For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments.
Commodity malware was the top observed threat this quarter, a notable development given the general decrease in observations of attacks leveraging commodity trojans in CTIR engagements since 2020. These developments coincide with a general resurgence of certain email-based trojans in recent months, as law enforcement and technology companies have continued to attempt to disrupt and affect email-based malware threats like Emotet and Trickbot. This quarter featured malware such as the Remcos remote access trojan (RAT), Vidar infostealer, Redline Stealer and Qakbot (Qbot), a well-known banking trojan that in recent weeks, has been observed in new clusters of activity delivering a variety of payloads.
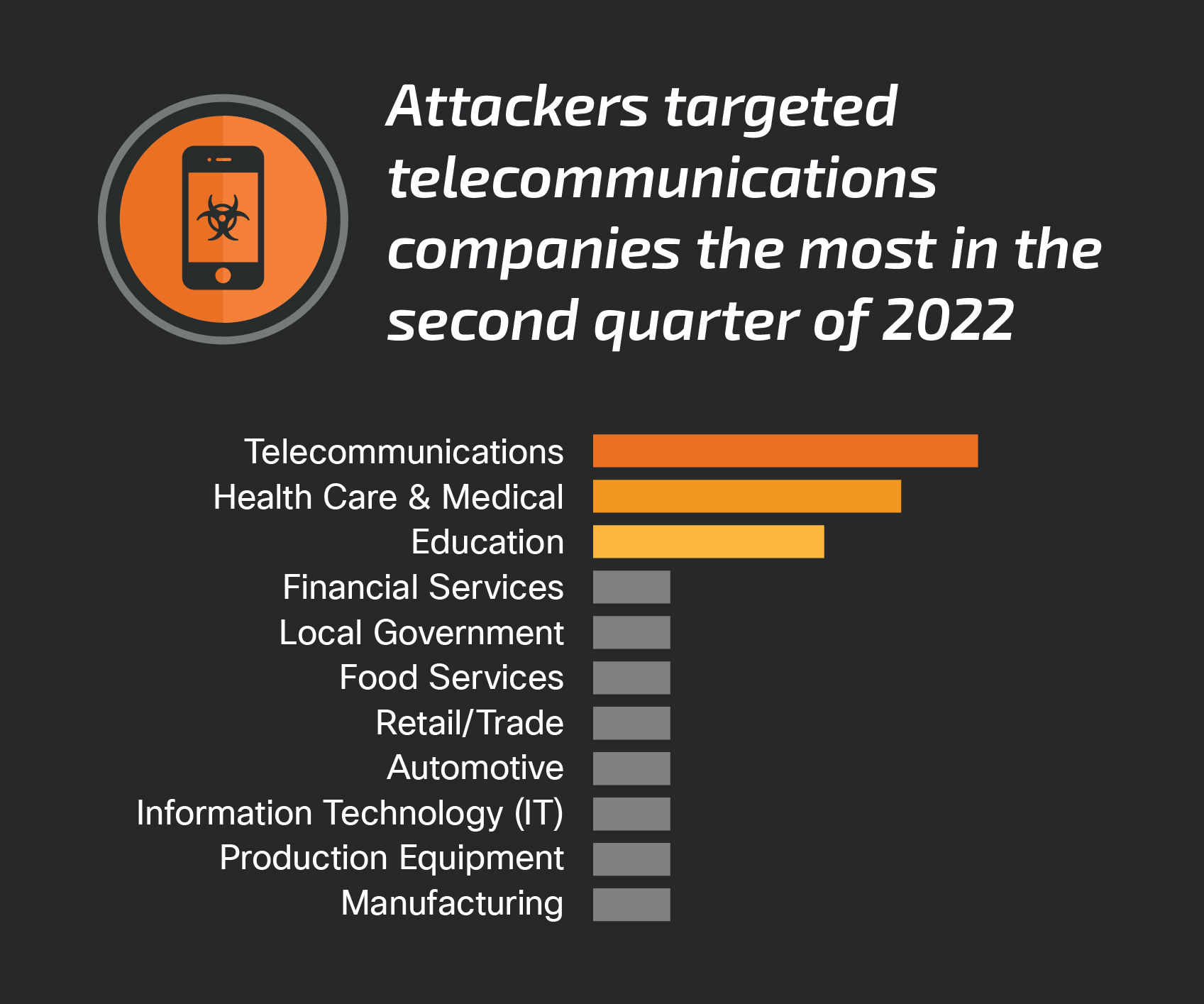
Targeting
The top-targeted vertical continues to be telecommunications, following a trend where it was among the top targeted verticals in Q4 2021 and Q1 2022, closely followed by organizations in the education and health care sectors.
Commodity malware
This quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity malware is widely available for purchase or free download, is typically not customized and is used by a variety of threat actors in various stages of their operations and/or to deliver additional threats, including many of the ransomware variants referenced below.
In one engagement affecting a U.S. medical facility, CTIR identified a malicious Microsoft Excel file (XLS) disseminated via phishing emails delivering a variant of the Remcos RAT. Active since at least 2016, Remcos records keyboard and audio inputs, captures screenshots, gathers clipboard data and much more. CTIR identified remote network connections using a systems administrator account just prior to the suspected timeframe. The aforementioned XLS contains Visual Basic code which will execute once a user opens the file and enables macros. We identified an IP address, 209.127.19[.]101, within a PowerShell command that would eventually download the next stages of the infection from URLs hosted on that IP. In March 2022, this same IP address was also reported as associated with a Remcos RAT phishing campaign, suggesting CTIR was seeing an extension of this activity using lures to entice users to open a malicious XLS file that allegedly contains confidential information.
In recent weeks, Talos observed ongoing Qakbot activity leveraging thread hijacking, a method by which threat actors use compromised email accounts to insert malicious replies into the middle of an existing email conversation. In an engagement affecting a U.S. local government, CTIR investigated three waves of phishing emails that, upon user execution, subsequently delivered the Qakbot banking trojan. All three waves of emails were constructed in two different ways: Purely spoofed content using fake emails related to tax documents and a blend of thread hijacking leveraging spoofed and legitimate email body content designed to appear to be a reply to an ongoing email conversation. CTIR noted that the legitimate content appeared to primarily be harvested from emails sent to external recipients in 2020 and 2021, which we’ll discuss in a forthcoming post. The legitimate content was partially scrubbed to remove certain email addresses within the text of the previous email messages, although at this time, the reason for this is unknown. While investigating the affected system, once the user clicked on the malicious link, a ZIP file was downloaded to the following directory, “C:/Users/<user>/Downloads”. The ZIP contained a Windows shortcut (LNK) file where the contents included a command intended to create a directory under the user profile and attempt to contact a C2 domain (bottlenuts[.]com) to retrieve a file and execute it using the Windows utility “regsvr32.exe”. While the Qakbot payload was not executed by the end user, the command line arguments and C2 domain are consistent with a recent publicly reported Qakbot campaign, suggesting that this is part of the same activity.
CTIR observed several information stealers this quarter, where in both incidents, MFA was not properly applied across the organization and their third parties. In one engagement, CTIR identified the Vidar information stealer affecting a telecommunications company based in the Philippines. First identified in 2018, Vidar is typically installed through spam emails and adware and potentially unwanted programs (PUPs). In this case, CTIR could not determine the initial access vector due to a lack of logging. However, the affected organization reported that the compromised victim did not have proper MFA applied.
In a similar series of events, in a Redline Stealer engagement, CTIR investigated widespread adversary MFA authentication accessing the victim’s O365, Workday and Citrix VDI environments. Adversary authentication followed two successful phishing attacks designed to collect usernames, passwords and up to two hashed one-time passcodes (HOTPs). First discovered in 2020, the Redline Stealer is sold on Russian language forums and messaging platforms such as Telegram and has become increasingly popular in its role as a primary and/or secondary payload supplementing activity associated with other malware.
Ransomware
Ransomware continued to be a top threat affecting Cisco customers. Of the ransomware engagements CTIR supported, this quarter featured previously seen high-profile ransomware-as-a-service (RaaS) variants, such as BlackCat (aka ALPHV) and Conti.
In a BlackCat ransomware engagement affecting a U.S. telecommunications organization, the ransomware was effectively blocked and did not execute in the environment. However, through the course of the incident, CTIR analyzed artifacts determined to be instances of Cobalt Strike with a Delphi loader capable of performing Mimikatz memory-dumping operations. CTIR observed two malicious domains that redirected to known Cobalt Strike IP addresses. Notably, one of the domains, standwithukraine[.]space, appears to be a reference to the ongoing Russia-Ukraine war. CTIR also detected numerous file downloads for Impacket’s Secretsdump module (“secretsdump.exe”) that performs various techniques to harvest credentials. While the appearance of the Delphi loader is not novel, BlackCat joins other ransomware groups, including REvil/Sodinokibi that have been reported leveraging the Delphi loader to run a Cobalt Strike binary.
In a Conti ransomware incident affecting a health care organization with locations across the U.S., Europe and the Middle East, CTIR observed a Conti affiliate exploiting Log4Shell (CVE-2021-44228, CVE-2021-45046, and related vulnerabilities) on a vulnerable VMware Horizon server, consistent with public reporting on Conti leveraging Log4Shell from December 2021. After establishing initial access, CTIR observed Cobalt Strike beaconing, system enumeration and unauthorized installation of remote access tools such as AnyDesk. The adversary then established persistence with the unauthorized creation of a local admin account and attempted to escalate privileges by modifying security-enabled group settings, service installation, disabling user accounts, accessing Windows Vault credentials, and resetting user passwords. For lateral movement, the adversary connected to IPC$ network shares and accessed a compromised host via remote desktop protocol (RDP). As discussed in the previous quarter, Conti is among the many threat actor groups leveraging Log4Shell as a means of initial infection, and we will likely continue to see threat actors adopting this exploit into their tactics, techniques and procedures (TTPs).
Interestingly, in May 2022, Conti first announced it was ceasing operations, and by June had taken much of its infrastructure offline, including Tor servers used to leak data and negotiate ransom payments with victims. As the effects of Conti shutting down are still unknown at this time, a relatively new RaaS variant dubbed “Black Basta'' is a suspected re-brand of Conti, based on similarities in payment and leak sites and communication styles from some of its members. Black Basta, while unseen in incident response engagements thus far, began operating in mid-April 2022 and is gaining notoriety by leveraging the aforementioned Qakbot banking trojan to move laterally on compromised devices.
Initial vectors
This quarter also featured several engagements where adversaries identified and/or exploited misconfigured public-facing applications. This includes active scanning, exploitation of public-facing routers and servers, and leveraging Log4Shell in vulnerable applications, such as VMware Horizon.

In one engagement, an IT company with operations in Europe had a misconfigured and accidentally exposed Azure server. An adversary had attempted to remotely access the system before it was isolated. The system was alone in its subnet but connected to other internal resources via an IPSec VPN tunnel, a common VPN protocol used to establish a VPN connection. Analysis identified multiple failed login and brute force attempts from various external IP addresses, highlighting the need to update and limit exposure to prevent unwanted traffic from reaching the application.
Security weaknesses
The lack of MFA remains one of the biggest impediments to enterprise security. In at least two engagements this quarter, the affected organization’s partner or third party did not have MFA enabled, allowing the adversary to gain access and authenticate into the environment. CTIR recommends that organizations ensure all third parties in the environment are following MFA security policies and guidelines.
In the Remcos RAT engagement, CTIR identified that domain users had local administrator rights across the environment. This makes it easier for an adversary to exploit Active Directory and move laterally around the network.
Top-observed MITRE ATT&CK techniques
Below is a list of the MITRE ATT&CK techniques observed in this quarter’s IR engagements. Given that some techniques can fall under multiple tactics, we grouped them under the most relevant tactic in which they were leveraged. The table below represents the techniques used with a relevant example, and the approximate number of times seen. However, it is not an exhaustive list.
Key findings from the MITRE ATT&CK appendix include:
- Adversaries leveraged valid accounts, achieved via techniques such as brute force, for initial access and persistence in several engagements this quarter.
- In line with last quarter, we continue to observe email-based threats leveraging a variety of social engineering techniques to entice users to click or execute a given link or file.
- We continue to see a variety of threats identify or exploit misconfigured or unpatched and vulnerable public-facing applications.
- Attackers use multiple techniques associated with credential harvesting tools and utilities, such as Mimikatz and Impacket, to obtain account and password information. The observed collection techniques exhibited the actors’ interest in specific information, including collecting details from Active Directory to harvest credential information about domain members.
| Tactic | Technique | Example |
|---|---|---|
| Initial Access (TA0001) | T1190 Exploit Public-Facing Application | Attackers successfully exploited a vulnerable application that was publicly exposed to the Internet. |
| Reconnaissance (TA0043) | T1592 Gather Victim Host Information | Malicious file contains details about host |
| Persistence (TA0003) | T1053 Scheduled Task/Job | Scheduled tasks were created on a compromised server |
| Execution (TA0002) | T1059.001 Command and Scripting Interpreter: PowerShell | Executes PowerShell code to retrieve information about the client's Active Directory environment |
| Discovery (TA0007) | T1087 Account Discovery | Use a utility like ADRecon to enumerate information on users and groups |
| Credential Access (TA0006) | T1003.001 OS Credential Dumping: LSASS Memory | Use “lsass.exe” for stealing password hashes from memory |
| Privilege Escalation (TA0004) | T1574.002 Hijack Execution Flow: DLL Side-Loading | A malicious PowerShell script attempted to side-load a DLL into memory |
| Lateral Movement (TA0008) | T1021.001 Remote Desktop Protocol | Adversary made attempts to move laterally using Windows Remote Desktop |
| Defense Evasion (TA0005) | T1027 Obfuscated Files or Information | Use base64-encoded PowerShell scripts |
| Command and Control (TA0011) | T1219 Remote Access Software | Remote access tools found on the compromised system |
| Impact (TA0040) | T1486 Data Encrypted for Impact | Deploy Conti ransomware and encrypt critical systems |
| Exfiltration (TA0010) | T1567.002 Exfiltration Over Web Service: Exfiltration to Cloud Storage | Actor exfiltrated data to file sharing site mega[.]nz |
| Collection (TA0009) | T1114.003 Email Collection: Email Forwarding Rule | Adversary used a compromised account to create a new inbox rule to place emails in a folder |
| Software/Tool | S0029 PsExec | Adversary made use of PsExec for lateral movement |