By Nick Biasini with contributions from Kendall McKay and Guilherme Venere
Headlines continue to roll in about the many implications and follow-on attacks originating from leaked and/or stolen credentials for the Snowflake cloud data platform.
Adversaries obtained stolen login credentials for Snowflake accounts acquired via information-stealing malware and used those credentials — which weren’t protected by multi-factor authentication (MFA) — to infiltrate Snowflake customers’ accounts and steal sensitive information. However, Snowflake isn’t the issue here. This incident is indicative of a much larger shift we’ve seen on the threat landscape for a while — and it focuses on identity.
Over the past few decades, we’ve seen the criminal threat landscape collapse under the ransomware / data extortion umbrella, which is generating so much revenue everyone is trying to grab their piece of the pie. This has been a stark transformation from a loosely associated group of criminals searching for credit card numbers to steal, and spam messages to send to large syndicates that generate, according to the FBI, more than a billion dollars in revenue annually.
Infostealer logs are a gold mine
As part of our regular intelligence discussions, Talos reviews all Cisco Talos Incident Response (Talos IR) engagements. Ransomware/data extortion typically dominate engagements, with business email compromise (BEC) periodically rising to the top, but more broadly, we’ve seen the ways these actors gain initial access continue to diversify.
Early on, active exploitation of known vulnerabilities or other critical misconfigurations would dominate the initial compromise leading to the breach. Lately, the sources have broadened with a focus on compromised, legitimate credentials. These credentials originate from a wide array of sources from generic phishing campaigns and infostealers to insider threats, valid credentials are the ideal cover for malicious activities. This is further supported with information from the most recent Talos IR Quarterly Trends report, where the top infection vector was valid accounts. This problem extends far beyond compromised credentials with large-scale brute force and password spraying attacks occurring regularly.
Infostealers specifically are commonly cited as a source of credentials for these breaches and have been reportedly involved in the recent wave. Many defenders think the infostealers landscape is a monolith with individual actors compromising victims and gathering credentials, but the truth is these are highly organized widely distributed campaigns. The groups have congregated online in Telegram chat rooms where credentials are sold by the thousands or tens of thousands. These actors operate large scale campaigns, gather, vet, and organize the credentials they harvest ready to sell to the highest bidder. This ecosystem includes providing tooling for searching and extracting specific types of data from the logs and validating the credentials before offering.
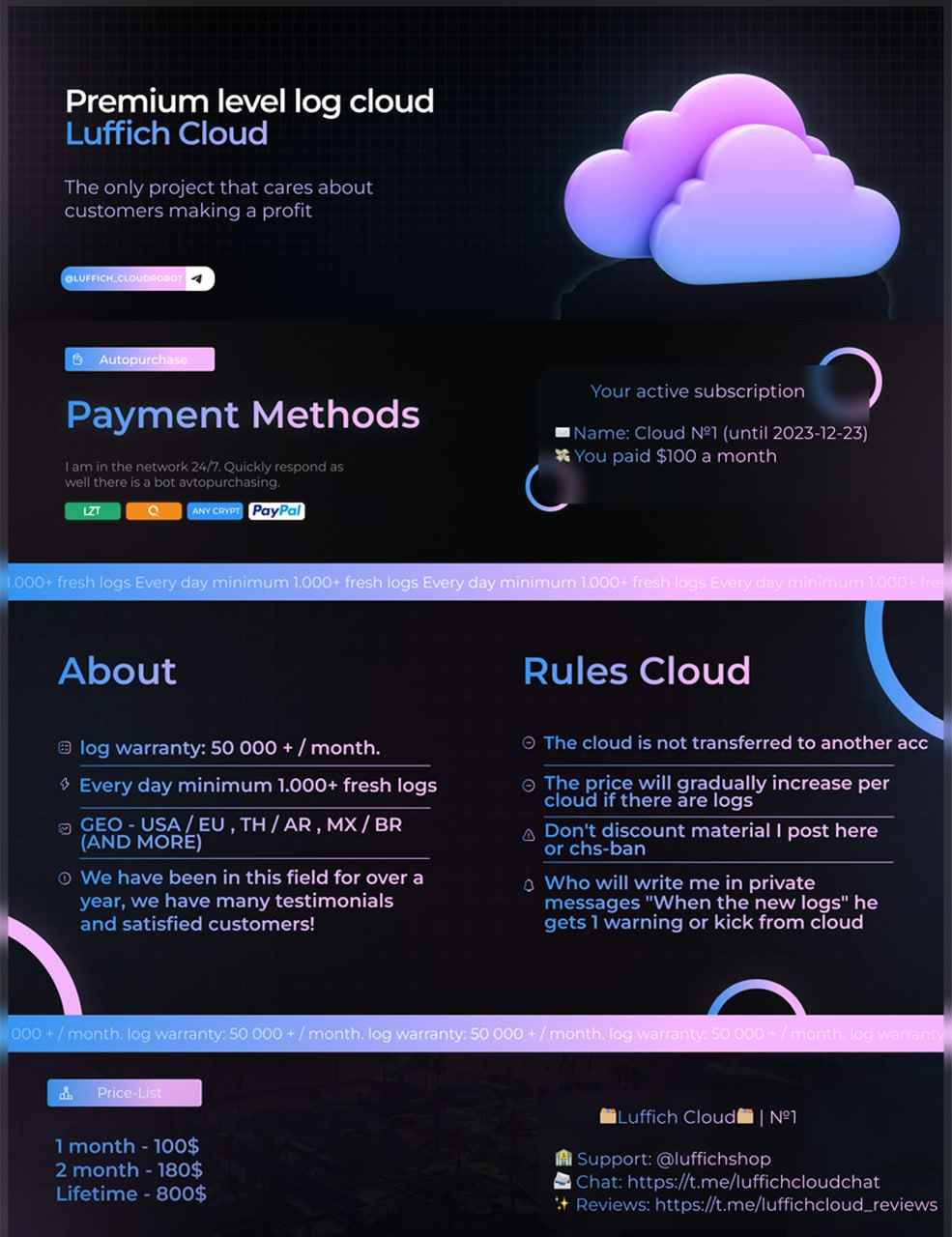
Cisco Talos has sat in these channels and seen thousands of personal credentials for things like Google, Facebook, Netflix, etc. posted for free as a teaser to the larger services they offer. For a fee, actors can get timed access to a repository of credentials to search and use freely. The cost to access these tools varies, but considering a compromised set of enterprise credentials could result in a multi-million-dollar ransom, it’s a minute price to pay.
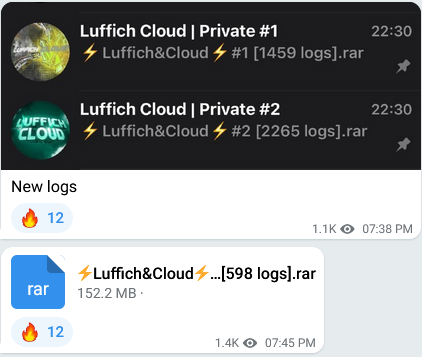
These channels are full of would-be criminals trying to gain the foothold necessary for their nefarious activities. So far, the focus has been on ransomware and data extortion, but BEC actors can also earn payouts from valid enterprise credentials — even the basic accounts tied to organizations like Google can be a windfall. The Cisco breach from several years ago originated with Google credentials and a password vault that contained their corporate credentials.
Today in many enterprises, the credentials alone aren’t enough, as organizations worked diligently to deploy MFA to improve their security baselines. The challenge is that the application isn’t consistent, and the focus has largely been on the enterprise (domain) itself.
Protect data with MFA, not just assets
Organizations have heeded the constant drone of security professionals pushing for deployment of MFA across the organization and its helped. We’ve seen a huge increase in attacks designed to defeat the protections MFA provides. We constantly observe things like MFA fatigue and social engineering to defeat MFA. This is further supported from the IR Quarterly Trends report, where for the first time, MFA push notifications was the top observed security weakness. Improper MFA implementation was also found in nearly as many engagements. Likewise, MFA itself has gone through some iterations with basic push notifications being insufficient for modern attackers. Now, challenge-based authentication is recommended for all MFA deployments. Actors have noticed, and this recent issue with Snowflake credentials has shown you need to protect data, not just assets, and corporate data is everywhere.
Software as a service (SaaS) has revolutionized business and provided advanced sales tools and analytics to a wide array of industries, facilitating growth and expansion. The problem is it requires data to leave the organization’s safe haven. Most medium- to large-sized organizations today are heavily invested in the cloud, if not multi-tenet cloud environments, with data and resources spread across multiple vendors around the globe. This creates many points of entry for attackers that might be more focused on data exfiltration than unauthorized encryption in 2024.
We’ve noticed a marked shift over the last year or two with larger cartels increasingly focusing on the data they can exfiltrate over the data they can encrypt. There are a variety of factors driving this shift, most importantly technology is catching up. We are seeing more pre-ransomware engagements that are detected and stopped before deployment in our emergency responses (ERs), an important shift from the years prior. Organizations are prepared and ready to respond to ransomware and have solid, practiced recovery processes to minimize any effects of data encryption. This has driven actors to focus on the data they can steal over the data they can encrypt.
Actors running large scale infostealer campaigns have compromised tens of thousands, if not millions, of accounts and the breadth of accounts is extensive. Modern infostealers will gather credentials from web browsers, applications, and the system themselves to even include crypto wallets. For many organizations, this includes the SaaS applications that house sensitive data that, when stolen, can result in financial damage. It’s obvious criminals have taken notice — the recent activity was linked to Snowflake, but all SaaS providers and other organizations that house business-critical data for organizations are at risk.
What can defenders do?
The solution to this problem isn’t going to sound novel, in fact it's going to sound quite familiar. Primarily, anywhere critical data is housed, it needs to be protected with MFA. Organizations should conduct audits of all external data houses and ensure that the vendor supports MFA, and that MFA has been configured along with whatever logging capabilities are available, specifically associated with authentication.
The next thing organizations need to do is acknowledge and act on infostealer infections with urgency. Once an infostealers is detected, assume that all credentials on that system have been compromised, work quickly and effectively to remediate by resetting the passwords, remembering this spreads far beyond just the enterprise itself. Speed is of the utmost importance, as high-value credentials will be sold and actioned quickly. The goal is to make sure that whoever purchases the credentials cannot access critical data. Additionally, ensuring your users have a vetted and trusted way to store passwords is critical. By having an approved mechanism, you avoid credentials ending up stored in web browsers and easy picking for infostealers.
In a perfect world, we’d expect MFA to be deployed everywhere, but that’s not realistic. For instances where MFA cannot be deployed, there are a couple mechanisms to increase security and protection. If possible, limit the access of these accounts to the absolute least privilege. If internal assets are going to be accessed, look at deploying jump boxes. This creates a single point of connection where increased scrutiny can be applied. All non-MFA protected accounts should have increased visibility and all security alerts generated from these accounts should be investigated quickly and effectively.
As attackers continue to shift focus to the data they are trying to steal organizations need to take an honest look at where this data is housed and what data protections are in place to ensure you don’t end up in the headlines for stolen data being sold to the highest bidder, even if that bidder is the compromised organization itself.
