- BEC is a multi-stage attack. Adversaries first identify targets, then they establish rapport with the victim before exploiting them for whatever their end goal is. In the case of BEC, a threat actor can impersonate any employee in the organization to trick targets.
- A policy that checks for authorized email addresses of the sender can prevent BEC attacks. However, scaling the approach for every employee in a large organization is a challenge.
- Building an executive profile based on email analysis using a machine learning model and scanning emails against that profile will detect BEC. Data collection for building and training machine learning algorithms can take time, though, opening a window of opportunity for threat actors to exploit.
- Detection of exploitation techniques such as lookalike domains and any differences in the email addresses in the "From" and "Reply-to" fields can also detect BEC messages. However, the final verdict cannot account for the threat actor’s intent.
- The intent-based approach detects BEC and then classifies it into the type of scam. It catches BEC messages, irrespective of whether a threat actor is impersonating a C-level executive or any employee in an organization. Classification based on the type of scam can help identify which segment of an organization was targeted and which employees were being impersonated by the threat actor. The additional information will further assist in better designing preventive features to stop BEC.
Business email compromise (BEC) is one of the most financially damaging online crimes. As per the internet crime 2021 report, the total loss in 2021 due to BEC is around 2.4 billion dollars. Since 2013, BEC has resulted in a 43 billion dollars loss. The report defines BEC as a scam targeting businesses (not individuals) working with foreign suppliers and companies regularly performing wire transfer payments. Fraudsters carry out these sophisticated scams to conduct the unauthorized transfer of funds.
This introduces the challenge of how to detect and block these campaigns as they continue to compromise organizations successfully. There are a variety of approaches to identifying BEC email messages, such as using policy to allow emails from authorized email addresses, detecting exploitation techniques used by threat actors, building profiles by analysis of emails, and validating against the profile to detect BEC. These approaches have a variety of limitations or shortcomings. Cisco Talos is taking a different approach and using an intent-based model to identify and block BEC messages. Before we get too deep into the intent-based model, take a deeper look at the commonly used approaches to block BEC from the simplistic through machine learning (ML) approaches.
Policy-based detection
The first place to start is with policy-based detection as it is one of the most common and simplistic approaches to blocking BEC campaigns. Let’s start by looking at an example of a BEC email.
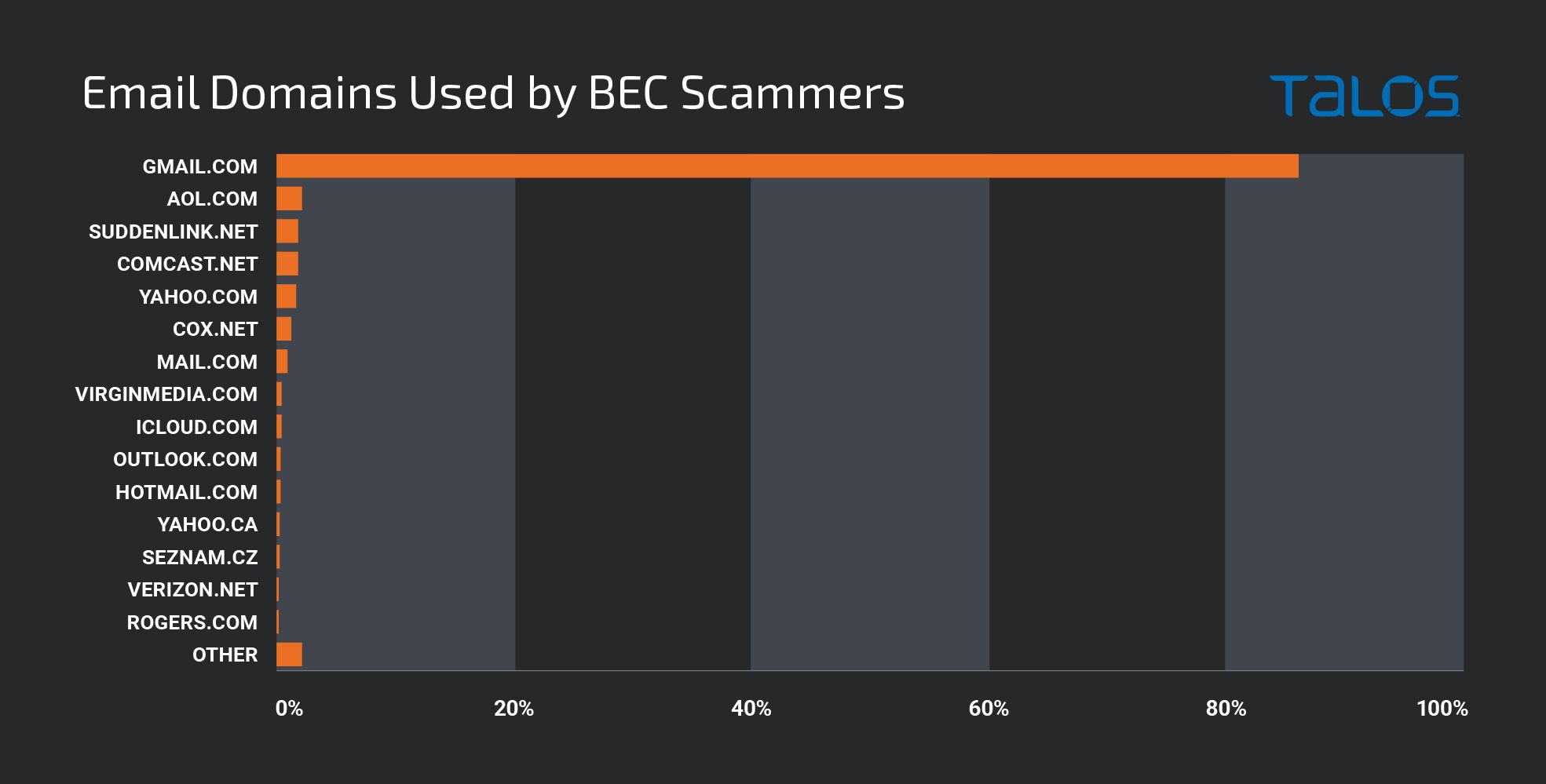
Here the actor is attempting to impersonate the CEO of an organization, but if we notice the email itself is associated with a Gmail address, obviously not the corporate domain. Threat actors commonly use free email addresses to send BEC emails.
In a policy-based approach, the names of executives and the email address from which they send emails are kept in a database. For every incoming email, a policy rule is implemented that identifies messages that contain the names of executives in the From field and which originate from outside of the tenant. If the email is not from the email address specified in the database for the executive, an alert for BEC is raised.
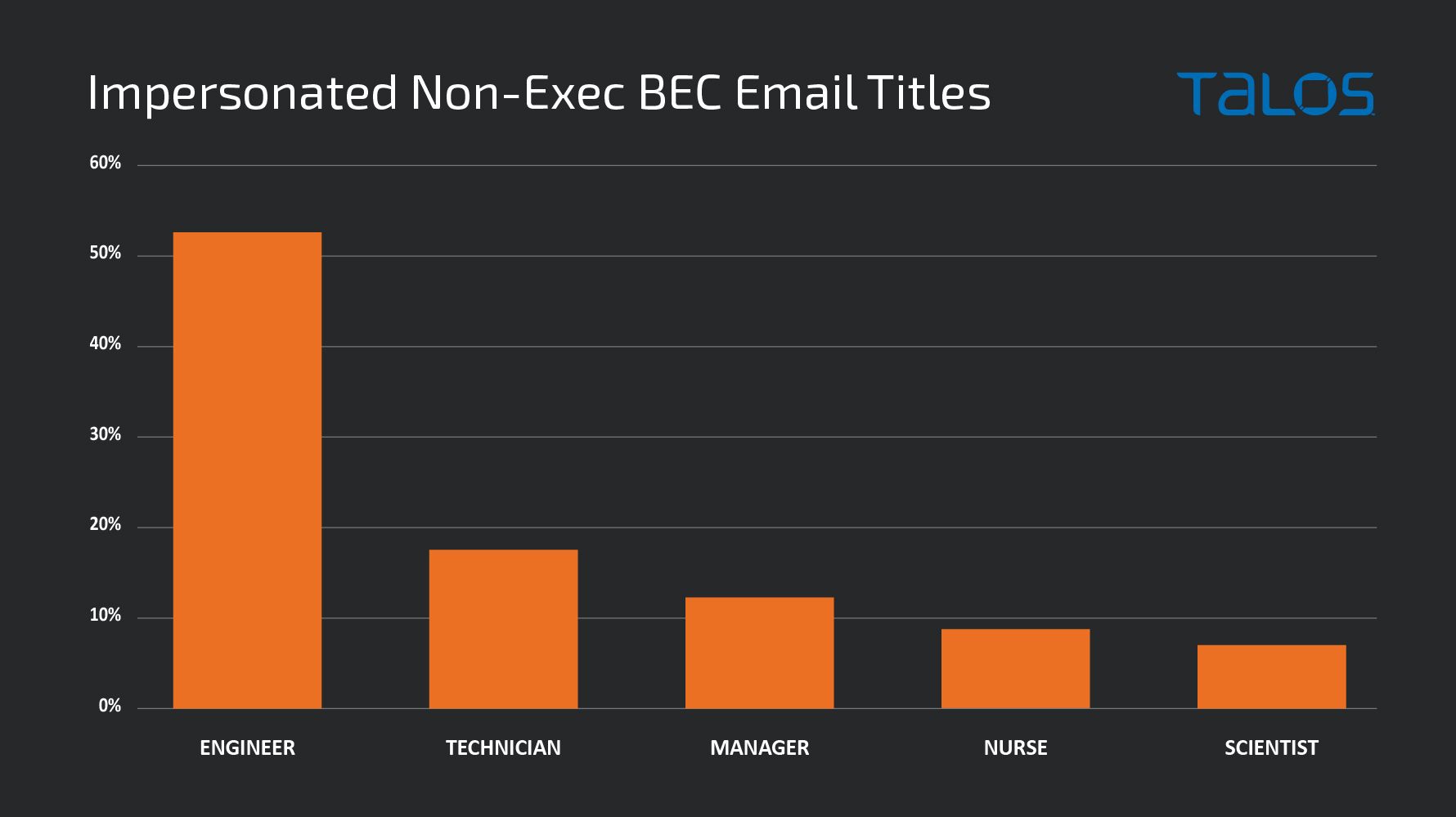
The limitation of this type of detection is that not all BEC campaigns purport to be originating from the CFO/CEO or other senior executives. The example below shows a payroll scam where threat actors were impersonating marketing managers. If the legitimate email addresses of other employees in an organization are not in the database, BEC email messages impersonating non-C-Level executives will get bypassed. Keeping the email address of every employee and vendor for a large corporation will be a challenge. The policy-based solution will stop the BEC exploitation; however, the verdict of the approach will lack the display of intent of the threat actor.
Detecting exploitation techniques
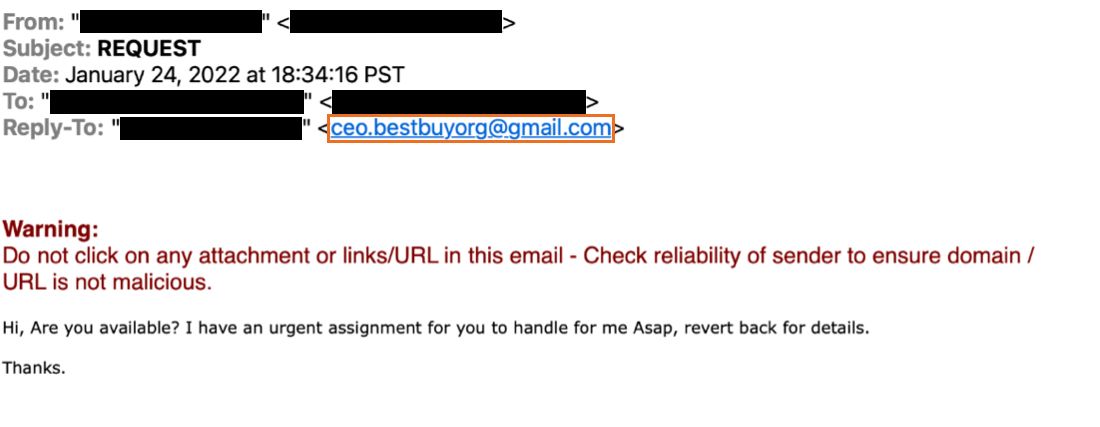
BEC emails can use exploitation techniques such as look-alike domains in the sender's email address, and the difference in the email address in the "From,” "Reply-to" fields. Some of the ways by which a look-alike domain can be constructed are brand name embedding with ('-'), brand name homograph, miss-spelled brand name, and brand name registered with an uncommon generic top-level domain. The screenshot below shows the initial lure BEC email where the email address in the “From:” field is a spoofed corporate email address, and “Reply-To:” is sent to Gmail. Any reply to the BEC email will be sent to the threat actor’s Gmail address specified in the “Reply-To” field.
These anomalies due to exploitation techniques in the sender’s email address can be aggregated with other behavior to detect BEC exploitation.
Even though the approach to detect exploitation technique will detect BEC email messages, the approach has limitations. BEC is a multi-stage attack. The first stage is to identify the target, the second stage is to establish rapport with the victim, and the third is the exploitation stage which involves instructing the victim to send money, gift card, or sensitive information. The final verdict of the algorithm will lack the intent of the threat actor. For example, in the verdict, it will not be clear whether the scam that got stopped was a payroll scam or an initial lure scam. Understanding the intent will aid in better understanding which segment inside the organization was targeted and at what stage the exploitation got stopped. The information can then be used as a feedback loop to design preventive features better.
Building a profile using ML-based model
A machine learning algorithm can be used to build a profile of C-level Executives by analyzing emails. Some of the feature sets which can be used to create profiles are writing style, activity base features such as date, time, geo-location- location from where a person is accessing emails, relations graph which will capture with whom the person interacts, etc. Every incoming email is scanned against the profile. In case of any deviation from the profile, raise an alert for BEC.
The method will detect BEC, but it has limitations. Training of the Machine Learning model will require data from real traffic. Data collection, model building, and training will take time, opening a window of opportunity for threat actors to exploit. The final verdict of the algorithm will still lack the intent of the threat actor. Threat actors can impersonate anyone in the organization for BEC scams such as payroll scams. Building the profile of everyone in a large organization will be challenging.
Intent-based approach
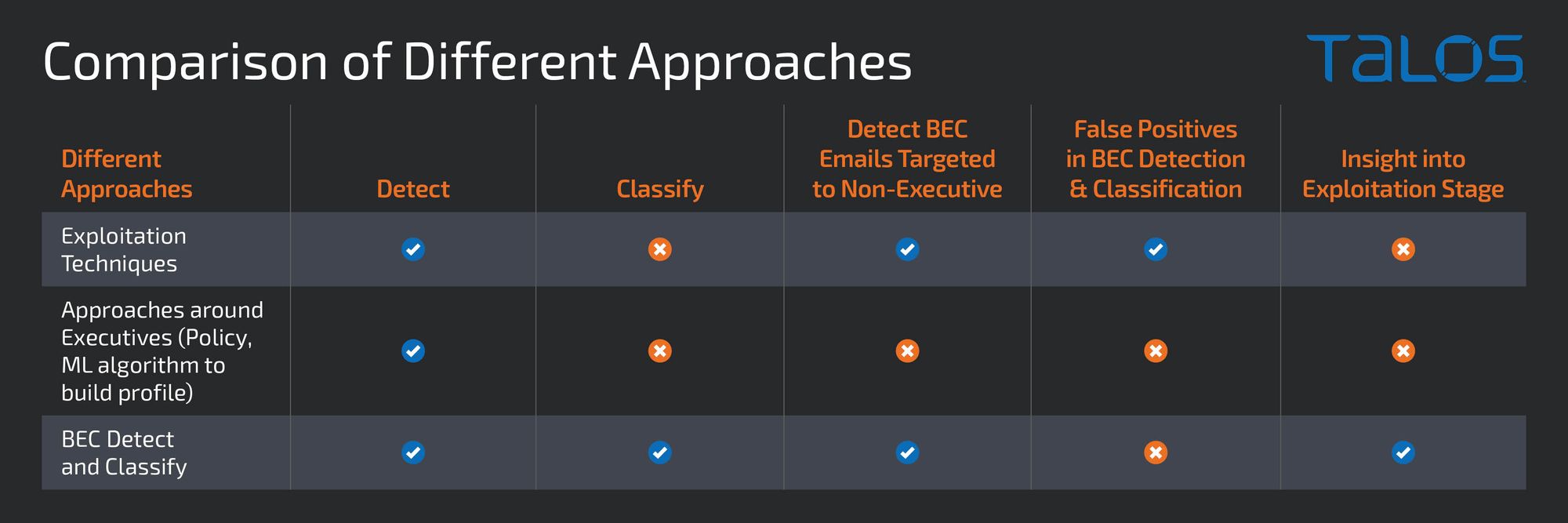
A policy-based approach to detect BEC checks for authorized email addresses; if the sender’s email address is not in the authorized list, it is dropped. The approach will require keeping the email addresses of every employee and vendor, which will be a challenge for a large size corporation. Building an executive profile based upon analysis of emails using a Machine Learning algorithm detecting exploitation techniques used by threat actors is the other approach used by threat actors. Both these approaches will lack the display of intent of the threat actor in the final verdict, and building the profile of every employee based upon analysis of emails in an organization will not be a scalable model.
To overcome the limitations of the above approaches, we designed an intent-based approach to detect BEC. The approach breaks down detecting BEC into two distinct problems, a binary class problem, which classifies emails into a BEC message, and a multi-class problem, which classifies BEC into the type of scam. So, the Intent-based approach not only detects BEC but also labels it into the kind of BEC scam, which can be Payroll, Money Transfer, Initial Lure, Gift Card Scams, Invoice Scams, Acquisitions Scams, W2 Scams, aging reports, etc. The approach involves the extraction of text from an email, converting sentences to numeric vectors by encoding the meaning of words in the sentences, using NNLM or BERT encodings, and then performing detection and classification using deep neural networks. The output of the model is a probability score. The high confidence score is used to give the verdict; the low confidence score is combined with other analytic detections to deliver the judgment of the BEC.
Intent-based approach to detect BEC provides an inherent advantage. The method will detect BEC exploitation irrespective if the threat actor is impersonating a C-Level executive or any other employee in an organization. Classification of BEC into the type of scam will aid in identifying which segment of the company is targeted. Detecting BEC at the initial lure is always much better than detecting fraudulent banking details sent by threat actors. It will also give an insight into the stage at which an exploitation attempt is being detected, which will aid in designing better preventive features. If you'd like additional help with these solutions, please contact Cisco Secure Email Threat Defense.