According to the Centers for Disease Control and Prevention (CDC), “If you’re ready for a zombie apocalypse, then you’re ready for any emergency.” While events haven’t yet risen to the level of “zombie apocalypse”, computer attackers are continuing to use their voodoo to zombify Internet domains, and repurpose them for their own heinous crimes.

|
| Image from the CDC’s Zombie Apocalypse preparedness site |
Take, for example, the case of the domain “gfmqatar.com”. According to whois records, this domain was created on October 16, 2014. Within a couple weeks of the date it was registered, a spear-phisher had compromised this domain; by Halloween 2014, this domain’s DNS server was serving phishing content aimed at impersonating Google.
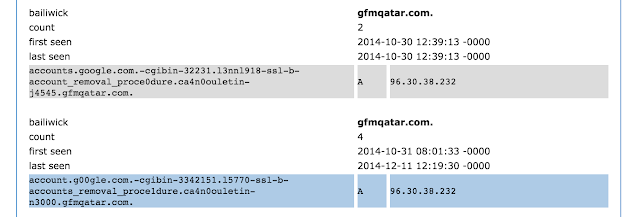
Effectively a zombie, this domain continued to be used by the phishers throughout the rest of 2014 and continuing into 2015.
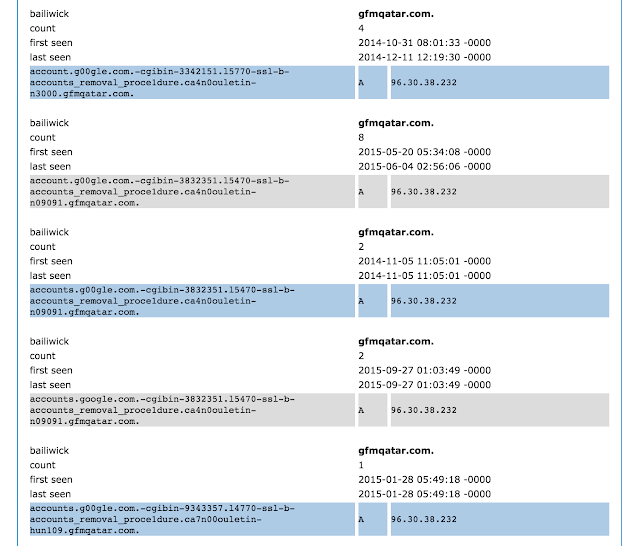
Based on the numbers in passive DNS, it appears this domain has had more visitors seeking the phishing subdomains, than it has had visitors seeking its actual, intended, legitimate domain. Visitors resolved the base domain name “gfmqatar.com” thirty-seven times between December 2014 and September 2015, while just one of the phishy subdomains was resolved over one hundred times during the month of September 2015.
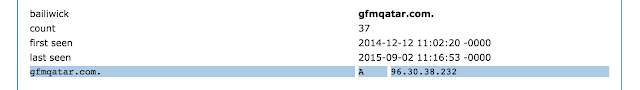
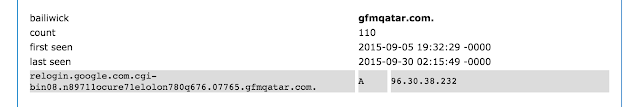
There are several more of these zombie domains that are similarly used for phishing. One of the things many of these zombie domains have in common are large numbers of subdomain labels; the leftmost labels having been designed to fool human users into thinking they are a known, legitimate domain. Below is a small sample of some similar “many-labels” phishy-looking subdomains that Talos noted were in use during the month of September 2015:
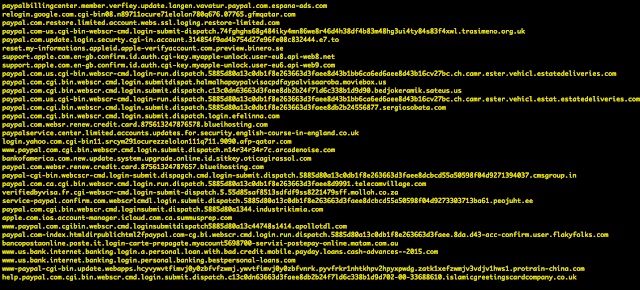
The domain “flakyfolks.com” is another great example of a zombie domain. Based on information in passive DNS, this domain was used for phishing as far back as March 2012.
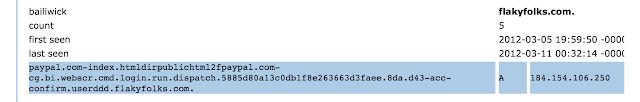
Similar looking subdomains at “flakyfolks.com” domain appeared once the domain name was renewed in late 2014, and new phishy subdomains continued to appear throughout 2015:

Since November of 2014, the nameservers for the domain “flakyfolks.com” have resided at ztomy.com. Some of our regular blog readers may remember the domain parking/monetization organization behind ztomy.com.
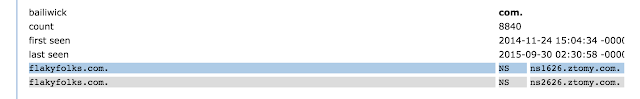
As part of the domain monetization service, the nameservers at ztomy.com appear to provide some mechanism for domain owners to resolve specific subdomains to IP addresses outside of the parked domain. And because of the dates when the phishing subdomains continued to appear, the most likely conclusion is that the domainer who owns “flakyfolks.com” has had their ztomy.com domain parking account credentials stolen.
If the miscreants behind this particular attack have compromised credentials for a domainer’s portfolio of domains, they would likely have access to a substantial number of parked domains they could appropriate for similar, nefarious purposes. Of course, this is just the tip of the zombie-domain iceberg. Many other neglected vanity and small business domains are also unwitting victims in this scheme.
The Big Picture To gain a better understanding of the issue, Talos sampled approximately 500 phishing hostnames that were using the “many-labels” technique. Talos extracted the root domains (~200 domains), and checked them against passive DNS to examine the behavior of the set of domains over time.
Interestingly, 31% of the domains in our dataset had been serving phishing-related hostnames via DNS for over three years --the oldest serving up phishing-related hostnames since the year 2010! However, phishing overall tends to be a game of whack-a-mole, and most threat actors favor using more recently compromised domains. In our dataset, 58% of the domains exhibited their first phishing-related activity within the past 6 months.
|
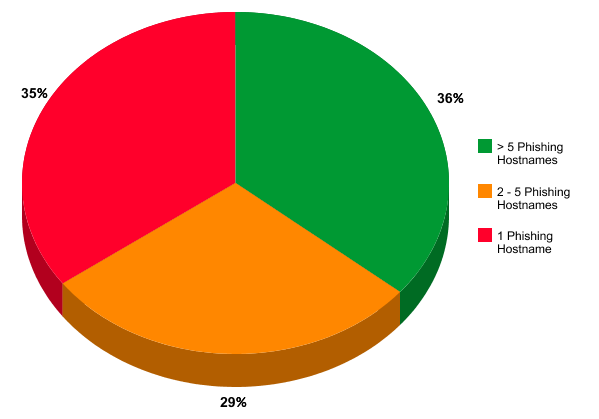
| Unique Phishing-Related Hostnames per Zombie Domain |
In our data set, 36% of the domains published 5 or more phishing-related hostnames; Some of the most egregious offenders apparently had registered domain names exclusively for “many-label” phishing purposes. Meanwhile 35% of the domains had only ever published one phishing hostname in DNS --perhaps an attempt to remain “under the radar”. What was most interesting among the set of domains that only published a single phishing-related hostname, was that some were quite long lived: Almost one-quarter of the domains publishing a single phishing-related hostname had published that hostname in DNS for three years or longer! “Braaaaaaaaains!”
While the use of many subdomains with brand-impersonating leftmost labels is not a new technique used in phishing, it obviously continues to be effective at exploiting unsuspecting users. In DNS, hostnames can be up to 255 characters long, with each individual subdomain label limited to 63 characters. If used in a URL, depending on the browser, and the size of the browser window, a location bar may not be able to accommodate the entire hostname.
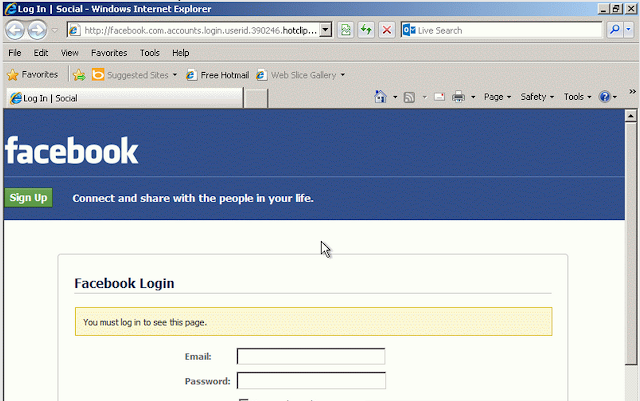
|
| Note the appearance of the location bar when a domain with many labels is used |
The use of zombified legitimate domains provides an element of cover for the attackers. The miscreants are commandeering the victim domain’s positive/neutral reputation, meanwhile they have no problem letting the victim domain become the “fall guy” when/if the phishing attack is eventually discovered.
Isn’t it fascinating how this horde of zombie domains is able to continue to operate, sometimes continuously for years? And all without the domain owners taking any notice of the repeated abuse. Thankfully, Talos is aware of this problem, and has long denied these zombie domains the pleasure of phishing for our credentials --or eating our brains.
Protecting Users
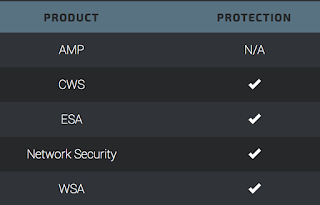
ESA blocks emails that contain these malicious hostnames in URLs sent by adversaries as part of their campaign.
CWS or WSA web scanning prevents access to malicious websites that use these hostnames.
The Network Security protection of IPS and NGFW can prevent users from navigating to website that use these malicious hostnames in URLs.
