Qakbot levels up with new obfuscation techniques
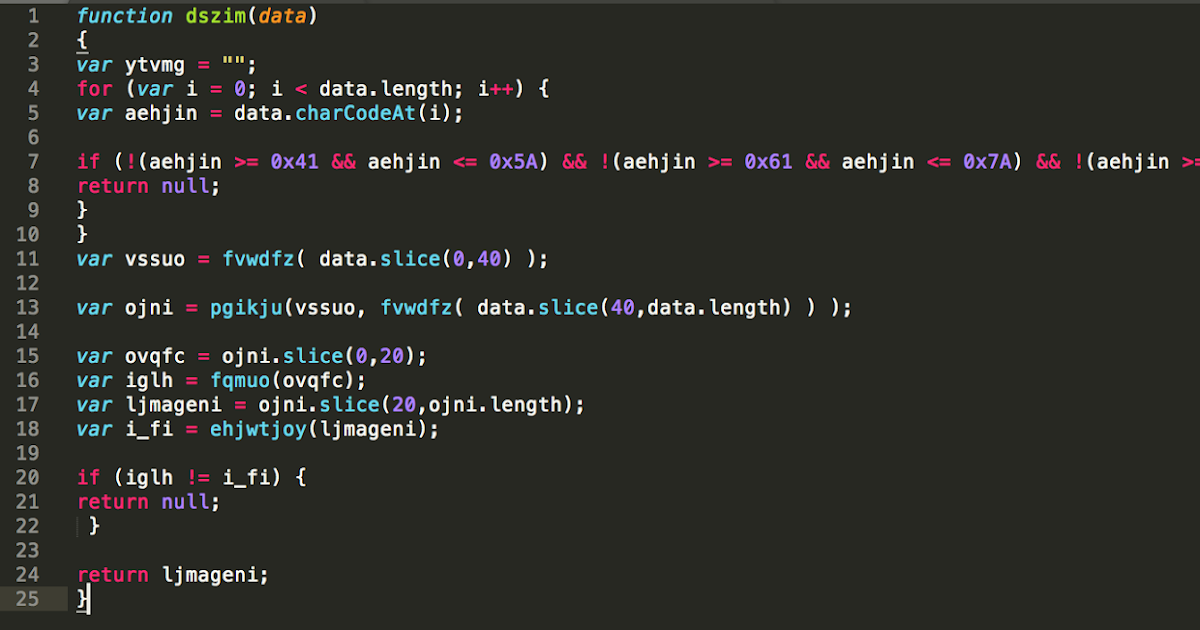
Executive summary Qakbot, also known as Qbot, is a well-documented banking trojan that has been around since 2008. Recent Qakbot campaigns, however, are utilizing an updated persistence mechanism that can make it harder for users to detect and remove the trojan. Qakbot is known
Etumbot Detection, more prior coverage
Arbor Networks recently posted details about a backdoor they named Etumbot. It provides technical detail about the functionality of the malware and it includes hashes of known samples. The Arbor write up is available here: http://www.arbornetworks.com/asert/2014/06/illuminating-
Delivering an executable without an executable
The 0-day That Wasn't: Dissecting A Highly Obfuscated PDF Attack
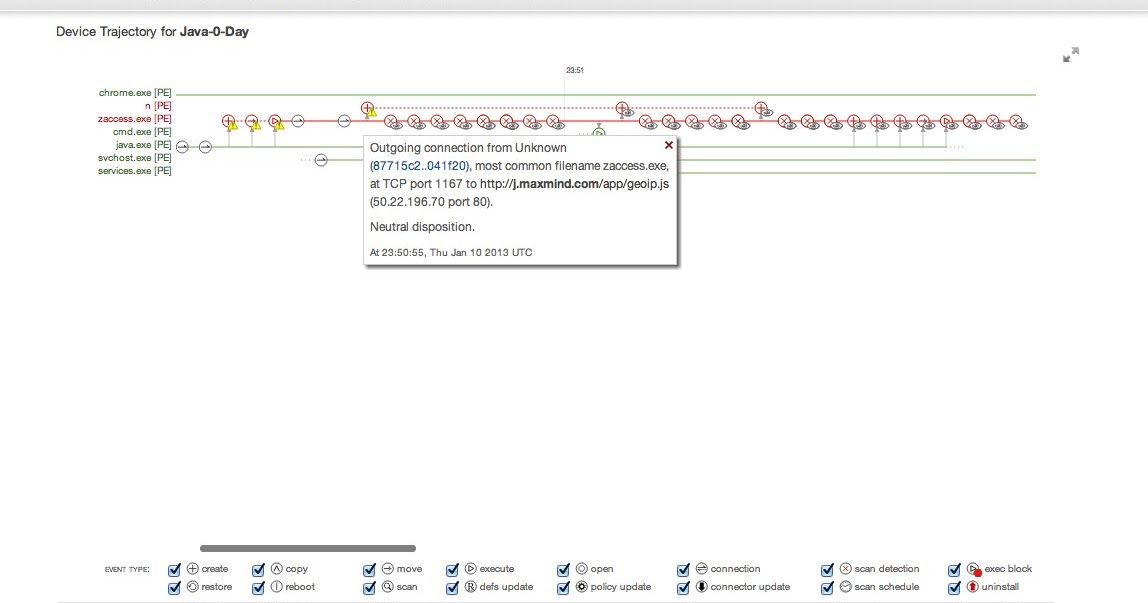
Generic Exploit Kit Detection & The First Java 0-Day of 2013
Using negative distance to create detection windows
A common method for delivering malicious pages to clients is with the use of hidden iframes. Before I get started I want to say that I have seen hidden iframes used legitimately and the rule discussed will not be in any policies by default, due to the risk of false positives. Th
Matryoshka packets
I have heard many people talk about ICMP and UDP tunnels but very rarely observed them in the wild. We recently had the opportunity to examine a sample that uses this technique for C&C. It communicates by either an ICMP echo with a data section that includes a full TCP SYN pa