Cisco Talos Incident Response (CTIR), as with everyone else in the cybersecurity world, dealt with a bevy of threats last year, as responders dealt with an expanding set of ransomware adversaries and several major cybersecurity incidents affecting organizations worldwide, all under the backdrop of the global pandemic, which brought its own set of cybersecurity challenges. In lieu of the regular incident response quarterly trends blog this quarter, this report will look at trends that emerged throughout 2021. Our findings reveal that:
- Health care was the most targeted industry vertical for the vast majority of the year.
- Ransomware was the clear top threat throughout 2021.
- The most commonly observed initial vectors included exploitation of internet-facing applications and phishing attacks.
- CTIR dealt with four major security incidents:
- The SolarWinds supply chain attack.
- Mass exploitation of Microsoft Exchange Server vulnerabilities.
- REvil’s attack against IT solutions provider Kaseya.
- The discovery of the Log4j vulnerability.
Of these four, the Microsoft Exchange vulnerabilities appear to be the most impactful for CTIR customers so far, as we have continued to see incidents leveraging Exchange this Winter.
Targeting

Health care was the top targeted vertical throughout the majority of 2021, with the only exception being the Fall, in which the top targeted vertical was local governments. We anticipated that health care would continue to be a top target throughout 2021 after a spate of ransomware adversaries targeted the industry in late 2020. The main reasons adversaries are continuing to target this industry is due to health care providers’ often underfunded cybersecurity budgets and extremely low downtime tolerance, the latter of which has been exacerbated by the ongoing COVID-19 pandemic.
Threats
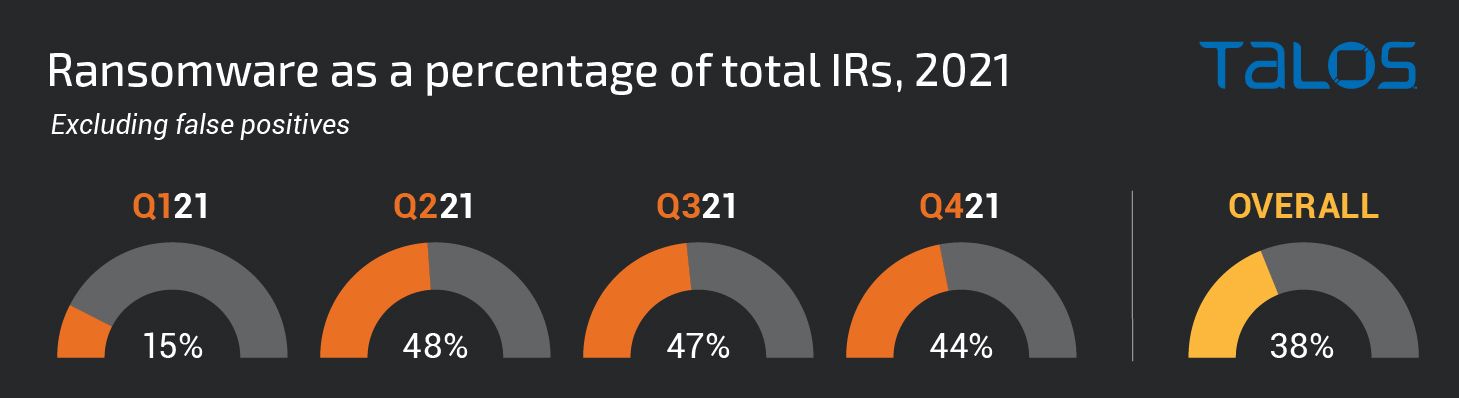
Ransomware dominated the threat landscape in 2021. We observed two trends emerging throughout 2021 in ransomware engagements: A proliferation of adversaries and an increased reliance on commercially available and open-source tools.
Throughout 2020 and in the beginning of 2021, Ryuk was the primary ransomware family observed throughout numerous engagements. As the year went on, however, Ryuk began to gradually disappear and has not been observed in either of the past two quarters. Ryuk was not the only ransomware family to quiet down in 2021. Darkside, BlackMatter, REvil, and Maze all recently ceased operations or were rebranded, as well. Potentially in response to the decline of some of these ransomware giants, we have observed a greater variety of actors culminating in this Winter in which no one family was observed more than once.
Besides the proliferation of ransomware actors starting around the Fall, we also saw an increase in usage of commercially available tools, open-source tools, and living-off-the-land binaries (LoLBins). Some of the most commonly observed included:
- Cobalt Strike
- ADFind
- ADRecon
- GMER
- Bloodhound/Sharphound
- PowerShell
- PCHunter
- 7-Zip
- WinRAR
- Windows Management Instrumentation
- RDP
- Rubeus
- TeamViewer
Initial vectors
In 2021, as in 2020, a majority of organizations had deficiencies in logging that made it difficult to ascertain the initial vector/root cause behind a majority of engagements. However, when an initial vector could be reasonably assumed, exploitation of internet-facing applications, along with phishing, remained the top initial vectors.
The reasons behind the large amount of exploitation include the disclosure of multiple severe security vulnerabilities in software widely employed by many organizations. Of particular concern were several Microsoft Exchange vulnerabilities that led to a cluster of incident response engagements.
Meanwhile, the uptick in phishing attacks may be correlated to the fact that it is a common means of initial infection for adversaries employing ransomware, which consisted of the majority of threats throughout 2021. 2021 also saw increased business email compromise (BEC), particularly in the Fall, which also skewed initial vectors toward email.
Major security incidents
Beyond the stress of operating under a global pandemic and dealing with the ever-evolving and worsening ransomware threat, CTIR also had to contend with four major security incidents that impacted organizations globally. They included the following:
- In December 2020, there was a sophisticated supply-chain attack in which adversaries gained access to victims' networks via trojanized updates to SolarWinds' Orion software. This attack targeted numerous large enterprises and U.S. government agencies.
- In March 2021, CTIR responded to a growing number of cases involving threat activity related to several Microsoft Exchange Server zero-day vulnerabilities.
- In July 2021, the ransomware group REvil carried out an attack against Kaseya, which provides IT solutions to managed service providers (MSPs). Because REvil targeted MSPs that manage IT services for their clients, they reached at least 1,500 organizations.
- In December 2021, adversaries began scanning for and exploiting a critical remote code execution vulnerability in the popular Apache Foundation Log4j.
Of these four significant incidents, the Microsoft Exchange vulnerabilities were the most impactful for CTIR customers, comprising 35 percent of all incidents in the early Spring. Thankfully, the majority of these incidents involved scanning and not post-compromise behavior, such as file encryption or evidence of exfiltration.
While the Exchange vulnerabilities were released in March 2021, CTIR continued to observe incidents in which Exchange is leveraged by adversaries to gain initial access. In the Winter, at least three incidents involved abusing Microsoft Exchange, and in at least two of these engagements, adversaries abused the Exchange Web Services (EWS) functionality on Exchange Servers to send phishing emails internally. In the other, the adversary exploited CVE-2021-31207, the third vulnerability that makes up the ProxyShell compromise, to execute web shells and subsequently deliver ransomware.
Although we have had minimal Log4j CTIR engagements involving post-compromise or adversary activity so far, we are continuing to remain vigilant as adversaries such as Conti continue to incorporate Log4J exploits into their toolkit.
We note as well that, although these are the events that affected CTIR the most, they were far from the only major security incidents that took place in 2021. For example, the DarkSide ransomware group targeted Colonial Pipeline in May, leading to the pipeline being shut down and panic buying throughout the U.S., underscoring the threat ransomware poses to critical infrastructure.
Security weaknesses
In 2021, with the explosion in ransomware engagements, CTIR emphasized that the lack of multi-factor authentication (MFA) remains one of the biggest impediments for enterprise security. CTIR frequently observes ransomware incidents that could have been prevented if MFA had been enabled on critical services. CTIR urges organizations to implement MFA wherever possible.
Forward Looking: 2022
We assess that 2022 will likely keep our responders as busy as 2021 since the underlying factors that impacted our IR caseload will likely continue or increase. We are currently monitoring the following trends in the upcoming year:
- Log4J vulnerabilities have caused widespread concern among customers and the security community at large, though so far CTIR has not observed much post-compromise or confirmed adversary activity. However, we could easily see an increase in related incidents in 2022. As many researchers have pointed out, this incident has far-reaching implications based on Log4J’s wide use within enterprises, the difficulty some organizations might have in finding and patching everything that is vulnerable, and the already documented APTs that have begun to leverage it. We expect that many adversaries may gain access to victims’ networks via Log4J, only to lay dormant for months as they conduct reconnaissance and plan subsequent attacks, as many sophisticated threat actors often do. Therefore, while we have not seen many related CTIR engagements yet, it is likely that we will observe future incidents in which we determine Log4J was the initial infection vector.
- We believe that 2021 was a harbinger of things to come in terms of supply chain and third-party risk. When adversaries target a large MSP or open-source software incorporated into countless enterprise products, they greatly expand the potential pool of victims. CTIR expects supply chain and third-party risk to continue to pose a large threat to enterprise security, as numerous actors ranging from APTs to ransomware groups leverage these attacks to pivot to high-value targets.
- Going forward, we will be monitoring the recent revival of Emotet and whether the botnet has any new connections to ransomware operations. Some security researchers have speculated that Emotet may be used to deliver Conti, but we have yet to see this claim supported in our own IR engagements. We note that Emotet has recently been observed dropping Cobalt Strike soon after infection, which allows threat actors to more easily achieve lateral movement and deploy ransomware on key assets.
- We are also monitoring the impact of U.S. President Joe Biden’s whole-of-government approach to countering the ransomware threat, which so far has included initiatives enacted by the Treasury Department, Department of Justice, and other agencies to disrupt ransomware actor’s ability to operate. Many of these initiatives will likely have ripple effects that have yet to be seen. We suspect that as U.S. officials prioritize countering the ransomware threat, we will see groups continue to shut down operations or rebrand under new monikers, become more restrictive about members joining their RaaS ranks, and attempt to improve their operational security. In one likely related development, we are continuing to monitor some changes on underground cybercrime forums that have likely been in response to the recent law enforcement crackdown on REvil and other ransomware operators. Some forums, like XSS and Exploit, appear to be tightening their restrictions on ransomware-related sales — including deleting posts and banning users — while others, like RAMP, have explicitly stated that they will not take such actions. Such changes could impact the ransomware threat landscape in terms of the proliferation of new adversaries, ransom negotiations, and open-source monitoring of ransomware groups, particularly if U.S. officials continue to aggressively enact new measures aimed at disrupting ransomware operators, as we saw them do in 2021.


