Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 6 and Jan. 13. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
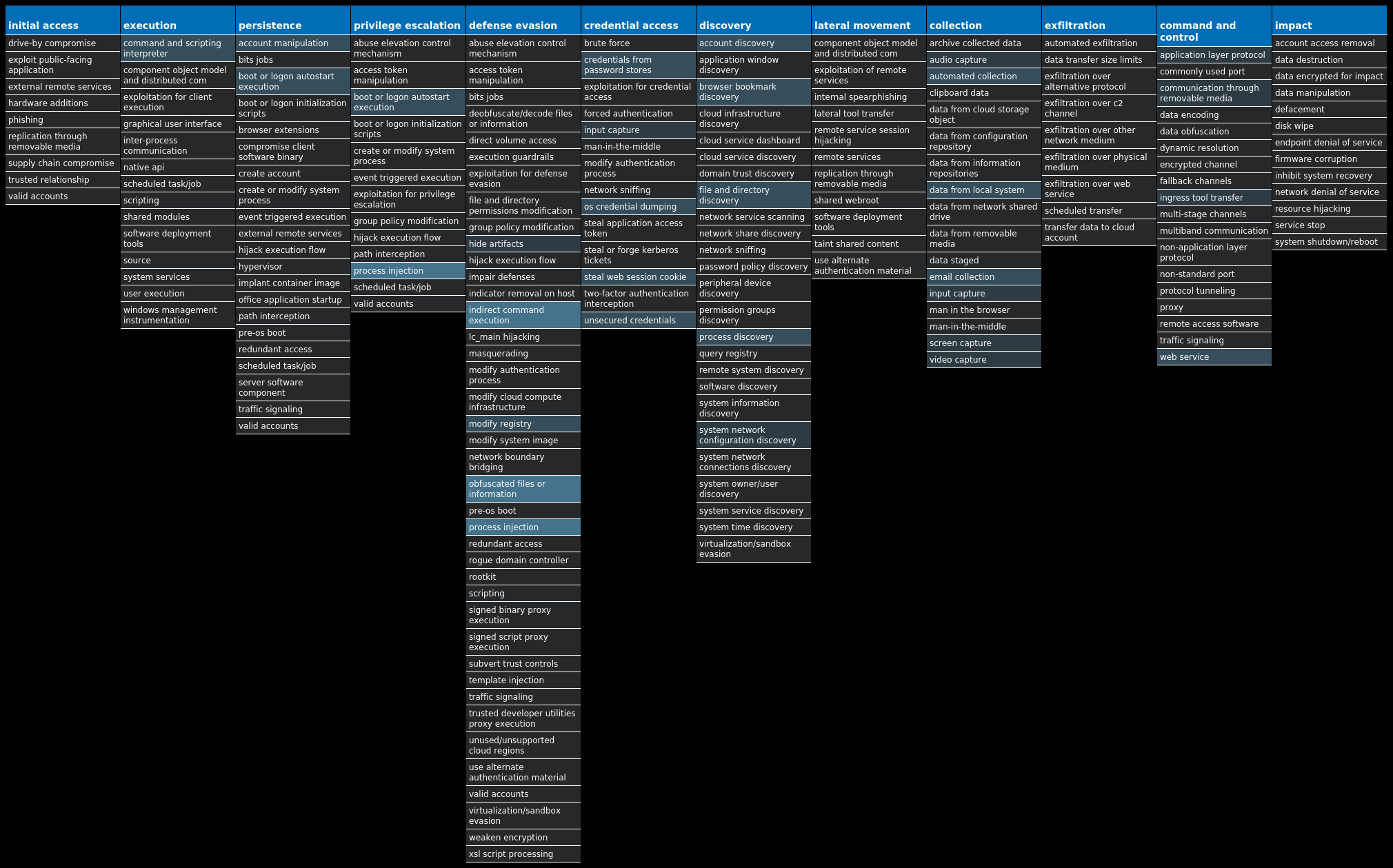
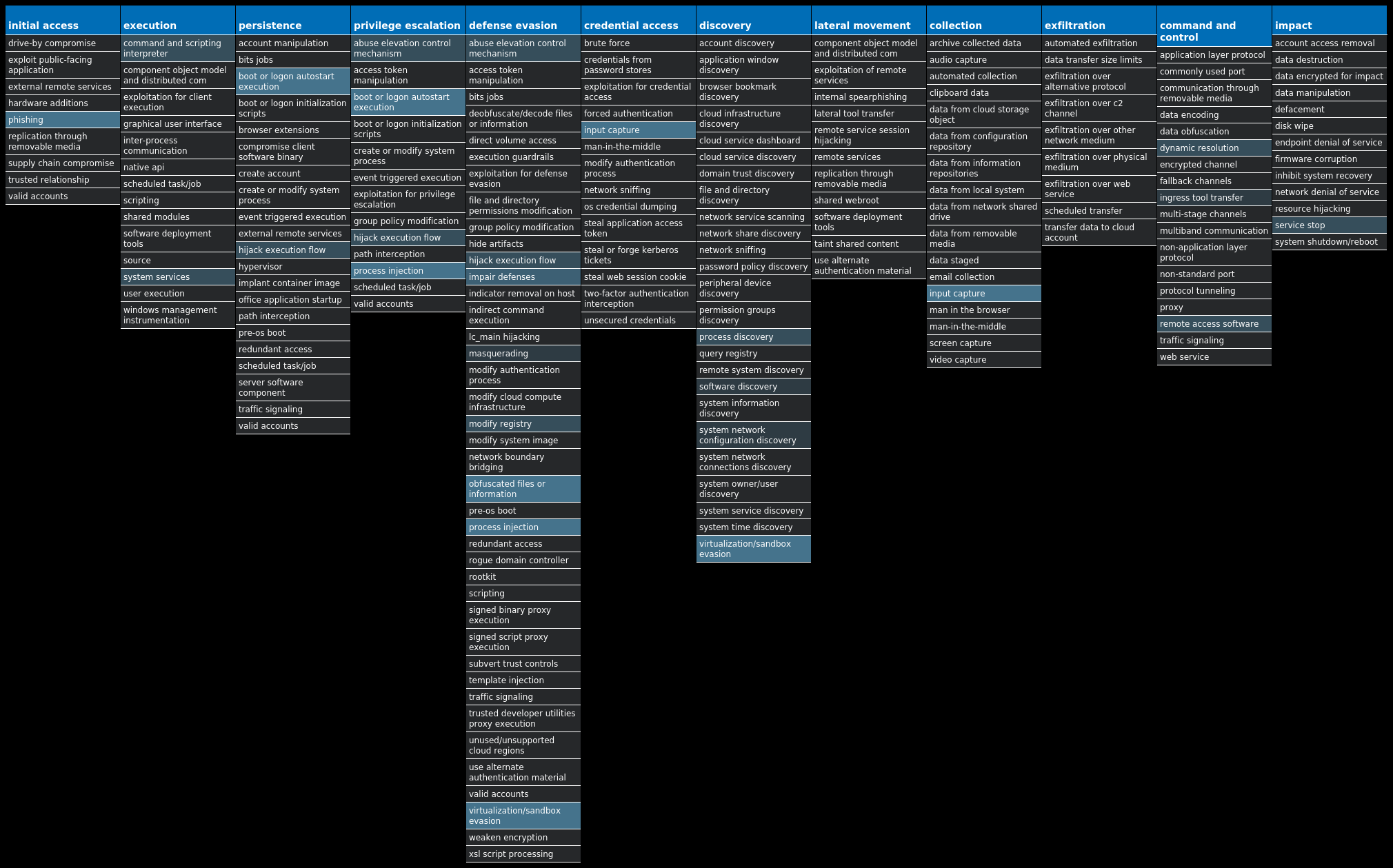
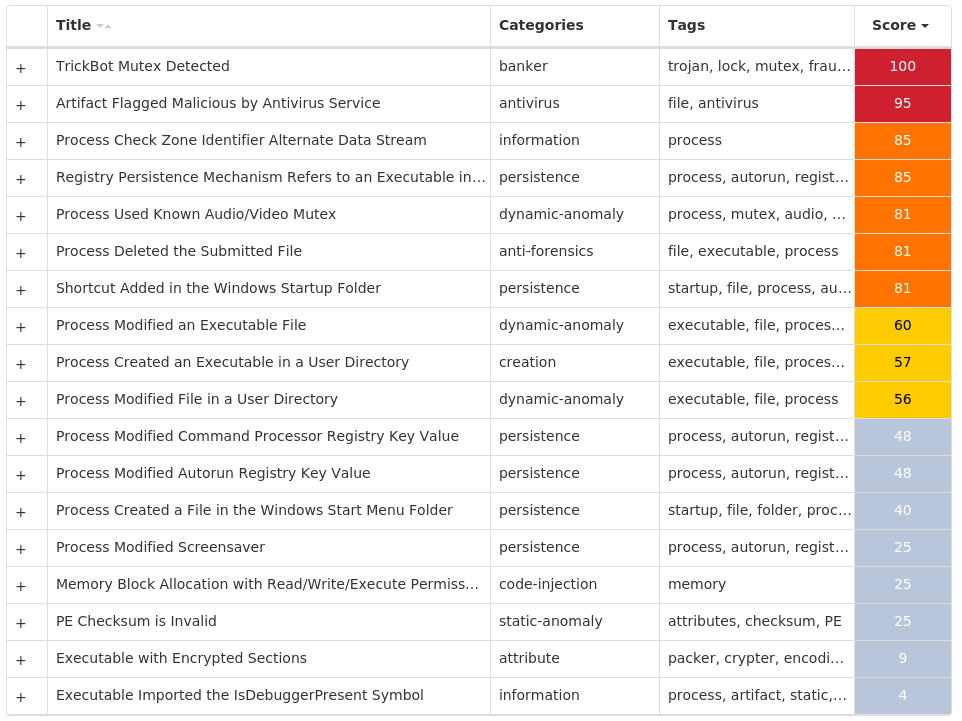
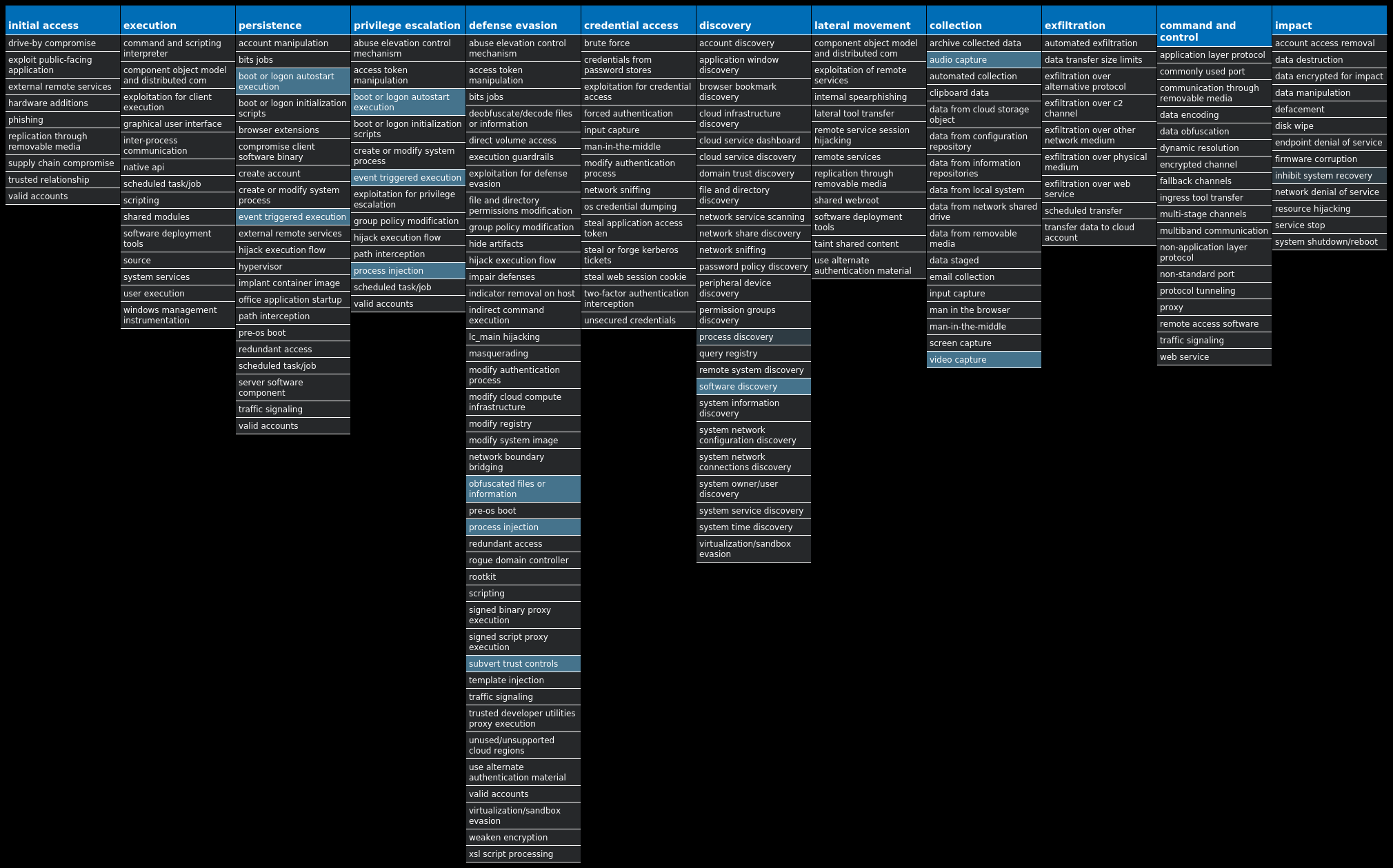
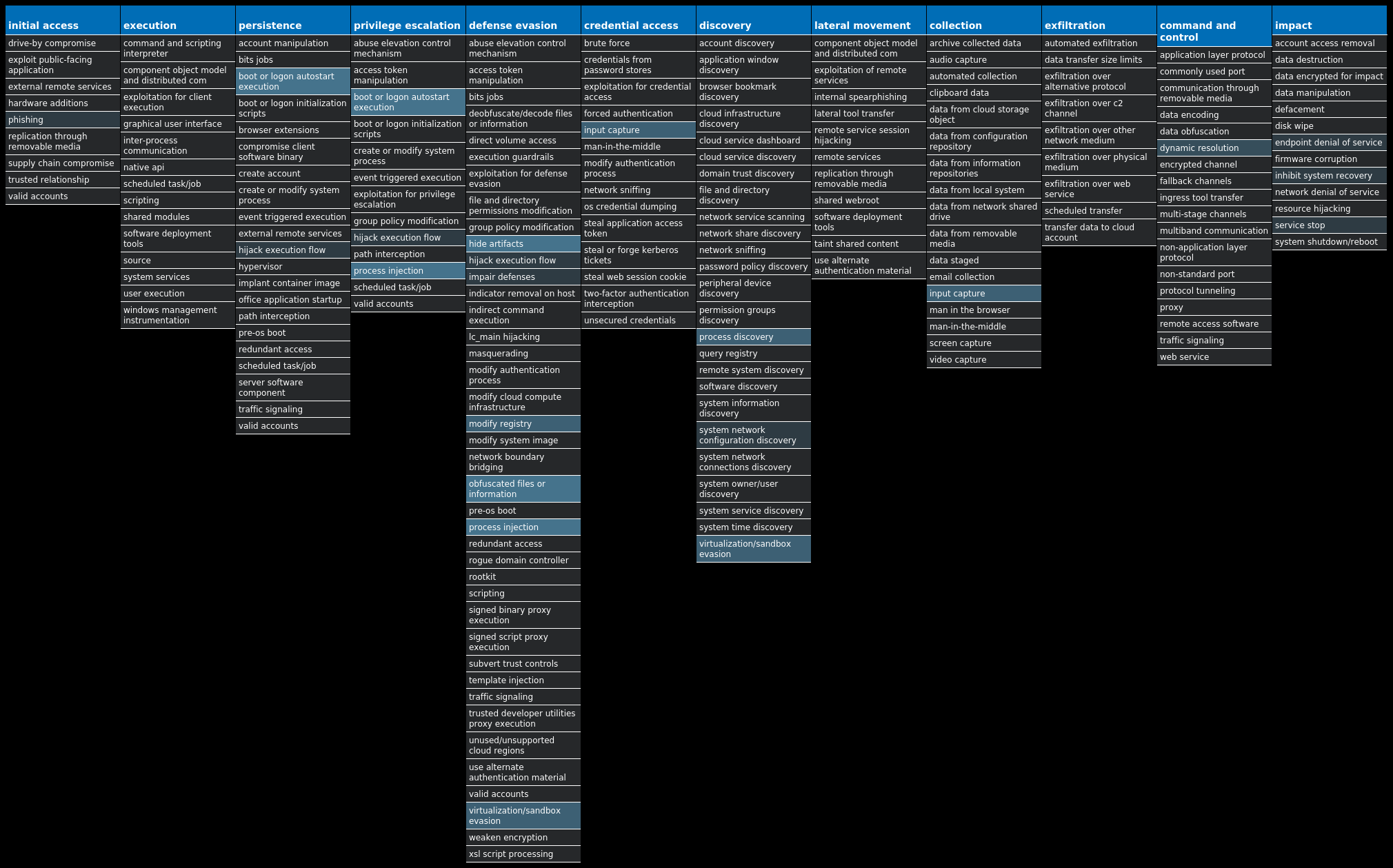
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Lokibot-9982061-1 Dropper Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Packed.Upatre-9982083-0 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Win.Worm.Vobfus-9982088-0 Worm Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its command and control (C2) servers. Win.Dropper.Remcos-9982549-0 Dropper Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Dropper.Bifrost-9982192-0 Dropper Bifrost is a backdoor with more than 10 variants. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attacker, who uses the client, to execute arbitrary code on the compromised machine. Bifrost contains standard RAT features including a file manager, screen capture utility, keylogging, video recording, microphone and camera monitoring, and a process manager. In order to mark its presence in the system, Bifrost uses a mutex that may be named "Bif1234," or "Tr0gBot." Win.Trojan.HawkEye-9982173-1 Trojan HawkEye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media. Win.Dropper.TrickBot-9982207-0 Dropper TrickBot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts. Win.Packed.DarkComet-9982401-1 Packed DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system. Win.Dropper.Shiz-9982208-0 Dropper Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site.
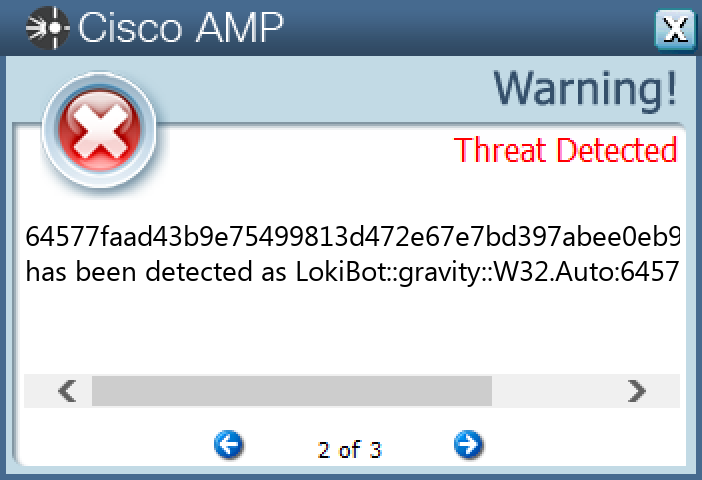
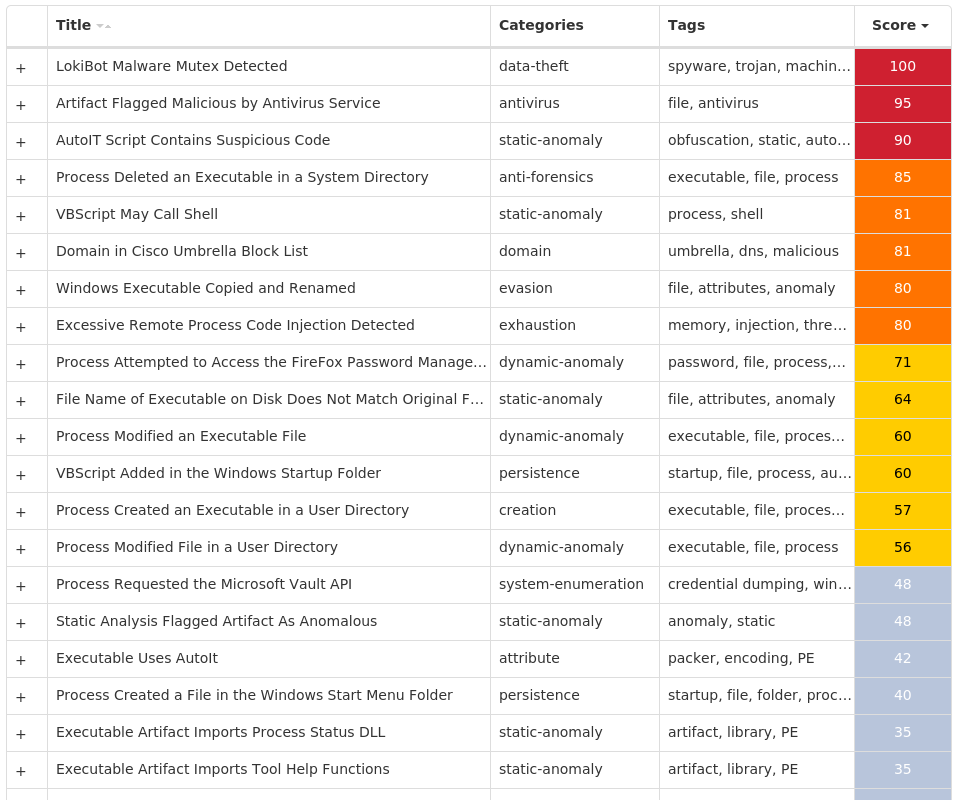
Threat Breakdown Win.Dropper.Lokibot-9982061-1 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Mutexes Occurrences 3749282D282E1E80C56CAE5A16
Domain Names contacted by malware. Does not indicate maliciousness Occurrences shopper[.]bulutlogistic[.]com16
Files and or directories created Occurrences %APPDATA%\D282E116 %APPDATA%\D282E1\1E80C5.lck16 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c516 %APPDATA%\D282E1\1E80C5.exe16 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\DeviceProperties.vbs16 %HOMEPATH%\AppVClient16 %HOMEPATH%\AppVClient\MuiUnattend.exe16
File Hashes 1e89d325c93e38db0a565868ab614d7cd834336b1385456c646be0e9082eba512b9fe265fe13c3f83371491ed5f17d80f9ff56ea693aaa8bffd0c494b2194a873400c14435d905a3053958cfa6329fc846c0345d6f623f9bca68afd2aa9dfa163471c7ad3727186cabbc29315177bdec9cfebd0f5874a86c94794d192562d07537d3eb83bc8face3956940c9a614dc9cd09cdbd6137537b7fe285609d9dba5ab586e4e5052d9a3c243f0b73cd116cbe61ff25569e453bd34ebf8c4c7b38513705cb7c2337aac3d6ba40b178a0fd12755ac352eeef55932e4abd4d359024dcf8164577faad43b9e75499813d472e67e7bd397abee0eb98d1c1c1799de5bba5c14686a5b923eddca1c0de89c38e4fdf7919ff109e20b151a2fca5211b3e28950aa6fe381048c428320914ba87e73dcb6616c791175418cbcd3750c40aa26f575a7997d88ee6e82e2f2361080b0e2c2f33772041202775f39f25ad12ba9076f6bc89df9f730ddf3ecc6268409cacf8c681f228c627ff3d2a0aa88ae28baae14ba4d9eb070abc0b299340d3005a2d2ed06c1da77868df0aaa665729dc5038d066c19b6372ea27cd357aefd5b8a59b5c68004c98420d4abfbce1887dae155f388fa48bc5d9e9a011c1dfec940cc15e7b8675955c84859d91849a71f75e47a48ffd5e9c7afef75dd4a83591cdfe132485a77b1a92e03175bf3dcac321957dd7dfc933f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-9982083-0 Indicators of Compromise IOCs collected from dynamic analysis of 29 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 38[.]65[.]142[.]1228 104[.]18[.]114[.]9715 104[.]18[.]115[.]9713 71[.]99[.]130[.]246 66[.]196[.]61[.]2185 96[.]46[.]103[.]2325 87[.]249[.]142[.]1894 98[.]214[.]11[.]2534 87[.]229[.]109[.]2504 216[.]16[.]93[.]2504 173[.]243[.]255[.]794 66[.]196[.]63[.]334 76[.]84[.]81[.]1203 85[.]135[.]104[.]1703 66[.]215[.]30[.]1183 104[.]174[.]123[.]663 188[.]255[.]239[.]343 69[.]144[.]171[.]443 69[.]9[.]204[.]1143 65[.]33[.]236[.]1733 68[.]70[.]242[.]2033 98[.]222[.]64[.]1843 24[.]148[.]217[.]1882 72[.]230[.]82[.]802 24[.]33[.]131[.]1162
*See JSON for more IOCs
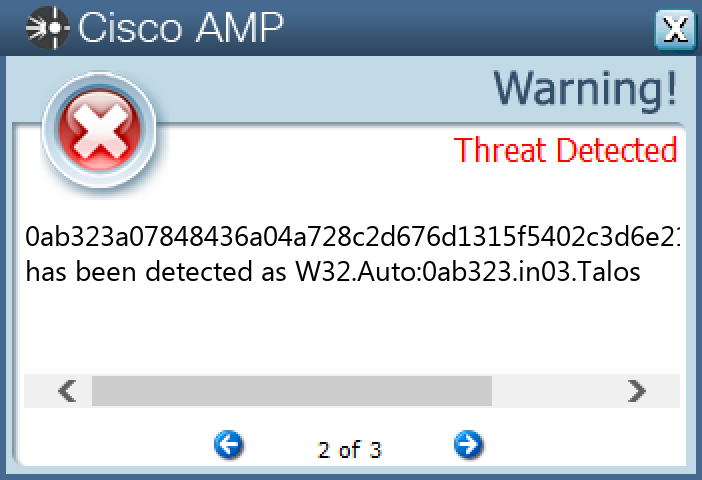
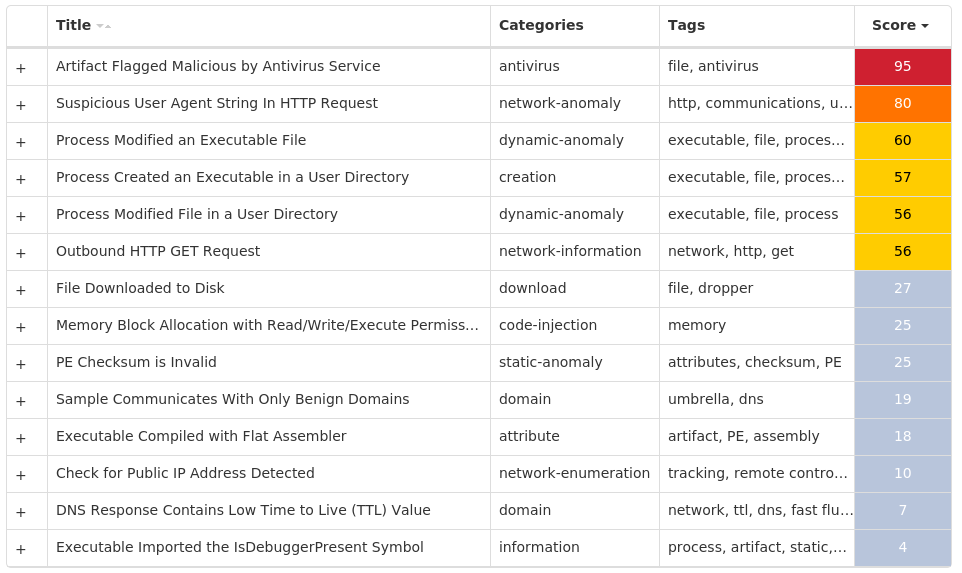
Domain Names contacted by malware. Does not indicate maliciousness Occurrences icanhazip[.]com28
Files and or directories created Occurrences %TEMP%\zoogymal.exe28
File Hashes 00a70ad787f7835979f4a4910c536b65cedcfdf999694baa561238bb1372c2110332d56c48dff801d3c4db04b9b7bc67b3b0c37481c912f8e5efebe25c65379f06e7cf4d404e6b3c4966658605178b7f27b97fa65b86ed3fe5ed7ba189ff074e0ab323a07848436a04a728c2d676d1315f5402c3d6e21e17a9e6edd648f795de0ad75143ea7b45a1e39d847d54c5bbde5ceb2b18843b52babe8574ca401e4db70b131013bbe7553832b45a6540c4be22c452a244ef432f7b6fddb47d5b1c2cf30be4b37c4717d53925486df11d9c527be53ea4290c585187bfdafc055aa8f3ff0fa4711a0c9e7dfc2135a0c7e9407691bf5677b1b1640e250abdc5db4a09f62914ee75574d7c50b36e0a606d910f393926becb99d0703ea403f207bf6cb0691815991e724ad40738bf12809d976053842ce01ed3922e49d501630adebc80e1281647d865e07ebfb89fa02898b63b0ea9c2ffa14455364081d3bdc4a56e06cfcc18a7a9ada7800ab1df038b7e0957c4aa8deba79dfdec0e390d75e964ee9b185319be03d1da5974890f083a5e2c014939ade91bc034c9eb6a88806a321232f9be1badcfc36cb64a1e931be9768d92cf991edcd2b04d61b22bd36e87e07700f4bd1be0f73ec48241a860f6551b37c5f732f2f96ff111632837906a143deac311c21cba83c1febd55426cca9fa581121acb3b54368642230a0cbfb067d82a1330891d346fc64f792be85c3b438f75085a4ffe499226d194c14518ba38a9f53226232319c3f4c8a8d8fd332eb5a5465c8c217d37930a611d7c9aa8971d273fb75d7423d3f205a2dbd4c71638daae0e45c65d52b6729c506ac5ba4bfc7901075c8dae24a9743e5e7368323e8b0a810a7bb5d3e81dc9e73a986f09f442e39462e671e7254349f4f682c7a562c562577b26c2ce3234cbc34b0412e6cb3865ca25c86cb1262d2e9044037fae2b213d3c4d85e1a22712a4af3c4ded3fd4866879c890a89d2878a00aa44232ea17f41e4d8284699bbe8765fdbadc516955ffc8ae93cc7add2adf5eeec4f05e65a240f3eb24479e665c54feb0053d772a5988531a63bb84252b447b52389bbd40e5d51244895e6deee21e7da0c507fd99e9d1b8d29993e376
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Worm.Vobfus-9982088-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: services 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: services 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: services 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: services 25
Mutexes Occurrences bs_pxy25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 173[.]192[.]176[.]13925
Files and or directories created Occurrences %TEMP%\win32hlp.exe.jpg25 %APPDATA%\win32hlp.exe25
File Hashes 01a927c98d1a6c4a6b4ec9a07772d16aa2e141c0713f28a9142da88dccd4661c01f6f311e250412bbaea712cf20a1bad3d033499d6b9feb1989c09d0d3b52bf5029f0cdafcd1e43c80b328a4149b9351f768a26db83aafcc2e679576302571cd032fe6ac96f6fb21fd01e2c0c146511f55b7a698f4520b2baa98921bed2192ca03c81f2f1bb42eeb694a778e87fd3e5b44cd81f91a2604f4504443749063841904149273008ed5b1aef18a5196719295e65ad049481432f5e5628a1de1208082044ca0f0a7948140f562cca6dca7177adeb4a740d195f03a870577f7a772299b052dd08dd67d615ac889ac38f34619e11f1c397471d2eeac5b9d921006aa193d053662d3d28f0490b893404303c9eb8279c59774c54c8a119b56e0dd20500140053f3008ebc5891beb7724ef27cf68da91289440de7e59b20f104398fa8288e905da1dffe77ae855f9ce7cb1f3ebc32d9701ba5e28654a04d5700ff4c75d9cb2075f636f08c1f017ab277e97a3ae5cd1bce9072f03a5bdaeac7c5500ad390acc07c6f9532ac8e9ac978c8a4d344d2cd92212208f8cad3f88d31f06ed89dd1e9e0aabbb55d700442b8fc073e529488352830242b18501c1932bb8d01d0ca316e90b10a7c650b7a702f86164af756af70372649e9f071e5dc60d3da73479902df80b52d2766c544cc0c0ef432e4e01a02f04e6d31dbe52f416a6ab962a4bb61f070bd49c63bf53de7d8c6efc3a1756a68041fba3c8e15fccf7266a56f972edc1df0c0a92c633f18385cb8502537836777131f0e9bdbf7a3e13a6eb4369f6b27b010cdc5acf471fc39aaea4e1de4b35b97647048a306e19221da5ac4796295650510d23312c0f80a322e11a114a700ebb97814d29deed5c90dcbb76f404052ad0b40d8f470ce4a58ab6bff8f30531f2e423b7eb9c835aeb105fcf06c9416fb5a96e0ece757c57f02ee83048fa87cd7582427f2fca256231182d0fa7dfb4708cab541027dd8ba0228dc47765f32f6328f3bfde47585b5870ef5e59791ed6667a741910c34e5c3a0aabfee083318141f9452e4cc60cad310a2dfc1a206fc83d5132b61165b40f6d4dac6d2c478553fcaaa541306b8246684108e001618238c4d3abd5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Remcos-9982549-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKCU>\SOFTWARE\WINRAR5 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 5 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 5 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 5 <HKCU>\SOFTWARE\WINRAR Value Name: HWID 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: windows 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{L501JP3X-C6PC-RH36-475X-RS2C2OQHHGS0} Value Name: StubPath 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hpsupportdf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: windows1 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{256C14W2-4307-17L5-O833-2WK3KRN38HN2} Value Name: StubPath 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{256C14W2-4307-17L5-O833-2WK3KRN38HN2}1 <HKCU>\SOFTWARE\HPSUPPORTA-PTVD521 <HKCU>\SOFTWARE\HPSUPPORTA-PTVD52 Value Name: exepath 1 <HKCU>\SOFTWARE\HPSUPPORTA-PTVD52 Value Name: licence 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{L501JP3X-C6PC-RH36-475X-RS2C2OQHHGS0}1 <HKCU>\SOFTWARE\REMCOS-7AHD4U1 <HKCU>\SOFTWARE\REMCOS-7AHD4U Value Name: exepath 1 <HKCU>\SOFTWARE\REMCOS-7AHD4U Value Name: licence 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 106f1d501242121b596cc520a89f0523397ced37435e8d4d81a5d57cc1f03714 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 106f1d501242121b596cc520a89f0523397ced37435e8d4d81a5d57cc1f03714 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Registry Key Name 1
Mutexes Occurrences -2 A16467FA7-343A2EC6-F2351354-B9A74ACF-1DC8406A2 Remcos_Mutex_Inj1 RV_MUTEX1 Global\<<BID>>98B68E3C000000001 Global\<<BID>>98B68E3C000000011 hpsupporta-PTVD521 Remcos-7AHD4U1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 38[.]26[.]191[.]784 79[.]134[.]225[.]1201 185[.]165[.]153[.]2211 35[.]205[.]61[.]671 185[.]165[.]153[.]291 172[.]82[.]128[.]2401
Domain Names contacted by malware. Does not indicate maliciousness Occurrences onlygoodam[.]com4 adiill0053[.]ddns[.]net1 manerck[.]com1 fuckusa[.]info1 werfcdxv[.]ru1 maccfund[.]duckdns[.]org1
Files and or directories created Occurrences %TEMP%\-<random, matching '[0-9]{9}'>.bat5 %APPDATA%\Install\Host.exe2 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\desktop.ini.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I62TWBD.ppt.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I6FGW9N.exe.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I6FZORX.doc.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IABMX83.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IAJ2Y6R.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IALGTCS.xlsx.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IAPSNOM.tsv.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IGORSF7.xsn.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IGTBBSA.accdb.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH49RPF.ppt.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH71GGR.ppt.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJKODPH.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJP965K.accdb.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IKY5R3M.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IMYCSIT.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$ISLP722.doc.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXLC77A.pdf.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXUL2U1.doc.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IYSR1FU.ppt.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IZ2GMJW.XLSX.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R08BO8F.xlsx.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R11KHR4.doc.id[98B68E3C-2275].[checkcheck07@qq.com].Adame1
*See JSON for more IOCs
File Hashes 0350cbfc4ff5a579a459d6ceff060d5d157d30f20fb451a94d82166631f18066106f1d501242121b596cc520a89f0523397ced37435e8d4d81a5d57cc1f037141e8ae5b358c8fcddc3e25758e2f49cb2b04ad661376022d9aaaa1aaecfb663c02a32b8c6cbdb61fd362baeab2cb9aa210dc51c6880656c14b9b36c50766582d22c1d66b0c4fab913bdbf03ddd3531a42963ac9ab30786ba67b25bca9bf703e952dbedfaf6e8b284906dc6545d481179baecde8b6e9e45dde980a0f286728897832a994ef75ffd4d823dbc85c190ed550194069ae7bce1e27828787979163ebef3ee249d38bcd7508c2312dcee9bf12168acfb0cb28065d51b4de0a5cd7699b574002487bcf5cc47ef93f8c28d48317df97a3ace3d956e4eb7eab11e5b732b1944cc637037c1f83181100f96402f254ce2bda39883588abf568a8d5bad2f4314e570532881997d16da4d18b37254530c7b501d4d91569d378234e636b1bfa3cf56b41117c6e33165b8ec66a7d30160c7f064f30bbf6bd21f117c7f016d5a0bad373cdc18ea1c2aa331faa0ba95fa505b4cd5e53f8229cff6aa9811f19099b84ef801b7cf336dc0f2d9dc8230f512482953f8286675a996416087edeb5cf0058838ea21f50c905a9dc0d76f2548961deb079607ee8af7bf8d1c54bc3bf2e794cc8a1d387233338d48539c3e00ac93eb7c527078ff14c3d14d5010a4c54a1a7e33ab267b1e0b3c64b88c9aa3b76b0ae2554612cc825490c7c34548be40ad77cb45ab748ff3fcf567b0d53fe1feeede4f88168427e38b8473bcc03264ac8e0c86721da0bd85734cdbcd85debc29e899728fe67995b62b10c3d433246cbf85006cd82df05fa9eb29122af6c45f533a41fbd33d22500c1107d2d3a8b368fa8f68a11e4e08b7135304c934b96d5fa6ec1a73f94bbb45e77558caee1b937c3b7d048baae
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Bifrost-9982192-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Bulas 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: FW_KILL 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: XP_FW_Disable 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: XP_SYS_Recovery 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Online_List 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Port 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: LanNotifie 5 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: DirectX For Microsoft® Windows 5 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5Y99AE78-58TT-11DW-BE53-Y67078979Y} Value Name: StubPath 5 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Shell 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Tport 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: ServerVersionInt 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Mail 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: KSil 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: ICQ_UIN2 5 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS5 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5Y99AE78-58TT-11DW-BE53-Y67078979Y}5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT SCRIPT HOST\MICROSOFT DXDIAG\WINSETTINGS Value Name: Hata 5 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 4 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 4 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS Value Name: Start 4 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS Value Name: Type 4
Mutexes Occurrences ASPLOG4 DENEK4 _x_X_BLOCKMOUSE_X_x_2 _x_X_PASSWORDLIST_X_x_2 _x_X_UPDATE_X_x_2 Administrator51 Bif1231 Local\{D45184B2-D44D-4D99-931B-B84626BC5EF2}1 Global\71448401-8e57-11ed-9660-001517baa3de1 2AC1A572DB6944B0A65C38C4140AF2F45c0722274681 2AC1A572DB6944B0A65C38C4140AF2F45c0722274901 2AC1A572DB6944B0A65C38C4140AF2F45c0722274A41 2AC1A572DB6944B0A65C38C4140AF2F45c0722274CC1 2AC1A572DB6944B0A65C38C4140AF2F45c07222758C1 2AC1A572DB6944B0A65C38C4140AF2F45c0722276DC1 2AC1A572DB6944B0A65C38C4140AF2F45c0722277101 2AC1A572DB6944B0A65C38C4140AF2F45c0722277501 2AC1A572DB6944B0A65C38C4140AF2F45c0722278281 2AC1A572DB6944B0A65C38C4140AF2F45c0722278B01 2AC1A572DB6944B0A65C38C4140AF2F45c073D961341 Global\7970dca1-8e57-11ed-9660-001517f0cb6e1 Global\8aa08521-8e57-11ed-9660-001517ec56121 Global\82b4eea1-8e57-11ed-9660-001517d6ab3f1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]237[.]20[.]141 23[.]222[.]236[.]331 24[.]201[.]72[.]1611
Domain Names contacted by malware. Does not indicate maliciousness Occurrences jrpg30[.]no-ip[.]biz2 vasadosvandalo[.]no-ip[.]org1 www[.]icq[.]com1 racker[.]no-ip[.]org1 jrpg30[.]no-ip[.]org1 racker[.]no-ip[.]org21 jrpg30[.]no-ip[.]org21 tallmaster[.]no-ip[.]org1 tallmaster[.]no-ip[.]org21
Files and or directories created Occurrences %SystemRoot%\services.exe5 %System16%\sservice.exe5 %SystemRoot%\SysWOW64\fservice.exe5 %SystemRoot%\SysWOW64\winkey.dll5 %SystemRoot%\SysWOW64\reginv.dll5 %SystemRoot%\cmsetac.dll4 %SystemRoot%\ntdtcstp.dll4 %APPDATA%\addon.dat2 %SystemRoot%\mstwain32.exe2 %SystemRoot%\tkjn.exe2 %APPDATA%\8570673.exe1 %TEMP%\njq6086.tmp1 %TEMP%\Kill1.exe1 %TEMP%\Kill2.exe1 %SystemRoot%\3790487.exe.bat1 %TEMP%\1878931.exe1 %TEMP%\7582623.jpg1 %TEMP%\gjq6344.tmp1 %TEMP%\PROGRAMA iTouch.exe1 %SystemRoot%\1068842.jpg1 %SystemRoot%\3790487.exe1 %SystemRoot%\7981640.exe1 %TEMP%\6118084.jpg1 %TEMP%\6221277.exe1 %SystemRoot%\SysWOW64\FGOIKG\AKV.exe1
*See JSON for more IOCs
File Hashes 16d1317d954506fb689c594e0dbea407c5d224882d02ee9c97944ecaf2aa815e2580b7e5ab9ca31e8dd146f1e5e3bde58287794e4c876ae6e74ab2b93f38fc90288990debffcd3adb7af4e84c86f83e49f1c3726b95f61bf84fded46fbd74a772e3cbe941ab655a6d3ea57382028a75794ebd7895dfaba49ac3aad78921f172f3c39945e576bdfe9a878b8543c925bbd48f03a778c4f4aabb50362aff6340bfa43931b0b9523f9f80e6846838495bfcdfac29b4ad4f47e24032ac02c1d0158f248e01c9d590f702876d78f5c7eb7c6d1473174c062e34aafd496fbccfff530ba4ce9d9c4d2bb24b5e1f2c7429f2fcd04096ee3038cf7bf3f1ec33d040a4e37fc5d3988d3e1f179c521916b9cab44bf663dacf9a4eb54065475f7619a89a8516069780d868e9beee05b3070af2dfc55e953ecde1d826aef0ec27cbbe8ca32ef146b11b23dbbc86681e47b0aa7e8406d7782e790ee187020e46762312c4cc8b9a878684bb61de2e43084294d8e38974d3e5150174fe5f0282c40ef701d5d621ab77deb18fe91d5c043b06f0d7cb3894176b8eaf26b76f3cec14aae17bd91facb8ab780a6616b56776be514c74c969be3c2b51acd03b81f3ace8d666d5d4b0d1febbf95dc1c0b1b6c234eb8eac2a967c38adbf28bf9aa22558aff970fc92def0813c4736cc96c32c48fb86a39d47b5732dc3171f71c0d48033cb1d4c9e62f0b08eae9bf3013a7a3985eb4c658e8973147c70770e96edb70b12faa77ea469312d0bdefc1da346ba66ebd0defb0be5cda235c16116b24778ad2ec386de715bec0bcdb
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.HawkEye-9982173-1 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Update 6
Mutexes Occurrences 3749282D282E1E80C56CAE5A7 Global\<random guid>3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]154[.]367 104[.]16[.]155[.]366 208[.]91[.]199[.]2241 23[.]94[.]43[.]901 185[.]128[.]81[.]1191 202[.]66[.]174[.]771
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com13 smtp[.]decemberdonreach[.]com2 www[.]traucotravel[.]com2 sahakyanshn[.]com2 smtp[.]wanjiall-group[.]com1 us2[.]smtp[.]mailhostbox[.]com1 smtp[.]millionslogs[.]com1 mail[.]mmt-me[.]com1 smtp[.]esrgroup-au[.]com1 mail[.]salesoffice1[.]com1 mail[.]hoordesign[.]com1 traucotravel[.]com1 jelimold[.]com1
Files and or directories created Occurrences %APPDATA%\pid.txt13 %APPDATA%\pidloc.txt13 %TEMP%\holdermail.txt10 %TEMP%\holderwb.txt9 %APPDATA%\D282E17 %APPDATA%\D282E1\1E80C5.lck7 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c57 %APPDATA%\WindowsUpdate.exe6
File Hashes 25c4e0e82248fe0f5eeaaa95ad509506e3ccebd87fa0b15fca2ca8e57f3e935530f98993c65d34b131df1de518b36914a4796d81a2cd97ff11efe20762052da95eb97290859f48710c13870e7008b00d27cd4fe5356619686d5377f864899be366d6b9f856cb4503446868cb31573c59dca8200426313934904c53d9821dc60d6dbb8e520f4c1e900e5d4f567a307ed846744c65faddf1dcc357411e8940d82a76752746dff742dac1f13faf8bf9d240a72b6974bdbc5d601e686718cde47de296afbc589d7d92a6568fa6a94b504d06be2a2d2b4e550540c3dd6268d50bb8239788c32ecfef8e2b6da49031079ff4014c626a5e2e28c7766fc12d9586828f5bb5e56bfc568d14950603308e17f3a5f2f40ba3575e97fae249a7fdb3f5357417bb51ebbb114d1771cf6648ed5eed18101e778cf4e5f9a2df1c4fed4c7998c8a7c8a07d72b1c68766407d754905e8b5d062152353d539f2ecfca13405308578f9c9d12b61c5fddd1bd91b6dedd56a41cdd0f0d5d065c34fcc1036de3716db0c88cd8a09b53f5e31666fad4af2ec32f8c48ce597ea4cf52e34a915b918dd148295d054dac92b28a478c46ccb71e304bac5ec172c2102b354c1e1298b0a5ba10bf5d1adb78134362a121474f955c2670fc4b675531d19c847d74a3d77fb660664a6d1e152fbf3252cc888ae7fa5e5b410153757243400c52f757963eb1da5d20860d616790f182767501f232ffea535d2c8c6c064d5b18fb05a9a9f2fa00ad87fd8e1bca0dbdf1b010b736edfe3fe6e2b6fc95f57c6215ff7c518394da624187b02e69bc21e37452867be7742b580edb17e41044c248816fc86155f74b2dce842eaef4dd196050818e15e47d2532912cdb6669d0cec9ca8f369aa3fc60eb8b3eda1
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TrickBot-9982207-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EFS Value Name: Start 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: ShowCompColor 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\EFS\CURRENTKEYS Value Name: Capabilities 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\EFS\CURRENTKEYS Value Name: NumBackupAttempts 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\EFS\CURRENTKEYS25 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES25 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINDOWS25 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE25 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINDOWS Value Name: UniqueUserHash 25 <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CERTIFICATES\36CA11DE9886E4D13A82049E967E9A354BA648662 <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CERTIFICATES\36CA11DE9886E4D13A82049E967E9A354BA648662 <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CERTIFICATES\36CA11DE9886E4D13A82049E967E9A354BA64866 Value Name: Blob 2 <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CERTIFICATES\36CA11DE9886E4D13A82049E967E9A354BA64866 Value Name: Blob 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: PATHPING 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: PATHPING 2 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: PATHPING 2 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: PATHPING 2 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: certreq 1 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ARP 1 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: ARP 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cacls 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: cacls 1 <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cacls 1
Mutexes Occurrences CTF.Compart.Mutex.{40873C05-0BAB-1575-53E7-E3B7E9D4CC75}25 MSCTF.SHARED.MUTEX.{7F088249-2BED-DE54-803E-53B1C3A674AF}25 Local\{6F884C5F-38C5-4662-BC91-53BD684CCB0D}S-1-5-21-2580483871-590521980-3826313501-50025 Local\{A55C3BEE-5BFF-4c61-8833-39CD46D49BC7}-1-S-1-5-21-2580483871-590521980-3826313501-50025 MSCTF.Shared.MUTEX.9cb030d925 MSCTF.Shared.EVENT.3e261e8325 shell.{C41FA798-DCC4-AA56-599A-737C5A6CFFA8}25 MSCTF.Shared.MUTEX.4acf71e125 MSCTF.Shared.MUTEX.c4db82e025 MSCTF.Shared.MUTEX.b45dae0d25 MSCTF.Shared.EVENT.4d29acca23 MSCTF.Shared.EVENT.c6bc01be23 MSCTF.Shared.MUTEX.4d29acca23 MSCTF.Shared.MUTEX.a694d66523 MSCTF.Shared.MUTEX.c6bc01be23 MSCTF.Shared.MUTEX.e35e00df23 MSCTF.Shared.MUTEX.10e27d8123 MSCTF.Shared.MUTEX.1ddf8ea223 MSCTF.Shared.MUTEX.2144df1c23 MSCTF.Shared.MUTEX.273b139623 MSCTF.Shared.MUTEX.2e3f926623 MSCTF.Shared.MUTEX.380fe35523 MSCTF.Shared.MUTEX.60d05f0d23 MSCTF.Shared.MUTEX.7722440923 MSCTF.Shared.MUTEX.80b41a1523
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 217[.]23[.]9[.]20625
Files and or directories created Occurrences \System Volume Information\EFS0.LOG25 %APPDATA%\Microsoft\Windows\dllcache25 %APPDATA%\Microsoft\Windows\dllcache\drivers25 \Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\StartUp25 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp25 \{40873C05-0BAB-1575-53E7-E3B7E9D4CC75}24 \temp\localsystem.txt23 %APPDATA%\Microsoft\Windows\dllcache\Magnify.exe15 %APPDATA%\Microsoft\Windows\dllcache\NAPCRYPT.DLL15 %APPDATA%\Microsoft\Windows\dllcache\fc.exe14 %APPDATA%\Microsoft\Windows\dllcache\ubpm.dll14 %APPDATA%\Microsoft\Windows\dllcache\takeown.exe14 %APPDATA%\Microsoft\Windows\dllcache\WEB.rs13 %APPDATA%\Microsoft\Windows\dllcache\w32tm.exe13 %APPDATA%\Microsoft\Windows\dllcache\eapp3hst.dll13 %APPDATA%\Microsoft\Windows\dllcache\rasctrnm.h13 %APPDATA%\Microsoft\Windows\dllcache\t2embed.dll13 %APPDATA%\Microsoft\Windows\dllcache\VAN.dll12 %APPDATA%\Microsoft\Windows\dllcache\cacls.exe12 %APPDATA%\Microsoft\Windows\dllcache\QAGENT.DLL12 %APPDATA%\Microsoft\Windows\dllcache\KBDBLR.DLL11 %APPDATA%\Microsoft\Windows\dllcache\JavaScriptCollectionAgent.dll11 %APPDATA%\Microsoft\Windows\dllcache\rasautou.exe11 %APPDATA%\Microsoft\Windows\dllcache\l2gpstore.dll11 %APPDATA%\Microsoft\Windows\dllcache\ucrtbase.dll11
*See JSON for more IOCs
File Hashes 010f84deb5e78bad41895e882203db172819778c5dfd28c26eb079e8be50d77f06dd24c4205cce7274c8b332e34abdc1cf6064d21bca8fc4407cd6cf075cfd090b6a83489612fbac0c8031c717c2ef806d1ab504ee882a4e83700bd277684eca25473161969a5ce442ced0c778e677792b07fa68fe500734f7fccab735dfc6ac25e7e21526add1508c644c31cbbffd221068779ed6fb1bae751a9a70c6133fd325f2be22535798e48ea2b92c08da3e62f15569f1f67bc45889d7dc403a2c5bf82d3ae3b2189a6ad6436f046c4dc4e30509132e0a0ae08175a2299105f26277ca2ea0fc4ce00afe714122a10fb44e4f8115724e56c88654b2c0bd0dd952db6b1a380b798da49861cb0cb551a7b945f8db7e3893402c2423b6f9ebac784c79abf63a65beafd1115dd9343e3204fe9b53dde7e76d269804ddfcc95d6b379c9a081b3fd4e4bc06b0c735ecb690e317fd0954b0b9011e6e32980e04af7611b938ec2c4038edea39f0d2c4155b1917759beca2f9fc8150a48d7e06a1b3e7b9b72652ae41892f3328b48749726630a3e75ee0addd7e41060beefcfc9d81d3bfc3ab55fd529883d5b3a9935f3863fcf277ed10086645b2c94e0363276358cd2af9dc5dc15685ddcb62cd05ed44dd16b1e9004f1c63a5cd8965ccd19089a4fda044a48e815945310e811930231bf36f6d6d34af46bef97aa4d23e6adc1911772f7b0f829963ca73da5b67e40b82967d71e3b07aed7a17de020d0a009ff5838cdef5955c0d6f48cb7449083ebf82b8507d3d32f30fe8d76f329babe728d8bc94628a8789816f5394ad933af9c28c7eefc6c62eead20d8e3ecf5ebe40b10d81f74d96d1dfe1723bc475c228b18acec71d248f9b79b189fa8a84d6685ea5b4b42cba55a7c9ab87ff71bee735095c209afefc60cda504cc77acc50fc4ba31d756c9ea4c853a89a3c04866cc1b9024efa30842042f2e50337a6cdb7a77776784ad25e322cf93d7a55543ec1b6966095c16d18874123733518b24859d943412b346bb1c1bc2aa45aceca08c357c2da59b3a311c8b3199ac1d7d903c03c14b6f35f84d77b76c4764b29afa8695161d81edf54df2f6c36c02bb81fdd109f0000b106cbafe4bcd27a5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
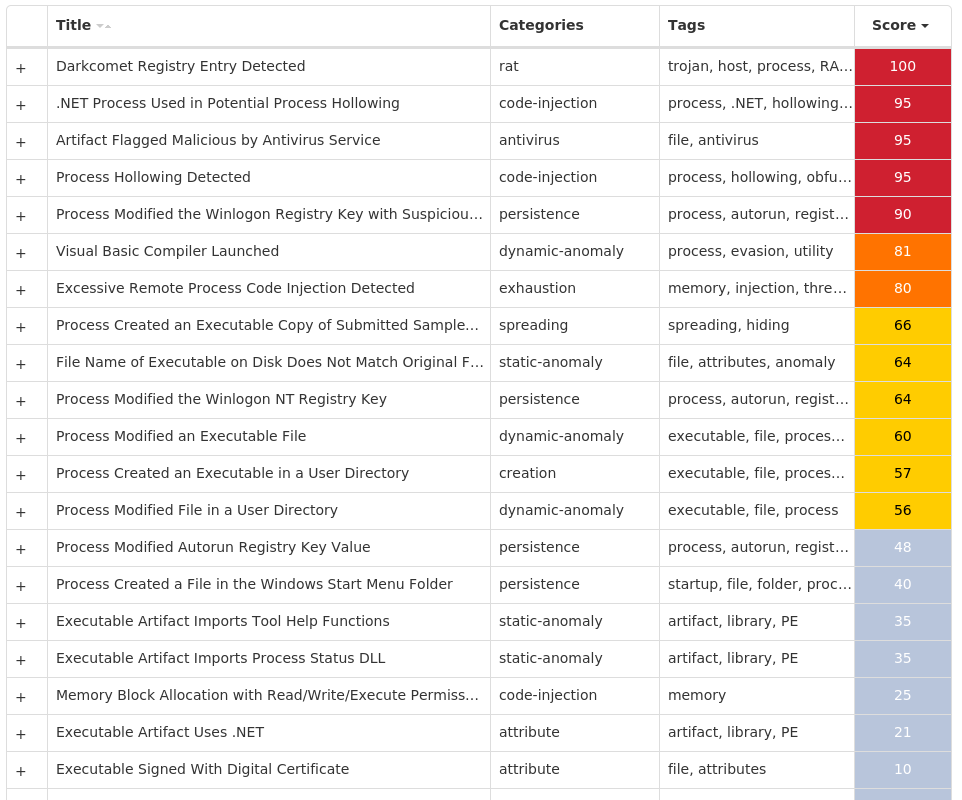
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.DarkComet-9982401-1 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC22 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 10 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: DarkComet RAT 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableRegistryTools 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rundll32 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableTaskMgr 1
Mutexes Occurrences DC_MUTEX-<random, matching [A-Z0-9]{7}>8 DCPERSFWBP3 DCMIN_MUTEX-ZDY0P6P2 Global\27d1fa40-3def-11ed-9660-001517b8248a1 DCMIN_MUTEX-BMAZJU11 DCMIN_MUTEX-MG8WJXZ1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences nitoh95240[.]no-ip[.]org4 epiclegit[.]no-ip[.]biz2 nzarkatar[.]no-ip[.]biz1 faffa[.]no-ip[.]org1 c0san0stra[.]zapto[.]org1 jonshouse[.]no-ip[.]biz1
Files and or directories created Occurrences %APPDATA%\MICROSOFT\WINDOWS\START MENU\PROGRAMS\STARTUP\<original file name>.exe15 %APPDATA%\dclogs12 %HOMEPATH%\Documents\DCSCMIN5 %HOMEPATH%\Documents\DCSCMIN\IMDCSC.exe5 %HOMEPATH%\Documents\MSDCSC3 %HOMEPATH%\Documents\MSDCSC\msdcsc.exe3 %TEMP%\MSDCSC2 %TEMP%\MSDCSC\msdcsc.exe2 %TEMP%\W63.JPG1
File Hashes 1ee3ae7119ccc045cefe6de4f99f2da69f05d244bfef964795a9e9b08163ad972d197747e2c5dc2d172bc08b1e7f3c1adf070c342acf4d524bfdbd8b1b5597fc39394d1402d67eeaa0e5dbe61c39ddb887d967580ce519f0d894e6925dd15da23ade4b5dacf560174f328d37199a1587b815648c677ff60905a1749ae2709bdf3c69bc8c19135271b0a5351654fa3905409f966a3190c660944a3071b73d6f673ddf068df01a2a27689c0386d1628dd73e78e662da9c578c2e0de46e3384c7d749b6c061933b71658c922c59a0875de71f39658f8eb6fee4493edc7ee16025a852f80fa0b078474e2c96e6127c4d14ea37c6045fbba9c26b36d2f4176408f020565c7f5cbaa6186e1f354dccf3b282876e5b0d3e4a16c47775928eec17bd031b5d3a530dc4e2239faff995c18198c52c43c5611e97c85d9f6d8153ad17c95ac869fb8a4b0dcf843b488925a12a664f506866b4def4306a5b95d02f0ac57c5bb0764a0fbece5bfbd92ad83afcdb96beeeacd9175fedfdd5bb2a177bf0ec1ab2ba769bfa392f99e29441cdbfb9a47024806f2574afde5822bddb8e25b7122935008a59869489013c041b79d313315d2030adb6cfcbb78ddf78c731bb29c9b7e74f8deac01f364bdd60a29d2385f3553ae181a2b37f9f8793ca163de7e50a5d0603b2eb151175905dbe1798d4052078de1ae3685e874b790175faf427c8e7981b11cae04ea9a81ce99fe9852967df998f3fda7c9f6df4fb028fc5a56827966e4a12ce191b65e2561192f86e3cc1203eac5905716ea931d9643207bece43d7bb927cddb3d1524e2951e0c194dade6c8aaf4af115e049454011951e754c6bfeffa7e7e03cd6c401eaea3f3979c3a968c8d86f95971102280c3c9c07555f183983368bf02897fc5ec543ee341e92ef6e33466e6903204695d5422edf762df3f8c863ebf76a9981c1aaf80aa7697887a25b0af110080b1871eba5a4123ed98c4636c183ff3f26a70e9dd751e0916718d8fa35d37011829501eeedbff292f779fc5093f5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Shiz-9982208-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 24 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 24 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 24 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 24 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 24 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 24 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 24
Mutexes Occurrences Global\674972E3a24 Global\MicrosoftSysenterGate724 internal_wutex_0x000004b424 internal_wutex_0x0000043c24 internal_wutex_0x000004dc24 internal_wutex_0x<random, matching [0-9a-f]{8}>24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]94[.]194[.]16924 13[.]107[.]21[.]20015 45[.]33[.]18[.]447 198[.]58[.]118[.]1676 45[.]33[.]20[.]2356 45[.]79[.]19[.]1965 45[.]33[.]2[.]795 45[.]56[.]79[.]234 72[.]14[.]185[.]434 96[.]126[.]123[.]2442 45[.]33[.]23[.]1832 173[.]255[.]194[.]1342 72[.]14[.]178[.]1742 45[.]33[.]30[.]1971
Domain Names contacted by malware. Does not indicate maliciousness Occurrences purijygirem[.]eu24 dimasyhageh[.]eu24 ciqofymosip[.]eu24 vonerymekix[.]eu24 novubymyvip[.]eu24 fobyqyhezem[.]eu24 gacucuhumeg[.]eu24 maxilumiriz[.]eu24 jelojujopen[.]eu24 qekafuqafit[.]eu24 ryhyruqeliz[.]eu24 kejepujajeg[.]eu24 tufibiqunit[.]eu24 lygumujycen[.]eu24 xudoxijiwef[.]eu24 pupoliqotul[.]eu24 citahikodab[.]eu24 direfiwahur[.]eu24 vowypikelaf[.]eu24 foqurowyxul[.]eu24 nomimokubab[.]eu24 mavaxokitad[.]eu24 rylupalyxad[.]eu24 jecekorosuk[.]eu24 qexeholagav[.]eu24
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp24
File Hashes 00a9f6bb07a133aff93fa5dfd009477e886e2da2fd0a6d41b19deb29e737c95006557ec3ed23a8540bbdf30feac70d64fdf50197ed543655bc86d9dc4ae40ca3150cd980f70b0ac30026ddc11726030e437e8d99f30526190d4647680ccdd8fa20fbca4e9d517b65d9ad39542de43f4ecf80d3f653f8d4748307dac7f4236fa2220c7b4e4ef91905ceab6f77684a404e73721eb23f32ffd650718ca9ddbfd21929fcea73b54b4a26583411eafc5ce2903b75111f530d9fb7abfac6ce01f69791336a303772ffa2db341afaa7b40557f9d8c7a32736cb13b9fc13ae1b9d13bdee4b0bd0dde73c84997a8421ebf0dd74ce9dafd6d7d366570bf7a516c5bc3cb4fa550c821409c3bc9b07552887050f73bdc2c4ee233caddd02966d6253acba38bc61ca67775b8fc5cdc5c29c93a58f7512c968a0d86dcd39bd5fcd90721f7ba28c783104d529b570eb73f9bc076c34c5ce762350481b1d402a70682a2e5a5a82897bc6edc2bbefcda6773e9971aca8737157b052155ca1b2fa3fb2f77e0c66da787bfd263a852f1ab102a73d13d291322ca36dc183093a713b07444fa93505439c7eef302158941c1bb82f0c4e04c2fd0e00c2c4cb3a726ddcfb44dbf928184a60800b61f1ab3fb1ec621d010899c02dc385ff7aaeae1917156177d4b62542a80a8c1b70702257d0bb944164fb0d1dd632052f97b372158eb8345886ebfee25e2f8f3a4f0679fb402e18f36fbf1ca9af09c3ba1065867aa3d66c833e71e5096a689ffccfa726c8f8dc8d5a907489613330c3835b8f72b526880edfe45c39701c32a3bf9835a71f576caecdee29e6a88eda042df5329f14eeb9bf1ab0efe4e384c6bbf195d48481ce62a1d2365dc61f7659dfe954fcd2632c4fee8e62658955e847bdc1cccd3799eef17fa58cabdee058b21633c275e78e79cf3ceddd744df9186fc295e1b17806f7c4fa05969f3d35774e47b728be43efb9d88a6fcfb0d5738adccc1aa7098b94c80c1cbed4629cfaa0ae0f782521d090bc294a2710b92db322a7cef4bbf70da8f02d496dcd38a64e5a08aaa92561c7df6319efb1e86701257369e03728e63ab6fcdf97ce09d26804de5dd939463d73659dcd9fa882dd2e940df0
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK