Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 13 and Jan. 20. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Virus.Xpiro-9983832-1 Virus Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Xls.Exploit.LokiBot-9983602-0 Exploit Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Dropper.Fareit-9983571-1 Dropper The Fareit trojan is primarily an information stealer with functionality to download and install other malware. Win.Dropper.HawkEye-9983397-0 Dropper HawkEye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media. Win.Dropper.Shiz-9983394-0 Dropper Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. Win.Dropper.DarkKomet-9984290-0 Dropper DarkKomet is a freeware remote access trojan that was released by an independent software developer. It provides the same functionality you would expect from a remote access tool: keylogging, webcam access, microphone access, remote desktop, URL download, program execution, etc. Win.Dropper.Nanocore-9984085-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.QuasarRAT-9983512-0 Dropper QuasarRAT is a .NET remote access trojan. It is an open source RAT providing threat actors a plethora of functionalities, including the standard features such as remote shell, file management, arbitrary command execution and credential stealing.
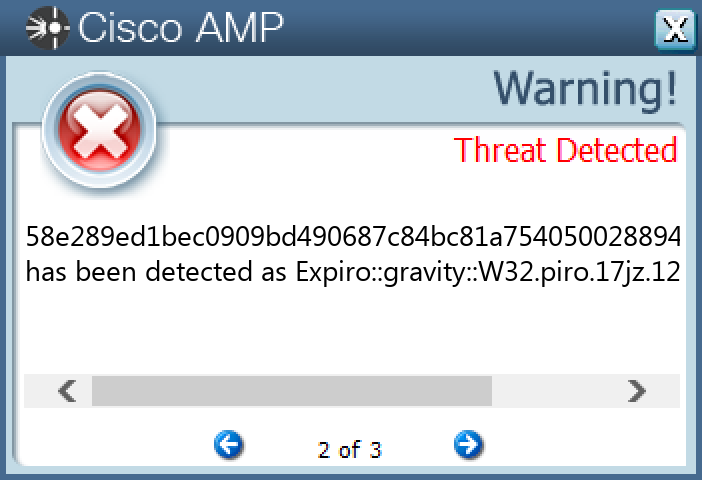
Threat Breakdown Win.Virus.Xpiro-9983832-1 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Start 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-50011 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500 Value Name: EnableNotifications 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC Value Name: Start 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 11
Mutexes Occurrences kkq-vx_mtx6711 kkq-vx_mtx6811 kkq-vx_mtx6911 kkq-vx_mtx7011 kkq-vx_mtx7111 kkq-vx_mtx7211 kkq-vx_mtx7311 kkq-vx_mtx7411 kkq-vx_mtx7511 kkq-vx_mtx7611 kkq-vx_mtx7711 kkq-vx_mtx7811 kkq-vx_mtx7911 kkq-vx_mtx8011 kkq-vx_mtx8111 kkq-vx_mtx8211 kkq-vx_mtx8311 kkq-vx_mtx8411 kkq-vx_mtx8511 kkq-vx_mtx8611 kkq-vx_mtx8711 kkq-vx_mtx8811 kkq-vx_mtx8911 kkq-vx_mtx9011 kkq-vx_mtx9111
*See JSON for more IOCs
Files and or directories created Occurrences \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE11 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.exe11 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.exe11 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.exe11 %CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE11 %ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE11 %ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe11 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe11 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe11 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log11 %SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog11 %SystemRoot%\SysWOW64\dllhost.exe11 %SystemRoot%\SysWOW64\msiexec.exe11 %SystemRoot%\SysWOW64\svchost.exe11 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log11 %SystemRoot%\SysWOW64\dllhost.vir11 %SystemRoot%\SysWOW64\msiexec.vir11 %SystemRoot%\SysWOW64\svchost.vir11 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\extensions11 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat11 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock11 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat11 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.vir11 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.vir11 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.vir11
*See JSON for more IOCs
File Hashes 14a816eca397542177be1b013a8550463aaada0e544428d833d79d247b918a044d4b1301cdc29373b5fdaa0b961117b4ea230f3182ff1033a50b75cb33cb673758e289ed1bec0909bd490687c84bc81a754050028894cad20e045ea684106f8763ef0e482f77540abbadc761522c8175d7e6f4b50a9932b0a98763f05916d9136ac332b34addca8a68fc3808e412bd094202cdae8b1f7f381931541030d1aca09b8f4ffb5c45eab8a4b1d2ddf7dca2d0e3c3a11cb9ff989ad78b18891ba4267b9e32c538f726a4dd30284cbe9427fbc3bd8daef548fddd35b9a0c1947028cba1b15b22c579087019a0bca33bd562bda64716b53854d1068024ecc2fd7db6a215b22d2e2f2850a578b83ab80b99f3c712395bd53b4d605f14396bbdb910089b3fb752731598528ea613850e0ad96c81ae76c9be21e6ab5b44928ce384910d0579c7fc0618631d7a46cd16ed17a0edf1ea25dd9d3766536ffb35aa74c0b2cae931
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
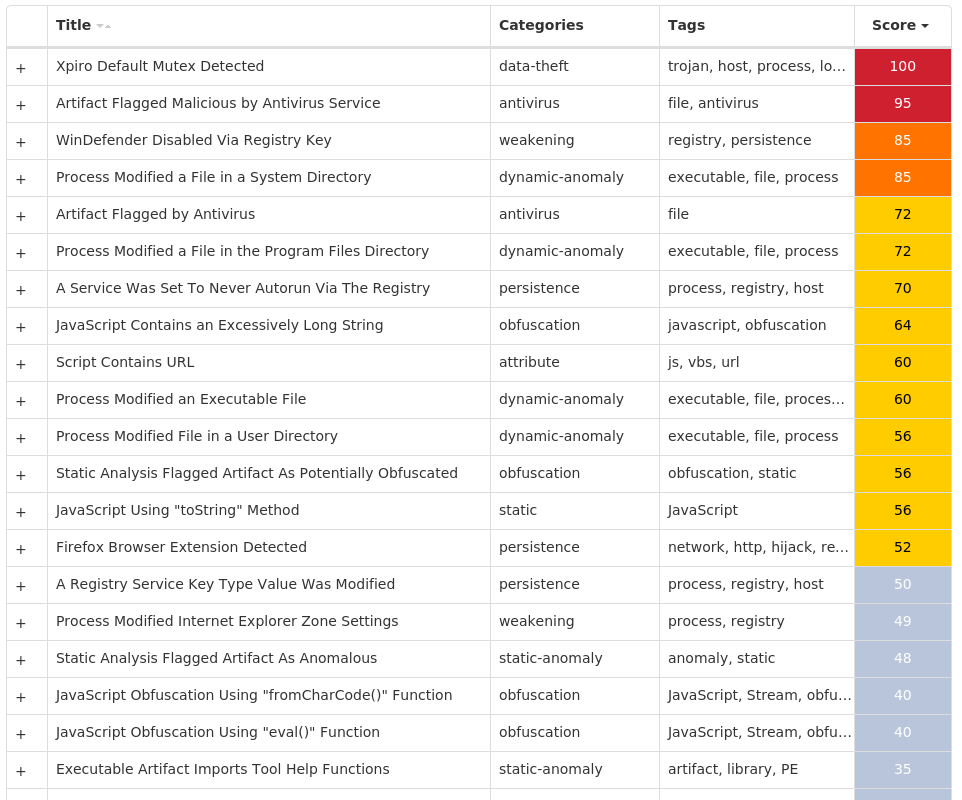
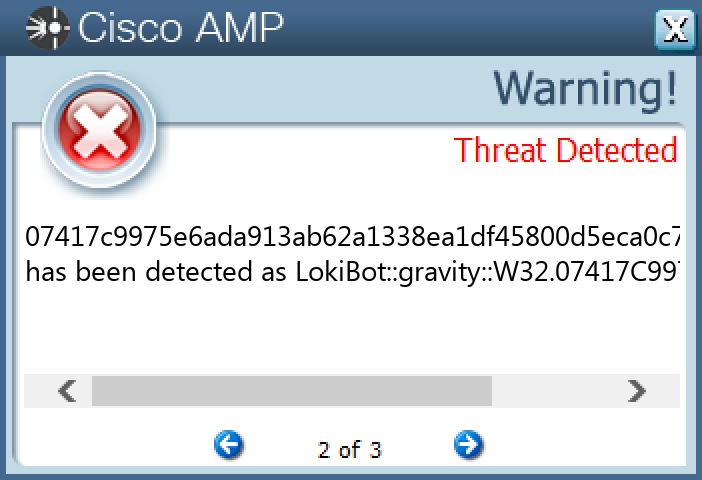
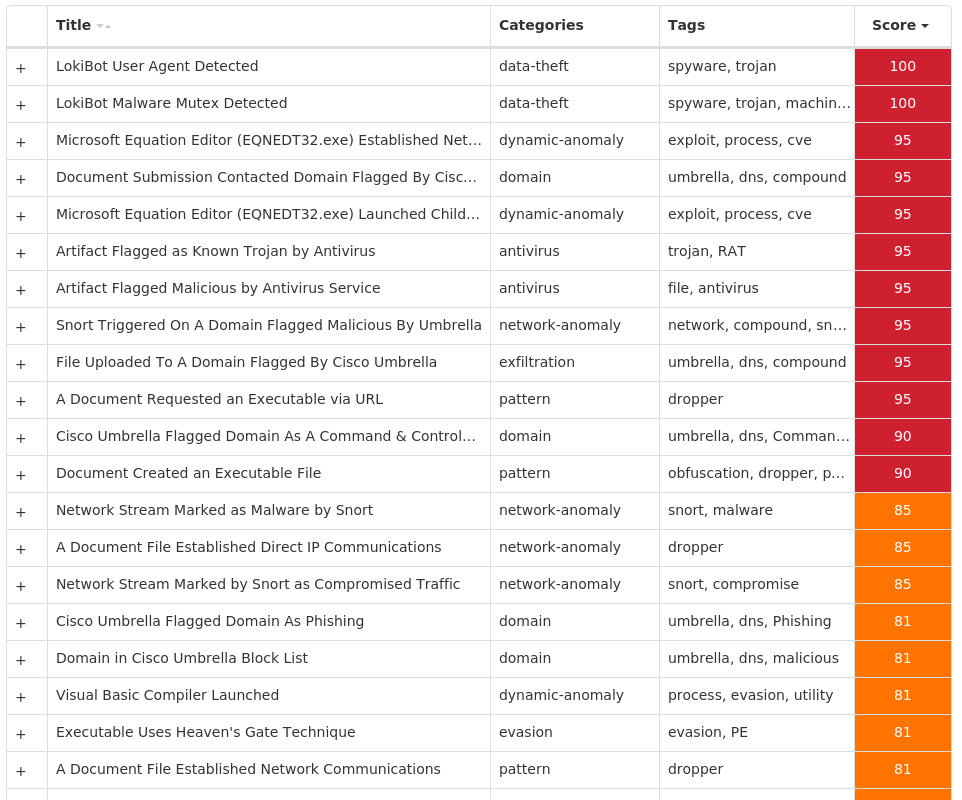
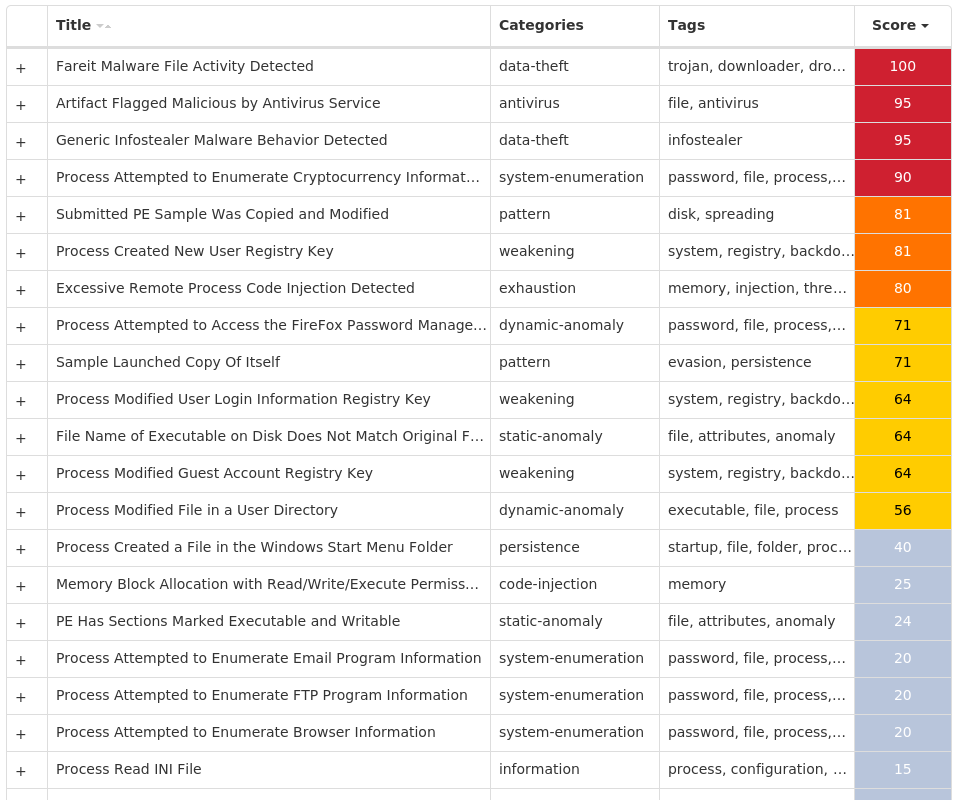
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Xls.Exploit.LokiBot-9983602-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 26 <HKCU>\SOFTWARE\MICROSOFT\EQUATION EDITOR25 <HKCU>\SOFTWARE\MICROSOFT\EQUATION EDITOR\3.025 <HKCU>\SOFTWARE\MICROSOFT\EQUATION EDITOR\3.0\OPTIONS25 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE21 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD1 <HKCU>\SOFTWARE\MICROSOFT\CALC1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM1 <HKCU>\SOFTWARE\MICROSOFT\CALC Value Name: Window_Placement 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\SADDELTAGENE1 <HKCU>\SOFTWARE\STANLEY1 <HKCU>\SOFTWARE\STANLEY\MUSTELA1 <HKCU>\SOFTWARE\STANLEY\MUSTELA\MEMORANDIZE1 <HKCU>\SOFTWARE\KOMPOSTER1 <HKCU>\SOFTWARE\KOMPOSTER\MYTHUS1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\SADDELTAGENE Value Name: Anabata 1 <HKCU>\SOFTWARE\STANLEY\MUSTELA\MEMORANDIZE Value Name: Hannss 1 <HKCU>\SOFTWARE\KOMPOSTER\MYTHUS Value Name: Udlbsdatos 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM Value Name: Implementing 1
Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786326 Local\10MU_ACBPIDS_S-1-5-5-0-6786326 3749282D282E1E80C56CAE5A4 1 irLbieSUCc1 8M65-UPTBHT-1F5Z1 8L30N9RRD4TG20Lz1 gsVeqYyojcjHvs1 qtHAQcA1 tKywdBwKac1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]3[.]136[.]1865 3[.]232[.]242[.]1703 52[.]20[.]78[.]2402 3[.]220[.]57[.]2242 208[.]67[.]105[.]1482 103[.]232[.]54[.]1432 104[.]168[.]45[.]1022 185[.]216[.]71[.]1722 103[.]167[.]85[.]1642 91[.]195[.]240[.]941 85[.]159[.]66[.]931 216[.]18[.]208[.]2021 208[.]67[.]105[.]1611 45[.]33[.]6[.]2231 198[.]23[.]188[.]1451 198[.]46[.]178[.]1741 103[.]139[.]44[.]521 193[.]222[.]62[.]41 192[.]3[.]101[.]261 103[.]171[.]0[.]731 175[.]41[.]16[.]1241 154[.]204[.]248[.]1371 199[.]192[.]23[.]2241 164[.]155[.]185[.]1521 145[.]14[.]156[.]1671
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org7 sempersim[.]su1 www[.]sqlite[.]org1 www[.]asiadesign[.]xyz1 www[.]easy005[.]xyz1 www[.]terratechpower[.]com1 www[.]porpubby[.]info1 www[.]glaaforum[.]com1 www[.]barefootcalzado[.]com1 www[.]bullcute[.]com1 www[.]hameaudeguzon[.]com1 www[.]allosteriacarpi[.]com1 www[.]brasil24horas[.]online1 www[.]hf9blwwuwpx7j8k[.]live1
Files and or directories created Occurrences %PUBLIC%\vbc.exe15 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp7 %APPDATA%\D282E14 %APPDATA%\D282E1\1E80C5.lck4 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c54 %TEMP%\ns<random, matching '[a-z][A-F0-9]{1,4}'>.tmp3 \Users1 %TEMP%\sqlite3.dll1 %TEMP%\CVRDF9.tmp1 %SystemRoot%\resources\04091 %TEMP%\sqlite3.def1 %TEMP%\nsxF2D0.tmp\System.dll1 %APPDATA%\Spisebordets1701 %APPDATA%\Spisebordets170\Tiltvingende1 %APPDATA%\Spisebordets170\Tiltvingende\ArtDeco_brown_5.bmp1 %APPDATA%\Spisebordets170\Tiltvingende\Hemmeligheden.Aqu1 %APPDATA%\Spisebordets170\Tiltvingende\Unsaluting.Str1 %TEMP%\nstD558.tmp\System.dll1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets1271 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets127\Thermomultiplier1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets127\Thermomultiplier\Fejekoste1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets127\Thermomultiplier\Fejekoste\Amidoacetic.Int1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets127\Thermomultiplier\Fejekoste\System.Text.Encodings.Web.dll1 %APPDATA%\Microsoft\Windows\Start Menu\Hematachometry\Optimumets127\Thermomultiplier\Fejekoste\media-playlist-repeat.png1
*See JSON for more IOCs
File Hashes 0096e380996a5c8896055aa0543c3f51bbebd5c1ea8178da1d67691a975cdbf7067c2a2f4c8344f55cae9cc1c6ba03324a4cc99ae5facd672d100c71f64233e007417c9975e6ada913ab62a1338ea1df45800d5eca0c73de33d1f53a72973bc60fa75b407da549a4c7e144216a5970b1c3803c74e57ebf433257c0d4381f34db10cd2aa23f0117fb286aba9f6a6ecbf7c467071881763d18c570574eed5b3dc82c585eb6a6b3d165c75312f0676e312fc0b1c9dbfd63ab4a060356669f605c903e8d8210b9d681c89f5df122c1598d4117b0c1843b706f7525039b5ba37f96af400e675021818214d2779c38b2d77b457ef9956518cd812b53bc7f41ca228bca57e5341a8009432af3aa5b4246eabb8774d292db8a245106fc045c4f36e5cddb7b34fede01164a6602eccc2e71a58535a8e484562fe634c82fcf87256f951bcd80bfd5671a9013cc4ba919582612f6d16076e0663990572188093e61ae40e2bd8126aa90f564c1662d9b42b333a7b0fe7489770c8b5069997b8dc5577ded2bc086fdff90584064c135a98f05986da5a03bd67abe414f1d8f5fbdbf424943001993a71008a2294209a986d896b26e8bcff214afc6923323687c9281919c033a919d6fcf6155af47fbacddd1f7feb457dc919f1ee29f3d28cc30f3c9c437ee516aa7225665972f421022ded04315aa75f15cda747e12dbd82130b1a8e87c9d062dafa915e7174b5c3da177ea2bc6573248a00d173dfe8f2ff8e7667557a3bf699fb66c265b35372a58775ab68db5392014be36b745f4647df6c3da1c0a7aab82fcb7062983e7667a1b86c1bd1123bc3aac29b7a8200b079c9bc4b566dd1c7ee44dc2745c75eefa6867cce4cc61d89d306810370e0958a550d039c5935e7012de71c9ebabe61d9c25500298ac578ba280ebb1b78fd2da07f32a82c44f1c11c3453ecc77dde534b4aa329ecf543351157ca8c9ee43730de6dbef2673d1f63f225f87cd0a74e966577953be0ea3d89be7467057d1356f5a8fc0f95a472fe938ca7ff5e7582ee773f6857a3f18e76453beefc46912089372f3b12bdd6e5735a3a3536de89082a08c246ba8e4bffb9ddb127a2ee24cef652e4b0a8772ad22d376a82eb7
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Fareit-9983571-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\WINRAR23 <HKCU>\SOFTWARE\WINRAR Value Name: HWID 23 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 23 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 23 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 23
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\filename.vbe23 %APPDATA%\subfolder23 %APPDATA%\subfolder\filename.scr23
File Hashes 02c648162f41e0ec54b1787c99bb274b484adeeaecbc99554fcd4428a276406e07ace7fc4681b7d16fd6a76364cbb679b4447128b77123424c788058659e07e20864a6c576429f1d5cb4a9529b016903bd8e368ae3c11527ef421e566b6b37ec0aaad800dbe8242fdc236b0d12cc3f0fade9c7d9ac02d2fc872f60075ec4dfa0143bee6fde9b3dee4f91e16e6925b6254848d9958f0c34ae1b8a5e7b444e8d6314eea17e15d2dd0092935ec71c98269ff4fe492eb6534b3c6baca1f48ea7376d15b459fd340458d8eaa5269296f9cfcccc3a3540942ef17f47637a73d59acc0a17704079963b83eb8a4aa50af808aa3f2facc1eaba7708b6715504806db95a64276fc674e4f232e25a17a67e53a98050265ec64a7698ad9bf56d3cc31ae0a7322acfbc4bb180b60e8b257795e5b66e51e3ceae0550a2187703d15dd9294716732c23d82a3f45947ef677c2a2a73d1900b27dc7a5b11c0e2464ad6270671c864c32a1ae5db46aeae9898d6c83a752d028b08e59b86f17c19e0d12287a5d42c85737a85828e7c787657ec66752d73db2ebcb85040b0fe9df689bb18067a304f95444bda2acfe872846b11d129916e66a5c158308266bbb2c5b4b659ae040bc672646802ef2d4c318d394572f84218f8bf385edd63699c5fb762aef10fdac0a48784a1371381fe29c6bf17b802e1671c3081687156df7c819fbe7bbe547dc3309a74b837e51f59054694d52f242ebc18a12a4ecf5080a5d7858032f7f968377ccca50b7ce25bf5591612540b416e12022f3284ea2de470eec1aa7759e9c0aa3469f5dd087571c55d345f926cbaee71f752052881f44f99e7712e491fa2ad349933c695aba9d911967937babbe5dbcf038ea43d67290959fbcc199cd1cac0f437ba0698540018cbc00b2136dcb4951190309375b01498265db094549593e9f335aed6e02c443b09119b78fce3ca1340f8bbf25380ba485f7fab41f3bd7d3bddc3fe670fb6ede7c66ae618cf6a2414d6e954926a9a83097607de52101f89e6606587e721968ba560a6e1d4def705be4279c5520a90015de5a08c1022448255d3d398e78f0cb383a71dd77a716fbe97052969ef11fc0fb4420dfad541d5e36a356f39f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
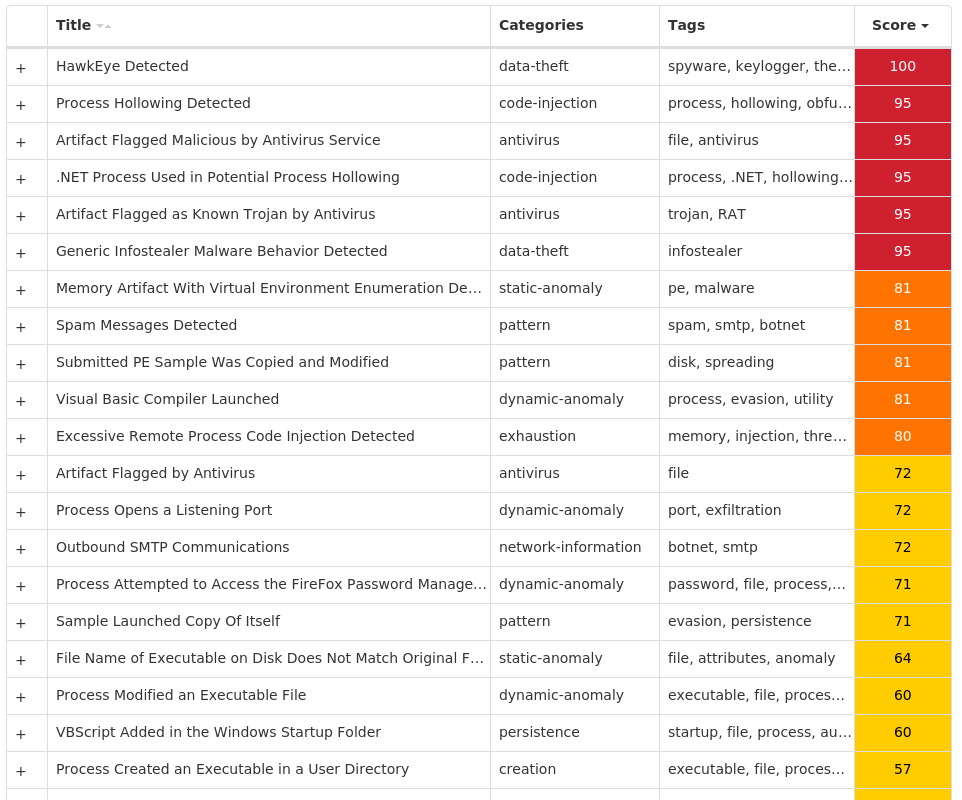
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.HawkEye-9983397-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 27[.]121[.]68[.]10915 104[.]16[.]154[.]3611 104[.]16[.]155[.]364
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com15 mail[.]yourstudyway[.]com15
Files and or directories created Occurrences %APPDATA%\pid.txt15 %APPDATA%\pidloc.txt15 %TEMP%\holdermail.txt15 %TEMP%\holderwb.txt15 %APPDATA%\subfolder15 %APPDATA%\subfolder\filename.exe15 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\filename.vbs15
File Hashes 00452dc6f78541178d6d024b47d0f4f928b17a9f14e770ebf0da15d87325737b1b583b41491e0c21eec87a0c150c234b5567906a42bd1b61ab1adb39e5b99efa1ea1014f69c680fcb2e23c10d56941508d7024bf04780b51e1f8d59bc45d2d87202ce3acdc22c7ad0761a03cdf5e15d593a4b0f6490815cc20dfed407b667f8622280734efa0e527d7517fec07479a955d5cc70128558ace13489311f3aae2fa3c04cad716a78717ddb48470b954ab6bce9feecdb3adc7a74dee8ecb9b62b3a44aece62cf34ce60c1f16d75140f47bc21bfcaf48da5a6f9eca0e48a43ff5b6d464b20ed5668241744570462e85987d91671fee3e0a94ca1546b68dd59df95997873645150140fc2f57e2e205d6b5e7d5b45fc35099d75eebe4b9a0989b98df0e89afbd7a372ee58c23edc29814c6faceeba8f7a9d82c0632a054577a491e748a8f10e57f73fc6f805908a3b36244ca92639500b5d08af601defd78498ec02b9caa264abc70a1d7eaf196bc83155a3764f5408b78e470f7bfa2fc3e81d60ee133c9d2b04de15964130afc80e4a41c7f71da8425302f6aa7297c7b0fad2cf09205f50240e0f888e5e17cabc3d088c04f2de75ef5b8acd20e3551fcc0dc26c3407ffe619680c0acc53af4ea30910cdc3bead472206ebe3c5eb040e11d4cbea07b4e
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
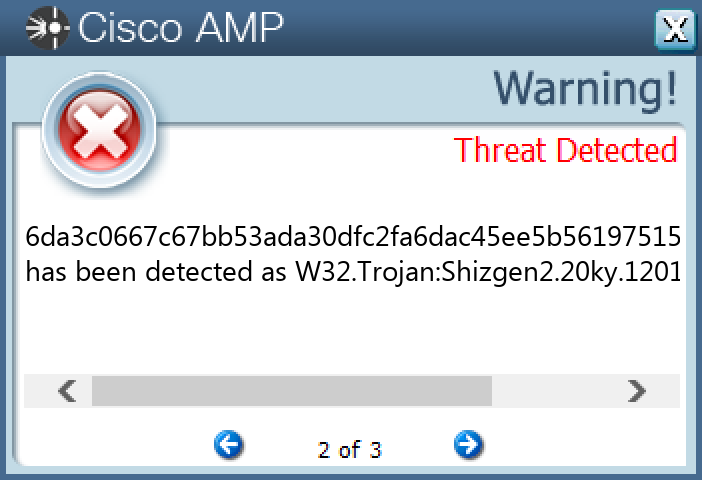
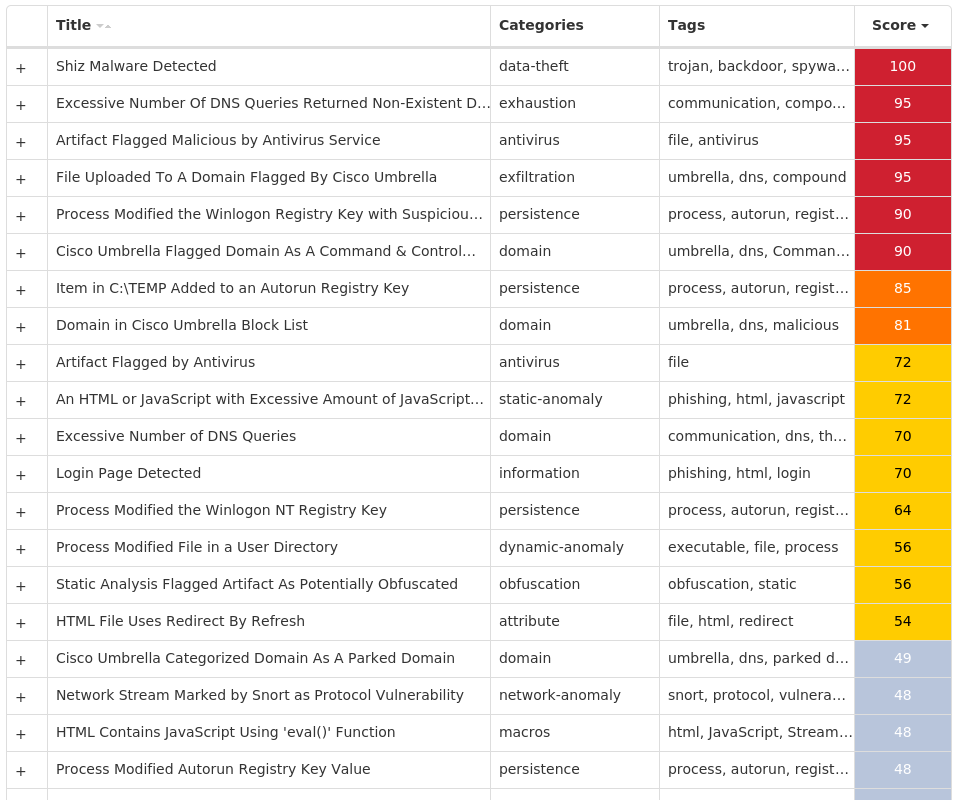
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Shiz-9983394-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 25
Mutexes Occurrences Global\674972E3a25 Global\MicrosoftSysenterGate725 internal_wutex_0x000004b425 internal_wutex_0x0000043c25 internal_wutex_0x000004dc25 internal_wutex_0x<random, matching [0-9a-f]{8}>25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]94[.]194[.]16925 13[.]107[.]21[.]20017 45[.]56[.]79[.]237 198[.]58[.]118[.]1675 45[.]33[.]2[.]795 173[.]255[.]194[.]1345 45[.]79[.]19[.]1964 45[.]33[.]18[.]444 45[.]33[.]20[.]2354 45[.]33[.]30[.]1974 72[.]14[.]178[.]1744 96[.]126[.]123[.]2443 72[.]14[.]185[.]433 45[.]33[.]23[.]1831
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dikymezosaj[.]eu25 cileretirus[.]eu25 fogixezajaq[.]eu25 gadohyzyvah[.]eu25 nofoletezup[.]eu25 masafytunux[.]eu25 jepepyxiwam[.]eu25 qetyrypopup[.]eu25 lymoxuxelam[.]eu25 lysenenyxis[.]eu25 tupycegubej[.]eu25 xutulenuqix[.]eu25 purijygirem[.]eu25 dimasyhageh[.]eu25 ciqofymosip[.]eu25 vonerymekix[.]eu25 novubymyvip[.]eu25 fobyqyhezem[.]eu25 gacucuhumeg[.]eu25 maxilumiriz[.]eu25 jelojujopen[.]eu25 qekafuqafit[.]eu25 ryhyruqeliz[.]eu25 kejepujajeg[.]eu25 tufibiqunit[.]eu25
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp25
File Hashes 08a7b276706517d28c3885c812f89b57549af4be14fe07059fc6f4651625f091091f71db383670a6815d3f57e5075000fc6fd016bc4823be5e7ae16bb53267a90d7c8955acc824a085be5d45102c510212ca6c5f4df5fad897ee2d5923d34a1f14b6836f41d60a28868dc0fcd758b7a23b86a9d7b5f08fc463de6ed950a737d11cc720425d2994b10536284c18e4a9e255ee5ea7ba21e6e6cafaf00310207a80342e45c1360a96d5b87847db6b3c85ef79bfda78c9f53a67a15424df91d785544056a5fa6b1b28126a3ffbeb4d8a2a046ed8017e49ab1941c64bb913dc9a6ace446ea4991b5630082258be07dc8fc7ac4297f89a4de7b63fcf2e09937f0ed2984d923330bfbba1410ba2e553ac6da20068c2714fc9405a76b64a35e5a5f3db1454f5f3b8f9310dfee013917c10d88dff4c524aa406e758c067e6ded17840834f55704fcf179904208e18ae3000599ae04869d57530fbb388f8e6aa37353e344c593d96413956b2ac7f3ac3cc7b9d5b106c480f8aa587789c48c77f43e15dccb36da3c0667c67bb53ada30dfc2fa6dac45ee5b56197515d0c083ea155a893730f7781a10e637ee035b26e363c178fbcf9e07d30a32444b50b00c715376388f6e2856b831b3f7ada0bb31ade63f755c35f7f4f381a956956052fff69e8119815ee8b9781057d5595fee84b6c45830ecb83fc0f261d6d9ba73b066f3c4b9c7f2c88bcb55a2df28a554fa12c514979c2080cb4244ee171686b8f910ce70a7f1f513ebe38aa13642e482adcf749e2cea5507e7942255e1b31c7c455c356dea793189fc74083c017fd115c3319f21234010c73650be020a95818b18aaca1b5902d73d8cadc40ac3e45eafe1977416e6bc4dd159ba74dd4becf5e177cdc6be9906c388ee4be229930351810431bc7c946fe36242e6e9f4c753578585c64fa1aebc09179eb95741a6ee9008efada291453ae1343a66d0eaa868b5554b6741d3d2a0dbd1aebfe801ee7ba2cfaa5b89359dff445569ec7883064d1bfa9f2a6cfb5394fe841eda4243c382593841fa5ee68b3ecf0c4d307a1b1cd01f6081bdf93373383a19bf0165180238c73a0fcdb1f9ec4142a3d98054a613373d1e67ce22dcbe53c7b08
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
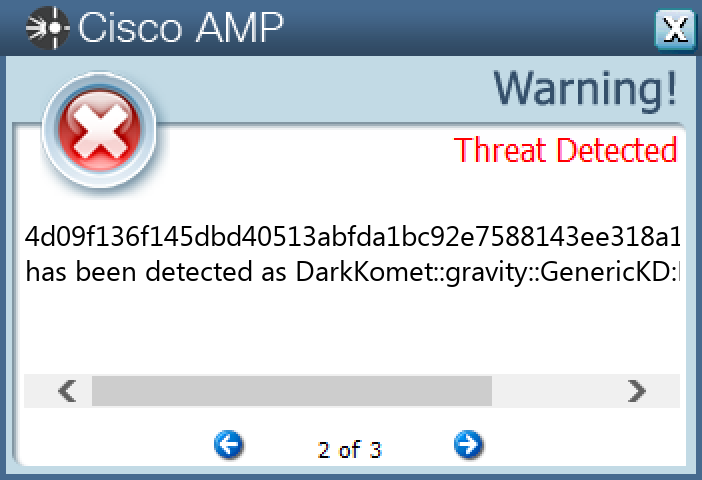
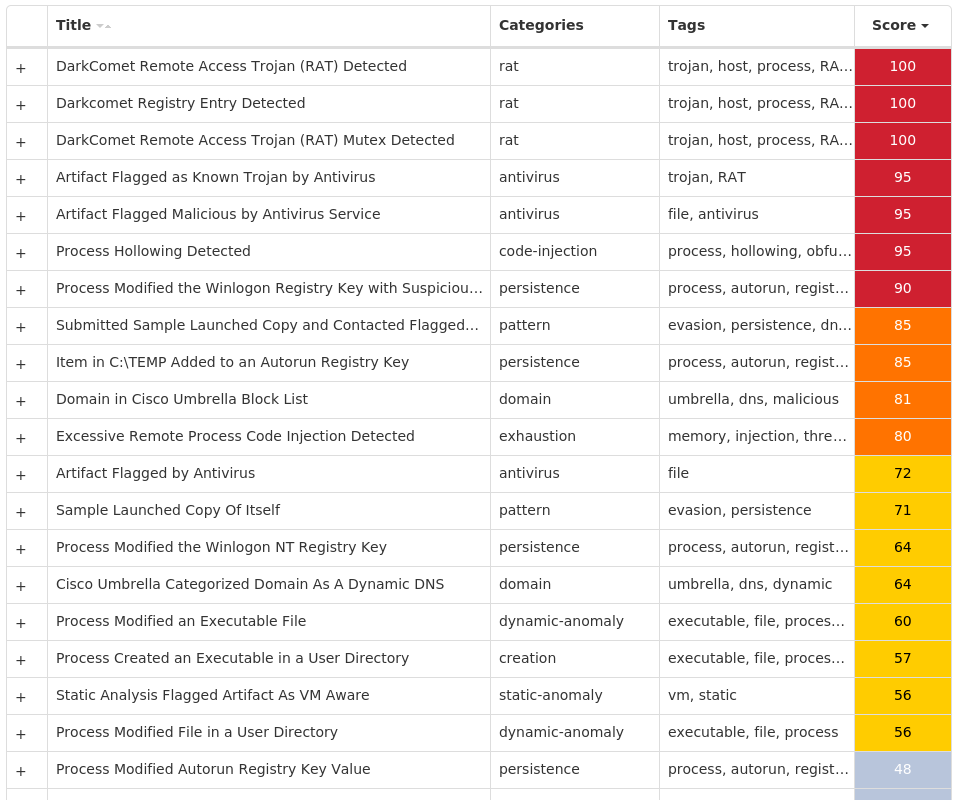
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkKomet-9984290-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN16 <HKCU>\SOFTWARE\WINRAR7 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 7 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 7 <HKCU>\SOFTWARE\WINRAR Value Name: HWID 7 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 7 <HKCU>\SOFTWARE\DC3_FEXEC6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 6 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: LiveSafe 3
Mutexes Occurrences DC_MUTEX-U4R2ZE36 1daec281-87cf-4d12-bf14-b425e26bf9ca3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]169[.]69[.]256 5[.]189[.]137[.]83
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 1ntershipping[.]co7 randomlovezs[.]duckdns[.]org6
Files and or directories created Occurrences %APPDATA%\dclogs6 %HOMEPATH%\Documents\MSDCSC6 %HOMEPATH%\Documents\MSDCSC\msdcsc.exe6 %APPDATA%\ConfigsEx3 %ProgramData%\LiveSafe3 %ProgramData%\LiveSafe\livesafe.exe3
File Hashes 06589ce72d7765cf161dd7efee2daecfe8a85899489a46d207c936af5a025528140e5bec9612622eb47912cf88cc82fc74e3ef2f0433dbc8a597cc2970b2cc0214de0def7ff5d9c43ecbcb207ab56a858fdc083229b30ef816e62e19dbf6b2d021df035a886ce850512c47bfe7eb83cf1c1ab521187894483e9220e06c2fd77330daa7fe12aa0818aa8739ef8dac3cea625a175a27cba68998545ce25fc17c2940511c3a0402ec8b6d90b294ea13f5d83b5f77a2a47c333c01dd231b3588da764d09f136f145dbd40513abfda1bc92e7588143ee318a11c5e498995847fb6c127bfb7f8f369004364519394d630587619447f397b1ce95f28984db7aede139827d1b8b1631a84926b840cd5b857c8fb4c21af7ed394ac85c4146d464eb413f5d97440f7334388258e72995338186e89a40aff17ba1f6fffffdb088d04141f0bea1296eade8e9e99c60155900604c318e6a5dd270495d9fd42ef5144f388ff033bfe82fd70f36efa6164bbd42d196381584d661d12c5de6312806100c37042558d1b45a3651bfa2af1186894fc579784a5b92997d8124a1bbde8725fe259f19bfde2673264d41fe0ef2391733223e9b092483f95a34fc0a5fa1acb69a9d29f920e4a1a2cb2e4d98adeb6eb38678de696425c437a42da49d0586028a32e7076bc8ea04019c2556bd95a4d5de9f1688a39af9a09bc83353026223e0d29a2cec81b0ecbd53c73ab4c3b0efe1f2e6aaceae13e19006584f615ead12d134d2fe52f282f211174d53657e1edf965e99c5fdee9f15f91bff3c41c4ceca1bd9b0abc38f82
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
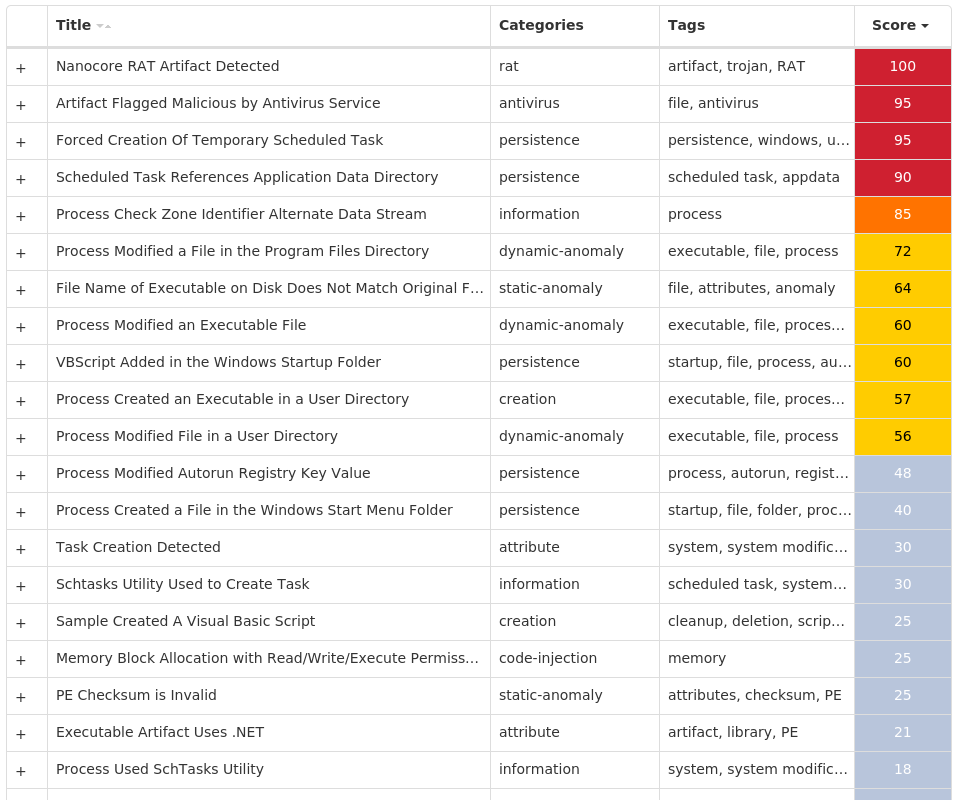
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-9984085-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 8 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MyApp 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR DATA\LINKAGE Value Name: Export 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR NETWORKING\LINKAGE Value Name: Export 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET DATA PROVIDER FOR ORACLE\LINKAGE Value Name: Export 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET DATA PROVIDER FOR SQLSERVER\LINKAGE Value Name: Export 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\CRYPTOGRAPHY\AUTOENROLLMENT1 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @C:\Windows\system32\DeviceCenter.dll,-2000 1 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @explorer.exe,-7001 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: b729dc2de3a09245553725e76a1d5da45456d6be6edf6a6c6b4ce0e922895d88 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: b729dc2de3a09245553725e76a1d5da45456d6be6edf6a6c6b4ce0e922895d88 1
Mutexes Occurrences Global\{6eacccb2-da40-404e-ba3f-9cf2cb842104}6 -3 3749282D282E1E80C56CAE5A1 Global\<<BID>>98B68E3C000000001 Global\<<BID>>98B68E3C000000011 Global\{2de2dd5e-5799-4adf-b77b-aaae77ba7236}1 Global\{217c10cb-4875-422a-a6ac-cae34e8afb0c}1 f8a1hk9am3adue2674aue1 Global\{d26f97e8-1d06-44a6-abc2-219db996fe51}1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 173[.]254[.]223[.]946 64[.]32[.]8[.]673 35[.]205[.]61[.]673 77[.]88[.]21[.]1582 185[.]107[.]56[.]582 37[.]235[.]1[.]1771 37[.]235[.]1[.]1741 185[.]19[.]85[.]1831 64[.]32[.]8[.]681 185[.]107[.]56[.]601 52[.]23[.]46[.]391 185[.]157[.]161[.]1471 185[.]107[.]56[.]571 35[.]169[.]217[.]1421
Domain Names contacted by malware. Does not indicate maliciousness Occurrences bright1[.]awsmppl[.]com4 brightgee[.]phatbois[.]biz3 checkip[.]amazonaws[.]com2 smtp[.]yandex[.]com2 ml[.]warzonedns[.]com1 epiccard[.]tech1 sarlelhassan[.]ddns[.]net1 stevesteves001[.]warzonedns[.]com1
Files and or directories created Occurrences %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C59 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs9 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator9 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat9 %ProgramFiles(x86)%\AGP Manager8 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe8 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat6 %System32%\Tasks\AGP Manager6 %System32%\Tasks\AGP Manager Task6 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp6 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ensptrbyxaelazb.vbs4 %APPDATA%\hbmwcjzrpp4 %APPDATA%\hbmwcjzrpp\ensptrbyxaelazb.exe4 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\zmpesqpigdgyqtc.vbs3 %APPDATA%\hqwhhfunce3 %APPDATA%\hqwhhfunce\zmpesqpigdgyqtc.exe3 %APPDATA%\MyApp\MyApp.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ncynfkdiseoqyjq.vbs2 %APPDATA%\gjqcrsyeiz\ncynfkdiseoqyjq.exe2 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\desktop.ini.id[98B68E3C-2275].[recovermyfiles2019@thesecure.biz].Adame1 %TEMP%\638094733462004000_0e17d79b-46a9-4d98-a066-dda3308efeb0.db1 %APPDATA%\lpupw5gp.0lp.zip1 %APPDATA%\lpupw5gp.0lp\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\sosikeuywehiylb.vbs1 %APPDATA%\ubrwzdoiby\sosikeuywehiylb.exe1
*See JSON for more IOCs
File Hashes 0aa0cbcf28aba3c9ea66255d21568dc834aee97f68d1071e7cc49c167e5f44301f73eb2dc88a5a499b95c95463428181c82612361c38490b9a749d5e6dd410a123064f9a8ba30be479e5890ec13b654d539098844e9c4a16409dbd4a015513c52348735813c9d79c4723a890b64468f68b448594574b9a70db7a6b9afe1bbb106a0dc109135a2a858cddc2b65387d3ad8d67ffc9325440c70eb1bc83f3ba9ef9769a82395d916954845a5dbcce1783e30b50a35e9249081494dfdd8acb05f67c843d2082b0ecfbfc99780647e82e5575e0371a2bef4ae06ca45e1afa559acc1a88fc092603ca33d605af12e8c9722ae65801377dc5703a1fd9041c046c0ef5db9ca16e853d60c67a4d6c379ce90d1a0492b28efc15ce89867a696937ddedd125a28e0e11818bc375921d1d2a07a3128b4db509eb5a1340ebb6d8eeaf7c875707b729dc2de3a09245553725e76a1d5da45456d6be6edf6a6c6b4ce0e922895d88c277448c9e5e8699e9d25258fe07632cc150515afc96a4ac160781552b52460bc873f96e97877322dab3712e7e32e652a5e7901c1fe41fa65cff80380bd39b52c8dae9c8a95d171ce5520f7d1d8fc089cb06cb6cc238e63dc7b2ed0214855cd6cd7ba4950c05210f3ce55da9466bd531319998be31ecbdab01df806d254ca64febf129df20c2e7fc5eeb1c67a0d3184e5f0c022a52368be4a9ea06fe3341c57eecb34493e0db3c2cbf6602e183732f43cc1af8b6572244ed8aa2eb18f1de8bf3f7a704fbd592324b3a2ea2d316db30463c47fe1c0c2039dbc13901a2ab9519ceff9a714c790ccd7c31eb5abb568dc79c9553ff3d99ac84050a62b0feebb6cb11
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
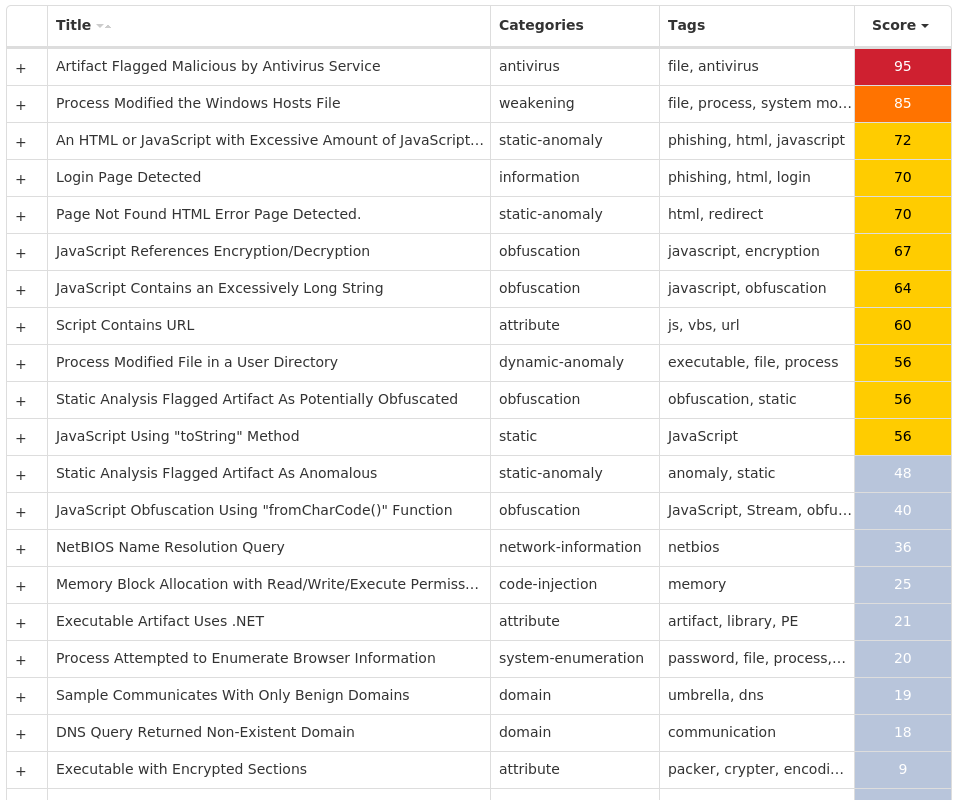
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.QuasarRAT-9983512-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 10 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 10 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 10 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 10 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}10
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 31[.]13[.]65[.]3610 31[.]13[.]65[.]17410 13[.]107[.]21[.]2008 157[.]240[.]241[.]637 142[.]250[.]65[.]2026 142[.]250[.]80[.]995 142[.]251[.]40[.]2055 142[.]250[.]176[.]2062 172[.]217[.]165[.]1502 142[.]250[.]64[.]781 142[.]250[.]80[.]141 142[.]250[.]81[.]2381 142[.]251[.]32[.]1101 142[.]250[.]65[.]2381 142[.]250[.]65[.]2341 142[.]251[.]35[.]1741 142[.]251[.]40[.]1421 142[.]251[.]40[.]1101 142[.]251[.]40[.]2141 142[.]250[.]65[.]2461 142[.]250[.]65[.]1821
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com10 www[.]instagram[.]com10 www[.]youtube[.]com10 www[.]facebook[.]com10 m[.]facebook[.]com10 r20swj13mr[.]microsoft[.]com10 www[.]eklinkk[.]net10 www[.]eneskeles[.]net10 fonts[.]googleapis[.]com7 static[.]cdninstagram[.]com7 i[.]ytimg[.]com6 accounts[.]google[.]com5 fonts[.]gstatic[.]com5
Files and or directories created Occurrences %System32%\drivers\etc\hosts10
File Hashes 19efdda9ec1232653d64ad9f6d3d8813904ddd9995df3e697e49ae4f267622b053b741a52f88d7e0f01dd4f5bcffac6882668922a45ecb1bc2e7275778afd5996a625df2a22684ec5c95df37818afc44ca1d7aca39e8011b7c0287c36958872899f9e4ecd9882db1a05327c07481941e8a4ce22dfdef90c15e9d200d9c79cbddae8220d48eb72043bdfc4fd965fce63a668cdd281553c6a93aaf574af554881ac37ff695876f126cc4f6b627a54f2a0bfd68983243b87d8e078143609c26f6a1ceecc1833d5bd98f7377e20514c3574e5e7baa11462fb952be29b2d7d2be10afceeddc45a3e52e50445abfd568287edf87649fa4e94d75d3a4533a7396ae1604e237afed733f19fb87d226904faa1f6b13a9279db2970aa9821bd7ba03a61487f707db5c91e9f1e70effecb99ae6d8101cb2343779df3b06eba56311bde64a41
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK