Over the past several weeks, there have been ongoing discussions regarding cyber attacks that have occurred against several political, governmental, and private sector entities in the United States. These discussions have revolved around allegations that these cyber attacks were designed to interfere with the 2016 U.S. Federal Elections as well as identifying who is responsible for these high-profile compromises. On December 29, 2016, the United States Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) released a joint analysis report detailing some of the tools and infrastructure used by adversaries to compromise these institutions. The DHS-FBI joint report is referring to this activity as GRIZZLY STEPPE. Talos is aware of these discussions and reports of malicious activity associated with GRIZZLY STEPPE and has responded to ensure our customers are protected.
Coverage for GRIZZLY STEPPE is available through Cisco's security products, services, and open source technologies. The IP addresses listed in the DHS-FBI report have also been evaluated and applicable ones blocklisted. Note that Talos will continue to monitor for new developments to ensure our customers remain protected.
AMP Protection
- W32.55058D3427-95.SBX.TG
- W32.9ACBA7E5F9-95.SBX.TG
- PHP.2D5AFEC034.backdoor.DRT
- W32.AC30321BE9-95.SBX.TG
- W32.9F918FB741-95.SBX.TG
- PHP.0576CD0E94.backdoor.DRT
- W32.Auto.0fd050.182066.in01
- PHP.1343C905A9.backdoor.DRT
- PHP.20F76ADA17.backdoor.DRT
- PHP.249EE04814.backdoor.DRT
- PHP.2D5AFEC034.backdoor.DRT
- PHP.3BD682BB78.backdoor.DRT
- PHP.449E7A7CBC.backdoor.DRT
- PHP.6FAD670AC8.backdoor.DRT
- PHP.7B28B9B85F.backdoor.DRT
- PHP.7DAC01E818.backdoor.DRT
- PHP.9376E20164.backdoor.DRT
- PHP.A0C00ACA2F.backdoor.DRT
- PHP.AE67C121C7.backdoor.DRT
- PHP.BD7996752C.backdoor.DRT
- PHP.D285115E97.backdoor.DRT
- PHP.DA9F2804B1.backdoor.DRT
Web Reputation / DNS Protection
- efax.pfdregistry.net
- private.directinvesting.com
- www.cderlearn.com
- ritsoperrol.ru
- littjohnwilhap.ru
- wilcarobbe.com
- one2shoppee.com
- insta.reduct.ru
- editprod.waterfilter.in.ua
- mymodule.waterfilter.in.ua
- efax.pfdregistry.ne
Snort Rules 41122-41136
ClamAV Signatures
- Win.Trojan.OnionDuke-5486244-0
- Win.Trojan.Agent-5486255-0
- Win.Trojan.OnionDuke-5486245-0
- Php.Malware.Agent-5486261-0
- Win.Trojan.Agent-5486256-0
Please note that additional rules, signatures, and other detection may be released at a future date and current rules are subject to change pending new information. For the most current rule information, please refer to your Defense Center or Snort.org.
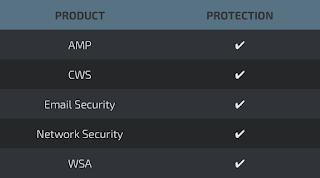
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances, such as IPS and NGFW, have up-to-date signatures to detect malicious network activity by threat actors.