Shellshock - Update Bash Immediately!
Shellshock is a serious vulnerability. Bash, arguably the most widely distributed shell on Linux systems, fails to correctly parse environment variables with function declarations. Why the fuss over environment variables? Because these variables are often set by programs that han
Internet Explorer & Adobe Flash 0-Day Coverage
Recently several "0day" releases have come out in the security world, and the VRT has released coverage for two critical vulnerabilities, so we wanted to notify you of this coverage so you can use the SIDs to protect your environment. Microsoft Internet Explorer 0day C
Heartbleed for OpenVPN
Core to the VRT's mission is challenging the general intrusion detection industry's view of "adequate" vulnerability coverage. One way we do this is to seek out new attack vectors for critical vulnerabilities the industry may have overlooked and take the initiat
Heartbleed Continued - OpenSSL Client Memory Exposed
The Heartbleed vulnerability is bad. Not only does it pose a risk to servers running the vulnerable version of OpenSSL (1.0.1 through 1.0.1f) with heartbeats enabled, it also poses a serious risk to clients running the vulnerable versions. OpenSSL clients process heartbeats usin
Heartbleed Memory Disclosure - Upgrade OpenSSL Now!
Heartbleed is a serious vulnerability in OpenSSL 1.0.1 through 1.0.1f. If you have not upgraded to OpenSSL 1.0.1g or installed a version of OpenSSL with -DOPENSSL_NO_HEARTBEATS it is strongly recommended that you do so immediately. This vulnerability allows the attacker to rea
IE Zero Day CVE-2013-3897 -- You've been protected for more than a week.
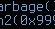
A little over a week ago the VRT discovered a very interesting bit of javascript on a popular JS unpacker site. Several things immediately piqued our interest in this sample. First of all, we found multiple calls to Math.atan2() with curious parameters: This is a popular techniq
Quarian: Reversing the C&C Protocol
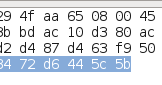
Win.Trojan.Quarian was reportedly first found in a leaked email from the Syrian Ministry of Foreign Affairs. It arrives on the victim's machine via a PDF document. The PDF contains an exploit for CVE-2010-0188 which, if successful, passes execution to embedded shellcode. The