Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 28 and Feb. 4. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
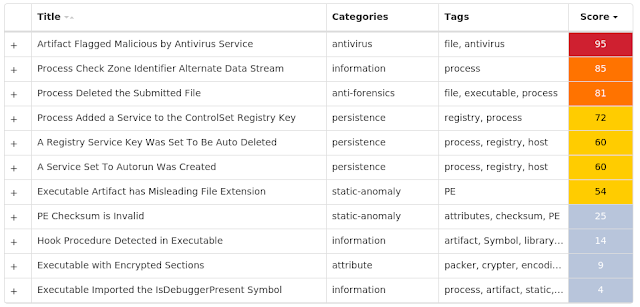
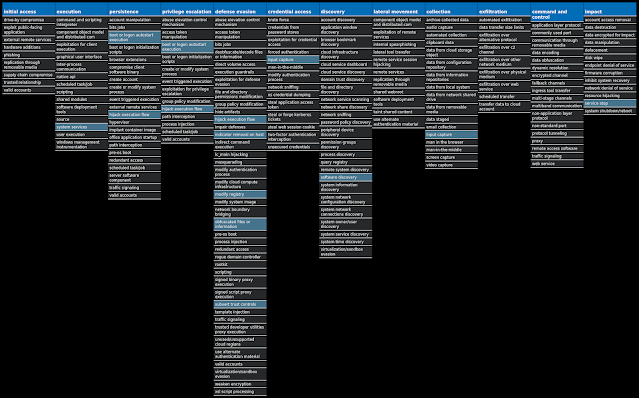
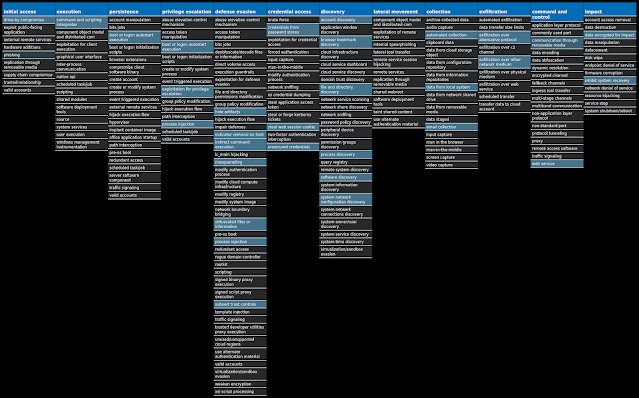
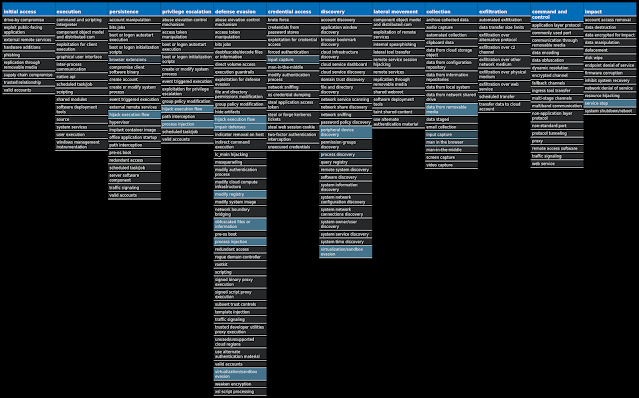
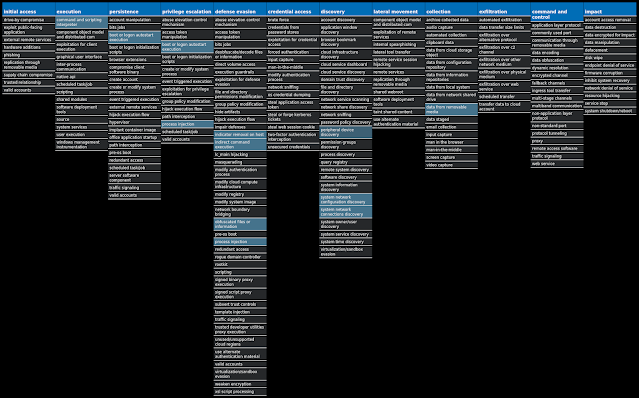
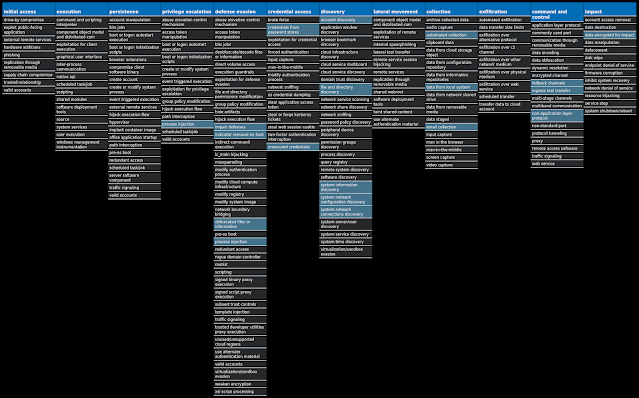
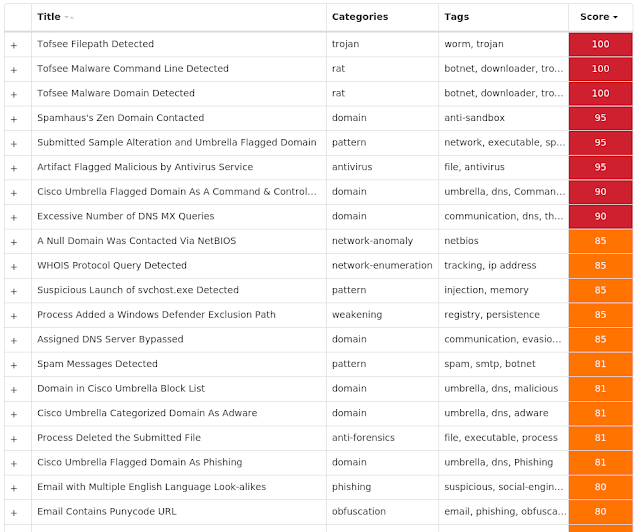
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Malware.Emotet-9937716-0
Malware
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Malware.Upatre-9937972-0
Malware
Upatre is a malicious downloader often used by exploit kits and phishing campaigns that downloads and executes malicious executables, such as banking malware.
Win.Ransomware.TeslaCrypt-9937798-1
Ransomware
TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily.
Win.Malware.Zusy-9938038-0
Malware
Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Win.Trojan.Xpiro-9937847-1
Trojan
Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Packed.Gh0stRAT-9937867-1
Packed
Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks.
Win.Ransomware.Cerber-9937930-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used.
Win.Packed.Tofsee-9937919-0
Packed
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control.
Win.Malware.TinyBanker-9937976-1
Malware
TinyBanker, also known as Zusy or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Threat Breakdown Win.Malware.Emotet-9937716-0 Indicators of Compromise IOCs collected from dynamic analysis of 33 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: Type 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: ErrorControl 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: ImagePath 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: DisplayName 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: WOW64 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: ObjectName 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: Description 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: DeleteFlag 33
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CMZYNTUVPXDV.PSU Value Name: Start 33
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
51[.]15[.]4[.]2233
173[.]214[.]173[.]22019
212[.]237[.]5[.]2093
216[.]158[.]226[.]2063
192[.]254[.]71[.]2103
162[.]243[.]175[.]633
58[.]227[.]42[.]2361
104[.]251[.]214[.]461
46[.]55[.]222[.]111
45[.]118[.]115[.]991
212[.]24[.]98[.]991
185[.]157[.]82[.]2091
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org25
isatap[.]example[.]org15
computer[.]example[.]org13
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com8
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com8
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com6
Files and or directories created
Occurrences
%SystemRoot%\SysWOW64\Qohugesysvrubfz33
%TEMP%\<random, matching [A-F0-9]{1,4}>.tmp33
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-17529550060\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-18270793970\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-21706820\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-4759708130\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-6757900\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin-8760897390\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin20259167780\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin20332743330\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Internet Explorer\Tiles\pin8215062560\msapplication.xml25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\PCALSGUV\ErrorPageTemplate[1]25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\FNF9BE4O\green_shield[1]25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\red_shield[1]25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\securityatrisk[1]25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\PCALSGUV\background_gradient_red[1]25
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\XN0IX3V7\shield[1]25
\Users\user\AppData\Local\Temp\~DF87E470CF564C4D93.TMP1
\Users\user\AppData\Local\Temp\~DF9490C5E3449E6B41.TMP1
\Users\user\AppData\Local\Temp\~DFA243755BE293EE1F.TMP1
\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{F8B6FA93-7FED-11EC-93F9-00007D868566}.dat1
\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{F8B6FA95-7FED-11EC-93F9-00007D868566}.dat1
\Users\user\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{F8B6FA96-7FED-11EC-93F9-00007D868566}.dat1
\Users\user\AppData\Local\Temp\~DF024DC091F3074AEC.TMP1
\Users\user\AppData\Local\Temp\~DFA5B1F2DB14703836.TMP1
*See JSON for more IOCs
File Hashes 007be7df137f6d199897d1dd75b858098461e6007fda33986106bb0dcd1e05f2
078fb234269958f8447de92c6dd949da090e44534bff43b36c367b8f7cadca93
08f826b0627cfe939a9180f960679d87d0e99ae7b8f9663712f2a5871313de62
0f45a4e10aa196a49c19f86f9190256b4040c1a2144bcfa97aa591e0d1dcb044
11cfa8190b9cd6d73a38d8b7a3487634af770d2cfefb5339333c59819618126d
165968518b6b688ddfd97db43269777fe2bc24e31810565d559bea627a790928
223d1634e6bfbd3c66022da2825eac42304f7e36b50d2a7b1a02eb248bc9d0d5
2636a748beadf515aebc0fc5f806c9d9d27ef433e1df7e8234c64c2786c27f28
2bd5996834021be415ed694f96bf5d899c8f1e2c2c7481aac6d2e2992df00954
336c881991576f4f0c0ff52798706554ba08e83618fab06ddd11edad77b12049
33d38853dee79a7c8b9c2399466b2eb1cde0443411e001c88ee428ae4b1523e0
38076ccf3df17401f2950aac1743ca3d02327fb8430afb4df4e0e586bec571ec
3b0aeff04b69c4bbccf2f32a9ae87955d604a16b4cadee91a7498c4a9404a57a
3fc46df716c86ed5b65cff074f786c732fa26794569605fa399077c154019f13
416e48c32dce4a4f2bade27b2da7fff519722bdc4e3511a3a281557c0e404572
4b58ac3ebf6781d5eedc3093a797a1f43e2eb5b9daa593b18b38b45c480aff4b
4b78855ae00f63be7ce846b722188ce314608627489f66bcaa868104a07f1061
4b8df0b4c0ae0ac0c4061c6c482aa82139366b411251d33661763e7a47b4cf41
4cdca7bdfc8c48ea766bb4fd69c5a205c93248e2b4136251acdbe6413cd4d09d
50d24a7a89c88c085caa2988f0c41ff6bb20d7fedceaf284edf4ca687acb8fed
52ddcef399eb12519b183ecd2feb630323b3a198f00e34658adcf994e2bf63de
55a361c7bd87d86c5da37792830d4df5837918f51bfdb4d5ef73985d66b0f1e6
5b7925c5aaebedbc9d7254be9535052c86509da1f8b5884ab6f59aec6f797e5e
605936ccf11fed962f64e5113c38f3322a094ea9a3039392d58313fd1f789719
65a02afb63023567adf7503b235df4c0bdacd4e0b3709730089cbfbb44b579cb*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
✓
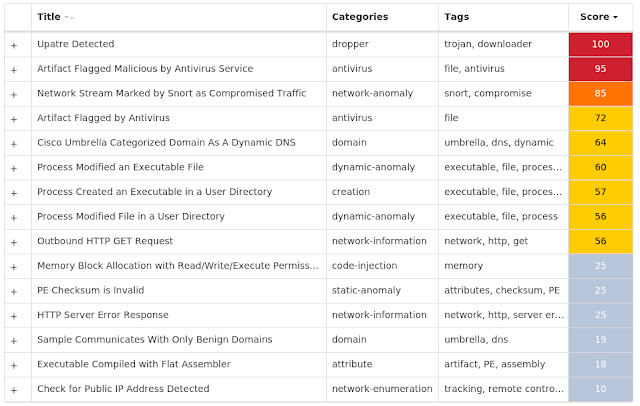
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Upatre-9937972-0 Indicators of Compromise IOCs collected from dynamic analysis of 49 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 45
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\STARTPAGE Value Name: StartMenu_Balloon_Time 4
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
93[.]185[.]4[.]9040
193[.]122[.]6[.]16811
132[.]226[.]247[.]7310
24[.]220[.]92[.]1938
176[.]36[.]251[.]2088
193[.]122[.]130[.]08
132[.]226[.]8[.]1698
67[.]221[.]195[.]67
158[.]101[.]44[.]2427
98[.]214[.]11[.]2536
65[.]33[.]236[.]1736
67[.]206[.]96[.]685
84[.]246[.]161[.]475
69[.]144[.]171[.]445
68[.]70[.]242[.]2035
64[.]111[.]36[.]525
188[.]255[.]236[.]1844
67[.]207[.]229[.]2154
98[.]181[.]17[.]394
76[.]84[.]81[.]1204
217[.]168[.]210[.]1224
188[.]255[.]239[.]344
216[.]146[.]43[.]70/314
188[.]255[.]243[.]1053
67[.]222[.]197[.]543
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
checkip[.]dyndns[.]org45
checkip[.]dyndns[.]com25
wpad[.]example[.]org17
www[.]msftncsi[.]com2
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com1
isatap[.]example[.]org1
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com1
Files and or directories created
Occurrences
%TEMP%\nioltei.exe28
%TEMP%\osenbraw.exe15
\Users\user\AppData\Local\Temp\nioltei.exe11
\Users\user\AppData\Local\Temp\osenbraw.exe7
%TEMP%\dylkemi.exe6
\Users\user\AppData\Local\Temp\dylkemi.exe2
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\SAOQH72M.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\U7J6ICLV.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\OXHPLY65.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\EGB0GBBZ.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\6M88EHFP.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\T05ZFWET.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\N5IDYM66.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\FGZNCIYI.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\YK23OU01.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\R7K3JRCG.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\HR60Y0LR.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\S0DQ656U.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\97MS5XL7.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\KYY2PRC6.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\YTRW8D4D.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\Q0FL8OLA.htm1
\Users\user\AppData\Local\Microsoft\Windows\INetCache\IE\OSZC6DKG\HK399NEB.htm1
File Hashes 0049448203a7bf7f14e0e757b7a9a32e74706b20aba329414bf96ecbe374269a
009cf1ab1fe7a05a0c41f00103513665d5baa9fe715ec23062241547a13e1f8e
018f81f7c36ee58233ec83da9d85a825c7e7d1d8ba0281d0ac8e16efe2f087bd
022581f752d26793bc2aad7a61a231c49263ba1462dbb8432c388450850688a0
0503001f3b84474cf2dee029143d3ffef04ddbbadae2a7e79d187ddd840ff7d7
056eb2aa2e4ac1445fb83e1a454bffce1646ccca1fea2ce245794e6e56edceca
070d473182dcce6e75218cd35d1320d1464f39b128072fc986b8cd1137ff8211
0973cb547faae91ec42c3c5ec59475d86ff12c63231dc86d6344569756b39308
0a9a9a0efce9f70db4cca9fc56ca25818589c18a340dc9480388c421dabe6bb9
0c551995bb34fa25fdc0bc316537f40b81411ddf88a3eb17e2bdcfcd46644ab5
0e69ee64f1a9a48fdd9ab2d29aeaa4b76fad75a8ed073d0526a6c89703968b4d
0e9eae10e6c70b16cf782d1ce4d84bddcb56cfcf1d9dcb4ac0537739936cacbb
14cd87638072837c84310c6c24d912c955861942adf624d88703cfa95ac0b4fe
1ba90f231767fd23ec2bc2f12d49c2fa7ff4260e9ae1955f5467df0c785cc53e
1ce7906e2db80dddb946dfb56bf1c211a3ed3d4b0e0c0127d05433d10739e8c1
1ce86312c51162c78056fc24e06209c6a327bbaddee4b454eed82f296a4be912
1ff41d9d2d9e778a942faf976beb4294d95b1aeb409884c57a15a4c5a8862d46
218adf9685e943fcd3aa6b9ce32fefec6a0c3fd3ed0f0bc09d83d507f4efeed3
228cea0f0c2d55ffd8f47514eb67c925993e7e6aad71171ec1833457919d70d1
22e5d41b1ca73a48fcae888b5105f41d3c90eb060b9572abb98c7adb4db24f0b
235430c5667841a2661bf6575aa7cad188e320657d2b719adb280a8fd9dabad5
2692db332ca4a6806b7ae65514b230cbf3af0c54202a740d337f5ab3c76f2320
28906c7124e13d452b2aaf59f1287741ec1e185bb2bd1e214f5d74120b4e74a6
28c4e57ccc9012cf842e8f8168040dde56c56af3f73be1e9f0f415a157ecf297
29e6026a639576b34af58052c1b2536e6e92aa2a43541d77a54d92de611cd9c6*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
✓
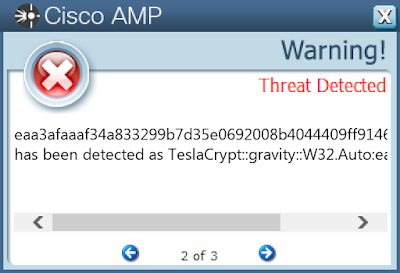
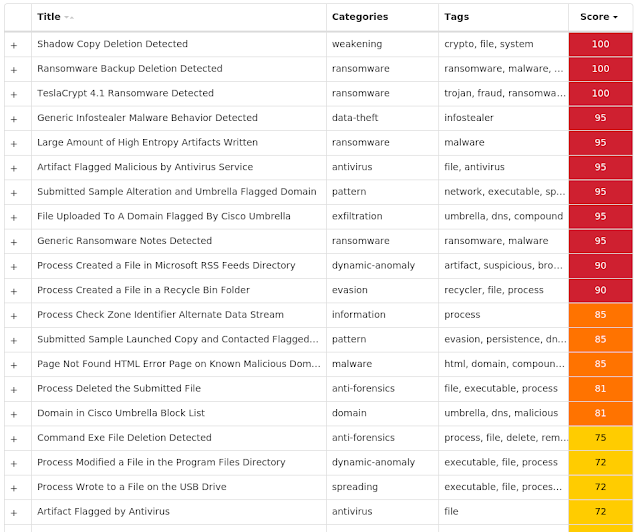
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-9937798-1 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 15
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgofeubm 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgtsajdx 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgcmqjec 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgtkbacb 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgjtevwu 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgcnrmvw 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgqrlmox 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgboinxx 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgvlyhvv 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgyjylva 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgivnsxg 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgnwsceu 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgerxmyn 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgekpant 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bssimgscvaut 1
Mutexes
Occurrences
__wretw_w4523_34515
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
81[.]2[.]194[.]12815
104[.]21[.]74[.]1148
172[.]67[.]157[.]2396
198[.]58[.]118[.]1675
72[.]14[.]185[.]435
45[.]79[.]19[.]1964
45[.]33[.]2[.]793
45[.]33[.]18[.]443
45[.]56[.]79[.]232
72[.]41[.]18[.]22
72[.]14[.]178[.]1742
74[.]220[.]207[.]1122
96[.]126[.]123[.]2441
45[.]33[.]23[.]1831
45[.]33[.]20[.]2351
45[.]33[.]30[.]1971
173[.]255[.]194[.]1341
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
thinktrimbebeautiful[.]com[.]au15
lorangeriedelareine[.]fr15
bluedreambd[.]com15
onguso[.]com15
loseweightwithmysite[.]com15
helcel[.]com15
wpad[.]example[.]org7
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com3
computer[.]example[.]org2
host112[.]hostmonster[.]com2
Files and or directories created
Occurrences
%ProgramFiles%\7-Zip\Lang\ka.txt15
%ProgramFiles%\7-Zip\Lang\kaa.txt15
%ProgramFiles%\7-Zip\Lang\kab.txt15
%ProgramFiles%\7-Zip\Lang\kk.txt15
%ProgramFiles%\7-Zip\Lang\ko.txt15
%ProgramFiles%\7-Zip\Lang\ku-ckb.txt15
%ProgramFiles%\7-Zip\Lang\ku.txt15
%ProgramFiles%\7-Zip\Lang\ky.txt15
%ProgramFiles%\7-Zip\Lang\lij.txt15
%ProgramFiles%\7-Zip\Lang\lt.txt15
%ProgramFiles%\7-Zip\Lang\lv.txt15
%ProgramFiles%\7-Zip\Lang\mk.txt15
%ProgramFiles%\7-Zip\Lang\mn.txt15
%ProgramFiles%\7-Zip\Lang\mng.txt15
%ProgramFiles%\7-Zip\Lang\mng2.txt15
%ProgramFiles%\7-Zip\Lang\mr.txt15
%ProgramFiles%\7-Zip\Lang\ms.txt15
%ProgramFiles%\7-Zip\Lang\nb.txt15
%ProgramFiles%\7-Zip\Lang\ne.txt15
%ProgramFiles%\7-Zip\Lang\nl.txt15
%ProgramFiles%\7-Zip\Lang\nn.txt15
%ProgramFiles%\7-Zip\Lang\pa-in.txt15
%ProgramFiles%\7-Zip\Lang\pl.txt15
%ProgramFiles%\7-Zip\Lang\ps.txt15
%ProgramFiles%\7-Zip\Lang\pt-br.txt15
*See JSON for more IOCs
File Hashes 1db9c6e37a0b18ebe5aadba9aaea71467e05aebeaa67b065592bb46a04d76368
27ebe5bf3aba1ad778dc43582f7468906007c5cbd40858294dfa9e1716c1b246
2c956a9ce5e5964c8bcc0caf6be44ceed54c80e6c98f8b54aa2711904bb8dfa6
40b17868f4b695330684cbf35e9286eb0ec1086d16d4a02a069b8886f970bc41
46d94eb497a9700630719e781319d55d9c693b04ac13ca7f38d46f8ba9ade1b7
498683c0be028065930ab7985b7cba9a1620a3724d4fa7424b7221a231f34bb1
7f0e6b707128faa8270fd5f291ba3c87cc685cfb48363f91220f74897140aebb
b2420aa8633408ef67a8c5e80df4a3aa061eb561649d887f5aa55481d350b655
d4577b3a267501cbd003cbdb898c03fe81eb14f9ddc1a7e71a5a54fa48fa27e2
d5afbd5425464bb6594a458be218e5c24db5abf4e88e8c11e065e357a14c8e49
e19fbf6376979c33bae2472ef372df206a23a21152ad7bb962ba653e0af75870
e808cf87d4055be30c9144a5d053b6314483f7800e0158b3614fa2ad266671c7
eaa3afaaaf34a833299b7d35e0692008b4044409ff9146fb98d4c796abd5e5ea
f17936397f6f9202ea8a728b07512ba8142fe7e224bf08cfbed0b247b3956ea4
feb67d669021041850e1b323cc17a7c5915fa581c8d5b06dfd4a82d4db48cdb0Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Zusy-9938038-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples
Registry Keys
Occurrences
<HKCR>\.EXE\DEFAULTICON 26
<HKCR>\.EXE\SHELL\OPEN\COMMAND Value Name: IsolatedCommand 26
<HKCR>\.EXE\SHELL\RUNAS\COMMAND 26
<HKCR>\.EXE\SHELL\RUNAS\COMMAND Value Name: IsolatedCommand 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MMDEVICES\AUDIO\CAPTURE\{E5F17801-A5F7-4B2F-BADC-3EC6DA930420}\PROPERTIES Value Name: {f19f064d-082c-4e27-bc73-6882a1bb8e4c},0 26
<HKCR>\.EXE 26
<HKCR>\.EXE\DEFAULTICON 26
<HKCR>\.EXE\SHELL 26
<HKCR>\.EXE\SHELL\OPEN 26
<HKCR>\.EXE\SHELL\OPEN\COMMAND 26
<HKCR>\.EXE\SHELL\RUNAS 26
<HKCR>\.EXE\SHELL\RUNAS\COMMAND 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MMDEVICES\AUDIO\CAPTURE\{E5F17801-A5F7-4B2F-BADC-3EC6DA930420}\PROPERTIES Value Name: {e4870e26-3cc5-4cd2-ba46-ca0a9a70ed04},0 26
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MMDEVICES\AUDIO\CAPTURE\{E5F17801-A5F7-4B2F-BADC-3EC6DA930420}\PROPERTIES Value Name: {e4870e26-3cc5-4cd2-ba46-ca0a9a70ed04},1 26
<HKCR>\.EXE Value Name: Content-Type 26
<HKCR>\MQKLDRV 5
<HKCR>\MQKLDRV\DEFAULTICON 5
<HKCR>\MQKLDRV\SHELL 5
<HKCR>\MQKLDRV\SHELL\OPEN 5
<HKCR>\MQKLDRV\SHELL\OPEN\COMMAND 5
<HKCR>\MQKLDRV\SHELL\RUNAS 5
<HKCR>\MQKLDRV\SHELL\RUNAS\COMMAND 5
<HKCR>\MQKLDRV 5
<HKCR>\MQKLDRV Value Name: Content-Type 5
<HKCR>\MQKLDRV\DEFAULTICON 5
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
153[.]92[.]0[.]10026
104[.]19[.]184[.]12014
104[.]19[.]185[.]12012
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
www[.]000webhost[.]com26
mvccs[.]webege[.]com26
Files and or directories created
Occurrences
\889ad32ed40b51203b2765b8cf7d65bb26
%TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp26
%APPDATA%\Microsoft\DLL7
%APPDATA%\Microsoft\SDL5
%APPDATA%\Microsoft\bin5
%APPDATA%\Microsoft\W643
%APPDATA%\Microsoft\SDL\icxml3
%APPDATA%\Microsoft\DLL\sconn32.inf3
%APPDATA%\Microsoft\DLL\lib_all3
%APPDATA%\Microsoft\bin\cmod3
%APPDATA%\Microsoft\Media3
%APPDATA%\Microsoft\DLL\apds3
%TEMP%\itzxujgnytpu.jpg3
%TEMP%\itzxujgnytpu.jpg.cr3
%APPDATA%\Microsoft\bin\winnt323
%APPDATA%\Microsoft\SDL\icxml\lust.bin2
%APPDATA%\Microsoft\DLL\srv32.inf2
%TEMP%\bnseprbpbsaetzxkchrxn.jpg2
%TEMP%\bnseprbpbsaetzxkchrxn.jpg.cr2
%APPDATA%\Microsoft\Media\list32.inf2
%APPDATA%\Microsoft\DLL\dwm32.exe2
%APPDATA%\Microsoft\DLL\nt32\openssh.ocx2
%TEMP%\uihaovzjnf.jpg2
%TEMP%\uihaovzjnf.jpg.cr2
%APPDATA%\Microsoft\SDL\sconn32.inf2
*See JSON for more IOCs
File Hashes 01fe52b810897fec2b30b8d03bb5d08c44c03f8921c41f3252877a31bc250875
039170d8ba2feeaac9c943aea7d3cf5709d2ed6fc1e3eaec8457ec13c631730b
0b7202dc4423ddaee59eff6909185052bc8c0cbd3cbe4e5224db8e83b935ec23
0b95c110d12725fcd8d95bf203b0fd8bf1bc9e57646f8b283ea63a35c0d4a38d
17289d65e7d2101e7b65d329981ff99e71a0896222d3c81e77b0fc196d995c17
19af3fe3c191528c15b3c9f791e02edc82eadab9126881da5f4ea4baa234f8c2
1c774c5849f22f0660abf46fc8bc270f7d26b4c10cf619e71617c65933b1950b
1f9d9c0ea95fc171040ee4c1614a4ff3e0b556411cad8f632e0abbb7ff0b9c89
1fe69a46cf7b96bc518b01a4f44ad5bdcf2581ec25faa3c6033c90cf8a8c6ee6
2de1e795015bf7ea4bfe8659300a525d83bbd2352e853b162a57a844eed0f05b
2f9b960d63a40d84ec185011dc06eaab64badb323f272c880934205e8a51819c
31ac7c0592bc741aad0745d85adb24db0766978a6111593fa46606c8d57bad83
36e800f52cf62574d21f46917bff838b2dd7f7e6d60556a597d593f9057c31ed
3fc9c60a2cdb4748b77a0433b71cfca6113fc67f06ab71c72745140ed126e134
44654adb36a0e86e49ece0f3d1193212d82779b5ac3a2f880a656cfddb52a2b9
47bca02db3899ec836de3305355861f86a7dccca64710b3f0e7ae5c7a2588440
4957c1f3ed393e71aa7875607d2b5e34c534058a81bd8709491ba809d8b208a0
4db97c35f9f17f68431a8683d9db3a426cd93e2ae95b863c2a5fbb0f4536f40e
6a295f8b9884fd1587f933876681928e002a5d320e460d1a97597462e60ef8ad
6ff434e99a93ca2f1cd000fcdadb7ee7122ad6bca1fc720304c1a4a08a1c0e6a
72c7b16114c3154dde6f62ba063379a880c8aaac76f9778be5db9f4f3efc26fa
7348942243782880e919a13c757f96808bb165c47e738619c8ac3f493e80591a
7a098345b4fa191021d8906cf2a027536fe85eecf8281eae3e968f09ad5e602d
818b73b6fcc1fdc0afab7e729a8ef3dda0f938450ea2c1533fe760d04f97d7d0
84f841117194485e3d6e26059e1b6336b45d02a9fa68a61cf611a2e54cd6f6a9*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
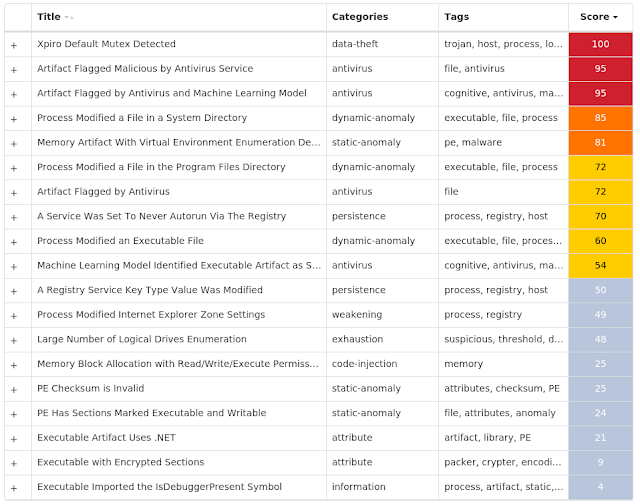
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Xpiro-9937847-1 Indicators of Compromise IOCs collected from dynamic analysis of 112 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Type 111
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 111
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 111
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 111
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 110
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 110
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Type 89
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Start 89
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC Value Name: Type 80
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC Value Name: Start 80
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Start 79
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 79
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 79
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 79
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 79
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 79
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Type 78
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 61
<HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 61
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Type 53
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 53
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Type 45
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 45
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC Value Name: Type 38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC Value Name: Start 38
Mutexes
Occurrences
kkq-vx_mtx1111
gazavat-svc111
kkq-vx_mtx58111
kkq-vx_mtx59111
kkq-vx_mtx60111
kkq-vx_mtx61111
kkq-vx_mtx62111
kkq-vx_mtx63111
kkq-vx_mtx64111
kkq-vx_mtx65111
kkq-vx_mtx66111
kkq-vx_mtx67111
kkq-vx_mtx68111
kkq-vx_mtx69111
kkq-vx_mtx70111
kkq-vx_mtx71111
kkq-vx_mtx72111
kkq-vx_mtx73111
kkq-vx_mtx74111
kkq-vx_mtx75111
kkq-vx_mtx76111
kkq-vx_mtx77111
kkq-vx_mtx78111
kkq-vx_mtx79111
kkq-vx_mtx80111
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org21
computer[.]example[.]org16
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com9
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com6
pizupedadu[.]net5
ejixab-ekew[.]ru5
ekaqo-copog[.]com5
epetyf-uxeb[.]ru5
enilof-azud[.]ru5
ecemi-gyqen[.]com5
edecub-ydyg[.]ru5
bukyrurysryvu[.]ru5
enacug-uzof[.]ru5
eryvof-ibuh[.]ru5
kesvawudoqu[.]ru5
elizyb-ypud[.]ru5
eleraf-yvot[.]ru5
eqiny-fecok[.]com5
ulepatok-ci[.]biz5
ekaba-gywuz[.]com5
emyta-habaj[.]com5
exezic-ucah[.]ru5
exybif-ajav[.]ru5
ezubih-inek[.]ru5
evahif-ufum[.]ru5
*See JSON for more IOCs
Files and or directories created
Occurrences
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe111
%System32%\alg.exe111
%SystemRoot%\SysWOW64\dllhost.exe111
%SystemRoot%\SysWOW64\svchost.exe111
%System32%\<random, matching '[a-z]{8}'>.tmp111
%SystemRoot%\microsoft.net\framework\v2.0.50727\<random, matching '[a-z]{8}'>.tmp111
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock110
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log108
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat107
%SystemRoot%\SysWOW64\msiexec.exe104
%SystemRoot%\microsoft.net\framework64\v2.0.50727\<random, matching '[a-z]{8}'>.tmp82
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe80
%SystemRoot%\SysWOW64\dllhost.vir80
%SystemRoot%\SysWOW64\msiexec.vir80
%SystemRoot%\SysWOW64\svchost.vir80
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log61
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.lock61
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngenservicelock.dat61
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe54
%SystemRoot%\microsoft.net\framework\v4.0.30319\<random, matching '[a-z]{8}'>.tmp54
%SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog51
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat51
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log48
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe45
%SystemRoot%\microsoft.net\framework64\v4.0.30319\<random, matching '[a-z]{8}'>.tmp45
*See JSON for more IOCs
File Hashes 0146b63880ff48e3814a8c984886c47173a131f512af5003a3d1649bc8d5fa16
082adebb6f224fce8804fd763d44f7fb6e660c6010aa48d1d4e80afafbb194db
0927940251747c3e852d2a4435b3199cac717b837266e59ab789d61394d8458d
0d13360e25f55da35580e86e36e3bce3f53898a61cae4314ddd40954b4e7b8d7
0fffdd58fb1e4e9808d5564968cca63bdf1d2e1346681de4e965b6ed8d90a693
109e9d59a74ca8720cc2119e5c30ab2a17bf4980b328e8823240d199bc26ef7c
10a7f2e6702f0e96d99c63f748b108ee5f129791fd16515e4493d06580f95cb7
11d1b21ef335f37f402aa8cf03f4dfd5e3b5a5a2b75c8e17664a86bfa82deccd
16167444c492a9130a165ed1aa0b5d40b3a28f3241b708b8022475cbcd7aed5f
173e844eb1999a886af8518694ecce89a1f97909ac91c3beffa9952fb9f92066
184dfba67aae7444b7f7c461658a499035c92d94f5c59031562dc9aea328bef3
19b4e88dd0f003319af5fa038b5fcc6bc87e84c98229e4341810f7e40fed149f
1b7f3e5991e0160fda07c58c161d937cb3941c61f85ba4dd50e414e08ed9f21b
1e18af808405e70485b4cd4adf8426654d5e3d6cf15dbebb7b97d6b02d46b9f6
215af852fedb9a012682f1154aa6eae31c0d10accaf82c19bc50783592b98840
22df92bd64bf9913bd653fa83bcedc642f25984a757da1cf0cab7f1195d0b01b
2766a8ac35d684d25370704d93997fa9e5043e6dc4df10a0f5dad558d29d4120
286e4ad9df37874b7cedfda35347ab13977c79a9e9fc63a57aed864b5ca18d9c
2975e2daa921e4e88d46f01d84564d4bdfd94438de09b558206c70bc39a7affe
2ccdf35fe35c441bdccad5c6ad17bffc54053058f7478b8f628a13a812e95520
30fb1200ca5e49f7d990b0ea0790df992f0dbd494283ec5b97e78567dadc0421
36350087b86461c74906f37e7a4cbea6bb8fcccb65f826b92da3c9e6e197157c
3948ec4de352687308b39c9a825102150d1e9b4a1d9f1e94ab6d29d9416090a8
3cfed6deb8617f09d5fc4f399512f29092423141fc8a4bee2df1308ec0b81a38
41302ac5bcf98bb12ac5c144f4cc79f6a1c314bcbad8d656a7ccdf0ddf69803c*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
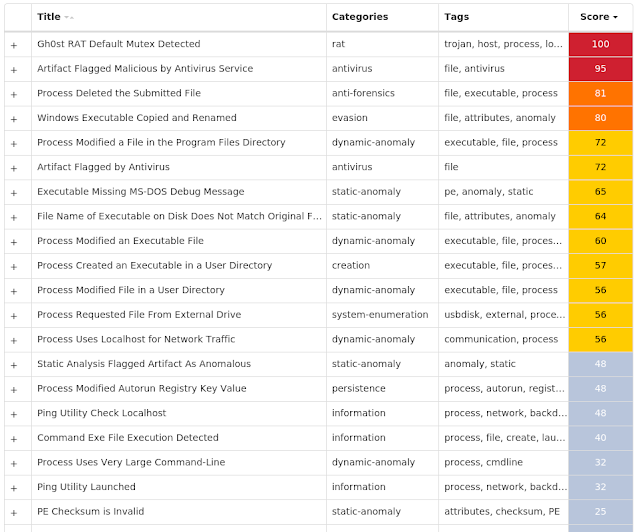
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Gh0stRAT-9937867-1 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ProMark 26
Mutexes
Occurrences
98.126.40.18:320426
M98.126.40.18:320426
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
98[.]126[.]40[.]2026
98[.]126[.]40[.]18/3126
123[.]126[.]45[.]9225
127[.]0[.]0[.]125
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
blogx[.]sina[.]com[.]cn25
blog[.]sina[.]com[.]cn25
wpad[.]example[.]org25
computer[.]example[.]org23
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com11
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com8
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com5
isatap[.]example[.]org4
Files and or directories created
Occurrences
\1.txt26
%TEMP%\<random, matching '[a-z]{4,9}'>.exe26
%ProgramFiles%\<random, matching '[a-z]{5,9}\[a-z]{3,9}'>.exe26
%ProgramFiles%\<random, matching '[a-z]{5,9}\[a-z]{3,9}'>.dll26
%ProgramFiles%\<random, matching '[a-z]{5,8}'>21
%ProgramFiles%\etutj\111311102
%ProgramFiles%\jizlhdgjy1
%ProgramFiles%\jizlhdgjy\111311101
%ProgramFiles%\fncqknndg\111311101
%ProgramFiles%\tgjiq\111311101
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\TBJLCRG5.txt1
\Users\user\AppData\Local\Temp\rjdtmdvea.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\I1NMHXOF.txt1
\Users\user\AppData\Local\Temp\jxexyvu.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\UOJOFISD.txt1
\Users\user\AppData\Local\Temp\vlrfn.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\5JI5O9IZ.txt1
\Users\user\AppData\Local\Temp\uymqzg.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\SVC5AK4U.txt1
\Users\user\AppData\Local\Temp\dhgza.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\SW18D943.txt1
\Users\user\AppData\Local\Temp\wrlcs.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\WJPYIEYE.txt1
\Users\user\AppData\Local\Temp\yfibrupfd.exe1
\Users\user\AppData\Local\Microsoft\Windows\INetCookies\PHFF8H3C.txt1
*See JSON for more IOCs
File Hashes 00c8756311125df601d4539e6db4e7510b2e4a22dc62d824820e14af23a07545
012baec662bcf7b4065ff3dd500ac62f68fa0060c5f947e77a9fe97c64d0fe7c
037994e3ad96e4ccc23e06954e35b61af161fb4af803c984cce75179d63f1c95
05e84b1c928d0dc80f25f9d397deb8104f9399cfe50052843b3d6b8889de09c2
0600d03e4084a5e85d25341b868abdf73fb670d26bb62ba62af6367f82052841
069f2b048ac362cf480808b9c007190af0a41d3aaa5489b7a6cd0c2bee65cac7
07c0945f8df6614e8e6eca4043bd01a01e17b7245dbde2a7fa996a94f79cfb56
07fd4ed37edadfcb54c718a9d2c3cae50b1544941a5ada086b2b0e66bec0458e
0844ece2826cbbc2d21e8fbfe96283973869e9fd72e3e90e4b430a5489b1331b
08901dc1c2920e63f7df244c8bcf841fc872fd0e094c8ca53f738993c39da428
103da6c0ad8c4abcda2ac74ea9a999dbe3058bedc4648a398cec7439d5116a87
10b153ebc28631b0c1c2229266a85094232031ffdb3da2d79d6cf6af5aa60bbb
12d4e6f409754c3d1f01c1c66dec57b84f3198ffcb76a32ad8e3dec16480e8c8
153e3f4f0e496e7dd9fcb16bc57b7b536ed973a472cf12d8cb679294a72993d8
16861b7e1b36c6f4f0b7939b27c58a7dccacf9c244ad3d606098fc189550e8ee
17744b8bb37cfdb35549ceea7f7ea9724e0de641c4dcdfd533b208e40fd53640
17b8ac30efb8b3ec96b6b0322ef90aae156193c5733d088f453edae3ee18521d
1857f227d2f67edba0e6c791d4c6e1de32a61155f872c00e6d266cdf3463b48b
19e9e5e4567c26dcb1dc95a57199400a40997d74afd0f30977c1cf8a4437cbc0
1a22d9de44ef690e4734297e1e604270c62f43ec46885c0c9e61b9e508dbeb6a
1aef59d0edd76bf0f9c1ae6a11a4e4a2530c6619a971baf3e38df34736c48d6b
1af9e537522c8d24879810774d573d5e059268989be0fc047dabd11f3c54f31d
1d01013febc339550b752056b7479e09d0f9a351014236c40051ffcb3d471200
1d7dedbf5b672fe96d0fd38296bf8780964e2db63108e392e1cd58f2b429cbfa
1d859f90f6408689672df6d0f33bcd4ed3177f0cacd1ef8ded3496a349d159f3*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
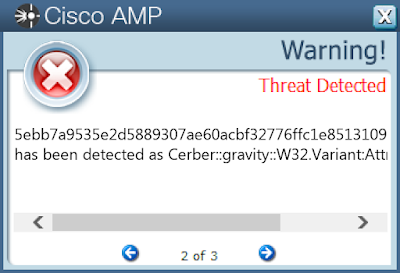
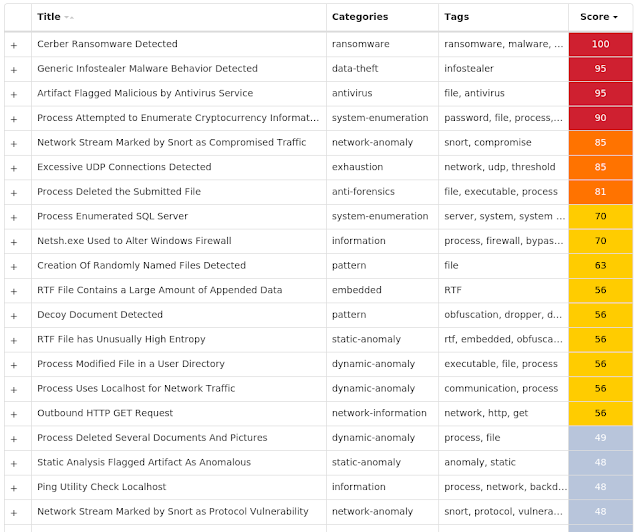
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9937930-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 15
Mutexes
Occurrences
shell.{381828AA-8B28-3374-1B67-35680555C5EF}15
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
178[.]128[.]255[.]17915
94[.]21[.]172[.]0/2715
94[.]22[.]172[.]0/2715
94[.]23[.]172[.]0/2213
172[.]67[.]2[.]888
172[.]66[.]42[.]2388
172[.]66[.]41[.]187
104[.]20[.]21[.]2514
104[.]20[.]20[.]2513
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
api[.]blockcypher[.]com15
bitaps[.]com15
chain[.]so15
btc[.]blockr[.]io15
p27dokhpz2n7nvgr[.]1k1dxt[.]top15
computer[.]example[.]org14
wpad[.]example[.]org14
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com3
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com2
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com1
Files and or directories created
Occurrences
\pc\users\public\recorded tv\sample media\win7_scenic-demoshort_raw.wtv15
%TEMP%\d19ab98915
%TEMP%\d19ab989\4710.tmp15
%TEMP%\d19ab989\a35f.tmp15
%LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat15
<dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.hta15
<dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.txt15
\Users\user\AppData\Local\Microsoft\Office\15.0\OfficeFileCache\CentralTable.accdb13
\Users\user\Documents\Documents\resume.docx13
\Users\user\Documents\Documents\resume.pdf13
\Users\user\Documents\Documents\resume.rtf13
\Users\user\Documents\Documents\resume.x.odt13
\Users\user\Documents\Presentations\Presentation 1.ppt13
\Users\user\Documents\Presentations\Presentation 1.pptx13
\Users\user\Documents\Sheets\budget.5.xls13
\Users\user\Documents\Sheets\budget.xls13
\Users\user\AppData\Local\Temp\24e2b309\1719.tmp13
\Users\user\AppData\Local\Temp\24e2b309\4436.tmp13
\Users\user\Documents\Documents\resume.docm13
\Users\user\Documents\Documents\resume.dot13
\Users\user\Documents\Documents\resume.dotm13
\Users\user\Documents\Documents\resume.dotx13
\Users\user\Documents\Documents\resume.x.xml13
\Users\user\Documents\Documents\resume.xml13
\Users\user\Documents\Documents\resume.xps13
*See JSON for more IOCs
File Hashes 08de2d3767faa6597f3f656f9548626b6b359d0e7858b14b162e9071c90c8024
1a3299de3a1cd0aa910aec86cd577091be1c6dcb8a19e069a808e1518d997136
1b7ee0c653b0ac56db4119dbce34d721d86adf64d019cb702fb7c3d770d28205
2148db4f9d6b8905d800c6e08235803d3fc3f27f8a5720d09dfdc45db942b81e
2188930d8b1a5fe57f3f88eb36367947c6b83aeb525d6943eeac4411c8530977
288ca900f24008e53da883abf9ed36d4aa0fbe92075172766c1c2800ad224642
48150a4c54fcc74aaaf5a3f06a1a976ffbb5c2239769ec29f25c15c7a17a410e
489e67d5ab246d3224ca5a14eeadaccc0f7da5f64c160ab03a779e6e7724d3c5
5ebb7a9535e2d5889307ae60acbf32776ffc1e8513109b023618eeacd6c53e8a
74c6d65599d8b5e6b0cb43455ecbb26d131cabbb88f6edf8a0f5ae30ddec2595
96b0bb69d046fef1b74a62f6e1ed81b2a129d0b86c0b79d505b5f6fd1f7707e0
ac81016b4bb9755c249bcf51a9087f0099c8240df7c852158a18f23914c05df4
adfbfcc0a8e3813b64087934c23ded140e41285335ad7e67923d18e9c145a656
b768646fd9ff96739a1322fbe5b2244f36d479803b83362281587bee2c0049ca
c0a91edf65cbaddb99c2d9dda1210b62d0f0895edf49dc44eb1618e9f81ee1c3Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Tofsee-9937919-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples
Registry Keys
Occurrences
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config4 16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES 16
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config3 16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\uvbxavmh 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\cdjfidup 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\wxdzcxoj 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\lmsormdy 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\opvrupgb 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\fgmilgxs 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\dekgjevq 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\xyeadypk 1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\ijplojav 1
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
91[.]243[.]33[.]4/3117
193[.]0[.]6[.]13516
74[.]208[.]5[.]20/3115
192[.]0[.]47[.]5914
125[.]209[.]238[.]10014
103[.]224[.]212[.]3413
157[.]240[.]229[.]17413
45[.]33[.]83[.]7512
211[.]231[.]108[.]46/3112
96[.]103[.]145[.]164/3112
185[.]244[.]41[.]12512
62[.]204[.]41[.]4512
144[.]160[.]235[.]14311
64[.]98[.]36[.]411
51[.]81[.]57[.]5811
117[.]53[.]116[.]1511
209[.]222[.]82[.]252/3111
64[.]136[.]44[.]3710
194[.]25[.]134[.]72/3110
40[.]93[.]207[.]0/3110
104[.]248[.]39[.]23610
212[.]54[.]56[.]119
87[.]98[.]164[.]1559
212[.]77[.]101[.]49
119[.]205[.]212[.]2199
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
fastpool[.]xyz17
249[.]5[.]55[.]69[.]bl[.]spamcop[.]net16
249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org16
249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net16
249[.]5[.]55[.]69[.]in-addr[.]arpa16
249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org16
249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org16
microsoft-com[.]mail[.]protection[.]outlook[.]com16
microsoft[.]com16
www[.]google[.]com16
patmushta[.]info16
whois[.]arin[.]net15
whois[.]iana[.]org15
ianawhois[.]vip[.]icann[.]org15
aspmx[.]l[.]google[.]com15
mx-aol[.]mail[.]gm0[.]yahoodns[.]net15
mx01[.]oxsus-vadesecure[.]net15
m[.]youtube[.]com14
mx1[.]naver[.]com14
naver[.]com14
www[.]instagram[.]com13
verizon[.]net13
park-mx[.]above[.]com13
mx01[.]mail[.]icloud[.]com13
mail[.]h-email[.]net12
*See JSON for more IOCs
Files and or directories created
Occurrences
%System32%\config\systemprofile:.repos17
%SystemRoot%\SysWOW64\config\systemprofile16
%SystemRoot%\SysWOW64\config\systemprofile:.repos16
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>16
%TEMP%\<random, matching '[a-z]{8}'>.exe14
\Users\user\AppData\Local\Temp\aqacoxot.exe1
\Users\user\AppData\Local\Temp\xzhgwwqn.exe1
\Users\user\AppData\Local\Temp\ibqvoqnw.exe1
\Users\user\AppData\Local\Temp\aqeoqudy.exe1
\Users\user\AppData\Local\Temp\yrlxhdsr.exe1
\Users\user\AppData\Local\Temp\vxkqxqdq.exe1
\Users\user\AppData\Local\Temp\dfsyfyly.exe1
\Users\user\AppData\Local\Temp\lcqnagj.exe1
\Users\user\AppData\Local\Temp\hojafkwd.exe1
\Users\user\AppData\Local\Temp\ipgpdpiz.exe1
\Users\user\AppData\Local\Temp\rhrtfofk.exe1
\Users\user\AppData\Local\Temp\kbpmzfi.exe1
%TEMP%\nespcil.exe1
\Users\user\AppData\Local\Temp\rcdvigyj.exe1
\Users\user\AppData\Local\Temp\lwxpcasd.exe1
\Users\user\AppData\Local\Temp\ibvhrncb.exe1
%TEMP%\krvuvcl.exe1
\Users\user\AppData\Local\Temp\qsazppjg.exe1
\Users\user\AppData\Local\Temp\vcxotykr.exe1
\Users\user\AppData\Local\Temp\exrdnjyx.exe1
File Hashes 56bdac8f204b5e033c4afc6716d8fd33a8fe6beb56a047d4af9f03e4c9c9e42e
698872f1e880627050b2ae7807f34b5de3d97031becc08eb6cf017743b10c7d2
707418b4d1337719e589bb9118f7d671d9dfedf6b9adf4be20a55236edb1d5c2
7ce600197d23b7aa778a38fd60581e6e4940878954e3c9d5cb252b7b22268415
82daa936a4d449f4c81c0c00382aa9265ba8c63ef465338a2595848ecbf67014
873dd8b59f5e66749623cbd67a4bfc1da5c58c3d4508b7fc6e4dbd48ce3b06dc
9167973f04bd43ea6afe9cd3c4495bf52642823ff9caba3d4b1002b614e1d697
95799e4845e5dab6f5dce9427e1454776a0106caebd97327993b9c41d6946317
9ad46638f30ae7c3b6a4db8c193c8940af245074f4d541c5902140978c4c0146
a2251469a43625ba05f126ab9dfb72de8af596796a7abcb17177f134c1610e52
a3ef861e97d21b65102377b7bab68ef33e22e1b4a0e44ff781e43c326821671c
a81b000c8092297045fc9e4747c27c633a3b25555a51f04785a136dd1a4f689a
b5827f75398807e71c85dea8b94d5065ca9637682e3e5ad916a571d4879f3277
b8ecbe2bc3f042ac701481bf5b999e0cfb1b0864dcb7a62322cc883ec2fca1e6
be0670b1c7cfb659c4996cd16b084c1075259d9bcec1bf39d7cb66d68d4f522c
d55d66c74de397b76d61e65c7de7933fb19373487636ffa3746d07954953bb7e
d8c21fd244ebafd495b42bca6afb4c4f2da8f0c02a2099b8ed8f5158850974c1
dee2ad9429c34f56b9171497718cbc8d2ade95bffca411c0c688d58b32162c2e
ed05f5d837cfc0f43103e27c5f498797f559d075c5ea8d9f7e96889251bc03c4Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.TinyBanker-9937976-1 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: F9D4B853 28
Mutexes
Occurrences
F9D4B85328
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
216[.]218[.]185[.]1621
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
www[.]google[.]com5
elitiorecfreetoo[.]cc5
wpad[.]example[.]org2
rbnqpdmnmmqy[.]in1
peekkbegqseq[.]in1
qiiorrvpixxh[.]in1
htcrixhpcbro[.]in1
phynembukviv[.]in1
rcwptdqhwgwn[.]in1
vggnnwluulow[.]in1
rfwbvyhebwhm[.]in1
qtimcktggoyb[.]in1
lsfeccdetgfn[.]in1
wdddcxsjipoj[.]in1
pccpmjksbime[.]in1
rvlltunqqtti[.]in1
limodtldsllw[.]net1
qjrsjiqjvuvp[.]net1
qiiorrvpixxh[.]net1
rcgrqvokxcbo[.]com1
rvlltunqqtti[.]com1
ppbvjehxriik[.]net1
qtimcktggoyb[.]net1
tetursjyjkxy[.]net1
wdddcxsjipoj[.]com1
*See JSON for more IOCs
Files and or directories created
Occurrences
%HOMEPATH%\AppData\LocalLow\F9D4B85328
%APPDATA%\F9D4B85328
%APPDATA%\F9D4B853\bin.exe28
\Users\user\AppData\Roaming\B0F5D613\bin.exe1
\Users\user\AppData\Roaming\C0B695D2\bin.exe1
File Hashes 004b32a0dffa653ec0ff5db7e53b5e7606ea7bd157fd1733d6a8b7ba0b60c092
011a76e331e5914079a3298e5bef41ffb264fce42fe9621e17dd441d207772fe
011e14f2d85716091b6c0e129afc1fe58308c4ce1bebf74e22ed328d65f8dd54
0157df54be488981123408a5bf03905e1823439ee3e547de5a113a5eb4d9105e
031fdf7833b8cec63dff1a3e1df355f98be610bc189263f08bf9b53081449c34
04ca485b3c7cc9082d7ab7e10ccb2e6ac302b056bafbcf97e4771fb1c94df1f5
05254328ae610070c4f40aeb962d01d40f35df78c19e2c227b41dcf079f2b5e0
064906db12fa19e05d96066049018488f02f34c163f3d97f577aec53152cd186
067f329c38bfb4e7d88c1f7b1aedccfede73e5852ff5db95ddadfa5db2ee8b0a
08a31bc88103314d111f57972f6694a9ba47e2dd9c6792575e15c529aaf7fc8b
098553a5cda7c243562f70c90a158a1a8233cead1922f5088458d5c50434f6ad
09ce4ba4a71edd640cf3563054aeb082beac84e38eed5e1dbb28a99cd7335603
0a3aac9c77ea6eb8a24c9f0cb770a6a1387779375b171f91cf083cf093592c0b
0c97785067aa72971a54779e9706c5e32428c15116a1fe41e3a32f76b7bddca0
0d93292363215081c943b2b4d9ebbb34fed6a63aeb2dbd3ba23d94f5ce2bfb3f
0e926dd8fb140117c135440fa4927607e6b936cb2f5825dc45cc0ca0cb82fa61
0ebd360107830750c835a525d2fdbf9e3ef3ac14e4818feb9a1ae6665967d86f
0ed37e99b4ea3cff1fe566af65b3ab8e6f840003a179d0b52fb1a60bf818f053
0f981423b4afe1bf9d133b947c416b5472d63833181da7765c4b015830ac3306
0fcb4ca8922d84d3016662082a87a28f95661197cd141f357ef6d456b15274bb
1041344672a27d141730bac1ce09627fe18b37f151ec73f16582a3fb1e896271
10f3f470c2714cb2aab0b9ea85c52c7215989d4c6dc9cf44681fea17ca7f8058
11e92cf32e0c4fb54841e43f06c53f2e73dde868eba7ad5c84dff3ff27a7d297
17d534514602b836c10fdd066273d3d26525bfb84821e568ec16f26f9b3e4891
17fadb2ba39656ec163749ae91310845d203382f0f624f946250b82b53707a41*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK