Given the recent slate of massive ransomware attacks that have disrupted everything from hospitals to car dealerships, Cisco Talos wanted to take a renewed look at the top ransomware players to see where the current landscape stands.
Based on a comprehensive review of more than a dozen prominent ransomware groups, we identified several commonalities in tactics, techniques and procedures (TTPs), along with several notable differences and outliers.
Talos’ studies indicate that the most prolific ransomware actors prioritize gaining initial access to targeted networks, with valid accounts being the most common mechanism. Phishing for credentials often precedes these attacks, a trend observed across all incident response engagements, consistent with our 2023 Year in Review report. Over the past year, many groups have increasingly exploited known and zero-day vulnerabilities in public-facing applications, making this a prevalent initial access vector.
Watch: Discussion of latest ransomware trends
The AlphV/Blackcat and Rhysida groups stood out with the broadest range of TTPs, demonstrating significant tactical diversity. Conversely, groups like BlackBasta, LockBit and Rhysida not only encrypted data and defaced victim systems to maximize impact. Distinctively, the Clop ransomware group primarily focused on extortion through data theft rather than typical encryption tactics and is one of the only actors to exploit zero-day vulnerabilities.
Our findings are based on a comprehensive analysis of 14 ransomware groups between 2023 and 2024. We selected the ransomware groups based on volume of attacks, impact on customers, and atypical threat actor behavior. Our research includes data from the actors’ public leak sites, Cisco Talos Incident Response (Talos IR), Talos internal tracking efforts and open-source reporting.
During this research period, Talos IR was actively engaged in responding to a considerable number of ransomware attacks heavily targeting the United States. These attacks spanned a broad spectrum of industries, notably impacting the manufacturing and information sectors, employing various techniques to encrypt data and demand ransoms, with their activities resulting in significant levels of financial losses and business disruption.
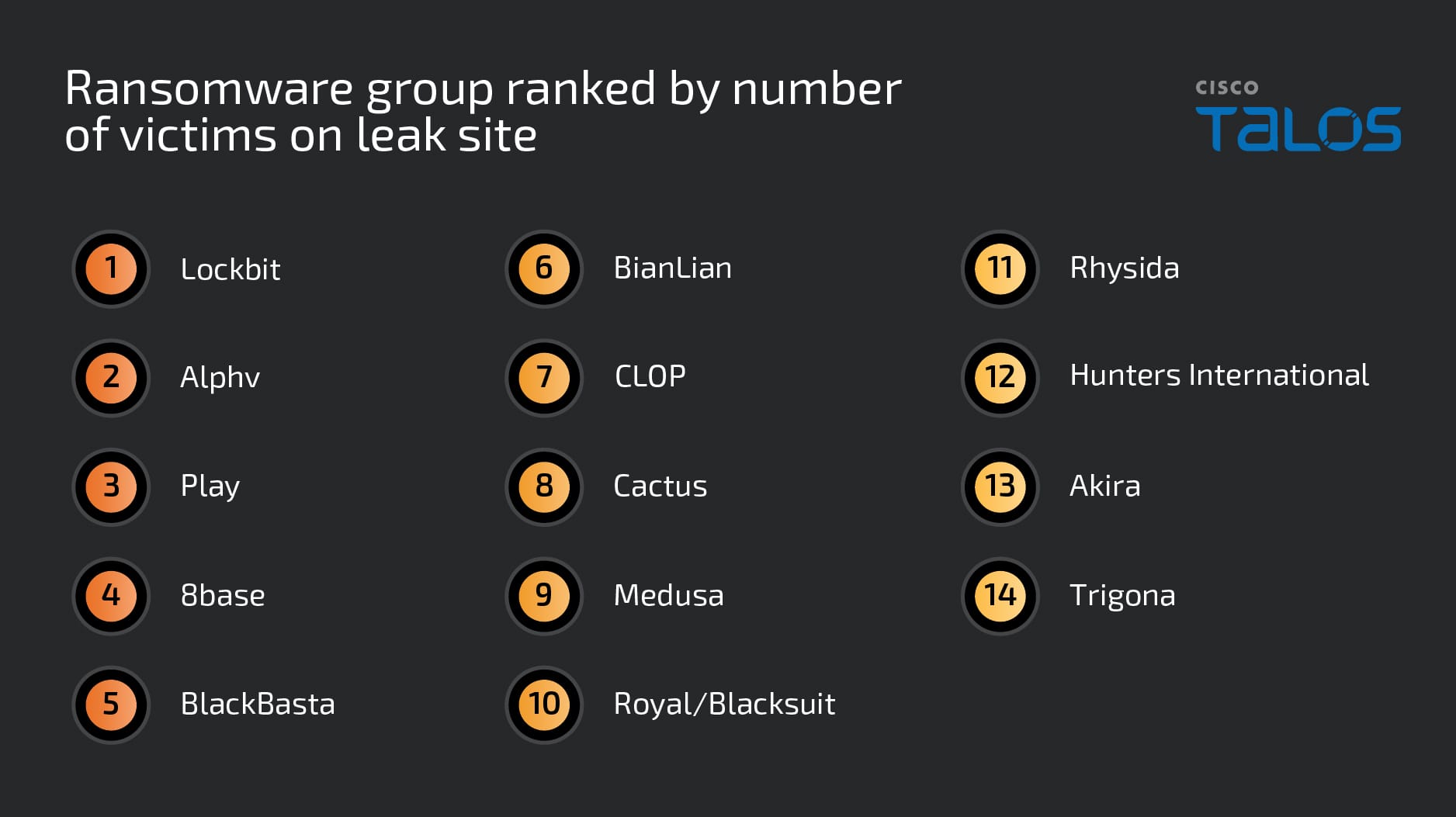
Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology. The diversification highlights a shift toward more boutique-targeted cybercriminal activities, as groups such as Hunters International, Cactus and Akira carve out specific niches, focusing on distinct operational goals and stylistic choices to differentiate themselves.
An advanced arsenal: Notable TTPs employed by ransomware actors
Utilizing the MITRE ATT&CK framework as a baseline, we identified the primary TTPs utilized by major ransomware threat actors over the past three years which involved a detailed examination of each TTP, its execution methods, and relevant sub-techniques, that highlight unique TTPs not previously emphasized in MITRE’s top ATT&CK techniques.
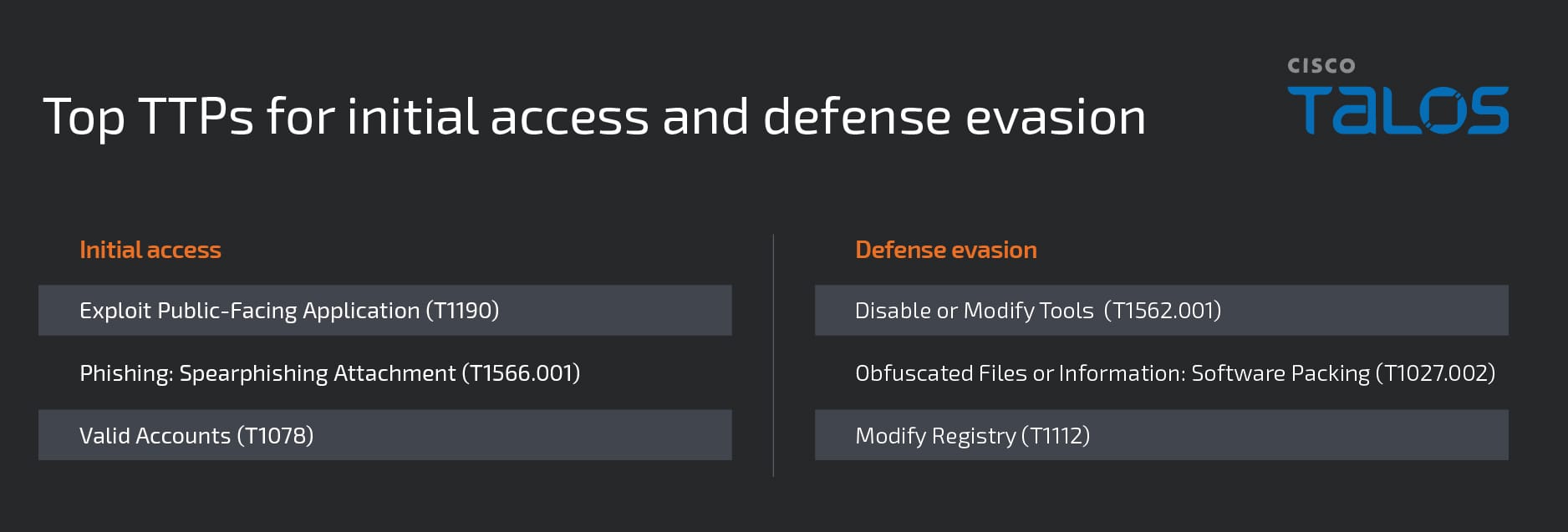
Key findings indicate that many of the most prominent groups in the ransomware space prioritize establishing initial access and evading defenses in their attack chains, highlighting these phases as strategic focal points. Within the past year, many groups have exploited critical vulnerabilities in public-facing applications, becoming a prevalent attack vector, which we addressed later, indicating an increased need for appropriate security controls and patch management.
Echoing a trend identified in our Talos Year in Review report, our data supported the conclusion that ransomware actors continue to apply a significant focus to defense evasion tactics to increase dwell time in victim networks. Typical popular defense evasion methods include the disablement and modification of security software such as anti-virus programs, endpoint detection solutions, or security features in the operating system to prevent the detection of the ransomware payload. Adversaries will also often obfuscate malicious software by packing and compressing the code, eventually unpacking itself in memory when executed. They’ll also modify the system registry to disable security alerts, configure the software to execute at startup, or block certain recovery options for users.
The most prevalent credential access technique Talos IR engagements have seen in 2023 and 2024 is the dumping of LSASS memory contents. Ransomware threat actors were seen often targeting the Local Security Authority Subsystem Service (LSASS) to extract authentication credentials by dumping memory. This technique involves accessing the LSASS process' memory to retrieve plaintext passwords, hashed passwords, and other authentication tokens stored in memory. This tactic is particularly effective because it exploits the normal functioning of a legitimate system process.
We also identified a trend in command and control (C2) activities indicating continued use of commercially available tools by affiliates, such as AnyDesk and ScreenConnect remote monitoring and management (RMM) applications, indicating a threat actor preference for readily accessible, legitimate technologies in maintaining influence over compromised systems. Abusing often trusted applications allows actors to blend in with corporate network traffic and reduce resource development costs without needing to develop distinct custom C2 mechanisms.
Typical attack chain of ransomware actors: Insights from the top 14 groups
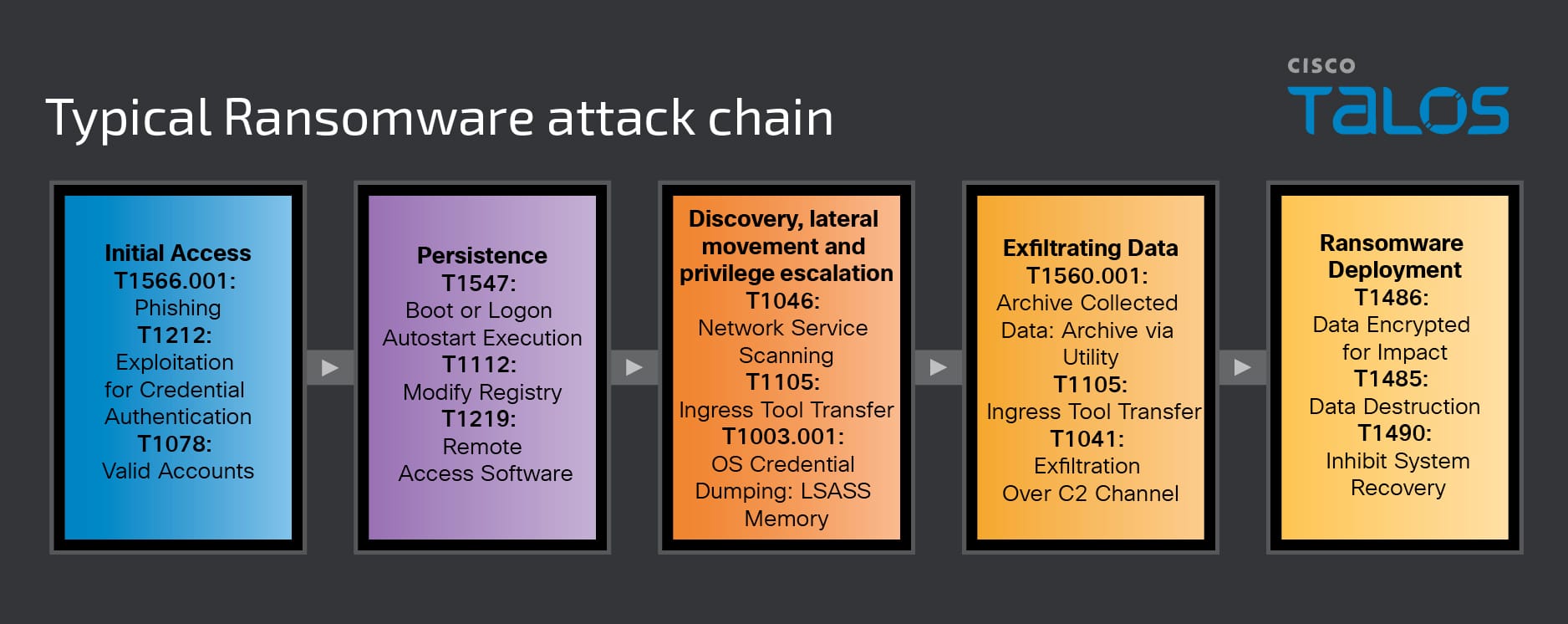
In the first phase of a ransomware attack, adversaries work to gain initial access to the target network, using a combination of social engineering, network scanning and open-source research to learn about their victims, identify possible access vectors, and customize their initial access attempts. Adversaries may send emails containing malicious attachments or URL links that will execute malicious code on the target system, deploying the actors' tools and malware, and exploiting multi-factor authentication (MFA). There are many ways adversaries hope to bypass MFA, whether because of poor implementation or because they already have valid account credentials. Most notably, we have seen an increasing number of ransomware affiliates attempting to exploit vulnerabilities or misconfigurations in internet-facing systems, such as in legacy or unpatched software.
Then, these actors will look to establish long-term access, ensuring that their operations will be successful even if their initial intrusion is discovered and remediated. Attackers often use automated malware persistence mechanisms, such as AutoStart execution upon system boot, or modify registry entries. Remote access software tools and create local, domain and/or cloud accounts can also be deployed to establish secondary credentialed access.
Upon establishing persistent access, threat actors will then attempt to enumerate the target environment to understand the network’s structure, locate resources that can support the attack, and identify data of value that can be stolen in double extortion. Using various local utilities and legitimate services, they exploit weak access controls and elevate privileges to the administrator level to progress further along the attack chain. Ransomware actors continue this cycle of persistence to escalate privileges and compromise additional hosts. We have observed the popular use of many network scanner utilities in conjunction with local operating system tools and utilities (living-off-the-land binaries) like Certutil, Wevtutil, Net, Nltes and Netsh to blend in with typical operating system functions, exploit trusted applications and processes, and aid in malware delivery.
In the shifting focus to a double extortion model, many adversaries collect sensitive or confidential information to send to an external adversary-controlled resource or over some C2 mechanism. File compression and encryption utilities WinRAR and 7-Zip have been used to conceal files for the unauthorized transfer of data, while adversaries often exfiltrate files using the previously mentioned legitimate RMM tools. Custom data exfiltration tools have been developed and used by the more mature RaaS operations, offering custom tooling such as Exbyte (BlackByte) and StealBit (LockBit) to facilitate data theft.
At this point, adversaries are ready to stage the ransomware payload and begin encryption. Steps they may take to prepare for the attack include customizing the code for specific objectives (e.g., ignoring certain file types/locations), embedding the ransomware in the environment, testing delivery mechanisms, and ensuring that the ransomware relates to and receiving instructions from the attacker's C2 server, which contains the encryption key. The adversary will then begin encrypting the network and notifying the victim that they have been breached. If the goal is pure data theft extortion, then this phase is skipped.
Ransomware actor’s exploitation of vulnerable applications (CVEs)
Analysis of Talos IR engagements focusing on the exploitation of critical vulnerabilities in public-facing applications by ransomware actors uncovered three vulnerabilities for their repeated exploitation: CVE-2020-1472, CVE-2018-13379 and CVE-2023-0669. Exploitation of these and other critical vulnerabilities can provide initial access and lead to privilege escalation by the threat actors.
CVE-2020-1472 ("Zerologon")
CVE-2020-1472, known as "Zerologon," exploits a flaw in the Netlogon Remote Protocol (MS-NRPC), allowing attackers to bypass authentication mechanisms and change computer passwords within a domain controller's Active Directory. Ransomware actors leverage this vulnerability to gain initial access to networks without requiring authentication, quickly escalating privileges to domain administrator levels. This access enables them to manipulate security policies, and potentially disable security defenses, facilitating unobstructed lateral movement and attack progression.
CVE-2018-13379 (Fortinet FortiOS SSL VPN vulnerability)
The path traversal vulnerability in Fortinet's FortiOS SSL VPN, identified as CVE-2018-13379, allows unauthenticated attackers to access system files through specially crafted HTTP requests. Ransomware groups have exploited this vulnerability to obtain sensitive information, such as VPN session tokens, which can be used to gain unauthorized access to the network. With access secured, attackers will then advance through the attack chain moving laterally within the network, exploiting further vulnerabilities or weak configurations, deploying ransomware, and exfiltrating data.
CVE-2023-0669 (GoAnywhere MFT vulnerability)
Discovered in January 2023, CVE-2023-0669 affects the GoAnywhere Managed File Transfer (MFT) software, allowing remote attackers to execute arbitrary code on the server without requiring authentication. This critical vulnerability enables actors to deploy ransomware payloads directly to servers or use the compromised server as a pivot for further internal reconnaissance and lateral movement. The ability to execute arbitrary code enables attackers to manipulate systems, create backdoors and disable security controls.
Talos also recently reported on a complex campaign targeting Cisco Adaptive Security Appliances (ASA), exemplifying further state-sponsored actors targeting critical vulnerability exploits in perimeter network devices. Cisco's PSIRT and Talos Threat Intelligence and Interdiction identified the previously unknown actor UAT4356, who employed bespoke tooling for sophisticated espionage activities, leveraging two vulnerabilities, CVE-2024-20353 and CVE-2024-20359, as part of this campaign.
The security of public-facing applications continues to be an area of significance due to organizations' continued reliance of scalable software applications, integral for day-to-day business operations, posing a significant impact on organizational security and data integrity. The exploitation of these vulnerabilities can lead to severe disruptions, financial losses and reputational damage.
Mitigation recommendations
Regular patch management: Consistently apply patches and updates to all systems and software to address vulnerabilities promptly and reduce the risk of exploitation.
Strict password policy and MFA: Implement strong password policies that require complex, unique passwords for each account. Additionally, enforce multi-factor authentication (MFA) to add an extra layer of security.
System and environment hardening: Apply best practices to harden all systems and environments, minimizing attack surfaces by disabling unnecessary services and features.
Network separation and client network authentication: Segment your network using VLANs or similar technologies to isolate sensitive data and systems, preventing lateral movement in case of a breach. In addition to utilizing network access control mechanisms such as 802.1X to authenticate devices before granting network access, ensuring only authorized device connections.
Monitoring and endpoint detection and response: Implement a Security Information and Event Management (SIEM) system to continuously monitor and analyze security events, in addition to the deployment of EDR/XDR solutions on all clients and servers to provide advanced threat detection, investigation, and response capabilities
Principle of least privilege: Adopt a least-privilege approach, ensuring that users and systems have only the minimal level of access necessary to perform their functions, thereby limiting potential damage from compromised accounts.
Minimize IT exposure to the internet: Reduce your IT systems' exposure to the Internet by limiting the number of public-facing services and ensuring robust protections for any necessary external interfaces.
