We love adobe. We love the u30. We love 32 bit values that are encoded as somewhere between 1 and 5 bytes. This is certainly a file format which has outlasted it's day in the sun. (56k modems)
Here Adobe mentions a CVE. Keep that in mind.
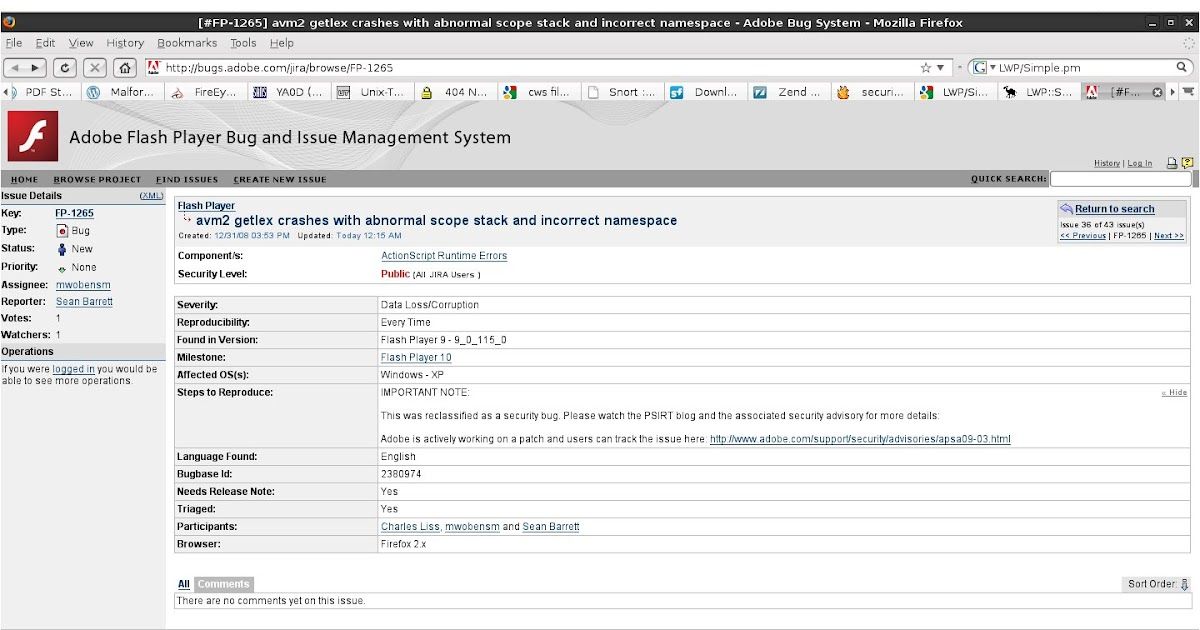
Yesterday, they locked a bug you might find interesting: (picture courtesy of Shirkdog)
One of the big problems with tracking the bug down is that if you change a value in the file, it no longer crashes. This isn't because you've found the triggering condition, but because if the flash is changed, Acroread gives up, and displays what it can, without any error message at all. The trick is not making the bad file not crash, but making a good file crash, and as you can see from the bug, this involves not a single issue, but multiple issues which can be hard to isolate.
Also, it seems like a few other people have caught on to the flash heap spray techniques after my tweet. The sample mentioned in a comment on the sans website as 0-day yesterday was actually a geticonv bug, which we quickly determined to be a different bug (since it didn't trip any of the breakpointed codepaths necessary to the flash bug), but still a live exploit of some kind. So yeah, we're only tracking a single bug at this point as live despite my big mouth. At the time we had two bad files, which exploited different vulnerabilities and I didn't take the bandwidth from bug one to eval bug two.
The patch I released on the 22nd was for the version of Acroread just before the current one (released on the 23rd), so it won't work on the latest one, but you should probably just delete authplay.dll until I can find a prettier way to disable javascript in a patch. It'll tank the program when it tries to load the missing dll, but that's just because some people don't check error codes, and it is not a vulnerable condition.