Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 20 and Jan. 27. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
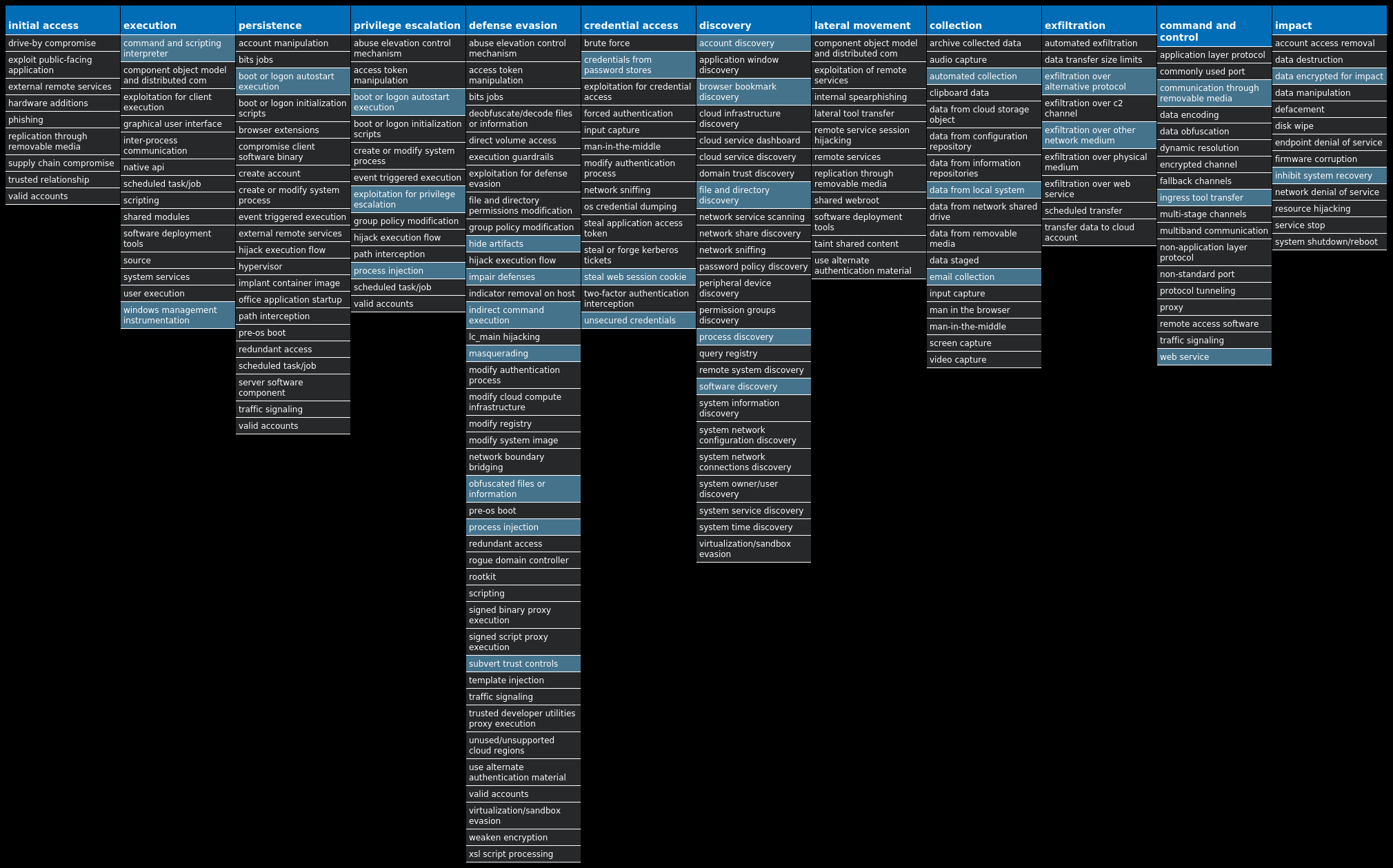
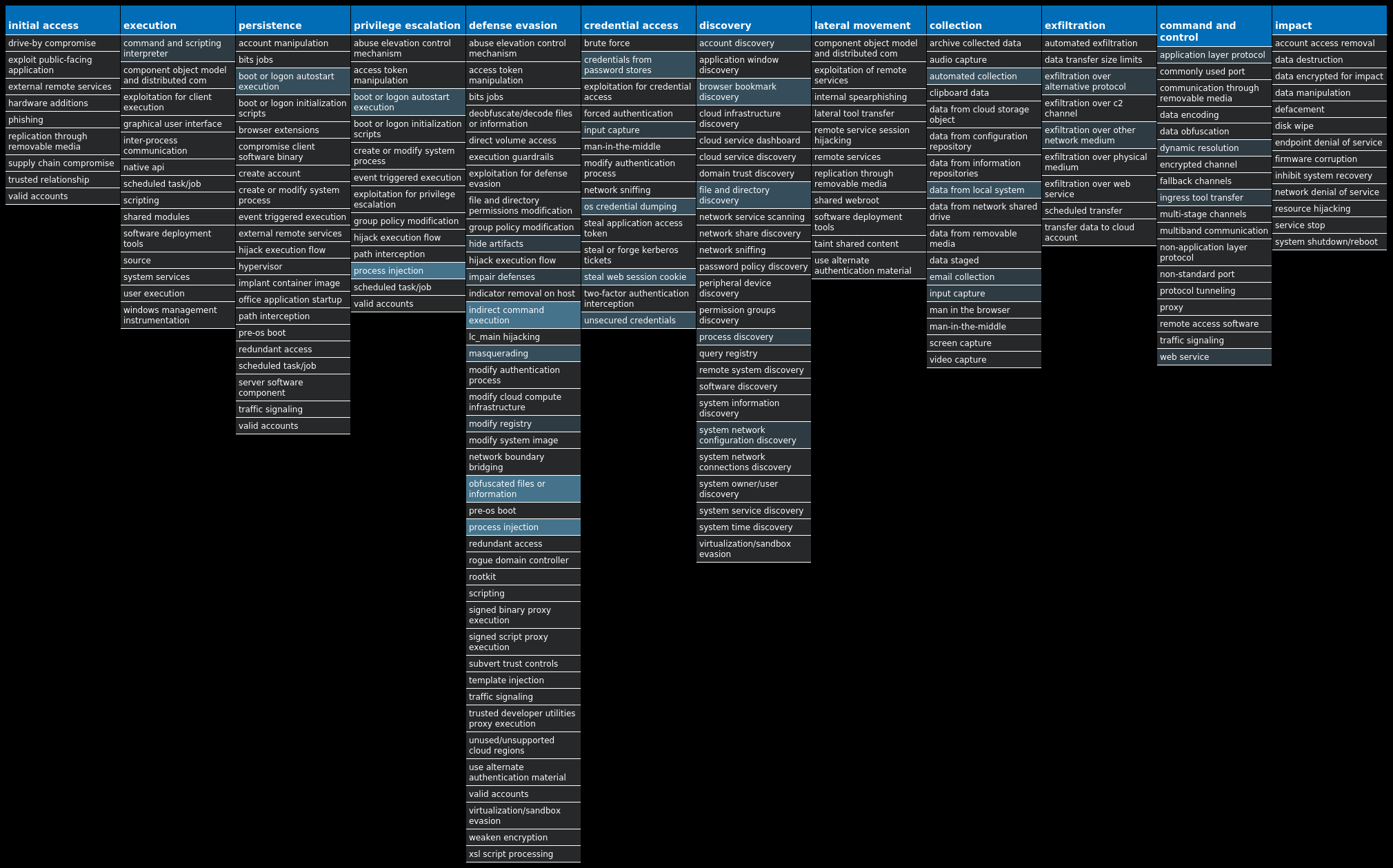
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.HawkEye-9984948-0 Dropper HawkEye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media. Win.Dropper.Zegost-9984959-1 Dropper Zegost is a remote access trojan designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. Zegost appears to be derived from Gh0stRAT, which is a well-known remote access trojan that had its source code leaked, thus significantly lowering the barrier to entry for actors looking to modify and reuse the code in new attacks. Win.Ransomware.TeslaCrypt-9985040-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the extortion request, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Ransomware.Tofsee-9985077-0 Ransomware Tofsee is multi-purpose malware that features several modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control. Win.Dropper.Zeus-9985129-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Dropper.LokiBot-9985173-0 Dropper Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Dropper.Nanocore-9985222-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Ransomware.Cerber-9985289-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Dropper.Bifrost-9985293-0 Dropper Bifrost is a backdoor with more than 10 variants. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attacker to execute arbitrary code on the compromised machine. Bifrost contains standard RAT features including a file manager, screen capture utility, keylogging, video recording, microphone and camera monitoring, and a process manager. Bifrost uses a mutex that may be named "Bif1234" or "Tr0gBot" to mark its presence on the system.
Threat Breakdown Win.Dropper.HawkEye-9984948-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Update 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]154[.]361 208[.]123[.]117[.]21
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com1 s3[.]dedicatedpanel[.]net1
Files and or directories created Occurrences %APPDATA%\pid.txt1 %APPDATA%\pidloc.txt1 %TEMP%\holdermail.txt1 %TEMP%\holderwb.txt1 %APPDATA%\WindowsUpdate.exe1
File Hashes 06572f2182ef9dfaf3b8c7d2e025a18a2f4529fb989ad41fd54e17c3532aac0b178319c41b50d3b78e36d6ac9105b81cbbe74375ce13b271e3ede79222f83854234f8d4603971d0c86b5a4ccd06212b785ec6a260f9c692db3cced7d3ae6ce77235bdaa330b9305eb30b08c8e63e28d318bcdb640e87e2bac1f77caf643e2494255a56ac4fda1184eabc21cca66983c70bd795c99851802595441c5151e4a1522ba523bc65c1f954e3f45324986840c5a910b4cd6d992d4bc228cbb86def8e983af54f2049dbc175ef4c589aa376141586711dd724617ed87e0a5bc7f1e431c04370bb6226f36558266a224de5ebb1582208f82bafdf9f2e2617a5cdace9d377508708e5f5ab169299334434b17fc926d7972b9cc601e0f588ec979a6fb67f4a549887b9e8e1ffe1e95a31a287c61ca265dd864b886034c22e4bf12bedb5ac9160355c9d953b39905ec1d23237cc8339b2e1ffe0eb29bc8028dde75bddedd8db71b210336d2277a498c150e99ddfb99750b8e481fb6dd0d647b7be571c2629f17628f72251de0d74df47361bb228fc34abdc121212d6da40936052a5215054e69143f2fe92b76f3a42dbeddccb738a397e2d07e5060046a367ed6c1a2c543dd4a1d8085822a839d8e4f5078584dadc2221738309dbb6e386deb60c4cb8685d90a3f5688c1f1d5473722fd4a6ae84be5c4f8235db2789fd1e77929cfbb026078aa41cf4f43bdf0ca8bd515799702f62a1ff811d898f823d1c0225422a54376607a6f20cc5f0a34adf5ac4582936e5407e48397db18847afa6ea3068c707cc40ddb30e4856fd0b7adacf553023314db78e88638cd6ee9a14f2f0b8e3dad8fff98cb66a4c2e0b22011ba409167c9bb663997b180a35f50fbe124bc0439403d65e74d28b60289c250c1a5a2661dd4a57839cfa3e273f5ef5b068624ff99a2ccc2b65d49278e577526a1839a13cb7066aabf02ea2d59cc7bb1c922404270cab602c1bde4afe7e3fe9fc07edbf818ef66a0534844a9daf92d843b3402d67946222637ee0ee8c2858064cf3eb1bb7a467aa07e9804255570d7b6e25ddfe927cef2d83f8e21e57541123a49fdfde9912b959fda0bdf5c5fb951094a44bda3fed61ee0c06
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
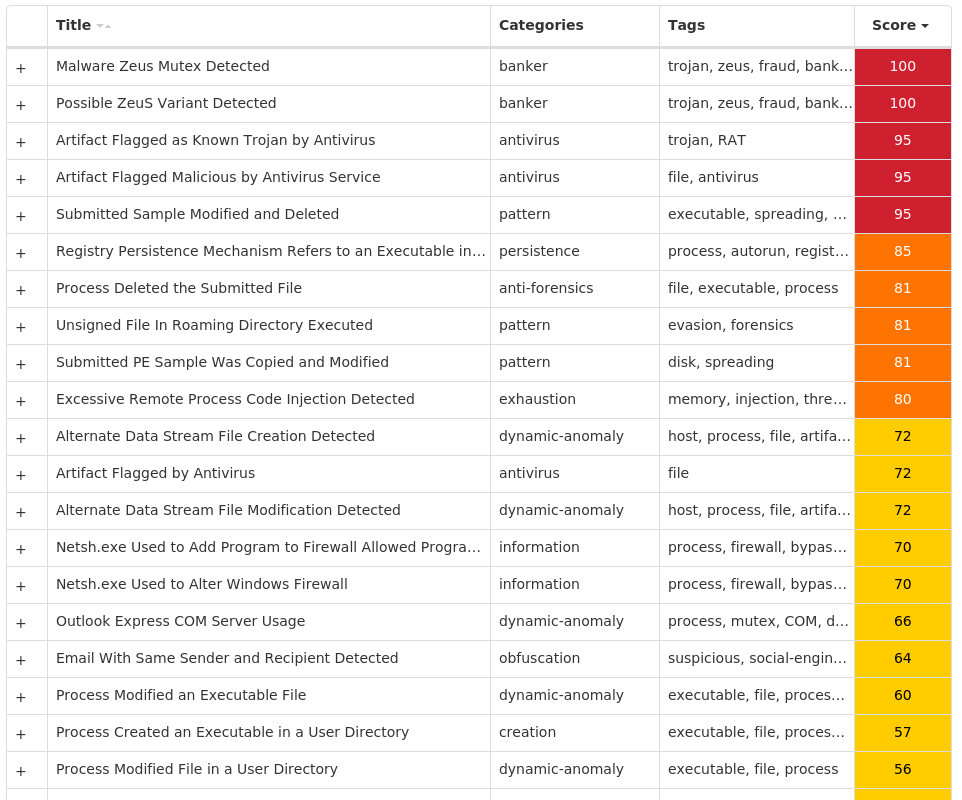
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zegost-9984959-1 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'>7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ConnectGroup 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: MarkTime 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Type 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Start 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ErrorControl 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ImagePath 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: DisplayName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: WOW64 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ObjectName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Description 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: FailureActions 5 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSETSR BQMYSGMF1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSETSR BQMYSGMF Value Name: ConnectGroup 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSETSR BQMYSGMF Value Name: MarkTime 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: ImagePath 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: DisplayName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: WOW64 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: ObjectName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUNTIME BROKER Value Name: Description 1
Mutexes Occurrences Global\58026681-1745-11ed-9660-0015174393491 csq1.e2.luyouxia.net:24705:Rsetsr bqmysgmf1 127.0.0.1:8000:Rscsso omyumyeq1 127.0.0.1:8000:Rsgewq wsqscuqa1 dlos1245.e2.luyouxia.net:21516:Rszhzn ppzrdglm1 182.61.134.76:8000:Rsidcj jyuwqkyj1 121.4.85.235:1499:Rsgkcs icmwmkam1 w794754387.e2.luyouxia.net:29523:Rswsue csscaksq1 43.230.169.58:8000:Rsvurb jfjqyucm1 112.18.159.112:34567:Runtime Broker1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 180[.]97[.]221[.]1202 43[.]230[.]169[.]582 123[.]99[.]198[.]2011 121[.]4[.]85[.]2351 182[.]61[.]134[.]761 124[.]248[.]66[.]2141 112[.]18[.]159[.]1121
Domain Names contacted by malware. Does not indicate maliciousness Occurrences lqwljs[.]cn1 sjlwql[.]top1 dlos1245[.]e2[.]luyouxia[.]net1 w794754387[.]e2[.]luyouxia[.]net1 csq1[.]e2[.]luyouxia[.]net1
Files and or directories created Occurrences %ProgramFiles(x86)%\Terms.exe1 %ProgramFiles(x86)%\Microsoft Qbeuxn1 %ProgramFiles(x86)%\Microsoft Qbeuxn\Wywssvd.exe1 %SystemRoot%\SysWOW64\Mawyace.exe1 %ProgramFiles(x86)%\Ezsszfx.exe1 %ProgramFiles(x86)%\Bjrvlbx.exe1 %ProgramFiles(x86)%\RuntimeBroker.exe1
File Hashes 1e31145e87fcaf55e61e38d4aa7f4dc71be19d35ff3f747a684e488805b075943ddcaa1008f22e9abddf2252d69ee1724a21a1d07005584ac42505539e5379a66d448045dbe5f11cca8ac423edb230c38279b201fbb512d5dc5f1207a93cbb177b61780a7a04cc483f25f790fbe210086748626a1de1988340cb35895f7df70e7f399111c9b70c0de1b51525fec281e6eb6a39af6802a0abe626678af0d1ced387233e65e7b07831749fb294687632b8ef51b2f155d412024a561243288e08b6a607a60d0d952d7d73649ce327646fe2de7f7cdaa2ca7785faa7851b9b8d100cd6457c55dd9eba5fd8078e7bacf965c65232d713a1e037064f3617ad4d45844ff6647a78d8bf05b80830dfd013a7876b4f9619c16433478a4fd2b69fbac9d0d9fc7a21b32715e94357d9e7659b18d93b5401e63187e9952b50b45a23673abc99
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-9985040-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 16 <HKCU>\SOFTWARE\XXXSYS16 <HKCU>\SOFTWARE\XXXSYS Value Name: ID 16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 16 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: aingokyddfin 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xynflbfpqxfg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xsrdyarnlxkb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: nrosuypgjita 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: uqjergivpotl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cokwmnrosuyg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xhcqdmqiixoc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fsglxsrdyang 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bajwwakyuxyv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: urbajwwakyuy 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xenfsxranlku 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xxynflbfqxsl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: dcpegxxynflb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xxynflbfpqxe 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wwakyuxyvyly 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wakyuxyvalcg 1
Mutexes Occurrences ityeofm9234-2342316
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]128[.]188[.]13816 162[.]241[.]224[.]20316 34[.]98[.]99[.]3016 154[.]219[.]146[.]24516 23[.]221[.]227[.]16510 23[.]221[.]227[.]1696
Domain Names contacted by malware. Does not indicate maliciousness Occurrences biocarbon[.]com[.]ec16 imagescroll[.]com16 music[.]mbsaeger[.]com16 stacon[.]eu16 surrogacyandadoption[.]com16 worldisonefamily[.]info16 apps[.]identrust[.]com16
Files and or directories created Occurrences \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I08BO8F.xlsx16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I11KHR4.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I5QKHLN.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I62TWBD.ppt16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I6FZORX.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IABMX83.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IAJ2Y6R.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IALGTCS.xlsx16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IGTBBSA.accdb16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH49RPF.ppt16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH71GGR.ppt16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJKODPH.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJP965K.accdb16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IKY5R3M.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IMYCSIT.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$ISLP722.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXLC77A.pdf16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXUL2U1.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IYSR1FU.ppt16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IZ2GMJW.XLSX16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R08BO8F.xlsx16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R11KHR4.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R5QKHLN.doc16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R62TWBD.ppt16 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R6FZORX.doc16
*See JSON for more IOCs
File Hashes 046979df42da0affa983d6c73be7ad19afacbb6a05a28855cd302a24624ebb9710a0df06ed33b5ed2771a316abc7cc9a621c2097fa9a4522d9c0ac31c4953b702bce73c239a95080211fbfbc5b5268e1fecc81b3e5348ca391d00486dfe67d703113c2ac299a173a07ea6de7da87a2f2f29ed95e509b9dc6e7128ea9a879626631e2b0639ccb2499f79c4d45a037a1b6db52e4d0145605076d5a3b28fe5645664559e437ee99d1f7cf2727597e030fade0c452c3ae0649e4669306372522db224f7473bb503c036c12d8e5850f3aaeb1c8abe9cab4dd8b16314f258999eaa5cf6fd825e2bddea82cbc88fccbfdd50f425aa05047ffab0b511fb55c3f85ae88e48837ded9097e82948c53a4c875d66ff10271127e93702f89a8e4a9265625564d91df821cfa7634ff2b6e08a73533885f3ed24c19aa61d3f5d5e346b97d1f1590acbbd4b0c721c51bd9e510823659b521536ce43aad5eb324783c1c9e03e94974cb998389d745287bc242eb23fe128d50bb42198b6e2cf7092e9576471cf25a38d89d2f295b2a07e6bf0bf6c2a1b47c8221700746b781a5e537099c212da6b06bd91e331d39b96788c6c7fb7ab3bf652d46f53be628331a7753ed1955e5f717bee5db44290dea09182ee4383925805ee3bc901966cba16d7c05704b5a01eed95aee0ca0f158ba207090b00152ac85b17e4ba097335bcf9242ca8246e849bcf537
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Tofsee-9985077-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES3 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 3 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 3 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: DisplayName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: WOW64 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: ObjectName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAV Value Name: Description 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: DisplayName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: WOW64 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: ObjectName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GHNJMHYT Value Name: Description 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\ijplojav 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\ghnjmhyt 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\QRXTWRID1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\QRXTWRID Value Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\QRXTWRID Value Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\QRXTWRID Value Name: ErrorControl 1
Mutexes Occurrences Global\<random guid>8
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 31[.]13[.]65[.]523 176[.]113[.]115[.]1363 80[.]66[.]75[.]43 176[.]113[.]115[.]154/313 176[.]113[.]115[.]1583 176[.]113[.]115[.]2393 176[.]113[.]115[.]1353 94[.]100[.]180[.]902 31[.]13[.]65[.]1742 77[.]88[.]21[.]1252 212[.]42[.]75[.]2402 52[.]223[.]241[.]72 40[.]93[.]207[.]02 142[.]250[.]176[.]1962 142[.]251[.]35[.]1632 20[.]53[.]203[.]502 141[.]8[.]193[.]1852 23[.]3[.]13[.]351 66[.]254[.]114[.]411 40[.]97[.]188[.]21 200[.]147[.]36[.]761 104[.]47[.]18[.]971 104[.]23[.]141[.]251 104[.]23[.]139[.]251 104[.]23[.]143[.]251
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net3 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org3 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net3 249[.]5[.]55[.]69[.]in-addr[.]arpa3 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org3 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org3 i[.]instagram[.]com3 microsoft-com[.]mail[.]protection[.]outlook[.]com3 microsoft[.]com3 www[.]google[.]com3 svartalfheim[.]top3 www[.]instagram[.]com2 video-weaver[.]lax03[.]hls[.]ttvnw[.]net2 www[.]google[.]nl2 imap[.]mail[.]ru2 imap[.]ukr[.]net2 imap[.]yandex[.]ru2 www[.]tiktok[.]com1 www[.]ebay[.]co[.]uk1 www[.]omegle[.]com1 imap[.]aol[.]com1 www[.]pornhub[.]com1 outlook[.]office365[.]com1 front1[.]omegle[.]com1 ebay[.]com1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile3 %SystemRoot%\SysWOW64\config\systemprofile:.repos3 %SystemRoot%\SysWOW64\ijplojav1 %SystemRoot%\SysWOW64\ghnjmhyt1 %SystemRoot%\SysWOW64\qrxtwrid1 %TEMP%\dsgdwcyb.exe1 %TEMP%\gnnrscmx.exe1 %TEMP%\ysizcadm.exe1
File Hashes 52d043fde53ca1f8206e8cccec0a6202608927cbe1ccc66c897ce7806e0bb8db52f7941f779a31924cbdc50ea92481821281f9ed61e1751689e6d0d77a28b865573c4a98edae30752a2a3153796707b149bd8fefe265509e6a4e95e64a00edde6017f05c453161374cfd6f9729b6b2e12d5e22f34e64c854700aeba843e512b4685db303322dd68e66a46447b37022cdc4d0000576cad05eef5234eb09dc9f31712f57fd1ad51878132bf31a9c10845cfdd201268b5f29683f331daaa94064e08b945dac10d16c2f76a20b497a392f9782768d4ec233c38890c5b4e4d347b7e08c766a9efc8d743b072044be56b41a98eaa0750d17bd9940fd334423bf4163d5942b61d7f36de871315070d6b89f8bee9d49f043fd115b710b202138209a51a79f7538929d41e712d2f0af226ca663c890b07301140d8569f071a43815dd39b4a378313d3462b42b4bd6f81218d6ddcad3c58730042a09d6ea7d2724de6ad8f5a8dab16a73c683ced6a88ba70b1b3fba1d06d5c214e3b8a534b69c49ceab3bacb7371868a517e14b30fc12515aa5dfea39f3786ce1a14b0061815d462302eebec8ecbd53f00218c14ea066848502f5828f7f77cde4fcee3b66e9c72088ab1ca8d4ded32b48c5896ea5c338e2f0fb6131ec4365d2aca874901f979ef1b34cff53dd14921b8274f08aebcfe6d02359191fec130e13feffbde9b4cb88f9810bc10be6f650114bc7e368a97786dacf73d57f3c4b8766f895fe2a570781ec9e8f6f28f68d76ebc0c51240fccaccd641c66f1e0059b5ccfeabff3737fc5e5bbab1ddb7
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-9985129-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY Value Name: CleanCookies 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {AA56720F-EB83-D818-7B46-E026C6F642DC} 1 <HKCU>\SOFTWARE\MICROSOFT\ZOOZIN Value Name: Yqameb 1 <HKCU>\SOFTWARE\MICROSOFT\ZOOZIN1
Mutexes Occurrences Local\{8D47BEAD-2721-FF09-7B46-E026C6F642DC}1 Local\{A847581D-C191-DA09-7B46-E026C6F642DC}1 Local\{DF676CEF-F563-AD29-7B46-E026C6F642DC}1 GLOBAL\{<random GUID>}1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences muzze[.]biz1
Files and or directories created Occurrences %APPDATA%\Moe\fylavai.hig1 %TEMP%\tmp264ba9dd.bat1 %TEMP%\tmp4e248681.bat1 %APPDATA%\Moe1 %APPDATA%\Xeit1 %APPDATA%\Xeit\ottyga.exe1
File Hashes 024e7d89552b263467f912568ccd95181ac718f4a8e5012e5c6ec1aacf2f77e40483f996d51c910d04083acc2057c6889473e9dde561dc1f9b9535f738e594a10f6486fdaf98bb93a0557a3c44bb906d41b4c0e00c007bcad189914fae85be7c16d63848bec52a9eaf184bdaa704674657c1a6b31cf50696b95cac7244fdc35817877bc57bf371e332f3f59d46102319728261a80090791293be290056020b0e1ac1fcff08cf6b2df798710c364bec4113d44c3447806dfc566191c0c5db7bb51c6cd22f8fdfc8219861db803349bce1cdeaa5cd880dae609e1a1667b5d022ad1f4457b541ac0ad19951d39a1e260b1733210c68c7bc16932d0f3467f2e7c8b6216e23b13eebcede1492f9414ef926bf49e825a42470bc265458debb103330ba2426d26e4924f9514d674304627480a7cfb43e5e5ff1d1876321c188502374dc2460deaefede5b79219cffdc473e5a9fc371d15b7797fa70d8449b4c4f9abe8d274192458297e01466260a43ded24165efa899fe4448c73198f0de81766e2527298f72fc3b9de5eb91ae3d6102526b832ae3365647d569877242d51e566f4029347ccb8f6bb23038c9cd690cd5a4ce3ad79824ee65a1ce7477987fd106b5fd323654aaff7c3064cb607cac6d1211e7e64cafd5ceacfb0a416dbba719bdffc2cd403122fe822bb9bc87aff93a2c93471a9360413d519781950d6871a8daeaf94d4190f82a028deb2d0f399520e034a6f1ab5a78d14c4d1433be8ba4a6d2f70b414272e583ff2c4b9ce0e507cf339d14d750c05288b897557d0fd672c6f23fc8bf427d2cfa6470def7183affabff2d26e582ee71dbb824e265261f01d86be2ac264a6538cbea79e455429465ced98f32a8736abe8a5a919d9f4f1446060a3f6c54507cdd0ac8cfffd9815c86431289eac78ee92f1aa19825ee82d29e6650858dd55170ccdc6131e2f4341274bac186dddde935f77c0f3d3d6dc429171714f856ff5308632516b9ae13e416fc7450750a8239a0d8a5aaa99e80af00ca5fb97d23866a432b1e261b3d366681b52fdec626a5673fd0fe8f3265898aabefc7be3705816a5c370e1a6326d988f483defdae1214d6c3dae5126e0b2129f90eee59e21e4b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.LokiBot-9985173-0 Indicators of Compromise IOCs collected from dynamic analysis of 27 samples Mutexes Occurrences 3749282D282E1E80C56CAE5A1 Global\f5549e21-9b80-11ed-9660-00151711fe831
Domain Names contacted by malware. Does not indicate maliciousness Occurrences sibiusmart[.]ro1
Files and or directories created Occurrences %APPDATA%\D282E11 %APPDATA%\D282E1\1E80C5.lck1 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51
File Hashes 0042a5fcd4c4e430c71d076dc5c95eac93069d77dfe821f412285bac7fa4597b02f2e2f38004334f9c00f100f8eb03c80b85e25bf3fae085c1f2b1289d4cdce3031c093a692f78038810f3249aacaf17b29b579432cabebe0344136c5812d1d404cebc586fb7609a622cb97edc1648efe1dd5109d8bfa8e6a5c65fd06e8a8c4a05f2cbf468cbc1f49fa11344598a33343463c6a1b98e41a61e715b5a8e046d4a09023da9a9c788b0b4f8fe97555f3f4487b37f29e64431c6dcfb269bfcdaeef30a34c917f81a02e080f92d9c5a4fe2c134da87861ea9e8cf54a99e027aa025830b8922eb675b84835d295358355ed825b98ba56f6ad2fb5a246a39dc2422a74a19291bfe2f477f9a462f7bfec2a1a29ba596b8693b0f3130eb1fd2c532312b541c5e0c66477b508177bd9da97721bb97607f65374dedfddc711057aecc15aed51e1fb567710358f2f81e72642528581e08807786da92014303979f5fdd7149bc1f93e1ad55e298fdade05c00dd0220ca9d3b26ab8044310388357ab0b900cefa20da9b41f6f1c34732f193eb011f1b9bd25c29289fb687bfcfd14f74d14d6689289a9718bf44f945cd95db839964ab225e347ac7490a5c89c8aa0a93f64748952b271dd0350ebce6ddd239803988c3f9a64aeee314cd032eb1d9d1ebfe26a8d22b2c302f12a0cf798e3621efe73064f0e938643956c07668fd8b54451b9acaec367b0bcfe9894c93d7c2f9993a8ecbea7b0c16d6992752afd97e8a749a3f80af38e9b92df247ef59650d723e0b04edeec9e7bc6983176edaa8c87cec9facbed5396d98aeca3665a187a2b31fb0b7e026181a4f4c11876fa62a5723caa2016af53ea57948ea5e4758ef408714b2ae55c1d214f605f8f2b776f0518a681cf7529e3f32dd4bdc512625ffbd05bb51c49bbb5500d63bb68a89826c1f2744601bc38c3fb4c8d385d957154279efc406c309134ec41bfe1e0a6c536be9c20ffd2850b642a65e0d026b317b0ebe217180e5391e77c7d10f4938ac14a5884ff68481667942b634f4a218d5093a94881b1548667722f87fa38d915a97fe126996ddf3c4ca46760a3057ab75e01adda1a49b4a156282a4ab596db0053bb59b5f1be57650f5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
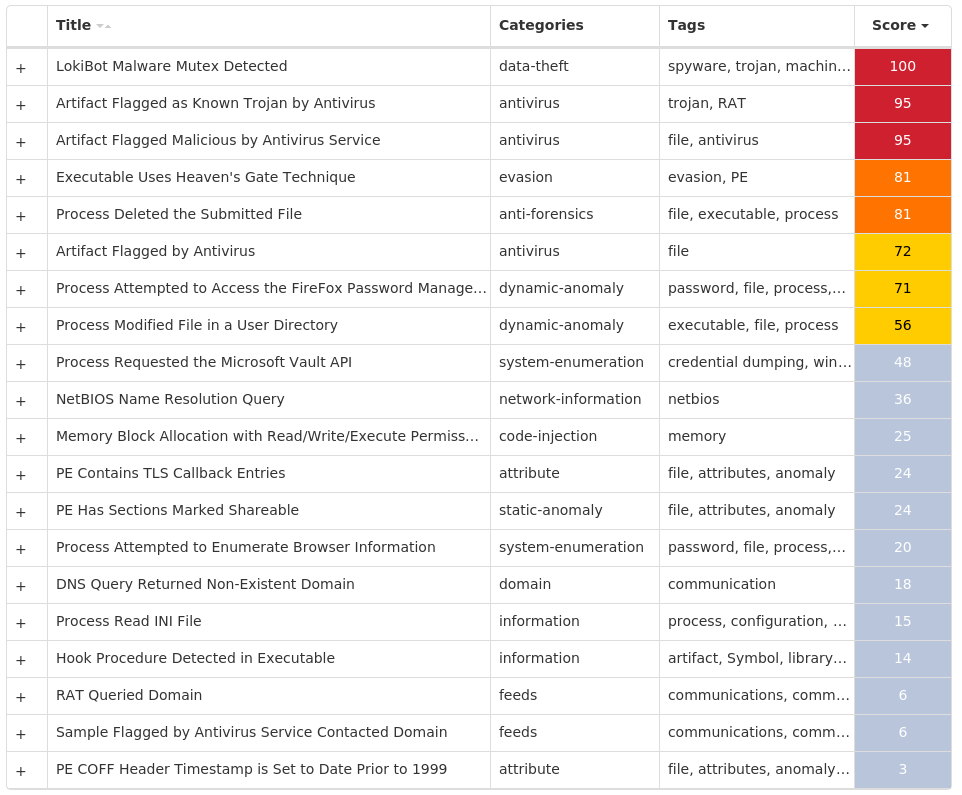
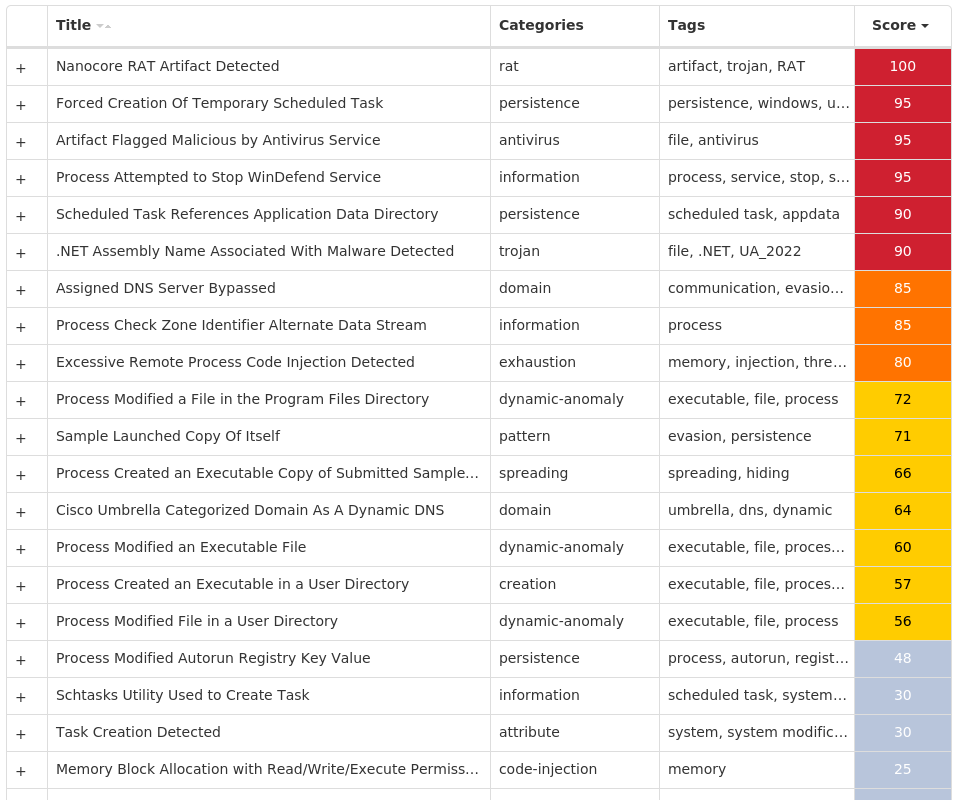
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-9985222-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 12 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @explorer.exe,-7001 4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: UpDaTe 3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: NXLun 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: DnDcR 1 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @C:\Windows\system32\DeviceCenter.dll,-2000 1
Mutexes Occurrences aBdraOSHWQtfP1 ImvdLkQNiWmhZ1 FOdhZrTOEIj1 Global\{cb7cb109-a06b-4fd7-8d0e-5290e77da5a5}1 RxDIBEIVVrpgGcjw1 obbAitLYlcWHDjd1 ZhStsilCCDoWCSTjZzsnSDITc1 LCEGTrpYB1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]154[.]167[.]2203 173[.]231[.]16[.]762 84[.]200[.]69[.]801 91[.]235[.]128[.]1411 104[.]237[.]62[.]2111 129[.]205[.]113[.]1511
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org3 api[.]telegram[.]org3 cp5ua[.]hyperhost[.]ua1 nonoise[.]duckdns[.]org1
Files and or directories created Occurrences %System32%\Tasks\Updates5 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp5 %TEMP%\UpDaTe3 %TEMP%\UpDaTe\UpDaTe.exe3 %System32%\drivers\etc\hosts1 %ProgramFiles(x86)%\AGP Manager1 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C51 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat1 %System32%\Tasks\AGP Manager1 %System32%\Tasks\AGP Manager Task1 %APPDATA%\NXLun1 %APPDATA%\NXLun\NXLun.exe1 %APPDATA%\DnDcR1 %APPDATA%\DnDcR\DnDcR.exe1 %APPDATA%\THGNjTonqYzAQ.exe1 %System32%\Tasks\Updates\THGNjTonqYzAQ1 %APPDATA%\lisuoa2h.jv31 %APPDATA%\lisuoa2h.jv3\Firefox1 %APPDATA%\lisuoa2h.jv3\Firefox\Profiles1 %APPDATA%\lisuoa2h.jv3\Firefox\Profiles\1lcuq8ab.default1 %APPDATA%\lisuoa2h.jv3\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1
*See JSON for more IOCs
File Hashes 0829ed65c94d0ad265f99961d35fe56915c7b506671ae27a4ff6cae75e49cc661273b8a3054090fdf04f696dd22f284639ccb57afe9aa0a657d6fdb8fbdd3bd1148a552de9c74376c409b18f2731c4dba0131c520c04a0cccb0af3364469bb732563e0db2599ab4c5d01fa046bc0706572b17a532ce52754f2977a735d8fbf01371f8375dde28de80b098d9e808df9de07a5d8f0ab13d086325984d73a9cd5ed3b704635a48f9ff94d44f0019e874ed71ddbc220bc3ce9f3cd7df38df120642a53d55a9c88eb76405269ee02a4c4818214be23b6793b348d817ebc764506e5af5fc15dd06f8ba66498c9865d6e82e6ff79c1f75284c5416ecb67baa8a604fa9770d209addc0fea8ad36babd76a4b11f247dc11c9d8c1b48fffaf4b0e38efe8867b9a9c4a56b756b499574a593ce6c5632f8a513abc4fd9a61844f211ffc672c890ab59d30c731411c996564775e58c6769535fd39e7ff51c48b690767c10f9e9b388b8fefb3086f17b010cb86fd23957822e9d913b8d99d5ed786c7969fbaf78ba846910ae2ae36a36f62eeaac3d693228dbe07d32484d23795414d5ac5908ffc8d7e38a611b60fe03397645b2ae0b3bc2aaa9604c68c81f0baf6565b813fb35cbf8d74421e9309ac79fd0556ef85c3b16e2bcf03fa196a5947eb3d0815cb1e6cf0f97b4319ac18159cf02f905f91d07d4fe70722aefef70e32abe1b1fab9e7ef7775262c09407cd3a8012620dd858aee083d645346d5419a4e16cff96eac373fe8dfa5a692cbfdcc238b360d8e7e2f07b673d7d7645d9d2a2eabd245213457c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
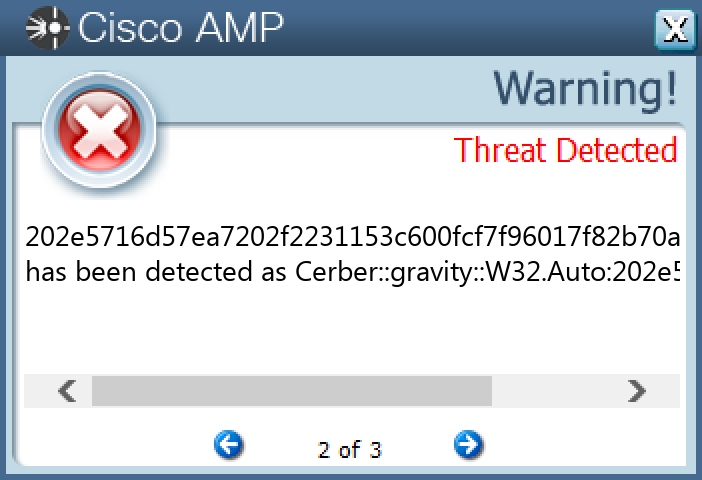
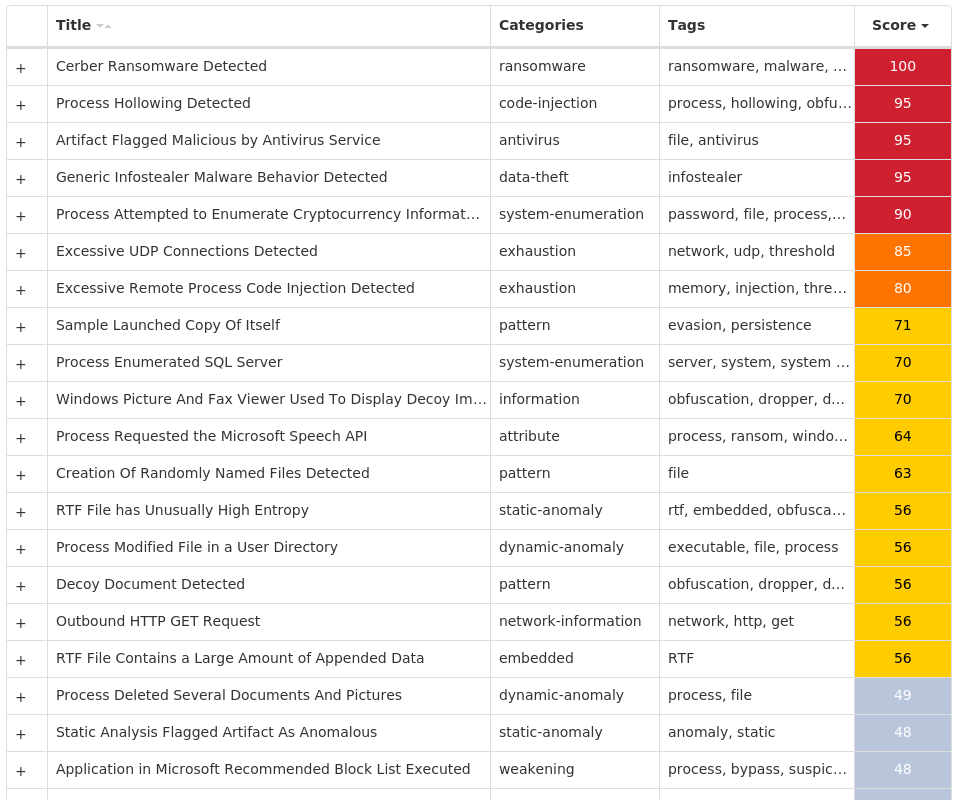
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9985289-0 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 28
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}28 Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!16613a828
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]128[.]255[.]17928 91[.]117[.]40[.]0/2728 91[.]119[.]40[.]0/2728 91[.]121[.]40[.]0/2228 172[.]66[.]42[.]23814 172[.]66[.]41[.]1814 104[.]20[.]20[.]25112 172[.]67[.]2[.]889 104[.]20[.]21[.]2517
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com28 bitaps[.]com28 chain[.]so28 btc[.]blockr[.]io28
Files and or directories created Occurrences %TEMP%\d19ab98928 %TEMP%\d19ab989\4710.tmp28 %TEMP%\d19ab989\a35f.tmp28 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat28 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp28 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp28 <dir>\_HELP_HELP_HELP_<random, matching '[A-F0-9]{4,8}'>_.hta28 <dir>\_HELP_HELP_HELP_<random, matching '[A-F0-9]{4,8}'>_.png28
File Hashes 04eb026fd69ee85a204deb1ab3d894fc95d543ff94667bc1f9baf05b77e1aa0c11dd9314fe25aa3eb43b042abf8b81b9e50fcfd79528b81288e3f98961789db6168ef2a56df0859de10120b164c6696d5affbf606fa9d6e79d78f6065d3edc031e0b0bfbc83d700f9583f730244b02b26b12ba1db5c50edbe3489418acc837de202e5716d57ea7202f2231153c600fcf7f96017f82b70a11d6f15cb637a28779258d29d87887f9e9303c0c23f466c6807c89f41ba19bc29d99d688971eb59c222e8e2e885a25bb09aa90943880e7d81b9addfc0013d76c205cc5f615028f18392f2f6a0ef0de62b9c305b24260b9208064130ea88d47a955f922a20f2be02ac031dc34001eb08664526ad2389b4b0cdf28214c595eba05bf0f84bf16fa6b119b341d486619e7e2f91de5be87f1bca56ab58c3edebcdc35a949ea306cc4f2c91b377df2eb0bffe8d47667a343f80f0dff71a47227369f8a63a5336736fca1718d3d3382e61f289dd249b6817a694dc2c5ddfcdce7dafad7d1f3074e04bfa9442d4843ee4070f7d7a3c6e06e2e1ba26014c1d1b54ba1ca6eed552ddbb7ffa76d7b4e38a707a26fda9ba556cc17b79cb01121a51e6692809c18afe36e491b39174d4f6e0e822cfb6ffa0cca7c80bd33a8184912e6621aa28459e06f70929d9d36d9562f05f30ffb78866d0077785cfb36d11200f44dbf4abd68b4c43b016a136f8d57631559806e8a977e616b9c00fbe3ff2a957d5c65bbd4bbd5fcd53a63489949588c4714537fe5243b82572b8b98d2cc83cb99a18d188eaf883791e5125786da5a21751f48b27dff8488521a6113a4e102164ad68f1d6ac43f90b8ad7a0ebc8d693969c204a6b9714af4128612abeb08e36fbfc03bbef71accd253b0895b45b5793c06d0016e679f27a26643ff229dc942588838874fa4605961c74d10c34a497e319635b05f872bcde07b37a87c45ac59a19cc403062b0a7a18125f6aa07d027f73061dda346d0528d01f811e508b5fc47076df69503576032053166340d2af80654347845e9392f5039a94342f7b28c345c1ae6766939d7bda21360bf605bd8444fb5e16ca451dad9a315610b43a604ded969009404bf88110f9a840cbd96b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
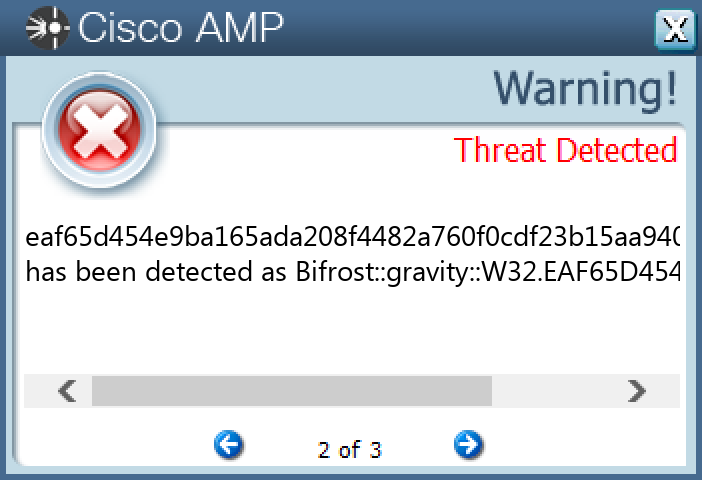
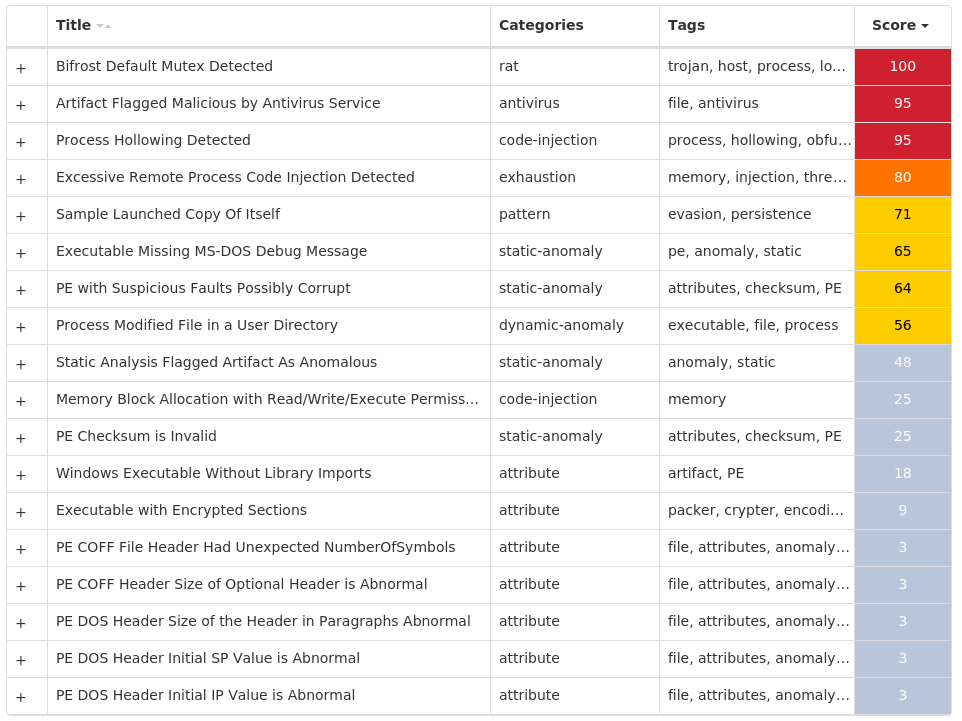
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Bifrost-9985293-0 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 4 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 3 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN3 <HKCU>\SOFTWARE\((MUTEX))2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2}2 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @C:\Windows\system32\DeviceCenter.dll,-2000 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: 36412 2 <HKCU>\SOFTWARE\((MUTEX)) Value Name: ServerStarted 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2} Value Name: StubPath 2 <HKCU>\SOFTWARE\((MUTEX)) Value Name: InstalledServer 2 <HKCU>\SOFTWARE\DC3_FEXEC1 <HKCU>\SOFTWARE\CYBER Value Name: NewIdentification 1 <HKCU>\SOFTWARE\CYBER Value Name: NewGroup 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN1 <HKCU>\SOFTWARE\CYBER1 <HKCU>\SOFTWARE\CJSXZ1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{05ACO487-3Q28-LSLC-XN56-108QEJS54A88}1 <HKCU>\SOFTWARE\CJSXZ Value Name: ServerStarted 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{05ACO487-3Q28-LSLC-XN56-108QEJS54A88} Value Name: StubPath 1 <HKCU>\SOFTWARE\CJSXZ Value Name: InstalledServer 1
Mutexes Occurrences UFR36 XTREMEUPDATE3 ((Mutex))2 ((Mutex))PERSIST2 ((Mutex))EXIT2 25621007962 lol2 CWSPROT20S2 Administrator11 Administrator41 Administrator51 DCPERSFWBP1 Bif1231 CJSXz1 DC_MUTEX-3MWQJGB1 FR725I0U8LRK051 FR725I0U8LRK05_PERSIST1 FR725I0U8LRK05_SAIR1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 20[.]72[.]235[.]822 146[.]185[.]235[.]2452 52[.]8[.]126[.]801 217[.]69[.]139[.]1601 208[.]91[.]196[.]461 104[.]96[.]229[.]1491 199[.]191[.]50[.]1661 31[.]170[.]164[.]191
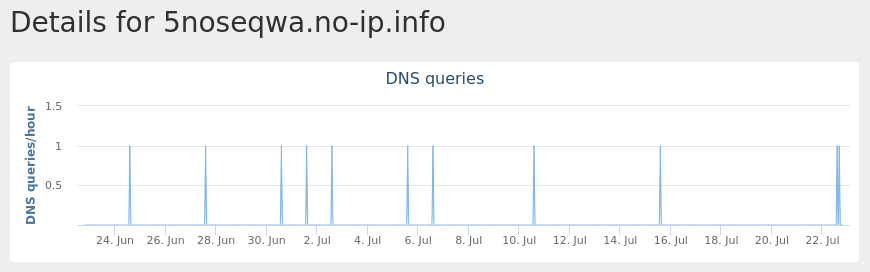
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 5noseqwa[.]no-ip[.]info2 ftp[.]vlakkeeetert[.]hol[.]es2 f4n6[.]hut4[.]ru2 smtp[.]mail[.]ru1 www[.]server[.]com1 ati2evxx[.]sytes[.]net1 x1[.]i[.]lencr[.]org1 kiwa[.]no-ip[.]org1 lolzor2h[.]zapto[.]org1 jalagui[.]no-ip[.]org1 www[.]webserver[.]com1 exploreinquiry[.]com1
Files and or directories created Occurrences \TEMP\ufr_reports5 %TEMP%\tmp.ini3 %APPDATA%\Microsoft\Windows\((Mutex)).cfg2 %APPDATA%\Microsoft\Windows\((Mutex)).dat2 %ProgramData%\Local Settings2 %ProgramData%\Local Settings\Temp2 %APPDATA%\dclogs1 %SystemRoot%\InstallDir1 %SystemRoot%\InstallDir\Server.exe1 %TEMP%\Administrator71 %TEMP%\Administrator81 %TEMP%\Administrator2.txt1 %TEMP%\x.html1 \directory1 \directory\CyberGate1 %APPDATA%\addon.dat1 %APPDATA%\Administratorlog.dat1 %HOMEPATH%\Documents\MSDCSC1 %HOMEPATH%\Documents\MSDCSC\msdcsc.exe1 \TEMP\ufr_reports\NO_PWDS_report_25-01-2023_02-45-25-726A6BBD-JDGK.bin1 \TEMP\ufr_reports\NO_PWDS_report_25-01-2023_02-43-24-726A6BBD-AIAB.bin1 %ProgramData%\Local Settings\Temp\mswxle.bat1 %ProgramData%\Local Settings\Temp\mswqmnvv.exe1 %TEMP%\report_25-01-2023_02-44-14-726A6BBD-FDGN.bin1 %TEMP%\isendsms_setup.exe1
*See JSON for more IOCs
File Hashes 0309e6c7cd2a73721e6956af2ec340c948bc5009450f76c9337ded167e60cfbd26dfd674facde0f957bb4ed81e7cea4dae37114ced4d59c491d86bfc667d5dc432ac27ab6cd0654430449b0624a744169e2d0cc6769192fd79599e1ab67176323596f41561adf0d6eeb205b7414e17993f20da0590a28d2a4c94d984fd327fa849704324bbf8ffde957586c01cc85d45a970458d2697fe34f381d7cb82d7f88d4c1986ea7e1ecea980fad59a62ddbf472bc2d7344c923332fd48f41dc6fbbe4852fe24425eb3e6248e59fd959ce1956e09d1cbb65809f63706f0f9170ea0eb485c86c8c3bad2edd4174675a5dbab131d9b84ca5e5325431d2fa91d1c22292afa6946be08c392001c142ad89213ff0860f3f3eac188b30c877e10783d435334ba73d73c1a9f1e4494f550597a9d2438a79ebd900914c8b0851164aea5f1cb688e7d2f5afc77e09d02b604cbdbfb5b33941914296966306761478609a23cd3a14e975d3f301392e173335b801f6a12e3a7556ba00c2984a968ca033a44e69610c3a6ab70d56a50d8446028ec0fef89bbde4e4a5784fd8a471b50392c0230d88fb0b1da9aaa33886f2d103540ffd831f46d5f97280eca05f8013e277579cfd0051ac1504e3f1b761540498a0fde42e462c0b20676502981ce84aa41049550159aabc2014131fcee489c7e1c4a943237bd89dfeb5ba2ab1216ff89cfb202b00e2671ca566fce1a39c24dd34479446524eac96d5e43634134e9e7616d2a18d5fba5cadf05799c88e4cb5cbc2661b83e286d3247fa682dae330e6932c52a1d661935cbeaf65d454e9ba165ada208f4482a760f0cdf23b15aa94022aa9617bf03609f2ff5e2cf6885a62fad9a6488a8487e0490e5892bfac0dddeff515ba97b2b86d2cd
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics Umbrella MITRE ATT&CK