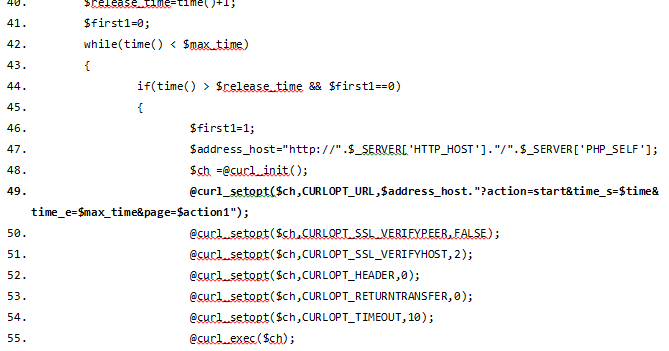
Life Cycle and Detection of an Exploit Kit
Exploit kits may not be as hot a topic as the recently released Mandiant Report, but they're still an important part of today's threat landscape. As the success of the Cool Exploit Kit lets its author buy vulnerabilities, for example, these kits are not only one of the mo
More Targeted PDF 0-Day
Much like other vendors in the security space, the VRT spent yesterday scrambling to address the latest Adobe/PDF vulnerability. The attack - which works across multiple operating systems, bypasses Adobe's sandbox, and which has been used in recent targeted campaigns - is sti
How To Become an Infosec Expert, Part I
I recently put a post on my personal blog seeking applicants for a position with the VRT, working directly with me on public-facing issues (such as writing for this blog, talking to customers, etc.). Since the skill set involved there is subtly, but importantly, different from a
Web Proxies, User-Agent Strings, and Malware Detection
One of the simpler ways to identify malware-infected machines communicating with their command and control servers is to watch for known malicious User-Agent strings in HTTP requests. For those not familiar with them, User-Agent strings are added to almost all HTTP queries on the
Information Superiority
I presented yesterday at the 9th annual Hackers2Hackers conference in Sao Paulo on the subject of information superiority, a subject the VRT has long been fond of. My slides are here for those who'd like to read them. In a nutshell, the talk made the point that, if you know
itsoknoproblembro, the VRT has you covered
When the large-scale DDoS attacks on American banks began a couple of weeks ago, the VRT started digging through all of our sources of information, looking to understand the precise tactics being used, so that we could put together the best possible protection strategy for potent
Anomaly Detection Rules & The Success of Open-Source Rule Testing: Don't Do That, Part 2
Last November, the VRT established an open-source rule testing group, composed of a number of Snort users from around the planet in industries as diverse as defense contracting and education. To date, we've tested well over a hundred rules with this group, and have had a grea
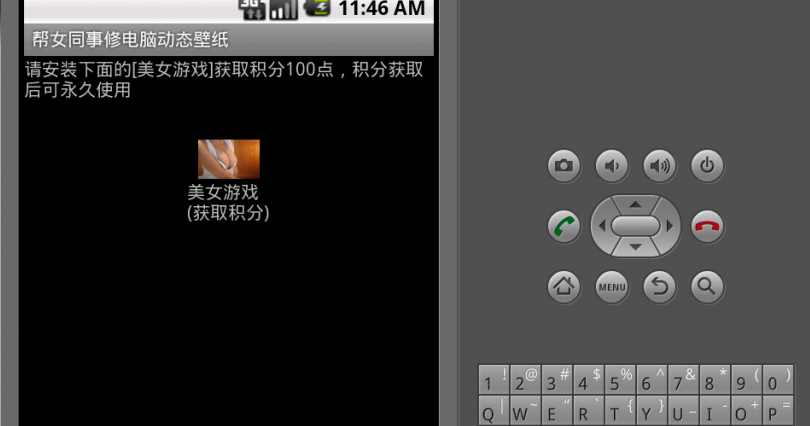
SMSZombie: A New Twist on C&C
One of the most virulent pieces of Android malware to date was recently discovered by TrustGo Labs. Dubbed SMSZombie, this malicious application has infected some 500,000 users throughout China, after having been distributed through the GFan mobile application marketplace. In so
CVE-2012-1535: Flash 0-day In The Wild
Yesterday Adobe released APSB12-18, which addressed CVE-2012-1535. As noted in the Adobe bulletin, the vulnerability has been actively exploited in the wild, though primarily in targeted attacks wrapped in Microsoft Word documents. The VRT was able to obtain a sample of one of t