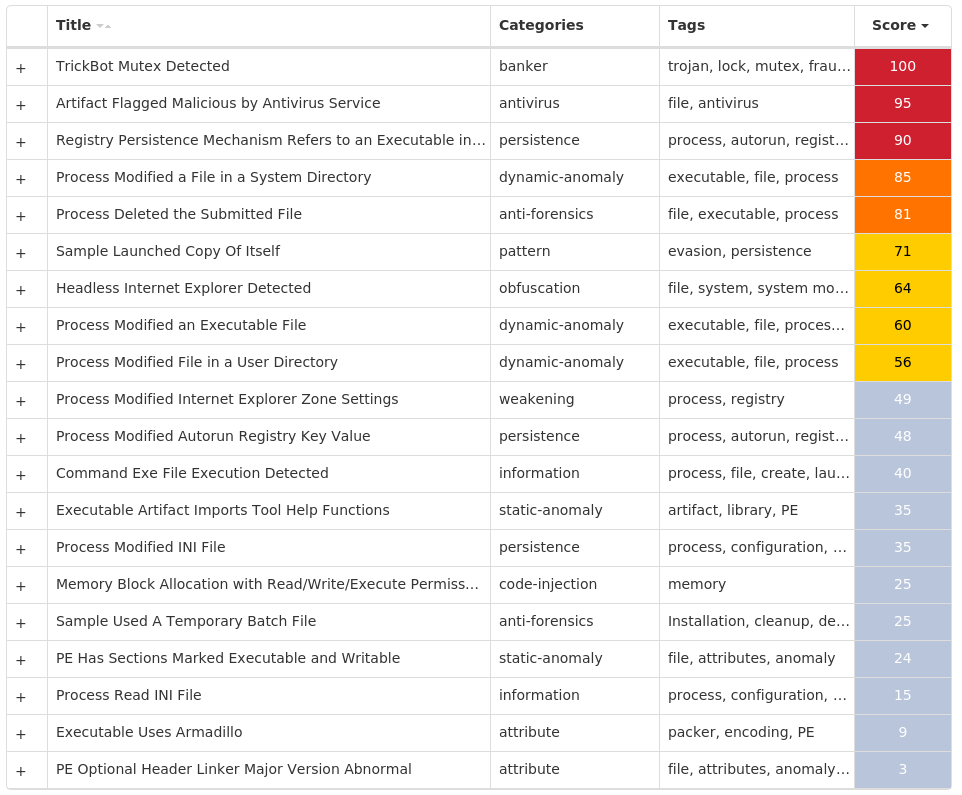
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 27 and Feb. 3. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
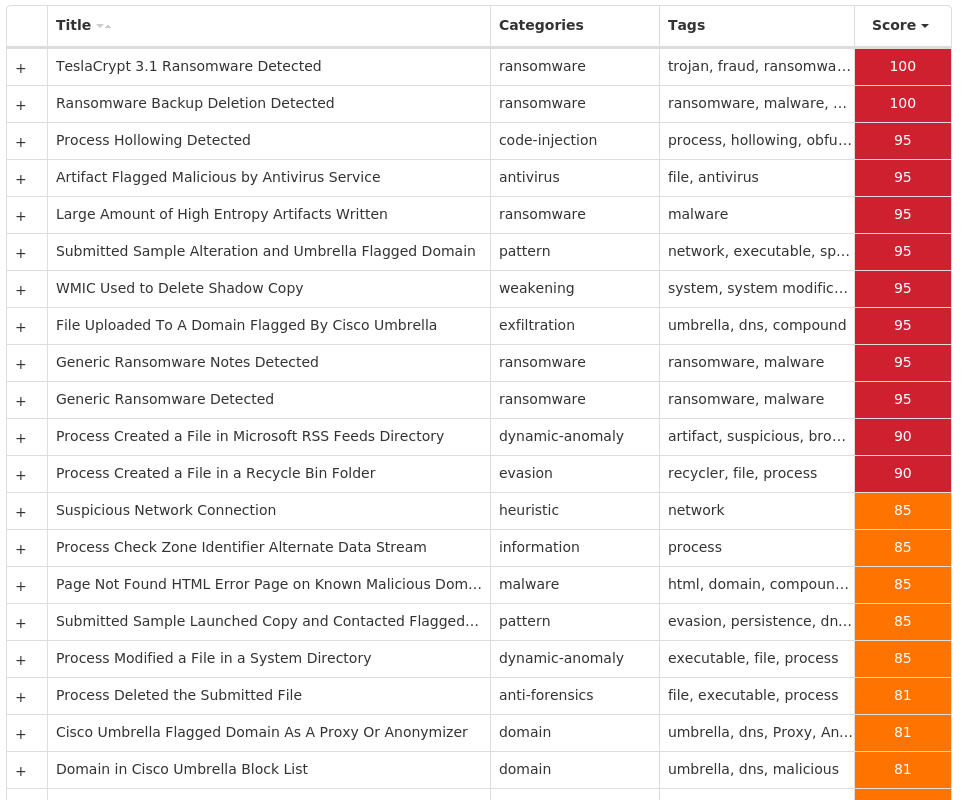
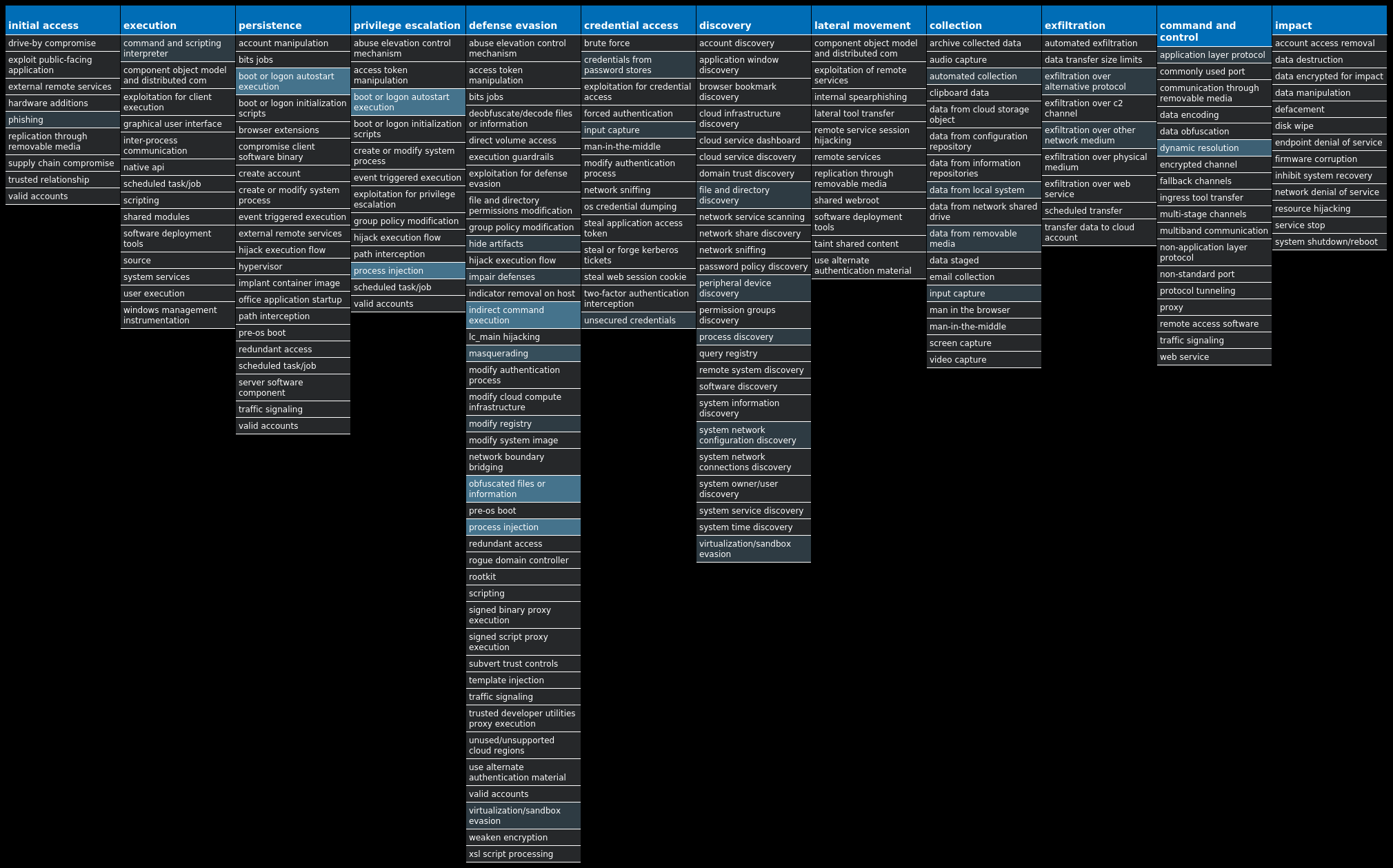
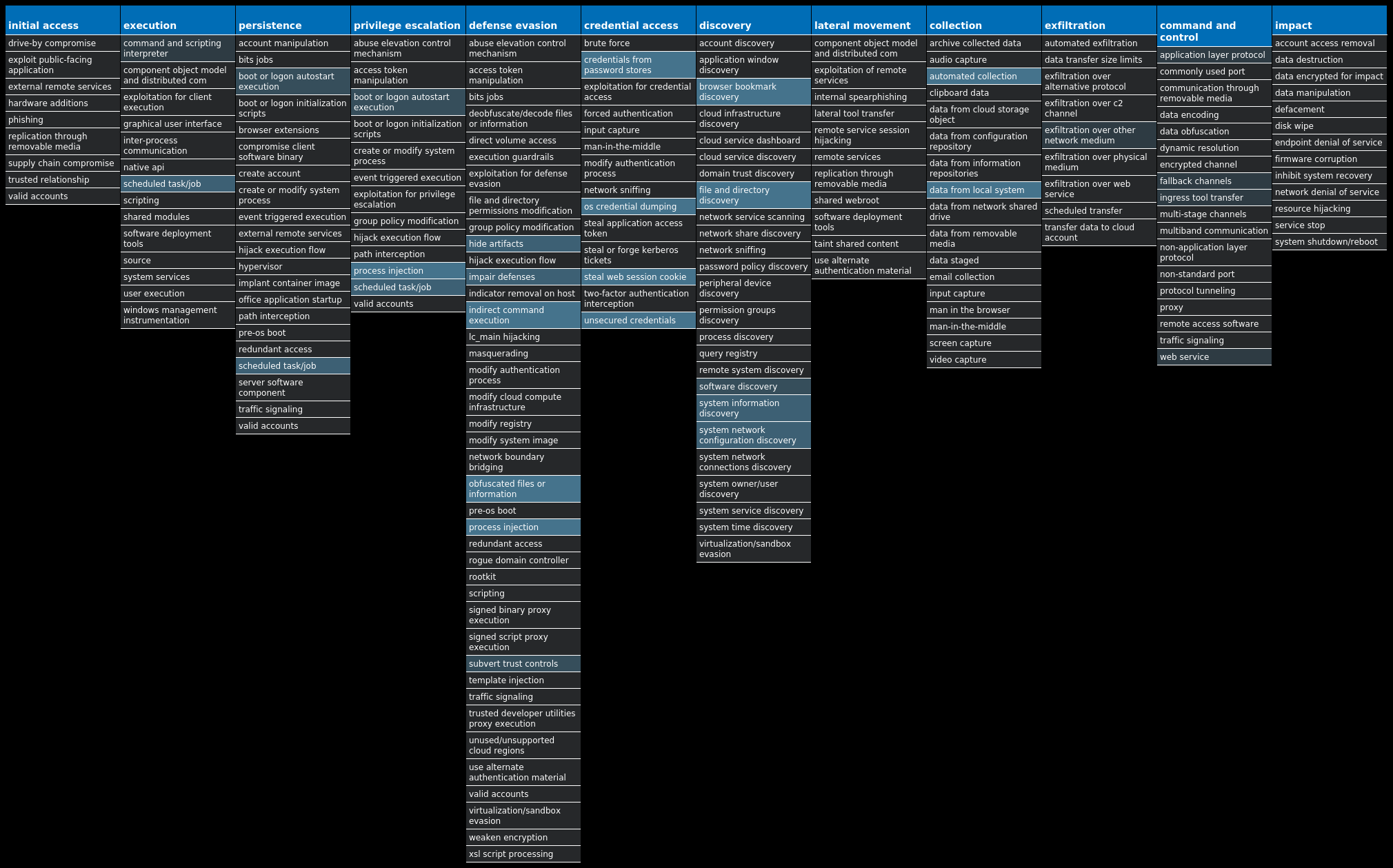
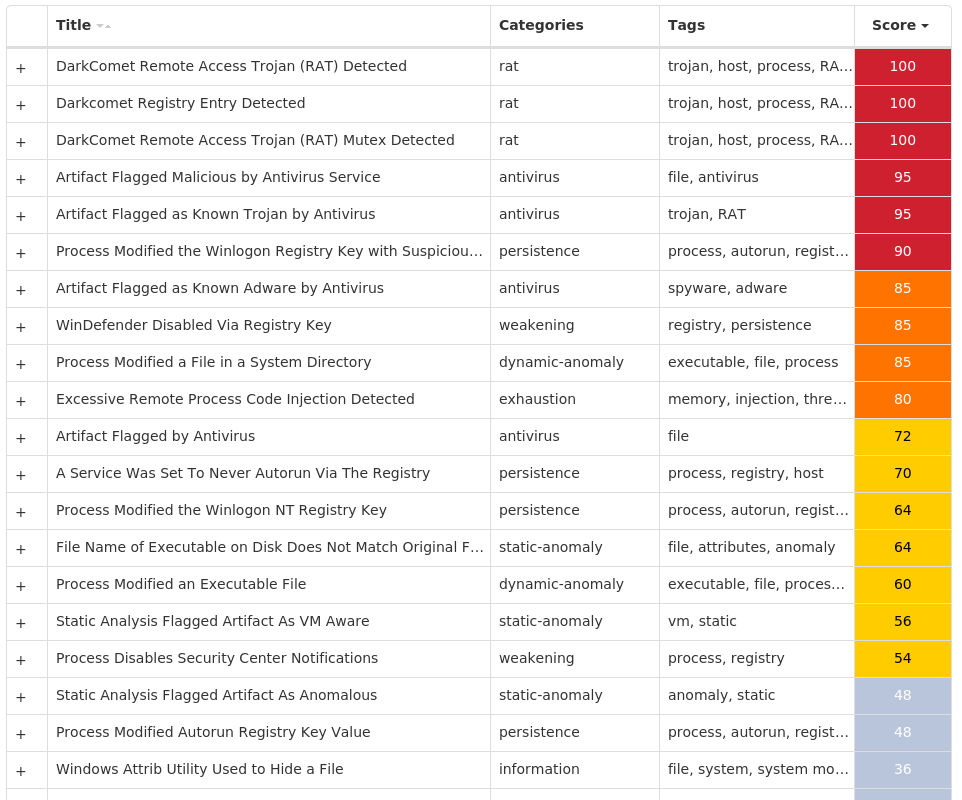
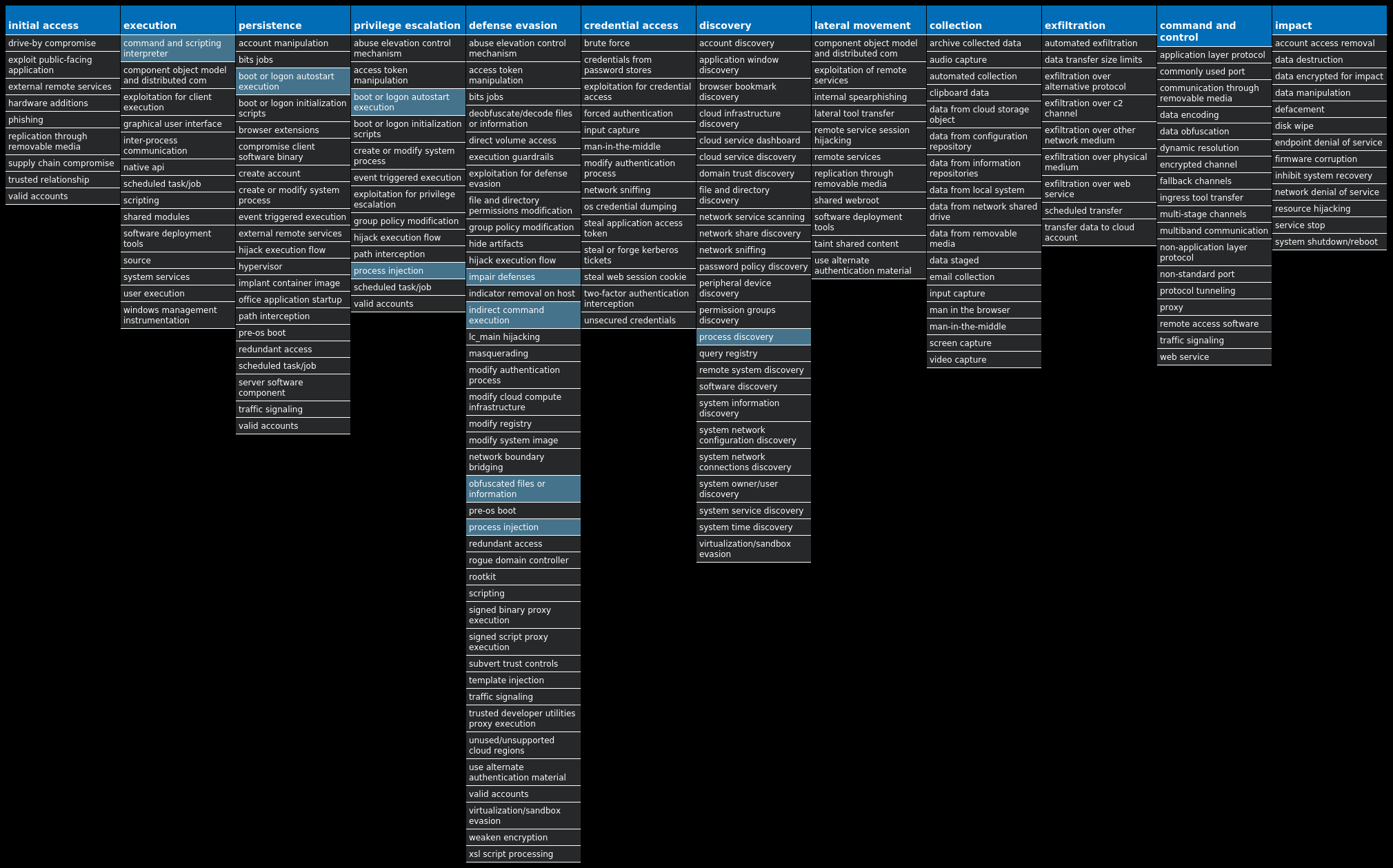
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
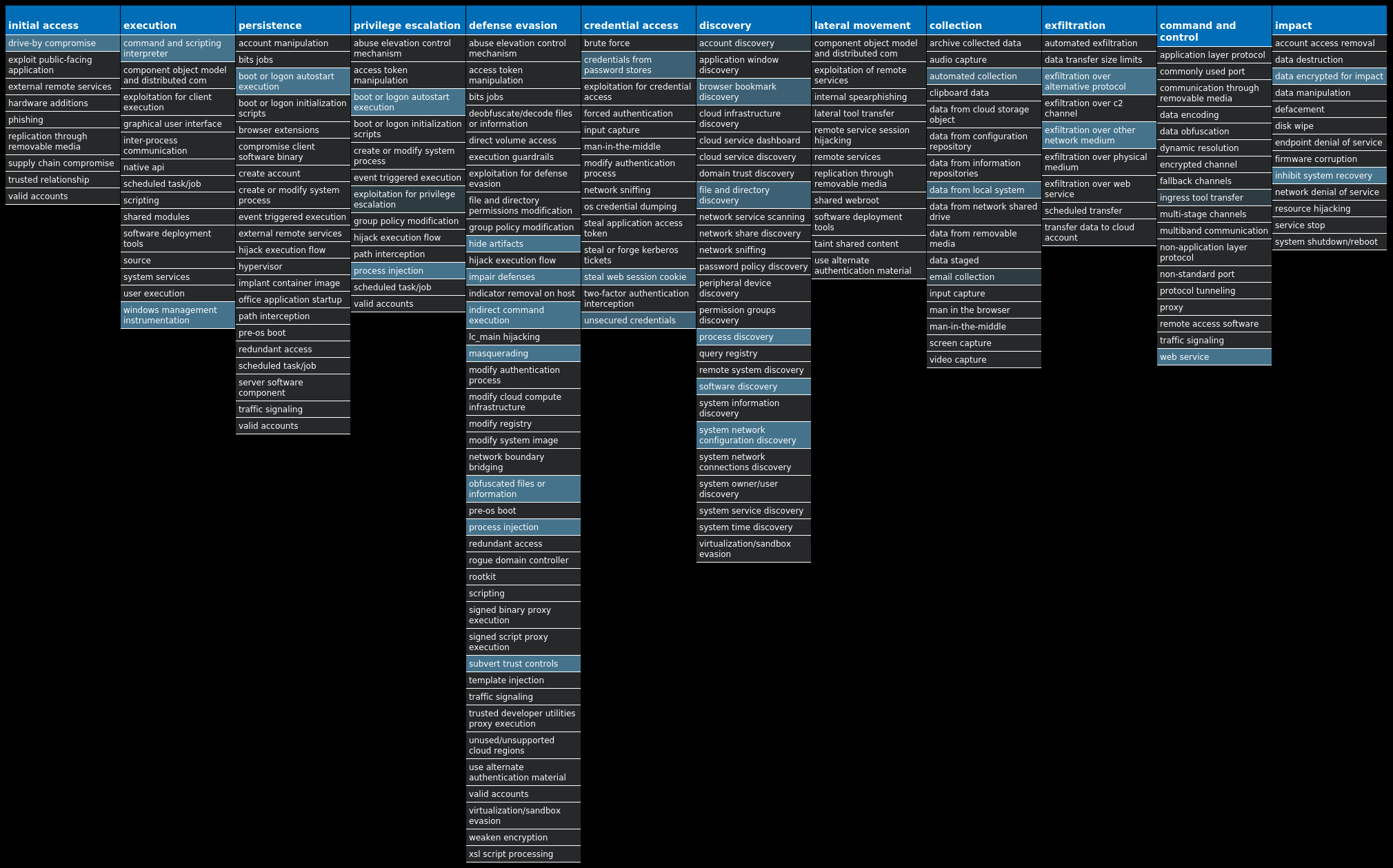
Threat Name Type Description Win.Ransomware.TeslaCrypt-9985404-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Trojan.Barys-9985440-0 Trojan This is a trojan and downloader that allows malicious actors to upload files to a victim's computer. Win.Dropper.XtremeRAT-9985707-0 Dropper XtremeRAT is a remote access trojan active since 2010 that allows the attacker to eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs. Win.Dropper.Remcos-9985482-0 Dropper Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Dropper.Formbook-9985599-0 Dropper Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard. Win.Dropper.DarkComet-9985655-1 Dropper DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system. Win.Packed.Shiz-9985661-0 Packed Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. Win.Virus.Expiro-9985780-0 Virus Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Win.Dropper.TrickBot-9985782-0 Dropper TrickBot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts.
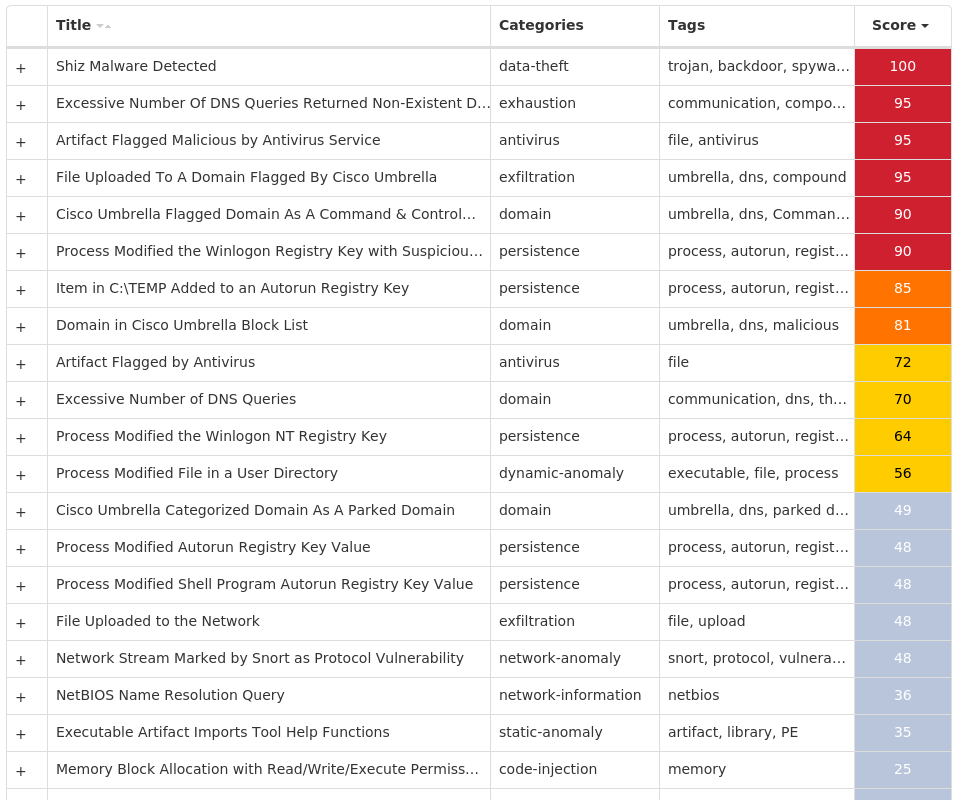
Threat Breakdown Win.Ransomware.TeslaCrypt-9985404-0 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 34 <HKCU>\SOFTWARE\ZZZSYS34 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 34 <HKCU>\SOFTWARE\ZZZSYS Value Name: ID 34 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>33 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 33 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL Value Name: NodeSlots 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL Value Name: MRUListEx 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\\1 Value Name: MRUListEx 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\\1\0 Value Name: MRUListEx 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: nbmjtgb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: oobeuyf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: udesqei 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rnawquh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fqcmsew 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xpiqopn 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lvywdxv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hbbrjsm 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: gucjfra 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hktrybh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ltivtwk 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ohwpmay 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lsbbsfv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hxtgtpa 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: imlwdse 1
Mutexes Occurrences 345432-123rvr434
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 35[.]205[.]61[.]6734 185[.]87[.]187[.]24534 192[.]124[.]249[.]13734 66[.]97[.]45[.]21931
Domain Names contacted by malware. Does not indicate maliciousness Occurrences adrianadoms[.]com34 tocstartup[.]com34 drcordoba[.]com34 edge-institut[.]org31 www[.]informaticauno[.]net31 iheartshop[.]net31
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\mn.txt34 %ProgramFiles%\7-Zip\Lang\mng.txt34 %ProgramFiles%\7-Zip\Lang\mng2.txt34 %ProgramFiles%\7-Zip\Lang\mr.txt34 %ProgramFiles%\7-Zip\Lang\ms.txt34 %ProgramFiles%\7-Zip\Lang\nb.txt34 %ProgramFiles%\7-Zip\Lang\ne.txt34 %ProgramFiles%\7-Zip\Lang\nl.txt34 %ProgramFiles%\7-Zip\Lang\nn.txt34 %ProgramFiles%\7-Zip\Lang\pa-in.txt34 %ProgramFiles%\7-Zip\Lang\pl.txt34 %ProgramFiles%\7-Zip\Lang\ps.txt34 %ProgramFiles%\7-Zip\Lang\pt-br.txt34 %ProgramFiles%\7-Zip\Lang\pt.txt34 %ProgramFiles%\7-Zip\Lang\ro.txt34 %ProgramFiles%\7-Zip\Lang\ru.txt34 %ProgramFiles%\7-Zip\Lang\sa.txt34 %ProgramFiles%\7-Zip\Lang\si.txt34 %ProgramFiles%\7-Zip\Lang\sk.txt34 %ProgramFiles%\7-Zip\Lang\sl.txt34 %ProgramFiles%\7-Zip\Lang\sq.txt34 %ProgramFiles%\7-Zip\Lang\sr-spc.txt34 %ProgramFiles%\7-Zip\Lang\sr-spl.txt34 %ProgramFiles%\7-Zip\Lang\sv.txt34 %ProgramFiles%\7-Zip\Lang\ta.txt34
*See JSON for more IOCs
File Hashes 00bf94b15560a365961a6ec0377125e1ef39d820d6dbfa378185707f6af35ae004c89b8a0f10c5e1568ed9097a0688ca60bde90ee967bb1c009897a7f3b4888e055481780ed5cc639ebe08539dd04a5299a34c81abb7210868d306b799ec0e7a07fd66fffac41c030a0a0385807a55047b7d9d5e9e64a68fcca7243c1a3bcf200a2d2a5c3a17a93da80e275d5ffc83814084d17985c9191431eeae054f182f6c0b17c081060be4975e1fc41f929b27c30077b471da401aef273ebb96631f1e96101a48c59fa7b5ca1f9ac7b72b4684da9ae5a6fdcb4f36b55c1c886c0b873d831c0c2a3695d71897ec5826bb038d8af10bc76450f908027252c2c347d78b62391d1101ee1aabf9c944567f3a8b749c95fa1e842b813b730d3153dc5bee5547b5213b9809092bf960014f911398f91aa267021c519beaa8fbdaa30366108ede1a2f4dfdf44d4454d0f6d3f77eec371d7feaf2a26c25a29e38d03e85cc8162fbd93b26dfda2bb97b7ddc9494b5e29a275f86b29bcee0562d308f917b0df35a20fa48051abf99eb35dfcb13414e979c6d147b1bb8faf111eac943331b17fb6dffd05194232df8f17a495b057aa8da1a511ef0374ee0063643ad8d010fa7ba32e1f85c8daa02bdc068920ebeae53ff4577eae39e39561b5db12e7e22eb5c081a7c425e041d722d83b7fd3b1d1207a63fe7e53bf3d091f2b237f32810e12f97d9c8865e144664268057d7d48d5c504c93eac270332519ecd0a223711c8746d0271a09630998d841a8a9b0a2aa41f022ba72ff964345804746c3b2c6226ed585a1cc306789ad990b22c352423c289ba77bcb4e38a796b9d2d0aaf77b9371c0e1d3900e679ae8e833d4bf9ac267ae1ecb3ce875f633b2774004cff42b43eb6e4f3965bc7b832ab4034e1302ef882ecd63eb70d00949152f26e5d0b9a04a2b68e3903f8b7c9e78c548dce7c1ce6afb0ed6718dd63fc432760571114e4053cf13ecc011b085a22270e90ad69392491b1f568e2c4a5ea7212f2e0c2f15b5acdef600a4216a894b084d1fa4b0bfb553b02e7f8508fdec92fef5afa4fd30e35d030639bdb7d48f28a171e69591ead7ad3db27bb980412a38e90e6d08604e3c5c37d3d7d30829
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
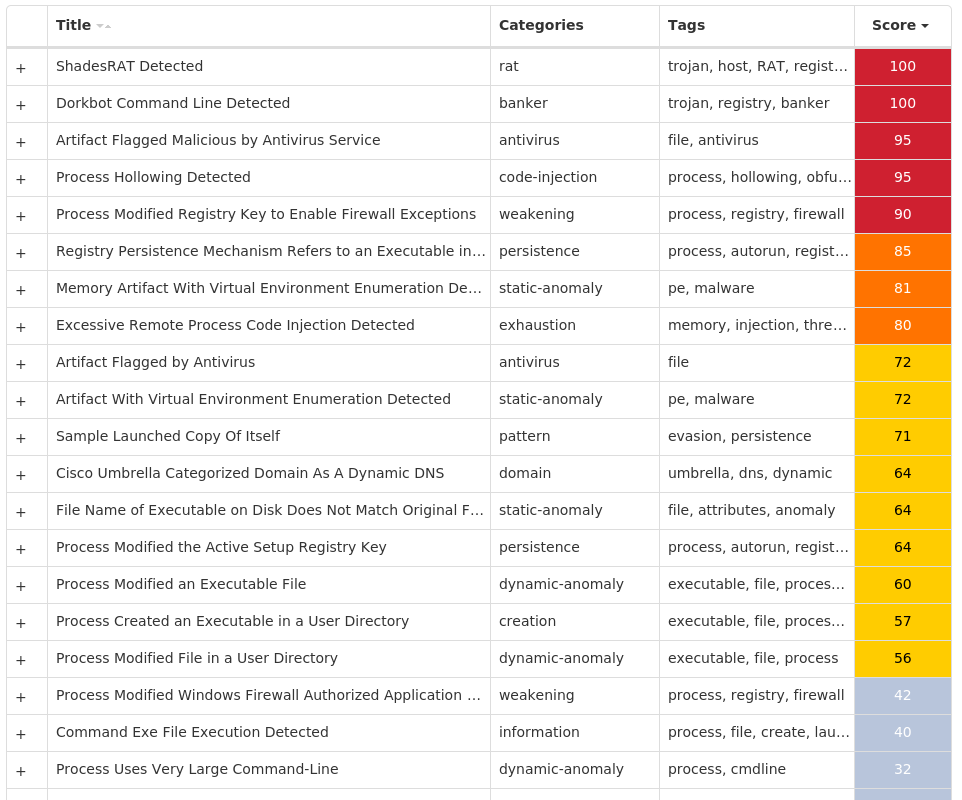
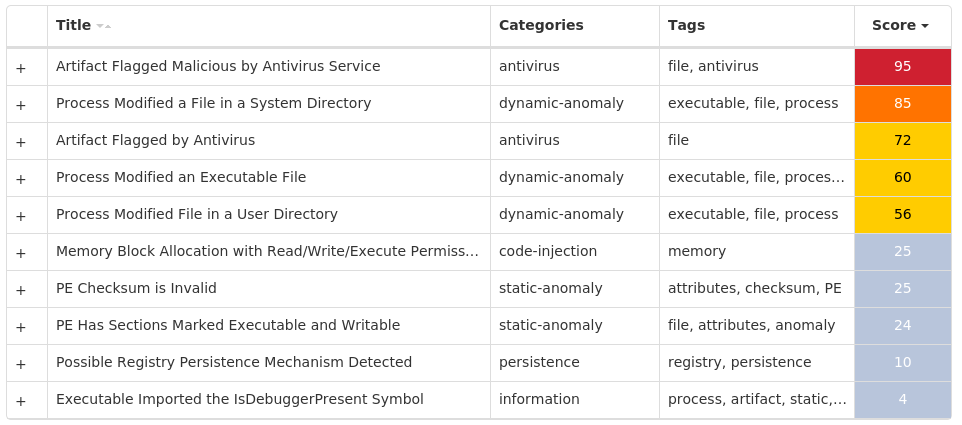
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Barys-9985440-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 26 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL26 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS26 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST26 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE26 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B4BFB70B-CBAC-86F8-BA7E-E98CC7EABA8D}26 <HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B4BFB70B-CBAC-86F8-BA7E-E98CC7EABA8D}26 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B4BFB70B-CBAC-86F8-BA7E-E98CC7EABA8D} Value Name: StubPath 26 <HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B4BFB70B-CBAC-86F8-BA7E-E98CC7EABA8D} Value Name: StubPath 26 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE Value Name: Q6UUSPIC65 26 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\Users\Administrator\AppData\Roaming\Swat.exe 26 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID25 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID25 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID Value Name: Q6UUSPIC65 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\f3d38ea5f9ba9c7334834c3b0f6ab0a062645d85d221b222d98a8f320d8b9563.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\009f1ec7c51398152db52064c3d271e601ccab8ddb33eaab6b6a6364b78dcdc4.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\0eca92089500a87412f8fe9400f9a7c1ae05c5e09d601f93d1e7c3b4c3d874dd.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\0b2c145f227de877c9b0539839951154f79ed4d15f4e681f74ae706cecab3db3.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\13b138bb4b71507d71d6c64d31a175e338048bdb830964d7998a000d1168f42e.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\04ee4488800161949dd91c5f80a82abd7bd2e71b35f2de743e65d45cb11ed290.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\05b0512d53800782344069835635ae3ac8a3bb9981f99b56193ee4315809289f.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\01092fd96e8f192acd2e2e5118dac67fae6157d218f9f9a915cd854953b41e39.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\0c997955d752296f77a7f1dc68eb01ccd63157342bedb3fd83e57bf97b9b301d.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\1646959c9a464bca27a352a0b4bb63e969ec342daad043c1413cadc854b00d24.exe 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\TEMP\0c00f6710d735133c5d6b953e89339d6e18db1ddda2993d95903523464e8ccf6.exe 1
Mutexes Occurrences Q6UUSPIC6526
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 212[.]117[.]48[.]24826
Domain Names contacted by malware. Does not indicate maliciousness Occurrences j8p[.]no-ip[.]info26
Files and or directories created Occurrences %APPDATA%\Fresh26 %APPDATA%\Swat.exe26 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp24 %TEMP%\pae96.tmp1 %TEMP%\kae77.tmp1
File Hashes 009f1ec7c51398152db52064c3d271e601ccab8ddb33eaab6b6a6364b78dcdc401092fd96e8f192acd2e2e5118dac67fae6157d218f9f9a915cd854953b41e39033dca7f44bf455cb4682aa7e2905fc61d76e50879bc1abce8246756fb6d82780488259e35476b4b869285899b4342c6fbf1d3c6d091bc64d34df465c217307d04ee4488800161949dd91c5f80a82abd7bd2e71b35f2de743e65d45cb11ed29005b0512d53800782344069835635ae3ac8a3bb9981f99b56193ee4315809289f088628babd6844408d1b1b13a4e6ab56eb4de7bc069fa0b5dfd9ac6e5e7d6162091a4051ad8b86b943f6ae73b8aed6ac96faea913e6157f10eea64de4b9e8579094a11660b938acbea1a97d730be269deccb1a3ab1d7b3132e36f46556681fa50b2c145f227de877c9b0539839951154f79ed4d15f4e681f74ae706cecab3db30c00f6710d735133c5d6b953e89339d6e18db1ddda2993d95903523464e8ccf60c5916f4245ae5c739dab218a61b9da76fa500dffa4e216bdd007e906629c6170c997955d752296f77a7f1dc68eb01ccd63157342bedb3fd83e57bf97b9b301d0d0ac40a0d28d339951bf22870115f9ee0c82ff12cf00a520c92d19c1b85eac20eca92089500a87412f8fe9400f9a7c1ae05c5e09d601f93d1e7c3b4c3d874dd0f5b160179e930e3f05059ffc40c959c7fa31e16372512ac4ebdd5afbce6d26d1148ee059fe060f4ead316a2c17383f0748fbed5abef3520736d4dd628e4c7be1249a90af1e47efe5fcca5420f878994fe0e9e1032bf98fc3173d537058f0ecb12cca5ba5947e5967101896ac4e1904797b0895c2c02afee873995b8959ba8fa13b138bb4b71507d71d6c64d31a175e338048bdb830964d7998a000d1168f42e1511d9e223ad4f5a7f648c7343c1ec4462dd28f1fb9088d267caf72c4cf27cfd161611e39a22e12bdbf452dc9b19ce0593eb53e97aaa2a2f92adc003273abeb216378adaffb32b0426986538bd567a8871980c2fc373da8236831e29ae593bfa1646959c9a464bca27a352a0b4bb63e969ec342daad043c1413cadc854b00d24167a8b41724b3a563c246197b8f6b0516843b22b3fb4daa38cc2a5e35858dee6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
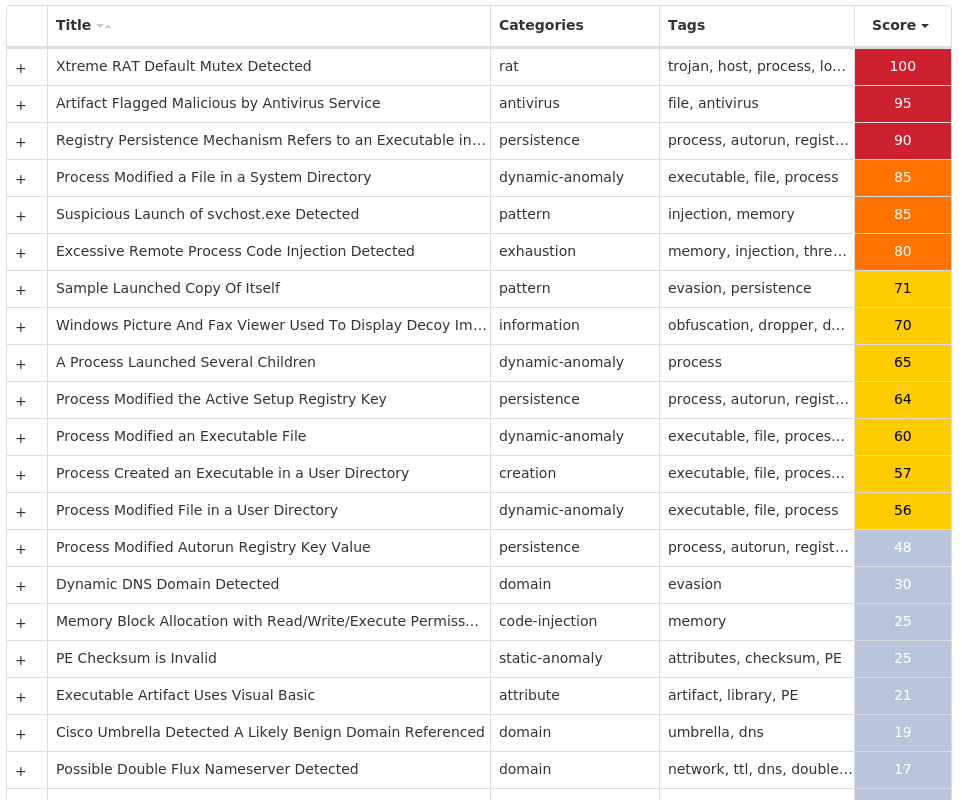
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.XtremeRAT-9985707-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 9 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 9 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN3 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS3 <HKCU>\SOFTWARE\E&BA09AZL3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{NH8ONC0M-V2S2-AQ8L-8OGF-WNY1SA685WDT}3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{NH8ONC0M-V2S2-AQ8L-8OGF-WNY1SA685WDT} Value Name: StubPath 3 <HKCU>\SOFTWARE\E&BA09AZL Value Name: InstalledServer 3 <HKCU>\SOFTWARE\E&BA09AZL Value Name: ServerStarted 3 <HKCU>\SOFTWARE\DC3_FEXEC2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: restore 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: restore 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: restore 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{02CEEFAF-818E-BDBC-F997-0A95FB467D1E} Value Name: StubPath 2 <HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{02CEEFAF-818E-BDBC-F997-0A95FB467D1E} Value Name: StubPath 2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID Value Name: H9MOWGZL8K 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\Users\Administrator\AppData\Roaming\Microsoft\restore.exe 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE2
Mutexes Occurrences XTREMEUPDATE9 E&bA09AzL3 <random, matching '[A-Z0-9]{14}'>3 DCPERSFWBP2 H9MOWGZL8K2 7B8aP$W2 MUTEX-CC3DTGP2 _x_X_BLOCKMOUSE_X_x_1 _x_X_PASSWORDLIST_X_x_1 _x_X_UPDATE_X_x_1 ((Mutex))1 ((Mutex))PERSIST1 ((Mutex))EXIT1 ***MUTEX***1 ***MUTEX***_PERSIST1 ***MUTEX***_SAIR1 25621007961 lol1 WIN7LDRMU1 vb9WpnVgQidk51 Global\23832241-a080-11ed-9660-0015175300e71 Global\23d41101-a080-11ed-9660-001517d40a311 WindowsFir3ewal4423633334631 MAIN_-7421399971 %h2FmB8N1
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]159[.]140[.]2032 75[.]2[.]70[.]751 99[.]83[.]190[.]1021 20[.]72[.]235[.]821 66[.]218[.]88[.]1671 66[.]163[.]170[.]521
Domain Names contacted by malware. Does not indicate maliciousness Occurrences entony[.]no-ip[.]org4 sandra81[.]no-ip[.]org3 6noseqwa[.]no-ip[.]info2 kura[.]myftp[.]org2 cromitest[.]no-ip[.]org2 testmicro[.]no-ip[.]org2 x1221[.]zapto[.]org2 smtp[.]mail[.]yahoo[.]com1 test1 cmjc[.]whhcd[.]info1 chinato[.]no-ip[.]biz1 asdawe1 felloh[.]com1 itsonmx[.]no-ip[.]biz1 marques444[.]no-ip[.]org1 nickyowned[.]no-ip[.]org1 legolas8[.]no-ip[.]biz1 fatal555[.]no-ip[.]biz1 daniel157[.]no-ip[.]org1 infeccionmaestra[.]no-ip[.]org1
Files and or directories created Occurrences %SystemRoot%\InstallDir7 %SystemRoot%\InstallDir\Server.exe4 %TEMP%\Administrator73 %TEMP%\Administrator83 %TEMP%\Administrator2.txt3 %APPDATA%\Administratorlog.dat3 %APPDATA%\Microsoft\Windows\E&bA09AzL.cfg3 %SystemRoot%\InstallDir\webcam.exe3 %APPDATA%\Microsoft\Windows\E&bA09AzL.dat3 %SystemRoot%\SysWOW64\install2 %APPDATA%\MSDCSC2 %APPDATA%\MSDCSC\msdcsc.exe2 %APPDATA%\Microsoft\restore.exe2 %APPDATA%\Microsoft\rigsis2 %APPDATA%\Microsoft\Windows\7B8aP$W.cfg2 %APPDATA%\Microsoft\Windows\7B8aP$W.dat2 %APPDATA%\logs.dat1 %APPDATA%\Microsoft\Windows\((Mutex)).cfg1 %APPDATA%\Microsoft\Windows\((Mutex)).dat1 %SystemRoot%\SysWOW64\Microsoft\Plugin.exe1 %SystemRoot%\SysWOW64\install\cmd.exe1 %APPDATA%\1.bat1 %SystemRoot%\SysWOW64\install\plugin.exe1 %TEMP%\459sexy.jpg1 %TEMP%\459sexy.jpg.exe1
*See JSON for more IOCs
File Hashes 0b003ca58ea39b22dc1762d60193b9a9cba6ad543321df6388bb3cfd81eb1a4024b34a24aa2ee2ca545a17a0eb348177322d90e638f5aa7bac69da72781d9b382c89b3049c5575c4f46c1a0e542966f8eb0481e0e2416e462d0d1de0582eb38a301a64e86b283b132b960d1d5341d58d4c450632430da8b3f5002da0a302597135b8b14994340558a4c89dfc7a74022c4b61b54eda1888d3c67191a3f2b3849e37f75e81fc7a8a9dae5965adbe61b5daebfee49e8bd94b729c87fb66711782e03b6fe25066ec58e347a7c6df3a54e011f1d3a7bacc80a17ece9f2e6c3c0a076643e478681ce21820e20c1ab0bd9dc95de8ba613ea34a51b0bde1904a1b7e9c3247345e7ea05a113892e6420a1a74596c9a94e4dad54ddab33cd6229f6451afd3477a1303031a8019c78b0c1c6d62d5dc7e21a89f8ef3a85bbb5230f4789cc72b47ae5d6d81fb747783a91ad8058392e744c5251d902462699a368149eb568c6d53a8010c7cefbcc287750d57736fcfd750e25d456c2120fcc525bc70a63a70b06577d660cda14fc5e8737068fc275b3791b413f8f4576826a236e351dbd842a77cf80b7f6acba3932a6469756748868a0fbb65283113cc6d162c8ad2d0af6638837fc6394f9b1ac11a99a5938a8b026c4b97f8847000ffec538a9a0909761e3b88707801058d1b8b55ad3fed37ec727d1bf784cf9942965779a51df69ce4c6519dd25c03f613b0ea7c7cb945f2eefbae477311620e1e0f40bf2b4a11b9ebbba5af595be13be2f8f0162f8637e1351b49a8b600c3bc56e46e5e84eff701b0dc2ab27c07bd657d797e5c19109f32201701097acedb21ae286c4a9aec3b66e08d80b6f64caae4854d4960307e864df0e4d296edab9f17793027edb4c2508ab7f093b77d0aec4c12a67d03a160477c8f9eea980b231807883aba297fe49098127086b7f052381885a6ee33286419bf8c82e53813c740f7b6788e9f66cdb56dcf031ebebdaf0564b486a23a8e42b4a490db0f147ed1ec9a4fa6581de415b444dd7282c16b9881099cebcb44b9f0ed252aa19b7e1d3149452af3991613e40409e630e1d7721a3b2666ac0e6d88c15312f8dbcb4285849f3b1c87f2e8e765cb62a96c6d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
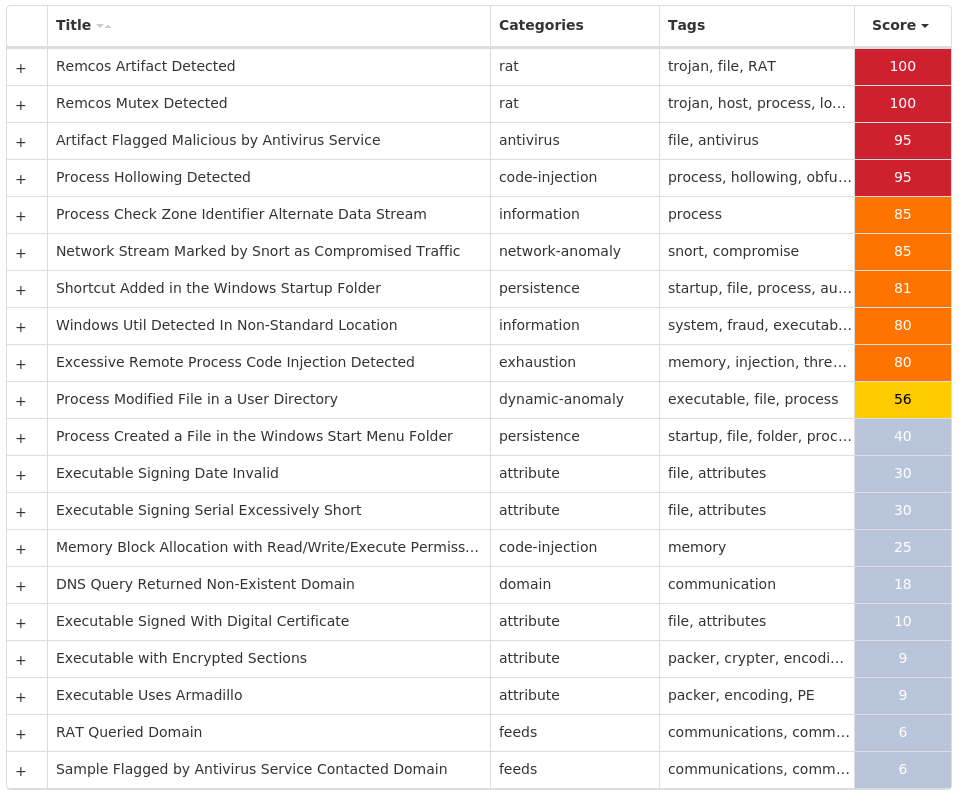
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Remcos-9985482-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCU>\SOFTWARE\ESDTRS_LBFGFPHXCSHDF-O7F47L12 <HKCU>\SOFTWARE\ESDTRS_LBFGFPHXCSHDF-O7F47L Value Name: EXEpath 12 <HKCU>\SOFTWARE\ERDATYFVUASG_AGSJHDJDJH-9CD4H15 <HKCU>\SOFTWARE\ERDATYFVUASG_AGSJHDJDJH-9CD4H1 Value Name: EXEpath 5
Mutexes Occurrences Remcos_Mutex_Inj17 ESDTRS_LBFGFPHXCSHDF-O7F47L12 ERDATYFVUASG_AGSJHDJDJH-9CD4H15
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 2[.]habladourf[.]top12 1[.]habladourf[.]site5
Files and or directories created Occurrences %APPDATA%\remcos17 %APPDATA%\remcos\logs.dat17 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Msconfig.lnk17 %SystemRoot%\SysWOW64\sistema12 %SystemRoot%\SysWOW64\sistem5 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\sysmon.lnk1
File Hashes 1b480c54d5f4b68c37c1b95bbf0f38c47ac43eb6e6efea46ee3b8a7e9aea60622b98c823d51c99b1eb8305988462ca4b0a597c2f56114bc0aed99ce8d871a4d22db151154ebc21a5c46fb34ce54cf8a241807e30999376f416e2cd4063bb09a22fdcd42bbd8f619ef738ddc159f991eafa1a65f91a7bf8652be68a29e8db27df3279dce56733c11b458b9c80ecbce3393f342a0dd8509bcb7b5a5cf60744dbe039688fa546b5a1804f6b7502b727d0f2a9471d75978a27a3c506ab452131531d5148eaf77e047e4f36dcffc0014784c513070117bd9112bdd85ff54ada38fb6c578e14ca76fc1433e4851f2faf0e7fc68a0b61addf6b924e68b4fc44c043566961567f6c5ee73824705c512977efeee6aef2ba5104325535dc38b3f805955203707d7dbf2fa8bc08563cdba2fb32de32ada565aede73d6c47cc179e50ba85ce98c39e5e6945c8dbf57cbed0336c56ac27222c0a853696f2e7748dadcebcb84bf8ccd90ec52fa901879c0fbb2aa0ade3840ba7fd11c2dc4cc403e45ca593d15e7a29be6e95bf4b5ea871fcf5178f460d06707a1bc9cabe83f927f00d56311f903ab2d3fc9c682087a625efcaeafaf7bb66adab4836a299c31c33d2627b67397f6bbd6a71d973e4abd4a6b15554a7a626fbda87a3c63a1c51d262961feaca01538beec34ac224e49087df629ddd08148bcc794c1657272946e7e40c97ef16b480de11c67b5ee7e8098dc837585a1a9c577786a75ac45855fe2a0648a4247f779edf8d991f61c31cb633f42b8c785eddb69291a3e3b75145f808d95bfea7acd9835
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
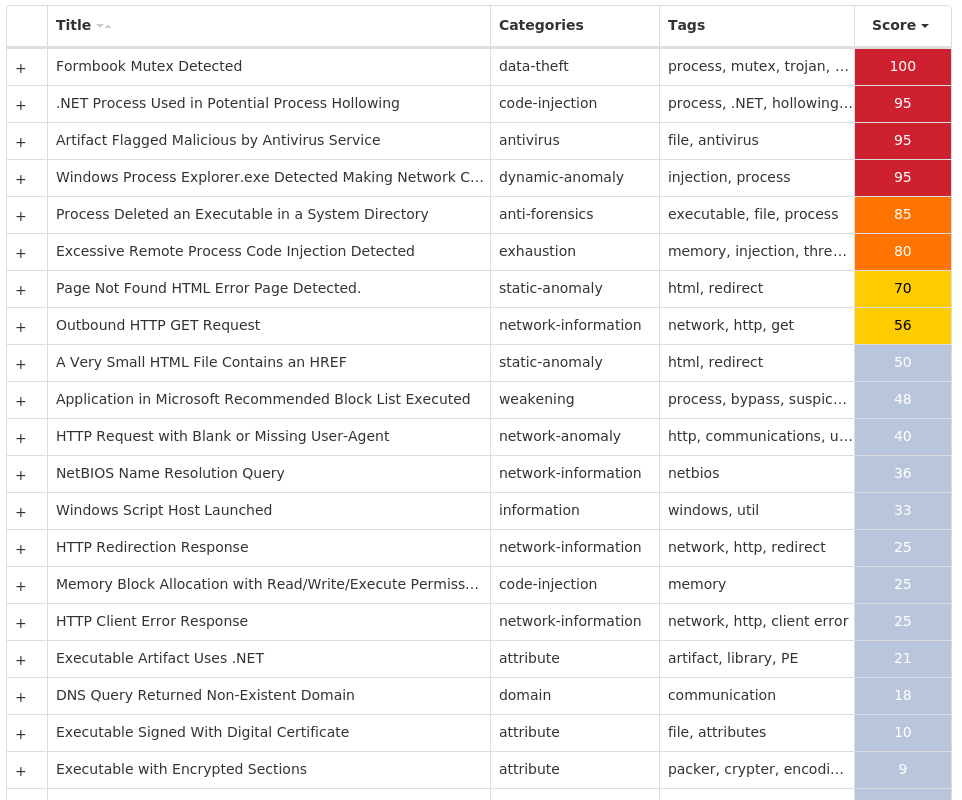
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: GsHLJkZ 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Skype 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rGxyJ 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: oonqj 1
Mutexes Occurrences 8-3503835SZBFHHZ1 S-1-5-21-2580483-124410344667061 43O8B1TCW2XBV8C51 VIFeIgKeLEykmegvqigXXPT1 ETkIKz1 Global\{562d3f5d-e645-4645-b571-86d856259c8f}1 KyHkIKu1 GEFveqIEBx1 sgcrlfpqsNOLJAUCfXfchdZSdUz1 ILDLahTnbnDORZnIDALLkJwrfeI1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 173[.]231[.]16[.]763 104[.]237[.]62[.]2113 149[.]154[.]167[.]2202 185[.]104[.]144[.]1662 37[.]235[.]1[.]1771 37[.]235[.]1[.]1741 198[.]54[.]117[.]2111 192[.]0[.]78[.]251 34[.]102[.]136[.]1801 162[.]159[.]135[.]2321 142[.]250[.]65[.]1791 91[.]193[.]75[.]1311 64[.]185[.]227[.]1551 31[.]170[.]160[.]821 217[.]76[.]142[.]2091 35[.]244[.]140[.]1141
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org7 api[.]telegram[.]org2 mail[.]xylometonline[.]gr2 discord[.]com1 www[.]davisgeneral[.]store1 www[.]kp34[.]vip1 www[.]shiroyagi-app[.]net1 www[.]homemaintenence[.]com1 www[.]iforusers[.]com1 www[.]favouritetee99[.]xyz1 www[.]miami[.]rsvp1 www[.]ferdat[.]com1 www[.]bucketsnbouquets[.]com1 www[.]bearpawbeardco[.]com1 wiz121[.]ddns[.]net1
Files and or directories created Occurrences %System32%\Tasks\Updates8 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp8 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat1 %APPDATA%\Skype1 %APPDATA%\GsHLJkZ1 %APPDATA%\GsHLJkZ\GsHLJkZ.exe1 %APPDATA%\ZlaRBfXtuZE.exe1 %System32%\Tasks\Updates\ZlaRBfXtuZE1 %APPDATA%\jz5tktcy.0cg1 %APPDATA%\Skype\Skype.exe1 %APPDATA%\us0zqags.ls21 %APPDATA%\us0zqags.ls2\Firefox1 %APPDATA%\us0zqags.ls2\Firefox\Profiles1 %APPDATA%\us0zqags.ls2\Firefox\Profiles\1lcuq8ab.default1 %APPDATA%\rGxyJ1 %APPDATA%\us0zqags.ls2\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1 %APPDATA%\rGxyJ\rGxyJ.exe1 %APPDATA%\HRdTfCzD.exe1 %APPDATA%\zz1tasa3.e3f1 %APPDATA%\zz1tasa3.e3f\Firefox1 %APPDATA%\jz5tktcy.0cg\Firefox1 %APPDATA%\zz1tasa3.e3f\Firefox\Profiles1
*See JSON for more IOCs
File Hashes 0ca35b63c11c3cb981f833414ebed109ec0efaabb75780924a7265fc05e5044218a3c3a3ee44e382d899d905099a69c8e0e378363153eb1720d1faeef5a71c801d815d0d8666918b92ba9ad7d998b096401ca509258d8526ac80289cb0c009a020097b824756d0ca9b24602aaadd51f0fcee82b663111fbbe506fe4243828a4432e2c5ac34b25d497c5383eeb0d444b9e011ec0e47764efc907e6955169f099b32f6848e3572b0e0bddab845c860fae280700446d1d04e5cb253270edd32022a4b9899d778c58bbf3a6822530b2fcc1ecba297049d74e84ef5dce30eac3c8ec265e9e0364afa672099d5920c57511d854b3f815d70135cbb08e562d1104c7ce576b53b0d5379f62e06c382cbecf8d8e5900c05575f545881da8db594df2030e67ecf2444570ef5d4de690d271bd88eb4f6819aad1acc3c3e382cd4e0471d75daa691f677c3659c9372fd4e4beb1004d19e368946e5cae0ad5e0e0d6a4f943e71b0aadad0628bae4420e2c53b888017907cb318ef906560df71cbf17634f31dd1bb4fabecc410e116a6885d9935781646c6c5a363c885d4a97efa4261bfdd128bc94fc73c5fcad1ab614fba37d9cc9c21f328c4787e39f3e3d673e1c408691434ddecfe4cc7384ea111ee90988969e06c3db18f782c4cd446ef720c4be5be0fcae9d7842178046601f88934e1e6f315c225323465be6fe64e00b1768567c5aebf
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
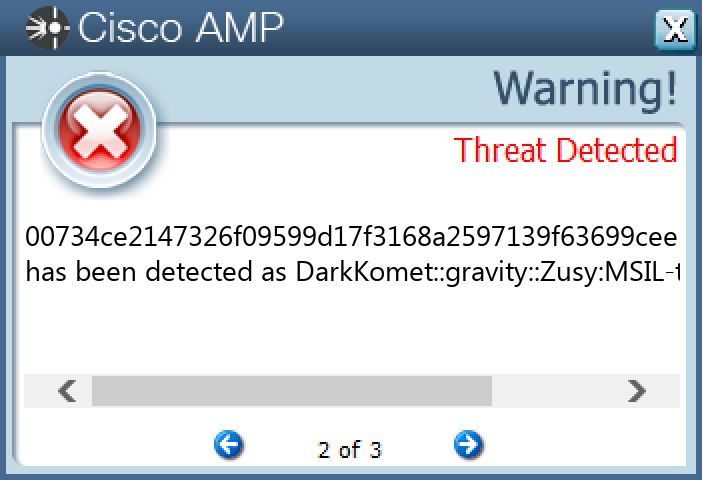
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkComet-9985655-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC23 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 17 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 8 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 6 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 6 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 6 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN Value Name: NoControlPanel 6 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION6 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN6 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableRegistryTools 4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableTaskMgr 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: WinUpgrade 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rundll32 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: System32dll 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HLCK module 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Hklc Module Key 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: explorer.exe 1
Mutexes Occurrences DC_MUTEX-<random, matching [A-Z0-9]{7}>23 DCPERSFWBP13 olipqhhvv1 snohitatusbkwujy1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 205[.]237[.]57[.]954 94[.]73[.]34[.]1951 78[.]159[.]131[.]801 78[.]159[.]143[.]1721 199[.]59[.]243[.]2221 173[.]208[.]96[.]441 24[.]122[.]252[.]191 142[.]251[.]163[.]1081
Domain Names contacted by malware. Does not indicate maliciousness Occurrences djbusta[.]no-ip[.]org3 exphiltrate[.]no-ip[.]info2 wannafucky[.]eu2 smtp[.]gmail[.]com1 www[.]limitlessproducts[.]org1 survey-smiles[.]com1 daynasmith[.]no-ip[.]biz1 markcms[.]no-ip[.]org1 wazdawg[.]no-ip[.]biz1 rats123[.]no-ip[.]org1 obsidian[.]no-ip[.]biz1 dcratfinal1414[.]no-ip[.]biz1 rayquazayeh[.]no-ip[.]biz1 iknightz[.]zapto[.]org1 whiteout[.]no-ip[.]biz1 i18[.]no-ip[.]biz1 sheepslaves[.]no-ip[.]biz1 hogwild45[.]no-ip[.]biz1 420ratted[.]no-ip[.]biz1 estherr[.]no-ip[.]biz1
Files and or directories created Occurrences \IOP.exe25 %APPDATA%\dclogs22 %TEMP%\MSDCSC6 %TEMP%\MSDCSC\msdcsc.exe6 %System32%\drivers\etc\hosts3 %HOMEPATH%\Documents\MSDCSC3 %HOMEPATH%\Documents\MSDCSC\msdcsc.exe3 %ProgramData%\Microsoft\Windows\Start Menu\Programs\system3 %ProgramData%\Microsoft\Windows\Start Menu\Programs\system\WinUpgrade.exe3 %APPDATA%\Microsoft\Backups2 %TEMP%\log.txt2 %SystemRoot%\SysWOW64\MSDCSC1 %ProgramData%\Microsoft\Windows\Start Menu\MSDCSC1 %ProgramData%\Microsoft\Windows\Start Menu\MSDCSC\msdcsc.exe1 %HOMEPATH%\Favorites\MSDCSC1 %HOMEPATH%\Favorites\MSDCSC\msdcsc.exe1 %SystemRoot%\SysWOW64\explorer\explorer.exe1 %SystemRoot%\SysWOW64\MSDCSC\CMD.exe1 %SystemRoot%\SysWOW64\sys641 %SystemRoot%\SysWOW64\sys64\cmd.exe1 %SystemRoot%\SysWOW64\explorer1 %TEMP%\008.JPG1
File Hashes 00734ce2147326f09599d17f3168a2597139f63699cee5345c177b4c533f20cc0305b3ab37f709d7ed33af5d71a45efdd7757961b310756552a9c83578ff5b4d066be692f1bcb869dc47014379d24d073b013e2596f934ba0e44c060f3ff3c890d4fc5dbfdabdc02710e2eeeeb1db3d0210c77423bff5976e2350bafd4684b331ee322af4acb4442ffab0572847ad788a59e048b28ba8b1388b273249221ab9623df138ff6fec0976438bc863fa8829b9b0f4b1165022d1b7b0a6f590dfec12c2478d5f4fd1e2f26e6bfb1cc418f75d429401d8077ad79404d66a92acf847a1e2cf568447e7fbba9deaa52ca020417e13f11948a2a371b429c72ae27a54e9abb3104d7ca6708a7a6e246fb9cc4f9037c76bf8b3eeb2af403b321798dec17fa0c333eec0b2d19cb7b97eeffc7b12eae83b705292e7d8e2fd816f495e69c6ddcdb3d05f037faebfa88b3b220081dfe503b96bc5df7e7a652136a67045062829eb94b0122f4b81461761c354a6d5f4d82f9aa252949f18c4af0c0e84e63b5d4cf25591d974202517d8245ffc8e110a52c1f3586ecd9fd72e5db53539acdf16deb5165f9cd4aae0b041b98340213f5b82e3ab7ad555cc7085f63937ded6ddce0fbb4692e0c82782756d009cff6c6307c77af3438dc47f82d9a5b513b69ec11d2a8696b8ad68cf898b33980de5aedcec95c877839f6280d0ed142fede780504d1fe1d7c03348bdb4c7495f3043399bba3b6e5fea2740e2fee464c2b449649cf6144798c69c1db04089d75a8196268c60c3ed879a910feadb8cc9c0c92f247701d30fb9606c4c48d0f0d8d631d2e98dff3db11f12b4195114281d5baa01b879def95bc9d43ba693dfdcb195c396090aa301bcc690336ae65e9d28450f9b92db23dc172aeb842100ce2ae8e8ad4aad1451a41b86c4cafdedccc6495aea762c3610d4ac8b450c4ea6ea91b39d22d68b499e1f1d57229ac5f2091c6095f6cf42cb1e115c2cb5c7c8cfe7d9aeb56c0f353c6a38eb1bb90dd79949d6d25f45ee9289cbbdefad37d7c369c8b9023f42df51d5c6ea7ecd56b7fa8620f8861452521cb0378bc16da5474791d8d183f850d609e11d90c54bdda68aba0522e284e600471c324cd31
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
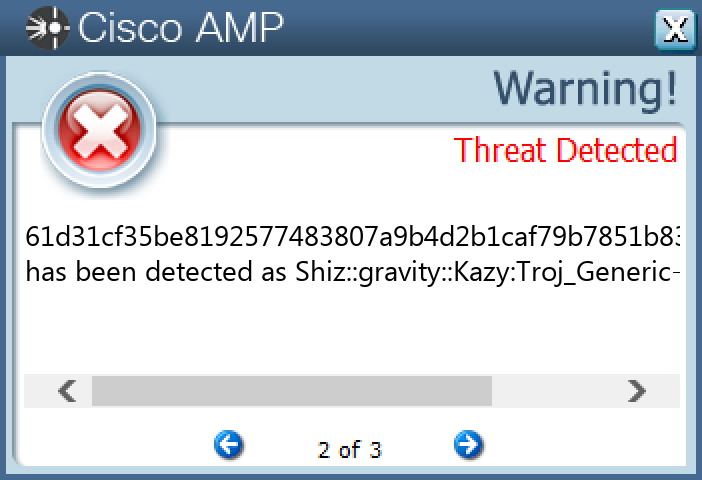
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Shiz-9985661-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 17 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 17 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 17 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 17 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 17 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 17 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 17
Mutexes Occurrences Global\674972E3a17 Global\MicrosoftSysenterGate717 internal_wutex_0x000004b417 internal_wutex_0x0000043c17 internal_wutex_0x<random, matching [0-9a-f]{8}>17 internal_wutex_0x000004dc2
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]94[.]194[.]16917 13[.]107[.]21[.]20011 45[.]33[.]30[.]1977 45[.]79[.]19[.]1965 198[.]58[.]118[.]1674 45[.]33[.]23[.]1834 173[.]255[.]194[.]1343 96[.]126[.]123[.]2442 45[.]33[.]2[.]792 45[.]33[.]18[.]442 45[.]33[.]20[.]2352 72[.]14[.]178[.]1742 72[.]14[.]185[.]431
Domain Names contacted by malware. Does not indicate maliciousness Occurrences xutulenuqix[.]eu17 purijygirem[.]eu17 dimasyhageh[.]eu17 ciqofymosip[.]eu17 vonerymekix[.]eu17 novubymyvip[.]eu17 fobyqyhezem[.]eu17 gacucuhumeg[.]eu17 maxilumiriz[.]eu17 jelojujopen[.]eu17 qekafuqafit[.]eu17 ryhyruqeliz[.]eu17 kejepujajeg[.]eu17 tufibiqunit[.]eu17 lygumujycen[.]eu17 xudoxijiwef[.]eu17 pupoliqotul[.]eu17 citahikodab[.]eu17 direfiwahur[.]eu17 vowypikelaf[.]eu17 foqurowyxul[.]eu17 nomimokubab[.]eu17 ganovowuqur[.]eu17 jecekorosuk[.]eu17 qexeholagav[.]eu17
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp17
File Hashes 012d19e704484b2a39d31eba8750a9b9353c07bdf08ec7d4d6311affaf7346ae07ffe0a9e57b4927cd20e8fabc42bcaea97c53bc0610877a3f1d494cd1dbccac34e4dece416c68fa10acb6943d246fca0b942f46fe3664aaff2c344a630d3e5a41fa3bac3b7e6712374e169e011756964d438f6e4162c2ae415fe904f39f358f5518dff75f344e50f2fbeb774c59a16af35c639c8726b1612fe58d75dbb385ef61d31cf35be8192577483807a9b4d2b1caf79b7851b83e69dfb2f12581eb96ed9819e088abf6eb464827532f5d1b8741e4a6197dcc75e0f1a9b54c1befa6a7b7989063d88c9bcbb080c62d3b19f9e26815072acd72a95bda3b2023f42339119aa2402cbb04576c9732889e17ba36e459137473975bd9b68ced4232d54af7355ea658dd42692e13ee1fcd77624943431970b8c4b9a51c375325bc0095f5578c5bb54cb741d49045e5d78dc09db3d449c0389037501d97431fa3743f833c0d0d3eb910095a1bf7f0bbe924f08fbba04a05cda37e2175334ac3cd5a07667c8c24d4be283aa132e7f648bf15e50da41499af44b12148d23d3b7c509d1e596ea679aac1cf08c50b93e9ad1393a9fe32773fb35c1868c12b5177dab9fb3fc103e53a5acdcc5d38793e1874a006082bb43bc4d3d242827d94e1407e39afe62bb910437aef84cc57f5b5ab0732dfc6106482bb4f6cefce89bc39dbef194759172f35b816fd9f1f1a0c7f1b22040488ce19bcb9b44624a5b08930808887be99e9074320e3
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
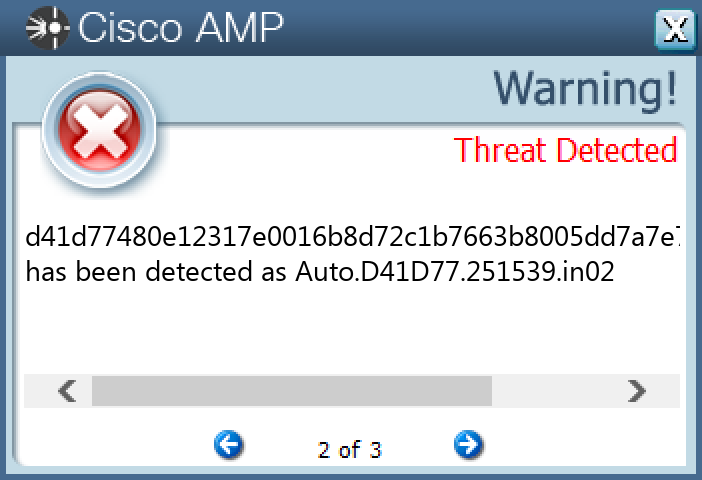
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Expiro-9985780-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Registry Keys Occurrences <HKLM>\SOFTWARE\CLASSES\APPID\{11AC3232-E7D7-49CD-ABFE-501700100B3A}23 <HKLM>\SOFTWARE\CLASSES\APPID\INTELCPHECISVC.EXE23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION.123 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION.1\CLSID23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION\CLSID23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION\CURVER23 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}23 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.023 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\FLAGS23 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\023 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\0\WIN3223 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\HELPDIR23 <HKLM>\SOFTWARE\CLASSES\APPID\{11AC3232-E7D7-49CD-ABFE-501700100B3A}23 <HKLM>\SOFTWARE\CLASSES\APPID\INTELCPHECISVC.EXE Value Name: AppID 23 <HKLM>\SOFTWARE\CLASSES\APPID\{11AC3232-E7D7-49CD-ABFE-501700100B3A} Value Name: LocalService 23 <HKLM>\SOFTWARE\CLASSES\APPID\{11AC3232-E7D7-49CD-ABFE-501700100B3A} Value Name: LaunchPermission 23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION.123 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION.1\CLSID23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION\CLSID23 <HKLM>\SOFTWARE\CLASSES\INTELCPHECISVC.CPHSSESSION\CURVER23 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.023 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\FLAGS23 <HKLM>\SOFTWARE\CLASSES\TYPELIB\{66DBA565-0D3D-4D8A-9391-A2A4CF16DF40}\1.0\HELPDIR23
Mutexes Occurrences Global\Multiarch.m0yv-98b68e3c311dcc78-inf22 Global\Multiarch.m0yv-98b68e3c311dcc78493cd690-b22
Files and or directories created Occurrences %System32%\alg.exe22 %APPDATA%\98b68e3c311dcc78.bin22
File Hashes 017914e50cb777cefee8c37387ee0ef0f2ed8d5e37f70631397cf970439f5d31043ad6bb1b9cdf89e6f755c305c4d1a63d434e224b970cd9ba2755b861acb5550998b37290085d19a2005b479e0d9984603670d15878655be31132c07f08e6641f6531dfaa028bf787fe17e7d06db3215f62a640bd9c4c1569d4671c02c76c892162f343de91915b86315191027723897abf71c71ebb8b83e658590ac833d7452a93031db9f3e0ae221bc0ddb74108ecbdb821998be33395e43ad6e7d3eb41a431a7cbe8089e1c700c6f4849f94c4e68dda6f52985993e158f88b34ef49bc46153ea5ad87000b3b20426ecfc34177889ac6a657dbf634bce6a32d0d17e28f06f597ea95de28f6cff7f98e394c1fb24d73ae25f9c4e05991d5bd5dc790f58d869676adafbcf97181d8d01152359ec35c6987b4bb9afa85dfceb3adbc5e6518bb97739b40252daa9775b0753af04fcc13c92fd67f542310cfdb3a91371cc6843718ddd46313fd45e956ffbdf06555b5cea30aae664cfae98fa564255c3e0da7147a149d4a4d73bf1e196473021b16b7ab91d406904bf0a3c6357990c9933a7ff03a207f03bb5c205d5711eaf6d0d39c327fbf0b07c4fc6de120528e935846cd7b6a54b5e9988c6527fa2e54da6e10807e9cddac1c0e468f4b60889f548c310e54baaedf85fe5ec1c4246b46de9d2597ed7ec88a7fdf3e85232e7f6c005bec4947ead4ae247194c47ecbae21d57dae9dba4f4292a57e833a0c6beefb211ea269501b2a794f77f82d865d0f5cb359f6664983dfeec7a5c86e3b098508af08440c75ac43dc105a3ecaca5a64f501bd997801db0c6f4f43a1def44840bea69fb0b1eb9d41d77480e12317e0016b8d72c1b7663b8005dd7a7e7aa7c4ec975bb4bee78bedc39b6d6feda5258836e59f7c68a8fd41315fe1975439358b3680812a066aab8e1f1f378121e8d6253bc727625f763931ed6ac1e559906d436309346ce815d2fe95a33ebb95c2bfdd1712f885437d5e4d739ffaa943c04c6d6f051a62c7619c1
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
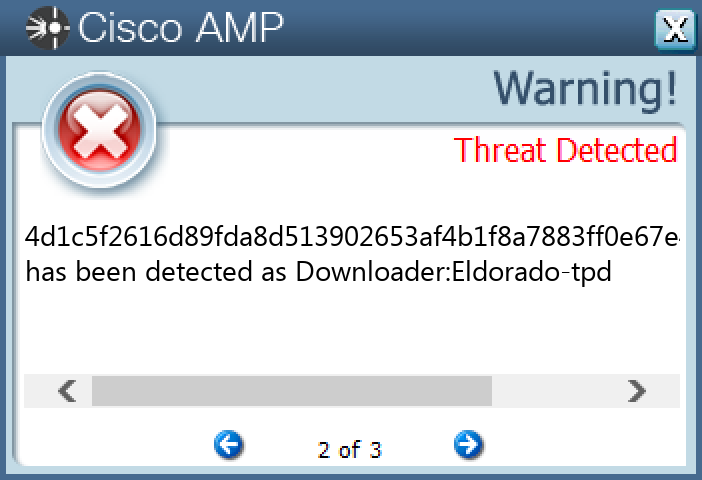
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TrickBot-9985782-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 26 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 26 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 26 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: svchost 26 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}26
Mutexes Occurrences dek390f0f928d9226 435665657766426
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 209[.]44[.]117[.]6226 13[.]107[.]21[.]20013
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com26
Files and or directories created Occurrences %SystemRoot%\svchost.exe26 %TEMP%\temp.bat26 %LOCALAPPDATA%\n.ini26 %SystemRoot%\SysWOW64\n.ini26 %SystemRoot%\SysWOW64\n2.ini26
File Hashes 01ed0fb6882729acc463fa74bf7dbb4b2d52ecaf4a7b3a236795f8c719b9bae90788af25244ad4ded923f262b5cbf9b2b7656474955a3ce9a8e1c8ce169dd438086a5e698a5fecd9718c60588fe7f0a7c2ad85b4261365f1e4f12dea219dd66c0ad8fbbb2cd9ae256f7ffd3e0d810c613ad4fccf25709710ae505ff7020922980d2d2c74d781dcf0a0fc85fbf0bb910ba9ae1e23c542bc82499f12c706f0389a117884e656b262ca26a5ea4fefb8887286485ffa34d8169489698cd3d70390561358dc0e747e2078b7539ebefe1b26999126792558eb9a258d48e48f5c98a98b14dc10b01dfa144cba31539629add223e684dd146619b99cb0bc26b80474ec32174cfb475dd37c80eed33ed96172bf120a16c993ddca02079c76b235153115d71b937d589376184eef0ec6e9ceef0f8bf8d70d6cd3c490693091993dd92c96452181e72e0405d21a62379cb0c4e613e5637b8be516dff966482c414a14e24d3423d902f81f5ce0b068d5cfa2ce39c0f0bb36477a30b536b9140afe0f30033b8324355d268e634c5c183be4c32bda47706a33e062f2a6623769a3f42dd31c8ecc290194df30f49fa36735d1797d482ed1154edd036641b741eeedae69d4856ebc2a9b89880feba1f5cde7b572182bf1bfbca980ff89ca225d1fdef2cb5ffb569e2bb6e9eb5e1df6e887fd6b0600f9d8b4e42b7ad046798c9eb3461af6d14e2491345d93112129b4505272c4d63013f7855cd0cc94a39052ef4ad4a00182fde2c9372c42a76358f43ad5ffa7062562421a211f37d365892c4eb009743deb84abf73a621078f9e229e7127c95bd5d3ab10bea2c81d852337bccd4edea64097b99753e657cbcb60878485642fa589de30a396d7c09fb0c0a87d86a779f09c9fdbbb347520b3363ae51ca763dc6cb152908e4a5f338088037923f4a500be9096a1bf14803db6f1a75d0149269ae0ecc49c89d92b9c2fbae542ccd039790ee08a403b04d1c5f2616d89fda8d513902653af4b1f8a7883ff0e67e4c347fef619ac4ddd34f059ddd4cfce979e16286c7b0f7e91050c671852c5a2e9bc558405108d3508e51486749cd363361c102da2c8452c16034bbb8cf743ad4e063ea95f9d519b11d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK