Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Feb. 10 and Feb. 17. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
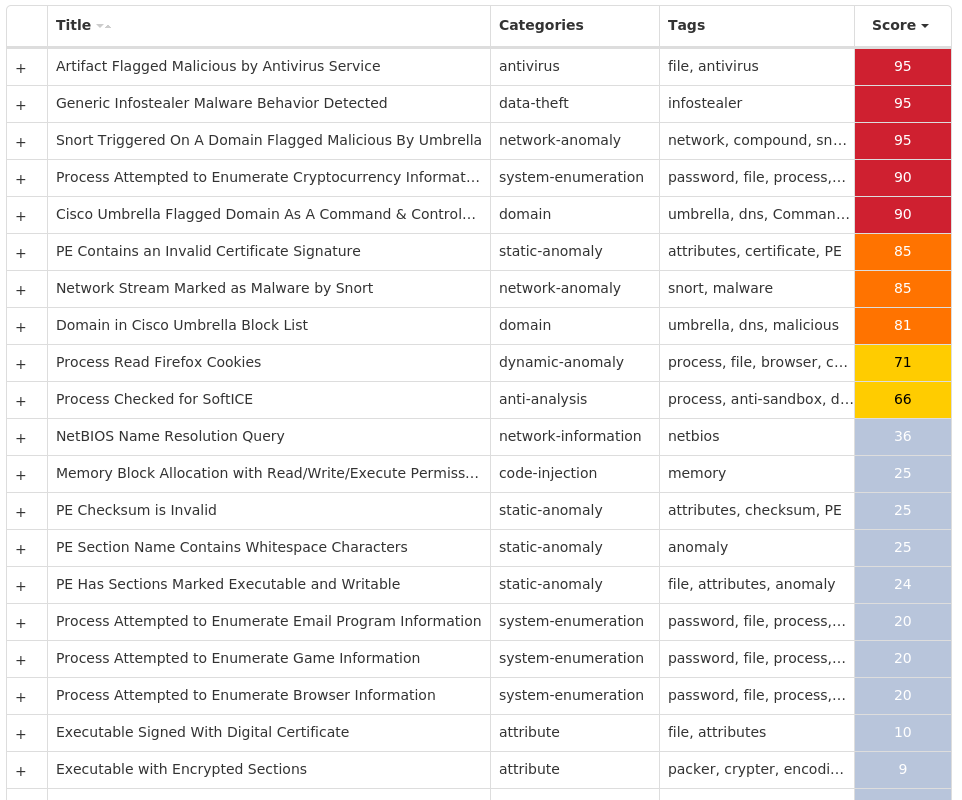
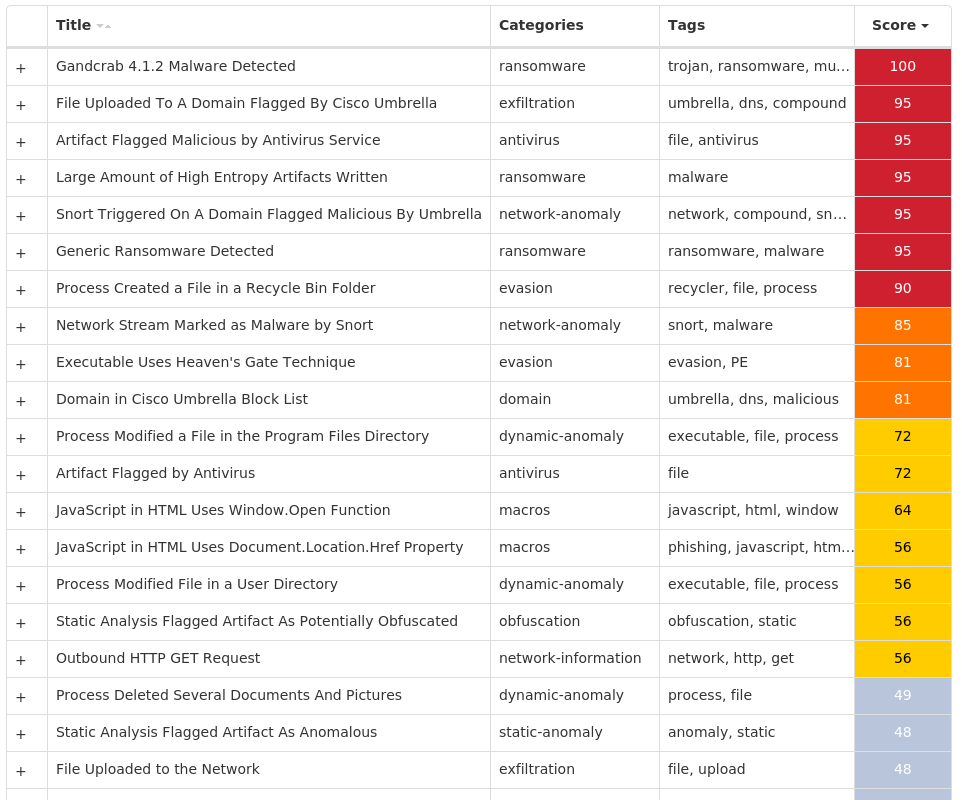
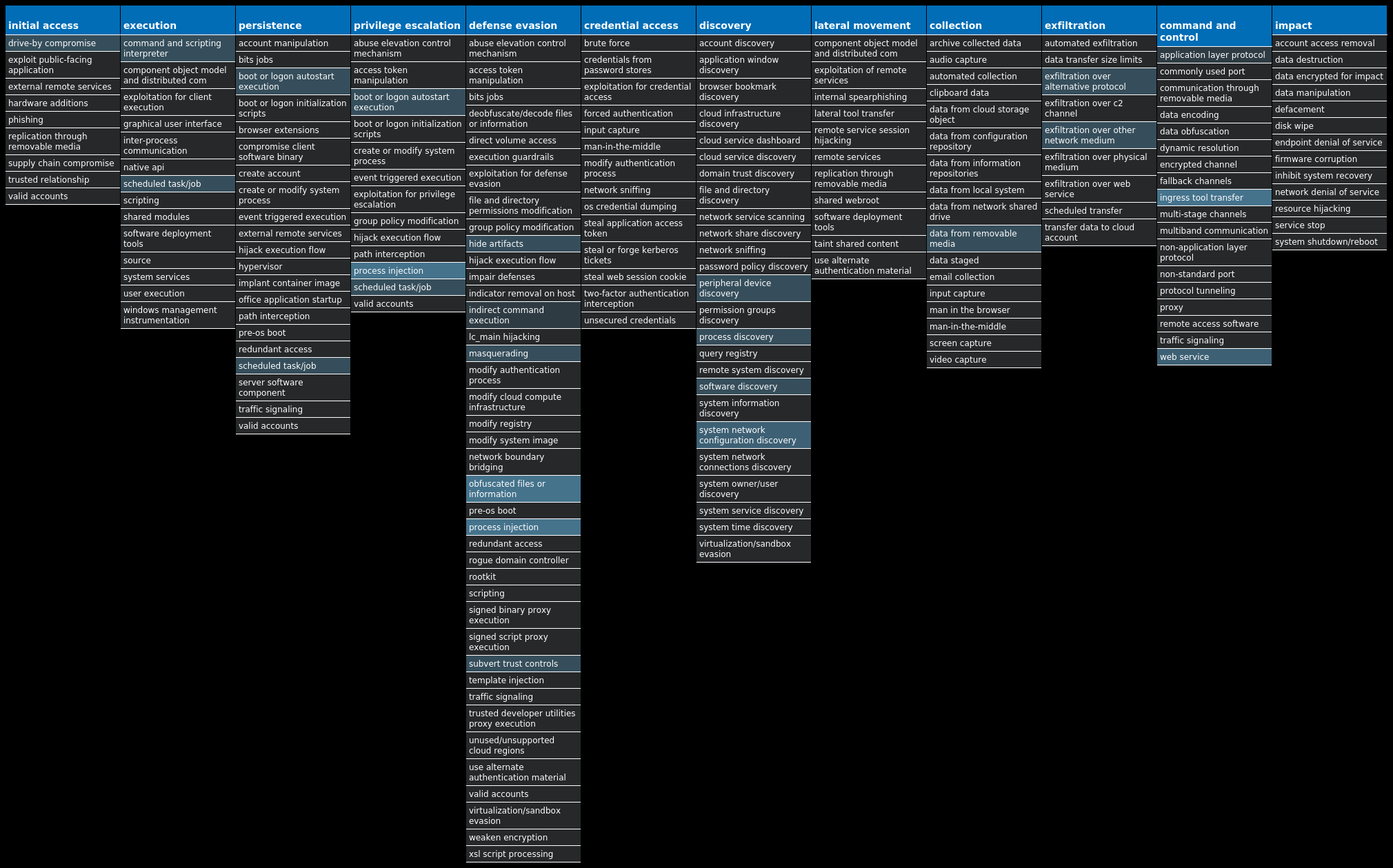
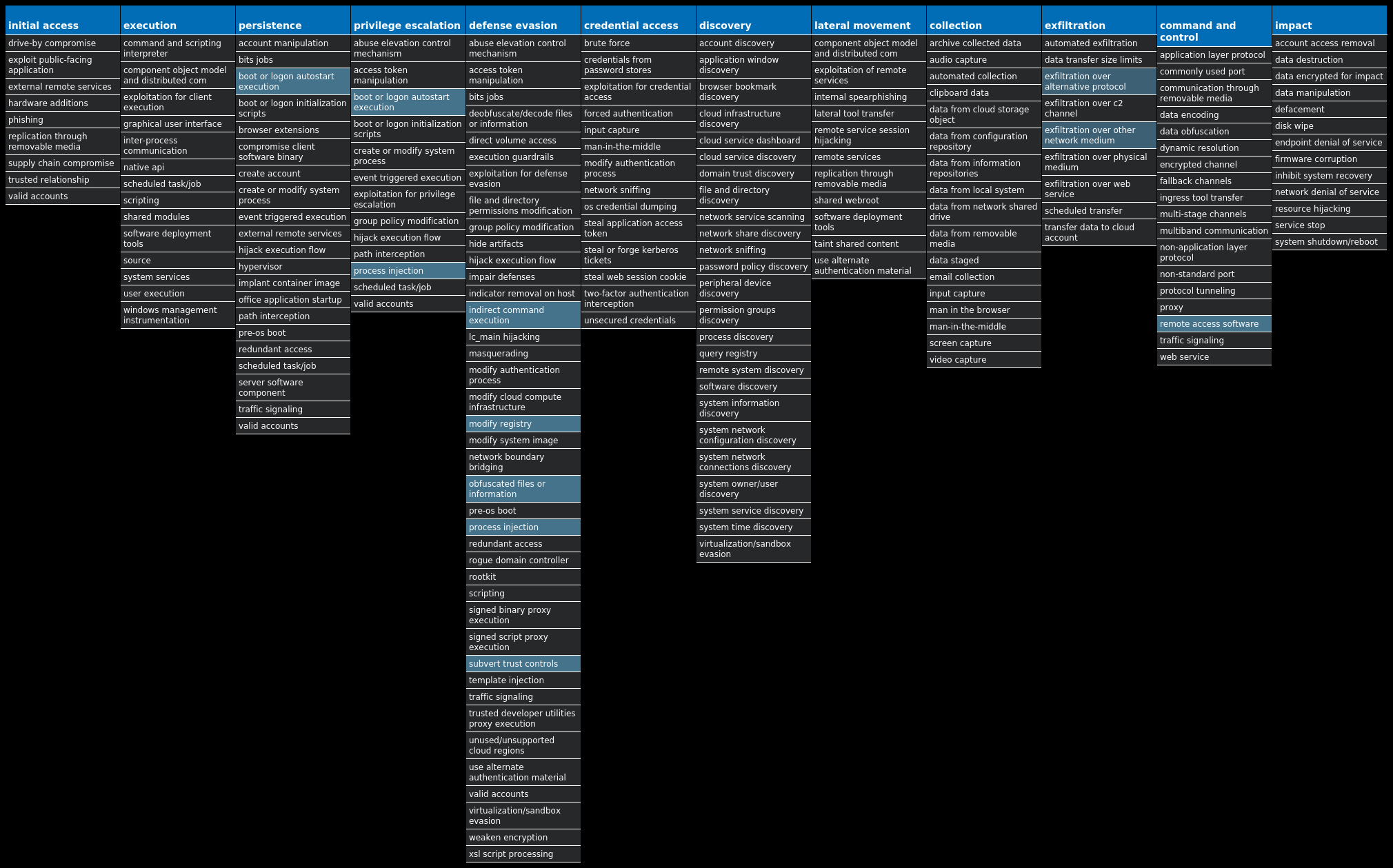
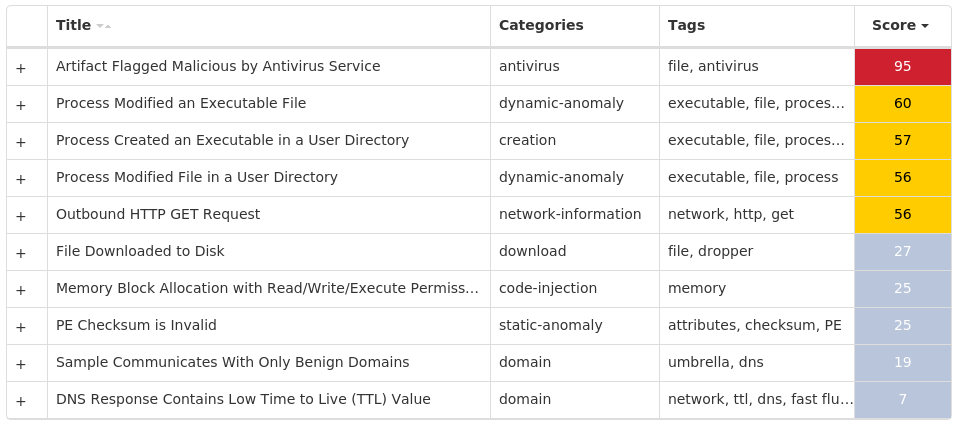
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Ransomware.Cerber-9987352-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Dropper.LokiBot-9987759-0 Dropper Lokibot is an information-stealing malware designed to siphon sensitive information stored on an infected device. It is modular in nature, including the ability to steal sensitive information from several popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Dropper.Ramnit-9987280-0 Dropper Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It can also steal browser cookies and try to hide from popular antivirus software. Win.Dropper.Gandcrab-9987386-0 Dropper Gandcrab is ransomware that encrypts documents, photos, databases and other important files using the file extension ".GDCB," ".CRAB" or ".KRAB". Gandcrab is spread through both traditional spam campaigns, as well as multiple exploit kits, including Rig and Grandsoft. Win.Dropper.TrickBot-9987411-0 Dropper Trickbot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts. Win.Dropper.DarkComet-9987724-1 Dropper DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. The malware can download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system. Win.Packed.Shiz-9987720-0 Packed Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. Win.Packed.Zbot-9987774-0 Packed Zbot, also known as Zeus, is a trojan that steals information such as banking credentials, using methods like key-logging and form-grabbing. Win.Malware.Upatre-9987791-0 Malware Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables such as banking malware.
Threat Breakdown Win.Ransomware.Cerber-9987352-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 94[.]21[.]172[.]0/2711 94[.]22[.]172[.]0/2711 94[.]23[.]172[.]0/2211 178[.]128[.]255[.]17910 104[.]20[.]21[.]2515 172[.]66[.]42[.]2385 172[.]66[.]41[.]185 104[.]20[.]20[.]2514 172[.]67[.]2[.]882
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com11 bitaps[.]com10 chain[.]so10 btc[.]blockr[.]io10 hjhqmbxyinislkkt[.]1j9r76[.]top1
Files and or directories created Occurrences %TEMP%\d19ab98911 %TEMP%\d19ab989\4710.tmp11 %TEMP%\d19ab989\a35f.tmp11 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat11 <dir>\_READ_THI$_FILE_<random, matching [A-F0-9]{4,8}>_.hta11 <dir>\_READ_THI$_FILE_<random, matching [A-F0-9]{4,8}>_.txt11 \pc\users\public\recorded tv\sample media\win7_scenic-demoshort_raw.wtv8
File Hashes 06b444d20ea1a2fc7726b4e1bc2c03708cb0719dd09db2e41604dc2f30755dfc14bff12c186c1042535d7ca79bab96738ddd5dbdc975ac4fb271113c01ff8c0214c70464b6367a5a9afe3254d5ceb04013896506cac23bead508b4a00442915717eaac07edc82c30cdcdb7e7ac163d9aa67607af29c25324de84a40fe4084e0f27fb7cd60bb97d1fe8ba827b8537191511391fb49c97da1208e982c325b4bc485d14e28719b83655d43461ea60f557e24c365269ffc41993e6c51eb7fa794f1c73c3883e26a9a403053c673859709b0a43fb32de196c71d86c4e7480b78207ee8be38ae7931c75bc6d8cb80fc9a2d95660eb269f321970cc7da453238bcd7482ca5f7747f518aa7b48e3454643860cd8d9909bbc965f6955ea70c8889ffe4504dacf34683b6aaf0f233d22d99eb5af7cdab36398e2e86af52ea53464e8be1539f73a96e66ead8238a4d5d83cf076456cd7e5b47558dbb5dc52e2ce9f9d91beac
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
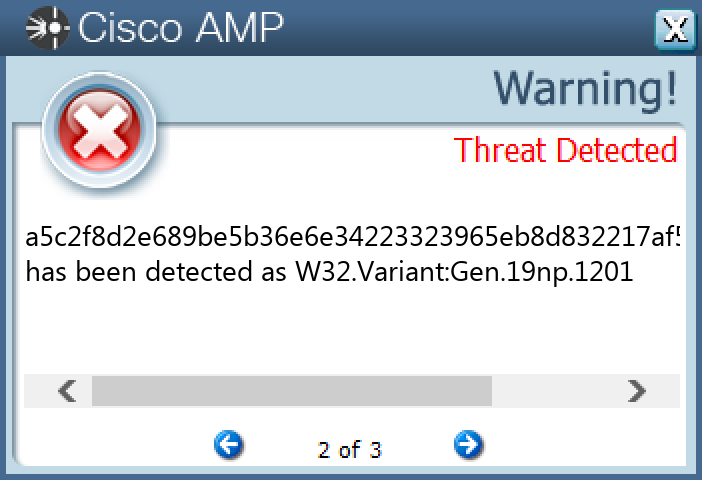
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.LokiBot-9987759-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: LLENES 18 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: DynamicInfo 1
Files and or directories created Occurrences %ProgramData%\TVINDINGER.scr18 %System32%\Tasks\LLENES18
File Hashes 07f02393195d8c9d597419c4ca54eb4dc90b2e847763d3d479caa69935411bc00be581f5f102f0fce5d5cf26b69942231d842cd7b221f008f0e633deeee055001621a2bb84b4c0d8e88be841f5bbf2d9457bba1d316d674faa7bc9c64bd50fea1e9623428570505c6ee127a9afaa4741c2ed8958c77f59367edfeaa0660ecaa764f47d30e8f110c89ed56a7c8344bc17aa46df114ec9d19cc3dae5889ad7cd796bc3d5bdea707ec5ef5fbffd0ee59ba99b1ca0a0fdaf7bb294549b067f397a986bfeb75aef998110a3a4e1ac4f5b8dcfce294ddc87d533c78a26fe0d111c4f5f7479bfd01c46646868bab0ad2839fafd1d850aa8386600a9580e1c0f53e2837078bcde4345b33c5ad9a30a07e0ab9e858b93aef79a6862a1ffa2e092502484e190d22eeb34f609676a6afc04b431851565d50f497b5a731391b4a7ded766b2019c5b4f080db8c8a25d52e1353d1672d72b8b663464774a6f4ed103c3c4798d679f88c5ca55ed9d689f59af586c55bbacfd9680677f8b8061377505cae622bafda18f7246f1250ba929c3c58b858939668e8ce96da1187148cb126ef399e42b8ab86886b7f3d80e751d0bba0f3a22c63613be992973fe4f8f0dacf2883f8d4ddec1a398db47a98d88de0ce57b36a29f67828f6ec6343bdf13e8323b33b8cddbe2dc896be13aed92322cd28ddacd63286ce933c335f3f2745d9ce53fee65298c4bdd355884a68a133f02930c8937e082cd4aca1124d6a1e61f0aed07bebaad053cfff5ccde8416fb79e016aaadecf5abd40786c84f76d137e6d792293c40a22576
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Ramnit-9987280-0 Indicators of Compromise IOCs collected from dynamic analysis of 75 samples Mutexes Occurrences b3c4139ec8994c68bbff2d53a795f30117 iwqdo1 mabwk1 bewc1 kcmkg1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 74[.]208[.]208[.]18317 74[.]208[.]175[.]1068 74[.]208[.]181[.]1797 23[.]94[.]163[.]164 198[.]12[.]107[.]2434 198[.]71[.]56[.]733 74[.]208[.]33[.]1483 74[.]208[.]151[.]2091
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cryptotab[.]me4 portexgame[.]xyz2 loadlink[.]xyz2
Files and or directories created Occurrences %System32%\Tasks\DriverUpdates17 %TEMP%\RES<random, matching '[A-F0-9]{3,4}'>.tmp17 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp17 %TEMP%\<random, matching '[a-z0-9]{8}'>.dll17 %TEMP%\<random, matching '[a-z0-9]{8}'>.out17 %TEMP%\<random, matching '[a-z0-9]{8}'>.0.cs17 %TEMP%\<random, matching '[a-z0-9]{8}'>.cmdline17 %LOCALAPPDATA%\Yandex4 %LOCALAPPDATA%\Yandex\YaAddon4 %SystemRoot%\Tasks\iwqdo.job1 %SystemRoot%\Tasks\mabwk.job1 %TEMP%\-5yl__pn.dll1 %TEMP%\-5yl__pn.0.cs1 %TEMP%\-5yl__pn.cmdline1 %TEMP%\-5yl__pn.out1 %TEMP%\iln_-8bo.0.cs1 %TEMP%\iln_-8bo.cmdline1 %TEMP%\iln_-8bo.dll1 %TEMP%\iln_-8bo.out1 %TEMP%\fhg_fw_h.0.cs1 %TEMP%\fhg_fw_h.cmdline1 %TEMP%\fhg_fw_h.dll1 %TEMP%\fhg_fw_h.out1 %TEMP%\_rbzi2m4.0.cs1 %TEMP%\_rbzi2m4.cmdline1
*See JSON for more IOCs
File Hashes 02bd161beee232d6ecf9c7a8a0fe80c2545227451547459f4612c5da81ba5b5b0368afd2468ede3c2a87c5988d8d880017b66907890d36285d4e878585ff1ff5041401ea1601b14048afc6b726d4b417ca8aa1a6358e51744ee4a123ba636f8708eb344569251e4fc99c3de92a7bf8d8ac36a1c6aa410273dd1e063ededb4a42096d82b60d52de1e7ec7e85c234db5bf8140730051127e87b5e8957c332b19f20d62d5ab9c799ad6d0121505f965400007cecc4f2b7fd5f907e69bb96e1f83c40e8673929faeaed582fbb578afa829f9363e7e297e2fea9addbe5a679ae5c0380fdb520255fdc09c07c596f670e077e7e974af4e9b2df6fa254ef034631d950c10bbc14c15b368e4a48aba3cf2e6e0192e73e3e190c1952df5d6a13f57295d9e14a3bcfe545de508cb00e55ed07bf88577f1f705ca6cdd15b733235f1d3847291b6e4c705bd5306e35649e5ee0812c80a0cdfa60b045454f488dd7ef8f55d4732107ea6810560dcedfc5a4ed35a11caa5619cba7cde29557642482b83dccdf272a6578cf548414e7f684ddb608b09d0584c6ee755e16bec78624368d2463b5082ba72a8de72521e03d24fd9c062d7c1d11e347198f09fbfc9726f78739a50baf2cf0e11b4d3ed524a99a327e52a246b73d5d91ff938bcbe58d31d4511d2b910f2d3ce270807d037b5cdc8ec95351c82ad17e03508ef554cdb9b4b419d0084e262e0fc89b9e4676bf7966ed1485581ca395d01bea1ea89df0c0529f5281bc73b03642e57a9da01bd7b6b5d9a1054c21fbbc73656e7253f0b7434fc952c9761b6d37e19470f3e2161ae58a9bda0a9fdce6e7ba726ee13027d5a50f7bcd1b891818380bf2a2bac7a49b9dfaa3dae8b56397672108ab24f41dfb3d670ffb28f6a8253a5f79652f87ccb4c9798113f7a919f9f88cf4221de4486d249a24eac1e846fc3b69ea5e38470aa747535697b40dc6f5a2924ce2c44ff8b809459bdbd41edf7d3c6b98c113741da5f2ac7896a314b8800bf60d90ab6e2ef7acb7380460d51f163e71f6d4e7142c28ee7fcc14925293f0c4608b0e0ae3a8e025faff261b4263b1418458f7a25840f6c8b8a9982dec09d02e297b93aeb73e2e87ce30eaf171622a
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Gandcrab-9987386-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKCU>\SOFTWARE\KEYS_DATA4 <HKCU>\SOFTWARE\KEYS_DATA\DATA4 <HKCU>\SOFTWARE\KEYS_DATA\DATA Value Name: public 4 <HKCU>\SOFTWARE\KEYS_DATA\DATA Value Name: private 4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}1
Mutexes Occurrences A16467FA-7343A2EC-6F235135-4B9A74AC-F1DC8406A6 10853E93BDB42AC8C03259A196091EB198B68E3C4 Global\8B5BAAB9E36E4507C5F5.lock4
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 139[.]59[.]208[.]2464 130[.]255[.]73[.]904 185[.]121[.]177[.]1774 192[.]42[.]116[.]414 204[.]11[.]56[.]484 193[.]183[.]98[.]664 5[.]135[.]183[.]1464 185[.]121[.]177[.]534 169[.]239[.]202[.]2024 144[.]76[.]133[.]384 51[.]254[.]25[.]1154 51[.]255[.]48[.]784 23[.]56[.]169[.]1473 15[.]188[.]214[.]2303 51[.]15[.]229[.]1272 35[.]205[.]61[.]671 23[.]221[.]227[.]1651 23[.]221[.]227[.]1721 13[.]37[.]189[.]211 23[.]56[.]169[.]1521
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]msftncsi[.]com4 d3s1[.]me4 kiyanka[.]club4 proxy-exe[.]bit4 www[.]billerimpex[.]com4 www[.]macartegrise[.]eu4 dom2[.]website4 apps[.]identrust[.]com2 www[.]poketeg[.]com1
Files and or directories created Occurrences %APPDATA%\Adobe\Acrobat\9.0\JavaScripts\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Acrobat\9.0\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Acrobat\9.0\Security\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Acrobat\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Flash Player\AssetCache\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Flash Player\AssetCache\TRFRW6GU\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Flash Player\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\Flash Player\NativeCache\KRAB-DECRYPT.txt4 %APPDATA%\Adobe\KRAB-DECRYPT.txt4 %APPDATA%\Identities\KRAB-DECRYPT.txt4 %APPDATA%\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\#SharedObjects\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\#SharedObjects\YXTRFETG\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\macromedia.com\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\macromedia.com\support\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\KRAB-DECRYPT.txt4 %APPDATA%\Macromedia\KRAB-DECRYPT.txt4 %APPDATA%\Media Center Programs\KRAB-DECRYPT.txt4 %APPDATA%\Microsoft\Access\KRAB-DECRYPT.txt4 %APPDATA%\Microsoft\AddIns\KRAB-DECRYPT.txt4 %APPDATA%\Microsoft\Credentials\KRAB-DECRYPT.txt4 %APPDATA%\Microsoft\Crypto\KRAB-DECRYPT.txt4 %APPDATA%\Microsoft\Crypto\RSA\KRAB-DECRYPT.txt4
*See JSON for more IOCs
File Hashes 011d8dcf09e7c54b212d4037f7a71ac101b38af87f59587527924ab7262fba410c9a8168c677c7d0f142bf2fb40911129fba345b6f2cc987e330200270b26e8c0e24bd59a7468274a57a681b6b864591747db3af0ee1c00e24e61516b57ecc57198f1ff97b3eeb1f167b6a620173f3f3dae13b2d25a9cfd4378f19904df076822c6f1952bf690b431ab3d7fb0c5e09e9d3fb23d4d77d987c12ca2b5827ef20bb3dddef51b9ae680dcd1a2bb65f7c1d0a012d16bae4b34fcbc734687d29818bde458c95a42deef0f5e7607899260126cf4b3c775200e9da6bad210f185d2cbff583af4f8b7564e214be08bb6565bb8639a351798be2ea899ac8d7587ece452e538f4ee5d0479a95e21085b79b27bf715e6e1a713284143945da888cfb7db34354993bf34450e99ae94dc4ab207f94b5a76d9d58d5409e8c3b33997d8101ead59e9a63c28232e75a2f33f12a67fcfc36b066629e969bbfc8c62a9d8fdd1228ee9cb5cbe9afa4667aec874360e40ed65629e454eb3d855dc0830b6a3b8f3ba36a4dd5a91ecaaa28f02c643345715e70fda018185cd6e263532b35054425d63ac790f4c8798bbc75092d7f4ef15f8c03c332e3c3b573e47c206a8805b5f2350abda3f7ed8a78e183bf47923b494c986ad97492a7af97cb6bd8cb4f42ab009052819effa35debf7c75fa5edbca2a5bec9cee472fe56c376d94c30e6bb7f4ac6c9c353
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TrickBot-9987411-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Mutexes Occurrences 426013762421440353595 159750485837088189094 2155379974398186253 371915662916028946102 325172455711402305382 45093008825631982552 65878208027747857992 40128409825132371251 108184562532608296941 24563602132736121781
Domain Names contacted by malware. Does not indicate maliciousness Occurrences elosadywo[.]pl5 inydufevi[.]pl4 utesoryzy[.]pl3 oloqucovu[.]pl2 ikurumona[.]pl2 upikemugo[.]pl2 ikymucucy[.]pl2 uzawabono[.]pl1 upuhisadi[.]pl1 ufyjelefe[.]pl1
File Hashes 01987037a00d02cef3050228a5c851e241c6aa9ec931e109756bc999dcf1c88f0c2dd463bf50ddbabc71dc084848ce95f78972c0600aa26bed751e5bef18057e12a376757c742e6f94031b9286e9b4c0025092a65bdc0f0a15cc6125e66eee351932391e0efe4f06e8de343cbfb922accd4a9f2e0e4cba9c83621471713dc34f1943fa2ca5fd556d27f0b571e41e0447f3dec7e9991375590133315ddcc2d7f61b9263870412c0947f709b1045f9e8fa21afd08c6444536ae261408ffbb1c0461c6caf1c53dde8437efbc6efa952215dcd30e33065a0a8156a3c38435af4c3a828d76e4d23fcf2f994cbda0cc2bcee9208af9eb9cc7cefb4b737574ae12eb14d2f1348fc757fe991abbcde8dfedde245bffb06270a4dd52aa210447c3b827916423c4ec707ea2743fcecacd8d08826c1a885a9d1fdeae3e424bdefea426b97c352aab1fe985479e1fc98d520caa011f977ae858605cd532de95730cde39760d259756273791a7fcc28951ffbb252c5e8206487ebc1d3975f7fe1c12da5f2226c5adc95e24e7a2d0cfad0fe91a94ab3ab63e3749348b8bbf5c278db267efe8b765f2c6c223db3cec8c103bbdee1321c2ff4301652ff51cf9524d91e4f7864a7d26477fa75e074c14bd33376825a9fe7f59f8e7a923828e418823769885a4f6ca86d48bb5316929dff81f3b0280a242dce971c0861cb47ba9ad3e0049025652e0b71656bab86e7c96d3f293a9b0a4b5e2b6d87c454796d070760383f14d2d92c8174094e2772540474f893ad07860f49cc618fee75ec8e275bdc6332ac2c1a3ced82b638848df5e8f1ae07a0fda4dbe376cad1bbadaef1473742a98919e741696d89c72fd3a0ad686e8277a2cc74d3ae885dbc97cafef1bb0f7560f182df098d908a6ea1a10a9ce26e7a30729c5a60cb29edbce32fa39bc8984ccbb33281688725950970aeedb226f0e03d1d85966d52138f482d3500fda7c0216034304acd67d89733d44e41600aea32ec42c44016c9d3abc50973ffe7f7f8d281e7f6a13d65bd9b2f63670a1e5724b69a25d6de99250636f453fe46823c6766a7dfa7ea2625b9a5c2f8d2e689be5b36e6e34223323965eb8d832217af5c5f93a8bfb3c24a35f2
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
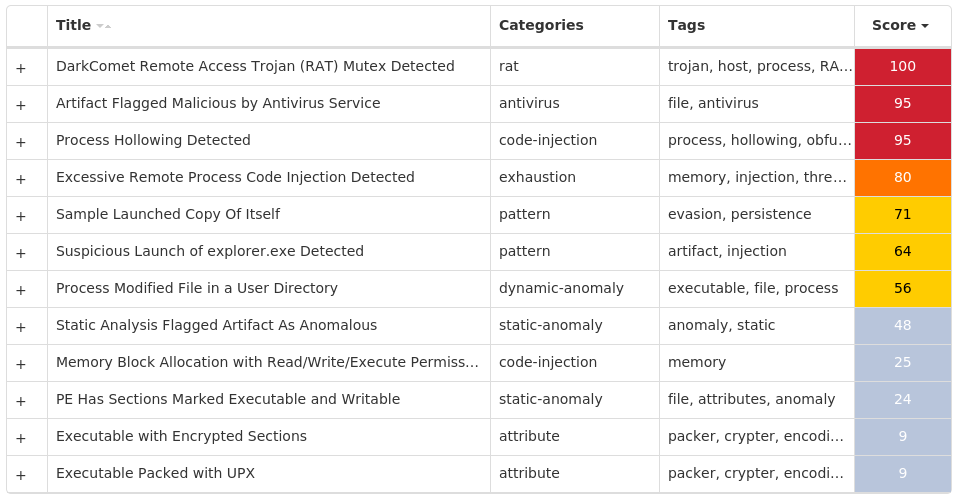
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkComet-9987724-1 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples Registry Keys Occurrences <HKCU>\SOFTWARE\REMOTE Value Name: NewIdentification 24 <HKCU>\SOFTWARE\REMOTE Value Name: NewGroup 24 <HKCU>\SOFTWARE\REMOTE24 <HKCU>\SOFTWARE\REMOTE Value Name: FirstExecution 24
Mutexes Occurrences Administrator524 xXx_key_xXx24 PFS7NJ0GG650A324 Global\62c608e1-84fc-11ed-9660-001517a057b61 Global\19563541-ab9e-11ed-9660-001517d2a55d1 Global\19d95f61-ab9e-11ed-9660-001517a99db11 Global\1a63ada1-ab9e-11ed-9660-0015172fcdb51
Files and or directories created Occurrences %TEMP%\Administrator724 %TEMP%\Administrator824 %TEMP%\Administrator2.txt24 %APPDATA%\98B68E3C24 %APPDATA%\98B68E3C\ak.tmp24 \default.html24
File Hashes 00dd7043f8f736d307e8d432dc4d53e169a0d01bbaf18c8e9c26d3d702b5b90105cf1d6e467dcacb7a8426d686aad3e467bebf56f14094a730acda703f6a81100870345c9baf599cafbdbf6c178af59bb84ca29132be8f25a99b631a5812f2c00f00ea2de2b3fbd975b0bf81b93ac892a32b9b38505ca7934975824994de5bfa17358278cec9baf2cc39db83075199b08f063744cdbc368503e0d9f480599c6f23b2a05f66fe4463b4a9b247e2553b3ab3e457d7692bcda4ef80b451a807cec72f21b95df665d9a895eb142d540ec232775dae8ca6d3fff982110eafd98a276d31106ecb5d2fc5a71e523638369efe1f98ce94d1e972d6f21a2eac30f248756a387edb31d8fbb1478a702773203645ad00d423444a7ce2213b693a35bffa1db85114f0e28f24ae8b78e9b7f1bc8a7275b8c5df906bfa5051c82cc58ef0560e1951b176c359d6ccd836ba35283c65b1936f45d79ea410ea877cfc88478192ed745f97bd4dd258cc40c67b0ee332ec1404bd4a42574b1f263f417a9bae926200f66c1219e68eeb403bbca8f012f3add1a65e0a8e3657436e69adf731d0f86171996fc939a835debb66a1718a11701631bdc8485cf8481bc031a1533a566fea0df1741bec34feb048eb37de1cd12cb70ed1d18e3aaa18af112538976d04fcc183ad745d2dbca92dfbb840b1cbd69f71bf25248012838f1e586968ba3bfac95701417f4676305a5cc0968444f30f1cdbfa04aed721176db2d20401fffb7c596c330284644a768c0ee235e16fd5a58e022b22a620c2e88b0b1f983ae72aa8e469a0bf88e478cbdf1cf481bd1b16daed1efde0eb243e144b0cf72cd27c20349dc82a9389b43b0ba7a914bd0c9f14f2db38aa24a221252b9f4d53600affca3986b3c88c993f856b5f28b0d05087f2d109dbf575f8fc9e9604496deb833b2af8bdc913a69f46a0aa254284347749d901fd9ca394bdbe7c9a14db990e493ed74f3b064445a75a74d8013f9efed45a98a3d5b2fb21f3e0f381240582ec398270a1562e3a46ab6a6f36256049b826b5034e820f8f160f19ddcbbacb32421dcf88f07f23a406b1f8c81db53ca15ca183f93dab27fae3d8ffa4ecebc1edd9944abcb1cd9ae25a
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
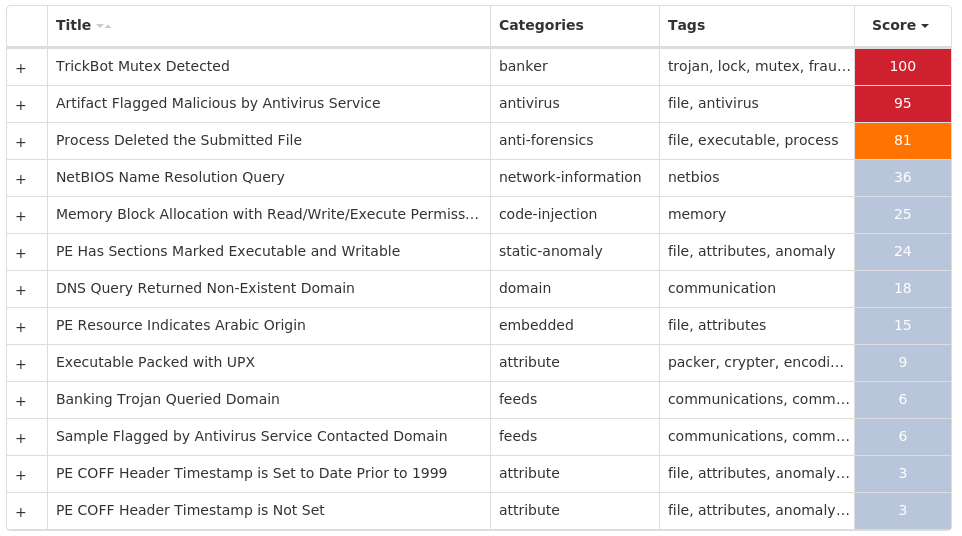
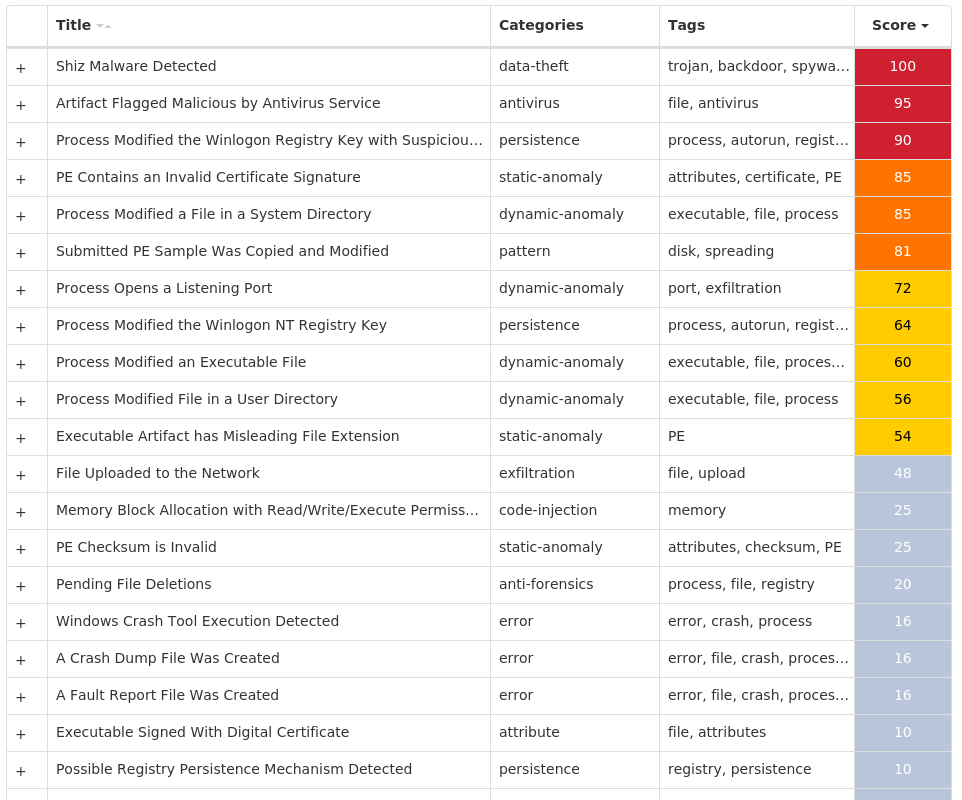
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Shiz-9987720-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 16 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 16
Mutexes Occurrences Global\<random guid>17 674972E3a16
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]195[.]211[.]9816 13[.]107[.]21[.]20012
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com16 bloodguiltiness[.]com16
Files and or directories created Occurrences %SystemRoot%\apppatch\svchost.exe16
File Hashes 0c2997425536269afe16a8b8b6c4be49f7e580897cad9e754ca4f381adb26bae14bccab22d068b3f5b4938b0559f808b13b393490948f21c14952d6b68238eec1ebc5c21db31eda328cce469c9c056a352d1ab6fcaa825b7deaf56bf05b0b8321f1f395ecb32379dbb2184c475f2cb12e8ad9850830f16892283f68886def8423e9ab9a9d9908138887813e35ad0e3f5939b4fd2b63500928e47b6f708f0d7c360991b4ce81c27bdf0b89e5856c2a22c662f34ad7b67f27ef14e64eef4d27e489b52e5276250652efa36ff6a4ee5212ffa7a7220db6f44ca1be7fed689b9eb869b8a1b42707e3cf61bc5167c45287c231c15f05d21c781512ba7a42418fa663eae0e6672faa1fed222b66f2f28e5a84bdfc6eb2b870e12d1017bdb31b8bda566ae70ed3cc01b0631a382136060c3085407e98e09205ed786b9fee5e5a20a139db49e6e226ecfbe22f5e14f8581e5fbdf82e0660b31aac0d91a59252100f535e6c4211dcd759802490cf3295c434c6f406f65c3b4b4e53292e1daaaaa5cf13d0ecb1505686cf31cdd0ff71e5c3dc3875f7e3f90166996dbaf04956f39bb7fbb40ce6e4769ebfda72940dc984db39956ef6f1f0becdd076262f4181a29f7591b54d27abb5761c73a05e6d2e729fc5a39f0de881d44e81465a2e5742ee251a61386d2a13fc8ea13355725e0db940203aaf57acc059464735950345defc4140ff4d0f7e62e5bcc96a9820b674ef0134222e0050acb2035b8f8260e84b6afcc6e643d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Zbot-9987774-0 Indicators of Compromise IOCs collected from dynamic analysis of 90 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\STARTPAGE Value Name: StartMenu_Balloon_Time 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 77[.]68[.]74[.]18990 54[.]235[.]219[.]18688 23[.]221[.]227[.]17240 23[.]221[.]227[.]16539 23[.]221[.]227[.]1698 23[.]3[.]13[.]1522 23[.]3[.]13[.]1291
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com90 steve[.]dxstorm[.]com90 benefitanswers[.]co[.]uk90
Files and or directories created Occurrences %TEMP%\pdflauncher.exe90
File Hashes 0134f50d273b3bbfc40f69b037ceeb8c4a0f9c57ef55e14cc564b2647c91d50b0308c618d462657e6fa1ab1566ea439fe7bc8fa175e00c3b3cb92b7de0a15fad0339ade6fc92c17d85d0a3063e1090d1d88f3e7013c63f962ac238ca6a5be0f203dd7a9a03627752acd6276135953f4e23a567211cda122055fe945ac058547e04049bf401f386b71c3f9370076fa0388ef36317379bd27a3d77521f319ef66c05a90746447511e32622f90440082d5ea344c81f408f2a8180a1a62554f4e56306b5d0d4827be79fc4eb1f518ad2f64cb8011c878172e0f44f9563b7233060be072854dbde422a9f17539752183436f9df9e13cd508e0705adf0a2fedd4b01c6079bb9784c275de6cec815b7fd8fc1ad35ce0cbaabbb5108ebf741fcfd02c00808db7034fce7c18a40454d7d3371739a5a27b324f07a3a84ece5daec32d1b78e094128fb2e38e2feff3360d922c08340c5ab51f4e5941d4b2e5e4e136886da4009cb932db632c40a5da9d5b50bac23d3aaa68a69bfaefdd6f9763d61ede0c3430afe581c70113703a47f4a4a320025d8c42287f3d2b0f50294417e1105d4265b0b66628a42bf861e41ac999ecef8edd7e200cbea9127c0eb6b3c1b94894a9cfe0b66ff19dded846c3ac661dda9a53af6fbc4f87164d160de4077164992152a650ca014f86962ffa520a1761912131c403e38f512ea37dae6d6ad669c9c5a3e6d0e8761857683220f2f36a62feb8ed9912a555bbcfbca1e38edb201ca1cd915610f04fc60a33db62f9f2683efeb0f13701cb2847fe33b15391fb10381624812430fc67b499b0d5c5a42183bcdfb947fe44e3684597844f75e9d88bd9a9b3630d91014177749ae458c7ac423564a0eda01319c5b68ea6b6c1c177e600a10d822eb101ddaf72d55116c5f72c5d5226f7aa8e7d7814c7cf28503e97a6eaf9e8e22f7106e36ed4efd530cadc507496a32ba2fbb3f40e6e6a860128c38dec4cb56767e11df0c2317b792d8e2c71e51cba375f26fa79c3893dee13bc5b3948b173cc12812d34ae371b5b947943eb4feb650c8e8549e74f3d17a178bbdc9e129ff555f76134cbcb9d9f7d69f3121eeeb8e6fd0b69075ec5755d34b1bb84506507c2fa804
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Upatre-9987791-0 Indicators of Compromise IOCs collected from dynamic analysis of 29 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 28
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 101[.]53[.]147[.]2628 23[.]221[.]227[.]16516 23[.]221[.]227[.]1729 23[.]221[.]227[.]1692 23[.]3[.]13[.]1521
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com28 tuhostingprofesional[.]net28 anuudyog[.]com28
Files and or directories created Occurrences %TEMP%\supdater.exe28
File Hashes 010243c7767a6b837801673fec5f7e2633a0e11c879cfeefb2bd4db175a7816a02ee375ae0dccec565db9e27ba3b24718760cdacd85b8cd74ed6102325114c6505d00dd79e4213b8aa6f2d89e84fd9e183bf900d39d36ab2f013ab67f8291be3060023bf7c5d1145bb08fffbc448274c20dd80c85a80e57f0df823e9f3c79c8a067258b2e61211b48cda093ec5472e6fc9af69126cd9df35d1a07694f5c24ffb089ab142bc7f8da4183552f2171a6c286cd794238cdb24c5ea1518fd45aa33670c726ff73b0d2611da857e263fad49b26526fec7f94843a1f1f524e0d48dc7530c8737ef332da6de9b470248f936c9aa177d4fd2aba7ffc8c9ed47fda93d7bdd1156286e6dbd4cfb3f9c4aa84d4eef23440bfb8e2f21b07f6f5354590a1c3f7216f0667362c8c5dd9335987ab41c24b92036945c9d1c0ddea04d90948516cb2217641c06747629a7720673f5dd039f5bf7df239ae1f8958ed3dc2f7705226d0c1855312928b2aa88ad5ac89ba51a862d4b2de4eeb33a0ae886e5e1966e780aae1c15b4eaf47ca47b54bd28bc9b153a8ede290944494061ba2bb5b8c85469d4b01d0578ae82bfd0fa95e9ed545cf5ed279950afd7a9d781b56b2da199644f94c51e26e6342757fc44a0481be553a7da9cfc7e7bee74f8d047ecdd3db48099cb8e1e854f3b2e5ac899a6b7af69222158dc863dbb6df3e772de4370fb9760d81420212e75aa87694683016e93419f5cbc8780ac745fdc1042bd386eeda4062cc24923c32f21fc7ec2b52e8c7ac55e5d1e3dacdacc436d5ee85f8ab9720f027aaf8d23ebe4536966753f6bbab01b39ffccb11c53be2e165511457945bd27b037aba124db56ac2049c9a8301b1da437ba4b444ffca88c878aba8edd742ef011768ccd24dca6c92172a2f6c6fd58cfdba88b1a6aa0be1ce57fc0675d5ca0da8df65a5325092b994541d8745e19da88f5a4a0fe4f11aa56eac0f3d8dc61d63c1add3556256e5aaff5776ae40c7e6125768229deb6b17682d6bd92985bc22f7c917e24c625e9b2184b29eb5da0c534c675bee126c09ddccd01f1c653612b6fb07342d7322784a7512e3c82f8525f358ea544fc613f7d47fc421004e0803dc1dd1e35d2d6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK