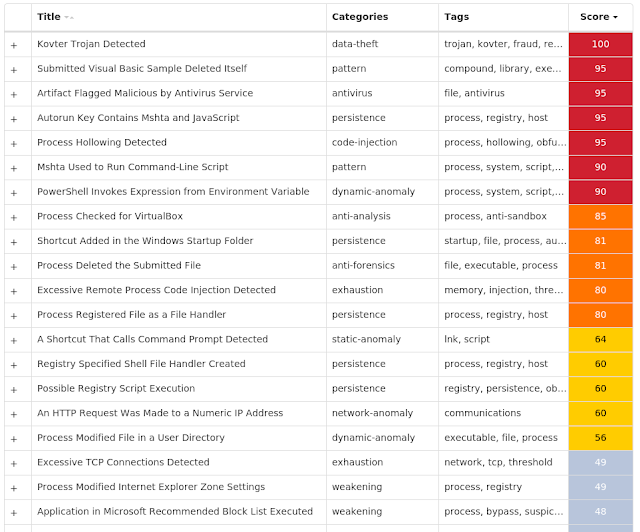
Kovter is known for it's fileless persistence mechanism. This family of malware creates several malicious registry entries which store its malicious code. Kovter is capable of reinfecting a system even if the file system has been cleaned of the infection. Kovter has been used in the past to spread ransomware and click-fraud malware.
Win.Ransomware.TeslaCrypt-9957356-0
Ransomware
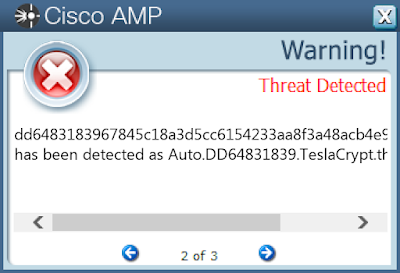
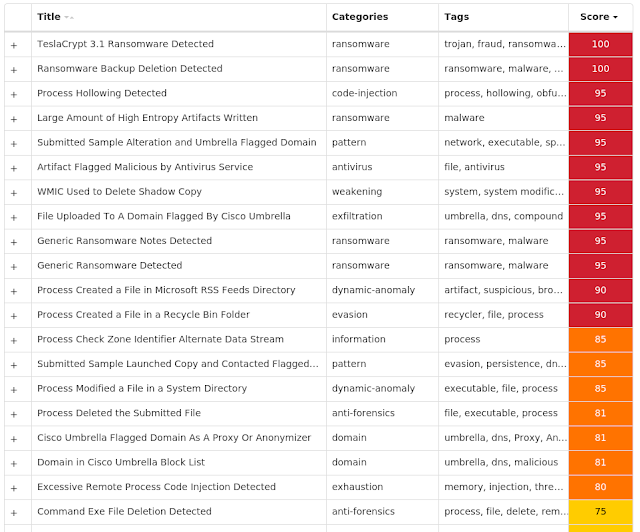
TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the extortion request, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily.
Win.Dropper.Shiz-9957241-0
Dropper
Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by victims visiting a malicious site.
Win.Dropper.Zeus-9957126-0
Dropper
Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing.
Win.Dropper.Tofsee-9957067-0
Dropper
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control.
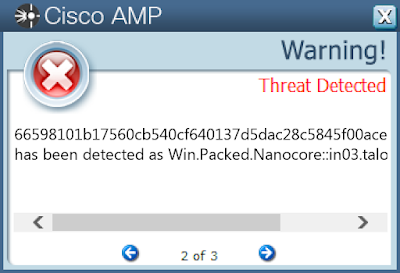
Win.Packed.Nanocore-9957022-0
Packed
Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes.
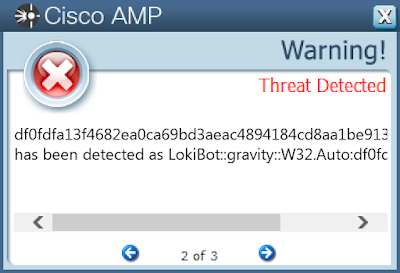
Win.Dropper.LokiBot-9957019-0
Dropper
Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature and can steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails.
Threat Breakdown Win.Virus.Ramnit-9957454-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusOverride
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallDisableNotify
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallOverride
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UacDisableNotify
16
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DoNotAllowExceptions
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: jfghdug_ooetvtgk
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: JudCsgdy
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
16
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
16
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}
16
{79345B6A-421F-2958-EA08-07396ADB9E27}
16
{7930D12D-1D38-EB63-89CF-4C8161B79ED4}
16
{7930CC18-1D38-EB63-89CF-4C8161B79ED4}
16
{7930DB19-1D38-EB63-89CF-4C8161B79ED4}
16
{<random GUID>}
16
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 195[.]201[.]179[.]207
16
142[.]251[.]40[.]142
16
46[.]165[.]220[.]145
15
72[.]26[.]218[.]70
15
208[.]100[.]26[.]245
14
35[.]205[.]61[.]67
14
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com
16
bungetragecomedy9238[.]com
16
kbivgyaakcntdet[.]com
16
oawvuycoy[.]com
16
fmsqakcxgr[.]com
15
jlaabpmergjoflssyg[.]com
15
kbodfwsbgfmoneuoj[.]com
15
oeuwldhkrnvxg[.]com
15
wstujheiancyv[.]com
15
yrkbpnnlxrxrbpett[.]com
15
ausprcogpngdpkaf[.]com
14
citnngljfbhbqtlqlrn[.]com
14
dvwtcefqgfnixlrdb[.]com
14
qislvfqqp[.]com
14
ypwosgnjytynbqin[.]com
14
wdgqvaya[.]com
14
gfaronvw[.]com
14
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe
16
%LOCALAPPDATA%\bolpidti
16
%LOCALAPPDATA%\bolpidti\judcsgdy.exe
16
%TEMP%\squhapjc.exe
16
%TEMP%\aacwxnxw.exe
16
%ProgramData%\qvqdlyny.log
16
%LOCALAPPDATA%\yjghhxdl.log
16
%LOCALAPPDATA%\aanqrsjf.log
16
\TEMP\naEnI23
6
\TEMP\YsbJf23
3
\TEMP\tbii193
3
\TEMP\sXw0IB2
1
\TEMP\DrPmx23
1
%LOCALAPPDATA%\bolpidti\pxAA0.tmp
1
\TEMP\48at1iwB
1
\TEMP\bvr7hgqN
1
File Hashes 040aba270ceca1eb00733e6733d2aa1da65f7a2c1f7aeff8f17c5d1070752535
0f95459d96bc1dd999753862126023c5a868d6b4350b6e72b6ca7aa683c3ade1
126aeea38387066d0cb15d2bf6476e7324abf67168defbc9e18352e68ef1174d
1d2f933a0c2c448e55f4106dae274696717ace70131035a4df42b6c5a373bb3e
283d8a891f3e3f478a74a3e5eacb12e4bcc803be1219c9c38cfdfb5890e2279e
2fbbaed010dc46bb6dac16bab57ee04e96965bea8142d37f7b3cb88a1e476e4f
587d34dd12dde3d009c85ba20416f1b354a4ae643777d28bb52ad8f9168cd4b0
5d490643405c093eab1f1a5b864943b0507400f0f3141de7f089c6ccc12fd316
7cacb6c76f80a1f500eacb7e9145fb7da0726343b54c547a4dc560d2f37fb18f
8f8d34773a5bfa95aea47bac3fb05fb11786312b6ef2a9223012b0bd88e167f9
99dafa7b30b55ca6c088739a27f3704862ba99fe051884478c5337ab5d507679
b297360c21d003261c25e314a2f16905086202ddc203765adc263ca5b6436ae0
b5f278f958e930c42e168e091ca7ff369aeab730d6626e6661bd51224ed93506
ba7ca9f0aa3d6ce0c63a81411e97deda8d952d06e9307f0058e0b3d08de72b87
c176340ea7e16d209b904405281425983679182aa7765e7a67646c87aa81c661
f7a787118f46b489f2a45ca7228322bebba7eb10aa00183cbde74773aa3753daCoverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
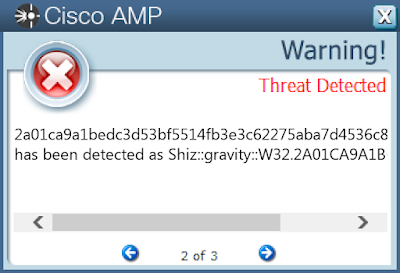
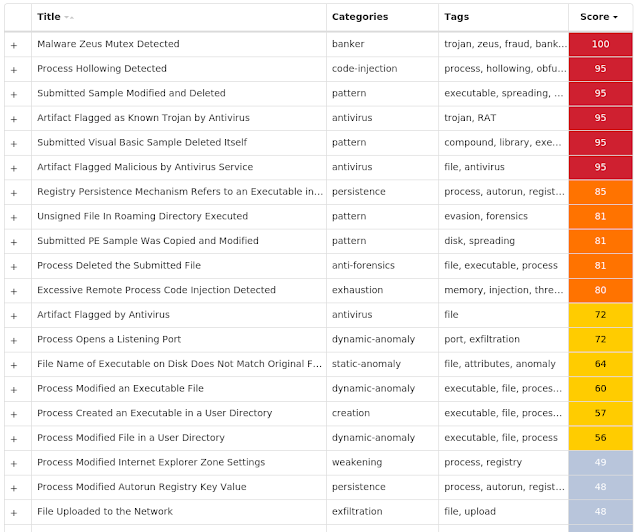
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Malware.Kovter-9957371-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
Value Name: DisableOSUpgrade
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
Value Name: ReservationsAllowed
25
<HKLM>\SOFTWARE\WOW6432NODE\XVYG
Value Name: xedvpa
25
<HKCU>\SOFTWARE\XVYG
Value Name: xedvpa
25
<HKCR>\.8CA9D79
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: vrxzdhbyv
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ssishoff
25
<HKLM>\SOFTWARE\WOW6432NODE\XVYG
Value Name: tbqjcmuct
25
<HKCU>\SOFTWARE\XVYG
Value Name: tbqjcmuct
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
25
<HKCU>\SOFTWARE\XVYG
25
<HKLM>\SOFTWARE\WOW6432NODE\XVYG
25
<HKCR>\C3B616
25
<HKCR>\C3B616\SHELL
25
<HKCR>\C3B616\SHELL\OPEN
25
<HKCR>\C3B616\SHELL\OPEN\COMMAND
25
<HKCR>\.8CA9D79
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting
25
<HKLM>\SOFTWARE\WOW6432NODE\XVYG
Value Name: svdjlvs
25
<HKCU>\SOFTWARE\XVYG
Value Name: svdjlvs
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: fcbburq
25
Mutexes Occurrences EA4EC370D1E573DA
25
A83BAA13F950654C
25
Global\7A7146875A8CDE1E
25
B3E8F6F86CDD9D8B
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 95[.]124[.]204[.]21
1
4[.]241[.]178[.]108
1
13[.]128[.]69[.]186
1
109[.]227[.]104[.]183
1
221[.]105[.]207[.]89
1
137[.]201[.]198[.]88
1
39[.]19[.]244[.]52
1
155[.]145[.]195[.]61
1
33[.]32[.]249[.]162
1
83[.]31[.]52[.]148
1
129[.]233[.]227[.]218
1
62[.]40[.]76[.]178
1
69[.]247[.]75[.]163
1
119[.]31[.]244[.]99
1
18[.]90[.]144[.]73
1
199[.]77[.]183[.]213
1
130[.]86[.]117[.]171
1
68[.]21[.]73[.]93
1
39[.]232[.]85[.]81
1
66[.]33[.]222[.]234
1
222[.]207[.]122[.]202
1
110[.]56[.]135[.]234
1
6[.]22[.]73[.]16
1
50[.]159[.]160[.]25
1
217[.]52[.]47[.]12
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com
1
reflex-demo-use-4[.]hannover-re[.]cloud
1
flyttstadning-stockholm[.]nu
1
Files and or directories created Occurrences %LOCALAPPDATA%\4dd3cc
25
%LOCALAPPDATA%\4dd3cc\519d0f.bat
25
%LOCALAPPDATA%\4dd3cc\8e9866.8ca9d79
25
%LOCALAPPDATA%\4dd3cc\d95adb.lnk
25
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\91b4e5.lnk
25
%APPDATA%\b08d66
25
%APPDATA%\b08d66\0b3c0b.8ca9d79
25
%TEMP%\VB<random, matching [A-F0-9]{3,4}>.tmp
25
File Hashes 00ebcb2374583159529a8dcb4d27e851246914eacfd1a3cf12d2cbd73f064294
093389823f1de777d5601b06cd106ff4380e408c1c8b39ac11cbfd93353d6314
0d93c80c3af7d2121af1d853585efd98693a06d376fd13464b3f52ca159c4cf1
0d947efab08d1bfc21b5abd2734ddfdbeeb9cb1d29346670a0128f7a531c6547
0dcc6cf63dc618f450127306942d91f8404e6a2cdb8326412f93ad36a892e9bb
134fea9f96af3845790cd2f8ba6f0a93b208469ae1a592da0135234387ef9410
194acafcf8cb53f889a9d77c8fb2cf511b3c27a989f4ce5e91e55153583fe318
1ee9b6d5909664f7d6d247088033be88d56aa674af63ae751ea625d9768b144b
26ce967cffd3a8650b2475553ecf09333dd04068f840c0d9f5077909766648e7
304c9568e3381dc75ec2f853c19d1de4f47fb40cf55f12d48612631728cb9740
3368e5d1bf347cd4cd6df01e4f60491d747adf1545a4e9006f062adc08eb95a3
35a3111fa824abf5130d52c377999d15450a7018a93ca406d88ccfe3e0913712
4084b83687be14dd8c8a98026c810fb0961abf771c8827b4779872b276055249
43ed7041f9096db31d7dad4f9cff7d6cd00c1ccdce383421638f8847b6bc568e
450f32871f007b32bdd06b40d1804b6e67c5625121eb0b2adbd276c8f48c1434
4625ab6090ec735194bac9aa2ce1cfc7fe9ad3db30cd2a220f4e1d1368878fdf
46c753dd41ac83e7f2a8b1dda5c2d46eddbd1f42a2197843ed6f7dff817f5a8b
477d345de8b818c1d855ab9d64578c1b39915624926108e97b9a9e65b2696bbd
488f1209f28a4be1f9c4fb2798de2bbcef4e1c8949467eee0cc8546abbd663d0
491d36c6a9d19e3e37871e83ac2fa710020093a7105617c9e371b5f1a6099b38
4a11d5d14df0fbb67f813a7425b4a9be69c5a33b0cc930c3f3886374b57eee43
4aabb5ca1a96a55395e53d8dd17e27552319b14264efca554c1fc78bec39a589
4bc7ba250aa345e8c96f8df64e846aeca90f8add2db2f269bdf452843c574398
4f4e505d0f4b1dca299ac0cbd8749adb91994e144e314f11e7677a4dc91a2f30
503d20ae3e5d78acf6a367f1f1c2fc177683e8136a5571e5320c3834070c3e97*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Ransomware.TeslaCrypt-9957356-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLinkedConnections
25
<HKCU>\SOFTWARE\XXXSYS
25
<HKCU>\SOFTWARE\XXXSYS
Value Name: ID
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0
Value Name: CheckSetting
25
<HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>
24
<HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>
Value Name: data
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hdtjbroygvvb
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: owvhajogulen
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: pyfepfifrjwi
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: xbmnkkfnowvh
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: gulenopvybnq
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tbqdqvojagik
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hajogulenopv
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: mgtbqdqvcoqj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ulenopvybnqj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: lpyfepfifrjw
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: epfifrjwiqou
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ifrjwiqouteu
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: teumgtbqdqvo
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: nrxbmnkkfnow
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: whmtlmoxvcsc
1
<HKCU>\SOFTWARE\159643D83772F
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: bmnkkfnowvha
1
<HKCU>\SOFTWARE\159643D83772F
Value Name: data
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: vcscusnnmyjx
1
Mutexes Occurrences ityeofm9234-23423
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 107[.]6[.]161[.]162
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences jessforkicks[.]com
25
heizhuangym[.]com
25
infotlogomas[.]malangkota[.]go[.]id
25
csucanuevo[.]csuca[.]org
25
snibi[.]se
25
danecobain[.]com
25
www[.]danecobain[.]com
25
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\ka.txt
25
%ProgramFiles%\7-Zip\Lang\kaa.txt
25
%ProgramFiles%\7-Zip\Lang\kab.txt
25
%ProgramFiles%\7-Zip\Lang\kk.txt
25
%ProgramFiles%\7-Zip\Lang\ko.txt
25
%ProgramFiles%\7-Zip\Lang\ku-ckb.txt
25
%ProgramFiles%\7-Zip\Lang\ku.txt
25
%ProgramFiles%\7-Zip\Lang\ky.txt
25
%ProgramFiles%\7-Zip\Lang\lij.txt
25
%ProgramFiles%\7-Zip\Lang\lt.txt
25
%ProgramFiles%\7-Zip\Lang\lv.txt
25
%ProgramFiles%\7-Zip\Lang\mk.txt
25
%ProgramFiles%\7-Zip\Lang\mn.txt
25
%ProgramFiles%\7-Zip\Lang\mng.txt
25
%ProgramFiles%\7-Zip\Lang\mng2.txt
25
%ProgramFiles%\7-Zip\Lang\mr.txt
25
%ProgramFiles%\7-Zip\Lang\ms.txt
25
%ProgramFiles%\7-Zip\Lang\nb.txt
25
%ProgramFiles%\7-Zip\Lang\ne.txt
25
%ProgramFiles%\7-Zip\Lang\nl.txt
25
%ProgramFiles%\7-Zip\Lang\nn.txt
25
%ProgramFiles%\7-Zip\Lang\pa-in.txt
25
%ProgramFiles%\7-Zip\Lang\pl.txt
25
%ProgramFiles%\7-Zip\Lang\ps.txt
25
%ProgramFiles%\7-Zip\Lang\pt-br.txt
25
*See JSON for more IOCs
File Hashes 11bf02df58d00bf7dfc22e46b27db8a2cfcb9c8d03ad38b2e3baafa193bbbd89
1a4a1e76c6d2dc585ce77c9be7163163c0d614d5668a0c83601bb3d6f91376a0
1c2ddbf956ee1e2b40472b70603371ed21817fbf95d5825b2f75bbf6f9728089
1d4114c8ee19f343f3dcf80a542295af29df63d9745ad77cce43562c909551c5
2f1f927c219ccfcffeb997c9433733a04200ae35a2fc0c48fc07cb49062cddc7
3ef3021ce3ffdffcfba2bd590c4186c3a3ecdd3b6ce40d51d2500897fb55ffb0
41ab6446df889a5a24e4e859146c0225d13a2ba8553c83cb93e45017212884b2
4bae8a4e0124724e695c10202a94eec99cf5990507fbc94ec3f08e11de3ce2c2
4dc12416bf7c3be9d573c8fa07847050307bd05cb67480e3c3874696614b73e9
4fa8c1eaa4846a8a06fb2480a746d5526f743cee314f7101db0508577bdd3776
5207a70e0e818741279d7c25c0d9cb6be136a4fc8ca8fe6f48112c4d0572d64f
5aaad74cb36db78ad6da4d499a75c41d2ace8b97ff8f88c5bc7f738ad353d3d7
67e2caf00dd0293080cb5b45d2db11d4f567ce9a3d6fd5c9723358d18da80e71
6a9e6e5c50b3b90376530ee4e9e81cdf5cdc9b7c07cdb71207b3a1799f77ec7a
6ab8f9569a70beb0f96bf4e030381e70bcce7703b308a05542f4ccf1b6002af9
71f0f23220cb0f5d8b31fce30f08bc1687acd675b7c3a8ae7e0538bacb0d3eec
a3a6b4f405f2175af97128c64d9ad68700e05e22d66c43dad966add8436af79f
a760b60722cfa7c719e79b5c97cfe789720c6300a200421c846e13287cdb160a
d8be6b950a872b1b7c752cc83a5440b4cfe62870097df78794f10986fb7fcb63
dd6483183967845c18a3d5cc6154233aa8f3a48acb4e9cccd3606afe7d4d7eef
de5dc2aed0e06894e0bb1292fb68343fadc46b489e6c85e6cca56cf5bad70c09
e1a00e6beb02475b4bdd8d821ccac3e67bbafd182332cbf35a45c6766ad83b87
e8c460f171e964db6fff16eb38684b9ec82134c4fd1a1cdc64ba338941ef1199
f69edf352cdca309c7faa71f87a429daf2b46e4ae6ed85a25ff03aa34b4702c4
fbcec257455e5546a294ec1534f7e11f05d144c73ef583a0e891e14759e133ebCoverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Shiz-9957241-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT
Value Name: 67497551a
23
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: 98b68e3c
23
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: userinit
23
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: System
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: load
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: run
23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: userinit
23
Mutexes Occurrences Global\674972E3a
23
Global\MicrosoftSysenterGate7
23
internal_wutex_0x000000e0
23
internal_wutex_0x0000038c
23
internal_wutex_0x<random, matching [0-9a-f]{8}>
23
internal_wutex_0x00000448
22
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]21[.]200
11
45[.]33[.]23[.]183
7
45[.]79[.]19[.]196
6
198[.]58[.]118[.]167
5
45[.]33[.]30[.]197
5
72[.]14[.]185[.]43
4
45[.]56[.]79[.]23
3
45[.]33[.]20[.]235
3
72[.]14[.]178[.]174
3
96[.]126[.]123[.]244
2
45[.]33[.]2[.]79
2
45[.]33[.]18[.]44
2
85[.]94[.]194[.]169
1
173[.]255[.]194[.]134
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fotaqizymig[.]eu
23
cidufitojex[.]eu
23
xukuxaxidub[.]eu
23
digofasexal[.]eu
23
gatuvesisak[.]eu
23
lyvywyduroq[.]eu
23
qetekugexom[.]eu
23
puvacigakog[.]eu
23
xuboninogyt[.]eu
23
cicezomaxyz[.]eu
23
dixyjohevon[.]eu
23
fokisohurif[.]eu
23
volugomymet[.]eu
23
maganomojer[.]eu
23
jefecajazif[.]eu
23
qedylaqecel[.]eu
23
nojotomipel[.]eu
23
rytifaquwer[.]eu
23
kepujajynib[.]eu
23
tuwaraqidek[.]eu
23
xuqeqejohiv[.]eu
23
pumebeqalew[.]eu
23
cinycekecid[.]eu
23
divulewybek[.]eu
23
nozulufynax[.]eu
23
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp
23
File Hashes 00180daca1b8b50f272a020eee54d9fa90094881d1d5ac3cfd9b8ef75cf1e6f4
0782fb4469241b17dacdb3040403425c5dfa726afe7608695d798c40ba0468df
096567f0324ce9d8dafbd8b2fa07baa4c024e734cee78966a2e1bda01cc6aab1
0b575be1b7f34effd28837fcbd89afb217202ce9dc99c23bd59d858343a2cebe
0b579d7b50d2036a46977367a6673faf3e7c1861f30138f19cfc64e2240f7ef4
0e4553fcdf4b905c069986826b4190fae4c301a72a31d84f70ebc82a3a4e08d2
10845e4f34b629a880154930d82e6533e4f2988ff7f8d190da77258b04c53a33
1422cdfe1c27c71dc5cac99bc1b94da21730d123c84808fb275a0a9ad4608ea6
1613108f8d6a07cf52c9342e2bc34ef95c142ccd0945e8863876499f373ee276
1a1075298b76367a0f09e1d32a33f3795d7fcedfbf562f8e97a73fd84b044d44
1a776926ba733dd76ac52335f28bca9f834eb424b9c3344e18c53be7bc488e16
1b2b7d611569a0ed98e7c8592b1ab68f89e5f9b9bb46004f40ab8e238da58c68
1b658f725eccb4d5b15339017f834e54e03280757ef214f98ebf7c02584b1259
1cafff0eb6f9b746d49ce3e6b29dc0581145df229089c43f234693a7f3c01911
1d6a5170f8caf1bac36b69953b6df43da07b1b5fbd2c6c135146edfb975d6c0d
1e12db0b8596f9b40eb120f663796ea2067a5af27fdc9c892d4ffdb042a88df7
1f16c27403f51502cd5cb7b15eac5e53c23b8f8d25f647ebc216cf5f2e57940a
206ffd6d82b9934e50b1de5555e5a544353f4dd8c59c7fe4c8c501024fc12438
25c3635d6874809bb1163763187c72f827756d773cca5aaf93d288015275ba50
27f644aed21754919d8236e2ec0c07ac85a65694a4c2eab289cef54905460545
2a01ca9a1bedc3d53bf5514fb3e3c62275aba7d4536c806a227f83b3265458d0
2a7755e96cff2e3186fde0936b3cf86648f242a5d9c0c3ba8903852905a5bfbf
2bb61e2487b38915a8a0a5b46ea26ea16b931a09a0acd9fe93fe58f63608caa5
2be38d866007d818551826d7b4eb1187f0a2e881634caa08d281ad11fed50b8f
2c77f57754219ee31db301679821ce62e0f2ba5326c04cc0685c53b7135c5a24*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Zeus-9957126-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY
Value Name: CleanCookies
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting
1
<HKCU>\SOFTWARE\MICROSOFT\XODYUZ
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Savyomzauc
1
<HKCU>\SOFTWARE\MICROSOFT\XODYUZ
Value Name: Seroymo
1
Mutexes Occurrences GLOBAL\{<random GUID>}
1
Local\{<random GUID>}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 199[.]2[.]137[.]201
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wearesofamousthatwestayontop[.]com
1
sunobowttteek2[.]biz
1
Files and or directories created Occurrences %TEMP%\tmp8f23b8f6.bat
1
%APPDATA%\Axfo
1
%APPDATA%\Axfo\ycner.elz
1
%APPDATA%\Ebyhvo
1
%APPDATA%\Ebyhvo\feyn.exe
1
%APPDATA%\Iqxa
1
%APPDATA%\Iqxa\oviku.ibc
1
File Hashes 01e483b094b3112e7cec3c76f73158d4b1897dedabef0bc03cdfe2e8fcfa7e9e
0439391736bebd073343fa84a894df1729747504cd228bea68b0657c4912bfcf
04b75511bf54e30bb62c43021b92070444fcaae9a6f461339efb112eb1ee9154
1308d38b43ffa2dca4d4a86d80cc69e14608c4f0f8e91c422ecbaf4886d088b2
182cc0c11d4cd6193428bd463b14df9b00bb2f69c351790142d660ed7d0f446b
1849049071f08094dc3b8fd471a77df1d4a06583e1a118bcdcf9668990ae4bf0
1fe334f9fb9b43a9a4ab48df2cf6612037bb12dd4b614379766567cfa70a788e
2580d43c6b5a0ce5556bce9857ebb208be8f3bc82705b1cd9df990cca3bea01d
2b14c895108d261f1dfa2ee718cda6c9aadf85540469c870d5c5ad8b10357a30
4248058bec9172b47b4b55e51a06f9bf57d9e848f35f0c0b42695ce9d66c0fab
43d0cbec39e4b9b041353774272484ed5074ec6dfd4a6fbd090a8a4ba3408b8b
517770a8a2092e068ad8d3eafb35039542500297426aab7be084eb7688639093
5ee6e167282e0c6917d36029e08cddf2d4d05121c48b4700782534427c72ce0b
623bcd68d0f7827540471935161c4d5094c3a88965f186a1492822ffb3ff1f18
6bbe78119dac51783873c433e28a5d24851b6fe7da23c822ec2ace75fd9c4153
702808b62a234ddbdb1d48c904ea6028d63f2d69782cc1e5ee5fe7c18e732376
79cbbb34180a74893002d4532e8310bc44a0718a3b990e866e1f4ad3ba82765a
807dea0f6d360b8de2df42defa29edf406b3596e78afca618ea984b2b9396272
8245c00bc1c311baba9ca23653af3432e2d8a084309c32dbc04da5adbf17bea8
8703fccdeecb0ce3afa979c06385e7e9d4361272aa2999c5f1eeba9ee9d6c174
99acfdfb1b763979e7507c245cc25849c09fa5bfcbf830b3f6d7638663e8f772
9b0f72b4ba66d99726123b379fed030b9257281b9f493e15b21e5dbc0b1b392e
a546480f68c4789f6630260b515e30ba27d53cdb256d186018c29ab89c279f8b
a70d2c24cc882a37161aed809bb1311edfe9fabfecb3496872884de46bcd30f2
a7dfcc11b3d17fa4f66cfc5bd08872f286705056bf283fca4e3bb3b4310ef407*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
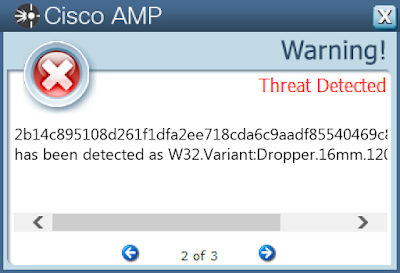
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Tofsee-9957067-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config4
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NXZUQIHD
Value Name: Description
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\nxzuqihd
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\EOQLHZYU
Value Name: Description
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\eoqlhzyu
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\TDFAWONJ
1
Mutexes Occurrences Global\07ada3c1-08f4-11ed-b5f8-00501e3ae7b6
1
Global\067cf3c1-08f4-11ed-b5f8-00501e3ae7b6
1
Global\08e8d341-08f4-11ed-b5f8-00501e3ae7b6
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 212[.]77[.]101[.]4
4
142[.]250[.]72[.]100
4
31[.]41[.]244[.]82
4
31[.]41[.]244[.]85
4
80[.]66[.]75[.]254
4
80[.]66[.]75[.]4
4
31[.]41[.]244[.]128
4
31[.]41[.]244[.]126/31
4
185[.]165[.]123[.]13
4
208[.]71[.]35[.]137
3
208[.]76[.]51[.]51
3
216[.]146[.]35[.]35
3
199[.]5[.]157[.]131
3
208[.]76[.]50[.]50
3
195[.]46[.]39[.]39
3
23[.]90[.]4[.]6
3
194[.]25[.]134[.]8
3
144[.]160[.]235[.]143
3
193[.]222[.]135[.]150
3
209[.]244[.]0[.]3
3
119[.]205[.]212[.]219
3
67[.]231[.]152[.]94
3
31[.]13[.]65[.]174
3
117[.]53[.]116[.]15
3
172[.]253[.]115[.]26/31
3
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net
4
249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
4
249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
4
249[.]5[.]55[.]69[.]in-addr[.]arpa
4
249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
4
249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
4
microsoft-com[.]mail[.]protection[.]outlook[.]com
4
microsoft[.]com
4
www[.]google[.]com
4
whois[.]arin[.]net
4
whois[.]iana[.]org
4
aspmx[.]l[.]google[.]com
4
wp[.]pl
4
ameritrade[.]com
4
mxa-000cb501[.]gslb[.]pphosted[.]com
4
mx[.]wp[.]pl
4
svartalfheim[.]top
4
www[.]instagram[.]com
3
mta5[.]am0[.]yahoodns[.]net
3
hanmail[.]net
3
freenet[.]de
3
korea[.]com
3
t-online[.]de
3
o2[.]pl
3
nate[.]com
3
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile
4
%SystemRoot%\SysWOW64\config\systemprofile:.repos
4
%SystemRoot%\SysWOW64\nxzuqihd
1
%SystemRoot%\SysWOW64\eoqlhzyu
1
%SystemRoot%\SysWOW64\tdfawonj
1
%SystemRoot%\SysWOW64\hrtokcbx
1
%TEMP%\oacsevkh.exe
1
%TEMP%\htrzurov.exe
1
%TEMP%\rzwntxyj.exe
1
%TEMP%\mcilsztg.exe
1
File Hashes 1b64011f2f80b0ded096cbdb81c2bdac9786dc8a4ea7425b15547bdca34e043f
34c17bb102b2ed718471668da1ddc7daf397175979582942bf89d8e272cfa141
59bdcd1599938f1c5c2845d1fef198a0d97b03744432fc6705c9c67f13eedab4
64d6709c3cfbf8765e9434abfe6fc8bad67d87a3e4fe0622e68aa1d15aac8d6b
6857bce2c5f73e1d1bc4b14cb7b281beb33fed8cb580a43f236460c2af0e65e2
6eb7dd7f943a22822b0aaef6301d32b54eb43e432070c41b7d3c6a3d041ec8b3
6f3ef01ce9f2896b54c06fe4cd5e5769dda3a958868557a20469feb21c7e1273
79699aa58081b925c0b75140f0110f3ebf9a47e9bc8ba1699d53d7b14cb49591
7e2975f6cb11bb324bd49ec6fd4b77478e3488bf99fe623851a29f06e9b1fb37
89974e5d8be578da3cc6c0a33398659aabb160cdb03f7158066969f430dab796
9449f5dd9a6728664a3be973ccb91adbf64ffe980ff96de05a0419eb0a77bbd7
b77c2b3942f50e8fef2440481de894d506418f7a7c35fb29d40cfa8ce795ebf4
cbbc899843ca8f5908c27645960a33952fbecbf3d5cefc5054ab1dd023bb8582
d0596ec9d08cdd81f86e07d5ab70b518c6ca23a9ed4f557d041d3307b3ca7020
d518bbcb40208cfd7cbb6965e1647fabd5f65f2f1c1520e1217996957a1ada8d
e6411e18f8a1096f9b5d7528a24f6acdf1f97d120dd0dae4d76703c8eb5e4040
efced050e17235d050db86e0d763a07cfff375771d586736bbd17520725f1ebfCoverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
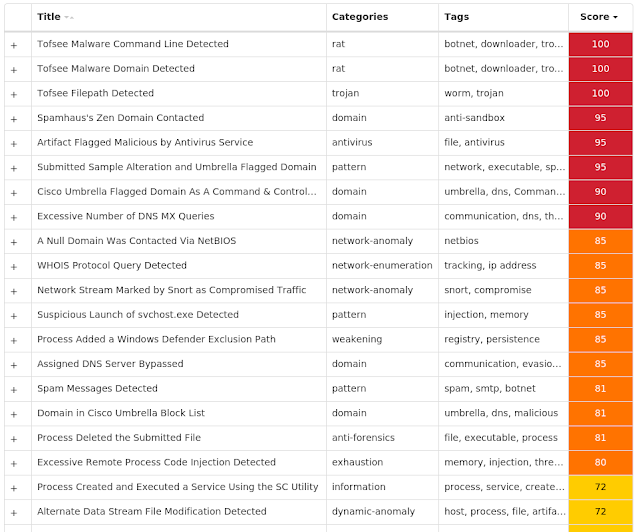
Secure Malware Analytics
Umbrella
N/A
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Packed.Nanocore-9957022-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\WINRAR SFX
Value Name: C%%Users%ADMINI~1%AppData%Local%Temp
9
<HKCU>\SOFTWARE\WINRAR SFX
9
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: AGP Manager
4
<HKCU>\SOFTWARE\7E3975E4EF230D7D9195
2
<HKCU>\SOFTWARE\7E3975E4EF230D7D9195
Value Name: 7E3975E4EF230D7D9195
2
Mutexes Occurrences Global\{8c60c66e-3013-47af-8bbe-7df02dd28d12}
4
Global\Protect7d723a8e.dll
2
\x6f21\x705\x43\x8f323\x746a3\xb096e\x27\x99491\xfa05\xe581\x7c\x22\x199\x3b2f\x1a33\x92ec\x7e\x4b\x55\x5b8c1\xa5894\x10e\x21a1\x4f\xfeaaf\x36a\x466\x78a\x1670\x1e3\x9f\x4a3\xe19a\x3c2\x253bd\x79\x7e\x6ce\x3a\x768\x1ae2\x36\x1bd43\x2ec0a\x58e\x75\x1994\x3bd\x25\x74c\xd0e0e\xfff90\x99de\x66a\x4c\x343\x5a554\x6a\x157\x3a\x39\x231\xb1cb0\x415\xe25f\x799\xd31\x57\x61e\x78678\x62\x1db\xc42cb\x314fd\x7e8\x748\x1bf1\xd40d\x3c9\xff4a\x34\x1ce54\x24\x3a33\xd89ea\x1a44d\xa08a7\x415\x62\x10e\x381\xd5\xbb640\x53c3\xea65\x34c\x74\x3d5e4\x4f\xf1948\x42050\xcb0fc\x46\x41e\x742d\xa328\x256\x3a\xfffd\xccc7\x14b54\x5a\x5c7\xa9ef7\x5ab\x7b\x10b246\x32123\x86f8\x77\x662\x41c3\x6bf9\x4a9\x367\x76\x328\x66e\xdfbe8\x424ec\x4239\x45\x87d0e\x8b461\x63\x6c9\xa8344\x65\xba571\x2d5a5\xc4236\x5d\x438f\xd2\x31\x6bb\x45\xb5d8d\x6d69f\x14ee6
2
Global\11971d21-08aa-11ed-b5f8-00501e3ae7b6
1
Global\15c3b7a1-08aa-11ed-b5f8-00501e3ae7b6
1
Global\1bb73741-08aa-11ed-b5f8-00501e3ae7b6
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 74[.]139[.]80[.]187
6
145[.]14[.]144[.]94
1
145[.]14[.]144[.]171
1
145[.]14[.]145[.]198
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wirelock[.]000webhostapp[.]com
3
Files and or directories created Occurrences %TEMP%\RarSFX1
10
%TEMP%\RarSFX0
10
%TEMP%\RarSFX2
5
%ProgramFiles(x86)%\AGP Manager
4
%ProgramFiles(x86)%\AGP Manager\agpmgr.exe
4
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5
4
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs
4
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator
4
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat
4
%TEMP%\RarSFX3
3
%TEMP%\RarSFX1\BouncyCastle.Crypto.dll
3
%TEMP%\RarSFX1\Google.Protobuf.dll
3
%TEMP%\RarSFX1\JLibrary.dll
3
%TEMP%\RarSFX1\MySql.Data.dll
3
%TEMP%\RarSFX1\Newtonsoft.Json.dll
3
%TEMP%\RarSFX1\Renci.SshNet.dll
3
%TEMP%\RarSFX1\Ubiety.Dns.Core.dll
3
%TEMP%\RarSFX0\Release.exe
3
%TEMP%\RarSFX1\VACBypass.exe
3
%TEMP%\RarSFX0\VACBypass.sfx.exe
3
%TEMP%\RarSFX1\ProcessInjector.dll
2
%TEMP%\RarSFX1\Venge.exe
2
%TEMP%\Protect7d723a8e.dll
2
%APPDATA%\MSConfig.exe
2
%System32%\Tasks\'MSConfig'
2
*See JSON for more IOCs
File Hashes 057168fa7b59c38e34fddae10931b74390d7b16488c6ad927bdd1f463041667c
18f9814993009f5ef87b0e0703644273e51658f5882344b562501c0039931a4d
2425730fc69eb3d59994dfbec8080540a2df37d62d76668aa7f6253631ec697c
66598101b17560cb540cf640137d5dac28c5845f00aceca4262a56461219ccdc
afdd30c190cf43d78f3cdee38bdc2786dfbbaf2d3c2be8f6d9a7c539f097f4fc
c08c4a75c4a5e26e98643b054d0dd19b7c2b729531402d97ac75a17aeef7d17d
c1c5d36e2794e08c6b400476b1a51f4c1c9b27ffee593dac838730ba27cc363b
d675794864f828743967e774b888663ee3dbff471c159fbadb3a699c7085e658
df9cb829ee95a1722dd61bfcb10145e1b11881fe1a86b296936a8aaa3011fcff
e6f42069d0c8ef236da20b41e61c25cc593ac7265057c996b35b67d73b7154e8Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.LokiBot-9957019-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Mutexes Occurrences 3749282D282E1E80C56CAE5A
7
uoXVcKrtOqoPVAWBhQA
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 198[.]187[.]30[.]47
4
193[.]122[.]130[.]0
2
132[.]226[.]247[.]73
2
158[.]101[.]44[.]242
2
37[.]0[.]11[.]227
1
45[.]133[.]1[.]20
1
47[.]88[.]22[.]122
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences checkip[.]dyndns[.]org
6
sempersim[.]su
1
Files and or directories created Occurrences %APPDATA%\D282E1
7
%APPDATA%\D282E1\1E80C5.lck
7
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
7
%System32%\Tasks\Updates
1
%TEMP%\tmp4B83.tmp
1
%APPDATA%\VQJJRC.exe
1
%System32%\Tasks\Updates\VQJJRC
1
File Hashes 22265bacbef33a949cd224cf527e8338b03f8d8a5e04acbbd3632e28af7e785a
2c93ec8bdcb28ec4793fb55a4ce8159287745c11d5cf36ca085c74c3925ff2e2
3e93bbc3ac47bb2cd468a1e58e9369a54215dfaaece767e99e40057ed7dd4c50
669363383d4189a6716b953aaf4663655dc22e960e002f100c3ef5012275db79
67fb6d554fb4128454a0fbaa1dd0becda062d72be7dfbb37a4b5dc1b7b5629ce
6bacc8bd474bde817e968bcedfe508492a100eb73749894ba4b61b2f6d0dec0d
6da89945dd9f904c718c4ae1de7aae9d311ac71317865718aca051854ff4913d
87878b131d80c5ad134ee68932fe4defbf5067a0a871f0cadba3e163f5e3cefd
99606bfc40c8743b6bc1a3059cf491b9105d1bbc5d3bd3de647781bce6d9636a
998474158374c53d0b802f00e92e9ef00d398321b90dab0464d50df65225a5e5
bf4a9315215e16a2239e01125082218867ffc5900e44de517d4c2b786ff1fa8a
c29b9d1075e86788bab4a9e75334f36de07c1feb22500759db93d9379c875171
c86ba22021597e8876b4432a5ffb954f495e7f2a0a926af5f630e1f3e3e8acf5
d94a1e9281426e715a46338e94e6b16c614a9ff271da27b3a52c3ddc2985d914
df0fdfa13f4682ea0ca69bd3aeac4894184cd8aa1be913ca5954bb4394af1b2e
df77c795653ea7686d5525118bc05d748a3393793a99960946dfa3bc5e188e02Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK