In today's threat landscape, Adobe Flash Player unfortunately remains an attractive attack vector for adversaries to exploit and compromise systems. Over the past year, Talos has observed several instances where adversaries have identified zero-day vulnerabilities and exploited them to compromise systems. Talos is aware of reports that CVE-2016-1019, an Adobe Flash 0-day vulnerability, is currently being exploited in the wild and is affecting systems running Windows 10 and earlier.
According to the Adobe Flash Player security advisory published on April 5, Flash Player versions 21.0.0.197 and earlier are susceptible to compromise via CVE-2016-1019. This includes Flash Player version 20.0.0.306 as well as Flash Player Extended Support Release (ESR) version 18.0.0.333 and earlier. One special note is that as of March 10, 2016, Adobe introduced a mitigation that prevents exploitation of CVE-2016-1019 in Flash version 21.0.0.182 and later.
Due to the continued nature of adversaries exploiting Adobe Flash, Talos is advising everyone to take precautions to mitigate the impact of this vulnerability and disable or remove unnecessary browser plugins. If this is not possible, Talos recommends all users upgrade Flash on their computers immediately. This is especially important for organizations who currently use Flash Player ESR. Per Adobe's advisory, the mitigation introduced in 21.0.0.182 is not present in the ESR 18.0 branch. For users who do not have the ability to update or remove Flash, Talos recommends that you make Adobe Flash "click-to-play" in your browser or to use a browser that sandboxes Flash effectively.
Talos is releasing the following Snort rules in response to this zero-day vulnerability. Please note that additional rules may be released at a future date and current rules are subject to change pending additional information. For the most current rule information, please refer to your FireSIGHT Management Center or Snort.org.
Snort Rules: 38429-38434
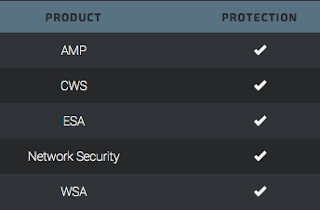
AMP is automatically covering the use of this Flash exploit in the wild as observed in the Nuclear and Magnitude exploit kits.