This blog post was authored by Jaeson Schultz.
For the past five years we have enjoyed a relatively calm period with respect to spam volumes. Back at the turn of the decade the world was experiencing record-high volumes of spam. However, with the evolution of new anti-spam technologies, combined with some high-profile takedowns of spam-related botnets, voluminous and indiscriminate spam attacks fell precipitously in popularity with spammers. Subsequently, having lower volumes of spam to contend with, anti-spam systems had the luxury of dedicating more computer processing resources to analyzing fewer messages for email-based threats. But, as the fashion industry adage goes, "everything old is new again." Spam volumes are back on the rise.
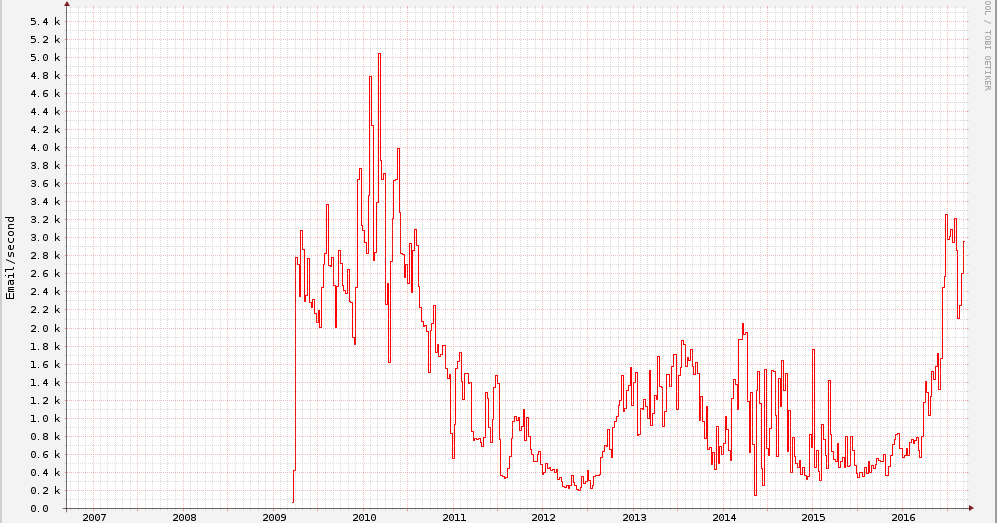
This year, 2016, has seen overall spam volumes creep back up to a level that we have not seen for a very long time. I present to you "Exhibit A": The ten year volume graph from the Composite Block List (CBL). According to CBL, the last time spam volumes were this high was back in mid-2010.
|
| An image from the Composite Block List showing total spam volumes since 2009 |
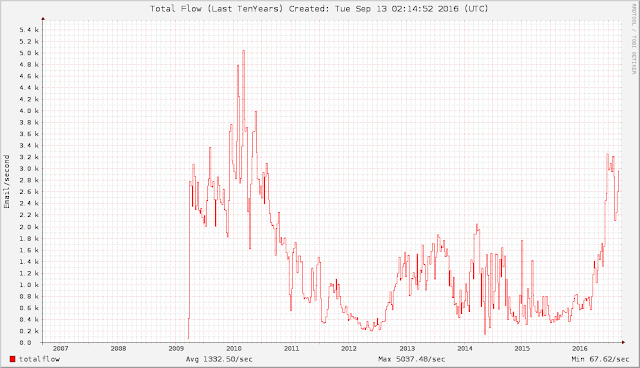
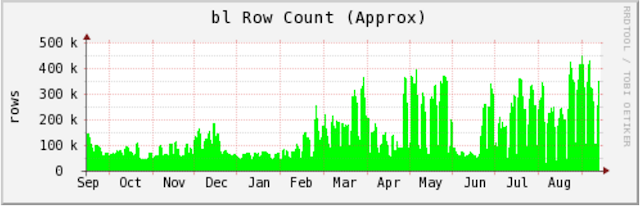
I now present "Exhibit B": An internal graph generated by SpamCop which illustrates the overall size of the SpamCop Block List (SCBL) over the past year. Notice how the SCBL size hovers somewhere under 200K IP addresses pre-2016, and more recently averages closer to 400K IP addresses, spiking to over 450K IPs in August.
|
A graph of the size of the SpamCop Block List (SCBL). Row Count == IP Count. |
Opening the Floodgates High-volume spam campaigns are typically sent by spam bots, and owing to their somewhat non-targeted/shotgun approach, these spam campaigns are very quickly caught by anti-spam systems. This being the case, then what could possibly be the advantage for spammers to crank up the volume?
We cannot predict the future and stop spam attacks before they start. Therefore, in any reasonably well-designed spam campaign there will always exist a very narrow window of time between when that spam campaign begins, and when anti-spam coverage is deployed to counter that campaign. In most anti-spam systems, this "window of opportunity" for spammers may be on the order of seconds or even minutes.
Rather than make their email lists more targeted, or deploying snowshoe style techniques to decrease volume and stay under the radar, for these spammers it has become a race. They transmit as much email as cyberly possible, and for a short time they may successfully land malicious email into their victims' inboxes.
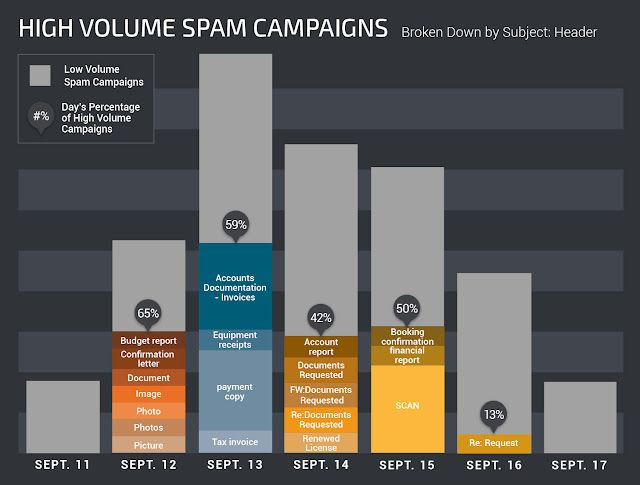
For evidence of this, we need not look very far. Analyzing email telemetry data from the past week, we can readily see the influence of these high-volume spam campaigns.
|
| Graph showing high-volume campaigns from September 11-18 |
September 12th, for example, high volume spam campaigns made up almost two-thirds of all spam sent for the day. Also take note of the lulls in activity around the weekend --the spammers seem to be taking weekends off. For these criminal professionals, spamming is their "day job".
Attribution What sinister forces are behind this global increase in spam? Cisco Talos believes the increase is largely the handiwork of the Necurs botnet.
Many of the host IPs sending Necurs' spam have been infected for more than two years. To help keep the full scope of the botnet hidden, Necurs will only send spam from a subset of its minions. An infected host might be used for two to three days, and then sometimes not again for two to three weeks. This greatly complicates the job of security personnel who respond to spam attacks, because while they may believe the offending host was subsequently found and cleaned up, the reality is that the miscreants behind Necurs are just biding their time, and suddenly the spam starts all over again. At Talos, we see this pattern over, and over again for many Necurs-affiliated IPs.
Some readers may recall when Nick Biasini from Cisco Talos blogged about arrests in Russia related to the Lurk trojan. When the arrests were made at the beginning of June 2016, many high profile threats fell silent. The Necurs spam botnet was among these (see the SpamCop graph above). However only a few weeks later, just as anti-spammers were breaking out their champagne glasses, Necurs returned. And not only had Necurs returned, but it switched from sending largely Russian dating and stock pump-n-dump spam, to sending malicious attachment-based spam. This was the first time we'd seen Necurs send attachments. The malicious attachments were propagating either Dridex, a well-known strain of banking malware, or Locky, a prolific ransomware variant.