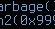
A little over a week ago the VRT discovered a very interesting bit of javascript on a popular JS unpacker site. Several things immediately piqued our interest in this sample. First of all, we found multiple calls to Math.atan2() with curious parameters:
This is a popular technique used in debugging exploits.
A breakpoint can be set in the following way:
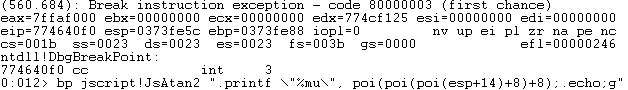
So that later on when the exploit is ran, windbg will print out the second parameter of Math.atan2 calls, in the case above "after gc". Further inspection of the sample revealed that it checks the systemLanguage of the browser and deactivates itself if it doesn't find MSIE 8.0 in the User-Agent combined with either "ko" or "ja" system languages:
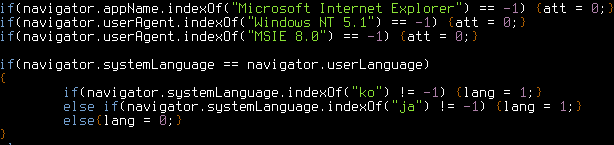
We suspect that the "ko" or "js" language packs were intended targets for ROP exploitation. After a quick run with windbg attached we are greeted with a crash:
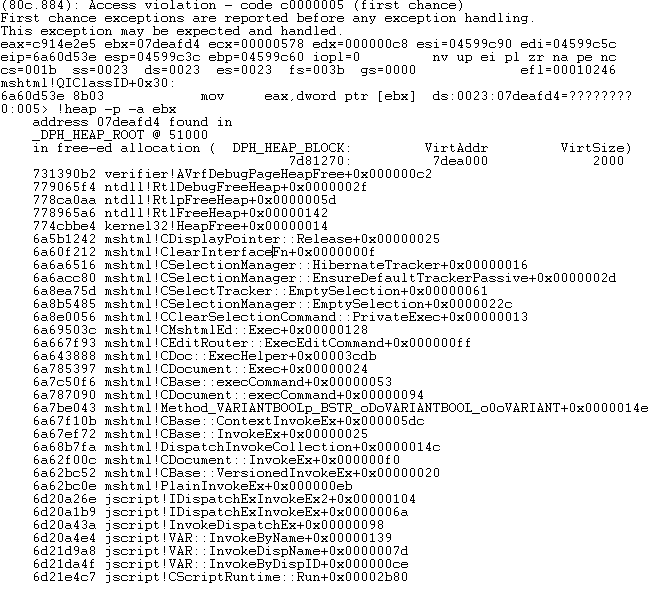
Below you can see the constructor for CDisplayPointer which creates a 0x48 byte HeapAlloc which is freed and the subsequently used:
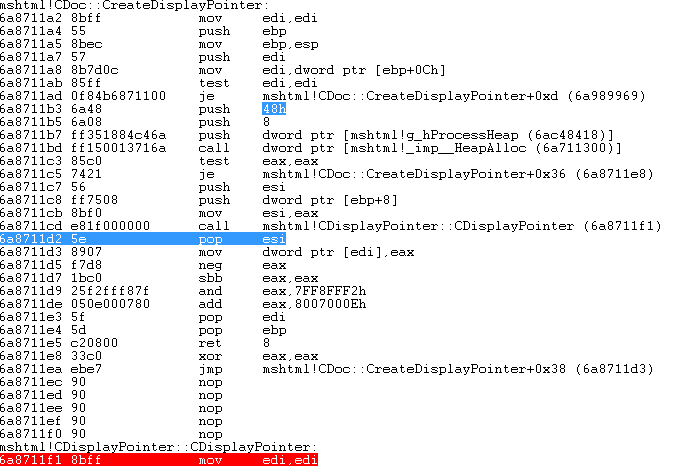
The VRT maintains a working exploit for this vulnerability which leverages a ROP chain from hxds.dll (MS Help Data Services Module) which is installed with Microsoft Office. Even before a MS advisory appeared for this use-after-free vulnerability the VRT released coverage in the form of a TRUFFLE rule. TRUFFLE rules provide a way for the VRT to release cutting edge coverage without exposing threats to the public through a plaintext rule. The SIDs for the TRUFFLE rules covering this vuln were 28091 & 28092. Now that the information is public our customers can find coverage for this vulnerability in SIDs 28207 & 28208.