Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Feb. 17 and Feb. 24. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats are subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post.
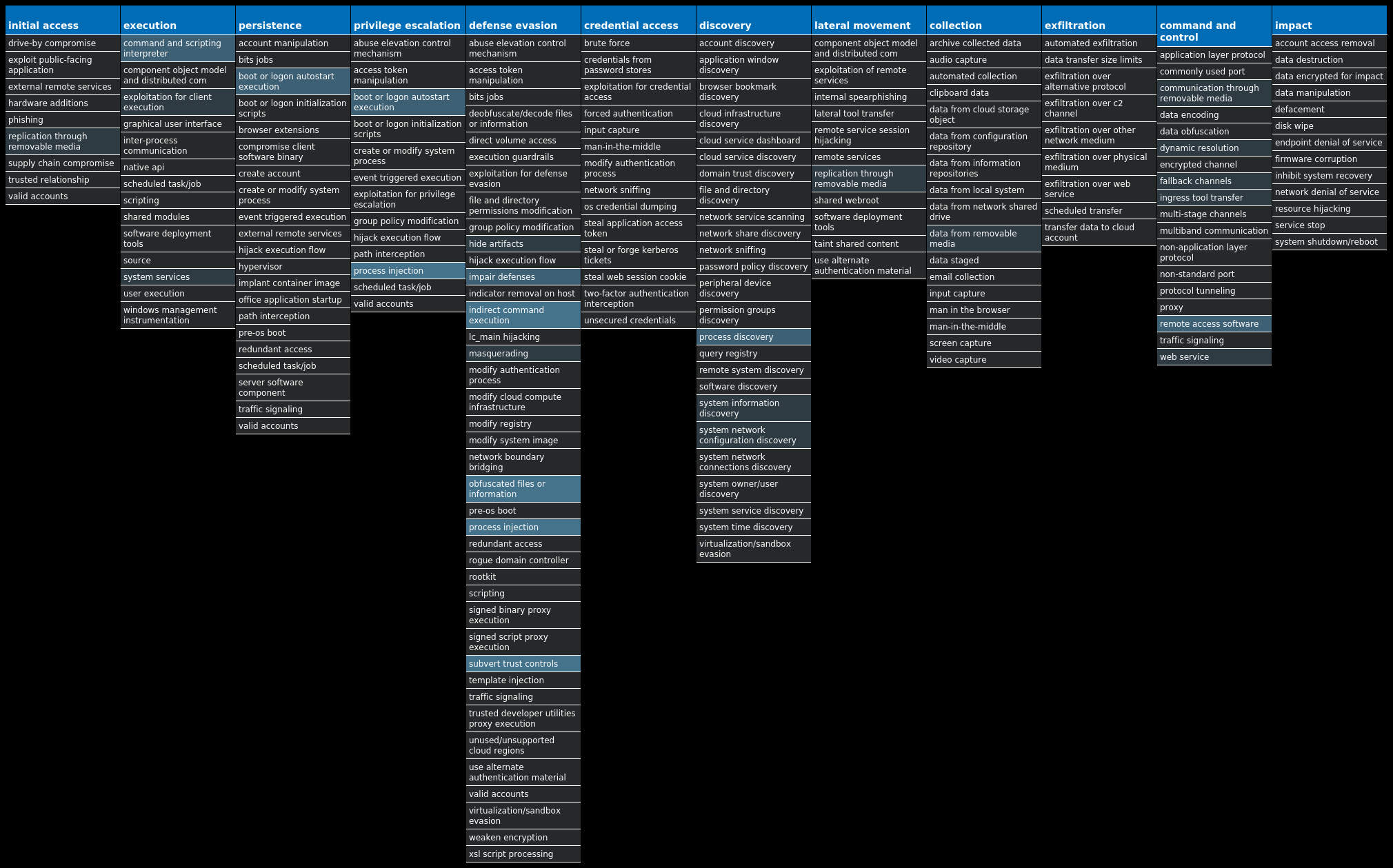
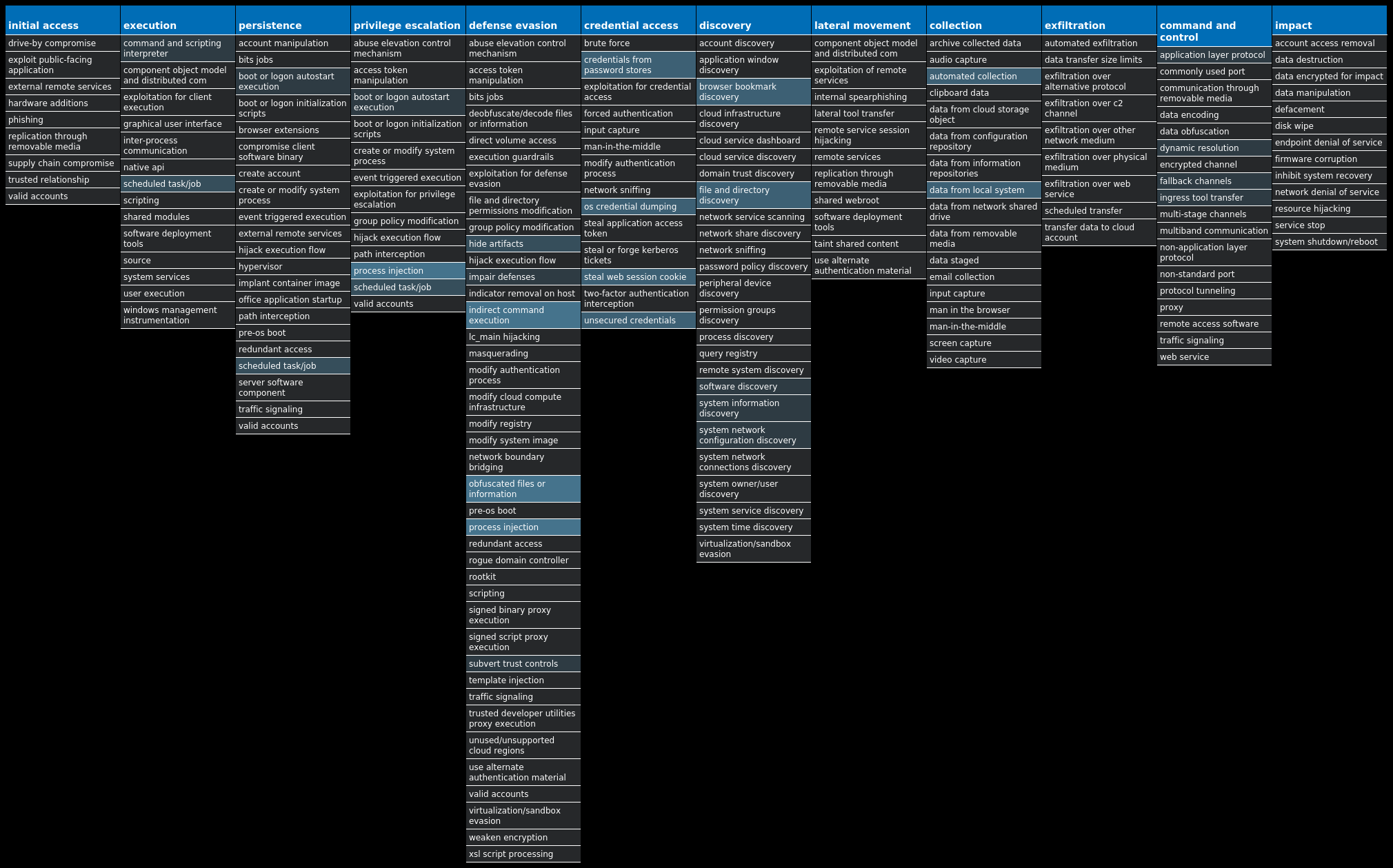
A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
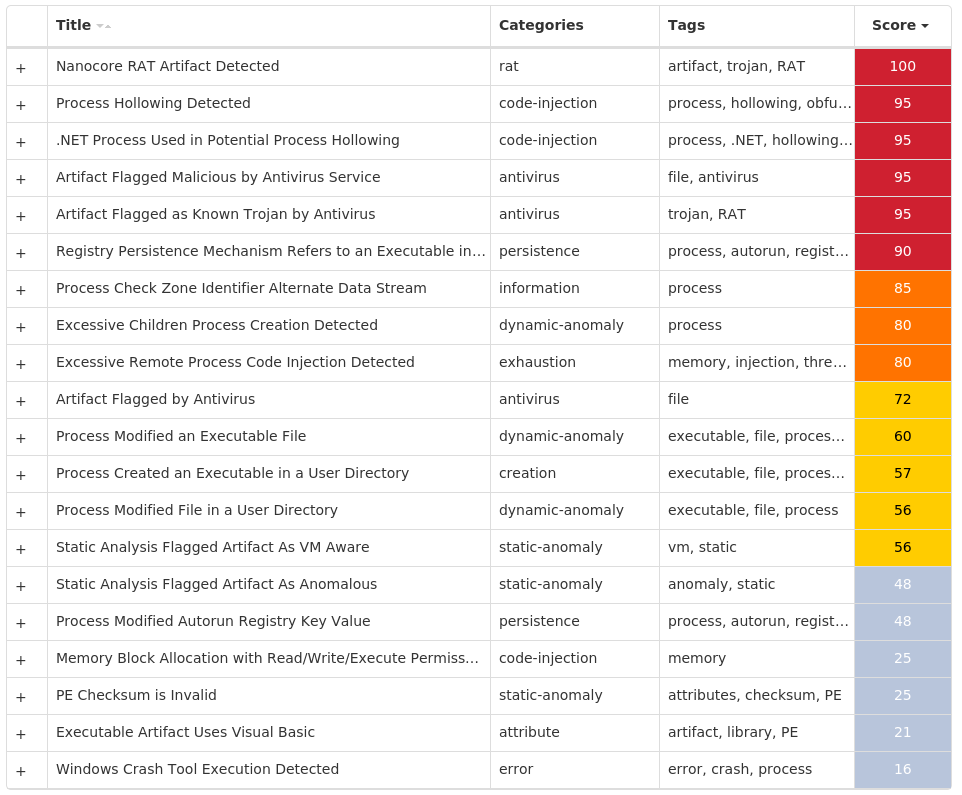
Threat Name Type Description Win.Ransomware.Locky-9988336-0 Ransomware Locky is ransomware typically distributed via spam emails containing a maliciously crafted Microsoft Word document crafted to trick targets into enabling malicious macros. This family was originally released in 2016 and updated over the years with additional functionality. Win.Dropper.njRAT-9988317-0 Dropper njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014. Win.Dropper.Raccoon-9988310-0 Dropper Raccoon is an information-stealer written in C++. It collects system information and a list of installed applications, then steals cookies and autofill form details from various browsers (Chrome, Internet Explorer, Firefox, etc.). The malware can also steal credentials from email clients like Outlook, Thunderbird and Foxmail, then scan the infected device for information about valid cryptocurrency wallets. Win.Dropper.Nanocore-9988136-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.Zeus-9988134-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Ransomware.Cerber-9988129-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Trojan.Qakbot-9988002-1 Trojan Qakbot, aka Qbot, has been around since at least 2008. Qbot primarily targets sensitive information like banking credentials but can also steal FTP credentials and spread across a network using SMB. Win.Dropper.Formbook-9987985-0 Dropper Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
Threat Breakdown Win.Ransomware.Locky-9988336-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 5 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 5 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS\DIAG\VSSAPIPUBLISHER5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: sessionstore.exe 1 <HKCU>\SOFTWARE\MICROSOFT\GUTID1 <HKCU>\SOFTWARE\MICROSOFT\KEMOA1 <HKCU>\SOFTWARE\MICROSOFT\IPCAEM1 <HKCU>\SOFTWARE\MICROSOFT\F12 Value Name: Izys 1 <HKCU>\SOFTWARE\{A3AF5C44-B74E-41D5-A87A-4A043A1FB0EC}1 <HKCU>\SOFTWARE\{A3AF5C44-B74E-41D5-A87A-4A043A1FB0EC} Value Name: temp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: How To Recover Encrypted Files 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Scanner 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 9adf00c647589ae33d841040666e28987e5a88aaf1f08e20a33bfb0c89280380.exe 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 5feca7d20b950f2b4a4498ae29a0b4abcdaa38e8e4da4cf1dc2786683ec2526c.exe 1
Mutexes Occurrences Global\4aEa7aGa9a4aBa6a4a4aBa1a5a8a4a1a5 Local\4aEa7aGa9a4aBa6a4a4aBa1a5a8a4a1a5 Global\syncronize_122STP2 Frz_State1 Sandboxie_SingleInstanceMutex_Control1 MicrosoftVirtualPC7UserServiceMakeSureWe'reTheOnlyOneMutex1 <32 random hex characters>1 Global\c7eef521-b0de-11ed-9660-0015179b4e341 {a3af5c44-b74e-41d5-a87a-4a043a1fb0ec}1 {84310dce-64d5-490d-9ae5-016108d66b7e}1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]31[.]59[.]55 13[.]107[.]21[.]2003
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com5 abrakadabra2017[.]com1 oowerl[.]com1
Files and or directories created Occurrences %ProgramData%\Mozilla\logs\maintenanceservice-install.log5 %ProgramData%\Sun\Java\Java Update\jaureglist.xml5 %ProgramData%\Microsoft\RAC\StateData\RacMetaData.dat5 %ProgramData%\Adobe\Updater6\AdobeESDGlobalApps.xml5 %ProgramData%\Microsoft\IlsCache\ilrcache.xml5 %ProgramData%\Microsoft\IlsCache\imcrcache.xml5 %ProgramData%\Microsoft\User Account Pictures\admin.dat5 %HOMEPATH%\DesktopOSIRIS.bmp5 %HOMEPATH%\DesktopOSIRIS.htm5 \MSOCache\All Users\{90140000-0016-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-0016-0409-0000-0000000FF1CE}-C\0PZW70DW--Z15 \MSOCache\All Users\{90140000-0018-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-0018-0409-0000-0000000FF1CE}-C\0PZW70DW--Z10I--E5 \MSOCache\All Users\{90140000-0019-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-0019-0409-0000-0000000FF1CE}-C\0PZW70DW--Z10I--5 \MSOCache\All Users\{90140000-001A-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-001A-0409-0000-0000000FF1CE}-C\0PZW70DW--Z10I5 \MSOCache\All Users\{90140000-001B-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-001B-0409-0000-0000000FF1CE}-C\0PZW70DW--Z5 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\0PZW70DW-5 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\0PZW70DW--Z15 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.en\0PZW70DW-5 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.es\0PZW70DW-5 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.fr\0PZW70DW-5 \MSOCache\All Users\{90140000-0044-0409-0000-0000000FF1CE}-C\0PZW70DW-5
*See JSON for more IOCs
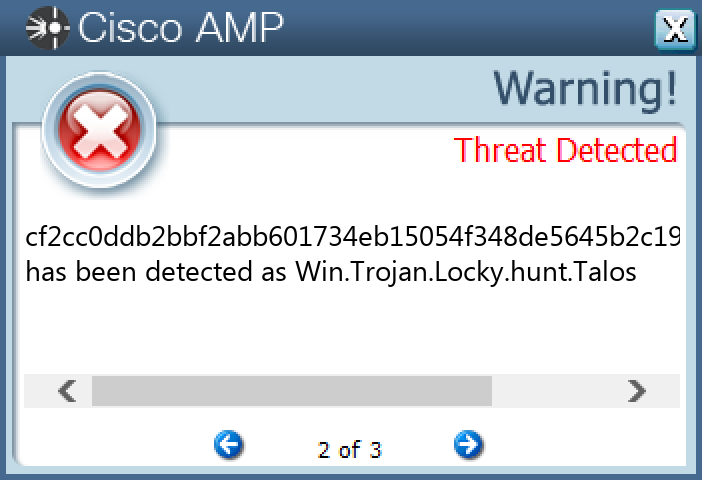
File Hashes 1d42deb34a41e503493a62da4c0c1e1fbc1ccd69613bb4f2776160eeaeb5e20330e8996a0f3b1ac41421482cda2a382729d335b4693a32667e6994b3157842ba395f1d3b183d2f200dd4c17fc07730eefdbeff0e30074b45adf7ab9ac010baf45feca7d20b950f2b4a4498ae29a0b4abcdaa38e8e4da4cf1dc2786683ec2526c7a72cc00144801b4d6efcdb2dfc87152fbbf63b95b75207e164c174deb31a82991bd44f78e8049943ee0f1515d1de58e8823c6bbf65687cb0ba92f2202010efd9adf00c647589ae33d841040666e28987e5a88aaf1f08e20a33bfb0c89280380c01daa19a50388dffaafaff71046b71afc896082c187775e1d43937b3b5858e6cf2cc0ddb2bbf2abb601734eb15054f348de5645b2c192fbc8906bc4dffceb11f556cd21035c1a5790ee917894525c8b7f48463c03f862da09e435f7c193b223ff0327525f5459163cd7b2a4795067e4fa74858c7bd0799909226239c96cdc5b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
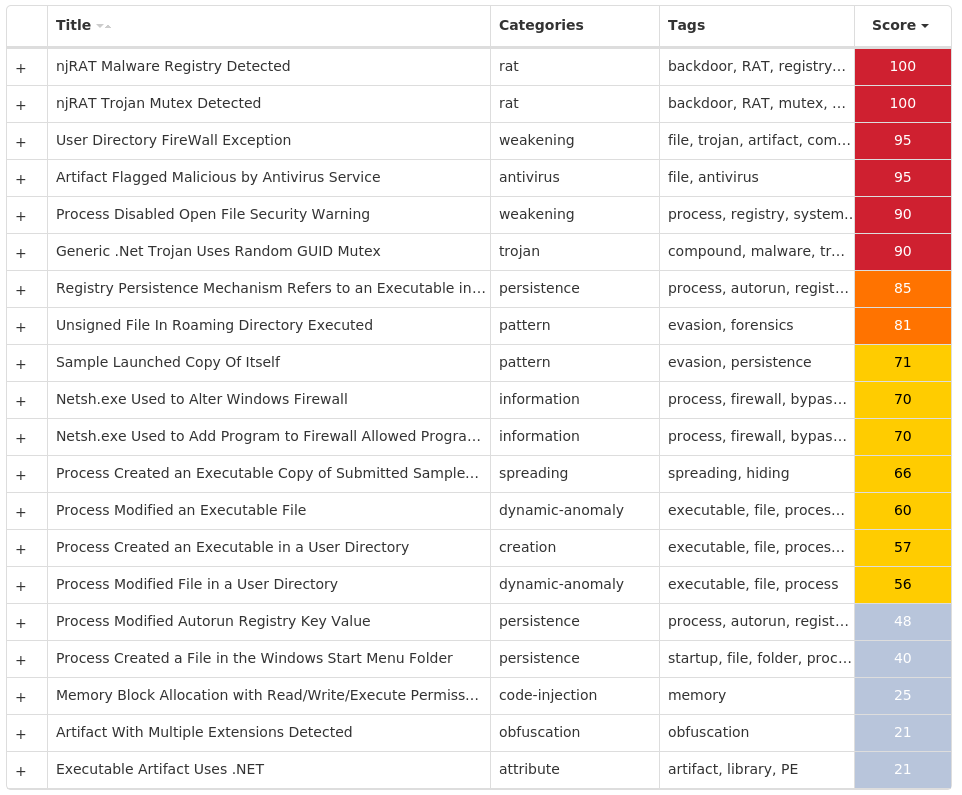
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.njRAT-9988317-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\ENVIRONMENT Value Name: SEE_MASK_NOZONECHECKS 9 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 2814667a3ff5b067280784d8be595983 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 2814667a3ff5b067280784d8be595983 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 8515eb34d8f9de5af815466e9715b3e5 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 8515eb34d8f9de5af815466e9715b3e5 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 93f19dda2412c86ad7520ba4198f39a0 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 93f19dda2412c86ad7520ba4198f39a0 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 301b5fcf8ce2fab8868e80b6c1f912fe 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 301b5fcf8ce2fab8868e80b6c1f912fe 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 3fc0f2282a8aad20e9973738d93f539b 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 3fc0f2282a8aad20e9973738d93f539b 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bb62e28591030e826081bf1f4a74c0b8 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bb62e28591030e826081bf1f4a74c0b8 1
Mutexes Occurrences <32 random hex characters>9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 189[.]51[.]21[.]221 200[.]153[.]144[.]1191
Domain Names contacted by malware. Does not indicate maliciousness Occurrences manatwork[.]no-ip[.]biz2 system-32[.]ddns[.]net1 lukkzhacker[.]duckdns[.]org1 bloodhacking[.]duckdns[.]org1 s3apika[.]freedynamicdns[.]org1 hackedlogoutz[.]duckdns[.]org1
Files and or directories created Occurrences %TEMP%\WindowsUpdate.exe.tmp2 %TEMP%\WindowsUpdate.exe2 %APPDATA%\explorer.exe1 %TEMP%\System.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\93f19dda2412c86ad7520ba4198f39a0.exe1 %APPDATA%\explorer.exe.tmp1 %TEMP%\dllhost.exe1 %APPDATA%\Trojan.exe.tmp1 %APPDATA%\Trojan.exe1 %TEMP%\System.exe.tmp1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\301b5fcf8ce2fab8868e80b6c1f912fe.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\8515eb34d8f9de5af815466e9715b3e5.exe1 %TEMP%\javaupdate.exe.tmp1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\3fc0f2282a8aad20e9973738d93f539b.exe1 %TEMP%\javaupdate.exe1 \TEMP\5eaa9f5769a034d4f29a1d0d10654a04cbc046a43c48a52c0bae0e531d98cfe4.exe.tmp1 %TEMP%\dllhost.exe.tmp1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\bb62e28591030e826081bf1f4a74c0b8.exe1 \TEMP\0decb4d54983bae4fe244fd05f37c44552dd41026ce2f7476e324d0d70528a20.exe.tmp1
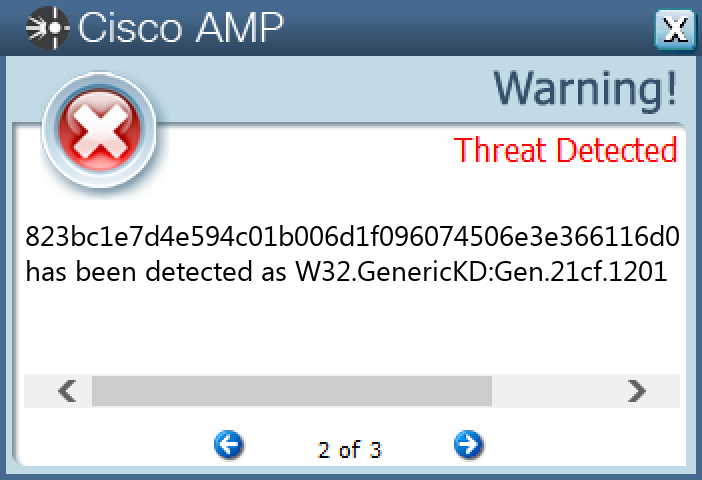
File Hashes 0decb4d54983bae4fe244fd05f37c44552dd41026ce2f7476e324d0d70528a2015c45e30b4ab1abfbd74b6e61809f33a103b89d517a2ac71d1e70b88689425aa3404e23a0a617c14889c39f1dac9bd7f8089f297bc080b3b8430146d02f28cbb514cd202222e9177c5e08d530ece79354aeffc92ed317788bdff6e0f6fd51ea95eaa9f5769a034d4f29a1d0d10654a04cbc046a43c48a52c0bae0e531d98cfe46ee0be250617ad76b6e6f63dfa9458ab0b9af4dc54d7900ddf6f7c1918702515784fab75d3d0ec206a77bb05194da023167ea8ae597465dc0ef52b30bb143931823bc1e7d4e594c01b006d1f096074506e3e366116d09d3be30f0dc2919f6570de81b5b06749d5baee35810180069081774764b81f132c03a7fc0b7e3e115675f1ea762519d991b1d3f53db198a886f7f42d9b5cc4d207d61394742e11f447e8
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
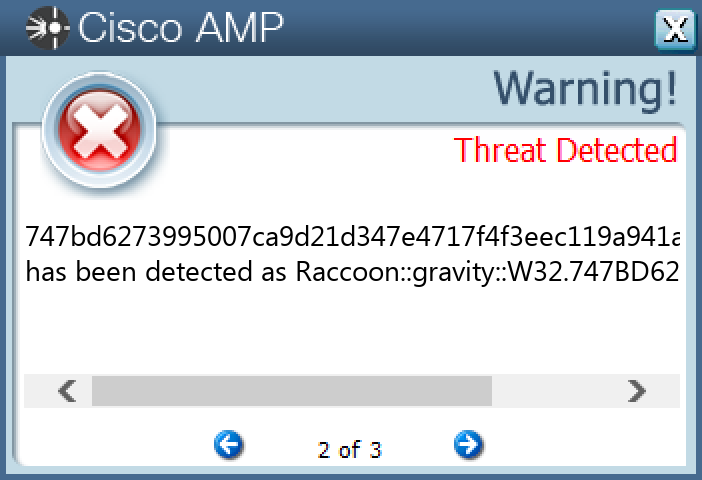
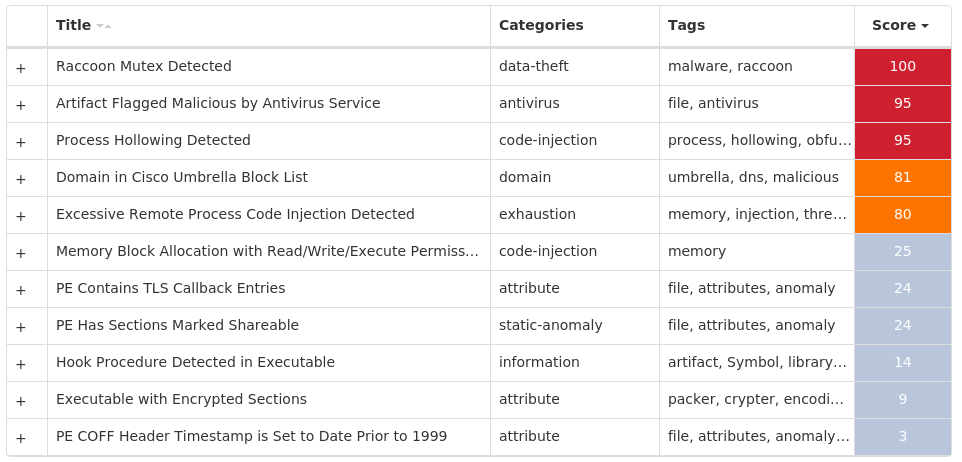
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Raccoon-9988310-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Mutexes Occurrences dfthorbnjAdministrator7 Global\<random guid>6 Asinc325372521
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]20[.]158[.]287
Domain Names contacted by malware. Does not indicate maliciousness Occurrences telete[.]in7 restreamnewsp1ot5s8[.]net1
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\smss.exe1 %ProgramData%\b26ec769d32209b95045aec12985cb3b1 %ProgramData%\d2adf13ee31 %ProgramData%\d2adf13ee3\bdif.exe1 %ProgramData%\d2adf13ee3\bdif.exe:Zone.Identifier1
File Hashes 01f4f01b6853139297b1604d5ebf7e09a2a5a2cf2a68f3f4daa0b321453a1be11d7e2c9f1ff6d0e0fb6e0fd9e27c5fa9017700913fd0ef99d765199e3b8ca63c1fbea8de123b8a8c9af77b9b5b92bdb63b0d19609e8990527378cb81ecf431e936fa1ef7e51ccbfb479295f282dcc041857bc815ffce4a804de9032d32b83f214f260d78edb483d8ba7a142a6f676c5cd557704d51e6685a4b8f4b102b464cf450de5d9e517b3873dce423f23e594132c345421351b422ab0afa102485a4215755d88c61e70034fe1b551101deb3428b95514fd2118dd3436c23f3164a1445b068708df5eec1937caa894bf69c8bc4cad786983059603309efdaa5d3cb32d0f1747bd6273995007ca9d21d347e4717f4f3eec119a941a401a4bc5206929cfa35866c9d84b99d9f3ec9eb5a334bcf09eb97656065d215db720e93ac1c7bce4527924e194f9a48d337a08e955ab59a4d950a345a67cdf82457352f46ac178cf3f29922548baf0ae8ebb1076f7f447843a908065b823478baa1b3863386d276ef619b81b625916ba8cbd0b75319d113463b7ba8792731f7e7ef18119976882018c0cfed04391c70bf143b7a8177719dc643196be2d35aced4753523a6e0468b907ed9bb6a6e6aecb53d126d326d539f0156b041fe13fcd2ec805f5e47c9c5e27f4ee3d9fba192a6ac072a26d8fe01bd46e588b8ac1a1884a9631bf065eda1030c4ee622bfc9c6c1457a6652dd284206d1ae23a06971b2cac1ffabf6ed907b0917be
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
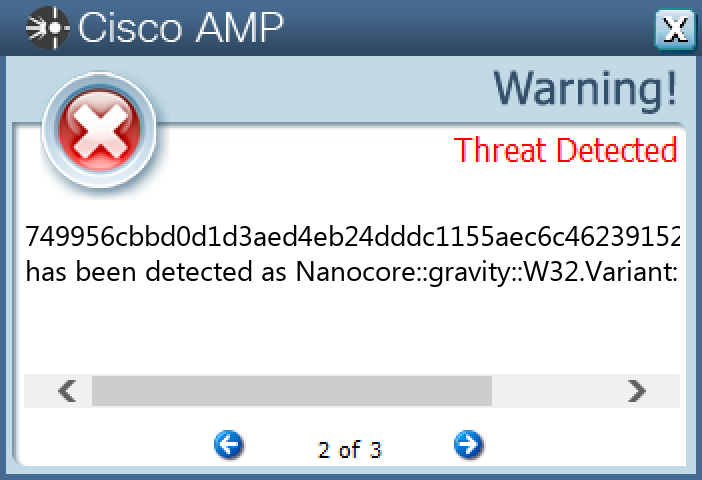
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-9988136-0 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: asd12z371623.exe 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Nvidia.exe 4 <HKCU>\SOFTWARE\ZWCCUKGLY8ABX3 <HKCU>\SOFTWARE\ZWCCUKGLY8ABX Value Name: ServerStarted 3 <HKCU>\SOFTWARE\ZWCCUKGLY8ABX Value Name: InstalledServer 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: asdhub1326t1t63.exe 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 2 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @C:\Windows\system32\DeviceCenter.dll,-2000 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: a659cfc22c71119 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 6888ba0030fb 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 971ae43462ae5e84a7f 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: e325b447a677a64e 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 54d42584b52325841 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 1a3c254271 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 25d466015585a2a 1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D Value Name: 4c8756bdc22d7d231 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSTRUI.EXE1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MYMAILCLIENT1 <HKCU>\SOFTWARE\APPDATALOW\GOOGLE UPDATER1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\BF4A0695A26DA0B1F1 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\55F941A93A30DC521 <HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\{3E0AE736-E36F-7A5F-0575-AB594FE2749A}\0E121E41\C28FB9BA8E7D1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5PQMSRGI-Q85J-60VQ-M4EG-UXW21U57UP7E}1
Mutexes Occurrences Global\{3edaf3de-dd09-4a68-8caf-e4d9870816f3}9 CYBERGATEUPDATE3 ZWcCUkGLY8aBx3 Global\{876508ca-5f42-46b6-bb64-6a0441f8d11b}2 -1 1e1f50f3-e850-4622-90c7-1d7628d20f191 Global\1e9b1fc0-af18-11ed-9660-001517052f721
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]31[.]65[.]1979 38[.]79[.]142[.]663 204[.]16[.]169[.]543 192[.]169[.]69[.]252 104[.]16[.]154[.]361 204[.]11[.]58[.]1891 142[.]250[.]72[.]1101 193[.]122[.]130[.]01 23[.]192[.]63[.]451 23[.]7[.]178[.]1571
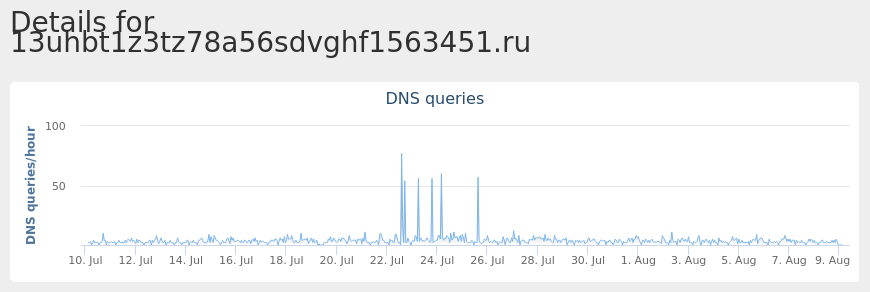
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wins10up[.]16-b[.]it3 sslwin[.]moneyhome[.]biz3 k4l1m3r4[.]publicvm[.]com3 put0carad3verg4[.]strangled[.]net3 clar0dsl[.]serveminecraft[.]net3 peppers[.]duckdns[.]org2 go[.]microsoft[.]com1 www[.]bing[.]com1 whatismyipaddress[.]com1 google[.]com1 checkip[.]dyndns[.]org1 learn[.]microsoft[.]com1 thoka[.]linkpc[.]net1 7163zbh16356ztug13765gv541[.]su1 kazaz[.]no-ip[.]info1 1378137613gbadz13567ds13[.]su1 asdjihnu1z763hubad6tn13[.]su1 hjadzgt613bhu8967rv61563fv[.]su1 mail[.]alonqood[.]com1 1376bad654134c667213[.]online1 137zt67g1635r5bd671563gbzasduzh512[.]online1 13hjkz7513v64541852v65431b5411dxv24[.]su1 13uhbt1z3tz78a56sdvghf1563451[.]ru1 713zgjj2iigbh1766av441bsd67613[.]ru1
Files and or directories created Occurrences %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C511 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs11 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator11 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat11 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\.lock11 %ProgramData%\asd12z3716236 %ProgramData%\asd12z371623\asd12z371623.exe6 %APPDATA%\Nvidia4 %APPDATA%\Nvidia\Nvidia.exe4 %System32%\Tasks\Nvidia3 %APPDATA%\Microsoft\Windows\ZWcCUkGLY8aBx3 %APPDATA%\Microsoft\Windows\ZWcCUkGLY8aBx\ZWcCUkGLY8aBx.dat3 %APPDATA%\Microsoft\Windows\ZWcCUkGLY8aBx\ZWcCUkGLY8aBx.nfo3 %APPDATA%\Microsoft\Windows\ZWcCUkGLY8aBx\ZWcCUkGLY8aBx.svr3 %TEMP%\asdhub1326t1t633 %TEMP%\asdhub1326t1t63\asdhub1326t1t63.exe3 %APPDATA%\pid.txt1 %APPDATA%\pidloc.txt1 %TEMP%\holdermail.txt1 %TEMP%\holderwb.txt1 %ProgramData%\CPU Temp Monitor Service1 %APPDATA%\Install1 %APPDATA%\Install\Host.exe1 %APPDATA%\Imminent1 %APPDATA%\Imminent\Logs1
*See JSON for more IOCs
File Hashes 053a7a87ab88862eaa93cc1ad7d2a6d063f5f4d4ced27d79293fa30e2b01f88606c1e92b9102991eba2779b9369f352b40342e1534ce036156b0ad96bc34d58b3efbe7ca98c370afb81540c589f0f2a9bae8de2f7cf5e0e96956da42aff04c1f40b8a9b13e4ecdf38e805c017af1381779626d2aef6f966bf1b32b5fb7884f3052336dc775740988572f7d158eadc307fdaa72a178dfddaa59523980ef0b97f353806c9d142b44c2d80270df36a34f82aaf5f42a38971ad8ef0a97d55ad43ea058d471afddee8cfdc699d41d67024e1d63b83c038f17c0058722f708485aeffc68ed334c88c0025bf39d643d78a3badf9b3e1d210c942b0db0a45c81ce725ec2749956cbbd0d1d3aed4eb24dddc1155aec6c46239152d536cfe1cbdfe23250bc79ef439dc27f1c73fc3ca890a34897951bc88ae654db07a1f7ccb27134f0a05582e1f7ad19a10760ff9917a9596f8feea2180086b9ade82064ef1a5344b9bb688fec72cbdcb941034a7c0c64052220cde12dc466cf2106304ec77ebd2c7bd2c1a650ed425a9549bd72db33f473722e19de1973131ffe5c92aac98febdcb2ae42c0d689354e7d9fd75932612420be7a3af50f68bfd3cb735553c0fc8e90ec9d6fe14b408bfb28c06b97d8d02899c880dbbf3c0ae966b8fa5e3a2c646dd0d30cb6ea358a82310adff5d0274118dd708c2f9ae94d0149358b91d9a5ca570bda8e56f3d3bf58ba929bfc591edef51a03d4e3ff1799bc9fe61c1c7791e948891866c0f43c85fe614c5115b376d23787a1836cdbdef9923e7132653332331314f5cea5fd4729c13748c27ae23dffdc85b658db358285579a5713c5216f15738d651fbfff40716166e751434afcf5e091af5570bd7db0867789bc3ac2a1fcb9d4157f4d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
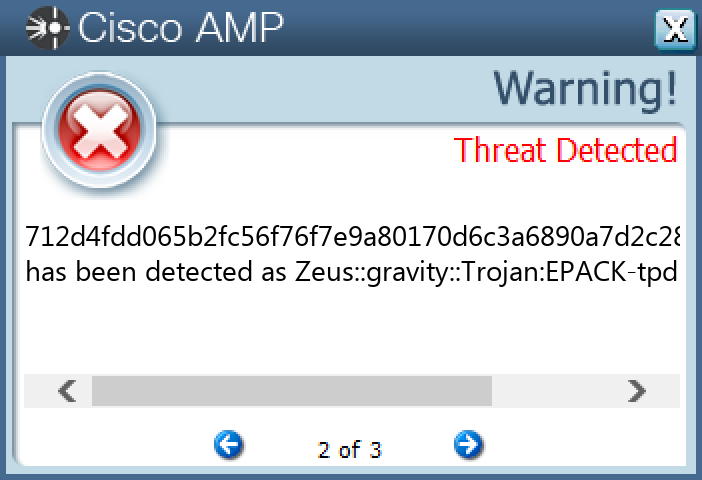
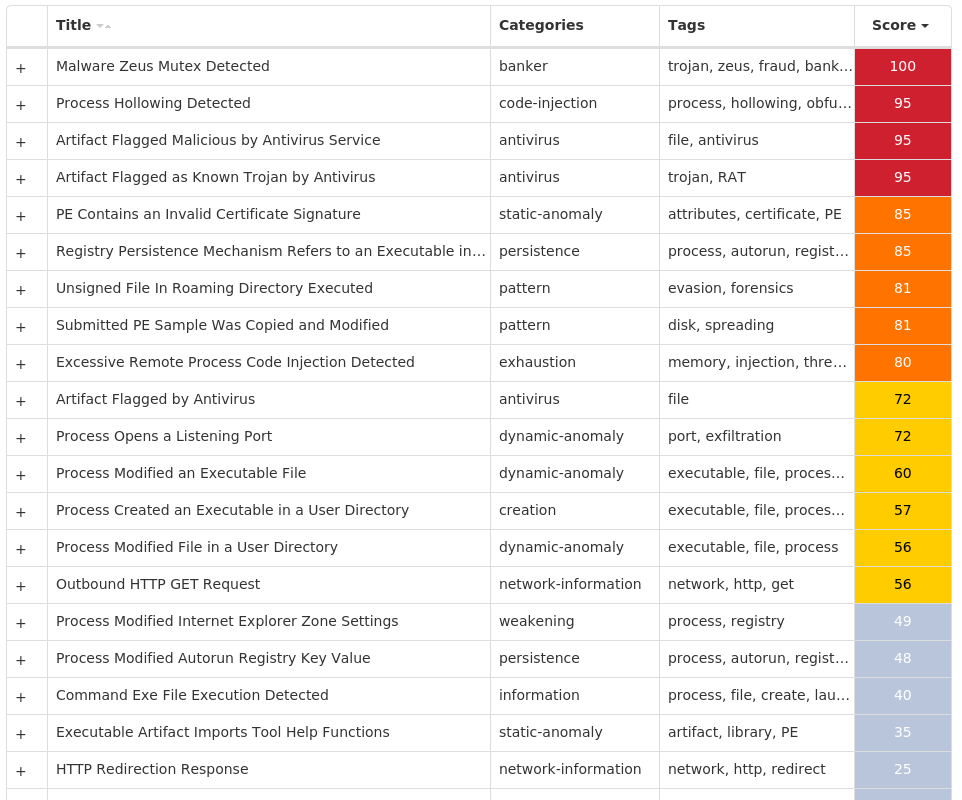
Screenshots of Detection Secure Endpoint Secure Malware Analytics Umbrella MITRE ATT&CK Win.Dropper.Zeus-9988134-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY Value Name: CleanCookies 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 7 <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {A6EB954B-36CE-6D51-9914-7AFC0F4D2293} 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Adobe System Incorporated 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: Microsoft 1 <HKCU>\SOFTWARE\MICROSOFT\GUZUDU Value Name: Vane 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Noawaj 1 <HKCU>\SOFTWARE\MICROSOFT\AKEDUP Value Name: Ofik 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {A321EDBC-895F-504C-36ED-F9F6E3D2B83B} 1 <HKCU>\SOFTWARE\MICROSOFT\PAYXPO Value Name: Cuabo 1 <HKCU>\SOFTWARE\MICROSOFT\ICONF Value Name: Loqy 1 <HKCU>\SOFTWARE\MICROSOFT\OXWU Value Name: Reyfcia 1 <HKCU>\SOFTWARE\MICROSOFT\AHUQ Value Name: Naleebd 1 <HKCU>\SOFTWARE\MICROSOFT\YWZI Value Name: Abixz 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {CA9B4E57-786A-6431-6D2A-F7D19DF1047C} 1
Mutexes Occurrences GLOBAL\{<random GUID>}7 Local\{<random GUID>}7 Local\{40FFE963-4AE6-8B45-9914-7AFC0F4D2293}5 c7312001 SSLOADasdasc0009001 SVCHOST_MUTEX_OBJECT_RELEASED_c0009001 -65b46629Mutex1 FvLQ49IÂÀzLjj6m1 mutex1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]58[.]112[.]1651 204[.]95[.]99[.]2431 34[.]98[.]99[.]301 78[.]135[.]105[.]71 31[.]210[.]72[.]2071
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]wipmania[.]com1 n[.]aoyylwyxd[.]ru1 n[.]ezjhyxxbf[.]ru1 n[.]hmiblgoja[.]ru1 n[.]jntbxduhz[.]ru1 n[.]jupoofsnc[.]ru1 n[.]kvupdstwh[.]ru1 n[.]lotys[.]ru1 n[.]oceardpku[.]ru1 n[.]spgpemwqk[.]ru1 n[.]vbemnggcj[.]ru1 n[.]yqqufklho[.]ru1 n[.]yxntnyrap[.]ru1 n[.]zhgcuntif[.]ru1 n[.]zhjdwkpaz[.]ru1 dogaltas[.]gen[.]tr1 www[.]dogaltas[.]gen[.]tr1 jeonero[.]com1 ismailerdem[.]com1 pongwebdevelop[.]com1 softtechinterviews[.]com1 paperboidope[.]com1 panhandlepros[.]com1 www[.]ismailerdem[.]com1
Files and or directories created Occurrences %APPDATA%\<random, matching '[a-z0-9]{3,7}'>8 %TEMP%\tmp<random, matching '[0-9a-z]{8}'>.bat7 %APPDATA%\<random, matching '[A-Z][a-z]{3,5}\[a-z]{4,6}'>.exe7 \$RECYCLE.BIN.lnk1 \System_Volume_Information.lnk1 \jsdrpAj.exe1 E:\$RECYCLE.BIN.lnk1 E:\System_Volume_Information.lnk1 E:\c7312001 E:\jsdrpAj.exe1 %TEMP%\c7312001 %TEMP%\Adobe1 %TEMP%\Adobe\Reader_sl.exe1 %LOCALAPPDATA%\svchost.exe1 %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Low\svchost.exe1 %APPDATA%\Yxgye\sovak.lec1 %APPDATA%\Gousla\kaun.epa1 %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Low\RCX51FD.tmp1 %APPDATA%\Uktipi\abox.okt1 %APPDATA%\Identities\Noawaj.exe1 %APPDATA%\Cayku\inwa.ivv1 %APPDATA%\Okbaeq\katao.yma1 %APPDATA%\Zaby\iwqa.due1 %APPDATA%\Tufafe\afaw.ukh1
File Hashes 2265ebdb4c1f4bff5b3b9a5ee22c656dc767300a4ed24fe75736920f3a87cfa028e97a0e80445dc2b6bdb7788f46e4725be66a8b6bd10bab9a0e6606a019d2334057a92dba45b12688236bbb8014ee4a6b0691a925d88cec95917aab3585826c4d1624381db7e6ddea26fdcef4599f304b31e1b0f9371abcc0b88ca131e10672509d232f20467648fe65a6e80633089c180a8578d8261f2a855468df181f21bf5b2afd2c68782390c8278ce3d4b66f57145f496c357add2b05bc5a54753456c7712d4fdd065b2fc56f76f7e9a80170d6c3a6890a7d2c2832fdad4e702eebd3f97bcec64384ba0f9c98c37dfe34aeb7a7e02d8274fb2a8c0dcf9f57a071ad749b8f396d7e2c9c39daf77269d2fc0c09c5e060dc6dcbd2e7c975edf0543dd831b2a30109e6257dcd2061f8b97048fb0857ffdc6ebd6aa182e7fab7fc991902ffa6a42ff67a87835c92866d6b6eb5be36eee73a38f2ec27e87e27f42f927f67c4e6a47fdaf0f8175a8987ee5f252116b29d92300fc27283d06c96da0e16a50500a7c99e88c7586e9387df13aa382de006760e6afa2c2e28450b4d4167e85c309fc2d1580f128d8482e61a2ffc369295047fc95f021f94e9254bd91d3e45e99402c1f0352da956db605dff874e2012a2cd7d1c8f5243113364d6573bdfd6a5b66cbdf7a26b708b437c1bacddbb219429f2080966fbe5c1e15215c75faa7ec659809af9a9251d8bb3367ddd526c4ede83e85131a746427dd0e4cbc91d911ded6dae14
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9988129-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}25 fuuu25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]202[.]64[.]0/2725 149[.]202[.]122[.]0/2725 149[.]202[.]248[.]0/2225 172[.]67[.]2[.]8811 178[.]128[.]255[.]17910 104[.]20[.]21[.]2518 104[.]20[.]20[.]2516 172[.]66[.]42[.]2386 172[.]66[.]41[.]184
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com25 hjhqmbxyinislkkt[.]1j9r76[.]top15 bitaps[.]com10 chain[.]so10 btc[.]blockr[.]io10
Files and or directories created Occurrences %TEMP%\d19ab98925 %TEMP%\d19ab989\4710.tmp25 %TEMP%\d19ab989\a35f.tmp25 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat25 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp25 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp25 <dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.hta25 <dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.txt25 <dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.jpeg25
File Hashes 01511c6ad7d6da2e5081db34c45aea2d6c2d157440d1e1f4fadb5cc3cff86f60021d7666d16dd5083ce4a0eb886f0ea16ac79edf334094233bf32cb93332963d1e26af9bdc05dcfdbf6626f1deb7cd8851ddead22c6e94e1ca39190e61bbc0fe23d6c1ece3a1ee85060b57e3faa3a6c2025381d91dbb478c0b853bad35314a38252a25e1adffe4f0458a34133a3a283258ab5b0e33e341ed66fd221b93f21215410a019072ab938487ea98d0a518251ba0bfed924ebeb782bb571664b06e1da946215f5401da97df51bef50822598f09ff32ddeb1f7e0294f27f3c58dcfe2356491b70e562b9b69d164e57ea99127bdd82437eabe0efcf27c59cbe715b5e2e0764eb2a2a555c87b8c081e98dd9bcc6f9bba87ac41f29770eb9bb5c1b16b4485e69eac3c62a2d29ebbb4839f1b65fd3ee98042afbcc92afa750d46f7528bfae606d4c281bbe47a629a26beb8fb2153eb45d72168e593456c84a14118f1bde0dc579dd9d68695ac2b81c4c45dff1bfece72543e55436b49a57a8aad0b11cd79e7b7a6d1a8de7a364659d5af20eae4199fe4541a21bfdb7171e01bb03ed562f640e85037ccf4776021c3b7d4803b18dc9435eeb0cb032c9409b580effd33db45e0885265f3b356aa631e4bd47e5978dc5e30ca590f368958d673f10ed5b5fc3e3fc86dbb841c5ad0120b910f3aac0eefab5fb04c760b43a53489c176145a6dc4ac28d56b340cac8fdf640565cfe1a767a1ec9c40fd9bc20aeb33c7d2903ee6122358da0cba69f36e57b1ec89d9485edc72b58e7912767c422791d83410dd8c1dfb98fe5a320488cbf6569bde928113c066395901e2a3c7fc285db5edd1443c8e63599ca82326950462e277e73f6c276cd52ec86e277ef7fe26df52cc441cfc23d36a7112b7c3ad24a2e23388f05d640c30d9ef92ecfdf2c870f554623f297cfe9ffab60c61cfa92cbfe6eae4dd3bf43f3148e94989ee1efdbe1e1fc2a34b5dc2cf4b1c64080fa8a33025ecb6e5774bf7e31d087df3cf38ca93de732a6915c14e34cb49f11f35af41c45c6d7a700485bb8bc638f8f74c2a6c8f35fe5dfb3a3c3fcb0b7836e20bc9631ace0f26deb0cc5c50515f94640b02149745661f5cba8cbffca
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
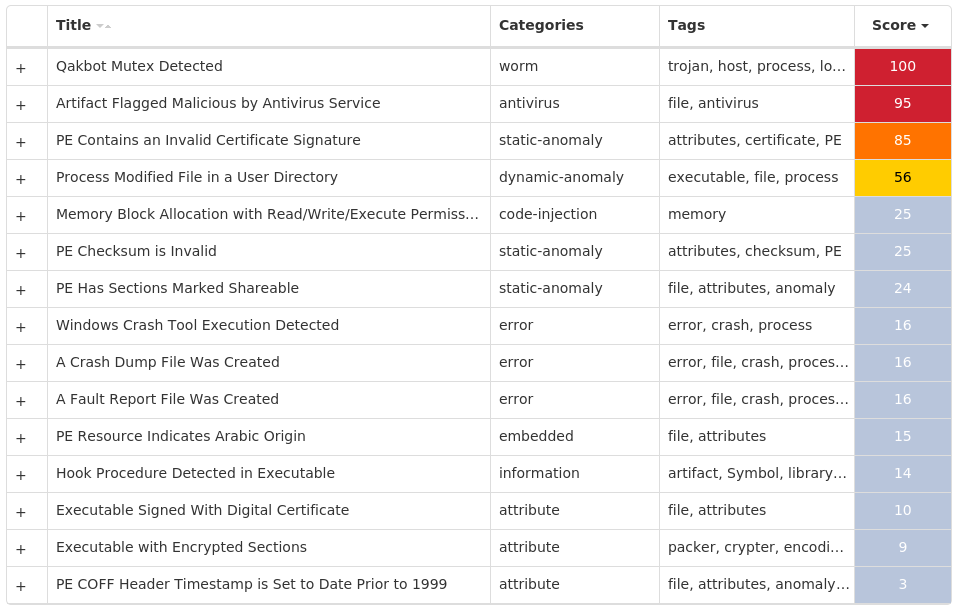
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Qakbot-9988002-1 Indicators of Compromise IOCs collected from dynamic analysis of 32 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bd63ad6b 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bf228d17 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: f7b512d3 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 79eea72 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 7a96a5f8 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: c22ac29d 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 5dfca0e 32 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 88fc7d25 32
Mutexes Occurrences Global\{06253ADC-953E-436E-8695-87FADA31FDFB}32 {06253ADC-953E-436E-8695-87FADA31FDFB}32 {357206BB-1CE6-4313-A3FA-D21258CBCDE6}32 Global\<random guid>32
Files and or directories created Occurrences %APPDATA%\Microsoft\Xtuou32
File Hashes 0266329991a609c3244535997bfc8a9c5a08953693f0960d72122d9dd19eaf530fa59b6e8585416434a04898181b63ddcf3b785377da2d6711aeb8c441ad949c10c51b1fc7c0331b2827d6cd076e444badf94c7c29ed982b198447c5b7eabf12126e16a74f8e126e8f8a87587423927cd7212cd761b058f40031fd8adad4ea2413cf01f962b5b63794e3774b2c616bb0fdbe487306b22045a50a18d209e10d3b15e2851fc6481958b95eaab92541a7e37d126d0407308adb5b144b87b15d6bba1635881fe75944629367a4d9a989ee70a4d0897289218fda9d4dd4fb621b7104182aa91cc52306e7f71ae4135292c6157b002b5e91ba16e309261c4d63bf95fd1879a0fbb682735b9496f3a5e01a52d6720ce157bc49cde377c382bae4ed75ab1e2a5a88e370b4bbc50a62e61040a2fc117af42bf672e56925c1e24b3dc5039e1e2dde336b5e068ed2f0ccaa2a14f2bbd61f32951b62ef1a964e542e1f65be661eceabe6da6e92bf09cb95edf20cc717baa50180146807164aed808691f0bcc92236204531ad81d7ab9b2c8e704497ebfde5e2554d2687fa3f5bd3800be540ff22be1aff400bff0e8488683681571b2c923e2aa2ed7b146c3f2d72da27c75942240f24d87905781e0d893683d560dfaf8e8e1c8533617fe4791e6aa0b851b2de2750e43ee7fb9e3ceffd87a2af2646454f63af292f6501804f3fdcacc0da612128d3830d68b8ead88c967f53d4544c5517fee4b18f27c2b7d7d4ecfdbc87c1dd2b1e565d706ae944fdc3517770819d310e346372bc52ec32ffbecfb4a05a2196305d2b4f7ebd85932c6daa7eca77fa08fa0adfb48e11cfe86e22e47e1aaf774a3cdf4800752be025dec2760a6c66eb059d734ebf2269d76186060fdb8176dfd93d5f9a4e0070cf99b4dffbe3d06500b8929462015467f294509c178c756c8b4b3e376c34b73658f6ecde946265299d14f14d191191843b66f2ff581dfb2e39c43ff648fe8c26ccf15b923e9de9f2b7cab25a047350a50cba019bed47b1ad1f40402dc9f0deb84bc6a911e6a13a953a6049e9eb79203968ca5cb123b21dd349f441536fc93761f6923f86562c12768a1053b08bb08f91b31043f423bf0a2c0229
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Path 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: NXLun 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Hash 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Triggers 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: uMakgx 1
Mutexes Occurrences 8-3503835SZBFHHZ2 Global\{bee718f3-e47a-44f8-955e-2fe2c6c0351c}1 1L21SQ530Y19A2G21 S-1-5-21-2580483-12447641952071 5Q85TO54T7IUJHCG1 DvgAsrEtPlXvjdEbGtypQiJ1 NGoDEoGyuCGBFiJVlcvNkyB1 Global\15842d41-ae1a-11ed-9660-001517b20fcd1 Global\3d822721-ae1a-11ed-9660-0015179ca3761 DUgGplDVWdlohlHdRLj1 WbyUtOvcY1 ghswoCxNjC1 KaILnwpfHSISrfJtaroX1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 81[.]169[.]145[.]1641 34[.]102[.]136[.]1801 75[.]2[.]60[.]51 193[.]122[.]130[.]01 63[.]250[.]43[.]31 146[.]59[.]209[.]1521 172[.]67[.]160[.]841 194[.]5[.]98[.]2261
Domain Names contacted by malware. Does not indicate maliciousness Occurrences checkip[.]dyndns[.]org1 freegeoip[.]app1 chinomso[.]duckdns[.]org1 www[.]junky[.]club1 www[.]glomesweetglome[.]com1 www[.]meyer[.]cruises1 www[.]klikq[.]com1 www[.]oldi-treffen[.]com1 www[.]caribbeanclubbonaire[.]net1 www[.]higherthan75[.]com1 www[.]roswellurbanvineyard[.]com1 www[.]rebuildtransmissionservice[.]com1 www[.]buyquickdeals[.]com1 ipbase[.]com1 www[.]gordonmicah[.]xyz1 www[.]magazinadziavane[.]com1 www[.]avp-travaux[.]com1 www[.]vgmpradio[.]com1 www[.]365bet356[.]com1 www[.]thealphabrains[.]com1 www[.]caldirectloans[.]com1 www[.]econiq[.]us1 www[.]showersplash[.]com1
Files and or directories created Occurrences %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp7 %System32%\drivers\etc\hosts2 %ProgramFiles(x86)%\AGP Manager1 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C51 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat1 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat1 %System32%\Tasks\AGP Manager1 %System32%\Tasks\AGP Manager Task1 %APPDATA%\NXLun1 %APPDATA%\NXLun\NXLun.exe1 %APPDATA%\ohursB.exe1 %APPDATA%\YYBuWmgsHfk.exe1 %APPDATA%\vGeroIiCN.exe1 %APPDATA%\sIYfcmrdwEC.exe1 %APPDATA%\rlOtoP.exe1 %APPDATA%\VwBkiqeJ.exe1 %APPDATA%\uMakgx1 %APPDATA%\uMakgx\uMakgx.exe1 %APPDATA%\KxVxzrkAELyD.exe1
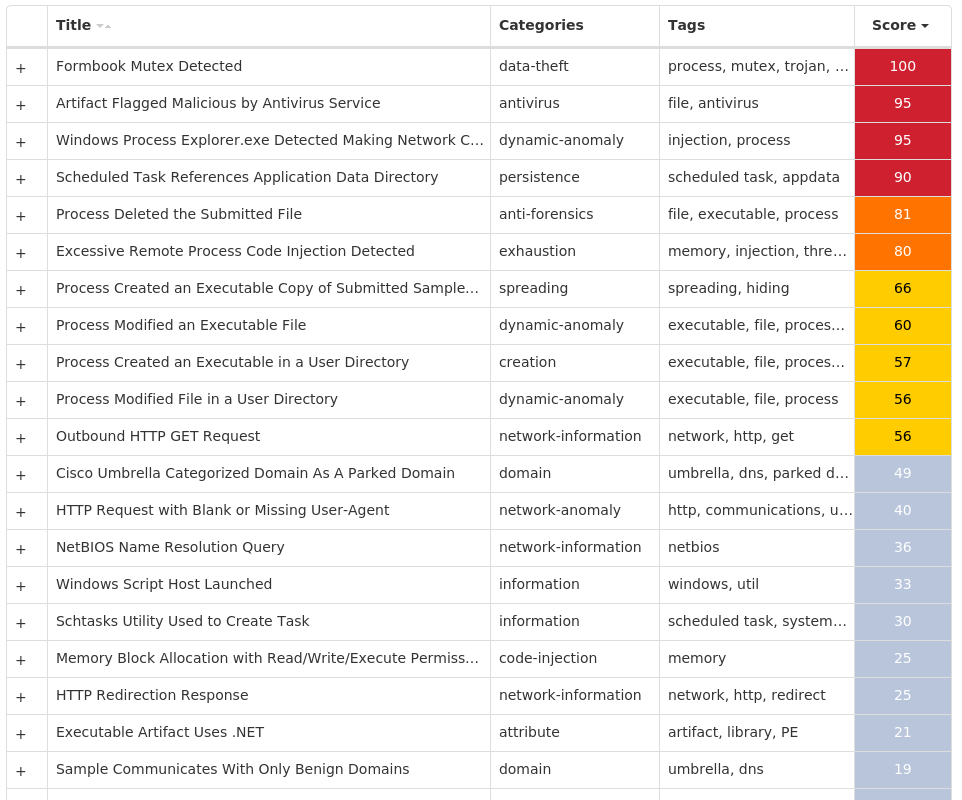
File Hashes 076951d55cc7d2bb25fe038497044c8743acc25898b7fde670c5da27d1a52cb41b884968467e50db56279a3d7058f96734186cdab01f51f29616babff72e53321e170d4925f50729c424e977db1cc81e86ca14305a7b8634d55bbe5265932f1d1f990c973ea05f2f378b060bcaa6a722c76533317b5700215684ea89f4307a112ffc755ae132cc543efb894bc94596f4beff9820abe8311c2f4dbc4efd7fc240331a2f20c2ac3630e787c3124c2d23c329bafd0cd058b6ee0b101dedcb7594a739f92d325132b3785dfc0c8344b9b56f6f15d91fc37f1d901fa4f4bc6b5ec2cb3b88eba319371131abc7c71ec3420a71045c3ddd7394ab2ee5a037449f5ca2443c0682e45d8c2b7127d90becc7354fea3928a6d3e981de82de8dd30c68766c993ceb374ef6968ff23e46095580a01e00eb2fa28512a04a643b97ba99eb5824cb43016c15520ced69adc74938c0dca2d675bc29450e55e70c617e423f30a0286b4aa831832b7ebd8961bdd8acd7146c934a7f0fb05850bf1a48abd91144b8186552579747e239df7738d31f9ff12669eadb6729fd8a3983b77f3a0bc772ce971456f1040045ad7e244e7825dfb1c8d6a4714811511cc4c72d73d5c13c7411a1685773fe5fe72f07ad3c3547c3d37169d78e65afa28163f960e8eedf620b8d94b4694b9ea09a47c2f24b47c60ddff0a0537828e8ba964c0ad0045b9862bce37d426afc0810fb38206252dacd24b06fe2deab975c9ba917d1e113a7abaed82d93f7851b20d33b8210f3d20ab4694011a0858eeb745e248a768c1e4c214efb59464b88e39d27b4ea76f3413a5561e71b3360f79de3c8025a0357b6dfc6764a721a398fa69958e1c3bb6964ce4f56bc4ca621c19a4902ed59872291f5727c2f0e04329daf1c68275ccf2f41c0772e712cb4549ec1d1e2aeda2ed8d64b1e4179f89bb5a20d6f1b2ff848088c1a588170ad1a1d726af6bb6a929c31ddf4cfc0e9e76a5fa63e0773595f36b7ada59361abb3b0df6bf684188170da64325f7224265ecc62aa42eafab66c88f070520fe3dbfdb60c53f8539630f57111c0201729b29b8e31c0e79df1a3c99ac22bb6ead55904af95d69e740a4c570d545335e6d74a41c8cb
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK