Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 29 and Aug. 5. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
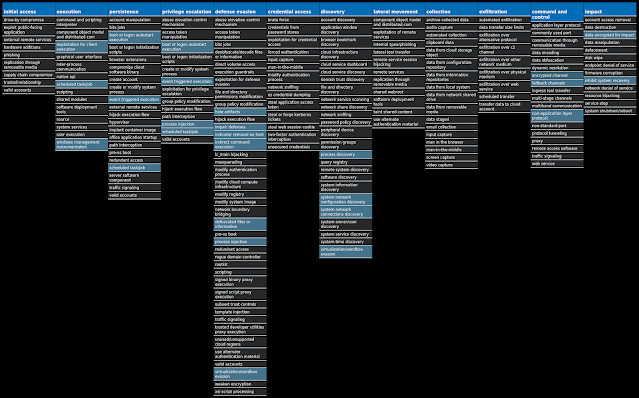
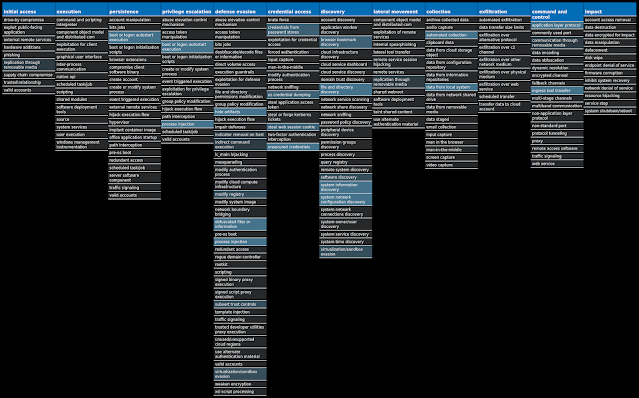
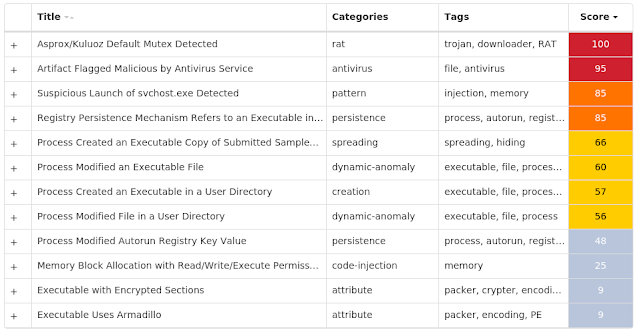
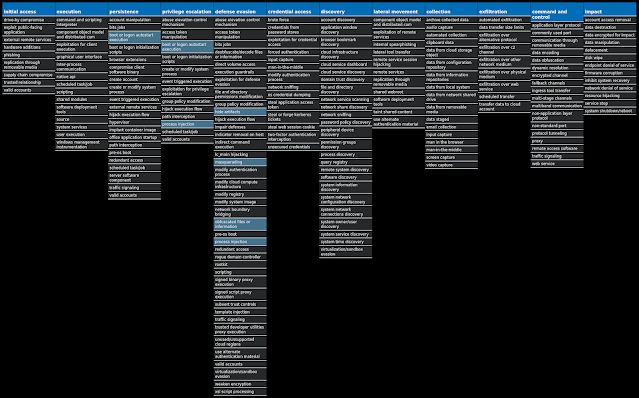
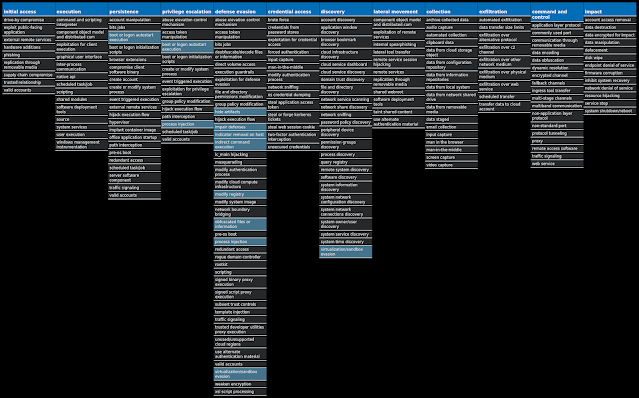
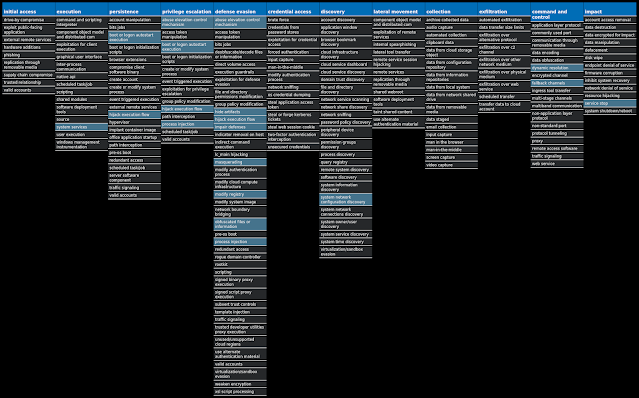
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.TrickBot-9958804-0
Dropper
TrickBot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts.
Win.Ransomware.Cerber-9958814-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns other file extensions are used.
Win.Virus.Xpiro-9958895-1
Virus
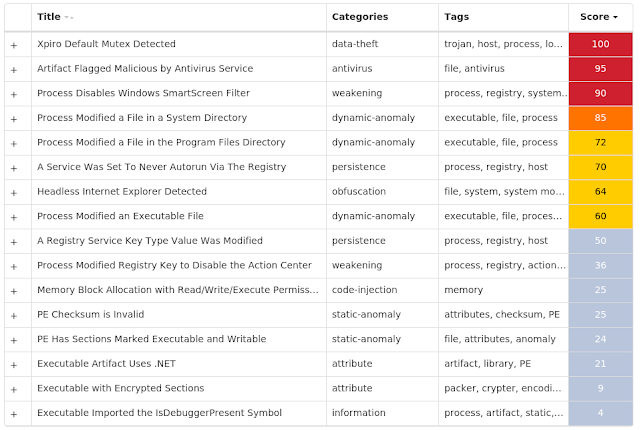
Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Dropper.Remcos-9960040-0
Dropper
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros sent as attachments on malicious emails.
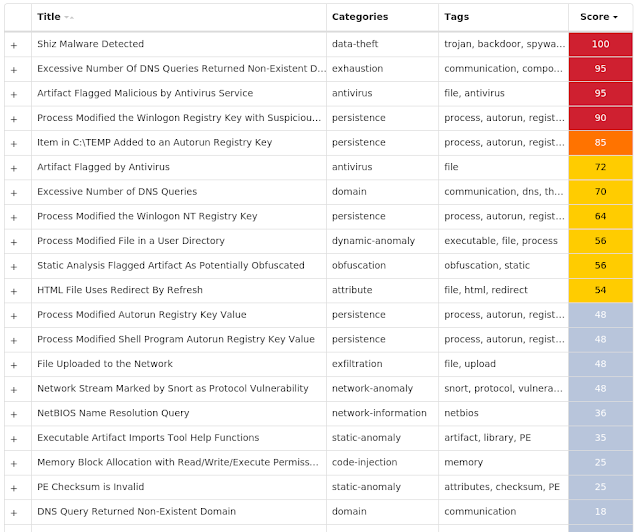
Win.Dropper.Shiz-9958984-0
Dropper
Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site.
Win.Dropper.HawkEye-9959777-0
Dropper
HawkEye is an information-stealing malware that targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media.
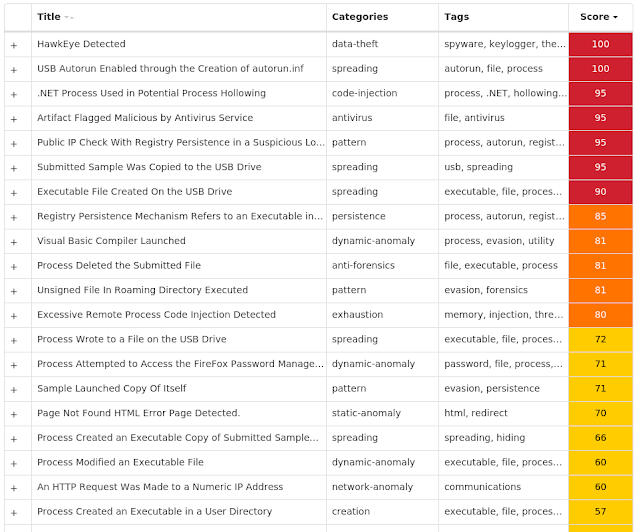
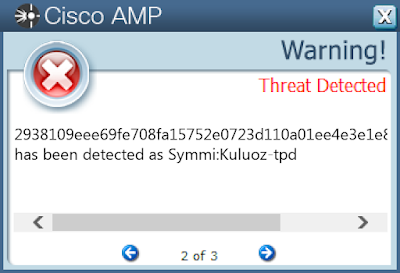
Win.Worm.Kuluoz-9959792-0
Worm
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
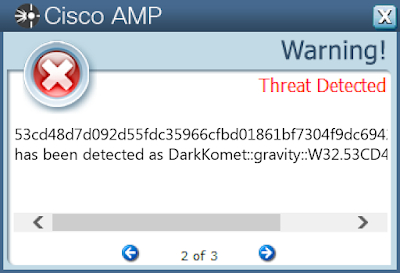
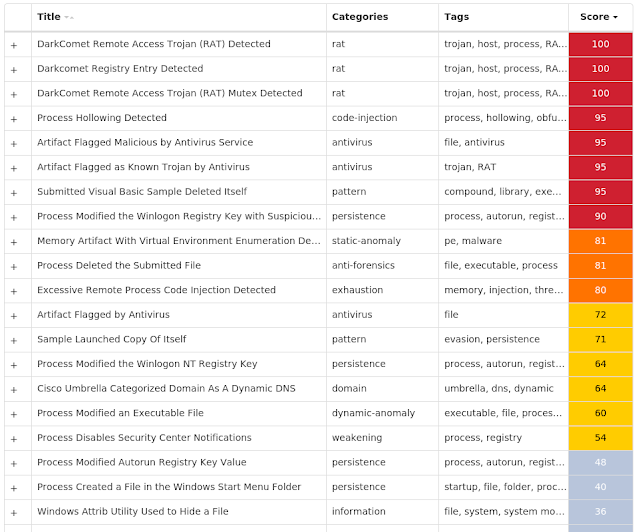
Win.Dropper.DarkComet-9959797-1
Dropper
DarkComet and related variants are a family of remote access trojans that provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
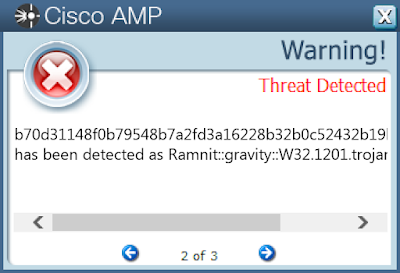
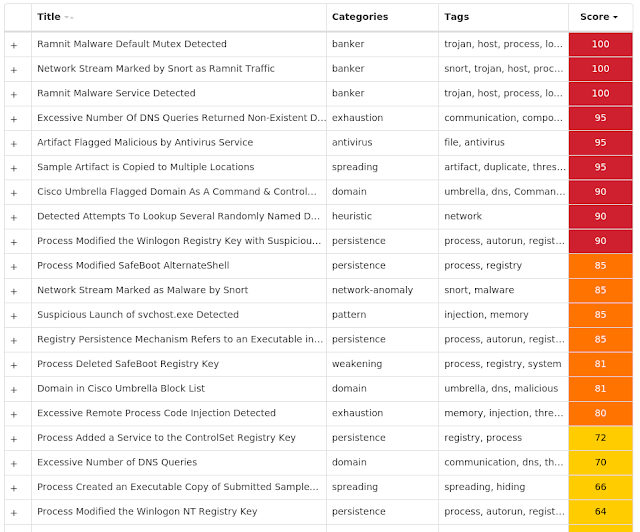
Win.Dropper.Ramnit-9960101-0
Dropper
Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It can also steal browser cookies and attempts to hide from popular antivirus software.
Threat Breakdown Win.Dropper.TrickBot-9958804-0 Indicators of Compromise IOCs collected from dynamic analysis of 46 samples Mutexes Occurrences 5502606391408671395
4
32899542343072484998
4
1124524871971925691
3
24112587554236391103
3
39744624822682236206
3
23819686304274202058
2
31572222973474305701
2
38648211142506533958
1
33656147683147949452
1
7918010151544240523
1
38748932962513239244
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wequinc[.]pl
4
patardd[.]pl
4
rydedun[.]pl
3
boristh[.]pl
3
lionopp[.]pl
3
matesic[.]pl
2
zanouns[.]pl
2
beryofn[.]pl
1
cabolth[.]pl
1
risiert[.]pl
1
githyet[.]pl
1
File Hashes 01a4f86457a252ffc23117ba653a2093902d0160140a3fda03e3cb9595f6d652
04a8a18b801bf158717c49444c3148f56fb1c23b6781b589106b848fad13557f
04d4ecf05a7bcc6ca0f318bacaa6087ea1e5badc14ca9eebec52aaff791718bc
08a004e94ce71ee0d239e38242283544f530996f4785924f85616040b278bef4
094f5c76889cd9f3f9357d72eda49a962eedc8457a77d586459dbd5968f85aef
0c25f673e25e8c9bb066ae56c41a83e28ef40a9da8327c9f7cd09f663b9a4614
0ef6c2cc035d61abd0f221d2bb8d6c0f5fc1e2e87cd5001f47861435fded326b
12eb4eb5dd38c776ec50166596c5e4ffda47108ce709990ae84a33a3a91776ed
1f14d617fd53588a36cd26c19e6f306fad28bac24140e9083986bb0cac607bc5
2184130eb8a891000fee1e343a5634531d72e05a7893fbafd6d53e52350bae19
23d19c57bacf51421505125da6917c815a1aa0d5c7346cf42c47f6667df0599d
2549d2a70d146340d14d981ecd9c33ce384bc743d4ed258f1eb9740c30792429
26851fc35426f83e70d1542cc4f00a3dd16222de418d2e0727a4ab9d5218c22b
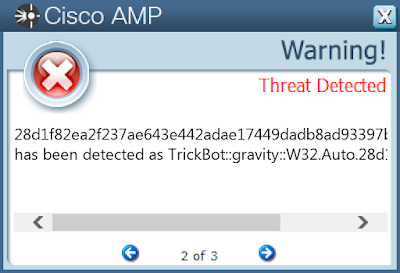
28d1f82ea2f237ae643e442adae17449dadb8ad93397bf2299b0b53abeee45cb
2d05858c463ea267870ff964d9f9779def1ca711586dcfea58745ebe6675ff1f
2d1e5cc0f414d6cc94ec251605c68c32c442740e129d7af97f8293844aecca6a
30636b11d051121251b2051971223e6e294dfaf917338239deb5b8edf5bce20b
39d4446bb6b1c8cbf319fe02f1316897f22a6b00633af1b7e6159dbd7b837556
3a0c89d07193ae260ced7a04873117af0213c43407248d2ff7edf95bd3b32421
3b5e722ae23b3656cfb17fcb9fd218b92c5e4f24c241c3f1c37bded99d92c035
3f32a6229d93292633dc3c9af4dcf7360463cd9fcc72bfc68bfc68afa666316d
4f47c12806778d27afa43905ebb5b2079a451da93237899167d6420333cfe9a8
50543f06717e0d022a4b58043861f0a38ab82e068f07414adc5be142a66c6cec
513125bc77c78f24fc6a29a125c0d5373d5b365f476ba496f90d8dc952fd4441
5584279c960a9a7aeb97ececdb90adc01da3dab0f1fe1cbf8c10e67f14d19c0d*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
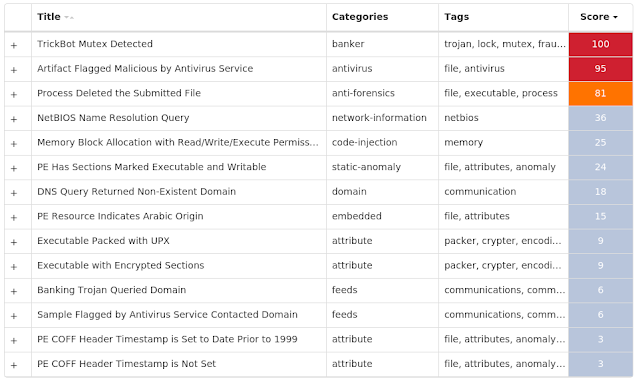
Secure Malware Analytics
MITRE ATT&CK Win.Ransomware.Cerber-9958814-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: Run
16
<HKCU>\SOFTWARE\MICROSOFT\COMMAND PROCESSOR
Value Name: AutoRun
16
<HKCU>\PRINTERS\DEFAULTS\{21A3D5EE-E123-244A-98A1-8E36C26EFF6D}
16
<HKCU>\PRINTERS\DEFAULTS
16
<HKCU>\PRINTERS\DEFAULTS\{21A3D5EE-E123-244A-98A1-8E36C26EFF6D}
Value Name: Component_01
16
<HKCU>\PRINTERS\DEFAULTS\{21A3D5EE-E123-244A-98A1-8E36C26EFF6D}
Value Name: Component_00
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: fc
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: fc
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntoskrnl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: ntoskrnl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: grpconv
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: grpconv
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hh
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: hh
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: WerFaultSecure
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: WerFaultSecure
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: javaws
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: javaws
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: at
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: at
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Dism
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: Dism
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: sc
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: sc
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: expand
1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
16
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]93[.]0[.]4
16
85[.]93[.]0[.]118
16
85[.]93[.]0[.]2/31
16
85[.]93[.]0[.]92/30
16
85[.]93[.]0[.]96/28
16
85[.]93[.]0[.]112/30
16
85[.]93[.]0[.]116/31
16
85[.]93[.]3[.]224/27
16
85[.]93[.]4[.]0/25
16
85[.]93[.]4[.]128/26
16
85[.]93[.]4[.]192/27
16
85[.]93[.]4[.]224/29
16
85[.]93[.]4[.]232/30
16
85[.]93[.]4[.]236/31
16
85[.]93[.]39[.]8/29
16
85[.]93[.]39[.]16/28
16
85[.]93[.]39[.]32/27
16
85[.]93[.]39[.]64/26
16
85[.]93[.]39[.]128/25
16
85[.]93[.]40[.]0/21
16
85[.]93[.]48[.]0/24
16
85[.]93[.]49[.]0/25
16
85[.]93[.]49[.]128/28
16
85[.]93[.]49[.]144/31
16
Files and or directories created Occurrences %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}
16
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\fc.lnk
2
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\fc.exe
2
%System32%\Tasks\fc
2
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\ntoskrnl.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\ntoskrnl.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\WerFaultSecure.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\WerFaultSecure.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\ndadmin.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\ndadmin.exe
1
%System32%\Tasks\ndadmin
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\grpconv.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\grpconv.exe
1
%System32%\Tasks\grpconv
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\sdchange.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\sdchange.exe
1
%System32%\Tasks\sdchange
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\at.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\at.exe
1
%System32%\Tasks\at
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\hh.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\hh.exe
1
%System32%\Tasks\hh
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\javaws.lnk
1
%APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\javaws.exe
1
*See JSON for more IOCs
File Hashes 13cb0416ecaedac2d05c117c68d7745d2f2ef8d2e41a5522ae28a9fdbe1cc464
18e9f9e0f0584b662165a2c78ca155ec06b59f48bfb09655929aaf6e4d3e04b6
273e649cfa2dba65d23094955a8901b2d8bcabd9d883eb53db97da09b2dc7257
37ce9b3d448b8d7ced3c71deebe8a826aa27095d155bbb08f5fe945edcaa665d
396c12c17e7de26873a87c37724b30ebeee8a246cb9f4dd8c81c4eb28e5a36ec
62e12d7f62c7c9826d8b20334d6bf5a9b9367cc92735c4c0ee0b9b04c68ebb30
636bb6784c21658f113ea4dcc00a82f0aa2c1e68927f3bb398d57ab5fcb6bc53
7017f1de73c8949efa7b04eb9973d73b712af738d2faf268cf32be7dea92b136
73fd26b7ee1d7939a55ee17a0ea15fc4a3aa85d417f9d19ec33230e71d21ac11
80574eb815087be8ead2c679474b8cf100a5a4db41cd3e012eff0c3e50ed900a
910aad5d8e14a47c2882531c587ceb7836af31e2c09296c43877a3ed2cc044e6
a340be1e9fe2140662c6bb04f1280eb91b1b1b1bd76c8e484ab4058ff25d5cf3
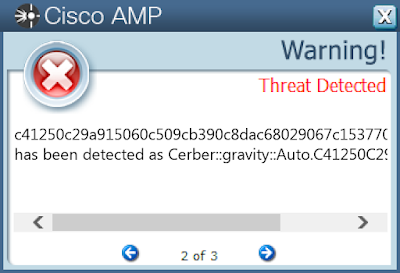
c41250c29a915060c509cb390c8dac68029067c1537707742ed211866ae2bff4
caba5cbc3931965b5f478934e02d20775413e15bcc559a684c632cfa9b151583
f6c4639bcabd34e8b2e9cf8323e07416a11bc4d579b910405880a8950128cfb1
fc73adec96749e88de8fb29777f1b4c27439c24690236857576076f545c8deb5Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
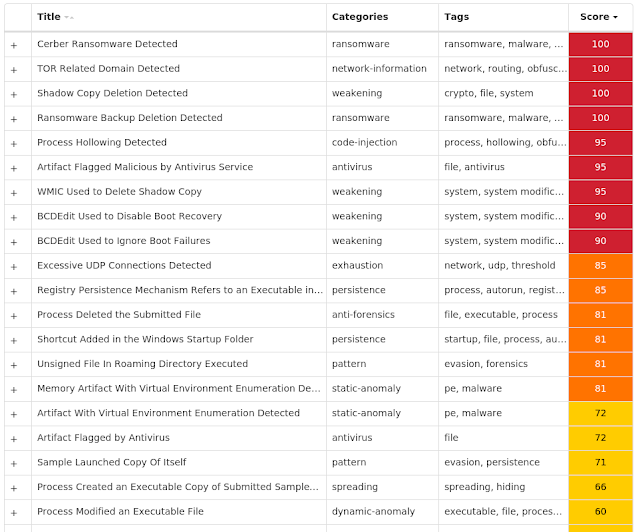
Secure Malware Analytics
MITRE ATT&CK Win.Virus.Xpiro-9958895-1 Indicators of Compromise IOCs collected from dynamic analysis of 37 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: HideSCAHealth
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT
Value Name: Type
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT
Value Name: Start
37
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM
Value Name: EnableSmartScreen
37
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500
37
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500
Value Name: EnableNotifications
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Start
37
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64
Value Name: Start
37
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE
Value Name: AccumulatedWaitIdleTime
37
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE
Value Name: RootstoreDirty
37
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE
Value Name: AccumulatedWaitIdleTime
37
Mutexes Occurrences kkq-vx_mtx61
37
kkq-vx_mtx62
37
kkq-vx_mtx63
37
kkq-vx_mtx64
37
kkq-vx_mtx65
37
kkq-vx_mtx66
37
kkq-vx_mtx67
37
kkq-vx_mtx68
37
kkq-vx_mtx69
37
kkq-vx_mtx70
37
kkq-vx_mtx71
37
kkq-vx_mtx72
37
kkq-vx_mtx73
37
kkq-vx_mtx74
37
kkq-vx_mtx75
37
kkq-vx_mtx76
37
kkq-vx_mtx77
37
kkq-vx_mtx78
37
kkq-vx_mtx79
37
kkq-vx_mtx80
37
kkq-vx_mtx81
37
kkq-vx_mtx82
37
kkq-vx_mtx83
37
kkq-vx_mtx84
37
kkq-vx_mtx85
37
*See JSON for more IOCs
Files and or directories created Occurrences %CommonProgramFiles%\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE
37
%CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE
37
%ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE
37
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe
37
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe
37
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe
37
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
37
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe
37
%System32%\FXSSVC.exe
37
%System32%\UI0Detect.exe
37
%System32%\alg.exe
37
%System32%\dllhost.exe
37
%System32%\ieetwcollector.exe
37
%System32%\msdtc.exe
37
%System32%\msiexec.exe
37
%System32%\snmptrap.exe
37
%System32%\sppsvc.exe
37
%System32%\vds.exe
37
%SystemRoot%\ehome\ehrecvr.exe
37
%SystemRoot%\ehome\ehsched.exe
37
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log
37
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log
37
%SystemRoot%\SysWOW64\dllhost.exe
37
%SystemRoot%\SysWOW64\msiexec.exe
37
%SystemRoot%\SysWOW64\svchost.exe
37
*See JSON for more IOCs
File Hashes 013aa31a250e2858846c6f078e12a5132abbc0fad271365d3b67527fa2c2f402
05c2e245c5f3a325472cf34f42093931e48d181c0f17caf9add2b35e7a3e828c
0aee33737e3213c74bb671a1ab7b9485e00ade57ade144e2be354f67506a7290
0af8855eff016554c3ddf0ce82bb61859ac3986ee4136ee06e7fe5d5a6d89788
0ca2f5ca6ce21bacf1b26601c214a36766a0c911320bec0c184b5a18923ece23
128d57cca2eae54f5754a5f1730a05df82d942a11764d0595e6c920498e9565f
1397eff74a13595ea3fcb206a76977d1447997680fdf81163c2b985a009b080c
13dd82a41add2789b1ea617cded11cf9bdbc143082372dcc2b26b2ae2616dbba
14e5e9016d589d815058b09845af3b2fc2781b9815a493499664f29e9832e9fa
16fcdd9f0950eda4799c80afd354767feefb725c58d82022c2d1385e25d48e96
1b0665bd149dd3b9ae9a3b19c7be06b5ddcd53da461f91cda65365b94b7a288b
1cf200ce049a09ea6f18ff56f65c651d519d6096d6eaf94331351c1217d2e002
1f98e6f12d028379751c4e5f6efe96e0fe8a286c7448513dda93c980e3d8acf6
26bd53dc56ec5c20627d67c8bdce2f67c3325bd6421a87319e3694abcf73867e
28664a444ff8d844816b801fcf92199100cad7375ebaedea96020b2f7e2c664b
290be865ff04b744f3f34e17cded589f11519cb10d5d186535cd5a21de8dd650
29e70dc26eb00d9ff16ed8864b2583dde97e70d6f7dc074c50f3665ad7f8b2dc
2c52d85ad0e41acf5112bccbbdde281950692c0e100e499a15b170d66d0154d0
30ed57cfe6626a3e05de88be3207d4524311c62a6a2b5647f9359a620ed22f11
3134096945a4cea5132ea9d0ad9b1a6925da40d2d4e86c8f8c8f4d3795b962ca
35f44b47ad1e072f2030291462cedd654234eb0575883ae8f8d5978c051d78e1
35fcd428c89e9586460cb2701ca4cb378824a32d497366a96fa234caf54d8048
3c8477fdcd2719855d6b38cf29849d36dca6bf90805f996286bf77fff7ba1fa3
3eb5cdb190ee1efbea012512c3ed6afd6215473bf208a1853f37701a3f7ba13a
3f53b25ccced470ef2b1eb2edb4b839099a0ca597f4dbcc3aa590b260d727ab0*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Remcos-9960040-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E
Value Name: LanguageList
7
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}
Value Name: FaviconPath
2
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}
Value Name: Deleted
2
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES
Value Name: DefaultScope
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}
2
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\APPROVED EXTENSIONS
Value Name: {761497BB-D6F0-462C-B6EB-D4DAF1D92D43}
2
<HKCU>\SOFTWARE\REMCOS-SFLVDU
Value Name: licence
1
<HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E
Value Name: @C:\Windows\system32\DeviceCenter.dll,-2000
1
<HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E
Value Name: @explorer.exe,-7001
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: mea
1
<HKCU>\SOFTWARE\REMCOS-SFLVDU
1
<HKCU>\SOFTWARE\REMCOS-SFLVDU
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-1MSE40
1
<HKCU>\SOFTWARE\REMCOS-1MSE40
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-1MSE40
Value Name: licence
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: Un9
1
<HKCU>\SOFTWARE\REMCOS-A21G8J
1
<HKCU>\SOFTWARE\REMCOS-A21G8J
Value Name: exepath
1
<HKCU>\SOFTWARE\REMCOS-A21G8J
Value Name: licence
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: re
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: dr
1
Mutexes Occurrences Remcos_Mutex_Inj
3
Local\55C37268-60E9-964A-3299-E2046F3CC613
2
Remcos-SFLVDU
1
Remcos-1MSE40
1
Remcos-A21G8J
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]225[.]214[.]71
4
13[.]225[.]214[.]108
4
37[.]19[.]193[.]217
3
95[.]211[.]75[.]16
2
162[.]210[.]195[.]111
1
13[.]225[.]214[.]91
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences piloresi[.]top
7
dioneras[.]top
7
downloadmirror[.]intel[.]com
5
uniresio[.]top
4
emperimen[.]com
3
www[.]bing[.]com
2
busyboydesign[.]xyz
2
toptoptop2[.]site
1
toptoptop3[.]site
1
toptoptop3[.]online
1
toptoptop2[.]online
1
lutheatre[.]com
1
fallium[.]com
1
sheaffic[.]com
1
Files and or directories created Occurrences %SystemRoot%\win.ini
21
%LOCALAPPDATA%\Administrator
8
%HOMEPATH%\kmm
1
%HOMEPATH%\kmm\Cam.exe
1
%HOMEPATH%\kmm\Cam.vbs
1
%HOMEPATH%\Dul\Slu6.exe
1
%HOMEPATH%\Dul\Slu6.vbs
1
%HOMEPATH%\Dul
1
%HOMEPATH%\Uds
1
%HOMEPATH%\Uds\sov.exe
1
%HOMEPATH%\Uds\sov.vbs
1
%HOMEPATH%\Sv9
1
%HOMEPATH%\Sv9\BUT.exe
1
%HOMEPATH%\Sv9\BUT.vbs
1
%HOMEPATH%\ref
1
%HOMEPATH%\ref\Bar.exe
1
%HOMEPATH%\ref\Bar.vbs
1
%HOMEPATH%\ma\No.exe
1
%HOMEPATH%\ma\No.vbs
1
%HOMEPATH%\ma
1
%HOMEPATH%\Oxy\Bru4.exe
1
%HOMEPATH%\Oxy\Bru4.vbs
1
%HOMEPATH%\tr\TEL.exe
1
%HOMEPATH%\tr\TEL.vbs
1
%HOMEPATH%\Oxy
1
*See JSON for more IOCs
File Hashes 1990701e4db9f573be94dbfd0e9edcb826c4a0ba858b42249812acb12cea572f
201ecff5a0b06b1401158972176bf3af310e1a25a9f603ea902b340f15262130
667fcc41313580c1c5dd3f74e84f13a4431a8b1daf4e1c60d5f3ab0c657e95ef
6754bcad108371e4192bc126187cf7ac07c39ea3f5ed7d975402a4c20d7fbcd4
68183c5baad715853bf2a38a2384288803a431ef4881be8c33b473f7e97d0186
6f70b508bcf39a1de4371f080c51bbf569ff5be7bf0f91793519c3c511710386
72d305998919d0c14d44659c0427e1130b9cf6539f386d328879c7d416ac085a
7cbbe9909fc023294a209ecf1b3882a02cb198d6841a129471201ce105c10d7f
905d2ba08aa3c839dfb815a373c5e2d0ae71badcbb1a70be1ef2683381dcb257
96eba5d5846bbcb803ffbac64ea5adf52fcb736ebda11abd466d509314dcc216
c2bfc250e5a0f8047d8eeb2bab36669e2d20becf57ddfa1e0ff5c33ff63864d5
cad62477913555b37902a162c9b437af27182fb219aa14647f257a0c48ddd556
d2a181619dc5bce7506d65bd893b411772de00c9ffdcbbcb9e3a78ab029a4997
d6e619e7f6f7578cef21ad4bea1ed94f397c0063aee69df329bc0aab3ea0b177
d9f6c0ffc135785c9c0355bad4cc4b8884f6f655c6e336c14b1b7a27568ddda9
dcd1f707b263fe1c37b94944b8399d92675d215d76aca304f0c7455250627d68
e9877a7c8d2daca6b15131b26a583695e4d5e2c05023b764f24a551666055b0a
f22c91af53fd11dae4ebeeca1886c5a3355f68970cb554be7eb10affbb547341
f57f13ef3d153621588b9aa9a273e08a77069dd2b9b7d5ad08c579f24feedc41
f7ac5679a471bbc48cb5af2fd54ea2e4621f7e825c06fba59a1690fa6745e56f
fd4de71e56062003053b8f93f6bb84188666361a07c415e56a4b015802237289Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Shiz-9958984-0 Indicators of Compromise IOCs collected from dynamic analysis of 88 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT
Value Name: 67497551a
33
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: 98b68e3c
33
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: userinit
33
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: System
33
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: load
33
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: run
33
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: userinit
33
Mutexes Occurrences Global\674972E3a
33
Global\MicrosoftSysenterGate7
33
internal_wutex_0x000000e0
33
internal_wutex_0x0000038c
33
internal_wutex_0x00000448
33
internal_wutex_0x<random, matching [0-9a-f]{8}>
29
internal_wutex_0x000007d0
12
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]21[.]200
16
45[.]33[.]23[.]183
9
96[.]126[.]123[.]244
8
198[.]58[.]118[.]167
7
45[.]56[.]79[.]23
6
45[.]33[.]30[.]197
6
45[.]79[.]19[.]196
5
173[.]255[.]194[.]134
5
72[.]14[.]178[.]174
5
72[.]14[.]185[.]43
4
45[.]33[.]2[.]79
3
45[.]33[.]18[.]44
3
45[.]33[.]20[.]235
2
85[.]94[.]194[.]169
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fodakyhijyv[.]eu
33
qekusagigyz[.]eu
33
maxyjofytyt[.]eu
33
xudylenyrob[.]eu
33
pufepepazyd[.]eu
33
vopibycywow[.]eu
33
fotoxysupyd[.]eu
33
gaqehysohec[.]eu
33
lyxaxududes[.]eu
33
rycovuvutiq[.]eu
33
kevimudyqec[.]eu
33
jewidonevin[.]eu
33
tulekuvigij[.]eu
33
vocupotusyz[.]eu
33
galavozaxog[.]eu
33
divufozutog[.]eu
33
kefidaxupif[.]eu
33
jejykaxymob[.]eu
33
xutevexecif[.]eu
33
puryxepenek[.]eu
33
lysowaxojib[.]eu
33
dimigesupew[.]eu
33
fobatesohek[.]eu
33
ryhadyvigis[.]eu
33
qekikyvutic[.]eu
33
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp
33
File Hashes 0426a2801b985679944d7956d57df0c195e4871cb5fa9ae5d3cb864600883613
06748264e401a4fcf30a802df0f390a75a14a3ff6148b8f064ee3e2585c742d9
09bf6eb80568c5d370d52e77ca1eddea41f0eb7e458549c994620b3e6af3967c
0affbf8c7691eaaab70491418b6db92cced36ff4a0a482673a4ebdd5492ad6c8
0fbe21b7ff8392a707d0d871494c2298e88e723ebcd7a4495c6a037232d4899b
11b3839df1c31d6c2f15591a0fa013c8b41862dd522d106c85876b49e7d561c0
11b6cfd9b8f56c8107511151282335f7b5f5d555665bec7506908515dcb6acab
11c19ec5a341f6a6bfa86170ea383439466f008ff42ec6dc04bd0445a658ba63
1641e6a92c47304c11521b9c875029a387e49b511438b3ac4c122ee7b14519de
1cac14ca2ad5715132446d1bb0503a6f783577d15f8fb97611dac9b7177903cc
1f4e2901cf95c9ca682d9e5c24235c11da57a47153969203e58b5528bd37b411
1f83440aab9dc62a6c4726b35ee58355b1cf76d23d194250397069423b17d281
237bf6bd91b6301dd01456859507771ed5fc2eda62f67e207bea6928f69573b9
253dc24fa6384c2c2757acc74ecfb88a231ab434c718e5b044a47e3fec4515f7
25525b728590f243275c528727c4887c3521fc16c25f60e3b364fb21e8b64dab
2553d02ff7f59fc5e0830783a508b4a5e8daff585bb4e5411c49bb34217f1b3d
259d0e1eb7a6ab82cfef210054b7cedd069d331455d6c0effff450c514fef6b1
2796098904f867adffd735f528461e5fb8be9f33ebd22bc37fb58684c3476112
27de5dc0ae67097bc22a0bcb3381dcebc372c469c4b8effe2b83d87f85f01cc1
2a6f60367dc3d70d2db9926e28dba4d79f20e319ceaf839c094cf85c9850c99a
2c729b76866357b2fae9d51f4d5f69c1554b18b5be35f896300631b7409e49e7
319155806bbb3e74cc753ed768a13455965e1fa7a175155f5862c2e030c2e35a
34b2879998dfd238977cf19e5f4e3d4cbccfa61a9b0688e43a569e19a75a2844
3578be24b2fe30600747846c30c1e286622e1906fce1a801e10b87117bf37ef4
385ddefdb0c298b4cd194b165f82e9ddec8c8e6616160e432125e576dae5603c*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.HawkEye-9959777-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Update
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Shell
5
<HKCU>\SOFTWARE\ROMO.PARTNERIAI2@GMAIL.COM
3
<HKCU>\SOFTWARE\ROMO.PARTNERIAI2@GMAIL.COM
Value Name: NewIdentification
3
<HKCU>\SOFTWARE\ROMO.PARTNERIAI2@GMAIL.COM
Value Name: NewGroup
3
<HKCU>\SOFTWARE\ROMO.PARTNERIAI2@GMAIL.COM
Value Name: FirstExecution
3
Mutexes Occurrences <random, matching '[A-Z0-9]{14}'>
4
X43238C48CI4NY_SAIR
1
M21V21V8G7Q66R_SAIR
1
05V015TT37XDUJ_SAIR
1
Global\07657600-129e-11ed-9660-0015174b6151
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]155[.]36
6
104[.]16[.]154[.]36
5
77[.]88[.]21[.]158
2
142[.]251[.]16[.]109
2
208[.]91[.]199[.]224
1
208[.]91[.]198[.]143
1
208[.]91[.]199[.]223
1
192[.]99[.]212[.]64
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com
11
kalashas[.]no-ip[.]biz
3
smtp[.]gmail[.]com
2
smtp[.]yandex[.]ru
2
mail[.]siliconsss[.]com
2
smtp[.]impexservicesindia[.]com
2
smtp[.]vsnl[.]net
1
smtp[.]thanawalagroup[.]net
1
Files and or directories created Occurrences %APPDATA%\pid.txt
11
%APPDATA%\pidloc.txt
11
%TEMP%\holdermail.txt
10
%APPDATA%\WindowsUpdate.exe
10
\Sys.exe
3
\autorun.inf
3
E:\autorun.inf
3
%TEMP%\Administrator7
3
%TEMP%\Administrator8
3
%TEMP%\Administrator2.txt
3
\directory
3
\directory\CyberGate
3
\directory\CyberGate\install
3
\directory\CyberGate\install\server.exe
3
%APPDATA%\Administratorlog.dat
3
%TEMP%\SysInfo.txt
3
%APPDATA%\Windows Update.exe
3
E:\Sys.exe
3
%System32%\drivers\etc\hosts
1
%TEMP%\oUK6NMZIZls5Ku6i.exe
1
%APPDATA%\6tOsSNNvNp7JOgxS
1
%APPDATA%\g3h44Njnele2nJzi
1
%APPDATA%\g3h44Njnele2nJzi\ZOqlaWVQEXMz.exe
1
%APPDATA%\6tOsSNNvNp7JOgxS\ChSV1JzLaHOS.exe
1
%APPDATA%\hAtRUbl2c5ywfar3
1
*See JSON for more IOCs
File Hashes 04e516d05c22e5489ba47b5e1bd03f6cb8bcf2b084e2b3dae23acbe25d4b4591
21e52c431fce5ea651800127be440f447fafd20c3d74f34b0d712e140b0c138d
21e949c72bc90a7b4647b305dd306e343f732ad2b898dba5e9b920edc33fc9a0
220c6f3ffe28c8c7cd3f3b669b47bccdde30b200ab1de9bd0cca55c475ad62cb
2f656303daecf2322749ed2a4b69b7124433dfea94d658c9e1e18d415db16456
32a841f8eaf7fa85d3c78469a9890988c1c9b90c97cfba674ac8f9f991bd3a94
4000b5bce992bdbdd73174fbe1e8d9b0fd65ad6c88f282889a8604dfa9fe0f59
5291c5d0bd7eaee2402fb660be1b8501c3a712471e9d66062b6728794909263a
5393c5a558225a02a03ee8ea46968d53a72b57194261e17dc7e35f0bd9b630ea
628eb845ab8309303d0ebb7448063dbafd36954a66596977a272d5806cacaeca
656d25151b846944e11c7ba03ce4fae066f7a8c29cdce84d0b241d4305a4245c
6d155125192252b756c6af33bca25810ab9a19be347e5793b534802662eb00a4
9a8797b6c2753e70ce0888185473510f40d3c0ff45b81b639dc8c077cb3679ec
ad52ce9456cb87f713ad43de89835e0c882fd3a77389bb41ab50396efd59088a
c4bf7dbe799d71e8e16c1aa5ca3f3af04f174b91e1a357a02e38b0155a46a600Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Worm.Kuluoz-9959792-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: uecguckk
1
<HKCU>\SOFTWARE\AEAKVJGE
Value Name: ujaduqcw
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: cuhmadmx
1
<HKCU>\SOFTWARE\UDVFKDFC
Value Name: vdqcxwxs
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: lhelwsfg
1
<HKCU>\SOFTWARE\SFLQPFKG
Value Name: pvgxfqel
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wrbmmivh
1
<HKCU>\SOFTWARE\SMXPKGUG
Value Name: cdjmiong
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: agokwqgv
1
<HKCU>\SOFTWARE\NGWWUMBN
Value Name: fpesjwgk
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: bomrkrmk
1
<HKCU>\SOFTWARE\LSCPUEQM
Value Name: lsekxadg
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: bxvvsgvr
1
<HKCU>\SOFTWARE\HIDBXWKK
Value Name: wudcreed
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: snwmmmvf
1
<HKCU>\SOFTWARE\TCUDAEVA
Value Name: dfvkflcs
1
<HKCU>\SOFTWARE\MNQGHNOP
Value Name: dlirvvqw
1
<HKCU>\SOFTWARE\MNFTGNBG
Value Name: csfqppjx
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: imcfhgpa
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: oqpeifcm
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: lhxptbjv
1
<HKCU>\SOFTWARE\HQMHIWJP
Value Name: durqeakc
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hsrhcrvj
1
<HKCU>\SOFTWARE\CGOEUIAE
Value Name: htpvdufk
1
Mutexes Occurrences 2GVWNQJz1
26
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 173[.]203[.]97[.]13
15
76[.]74[.]184[.]127
13
37[.]59[.]82[.]218
13
94[.]32[.]67[.]214
13
212[.]45[.]17[.]15
13
142[.]4[.]60[.]242
13
50[.]57[.]139[.]41
12
82[.]150[.]199[.]140
12
92[.]240[.]232[.]232
10
113[.]53[.]247[.]147
10
203[.]157[.]142[.]2
9
176[.]31[.]181[.]76
9
188[.]165[.]192[.]116
7
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe
26
File Hashes 01d6c50b70eb28d693e74b7ad15158707b8f57a9711e35c07d3d1c4ee7f630ee
08c25287e368a2158b029684e74626ba867a606837cce07ea2837b6ed78857a4
09bb26d956e0eb8aba714e836c041d844ac01eb4ccb3e498382c07ae3e267ff4
0bf1e31c2a0fe232876deef8bad8cbe1e08a3ad377db920ffc27c4852ef1dc89
0c6ec5510575da4416321eb58b20d3e447746e0cea1ffd06241f8a1e6bbb2837
0dd0361ead8f0e962be7a115dd8a4fa9d1a12b88c11633f82cfeae655a59f809
0fb3d456de4717b29c3a332e29a10cc9c52c94c92f6438f32791f5a5785b603b
1052ac160c67084f7dae6af5d9ee545fb0df20b99b8e989177ffb795a32aa35c
192d087160aad1afdb5ed06eb4128d997e578af554a626887746d91e66bc688a
1f4a448e60174255ef3d7492e60464ef4cfd84f65acb8c9824493b71d6864b8f
1f7810a638c2f1825276f2784cf557d7610ca0eabb463d06e6b25597fd077043
230a54a47fed1921adb452b5e88f1467e021dd85aac8f0d60a5a41912b991d28
26cad8fc0603c849db06f59e46b452bb4c3fe5cadfd46e344ce9a7f10365ddb8
276bb12ea62aa7f7ffce0531b84bbe1f7f2e6a19f4150ca6a7b1c69f4662b595
286bc1cee4c188350c8bb50812e30f7bec0b794efca5a2eb0b12368b479211b3
2938109eee69fe708fa15752e0723d110a01ee4e3e1e804cc97bbde01267fdb8
2a850531aeb725e5f138b9b1158640fe41c05a25560e2550fa2b070d96490a8e
31266599481409d70b317821d5af1aea693e7c1c7cedd04fd5dec0008bd816a7
384b51772d288e63038e146446e6e84b1f737cd3d8d34c3871d875fda77ff29a
38e1edffa779f9e2dd16104c35fc7a6c4a21dff7f3ad9bc8233b5817e8666441
3949d166ce5f75648fcb66ea3f9aaf251aa9847d576aef7d10b2830a295e2096
3ffee22fa7f00e260b92385c8cda56eee17c133b7c47cb33cf701d0c9e2ae89e
419c33660b59de42d150f8c1163873db94fa59e8d684bb44d0ec866eaebd00a7
441c34ba7b9ee2d7b0506013a2fb9fd5c5b517d38a66e1228edf4d7e1e20b9e8
446d8276a7008c24317b101c5d7050da5f1a51301a47842cd35f5d8a362eee83*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.DarkComet-9959797-1 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
11
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: UserInit
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicroUpdate
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
11
<HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E
Value Name: LanguageList
11
Mutexes Occurrences DCPERSFWBP
11
DC_MUTEX-01SYFCM
11
Domain Names contacted by malware. Does not indicate maliciousness Occurrences zapto666[.]zapto[.]org
11
sildelanoe2[.]zapto[.]org
11
Files and or directories created Occurrences %ProgramData%\Microsoft\Windows\Start Menu\Programs\MSDCSC
11
%ProgramData%\Microsoft\Windows\Start Menu\Programs\MSDCSC\msdcsc.exe
11
File Hashes 236c360d988e5b28b1a4eee229d0f3b5baa203043fc5ae8f016519f753e6b6bf
27990599b2e3ae192d5a897ed30cb98a20eae1d3ed8506dac8d82fef9ed9442e
53cd48d7d092d55fdc35966cfbd01861bf7304f9dc694237d322ff189adb32a4
55754ae53d9555a67d25be9cd73b5d85141d4ef43cd55ae2cf237be1cfa0d965
5dcd64134e33496cdd5ad13012b35834164d59d470a17359710a335469fdf35a
6e0d5bd7c55c9ec287377f8cadd342768c887a8901d015253996112442ff5d6f
a53ebd4f480bdf3cf2199692af1d27c2864fc5c038fefed214688416cc2a1066
acaf2d6a74e24b2ab85338fa62efc85d76f6ec9c1cd11657230d975fd0dcde42
c4c677ab5115a0a568d1817528005ad24d0dc06ddd9d738d5f1fb75a3074b3f0
d2e83abd3d779b825e4088f53b43aa8521131a9ebd0dad8006e70fcc0e249e8d
eea1adee202040b2c06dfb226eacd4c662b57714f44ffcc0561ff8cb2ec2a6d6Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Dropper.Ramnit-9960101-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
15
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SAFEBOOT
Value Name: AlternateShell
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: WlkSgauv
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: Type
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: ErrorControl
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: ImagePath
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: DisplayName
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: WOW64
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: DeleteFlag
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICORSOFT WINDOWS SERVICE
Value Name: Start
15
Mutexes Occurrences {79345B6A-421F-2958-EA08-07396ADB9E27}
15
{7934684F-421F-2958-EA08-07396ADB9E27}
15
{7934723B-421F-2958-EA08-07396ADB9E27}
15
{7934684E-421F-2958-EA08-07396ADB9E27}
15
{<random GUID>}
15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 82[.]112[.]184[.]197
15
72[.]26[.]218[.]70
15
195[.]201[.]179[.]207
15
208[.]100[.]26[.]245
15
35[.]205[.]61[.]67
15
142[.]250[.]80[.]14
15
75[.]2[.]18[.]233
15
172[.]105[.]157[.]192
15
46[.]165[.]220[.]150
15
Domain Names contacted by malware. Does not indicate maliciousness Occurrences kbadlfpgtec[.]com
15
ymcwineqkj[.]com
15
tupexbvpmsc[.]com
15
mwsjitqbf[.]com
15
ccsnpnqxii[.]com
15
dpdadshi[.]com
15
eljmrnwualb[.]com
15
hjxrksvo[.]com
15
lfnjosunfd[.]com
15
paoxlrmbg[.]com
15
qekgxfrk[.]com
15
uhjwxipj[.]com
15
mkmngqxwk[.]com
15
ybmhumhymqj[.]com
15
qopdypfxhda[.]com
15
pfkilgedjhq[.]com
15
sgimiytkanu[.]com
15
leqnxekmi[.]com
15
ieugluxmlx[.]com
15
elieidkolpc[.]com
15
oluddrbaeb[.]com
15
skroackqs[.]com
15
pbfttfgw[.]com
15
ujypninrop[.]com
15
qpvvabbaqcn[.]com
15
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\wblmbpwi.log
15
%LOCALAPPDATA%\xrpatmbf.log
15
%LOCALAPPDATA%\ntqipnfr
15
%LOCALAPPDATA%\ntqipnfr\wlksgauv.exe
15
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\wlksgauv.exe
15
%TEMP%\dljcankv.sys
15
%TEMP%\oqinictcdtumygeo.exe
15
%LOCALAPPDATA%\ntqipnfr\px1F71.tmp
1
%LOCALAPPDATA%\ntqipnfr\px26AF.tmp
1
%LOCALAPPDATA%\ntqipnfr\px203A.tmp
1
%LOCALAPPDATA%\ntqipnfr\px1CC1.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2B70.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2BFD.tmp
1
%LOCALAPPDATA%\ntqipnfr\px1EB4.tmp
1
%LOCALAPPDATA%\ntqipnfr\px1B98.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2365.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2307.tmp
1
%LOCALAPPDATA%\ntqipnfr\px28A3.tmp
1
%LOCALAPPDATA%\ntqipnfr\px25C5.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2DD1.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2BED.tmp
1
%LOCALAPPDATA%\ntqipnfr\px2529.tmp
1
File Hashes 10df6ef7114ab16c25690d0183960e51d80488690e4f52680be2cf38d4aeb85b
1b39ecf9dc61b7e01c410b02eb8cb5c01ccdb1346474c62d7b916a9fb136681e
25354347217865d4e0a18080a942021de378cdcdff3633edc32583d892639569
265febc90d4163d2d1f29c0f07c8b003002ec7ee9ca4a3f8607ca5364cf06dc3
370c3bdde1b51bf0b9d079e644871b79848ac588c37ea7f89c94a2e2c3103642
3b955ab71c4147497bb1aa0fd65ee9b94bb1cbc897a0be46427f0f66a829de5d
55835f514e7ab6da28a6c69a3ffbe2d356b8ca987a274bc7a190689a57cbfbf2
615c3bfaa531cda8c1ac55bf9d5d93598617cd208702a7ce4c26cd94b2f2d4fd
61657d27b739df7dd856194cc29354ebf9d4a9abe3cb37d8782b5e6bddcba23c
7227840a73bce222d285d89cb1f528a5f5caf230af943a78f85f5e07136f1c4f
91cec64e347f7355c3dabb30b6e70c73d8a16890aa698ef526476930b998dd78
b70d31148f0b79548b7a2fd3a16228b32b0c52432b19b9d651fc9d6f9458c845
b7841d3db93f9a48887fdb82d3492b43f33f36ee8959e4f26a74c77962793e65
e80bad25222ffce33d1fa8c5962b235fecdce744b6dcf9c35db869844802573c
ee4d65ec638095b28ec9c1290bf3edac8c767fb2a094c00925fabcde83dfb205Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK