The cybersecurity industry tends to focus on extremely large-scale or sophisticated, state-sponsored attacks. Rightfully so, as it can be the most interesting, technically speaking.
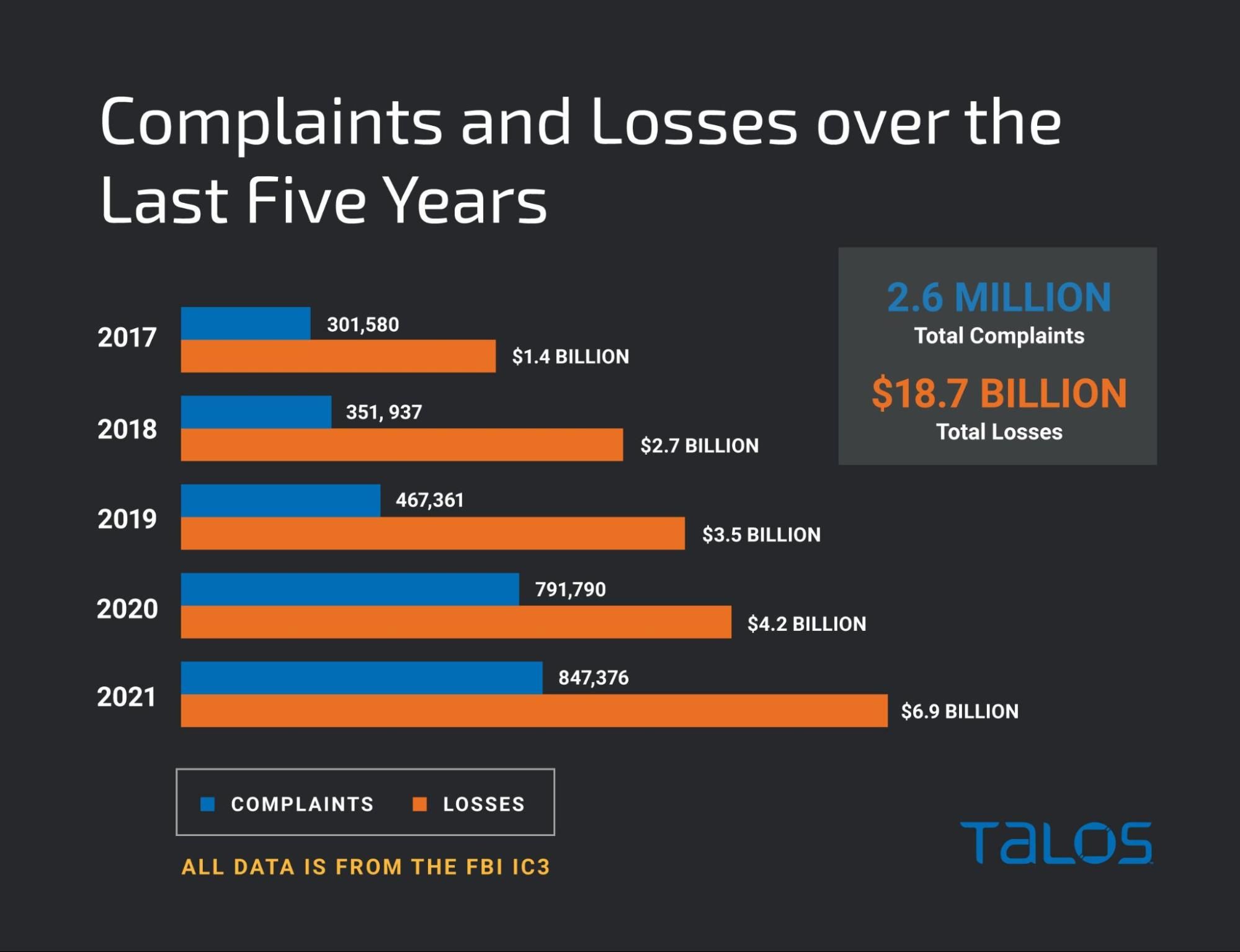
When most people think of cybercrime they think of large-scale breaches because that’s what dominates the headlines. However, the problem is much bigger. In 2021, the Internet Crime Complaint Center (IC3) received a staggering 847,376 complaints, with each victim losing a little more than $8,000 on average. Once you account for the high-value breaches, the true impact is even lower. The average person is far more likely to have their identity stolen or fall victim to some other sort of scam than be directly affected by a large-scale breach — and business is booming.
A deeper look at the data from IC3 shows that the amount of complaints and revenue being generated from cybercrime continues to rise. Interestingly there is a huge jump in cybercrime during the pandemic with a staggering increase of more than 60% in complaints between 2019 and 2020, with it increasing further in 2021. It's clear that cybercrime is on the rise, but what’s driving it?
There have been a variety of reports that criminals are turning increasingly to cybercrime instead of traditional drug crimes, with which they were commonly associated in the past. This is both a blessing and a curse — it removes a lot of violence and crime from the streets but is adding a significant amount of pressure on local law enforcement. This is an international problem. Several recent reports highlight that this is also an issue in Italy and Spain.
There are cybercriminals everywhere and the U.S. is no exception. What's changed is who is involved. Historically, cybercrime was considered white-collar criminal behavior perpetrated by those that were knowledgeable and turned bad. Now, technology has become such an integral part of our lives that anyone with a smartphone and desire can get started in cybercrime. The growth of cryptocurrencies and associated anonymity, whether legitimate or not, has garnered the attention of criminals that formerly operated in traditional criminal enterprises and have now shifted to cybercrime and identity theft.
Cybercrime is a local law enforcement problem
For cybercrime to get the attention of national law enforcement, it needs to rise to a certain level. In most cases, that means the monetary value of the crimes. Effectively, a criminal needs to steal a lot of money to get the attention of the FBI or other national law enforcement agencies — and criminals know it. The majority of the cybercrime street criminals are operating in doesn't garner the attention of national law enforcement, since it's much easier to cash out a small payday than it is to cash out large lump sums of cash. A criminal can walk into a big box store and buy a couple hundred dollars worth of gift cards using a stolen credit card relatively easily. Trying to cash out the $100,000 in Bitcoin they just stole in a scam is much more challenging.
The wave of cybercrime that's coming isn't going to be targeting huge multinational corporations looking for millions of dollars, it's going to scam folks out of their tax return or sign them up for fraudulent unemployment benefits. One thing that might become increasingly popular is the return of identity theft and associated credit card fraud. Ransomware cartels dominate the headlines with the tens or hundreds of millions of dollars they are taking in, but it's the low-level criminal compromising those around you that will be an urgent challenge in the months and years ahead.
Quantifying criminal activity presents challenges with interesting results
The IC3 data clearly shows that cybercrime is on the rise, but can it be correlated with a decrease in other forms of crime, or is it net-new bad actors? When initially looking at this topic, we were curious if there are trends pointing to reduced crime rates in some categories. The thought is that as more criminals move into cybercrime, we would see reductions in other types of crime. However, not all crime is created equal, and the challenge becomes, “How do you compare criminal behavior?” We started looking at the types of felonious crime that are commonly prosecuted in America and there were two big buckets of potential crossover criminals: violent crime and drug crime. We decided to focus specifically on felony drug crime since both drug and cybercrime tend to be non-violent offenders but wanted to include the violent crime landscape to see if there have been any noticeable shifts.
Being in a pandemic means we needed to look at a larger dataset extending beyond the pandemic, as some of the data could be skewed. Granular data on crime isn't widely available, but some of the larger police departments in the U.S. do publicly expose some of that data, most notably the New York Police Department. These larger cities are often considered a bellwether for the way the country as a whole will shift in the months and years ahead.
The NYPD breaks out data in a variety of categories, including various types of felonies. We focused specifically on the non-seven major felony offenses that included felonies for drugs and weapons. To avoid biased data from the pandemic, we began looking at the data beginning in 2013 and ending with the end of 2021, as the 2022 data is still being gathered. The resulting data paints a pretty clear picture of how crime has changed in the past eight years.
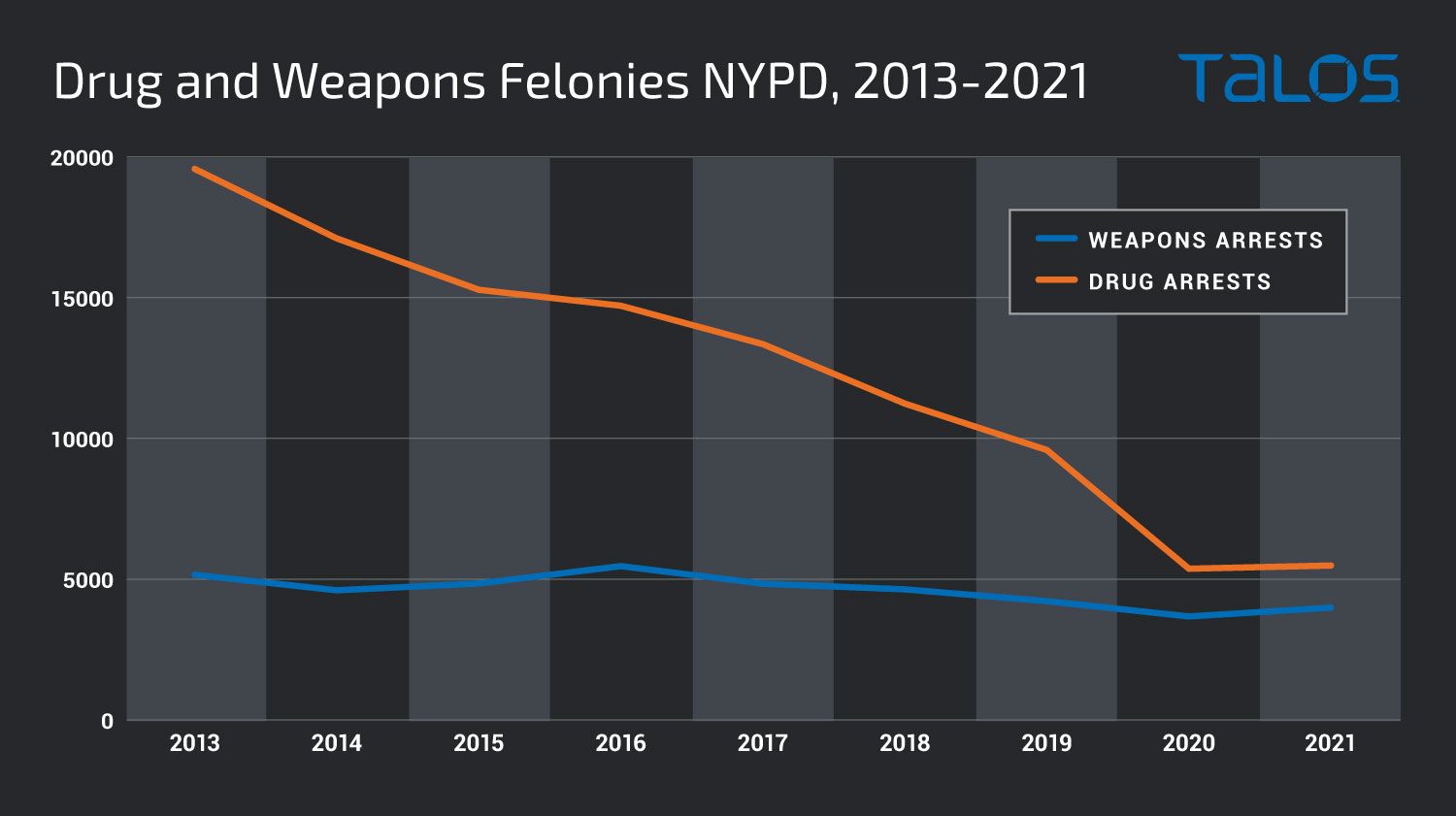
Clearly, the amount of drug felonies over the past eight years has dropped off drastically before stabilizing during the pandemic. Interestingly, over the same period, the amount of weapons-related felonies has stayed largely static, with small shifts from year to year. The question then becomes, “Did a large number of people decide to stop committing crime or have criminals moved into different criminal ecosystems?”
It seems unlikely that we would see this significant dropoff in drug crime, especially as the percentage of people abusing drugs hasn't likewise dropped significantly. It's important to note that shifts in cannabis laws may have affected the number of arrests, but cannabis wasn't fully legalized in New York state until March 2021.
Additionally, initial data indicates that some crimes including murder, assaults, robberies and grand larceny thefts are decreasing. Major cities in the U.S. reported decreases in said crimes between 30% and 42% following the implementation of stay-at-home orders due to COVID-19. Although the problem may have been exacerbated during the pandemic, it's been around a lot longer.
A recent Forbes article notes that this behavior is a trend that started about a decade ago but has since begun to accelerate. Street gangs are moving away from drugs and toward fraud fueled by cybercrime in the U.S. and around the world. These criminals can operate in two different modes: one where they are actively gathering the data which can require specific expertise in technology, hacking, and malware or the data can just be bought. There are numerous forums where enterprising criminals can buy stolen data including names, addresses, social security numbers and other relevant information required to commit fraud and identity theft. Then, the issue is just monetizing it, and business is booming.
The fact that it is typically a smaller monetary crime makes it easier to accomplish. From a criminal’s perspective, it's far easier and safer to take a stolen credit card and buy a $500 gift card from a big box store than it is to launder and process $10,000 stolen through similar means. The larger the denomination and the larger the scale, the more likely you are to draw the interest of federal law enforcement, who have far deeper pockets and much more sophisticated capabilities when it comes to prosecuting cybercrime. The pandemic has introduced additional avenues of fraud that criminal gangs have capitalized on, including COVID-19 relief funds and associated unemployment benefits fraud. In addition to the increases in available funds, the application processes were moved online to ensure the health of those involved, a boon for would-be criminals. Combining these with the already ongoing fraud and identity theft crime and the amount of money these groups are obtaining is significant.
Law enforcement challenges lie ahead
This brings us to the organizations tasked with bringing this new wave of cyber criminals to justice: law enforcement. However, since the majority of this crime is small time, the majority of the responsibility is going to fall on local law enforcement instead of state or federal agencies that tend to cover more significant financial crimes. Unfortunately, that benefits the criminals in some ways. Local law enforcement has many challenges they face daily, including drug and violent crime, to which they are highly trained. These types of arrests can be dangerous and require a very specific skill set.
Cybercrime, on the other hand, is a completely different type of problem to deal with. Instead of breaking down doors and dodging gunfire, law enforcement officers are pouring over data from the criminal themselves and the organizations/people they target with their fraud, trying to tie together transactions to build a solid, forensically sound case.
The real challenge lies in how to effectively deal with these two problems that require completely different skills. This is the dilemma that local law enforcement departments face in the coming years. As we are all aware, information security professionals are highly sought after and can demand significant compensation, and training existing law enforcement officers on how to build cases of cybercrime can be challenging.
Law enforcement can take some cues from private industry here. One trend we are increasingly seeing to address the security talent shortage is to look elsewhere in your organization for those with a penchant for security and the investigative drive necessary to succeed. There are ample investigators inside police departments, look for those with skills in online-based investigations and leverage them for cybercrime in the future.
Additionally, looking to the youth in your community could be another powerful resource for building a talent pipeline. Building relationships with existing computer science programs or high schools in the area to identify this talent could be a great resource. We're already seeing this applied around the world. For instance, in the UK, an investment of seven million pounds in a single year helped lead to the creation of cybercrime units in every police force in England and Wales.
There aren't any easy answers here, but likely will require a shift in the way we handle policing in the future. As more criminals begin to hide beyond keyboards and phones, away from the streets, traditional law enforcement is going to have challenges and what may initially appear to be a reduction in certain types of crime may be accompanied by a similar spike in fraud and cybercrime that isn't as easy to quantify. The future of policing is going to require an increased ability to identify and prosecute more high-tech crime, while still maintaining control over potential drug and violence issues in the jurisdiction.
Conclusion
As we've seen repeatedly over the years, we don't typically see new types of crime, just crime taking new forms. The world today is run by technology and it is becoming an ever-increasing part of our lives, as such, criminal activity is bound to increase. Criminals may seem like they are just out to commit crimes, but in reality, most criminals are choosing to live a life of crime to support themselves and their families. They, like anyone else, are familiar with risk assessment and now it may make more sense to commit crime with a keyboard instead of selling drugs as the risks are lower across the board. It's a lot less likely to draw immediate law enforcement response and there typically aren't turf wars in cyberspace and if they are they tend to be less violent. Furthermore. the margins in cybercrime are significant and in the end the goal is to make as much money as quickly as possible: technology is the key to scale and speed.
Law enforcement, especially at the local level, is going to need to evolve along with the criminals as they are tasked with protecting the general public. The future criminal is going to be aware of operational security and technologies like Tor to make their arrests increasingly difficult. The time is now to start building the capabilities into police departments to be able to handle the shift that has already been happening for a decade but is poised to explode, as people have been locked away for several years during the pandemic. The question becomes — how did criminals make use of that time?
Coverage
Ways our customers can detect and block this threat are listed below.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following Snort SIDs are applicable to this threat: 59145, 59160, 59500 and 59501.
Orbital Queries
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click here and here.
Indicators of Compromise
Indicators of Compromise associated with this threat can be found here.