By Jaeson Schultz and Matt Valites.
As students return to school for in-person and virtual learning, Cisco Talos discovered an increase in DNS requests coming into Umbrella resolving domains we classify as "academic fraud." Data from Pew Research on back-to-school dates aligns with the growth we observed in queries to these malicious domains. The figure below shows that queries to academic fraud domains nearly quadrupled starting the week of Aug. 12, the most popular week to start schools in the US. When we compared these numbers with data from the same time last year, we noted an approximately 4x increase in requests for domains classified as "academic fraud." These sites have risen dramatically in popularity in 2020 as more and more students have moved to virtual learning.
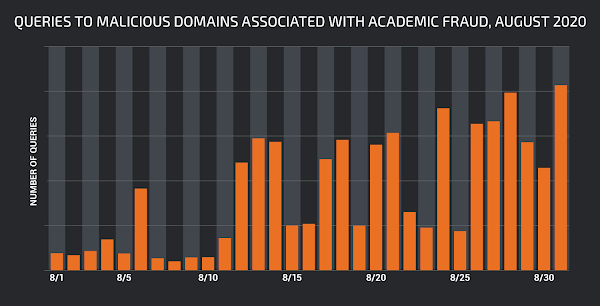
A graph of DNS requests for "Academic Fraud"-related domain names.
While unlike the other types of fraud Talos regularly deals with (phishing, malvertising, bank fraud, etc.), academic fraud does share some remarkable similarities with other types of fraud, especially social engineering. When navigating to these domains, you can never be 100 percent sure what you'll get. Users may receive the services they intend to purchase, or criminals may take advantage of these users' need for help, and in the process serve them malicious content.
As with any arms race, the more advanced scholastic cheating has become, the more advanced the methods of detecting cheating are. When students began sharing assignments, essays, and test answers online, a whole industry of "plagiarism detectors" sprang up to curb this specific type of abuse. In fact, even just the simple act of registering a domain name and putting up a website can elicit a visit from these online plagiarism detection services' web crawlers. Of course, academic fraudsters have found ways around this by paying an individual to develop brand new content. There are many websites offering services to do homework for students or even take a student's online exams. A simple Google search for the phrase "do my homework" currently yields 270 million results, and flipping through the list of search results, there are literally hundreds of different domains offering pay-for-homework and other similar services. As we discovered, not everything can be trusted when dealing with domains offering shortcuts to academic success.
A popular app Who facilitates this kind of homework-for-hire? How easy is it, and what would the results look like? To find out, Talos engaged with one of the domains we found providing these types of services — essayservice[.]com. The site is branded as "Essaypro."
Essaypro offers an app on the Google Play Store. The reviews appear to paint a positive picture of the app. It currently has 291 reviews and nearly a perfect five-star rating.
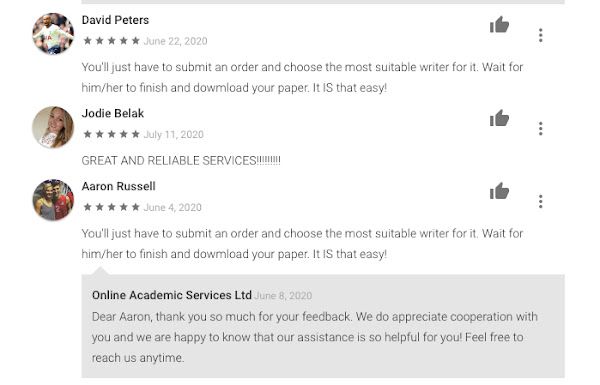
However, looking deeper at some of the app's reviews, many reviews seem a little "off." For example, on June 4, 2020, a user named "Aaron Russell" wrote, "You'll just have to submit an order and choose the most suitable writer for it. Wait for him/her to finish and download your paper. It IS that easy!" Later, on June 22, a different user named "David Peters" left the exact same review, right down to the punctuation and extra capitalization of the word "IS."
This was not the only occurrence of this type of activity. On June 4, 2020, a user named "Jayden Snyder" wrote, "You'll receive amazing results for a very affordable price. I found the best proofreader for a good price!" On June 22, a different user named "Ronald Horton" left a review with the exact same text.
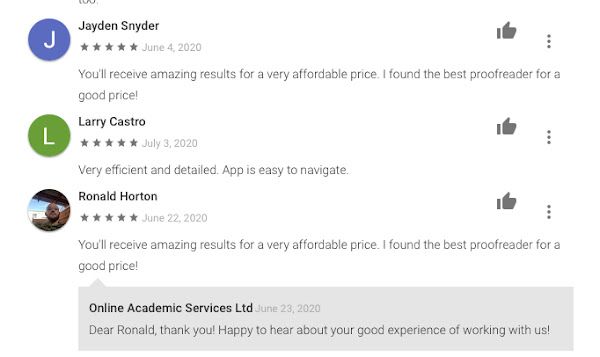
Many other reviewers leave similar themed reviews, raving about the product and the customer service, but using slightly different wording and using generic sounding names. Of course, as most developers are undoubtedly aware, astroturfing reviews to game app store placement is against the terms of service for developers on the Google Play Store.
Ordering an essay The Essaypro service also has a corresponding website. Navigating essayservice[.]com is as easy as any normal online business. Once we established a user account, there was a choice of what type of assignment we would like done, along with a schedule of approximate fees. We commissioned a four-page, PhD-level essay, which costs approximately $50.
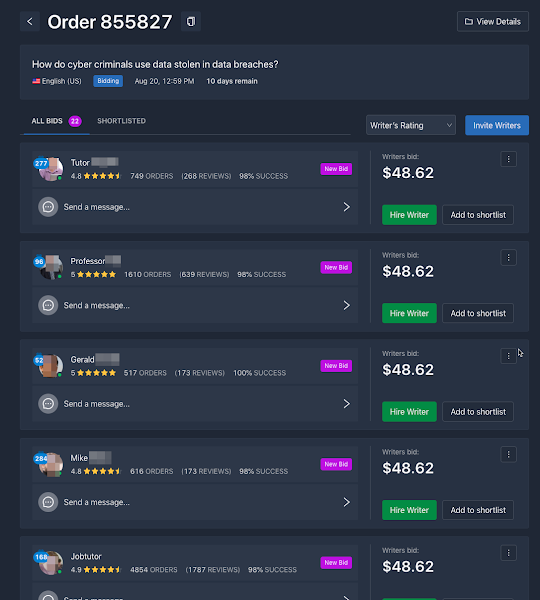
We selected our author from a list of different writers employed through the service. Each writer had a list of credentials, and even had ratings from previous customers. It seems most writers had a rating of four stars or higher, some based on more than a thousand reviews. Given our findings in the Play Store reviews for Essaypro, this seemed slightly suspicious.
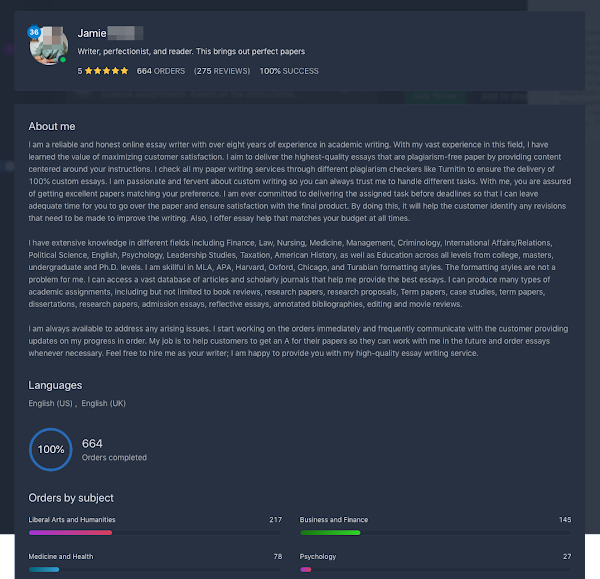
We finally selected a writer and asked them to write a paper on the following topic:
"Stolen digital data has become commonplace. Pilfered personal data can be easily found all over the Internet, including on social media networks, BitTorrent sites, and Tor onion services. Targets of information theft are not only victimized once; after their data is stolen, depending on where the information winds up, they could be victimized again and again.
Write an essay describing how cybercriminals are using information stolen in data breaches. Cite at least four breaches in your work. Discuss what data is targeted, why and how data is re-used by attackers, and any new trends in how attackers might acquire and use compromised data in the future."
The assignment was scoped to four pages in length, and due in 11 days. We messaged our selected writer in the app.
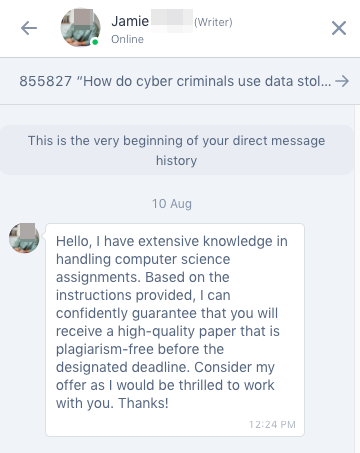
Eventually, our writer gave us the finished essay.
Despite ordering a PhD-level essay, what we ended up with was barely fit for high school. There are numerous errors in the paper, including right in the title of the essay. Many statistics and references used in the paper are quite dated. If you are a student looking to take some shortcuts to learning, be advised that these homework-for-hire services will likely not produce the grade-A content you're looking for.
No free school lunches Not all the academic fraud websites that we investigated were essay mills. Advertisers and criminals recognize the market for academic web traffic and attempt to capture clicks and views with typosquats or academic-sounding domains, such as itexamwin[.]com. Clicking on a link to this domain will route you through a malicious redirect network, a familiar malvertising technique that Talos has previously researched. Depending on your browser or operating system, you may receive a fake Flash malware dmg installer, malicious javascript with some shellcode, or any number of other malicious objects. At one point when browsing on a Mac with Brave, the browsing redirects ultimately lead us to an Amazon AWS S3 storage bucket serving a fake Flash Player.
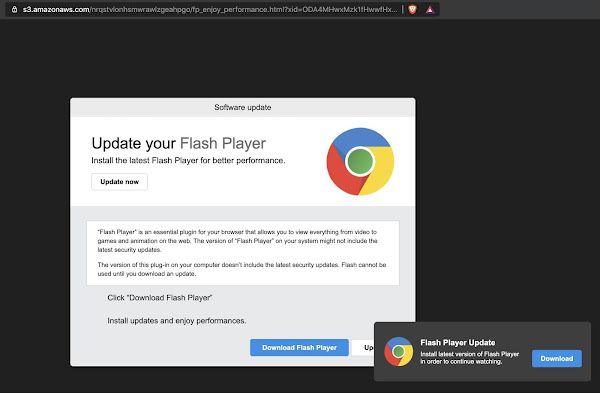
Other browser and OS combinations often led to malware such as the below malicious shellcode and JavaScript.
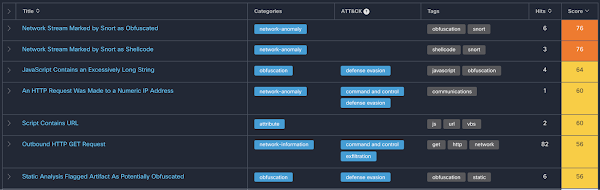
The infrastructure for itexamwin[.]com fluctuates, using at least 3 different services for name servers, and has resolved to 8 IP addresses at 4 different hosting providers in the last year alone. This frequently changing underlying infrastructure as the entry point for the redirect network is an effective technique for criminals to hide their operations.
"Our website is verified and trustful" Another fraudulent website that we observed is gceguide[.]xyz, which appears to be a clone of the original gceguide.com, a site that bills itself as the "Ultimate Resource For Cambridge Assessment International Education." Both sites contain links to hundreds of academic papers as PDFs. The .xyz version of the domain was registered in 2016, two years after the registration of the original .com domain. The similarities between their sites can be observed below.
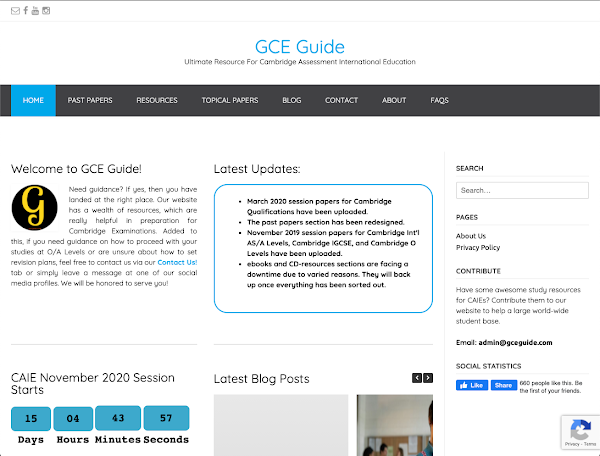
Original site - gceguide[.]com
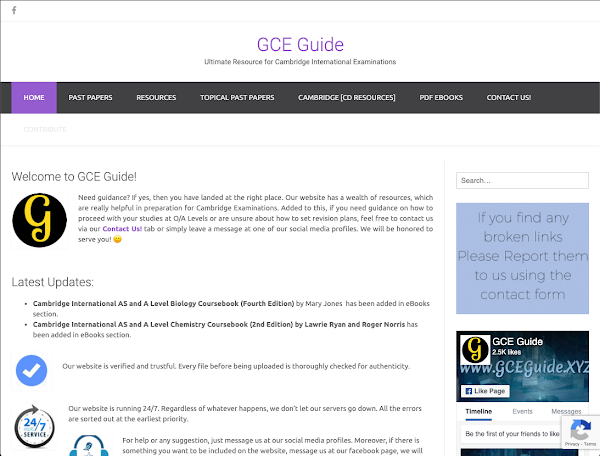
Watering hole - gceguide[.]xyz
Like their websites, both domains have also nearly identical Facebook pages, as can be seen below.
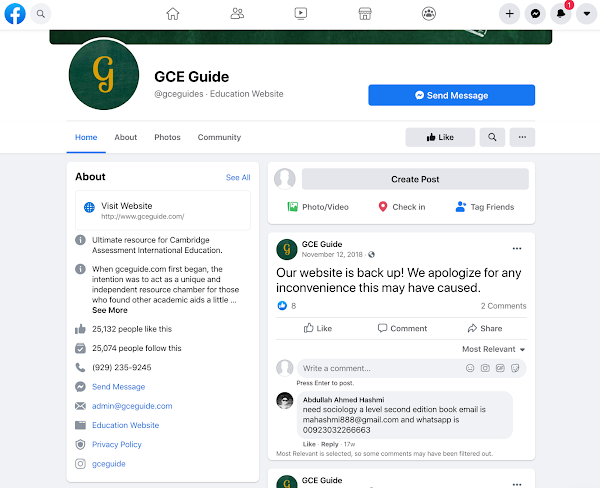
Original gceguide[.]com Facebook page
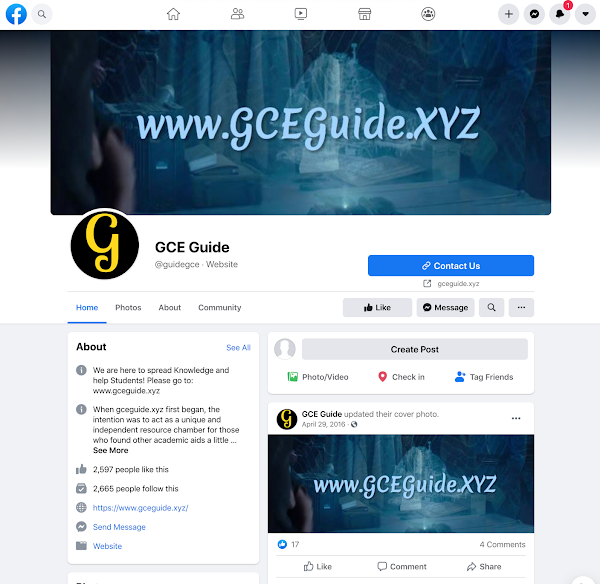
Watering hole gceguide[.]xyz Facebook page
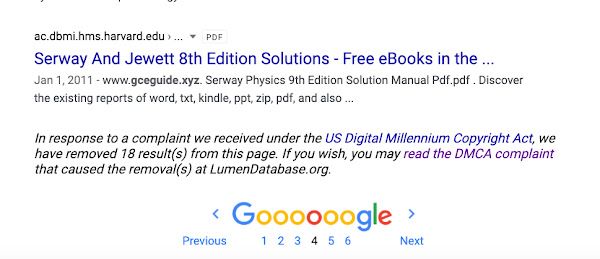
A Google search for "gceguide.xyz" shows links coming from prominent domains such as virginia.gov, ucsf.edu, and, as can be seen below, harvard.edu. Google's search results also link to a DMCA copyright takedown of several sites linked to gceguide.
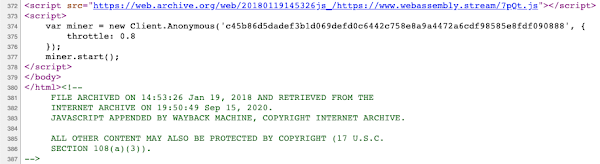
Looking closer at the "gceguide.xyz" website, it appears to have been hosting malicious content. A ThreatGrid analysis of the "gceguide.xyz" website from June 7, 2020 shows multiple antivirus hits indicating that the copycat site was hosting a cryptocurrency miner. The ThreatGrid sample shows the code used to launch a JavaScript Monero (xmr) cryptocurrency miner. A search on archive.org's Wayback Machine digital archive confirms the presence of the malicious cryptomining code, as seen in the image below. The cryptominer has been in place on this website since at least January 2018.
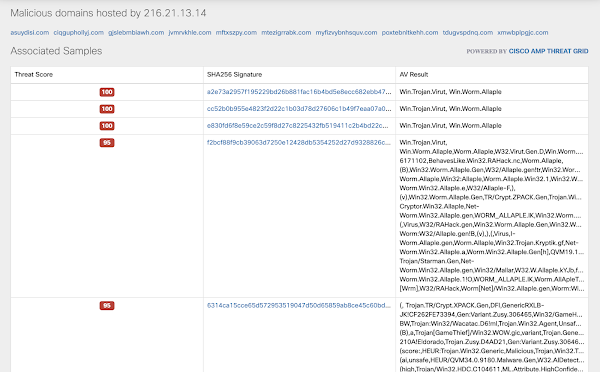
The current version of the "gceguide.xyz" website makes requests to some suspicious looking domains "ueuodgnrhb.com" and "shqbsdjatunl.com." Both of these domains resolve to 127.0.0.1 currently, but according to passive DNS, they were, as recently as July 2020, resolving to 216.21.13.14 and 216.21.13.15. Umbrella Investigate reveals a diverse collection of other malicious domains and malware samples related to these two IP addresses.
As we have demonstrated, students seeking assistance by way of these types of websites should be especially aware of the potential threats that may come bundled with the experience. In any case, endpoint protection is vital to maintaining the security of students' devices. Additionally, now that many students are sharing the same home network with their parents this creates new elements of risk that weren’t present before. Home networks are generally less secured when compared with enterprise office networks or even school networks, and this creates new opportunities for attackers.
Conclusion The COVID-19 pandemic has changed the way students attend school. In many places, they're learning exclusively online from home. Because of this, it only seems natural that some would find creative ways around doing some of their assignments. In a best-case scenario, students may cheat themselves of the opportunity to learn, and in the worst case, they may be exposing themselves to malware infection. This not only affects the student, but also has the potential to affect other users who share the local network with the student, including parents who are now working from home because of the pandemic. Having a presence on the local network could provide criminals with the proverbial "foot in the door" that they need to infiltrate a connected enterprise network and do real damage.
Blocking domains classified as "academic fraud" using Umbrella, or using other DNS security mechanisms is a prudent way to ensure you do not fall victim. Endpoint protection such as AMP can also be critical when it comes to avoiding infection in the event that a user is inadvertently exposed to malware. Above all, no matter what security technology protects you, it is no silver bullet. You must also make an effort to educate users about the pitfalls inherent in dealing with potentially hazardous websites and applications.