- Insider threats are becoming an increasingly common part of the attack chain, with malicious insiders and unwitting assets playing key roles in incidents over the past year.
- Social engineering should be part of any organization’s policies and procedures and a key area for user education in 2023 and beyond.
- Mitigating these types of risks include education, user/access control, and ensuring proper processes and procedures are in place when and if employees leave the organization.
Traditionally, attackers try to leverage vulnerabilities to deliver malicious payloads via exploitation. But more recently, that activity has shifted away from exploitation and consistently moved closer and closer to the user. Initially, threat actors loved to trick users into enabling malicious macros in Microsoft Office documents, but as Microsoft moves to blunt the effectiveness of macros, adversaries are always going to move to the next avenue to generate malicious revenue. This is where insider threats come into play. There are two broad categories of insider threats: the malicious insider and the unwitting asset. Both present unique challenges in detection and prevention for defenders and organizations’ IT admins.
Malicious Insiders
There are a variety of reasons a user may choose to become a malicious insider, and unfortunately, many of them are occurring today. Let’s start with the most obvious: financial distress. When a user has a lot of debt, selling the ability to infect their employer can be a tempting avenue. We’ve seen examples of users trying to sell access into their employers’ networks for more than a decade, having spotted them on dark web forums. The current climate is, unfortunately, ripe for this type of abuse. The economy is on the brink of a recession, inflation continues to spike, and the cryptocurrency markets have lost as much as 70% of their peak value from late 2021. Combined, these factors can create an environment where employees are susceptible to coercion, putting the enterprise at risk.
Financial distress is a serious concern for employee compromise as evidenced by the fact that nearly half of the security clearance denials in the U.S. have to do with financial considerations. It is also a common factor in clearances being revoked, clearly demonstrating the risk it can present. This financial distress can also be leveraged by adversaries to force users to take actions they would not have otherwise by threatening to expose the issues publicly.
Financial distress isn’t the only factor that could drive an employee to turn against their employer. In today’s highly polarized political climate, the risk that an employee may take malicious action against their employer due to a perceived political stance from the employer is ever present. These could be spurred on by the action or inaction organizations take related to a piece of legislation or other societal issues. These risks, although less common than financial distress, present unique challenges to employers as they try to navigate the current political climate and closer to the 2024 presidential election.
The final risk for enterprises comes from employees that have recently left the organization — especially if the separation was not mutual. Employees that have been forced to resign or fired from their jobs may take matters into their own hands. It’s this group that is typically focused on destruction that can really wreak havoc inside an organization.
At the least, malicious insiders may be willing to click links, open attachments, plug in a USB drive, or hand over credentials. In a worst-case scenario, if the malicious insider has an elevated level of access, the effects could be devastating. This is the primary insider threat organizations face, but they also need to be prepared for the user that is being used as an unwitting asset, typically via social engineering.
Unwitting Assets
This other category of insider threat is the more challenging of the two to deal with, as they likely aren’t aware they are acting maliciously. Social engineering attacks are on the rise, we see social engineering becoming a more prominent part of the attack lifecycle as we continue to improve things like exploit detection and prevention. Social engineering attacks are those that focus around leveraging the user to aid in the infection, typically through some form of manipulation. It played a role in the recently disclosed incident affecting Cisco, as well. Social engineering has some obvious applications, as we’ve seen repeatedly in the Business Email Compromise (BEC) space. It isn’t uncommon, especially for the more sophisticated groups, to open with a request for a phone number to discuss an issue further.
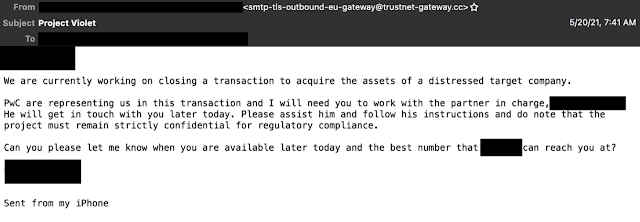
The attackers have realized that if they can get a potential target on the phone, it’s far easier for them to extract money, as people tend to want to help and can be better manipulated over the phone. This is far from the only way users are becoming unwitting assets.
As we continue to deploy multi-factor authentication (MFA), attackers are getting better at evading it, commonly through social engineering. Through our investigations, we have found numerous examples where attackers pose as IT Support or Security Operations inside an organization and call the victim, using social engineering to get them to accept the MFA request as they are sending it to the device. This was similar to the approach we saw taken in the recently disclosed attack against Cisco, where voice phishing played a role in the sophisticated attack, illustrating how once attackers have people on the phone, they can more easily manipulate them.
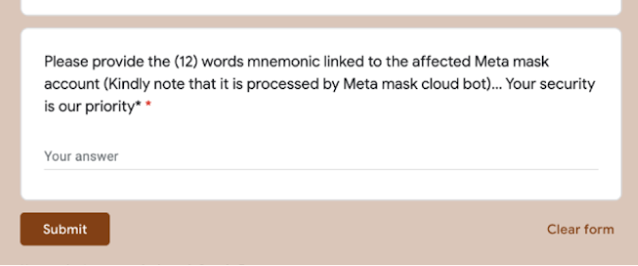
The other space where social engineering attacks have been occurring at pace is the cryptocurrency and web3.0 space, even though the value of cryptocurrencies has cratered recently. Cisco Talos has talked at length about the ways scams have emerged in Web 3.0, but social engineering attacks against NFT/Cryptocurrency users are increasingly common. Users are commonly approached if they post about having issues with their accounts, with criminals waiting to defraud them out of whatever value they have in their wallets. These attacks are widespread, as users posting anything related to issues with MetaMask can attest, they will find you quickly. Most of the time, it seems innocuous with the adversary asking the target to fill out a form, but in the end, adversaries are after users’ mnemonic password, allowing the attacker to empty the wallet with little recourse for the victim.
Defending against insider threat
Defending against these types of insider threats is difficult for a variety of reasons, but first and foremost, they typically are allowed to access the network and have valid login credentials. This is where traditional security controls like user and access control come into play. Organizations should limit the amount of access a user has to the minimum required for them to perform their job. This should prevent them from accessing documents or systems that they shouldn’t and, along with proper alerting logic, should generate alerts if they attempt to access something they shouldn’t. Users make mistakes and click things occasionally, but a user being denied 15 - 20 times in a short period should be investigated.
Additionally, administrators should ensure that the organization has proper defense-in-depth and is inspecting laterally across the organization and not just analyzing traffic traversing your boundary or going north/south. This will ensure if the user is being leveraged to help the attackers, whether willing or otherwise, there are solutions in place to detect and block it.
This is also where routine auditing can play a role. It’s common for an account to be created for testing or other purposes and forgotten, these types of accounts can be devastating if missed. Additionally, auditing the access users/groups have regularly can eliminate things like access hoarding, group sprawl and permission creep, which results in users having far more access than they should.
For those organizations that deal with financial transactions, ensure that there is a system of checks and balances in place so no one single person can initiate and complete a wire transfer or other significant movement of funds without additional oversight and approval. Too often, have we seen organizations without these types of controls have significant amounts of money leave via BEC or another financially motivated social engineering attack.
Finally, there is the issue of what to do when someone leaves the organization. There are some obvious steps like disabling their accounts and ensuring they can’t connect to the enterprise remotely through VPN. However, less obvious is ensuring the user doesn’t have any existing connections and, in today’s hybrid work world, it’s likely they will still have access to company assets, including laptops and other systems. Implementing a mechanism to wipe those systems remotely will be important, as well.
There are additional steps organizations need to take, specifically for users with an increased level of access. Rotate shared credentials — in a perfect world, this wouldn’t be an issue, but we’ve all worked in organizations where shared credentials are a thing and can commonly be abused by recently departed team members. Along those same lines, rotate any cloud credentials. Today, almost all organizations have some or most of their data hosted in the cloud and there are ways to access that data from outside the organization. These lines of access should be addressed when key employees leave the organization.
One final step is to create some detection logic to look for login attempts from disabled users. This will at least will give admins some level of indication that a former employee could be attempting to establish access. Likewise, admins and defenders should ensure all service accounts cannot login directly which can be configured via Group Policy, as they can also be abused by a malicious insider if misconfigured, resulting in an elevated level of access ripe for abuse.
Regarding unwitting assets, the key is user education. Enterprises should include social engineering attacks as part of their red teaming or other pentesting that occurs regularly. Additionally, they should roll out specific training to employees to educate them on social engineering. This needs to include what normal MFA activity looks like, the ways that support would contact users and the types of things you should never share, and finally, for financial organizations/departments, understanding how money transfers should be handled and vetted.
Insider threats increasing
Over the past six months to a year, we have seen an increasing amount of incident response engagements involving malicious insiders and unwitting assets being compromised via social engineering. As we continue to improve the ways we can detect and stop active exploitation and as macros are slowly removed from the landscape, the options for adversaries are going to dwindle.
Realize they are always going to take the path of least resistance, historically that meant active exploitation, more recently it fell to maldocs, and in the future, it’s likely going to fall increasingly to social engineering attacks and turning a user into a malicious insider. Unfortunately, as the payouts have shown, the amount of money at play is significant and they will likely find users willing and able to take that leap to the dark side.