Welcome to this week’s edition of the Threat Source newsletter.
I could spend time in this newsletter every week talking about fake news. There are always so many ridiculous memes, headlines, misleading stories, viral Facebook posts and manipulated media that I see come across my Instagram feed or via my wife when she shows me TikToks she favorited.
One recent event, though, was so crushing to me that I had to call it out specifically. Former Japanese Prime Minister Shinzo Abe was assassinated earlier this month while making a campaign speech in public. This was a horrible tragedy marking the death of a powerful politician in one of the world’s most influential countries. It was the top story in the world for several days and was even more shocking given Japan’s strict gun laws and the relative infrequency of any global leaders being the target of violence.
It took no time for the internet at large to take this tragedy and immediately try to spin it to their whims to spread false narratives, disinformation and downright harmful fake stories that mar Abe’s death and make a mockery of the 24/7 news cycle and the need for everyone to immediately have their own “take” on social media.
Shortly after Abe’s murder, a far-right French politician took a false claim from the infamous online forum 4chan that video game developer Hideo Kojima was the suspect who killed Abe and shared it on Twitter. The politician, Damien Rieu, even went as far to connect Kojima to the “far left,” linking to pictures of the “Metal Gear Solid” creator wearing a shirt depicting the Joker and a bag with Che Guevara’s face on it. Rieu’s tweet was taken as fact by a Greek television news station, which also aired a report that Kojima was the assassin.
Thankfully, this claim was quickly debunked and the politician issued an apology, but Kojima and his company have threatened legal action over the ordeal (as they should). This is an appalling scenario in which social media was quick to assign blame for Abe’s assassination, then picked up by an influential person and even making it to a reputable international news station. This goes beyond the realm of the typical “Russian bot” fake news we think of this was a failure to run any simple fact checks before reporting a damning claim about someone. Imagine if it was just anyone who was blamed for Abe’s assassination, and not someone like Kojima who has a very public platform and the funds to fight these claims.
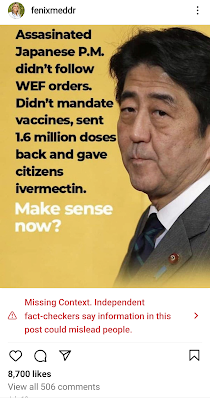
People also took the opportunity within the first few hours of Abe’s death to try and craft their own narrative using fake news and misleading information. A viral claim that he was killed over his COVID-19-related policies made the rounds, though these claims were later proven verifiably false. Another completely fake and manipulated screenshot claimed to show that Abe had tweeted shortly before his death that he had incriminating news about U.S. politician Hillary Clinton.
I went on Instagram and found a still-active post from an account with more than 54,000 followers that indicates that Abe was assassinated because he had less-than-strict COVID policies that did not align with the “global agenda.” Instagram flagged the post as “missing context,” but does not flag it as downright false and the content is still accessible as of Wednesday afternoon.
What disturbs me the most about this whole event is that nothing is off limits for social media users to bend to their whim. I suppose I can't say I’m surprised — ESPN even recently fell for something as silly as a fake TikTok video alleging to show a UPS driver dunking a basketball while jumping over a car. But it is a stark reminder that when breaking news occurs, no matter how serious or dangerous it is, there’s always going to be people online who will be spreading fake news, disinformation and/or misinformation. This makes me miss the days when the biggest fake news story out there was Balloon Boy.
The one big thing
The U.S. Cybersecurity and Infrastructure Security Agency is asking all federal agencies to patch for an actively exploited Microsoft vulnerability disclosed last week. By adding CVE-2022-22047, an elevation of privilege vulnerability affecting the Windows Client Server Runtime Subsystem (CSRSS), to its list of known exploited vulnerabilities, agencies are compelled to patch for the issue by Aug. 2. Microsoft and CISA both say attackers are actively exploiting the issue in the wild.
Why do I care?
This vulnerability is the only one disclosed as part of last week’s Patch Tuesday that’s been exploited in the wild. An attacker could exploit this vulnerability to execute code on the targeted machine as SYSTEM. However, they would need physical access to a machine to exploit the issue. That being said, if CISA is warning users that it’s being actively exploited in the wild, it’s good of a time as any to remember to patch.
So now what?
Our Patch Tuesday blog post contains links to Microsoft’s updates for Patch Tuesday and a rundown of other vulnerabilities you should know about. Additionally, we have multiple Snort rules that can detect attempts to exploit CVE-2022-22047.
Other news of note
The U.S. Department of Homeland Security declared the Log4shell vulnerability is “endemic” and will present a risk to organizations for at least the next decade. A new report into the major vulnerability in Log4j declared that the open-source community does not have enough resources to properly secure its code and needs the public and private sector to assist with the implementation of patches. They also warned that there are still many instances of vulnerable software that attackers could take advantage of. The DHS report also says the original vulnerable code could have been detected in 2013 had the reviewers had the time had the appropriate cybersecurity knowledge to spot the flaw. That being said, the investigating panel said there were no major cyber attacks against U.S. critical infrastructure leveraging Log4shell. (Dark Reading, Associated Press, ZDNet)
The European Union is warning that increased cyber attacks from Russian state-sponsored actors run the risk of unnecessary escalation and spillover effects to all of Europe. A formal EU declaration says that member nations “strongly condemn this unacceptable behaviour in cyberspace and express solidarity with all countries that have fallen victim.” A Lithuanian energy firm was the recent target of a distributed denial-of-service attack that the country said was the largest cyber attack in a decade. Belgian leaders also say their country was recently targeted by several Chinese state-sponsored groups. (Bleeping Computer, Council of the European Union, Infosecurity Magazine)
A relatively small botnet is suspected to be behind more than 3,000 recent distributed denial-of-service attacks. The Mantis botnet, which is suspected to be an evolution of Meris, has already targeted users in Germany, Taiwan, South Korea, Japan, the U.S. and the U.K. Most recently, it launched a malware campaign against Android users in France, using malicious SMS messages to lure victims into downloading malware that adds devices to the botnet’s growing system. Security researchers say users have already downloaded the malware about 90,000 times. (Bleeping Computer, ZDNet)
Can’t get enough Talos?
- Vulnerability Spotlight: Issue in Accusoft ImageGear could lead to memory corruption, code execution
- EMEAR Monthly Talos Update: Training the next generation of cybersecurity researchers
- Beers with Talos Ep. #123: Hunting for ransomware actors on *whispers* the dark web
- Talos Takes Ep. #104: The psychology of multi-factor authentication
- Pakistani Hackers Targeting Indian Students in Latest Malware Campaign
Upcoming events where you can find Talos
A New HOPE (July 22 - 24, 2022)
New York City
CTIR On Air (July 28, 2022)
Talos Twitter, LinkedIn and YouTube pages
BlackHat U.S. (Aug. 6 - 11, 2022)
Las Vegas, Nevada
DEF CON U.S. (Aug. 11 - 14, 2022)
Las Vegas, Nevada
Most prevalent malware files from Talos telemetry over the past week
SHA 256: 9f1f11a708d393e0a4109ae189bc64f1f3e312653dcf317a2bd406f18ffcc507
MD5: 2915b3f8b703eb744fc54c81f4a9c67f
Typical Filename: VID001.exe
Claimed Product: N/A
Detection Name: Win.Worm.Coinminer::1201
SHA 256: e4973db44081591e9bff5117946defbef6041397e56164f485cf8ec57b1d8934
MD5: 93fefc3e88ffb78abb36365fa5cf857c Typical Filename: Wextract
Claimed Product: Internet Explorer
Detection Name: PUA.Win.Trojan.Generic::85.lp.ret.sbx.tg
SHA 256: e12b6641d7e7e4da97a0ff8e1a0d4840c882569d47b8fab8fb187ac2b475636c
MD5: a087b2e6ec57b08c0d0750c60f96a74c
Typical Filename: AAct.exe
Claimed Product: N/A
Detection Name: PUA.Win.Tool.Kmsauto::1201
SHA 256: ea500d77aabc3c9d440480002c3f1d2f2977a7f860f35260edda8a26406ca1c3
MD5: 5741eadfc89a1352c61f1ff0a5c01c06
Typical Filename: 3.exe
Claimed Product: N/A
Detection Name: W32.DFC.MalParent
SHA 256: 125e12c8045689bb2a5dcad6fa2644847156dec8b533ee8a3653b432f8fd5645
MD5: 2c8ea737a232fd03ab80db672d50a17a
Typical Filename: LwssPlayer.scr
Claimed Product: 梦想之巅幻灯播放器
Detection Name: Auto.125E12.241442.in02