Today, Talos is publishing a glimpse into the most prevalent threats we've observed between December 01 and December 08. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
- Doc.Dropper.Agent-6394293-0
Office Macro Downloader
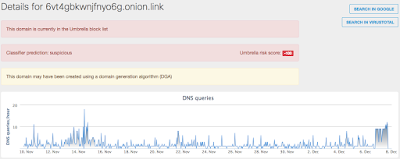
This is an obfuscated Office Macro downloader that attempts to download a malicious payload executable. The sample was unable to download the next stage so no further analysis is available. Interestingly, this sample attempts to callback using a Tor service by using the onion.link proxy service. - Doc.Macro.Obfuscation-6389653-0
Office Macro
Emotet has slightly altered the VBA macro obfuscation used to hide its obfuscated PowerShell commands. The obfuscation technique leverages a large number of unused VBA APIs relative to the overall lines of code used. - Doc.Macro.Obfuscation-6394435-0
Downloader
We have discovered another trending pattern of Valyria downloaders delivered via malicous email spam. The macro code barely resembles common VBA code at all, save for a few keywords such as AutoOpen & Shell. The bulk of the malicious downloader code is deobfuscated through a long series of cast arrays containing upper cased strings & string splitting via the Mid function. - Win.Packed.Agent-6395107-0
Malicious packer
This style of packed executable has been has been seen recently carrying Firefox credential stealers and Zuzy - Win.Trojan.CeeInject-6394235-0
Trojan
These samples contain the PoSeidon malware. PoSeidon is a Point of Sale malware which gathers credit card information. - Win.Trojan.Delf-6394424-2
Infostealer
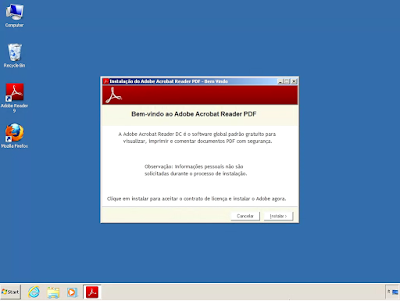
This infostealer malware family targets Brazillian users. It pretends to be an update to Adobe Acrobat Reader to steal steal data by getting access to the clipboard. It also tampers with keyboard and mouse activity - Win.Trojan.GenCNs
Trojan
This family is a classic trojan and it has a dropper behavior as well as an adware component. The samples contact many Chinese websites and other remote website. Additional files are downloaded and executed and the sample tries to inject code in another process's address space. - Win.Trojan.Tinba-6390856-0
Trojan
This banking trojan steals sensitive information from the user such as bank account login information by using man-in-the-browser attacks, web injection, or traffic interception.
Threats
Doc.Dropper.Agent-6394293-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- 6vt4gbkwnjfnyo6g[.]onion[.]link
- ypg7rfjvfywj7jhp[.]onion[.]link
- yztnv4ha5rapf6gj[.]onion[.]link Files and or directories created
- N/A File Hashes
- 0099b9221eb92408f0b8bead5d703b5c7ecb11962f49f5e67f60725427318236
- 094842414f8029ea69cca6237b7758c2559dd553c98990cb4e8474e6653e0b9f
- 0b81075cc3ef1121f3eca801d2f821719a7cfa31e5d95081ec3feb195f44d8c6
- 0e9b2c7a5526c8d469c3e2183cd52a38d862773118d2401467c59472aaf17263
- 14a415384df11be5271c58e66474cb4326aaeb4af0035afce1d61f75eaf53db3
- 2e6523b856a9f40bf3cf851407f3003a6564a7fb5d86657781a03bbd30d63966
- 365d356b6d8d463ee4d6924b37acfecf16624a58d8d2e6a783a9ef289e74ace3
- 3ac9e97344506f3e443490eb6b0d5f877e0c8d4462ab9bf9544b5128aafc78bb
- 3cae4325b4b559431dba511779feadeff19433aed194511e4ea8f4ef676ac6c7
- 3cc669528549cc7394074ac3ffbaa6cf3eed14436a1653d70f54ca2b3d5cdead
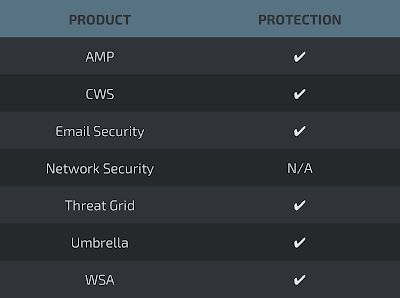
Coverage
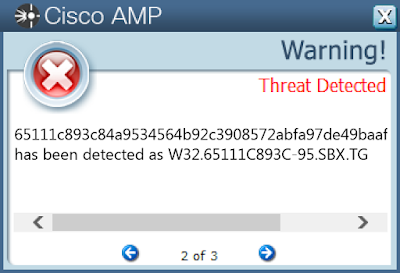
Screenshots of Detection AMP
ThreatGrid
Umbrella
Screenshot
Doc.Macro.Obfuscation-6389653-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- seoexpert4rank[.]com/yfu/
- inade[.]mx/KoSZG/
- 1000id[.]ru/JtcKoSROv/
- www[.]ra-lang[.]ch/gNFQe/
- nts-tech[.]co[.]kr/RI/ Files and or directories created
- N/A File Hashes
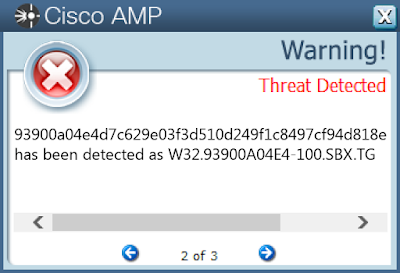
- 93900a04e4d7c629e03f3d510d249f1c8497cf94d818e0ae5913b685e467be6b
- 0a6d8c964286f1ec0173cde38caf3d5e36147945baaa83a0200e6f35f82446af
- baf01275b874c04687f84d78451e41231b31bfc0e71995e124830ba63379fedd
- 5dbf9dc9341bd506eb2cdf5ec294c6c3029535424aa0a42e9b045cbd95c6d3df
- 0f236dccbbdb81b7724f71569eff462c6fb40658f1697331617a38074a99c6e8
- d3e06e4d623b1bbf7b72ec709541c3b3fe66d09c4616c356cdc93240bd4b4c6a
- a44450c9b8514dd5647128f55d2704889c87e852e3eaceea80734ae7bf8d9f49
- 46217dc4ef9fcef981be9a931995008f56b71e3f510721c33ed4b58b577e8fbb
- 4519c2f4fc0bc43cace2e70e464c00e7302e003262d7e6f903672becaba9e8ed
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
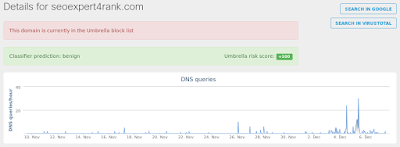
Doc.Macro.Obfuscation-6394435-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 91[.]121[.]175[.]92
- 185[.]125[.]46[.]161
- 95[.]213[.]194[.]234
- 62[.]109[.]26[.]193 Domain Names
- smart-soft[.]pl Files and or directories created
- \srvsvc
- %Public%\95857.exe
- %SystemDrive%\~$7369835.doc
- %SystemDrive%\10001.exeFile Hashes
- 1879023e70e891830300f667e1d08f5d3712d313108795c0fc2234942fc525f4
- 189f27929e2ac19501e00b9bfefddd92aed496030af4dec597d7832b38c80d84
- 2054a559d38206a764ce41fcff3a581ca6501e69ea87fc551ad57575cdbc5f04
- 33a689526403786d393a27f65e288a817fda4b2cfe2a6b153d0bcfb6eb46c2a7
- 33b2b1ff14870f1d94d70921ab347ebeedd7bc680bbaab9fa500f76f775b34cb
- 404acc127b63c29d78bef4309711b4cce103e772ec5d69d0674876f1ca38a52d
- 6591be6105ffedee758410af2d9e6ae849cae900aea514facf42642b6743a62c
- 68d539f5e356adca4d9c2c5c79839567c2d1d633a4762dc7bd84a71bd684855d
- 7364757fd07097278b46d8943e7ab7cc787db37a0ec28bf6d22fa92eae78c633
- a658d88baff44592b269b9bc64c4b69b16e44478d86a3a7cacc201be26574fa8
- af732649a7f58fc1bc8c81d513e0936c042f12342d9d6da30ff2e4f30f5a949f
- b0010bb2f93bfcccdeb51beff7ce67c4b84fbfd65f892ed828de0f75e84a7ddb
- bc8bb9ae27cf534eeecbb8d41da1b48e33c8a222d793e16dcb10edfc792ac92f
- c7d07eb16ecddfeaa812ad251210c2bdc1681e04ea585bf145f567f9575e6757
- d322b11db04a9ecd13cea36438e591d2ddd8aa0f92b6a41bd5808d21e4854683
- d35c4be48d34270cc43367e37a53d6ca5c29637fc7517d9b95b5ab8048a36062
- dcc5cc23f492dee38ce7411daa8e0f89bb72dbfc89b7da3a6ca6a799e1f0f324
- deb9f507b68ec8201318e3be8bc44a20d549a57981a07f25f687ad97ddf63c73
- df79ffd3c6e157de55104b9ab3eb4a62ed341926bbaffbd2c9216895d5adfe26
- e1fe9f1caee0a7adedcc8fbb3270388c54c694171d7b7ea6991b7d0b43cbcc40
- e3c59888637ff64ea4418986c375b41b0b46168e8bffde3fc3606b0c212f712b
- e67446529af580230d0f007e9805a93978885a440dc68029744d951db5b07914
- f348c2fd327ad98abcb609e6e1555445cd90cd9488322aa769e2680e0aae6415
- f68502a6a1920806528873682da860231f60a2146dd010d2cd63e042c6f80e28
- faa0729ac6b3dc7cdfbeb5c042e4d9ff95ecfa51d1c3efdaf79560f9c27956b8
Coverage

Screenshots of Detection AMP
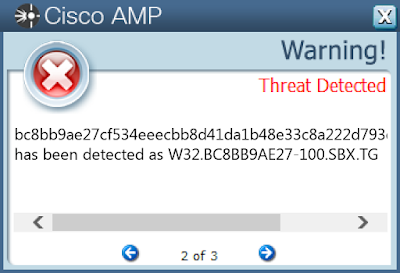
ThreatGrid

Umbrella
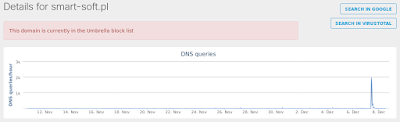
Screenshot
Win.Packed.Agent-6395107-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- 3749282D282E1E80C56CAE5A IP Addresses
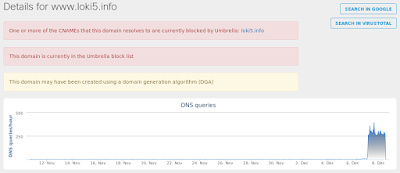
- 52[.]76[.]169[.]66 Domain Names
- www[.]loki5[.]info
- hkfb[.]01power[.]net Files and or directories created
- N/A File Hashes
- 085dbab7e810819bff0abe261e1d7015cbb4de4bb54261d547a7fa91e4d09d88
- 95966d29d229e3643a7670604daa0e3b0ffc4c7488eeca9b1b8268072b5e4b80
- df77604366128916f33b09dbb2fdb14ff88563bf214cbb4fd65d695858fb15fc
- 3edef9b394c47000fcca8f62f9f43875b1691cd26db56013327735c224d0498f
- 111df72bee877678a03a98f57f59ef1f9614ff0fee6fbaa2cea120e0d452a009
- 918911a937295b041ef4cf59cdadc4de332161cde87bc83d7f87e7e0e3fdbaa5
- 89d660f623dc3b4a64986709076b0923c85a88d23648156badf61897d40970fb
- 4fedc2463dcf7d3bbac73858d35a85a06bbde28f42937f13c1908f4d360e8987
- 1b011c8b56701fe3ef08308320d2913548b2284c55c0f7cda8b9de32de76648c
- 5e243d5865898124260d1eaac4c5a0f8952919cbd07ecc18831dcd632666c122
- a3c28f543dcb02e10a8172e7179eefb09281828cfb79a278ebbf969998866fa1
- b266bf5879122f2a0ab8623f4c35bea290dab54acfe6e7c3ffde5dc09f75a630
Coverage
Screenshots of Detection AMP
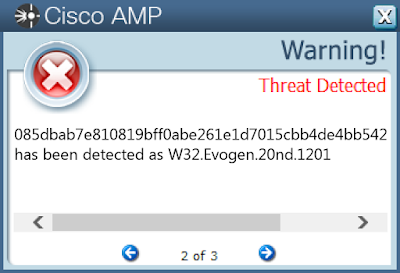
ThreatGrid
Umbrella
Win.Trojan.CeeInject-6394235-0
Indicators of Compromise
Registry Keys
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: _FileId_
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: Type
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _Usn_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- Value: ObjectLru
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: AeProgramID
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: DisplayName
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: AeFileID
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: AeFileID
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\10000000095A9
- Value: AB6
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D4
- Value: ObjectLru
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _FileId_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: _UsnJournalId_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\3A-57-D6-05-63-AB
- Value: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\11000000005DAF
- Value: AB5
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: _ObjectLru_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- Value: ObjectId
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- Value: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- Value: WpadDecisionTime
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: ErrorControl
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _ObjectLru_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\3A-57-D6-05-63-AB
- Value: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\3A-57-D6-05-63-AB
- Value: WpadDetectedUrl
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _ObjectId_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D4
- Value: ObjectId
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE
- Value: _CurrentObjectId_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- Value: WpadDetectedUrl
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: _Usn_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\3A-57-D6-05-63-AB
- Value: WpadDecisionReason
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: AeProgramID
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- Value: WpadNetworkName
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST
- Value: CurrentLru
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _UsnJournalId_
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- Value: 10000000095A9
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- Value: _ObjectId_
- <HKU>\.DEFAULT\SOFTWARE\CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: WOW64
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- Value: WpadDecisionReason
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINHOST
- Value: ImagePath
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- Value: 11000000005DAF
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CTLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\SmartCardRoot
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D4
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FileIdIndex-{3f37ba64-ef5c-11e4-bb8d-806e6f6e6963}
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\SmartCardRoot
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\CA
- <HKU>\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Disallowed
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\10000000095A9
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WinHost
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Root
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CRLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\Disallowed
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\3a-57-d6-05-63-ab
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\Indexes
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\My
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\trust
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\INDEXES\FileIdIndex-{3f37ba64-ef5c-11e4-bb8d-806e6f6e6963}
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\Indexes
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\TrustedPeople
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\Certificates
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\11000000005DAF
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\AuthRoot
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\Certificates
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CRLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Disallowed
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CTLs
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{D9F0881D-8458-4CC2-AE9B-5472D27E0970}\3a-57-d6-05-63-ab
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\trust
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CTLs Mutexes
- WinHostWD
- Local\ZonesCacheCounterMutex
- Local\ZonesLockedCacheCounterMutex IP Addresses
- 144[.]217[.]254[.]90 Domain Names
- linturefa[.]ru Files and or directories created
- %WinDir%\SysWOW64\WinHost.exe File Hashes
- daee59ee955587d378dd6dc11af1a702d554c7926a9f42bac3752732c33e9317
- 1a7de2ac4b22ca77acef5afe8e8b45dcc5150deb3408c8934221cfbbaee0655e
- fe33dc8941a6cd8ef4f64af295c2066eb0974966dfb355b5dd57e0c277261033
- 62a22fb0f59578de3679f70a41c2971b384167aebb032dd782f1d23d27015aa3
- b7ad41fbecce918894c0645aedbc60e4ac8daee24405b6a4957c98a728a14b9a
- 58e226e02f8dded4b24ae60d2524497083c3d0dafb02436df5209fa9e1061085
- d065ba2603790329d31e35cd45538b693c77f9870d98c4656e490c1a5034a8fa
- 36d4800fb0bed77e59468ae9b732eb806d59999ec2832a72e0209473069af5b1
- 3507a76940a2e6c930882b5cde32d2f11ba48cc0e6bfd6e4771a973ebe9db5ab
- 952e29ae44bb49c78f2b3fcd8c13e22181bc0a610e36723e41b79f8c1147649f
Coverage
Screenshots of Detection AMP
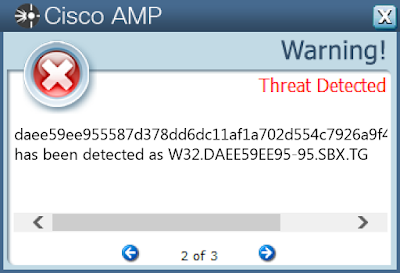
ThreatGrid
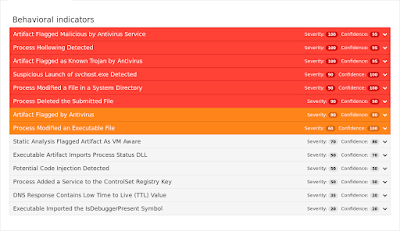
Umbrella
Win.Trojan.Delf-6394424-2
Indicators of Compromise
Registry Keys
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix Mutexes
- IP Addresses
- 191[.]252[.]186[.]108 Domain Names
- N/A Files and or directories created
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01.chk
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat
- \Users\Administrator\AppData\Roaming\Microsoft\Windows\Themes\slideshow.ini
- \Windows\ServiceProfiles\LocalService\AppData\Local\lastalive0.dat
- \Windows\ServiceProfiles\LocalService\AppData\Local\lastalive1.dat File Hashes
- 04c3a321d00b8f54ae242969ede062ae10b8906ba5d7071fd0aa4f3b3b4ef73e
- 248b6182fe5aaa120a6ad009595a93bf9431cbcd3e723ad711aef9b2d4562abf
- 3b221118a4c2716c6c76ddc1b6b01866fcc2643d7c29e38279d6aa2dd27d60a7
- 3dde0bb92308140701cb61711dc7e7298baff68668d96d2db9390e2b691efeb9
- 44e27c54ae3dc4c4c228dc10389d2b28d1230a8933d61661271f4eaf65925b1f
- 482142f886ed2ee2610e2740695435e0488b5c7d6081daaeffdc93c87b6e2f93
- 4bdae37fe1f8dab61a16f406f08a3bbe1482cd1387351f23b29849e1de64875d
- 67ed3caf144d2b2dd0e8f0b6ed4de1e0ee4052e152cf32fdc22b9a3f8c935e67
- 75eecd86ca4cbc10e60a6b5dc85964374fd91b25f0ecf08dcb7cd96d726ec581
- 7a41c90ba46f40af093491c1f03fa64b36c6a10603c29a9af78540cde8440d60
- 8486ba3a5d2ae2297118de5f39770fb89227752bbe3e59f951cd0ef0bab8c5b5
- 9b6087e9607aa0149beecd97709d27cf2e3703fded3f7d31dd613a6d3f23ccaf
- b17f8e85944768cc88c0a3b7103290c6eab820348103fa7a8a412af945e1d1dc
- b7c8faa19fb394f42733df9c1bc7c5f0a5313ead7b0ec870c0db05f6e3baa910
- c14055b23eb3a90e163962c9c70df3338bca68b67a615531ef40c6e8f8f6eabe
- c45fabfd7e6f52fa519d8215ac1d569ca385bb4552eae82e63da4befa319f1d9
- cc1eadad7810c4c94cdeebd63b7e54604253c4651c3a31bdf27dc96c189baa10
- d44dff94eaf9ed08c7f4ef47e69e0a9b308ce49c8bc814b94b2c95c92ba53fc3
- db1181dbda2b6053b008568b8f2f7b8a98cc3bd30fbea83ac8f69900d657e56f
- f1db091fff240dd3d49f0d22d4809db237fda042cb7ddf7afc81a0430f5c4b8c
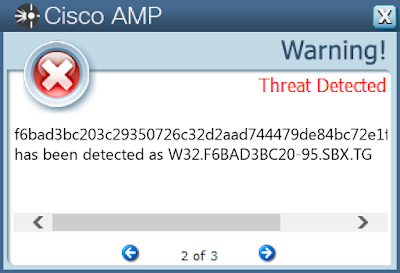
- f6bad3bc203c29350726c32d2aad744479de84bc72e1ffed0ad8392e5dde43d0
Coverage
Screenshots of Detection AMP
ThreatGrid
Screenshot
Win.Trojan.GenCNs
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\IEXPLORE
- Value: Type
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{D27CDB6E-AE6D-11CF-96B8-444553540000}\IEXPLORE
- Value: Count
- <HKLM>\SOFTWARE\Microsoft\SystemCertificates\CA\Certificates\189271E573FED295A8C130EAF357A20C4A9F115E
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\IEXPLORE
- Value: Time
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN
- Value: FullScreen
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpInterfaceOptions
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMAINSUGGESTION
- Value: NextUpdateDate
- <HKLM>\SOFTWARE\Classes\TypeLib\{1EA4DBF0-3C3B-11CF-810C-00AA00389B71}\1.1\0\win32
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{DBC80044-A445-435B-BC74-9C25C1C588A9}\IEXPLORE
- Value: Type
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\IEXPLORE
- Value: Count
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012017120620171207
- Value: CacheRepair
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{18DF081C-E8AD-4283-A596-FA578C2EBDC3}\IEXPLORE
- Value: Type
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\IEXPLORE
- Value: Blocked
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\TABBEDBROWSING\NEWTABPAGE
- Value: LastProcessed
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\IEXPLORE
- Value: Count
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS
- Value: DhcpScopeID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\IEXPLORE
- Value: Time
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDomain
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\IEXPLORE
- Value: Count
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{789FE86F-6FC4-46A1-9849-EDE0DB0C95CA}\iexplore
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012017120620171207
- Value: CacheLimit
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012017120620171207
- Value: CachePath
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\WINDOWSSEARCH
- Value: Version
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\TABBEDBROWSING\NEWTABPAGE
- Value: MFV
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServerList
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\URLBLOCKMANAGER
- Value: NextCheckForUpdateLowDateTime
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{DBC80044-A445-435B-BC74-9C25C1C588A9}\IEXPLORE
- Value: LoadTimeArray
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN
- Value: CompatibilityFlags
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNetbiosOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\IEXPLORE
- Value: Blocked
- <HKU>\Software\Microsoft\Internet Explorer\LinksBar\ItemCache\0
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{18DF081C-E8AD-4283-A596-FA578C2EBDC3}\IEXPLORE
- Value: Blocked
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E2E2DD38-D088-4134-82B7-F2BA38496583}\iexplore
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{D27CDB6E-AE6D-11CF-96B8-444553540000}\IEXPLORE
- Value: Time
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Favorites\Links
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\RECOVERY\PENDINGRECOVERY
- Value: AdminActive
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpSubnetMaskOpt
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMSTORAGE\52DFG.COM
- Value: NumberOfSubdomains
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\IEXPLORE
- Value: LoadTimeArray
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{FB5F1910-F110-11D2-BB9E-00C04F795683}\iexplore
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\IEXPLORE
- Value: Type
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012017120620171207
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{DBC80044-A445-435B-BC74-9C25C1C588A9}\IEXPLORE
- Value: Time
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\RECOVERY\ADMINACTIVE
- Value: {6C9F4A61-DA9E-11E7-BE93-00501E3AE7B5}
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpDomain
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{D27CDB6E-AE6D-11CF-96B8-444553540000}\IEXPLORE
- Value: Type
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{18DF081C-E8AD-4283-A596-FA578C2EBDC3}\IEXPLORE
- Value: Count
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\RECOVERY\ADMINACTIVE
- Value: {00000000-0000-0000-0000-000000000000}
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\URLBLOCKMANAGER
- Value: NextCheckForUpdateHighDateTime
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{18DF081C-E8AD-4283-A596-FA578C2EBDC3}\IEXPLORE
- Value: Time
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMSTORAGE\BAIDU.COM
- Value: Total
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDefaultGateway
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\IEXPLORE
- Value: Time
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\IEXPLORE
- Value: Type
- <HKLM>\SOFTWARE\WOW6432NODE\JAVASOFT\JAVA WEB START\1.6.0_41
- Value: Home
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012017120620171207
- Value: CacheOptions
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMSTORAGE\52DFG.COM
- Value: Total
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\TABBEDBROWSING\NEWTABPAGE
- Value: DecayDateQueue
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN
- Value: Window_Placement
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{DBC80044-A445-435B-BC74-9C25C1C588A9}\IEXPLORE
- Value: Count
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMSTORAGE\BAIDU.COM
- Value: NumberOfSubdomains
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\DOMAINSUGGESTION\FILENAMES
- Value: en-US
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\SHELL EXTENSIONS\CACHED
- Value: {17FE9752-0B5A-4665-84CD-569794602F5C} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E7E6F031-17CE-4C07-BC86-EABFE594F69C}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\iexplore
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKCU>\SOFTWARE\MICROSOFT\MULTIMEDIA\DRAWDIB
- Value: 1024x768x24(BGR 0)
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CTLs
- <HKCU>\Software\Microsoft\SystemCertificates\My
- <HKU>\Software\Microsoft\CTF\TIP\{1188450c-fdab-47ae-80d8-c9633f71be64}\LanguageProfile\0x00000000\{63800dac-e7ca-4df9-9a5c-20765055488d}
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\System\CurrentControlSet\Services\Tcpip\Parameters
- <HKCU>\Software\Microsoft\Internet Explorer\Toolbar
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Root
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CRLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKCU>\Software\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\SmartCardRoot
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\baidu.com
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\SOFTWARE\RegisteredApplications
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Disallowed
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\www.52dfg.com
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHist012017120620171207
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CTLs
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\pos.baidu.com
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKCU>\Software\Microsoft\Internet Explorer\TabbedBrowsing\NewTabPage
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CRLs
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\52dfg.com
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\trust
- <HKLM>\Software\Microsoft\SystemCertificates\trust
- <HKCU>\Software\Microsoft\Internet Explorer\Main\WindowsSearch
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKU>\Software\Microsoft\Internet Explorer\Recovery\Active
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKU>\Software\Microsoft\Internet Explorer\International\CpMRU
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\Software\Microsoft\SystemCertificates\TrustedPeople
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKCU>\Software\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKCU>\Software\Microsoft\SystemCertificates\Root
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKCU>\Software\Microsoft\SystemCertificates\SmartCardRoot
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Root
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CTLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CTLs
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKLM>\Software\Microsoft\SystemCertificates\CA
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\TrustedPeople
- <HKLM>\Software\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\Certificates
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\AuthRoot
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\cpu.baidu.com
- <HKU>\Software\Microsoft\Windows\ShellNoRoam\MUICache
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\Certificates
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\CA
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKU>\Software\Microsoft\Internet Explorer\LinksBar\ItemCache\0
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKCU>\Software\Microsoft\Multimedia\DrawDib
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CRLs
- <HKCU>\Software\Microsoft\Internet Explorer\Main
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\CA
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CTLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Disallowed
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\P3P\History
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\Disallowed
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKCU>\Software\Microsoft\Internet Explorer\DOMStorage\Total
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKCU>\Software\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Root
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\trust
- <HKCU>\Software\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
- <HKCU>\Software\Microsoft\Windows Script\Settings
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CTLs Mutexes
- !IECompat!Mutex
- IsoScope_2f4_IESQMMUTEX_0_274
- Local\URLBLOCK_DOWNLOAD_MUTEX
- {66D0969A-1E86-44CF-B4EC-3806DDDA3B5D}
- Local\URLBLOCK_FILEMAPSWITCH_MUTEX_756
- UpdatingNewTabPageData
- IsoScope_2f4_IESQMMUTEX_0_331
- Local\VERMGMTBlockListFileMutex
- Local\DirectSound DllMain mutex (0x000006A8)
- IsoScope_2f4_ConnHashTable<756>_HashTable_Mutex
- !IEFileUpdater!Mutex
- Local\InternetExplorerDOMStoreQuota
- Local\URLBLOCK_HASHFILESWITCH_MUTEX
- Local\ZonesLockedCacheCounterMutex
- Local\https://cpu.baidu.com/
- IsoScope_2f4_IESQMMUTEX_0_303
- IsoScope_2f4_IESQMMUTEX_0_519
- Local\https://pos.baidu.com/
- !PrivacIE!SharedMem!Mutex
- Local\MSCTF.Asm.MutexDefault1
- {5312EE61-79E3-4A24-BFE1-132B85B23C3A}
- {C20CD437-BA6D-4ebb-B190-70B43DE3B0F3}
- Local\!BrowserEmulation!SharedMemory!Mutex IP Addresses
- 106[.]39[.]162[.]36
- 61[.]135[.]185[.]23
- 117[.]27[.]232[.]35
- 106[.]11[.]30[.]202
- 104[.]27[.]97[.]74
- 66[.]102[.]255[.]61
- 116[.]253[.]191[.]237
- 106[.]11[.]30[.]205
- 103[.]7[.]29[.]251
- 111[.]202[.]114[.]35
- 204[.]79[.]197[.]200
- 66[.]102[.]255[.]57
- 66[.]198[.]178[.]124
- 140[.]205[.]250[.]8
- 103[.]235[.]46[.]191
- 140[.]205[.]248[.]60
- 120[.]132[.]3[.]45
- 106[.]11[.]93[.]16
- 66[.]102[.]255[.]39
- 104[.]27[.]96[.]74
- 66[.]198[.]178[.]122
- 104[.]27[.]93[.]74
- 165[.]254[.]60[.]146
- 65[.]153[.]196[.]195
- 65[.]153[.]196[.]196
- 198[.]11[.]132[.]221
- 66[.]198[.]24[.]253
- 111[.]202[.]114[.]81
- 66[.]231[.]239[.]122
- 66[.]231[.]239[.]120
- 47[.]89[.]67[.]254
- 66[.]231[.]239[.]124
- 140[.]205[.]60[.]79
- 140[.]205[.]218[.]67
- 119[.]146[.]74[.]34
- 65[.]153[.]158[.]144
- 104[.]193[.]88[.]109
- 220[.]170[.]182[.]31
- 103[.]235[.]46[.]39
- 66[.]102[.]255[.]42
- 66[.]102[.]255[.]43
- 111[.]206[.]37[.]219
- 222[.]186[.]49[.]224
- 66[.]102[.]255[.]45
- 66[.]102[.]255[.]50
- 140[.]205[.]136[.]1
- 140[.]205[.]158[.]4
- 66[.]102[.]255[.]44
- 112[.]80[.]255[.]55
- 47[.]89[.]69[.]254
- 104[.]27[.]92[.]74
- 180[.]76[.]22[.]48
- 65[.]153[.]196[.]201
- 112[.]80[.]248[.]186
- 106[.]11[.]129[.]144
- 66[.]198[.]24[.]243
- 14[.]215[.]178[.]152
- 65[.]153[.]196[.]200
- 106[.]11[.]209[.]24
- 65[.]153[.]196[.]202
- 65[.]153[.]196[.]203
- 103[.]235[.]46[.]40
- 65[.]153[.]158[.]143
- 65[.]153[.]158[.]145
- 119[.]146[.]74[.]49
- 140[.]205[.]61[.]61
- 65[.]153[.]158[.]148
- 66[.]231[.]239[.]92
- 115[.]239[.]210[.]141
- 140[.]205[.]61[.]85
- 140[.]205[.]218[.]72 Domain Names
- www[.]taobao[.]com
- fj[.]1235k[.]com[.]cname[.]yunjiasu-cdn[.]net
- z13[.]cnzz[.]com
- pos[.]baidu[.]com
- static[.]fraudmetrix[.]cn
- dfjs[.]1235k[.]com
- f11[.]baidu[.]com
- cm[.]pos[.]baidu[.]com
- cpu[.]baidu[.]com
- dup[.]baidustatic[.]com
- gss1[.]bdstatic[.]com
- cnzz[.]mmstat[.]com
- zz[.]1235k[.]com
- cpro[.]baidustatic[.]com
- fp[.]fraudmetrix[.]cn
- icon[.]cnzz[.]com
- sslshare[.]jomodns[.]com
- f12[.]baidu[.]com
- wn[.]pos[.]e[.]shifen[.]com
- imageplus[.]baidu[.]com
- wmjs[.]jomodns[.]com
- ope[.]tanx[.]com
- ad-sh-sz-zb[.]wagbridge[.]tanx[.]alimama[.]com[.]gds[.]alibabadns[.]com
- zz[.]1235k[.]com[.]cname[.]yunjiasu-cdn[.]net
- webb[.]jomodns[.]com
- gw[.]aicdn[.]com
- opencdn[.]jomodns[.]com
- publish-pic-cpu[.]baidu[.]com
- eclick[.]baidu[.]com
- atanx[.]alicdn[.]com
- p[.]tanx[.]com
- c[.]cnzz[.]com
- apisoft[.]df0535[.]com[.]cname[.]yunjiasu-cdn[.]net
- www[.]52dfg[.]com
- dfjs[.]1235k[.]com[.]cname[.]yunjiasu-cdn[.]net
- ope[.]gds[.]tanx[.]com
- bzclk[.]e[.]shifen[.]com
- fj[.]1235k[.]com
- f10[.]baidu[.]com
- wn[.]pos[.]baidu[.]com
- hm[.]baidu[.]com
- sp0[.]baidu[.]com
- world[.]taobao[.]com
- u755[.]v[.]qingcdn[.]com
- cm[.]pos[.]e[.]shifen[.]com
- simage[.]gshifen[.]com
- z[.]gds[.]cnzz[.]com
- cb[.]e[.]shifen[.]com
- all[.]cnzz[.]com[.]danuoyi[.]tbcache[.]com
- apisoft[.]df0535[.]com
- bzclk[.]baidu[.]com
- 7xjnh3[.]com2[.]z0[.]glb[.]qiniucdn[.]com
- caclick[.]baidu[.]com
- atanx[.]alicdn[.]com[.]danuoyi[.]tbcache[.]com
- z11[.]cnzz[.]com
- imageplus[.]e[.]shifen[.]com
- ecomcbjs[.]jomodns[.]com
- cpu[.]e[.]shifen[.]com
- open[.]t[.]qq[.]com
- origin[.]open[.]qq[.]com
- jpaasne[.]e[.]shifen[.]com
- s4[.]cnzz[.]com
- ieonline[.]microsoft[.]com
- flashservice[.]adobe[.]com Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\thread-next[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\fb[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\avatar[1].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\style_1_forum_viewthread[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\ex[1].js
- \TEMP\AppData\wwblist.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\checkonline.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\style_1_common[1].css
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@1235k[1].txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\px[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\avatar[2].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\forum[1].js
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{775A3D20-DA9E-11E7-BE93-00501E3AE7B5}.dat
- %AppData%\Microsoft\Windows\Cookies\MTSHQBBR.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\qq_share[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\bd_logo[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=1555995088,2202163700&fm=76[1].jpg
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\arw_r[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\stat[1].js
- \TEMP\AppLink\sql.dll
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\avatar[1].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\fm[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\MWWX7599.htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\userinfo[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\jquery-1.8.3.min[1].js
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\showip.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\arw[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\detect[1].js
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\~DF4E88.tmp
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{6C9F4A61-DA9E-11E7-BE93-00501E3AE7B5}.dat
- %AppData%\Microsoft\Windows\Cookies\28944M2J.txt
- \TEMP\gzcvaqtzdusmspytflzf.dfg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\showip.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\6108[1].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\fj_btn[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\search[1].png
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{6C9F4A63-DA9E-11E7-BE93-00501E3AE7B5}.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\avatar[5].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\noavatar_small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\log[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\20171206005032_61527[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\nv[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\share_btn[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\md5[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\favicon[2].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\58d12356-49a1-4b13-8946-cf0414ecedd8[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\arw_r[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V0100010.log
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\thread-100646-1-1[1].htm
- \TEMP\AppData\QS.db
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\59_avatar_middle[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\thread-next[1].png
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\print[1].png
- %SystemDrive%\gpoigmfsdzfgohtecxlq.dfg (copy)
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\style_1_common[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\seditor[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\fav[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\avatar[4].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\jquery-1.8.3.min[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\avatar[3].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\avatar[1].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\pengyou[1].png
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\qmenu[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\ico_lz[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\avatar[2].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\highlight.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\pc_ads_bear.1x[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\adClosefeedbackUpgrade.min[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\switch_width[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\background[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\oshr[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\df_logo[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\qmenu[1].png
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@zz.1235k[1].txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\bg_rb[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\fastreply[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\i[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\53_avatar_small[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\avatar[3].htm
- %AppData%\Microsoft\Windows\Cookies\IDOPFIC9.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\forum_viewthread[1].js
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\Microsoft\Internet Explorer\Recovery\Active\{17DE33AB-DA76-11E7-800A-00007D8081C0}.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\kindeditor-min[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\list-style-119[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\2f57811a-a7ec-49be-8a67-fcae1fecd305[1].jpg
- %AppData%\Microsoft\Windows\Cookies\AZ8N99IZ.txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\background[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\editor[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\scrolltop[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\px[1].png
- %AppData%\Microsoft\Windows\Cookies\AISN47QD.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\c[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\vchm[1].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\tongdun[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=4262931832,9247409&fm=76[1].jpg
- %AppData%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\fm[1].js
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\common[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\stat[1].htm
- %AppData%\Microsoft\Windows\Cookies\FTBCR8D3.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\stick.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\DOMStore\R85DXRAK\cpu.baidu[1].xml
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\dfg.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\coreMobilePc[1].js
- %SystemDrive%\AppData\QS.db
- \TEMP\AppData\wwwlist.txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\logging[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\bump.small[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@www.52dfg[2].txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\noavatar_middle[2].gif
- %AppData%\Microsoft\Windows\Cookies\3BST8HRF.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\36_avatar_small[1].jpg
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\checkonline.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\style[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\hot_3[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\collection[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\cba256a9-f1e4-429e-a5c2-cade0a1ff7ad[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\profile[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=1130617034,1673256959&fm=76[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=725440160,1310097331&fm=76[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\avatar[1].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\open.small[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\qq_login[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\online_moderator[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\qzone[1].gif
- %TEMP%\dfg.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\avatar[4].htm
- %AppData%\Microsoft\Windows\Cookies\GURHNPBW.txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{17DE33AA-DA76-11E7-800A-00007D8081C0}.dat
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\md5[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\weibo[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\fp[1].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\pt_item[1].png
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\arw_l[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\default[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\pn_post[1].png
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\da98dd37-304c-4f34-8692-963ad9d3fb83
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\userinfo[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\pn_post[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\dm[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\pn[1].png
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\jquery-1.8.3.min[1].js
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\~DF274C.tmp
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\qshare[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\20171206005032_61527[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\tanxssp[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\settop[1].png
- %SystemDrive%\AppData\QS.db-journal
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\wh[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\qq_login[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\hm[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\25_avatar_small[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\avatar[3].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\search[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01.chk
- %SystemDrive%\AppLink\sql.dll
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\comm[1].js
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\nv[1].png
- \TEMP\AppData\AppConfig.ini
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\fp[1].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\hot_3[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\print[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\midavt_shadow[1].gif
- %AppData%\Microsoft\Windows\Cookies\OL83W4WY.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\core[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\avatar[5].htm
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\pn[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\avatar[4].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\logging[1].js
- %AppData%\Microsoft\Windows\Cookies\3QDRLGBW.txt
- %AppData%\Microsoft\Windows\Cookies\BWJZDR10.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\arrow_top[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\home[1].js
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\imagestore\aowwxkh\imagestore.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\locked[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\clear[1].swf
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\thread-prev[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\close.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\pc_ads.1x[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\cf2ca419-ddee-4d2b-856a-3354b551e5a3[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\o[1].htm
- %SystemDrive%\287140881.exe
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\forum_viewthread[1].js
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\nv_a[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\common[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\232719bv8ve5cvzl1l8zls[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012017120620171207\container.dat
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\arw_l[1].gif
- \TEMP\ÈÕÖ¾\²Ù×÷ÈÕÖ¾2017Äê12ÔÂ6ÈÕ.txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\jquery-1.8.3.min[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\rar[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\pt_item[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\ad[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Internet Explorer\DOMStore\ROKQPSRG\www.52dfg[1].xml
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\nv_a[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\namepost.small[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\pic1[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\avatar[2].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\arrwd[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\31_avatar_small[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\online_member[1].gif
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=2144616610,2983434978&fm=76[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\43_avatar_middle[1].jpg
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\fj_btn[1].png
- \TEMP\AppData\qblist.txt
- \TEMP\AppData\qwlist.txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\style[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\u=4083043643,3990593241&fm=76[1].jpg
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\switch_width[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\avatar[2].htm
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\u=1199205626,971402299&fm=76[1].jpg
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\ui[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\icon[1].gif
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\thread-100646-1-1[1].html
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@www.52dfg[1].txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\comm[1].js
- \TEMP\093477fa334791163629386b655b01a8284cf9826760b2dd9c3046e370ce026b.exe
- %SystemDrive%\AppData\AppConfig.ini
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\style_1_forum_viewthread[1].css
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\favicon[1].ico
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\6OG0LJ4F\df_logo[1].png
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\cb_pc[1].js
- %SystemDrive%\ \ 2017 12 6 .txt
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\forum[1].js
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\list-entry[1].js File Hashes
- 093477fa334791163629386b655b01a8284cf9826760b2dd9c3046e370ce026b
- 32529dd47d10c539f3b8334ba849decf6b7707196ab8bcc893dd3e4aa4399c3e
- 354c9f630336cce0332558d73ae8000b62f61ca3eb7462e21183546f0da613b8
- 36992980b5db3833a294748ce2abe530b9313dad5b0a8094bf9b10106ecbf250
- 3e47b0d23d7e39af6759ca207d3307584862fe4181a6a4a54ea38cd45ce8c542
Coverage
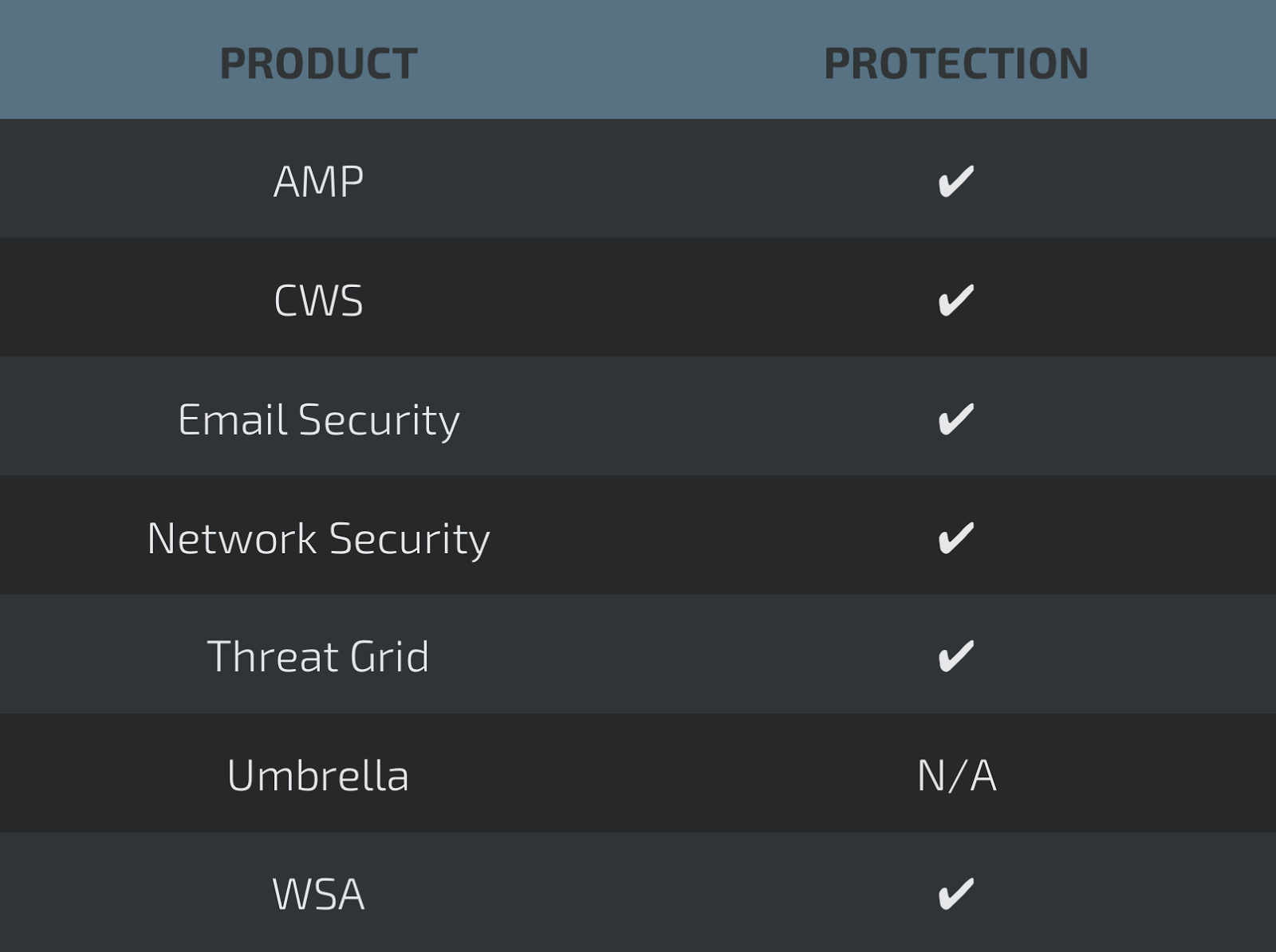
Screenshots of Detection AMP
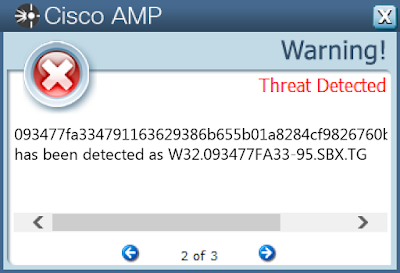
ThreatGrid
Screenshot
Win.Trojan.Tinba-6390856-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: F9E7DE7B
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Run Mutexes
- F9E7DE7B IP Addresses
- N/A Domain Names
- N/AFiles and or directories created
- %AppData%\F9E7DE7B\bin.exe File Hashes
- cc235fb882372820d6232ba89455e5da28bc9b1877e528ac2397d280b0a7d5ff
- baf4a030d51e688aebe5d190334f9751339e75b79c55e1ae9e277b7a33dd8808
- 17147dc9d03023c4772817b6904676eb9417be3294d998ba118bf0a9d1f0d6d6
- afdcc240157e03a46e8141ee99b24e4d6bcbe37c2a8d1b30e6ea860496cc3352
- eef6f6d965da6f45e376eb9e5e01451ea110466e4b02780625cd5170edad4119
- 52d0de1c298a088a0455941e1fe0e7894671db98338a34febf4f9870aa4f387c
- bda3c8f957b7195dec6d5f2f4114022346aef9791ca434943876359d3d4f15e8
- b3e98e2aed557dad670309692bdc0c6d7d580ea51933449ed01354bf2dd8ca3e
Coverage
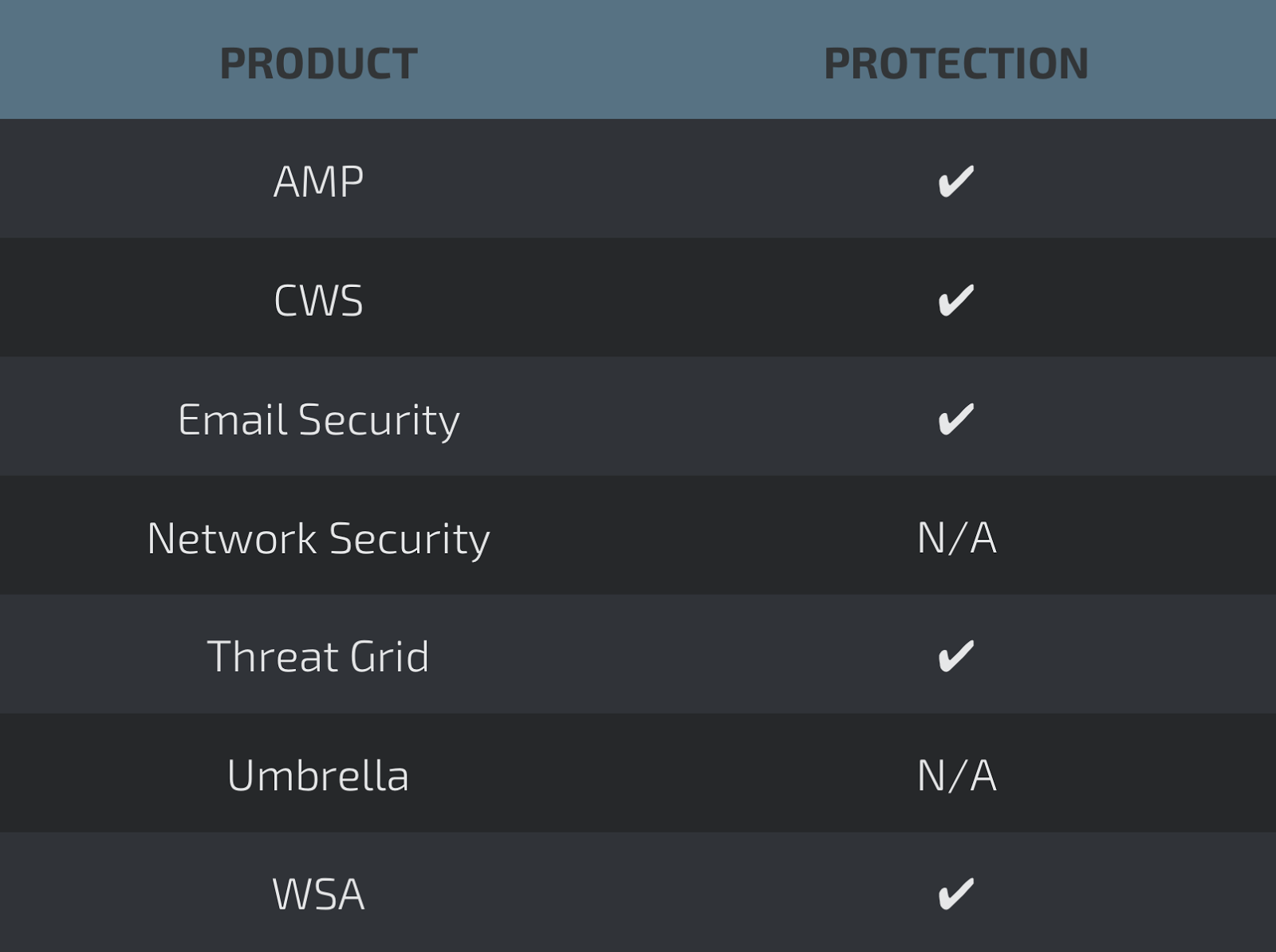
Screenshots of Detection AMP
ThreatGrid