Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 10 and March 17. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
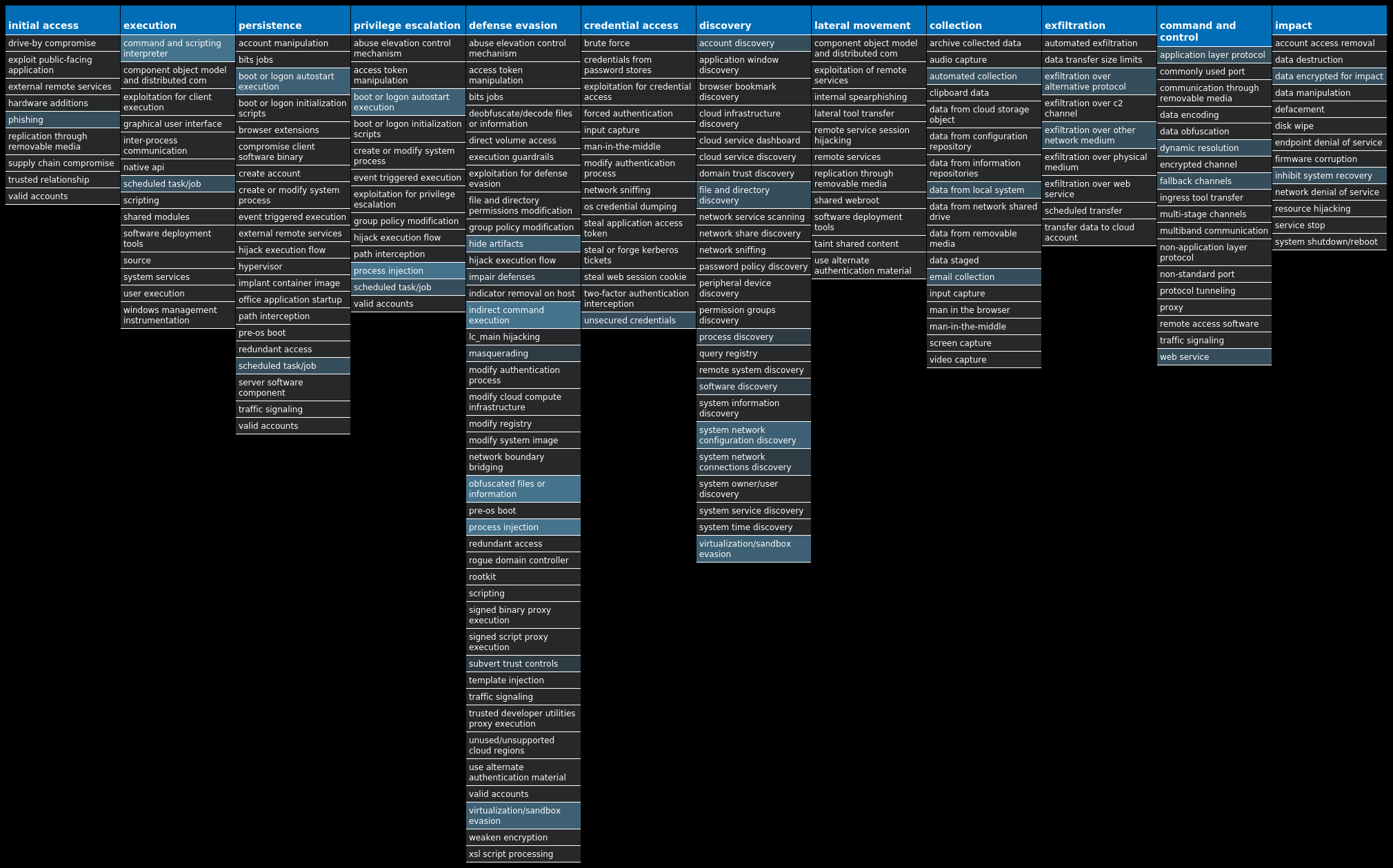
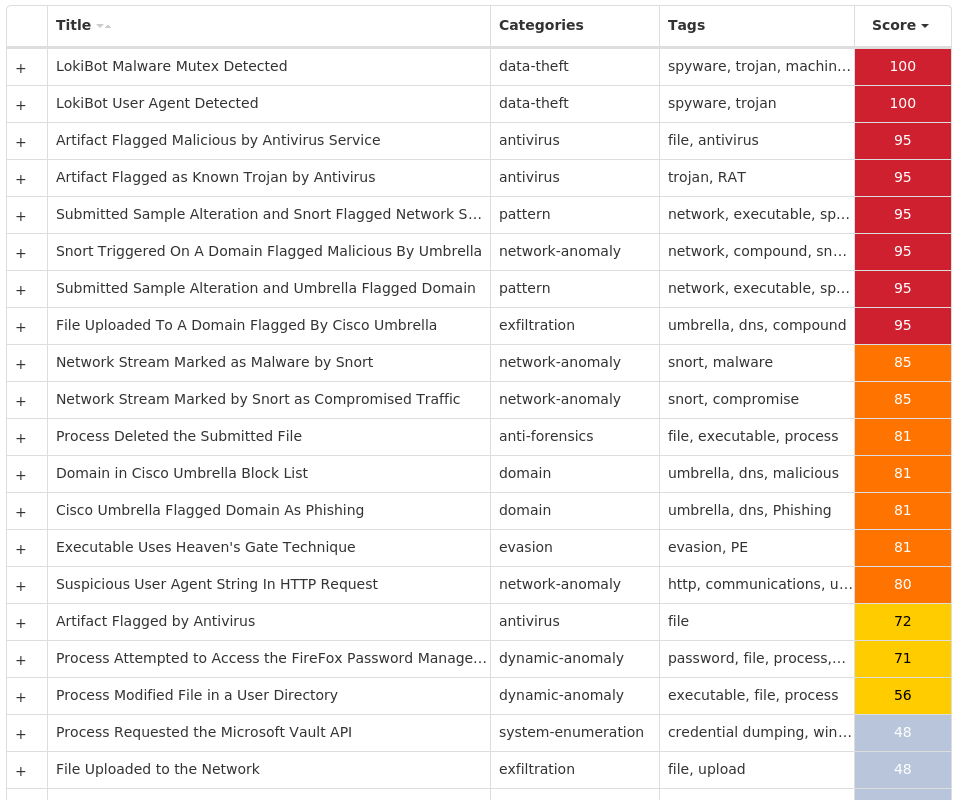
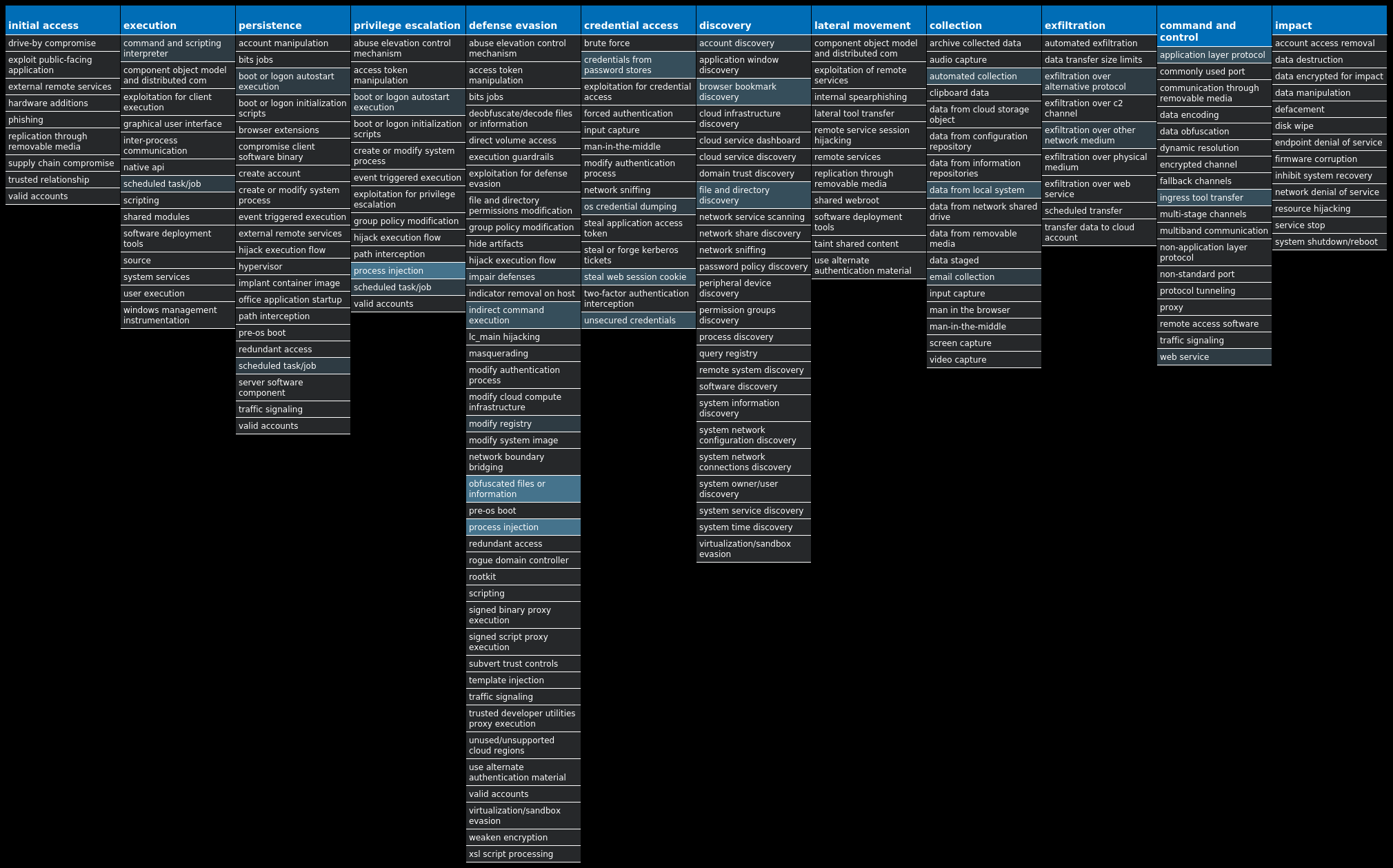
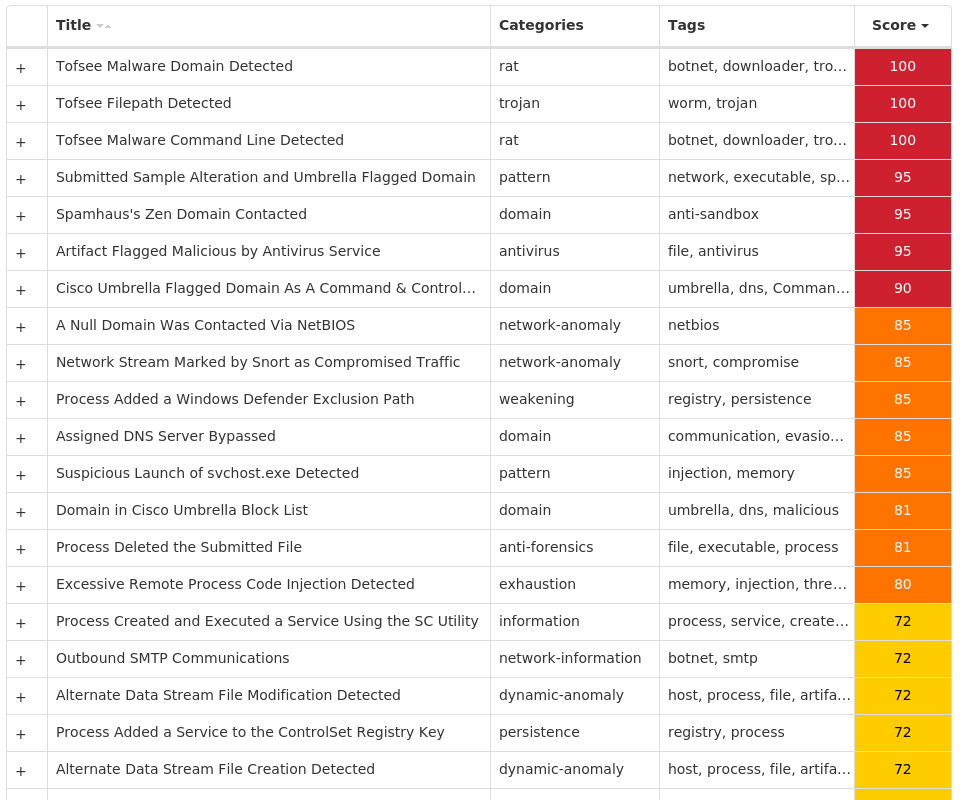
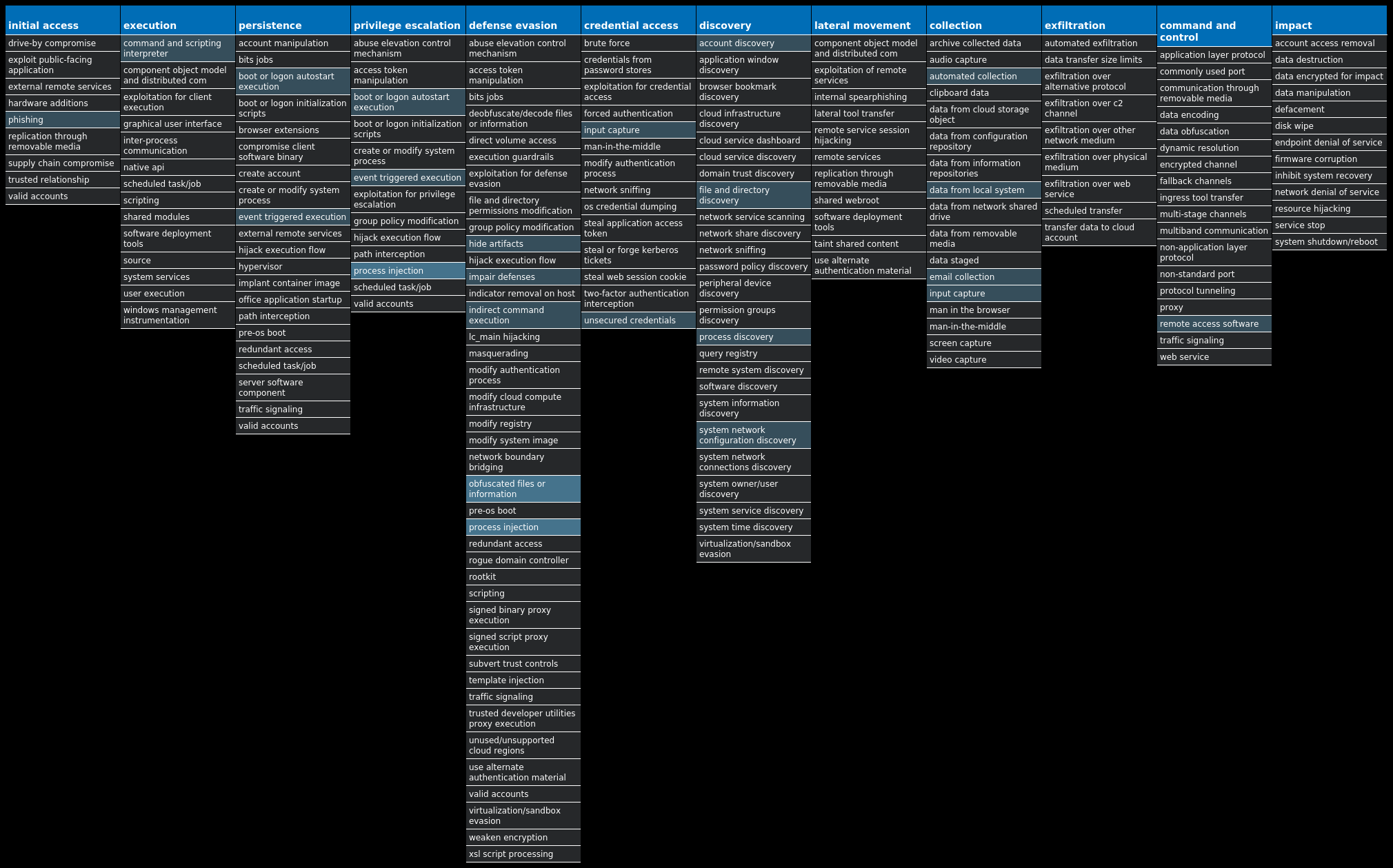
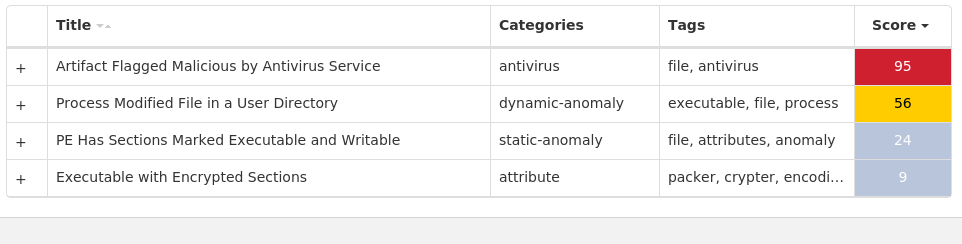
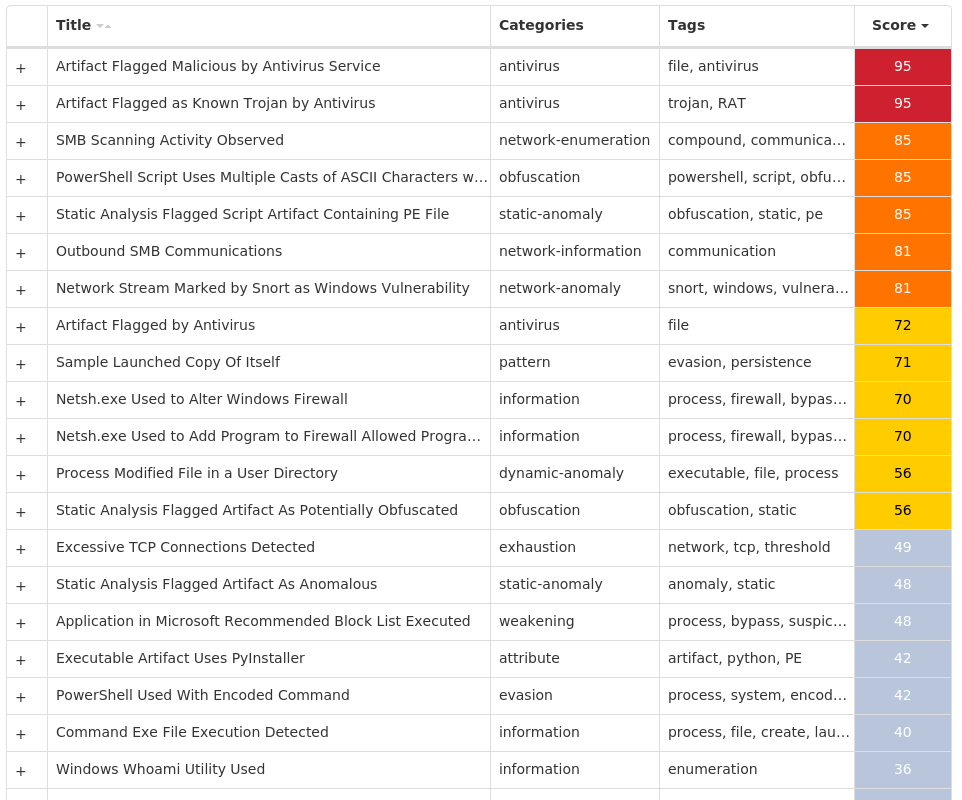
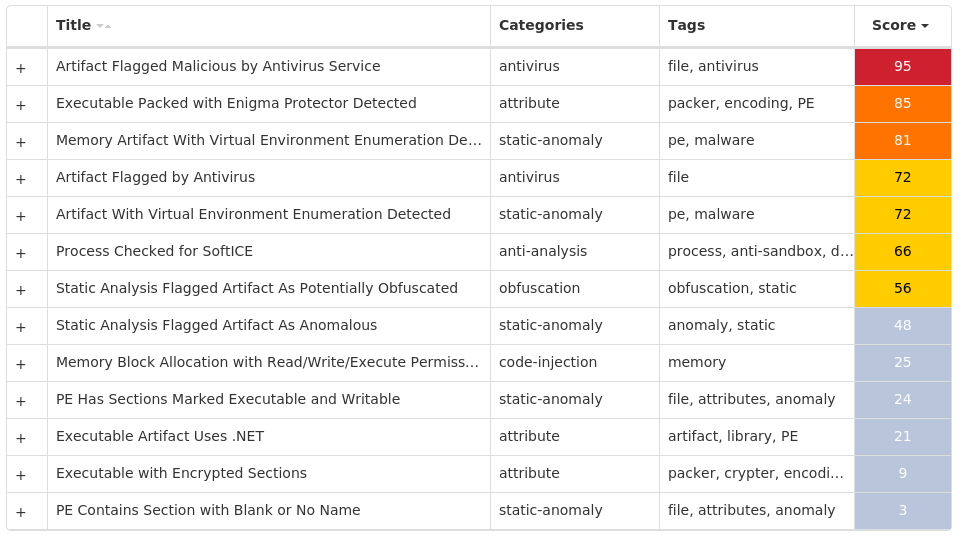
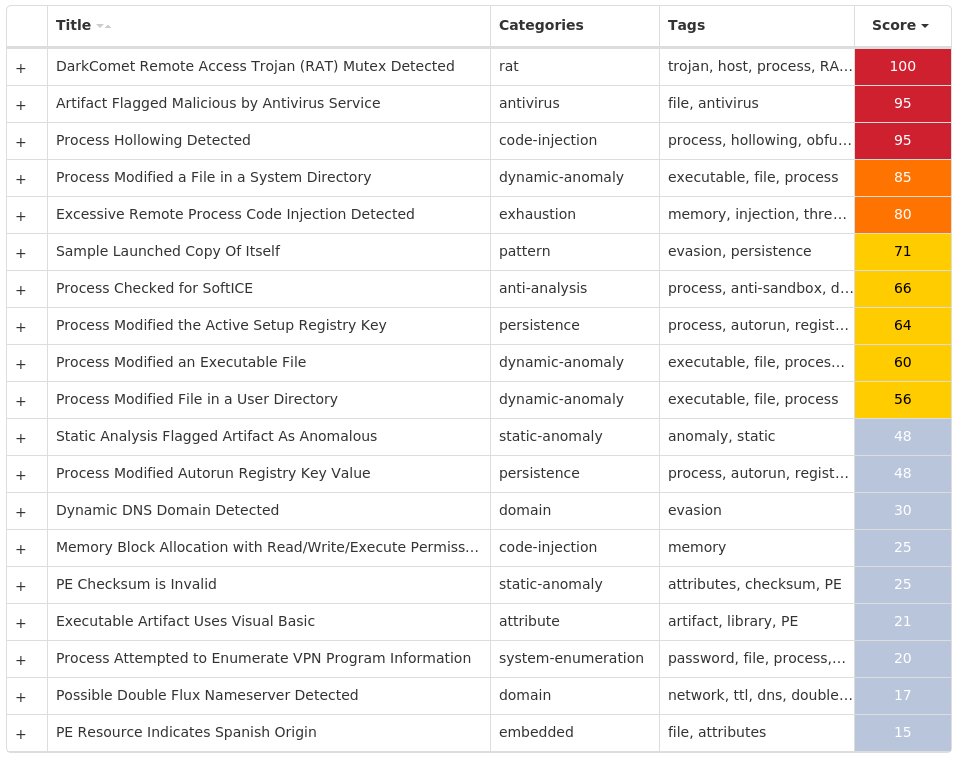
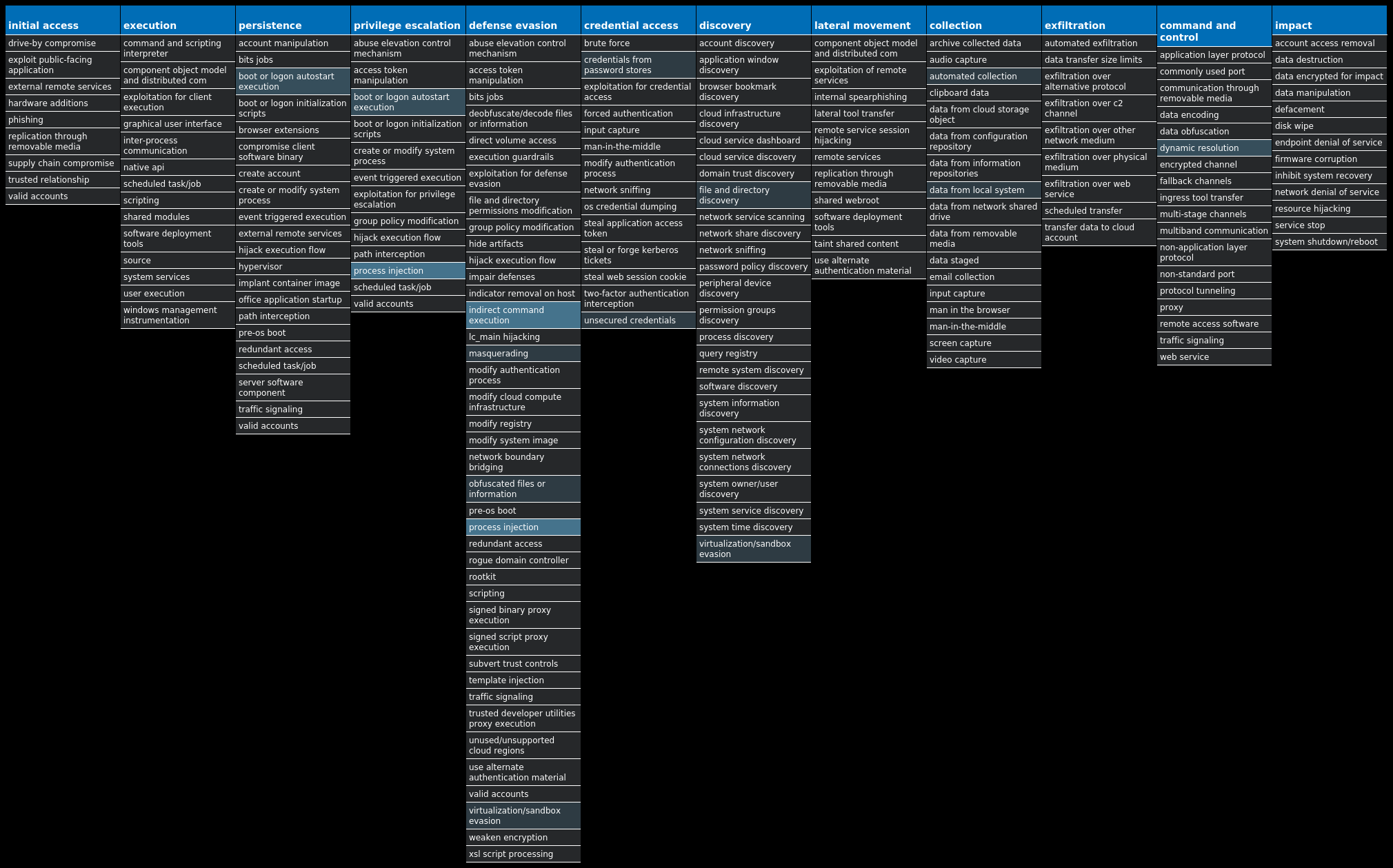
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Locky-9992697-0 Dropper Locky is ransomware typically distributed via spam emails containing a maliciously crafted Microsoft Word document crafted to trick targets into enabling malicious macros. This family was originally released in 2016 and updated over the years with additional functionality. Win.Dropper.LokiBot-9992313-0 Dropper Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents attached to spam emails. Win.Dropper.Tofsee-9992775-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control. Win.Dropper.TrickBot-9992835-0 Dropper TrickBot is a banking trojan targeting sensitive information for certain financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB scripts. Win.Dropper.Zeus-9992851-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Ransomware.Cerber-9992849-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Virus.Expiro-9992651-0 Virus Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Win.Malware.Ursu-9993206-0 Malware Ursu is a generic malware that has numerous functions. It contacts a C2 server and performs code injection in the address space of legitimate processes, after which it achieves persistence and collects confidential data. Ursu is usually spread via email. Win.Dropper.njRAT-9993044-0 Dropper njRAT, also known as Bladabindi, is a RAT that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014. Win.Dropper.DarkKomet-9992898-0 Dropper DarkKomet is a freeware remote access trojan that was released by an independent software developer. It provides the same functionality as expected from a remote access tool, such as keylogging, webcam access, microphone access, remote desktop, URL download and program execution.
Threat Breakdown Win.Dropper.Locky-9992697-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS17 <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS\DIAG\VSSAPIPUBLISHER6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}5 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 4 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DIB2 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DIB\RECENT FILE LIST2 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DIB\SETTINGS2 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\6C5DD69827FF1ABDECAB932DBD7E0843B635C7F90215ADA0A2091CFCD28F7130\RECENT FILE LIST1 <HKCU>\SOFTWARE\MICROSOFT\IQLUCI Value Name: Viuxyxe 1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\6C5DD69827FF1ABDECAB932DBD7E0843B635C7F90215ADA0A2091CFCD28F7130\SETTINGS1 <HKCU>\SOFTWARE\MICROSOFT\BOOCI Value Name: Amelfyf 1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DESKTOP1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\69FAC913942B3BD4F8B5D270EAB4E0853AA303F395E3B0E9CAAF4D065FB102B71 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DESKTOP\RECENT FILE LIST1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\69FAC913942B3BD4F8B5D270EAB4E0853AA303F395E3B0E9CAAF4D065FB102B7\RECENT FILE LIST1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\58F5DD18D509C4DA0CD87C38EB9E2E3604B743DF73128E6BB70D4BB7F888E8DC1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\DESKTOP\SETTINGS1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\F17E2A581FBDC1937F772D1CB6DE2A1819AE70433A02399580DBBCD02BC24C5C1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\69FAC913942B3BD4F8B5D270EAB4E0853AA303F395E3B0E9CAAF4D065FB102B7\SETTINGS1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\58F5DD18D509C4DA0CD87C38EB9E2E3604B743DF73128E6BB70D4BB7F888E8DC\RECENT FILE LIST1 <HKCU>\SOFTWARE\MICROSOFT\MYYFEK Value Name: Paegiziv 1 <HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\F17E2A581FBDC1937F772D1CB6DE2A1819AE70433A02399580DBBCD02BC24C5C\RECENT FILE LIST1
Mutexes Occurrences qazwsxedc17 Frz_State7 Sandboxie_SingleInstanceMutex_Control7 MicrosoftVirtualPC7UserServiceMakeSureWe'reTheOnlyOneMutex7 <32 random hex characters>7 Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!16613a85 Y2BfYmRgYl8x1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 91[.]142[.]90[.]554 109[.]248[.]222[.]474 13[.]107[.]21[.]2002 184[.]105[.]192[.]22 176[.]31[.]24[.]272 178[.]17[.]170[.]1331 185[.]14[.]29[.]1401 37[.]187[.]0[.]401 128[.]199[.]248[.]1051 95[.]85[.]9[.]861 89[.]108[.]73[.]1241 91[.]211[.]119[.]981 95[.]46[.]114[.]2051 82[.]146[.]32[.]921 91[.]107[.]107[.]1651
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com5 mynetworkinginc[.]com2 mydnswebs[.]com2 wronig[.]xyz2 brxgpire[.]click2 iiuchklnnmgatboed[.]work2 axjjaljeoopjyxi[.]ru2 dewsqfil[.]pl2 kspliksk[.]org2 ebljuseyhutbj[.]xyz2 josebrmhfiouodlpc[.]biz2 dyxbxbyyftsfvtv[.]xyz2 nxxjpjtgyrbmeomi[.]org2 ceawfapxacmpax[.]work2 vxwndredj[.]pw2 yvkuslknsjcjam[.]su2 rbdtujaxgleucvcq[.]pw2 hubtpfr[.]info2 lfilqricrecvah[.]work2 yabodjkyclgldh[.]info2 madxxabsulkwvud[.]su2 tdwhssrbqednweqts[.]su2 samorensc[.]top1 sportzpro[.]bit1 vfffcjrodbewspv[.]su1
*See JSON for more IOCs
Files and or directories created Occurrences \MSOCache\All Users\{90140000-0018-0409-0000-0000000FF1CE}-C\_5-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0019-0409-0000-0000000FF1CE}-C\_6-INSTRUCTION.html6 \MSOCache\All Users\{90140000-001A-0409-0000-0000000FF1CE}-C\_7-INSTRUCTION.html6 \MSOCache\All Users\{90140000-001B-0409-0000-0000000FF1CE}-C\_8-INSTRUCTION.html6 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.en\_9-INSTRUCTION.html6 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.es\_10-INSTRUCTION.html6 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\Proof.fr\_11-INSTRUCTION.html6 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\_12-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0044-0409-0000-0000000FF1CE}-C\_13-INSTRUCTION.html6 \MSOCache\All Users\{90140000-00A1-0409-0000-0000000FF1CE}-C\_14-INSTRUCTION.html6 \MSOCache\All Users\{90140000-00BA-0409-0000-0000000FF1CE}-C\_15-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\_16-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0116-0409-1000-0000000FF1CE}-C\_17-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0117-0409-0000-0000000FF1CE}-C\Access.en-us\_18-INSTRUCTION.html6 \MSOCache\All Users\{90140000-0117-0409-0000-0000000FF1CE}-C\_19-INSTRUCTION.html6 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\_20-INSTRUCTION.html6 %ProgramData%\Adobe\Updater6\_21-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Device\{113527a4-45d4-4b6f-b567-97838f1b04b0}\_22-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Device\{8702d817-5aad-4674-9ef3-4d3decd87120}\_24-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Task\{07deb856-fc6e-4fb9-8add-d8f2cf8722c9}\_26-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Task\{07deb856-fc6e-4fb9-8add-d8f2cf8722c9}\en-US\_25-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Task\{e35be42d-f742-4d96-a50a-1775fb1a7a42}\_28-INSTRUCTION.html6 %ProgramData%\Microsoft\Device Stage\Task\{e35be42d-f742-4d96-a50a-1775fb1a7a42}\en-US\_27-INSTRUCTION.html6 %ProgramData%\Microsoft\IlsCache\_29-INSTRUCTION.html6 %ProgramData%\Microsoft\User Account Pictures\Default Pictures\_33-INSTRUCTION.html6
*See JSON for more IOCs
File Hashes 03404430c812f7297e6ccf037d95590036c35f3369c84429faf43a112eb3159d1f39d68c1383404e9ce8c8494a281d109d2fead83f867818c652c7766e6416c622bdcf10b4ac46641ef8c1fba64144399fffe227a97b0b786ed9c91c5d581ef32883a2a845611b989db2c7483ed997aaae68e382d7be267ea18e7ad0445caba83fe30273342b0f10c6add37a464d5f99fcbdc167d1a38b0077ba74a6de904fec44e5e6bdda44e20f0505724dfa0d7e87773dc611d2dc7e8b761a9c6cdba5cc2e48fca8118cb07b782cfea98d576daf12149ee938497d511fcbb5241417d02bd258f5dd18d509c4da0cd87c38eb9e2e3604b743df73128e6bb70d4bb7f888e8dc59b1c883ba3ea6dec6ed732a870f226c8353190a78f77691d7d94fee9d6dea3669fac913942b3bd4f8b5d270eab4e0853aa303f395e3b0e9caaf4d065fb102b76c5dd69827ff1abdecab932dbd7e0843b635c7f90215ada0a2091cfcd28f71306ffc6676f47c334b781a22e7e54b01e9ae95bd81d6060570f98a0d021fcf38e37e0fec39c088ab36d4402f7b9e8a50e9ffc91496bc60e2344937b4b7de1cd91689dbe6d3a77fbf01b9c794b4616f498ea9af821462967eadc837fcbeeac9f9b19f3c9566c3d9316c2d71853a10a8f3f300c2e9b1eef52e6f6d56de61c6f93812da6f0ce0fc5f0106749a049b46efa6ad0d3a6dc6cc918e0cd57a6df11eb60d25f17e2a581fbdc1937f772d1cb6de2a1819ae70433a02399580dbbcd02bc24c5cfabc55649e253e31e1a44a3c34f475a72560a5dcacb80ed7bd351503e881d942
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.LokiBot-9992313-0 Indicators of Compromise IOCs collected from dynamic analysis of 31 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\USER SHELL FOLDERS Value Name: Startup 1
Mutexes Occurrences Global\<random guid>9 MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}5 Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}5 3749282D282E1E80C56CAE5A1 b4ababd1041a78e0c10e1f239485aa261
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 179[.]43[.]154[.]2165 185[.]11[.]61[.]1255 45[.]12[.]253[.]563 46[.]148[.]39[.]361 85[.]31[.]45[.]1991
Domain Names contacted by malware. Does not indicate maliciousness Occurrences sempersim[.]su1
Files and or directories created Occurrences \x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x735 %APPDATA%\D282E11 %APPDATA%\D282E1\1E80C5.lck1 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51 \{0cfd3854-32d2-d209-9694-f357f74eb398}1 \{965e0e8b-06f9-999b-2d71-2f8c50a6f3a2}1 \{acaa6a86-be45-08e5-79af-69e1952e99fd}1 \{4fa167ab-f7e2-ff24-2e48-647ef8633960}1 \{1e0b0e53-9094-b1ae-cc0d-9f9c10035e4c}1 %System32%\Tasks\026ade5f55f55a80adfeb99faf24652330cb48610c7cf25df9bb60faab6f246d.exe1 %APPDATA%\nsis_unsf8a8da0a.dll1 %APPDATA%\nsis_unsefc49040.dll1 %APPDATA%\nsis_unseeeaf100.dll1 %APPDATA%\nsis_unsf89f8556.dll1 %APPDATA%\nsis_unsef569933.dll1
File Hashes 026ade5f55f55a80adfeb99faf24652330cb48610c7cf25df9bb60faab6f246d05d14d976f9266cfa0d3ff95eee3bf004cff0c39a41c1edf77d74fff4fc7d67905e3406e34247062909a949470252f4063811e030b3ea5d8c1b39c92a7375582087969b4fec1bfae1b33eb26787984ce0f41b74f683dc85e2448122c9e6e741f0baa53972ce2be403f9e5d9d3a7f5d7098858a3acd9e16a315f6e4f5e0b2c90216348b729d2bdff35ff7e63de806e7830b25d6675faa623528860cd907dba6491c9e1883dd7bd24c169915cbd1f97860d26217b7ff7fb24c074c3798a1bf0fd1354334c9eb20671e94841fa04d729b28ce5f6a3cfbff5be1675d7f3aaa9666b036bded90af0ae1ab040893d92b507584edd026785f64f9f75b46c0ec5734cd87462eed45dc1290581f17a55adb2f731b9d86e7acab870c3b76a17a5786b5788f4b0e4fd6806fe1cd9dd277211a3aa9ab0510a3795355190acf8a84f6a2e5a50853af917ad08d3193143ae5a1d76475bebc70010d4e68081b411ae10baf91437655da9058a111a99e89dc332fcc1bc050391ca0b55a11bee16ca87d245a9ba3df6147208f4b1a7f58babe5be217c35692f28ac5f5c1cc3ee24ecfc2a3018e605161b369d98c58eb599c2f47b3e96ce2baa46b68e30b8fb4ca6401c6f1c564de846330cd9ef47e0dc267be011ac72402ef04bf66df0ebe56833764016d6b5c6eac6ec88c6d30afcccbb811bb0bc095df2b5ec8ec157451bfd3d13a5340c556a4957c4774a0b460ff234f93ec5f4c0b74e3b70d5931b5783b04249bbbe016065a1581cbe91ed74a6fe470374f44eee64544bb40a7e9e7bc20d733efe10d9b06ee2389bfa492dd655889006b5eea8133f6081c18fda93ff4bf1b3034284b345f50d093e16f6b26e069b4863446dcdd12b7e695298624a3e3bed6b85c574cc6ff9a4e98486c4a7ec955c2aeaea579f8a2d33219d239d55535459748f5e095aef92c2c9c88be5968b7f8817fe5832fdabfe213d1bc19168c4ee260afffb75651c7939da4aa00e22151b6feaade9290ec71759739c6c0bf76d1cc0d8123ffd497c781c1b40ec204d6bc2143f05504dbd995a1f361f8a498fd13b68598653b7c335dddde
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-9992775-0 Indicators of Compromise IOCs collected from dynamic analysis of 179 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 117 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 117 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 117 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 117 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup0 113 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup1 113 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\FEATURES113 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 113
Mutexes Occurrences 006700e5a2ab05704bbb0c589b88924d113 Global\<random guid>23 {1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}9 M5/610HP/STAGE29 Random name4 MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}4 Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}4 WTfewgNmxpcaVXHKTu1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 193[.]233[.]20[.]28114 31[.]41[.]244[.]200113 149[.]154[.]167[.]9911 162[.]0[.]217[.]2549 185[.]11[.]61[.]1259 95[.]217[.]240[.]2499 176[.]113[.]115[.]1367 80[.]66[.]75[.]2547 80[.]66[.]75[.]47 176[.]113[.]115[.]154/317 176[.]113[.]115[.]2397 176[.]113[.]115[.]1357 108[.]156[.]22[.]1237 80[.]66[.]64[.]1877 142[.]251[.]32[.]1006 157[.]240[.]249[.]1746 45[.]159[.]189[.]1056 104[.]199[.]178[.]2485 20[.]84[.]181[.]625 108[.]156[.]22[.]495 108[.]156[.]22[.]1165 40[.]93[.]212[.]04 23[.]36[.]87[.]1134 20[.]44[.]209[.]2094 45[.]150[.]65[.]44
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences t[.]me11 api[.]2ip[.]ua9 uaery[.]top9 zexeq[.]com9 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net7 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org7 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net7 249[.]5[.]55[.]69[.]in-addr[.]arpa7 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org7 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org7 microsoft-com[.]mail[.]protection[.]outlook[.]com7 microsoft[.]com7 www[.]google[.]com7 www[.]instagram[.]com7 jnb-efz[.]ms-acdc[.]office[.]com7 nidavellir[.]top7 mail[.]zoom-a[.]com5 api[.]twitter[.]com4 steamcommunity[.]com4 in-jsproxy[.]globh[.]com4 i[.]instagram[.]com3 video-weaver[.]lax03[.]hls[.]ttvnw[.]net3 imap[.]mail[.]yahoo[.]com3 api[.]steampowered[.]com3 www[.]ebay[.]com2
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\Yandex114 %LOCALAPPDATA%\Yandex\YaAddon114 %TEMP%\IXP001.TMP113 %TEMP%\IXP001.TMP\TMP4351$.TMP113 %TEMP%\5975271bda113 %TEMP%\5975271bda\metafor.exe113 %System32%\Tasks\metafor.exe113 %TEMP%\IXP002.TMP104 %TEMP%\IXP002.TMP\TMP4351$.TMP104 %TEMP%\IXP001.TMP\dry40s70.exe75 %TEMP%\IXP001.TMP\film3390.exe75 %TEMP%\IXP002.TMP\bus8956.exe75 %TEMP%\IXP002.TMP\con3920.exe75 %TEMP%\IXP000.TMP\en894441.exe75 %TEMP%\IXP000.TMP\film0968.exe75 %TEMP%\IXP001.TMP\dix60s27.exe18 %TEMP%\IXP001.TMP\film3173.exe18 %TEMP%\IXP002.TMP\bus2289.exe18 %TEMP%\IXP002.TMP\con9203.exe18 %TEMP%\IXP000.TMP\en504805.exe18 %TEMP%\IXP000.TMP\film4417.exe18 \x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x7314 %ProgramData%\freebl3.dll9 %ProgramData%\mozglue.dll9 %ProgramData%\msvcp140.dll9
*See JSON for more IOCs
File Hashes 0081caa4f5e8666d6dec071ffb012a9d7beaab29def3786fa872089b1f5a62860132ea76017ff9b5356eefc5e1dc9a3c57aa30873b5fbd9322aedc887d6250b5014302d7d081b449b499c26f94fb69e046fd7c89b9a1d777d796dd9f73b4acac01e43f88843f875630cbfcc5bf5eb5e8b1b53eecbf466f1540c5ee0349d68239020dfce0a33a2694c201c296615423ba6ea6ebf0aba1fbf54936a48b1238ba330231ae64405c9a2797794956580d0a88a983b824b058f00f349fe67e983710d70302badfae68ce3a7d50ea6efb4d2ab579e2c93ae4942b1546334fcb76704cdb04a5ecc7869bd8333617902600a450d5851507c3c4c487a9db1652e38b368f2f050cff9aa4e6dd7d759f3e3f32a5136c8619d3f3d681808dff9442d434bd4bd906b509741fd69c20bd174f9edcb3bf69a3a0200a1a88a9008c9b6bd45be60b2407760befc629ce7e5cb2f67f7df22630038f2725d414ff10e16251e2ab526f7d094d8c8828f34953e2fe3bce088b88625c3d73050dbbd52ac87baa478a001a950b48a318800bf7c8b49d20356f6ad142b97c8cb1c20465aebd4aa1386401e4210e58d6042b0b37f41b15d4cb18a6020e4154b8a67de3d8823d3da2b7a5cba6d50f3e9b74ec8a0b712669883c8148adae65d495ad3da1cf0e53729a84ec218a9d0fc7bccfa207f120a1e43e75caa5390c28cbc0357a785b8d8f5fa262368c41f0166a89f2f7e0fdd7d7f1ae3f4ae51677e1febb9573d33d9c8f67f24b2fa5381818639951491277c647bde41ff7518a6ee204836b5f4bd77813d9fe6d638933151d07f6d20edfb4b7a052a34c9baf1faacf1f0f7f109fcf3063009b10a3457d192187fcec456d7a6a122a594105fe6308b245fe1a8d442f67a6ae9358660ec6c3224b635af938ca1e5314229ba5401ba2ae506678c9235c86caa01e87c5435f2d2251ee7392ff79e0b664f3dc135ef9a2ff1273510af10678f819c573b8922a8a22c9e782d2f4ff527ed4e0578100d5f9bf50c7d37a9e49f33a63b227b6c8e898244281a32a9da1dea28355b0cfcc20e35613001a6b6e5a48dde9ac59521ab78d245b649d0e74658abe321a3f6b7be8ff02457a1d958d78d958c91e1595023eb4
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TrickBot-9992835-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Mutexes Occurrences Global\316D1C7871E1025
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 181[.]129[.]104[.]13911 181[.]140[.]173[.]1864 5[.]182[.]210[.]1324 5[.]2[.]75[.]1374 198[.]23[.]252[.]1173 172[.]82[.]152[.]1363 181[.]113[.]28[.]1462 85[.]143[.]220[.]412 107[.]181[.]187[.]2212 107[.]172[.]208[.]512 23[.]94[.]70[.]122 194[.]5[.]250[.]622 195[.]54[.]162[.]1792 181[.]112[.]157[.]421 107[.]172[.]29[.]1081 107[.]172[.]251[.]1591 64[.]44[.]51[.]1061 198[.]46[.]161[.]2131 195[.]123[.]245[.]1271 184[.]164[.]137[.]1901 202[.]29[.]215[.]1141
Files and or directories created Occurrences %System32%\Tasks\System Network Extensions25 %APPDATA%\sysdefragler25 %APPDATA%\sysdefragler\data25 %APPDATA%\sysdefragler\settings.ini25 %APPDATA%\sysdefragler\à âûñ÷âöóûâïï.exe25 %ProgramData%\à âûñ÷âöóûâïï.exe25
File Hashes 0313de637b547f58e37019e1c1e8a4c8c8c379b0cd70e26973fe1964d19370c0065321daeffa60da415d858b97a047969eefa46b37156e108ddcb9f5754130200a3afbc780cad1d1362aa1a878dd4b5083aca8dee29612a153d5774f614305c811c43a83f4c74b79d4790739fa7268d3f7d881d2f7b6ec360fe04ea1a4d1861e19181d38dacd716cf20a7a946003be12fb86e6a0c751639ddd6d53efe3efda301bff35e3ecf565e6b00a71aa200718f819e7f16ae0f15d0bf02d3b19469e7ae51da3627b54308455a08ee0c7438ab351c5401a27658c7aef4107e37c8f3178e535fbb53097e23c03420490049f2312459bb39dc7d0b9f938f11d03a6590b8ce9394426bf9f92de4a9f17fb55e2cf673913f0b3316a835a9997e344c202d11bb8398bcec3fdcdb9741f0964893f0601e3cffbc7acbe341aa437b41c24df0fe62e43e0fef28e8043c80d9f55f761024132094667e5f339dfa6058ccd6055ebfd79455f826f7c7c1e1e457af75b3a1c352e15d59c0550047f6a0bb315018501bc864953287f3a0f5f765cc3a829479c95e27d1e88ef1b8307bf768c44e250c4c0da4e3d6f9482cc48ca25ef232c2561d665f0aac62c6c04bf344c8a8a13d56450b855e67ce7c42149309618cedc8e1ea4da6acd01396d8b1cd4019e99fc2007d14c5c5462890f505c6ca3c85a5b8b147c12a0a09d2904021c572b94de94793eb9b85cf5cdda923dc5e45389de58b252df23ba48cfbb640a6061c5fd7e9154e40b4861dacaba2faa01e74db47dfd948d7a4431be91e6d97950a0c3ad3178b6648bc8629ce5216f881a8ed29eff04eb8224968e25607259ec4a5c579253bb252c986b6ccc41ce35ea17f12dce382972eaeb3e6f1ed1a562a22fba64d3fbcc69e0b66e705ec0aac3f4ce4bda3c9c6beef15b039b22c6c123a40a564d2216600392145173b79085f4ee914a9b41772c59effae7d372f413e543a53c8f0bea7944567f11745dfad60a85705913fbea3da445078a4f4a45dd9f4f9d4ac6a9cd316973f77c756cad16e6999d083a3c2d260ee091738f61423f2036d5d52865350bbb73da2c76f37200eae123f5c6fe3935ef3c7776c554c8f85e3cb459bf3ac12affe72e71
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-9992851-0 Indicators of Compromise IOCs collected from dynamic analysis of 22 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY Value Name: CleanCookies 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 8 <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Ahxesuhi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Iwagarwas 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Atmuiz 1 <HKCU>\SOFTWARE\MICROSOFT\DAAHI Value Name: Xuhowoc 1 <HKCU>\SOFTWARE\MICROSOFT\TOYRAC Value Name: Coewbai 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Cewaik 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Saxagoi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Doixotfees 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Ampyylhy 1 <HKCU>\SOFTWARE\MICROSOFT\WUOFUZ Value Name: Yqemxiavu 1 <HKCU>\SOFTWARE\MICROSOFT\LYEFE Value Name: Elca 1 <HKCU>\SOFTWARE\MICROSOFT\QEGYL Value Name: Ergafoly 1 <HKCU>\SOFTWARE\MICROSOFT\WOHI Value Name: Qoawfyali 1 <HKCU>\SOFTWARE\MICROSOFT\NAEX Value Name: Zeeple 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Kyyfidt 1 <HKCU>\SOFTWARE\MICROSOFT\UMAT Value Name: Laliaxon 1
Mutexes Occurrences Global\{24146835-2A78-0A63-790E-75826EC5FCEA}8 Global\{B16FE7F0-A5BD-9F18-790E-75826EC5FCEA}8 Local\{BAB1B2C6-F08B-94C6-790E-75826EC5FCEA}8 Local\{CB0EC182-83CF-E579-790E-75826EC5FCEA}8 Local\{E695734A-3107-C8E2-790E-75826EC5FCEA}8 GLOBAL\{<random GUID>}8 Local\{<random GUID>}8
Domain Names contacted by malware. Does not indicate maliciousness Occurrences seantit[.]ru8 programcam[.]ru8
Files and or directories created Occurrences %TEMP%\tmp<random, matching '[0-9a-z]{8}'>.bat8 %APPDATA%\<random, matching '[a-z0-9]{3,7}'>8 %APPDATA%\<random, matching '[A-Z][a-z]{3,5}\[a-z]{4,6}'>.exe8 %APPDATA%\Doanih\ryoga.zoy1 %APPDATA%\Obego\yrefy.ehw1 %APPDATA%\Ylqyu\osxy.hag1 %APPDATA%\Yxidc\coel.die1 %APPDATA%\Cyimp\uvog.mom1 %APPDATA%\Uzoxi\wiyg.ygo1 %APPDATA%\Meixa\ewoq.lor1 %APPDATA%\Niugaq\icus.duu1 %APPDATA%\Ehgefu\fuke.xau1 %APPDATA%\Aduwq\bafoi.izk1 %APPDATA%\Iqoqro\umme.gab1 %APPDATA%\Woileb\iburh.tab1 %APPDATA%\Qeomuh\wucau.agf1 %APPDATA%\Foyd\yzdem.uvv1 %APPDATA%\Lete\burey.idc1 %APPDATA%\Humauk\garya.cyi1
File Hashes 0935b1313026751474c8e452a12c6448ce6e30b5d1b5c0967c586e7d59e27bf311e6674849c05f1916df77e9ef1c2901557a5f8693c75c070bd7928454ea75e91e0a8c2ff53c2e2ae63f27cc0e4dc8d63504e239f9c8e30ffa5bf41c9721500c2766493fef96833aeef0673a942fce273364fd1b1a53dd95bc41e73064ffb0733c451c7b064a05f544b79f2983ea50406f4ffb7c4ed4bfaf7d7eb64bba6a4b574ae384eb35f66701b1c7982217ba0cf7ad99a3885112ddea2a2e002b878e8e815009c9fc0e9860a5f37362f7864b5ef3927cfe2c96a86bad869a763f92e230f9738a13a9fb97ba602d258f0a5ec3ff1f8afbb59adbb1c9154e38f304ad5b216e782c689a5c281dc302d6bdb126cfa8df1ced22ab3fc63b230778fc2e64bfacab7d93c290c406a409792f172b92a8d6097cc74e35fb55dfb9c5c69538609dbe237f56974fd0f1cbd93f4c870dc775232122dc97b0717a558787002f188210811284308452f37d7cdb9564a9c2071665814a35d2453c3d092e5c40b8a3a0f4c13eac066d7f5900739b97b6eac8ee7ade59662ec8a4af16ec46a817d1e54920bf98b28fde84bc2b9535225e5f6f1f284646403dbf707d2609985f5872d6c72e17dabe622d2ddbd39acca31e736960f85a08379643e71ca5a8d724062bcbd73b0657c025464ccd5971670cf1352385f5deee5d06d211a041911b9893d92ce35fff77c6c1df7700357b8ed73d1400688283881aa2c8a0126dd590ed1d3b049b7f3574d85697ed71f46377b05313fa694c5732215ec3a0d42f72a25acbdb75c2d23260e31dcc2a376bb1db057495c94be048750b3b9a0caa1f7c50c7a083bfa6664a84e96c8403c4348f5f6147cc59eb69f968827525dc726c10ef07e3eac33ed2c8a3f873c2818ef358e31a901bcdc43a2364cfdddae31641320d9305b0a44c061f25fb02bc10f36a6afb9a8c9f5e464243f14edcfce3ec28b8690d5daeaea1d338a1
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
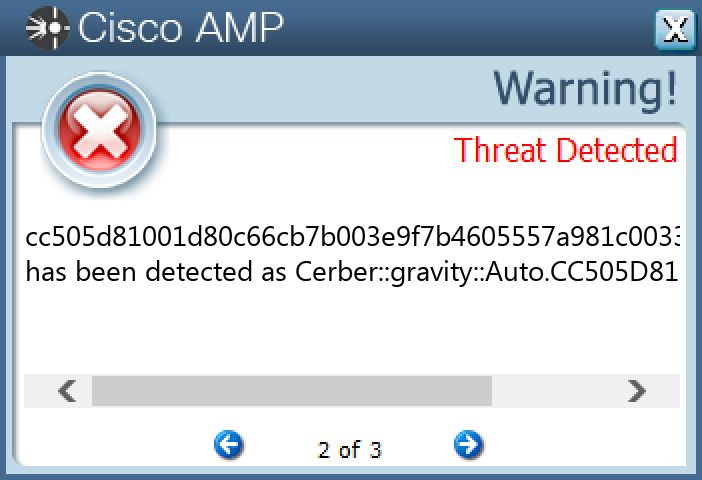
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9992849-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]165[.]16[.]0/2211 17[.]1[.]32[.]0/2711 78[.]15[.]15[.]0/2711
Files and or directories created Occurrences %HOMEPATH%\Contacts\Administrator.contact11 %TEMP%\d19ab98911 %TEMP%\d19ab989\4710.tmp11 %TEMP%\d19ab989\a35f.tmp11 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat11 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp11 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp11 %APPDATA%\microsoft\outlook\_README_B74MN_.hta1 %HOMEPATH%\contacts\_README_H6VK_.hta1 %HOMEPATH%\desktop\_README_CHIF_.hta1 %HOMEPATH%\documents\_README_JXC2RA_.hta1 %HOMEPATH%\documents\onenote notebooks\notes\_README_JPGA1Q_.hta1 %HOMEPATH%\documents\onenote notebooks\personal\_README_B153_.hta1 %HOMEPATH%\documents\outlook files\_README_Z5UUMH77_.hta1 %LOCALAPPDATA%\microsoft\office\groove1\system\_README_X9XYQJ6S_.hta1 %LOCALAPPDATA%\microsoft\office\groove\system\_README_I01IR_.hta1 %APPDATA%\microsoft\outlook\_README_F763VNMA_.hta1 %HOMEPATH%\contacts\_README_7SJPVX_.hta1 %HOMEPATH%\desktop\_README_VORHMMO_.hta1 %HOMEPATH%\documents\_README_YC31F5JF_.hta1 %HOMEPATH%\documents\onenote notebooks\notes\_README_Q969WJ_.hta1 %HOMEPATH%\documents\onenote notebooks\personal\_README_UE3L_.hta1 %HOMEPATH%\documents\outlook files\_README_GBMFP_.hta1 %LOCALAPPDATA%\microsoft\office\groove1\system\_README_OK32B_.hta1 %LOCALAPPDATA%\microsoft\office\groove\system\_README_6EDL1F_.hta1
*See JSON for more IOCs
File Hashes 0299f52568e3c3e8a20eed942d9c917abe85706ed632ab41740171032b75ba2733aa469808a2fac1af7bde02073497141f80d3f979f01ab3a7fc3ea253ad152d3a91173ac37aa2d6c4e5175571d3c6c3d41519b5854adec234f6a8a0199857357a5654712c457a298d328527fa233e107666495305bf0c6dce05f92dea718adb8bf09171baa96b2c3d6a5741b171a94b6140719a18c4f5e4ba198b8ee5c664b999e06cf857f018f62505a683f1fbd5fe6176d995953a9f46a64e7ab338a9ff29ae013908e9d0e586d733badf1dea24f4ae985c98313b47ae62ca0f48562cfaa1b35c0c351f090cc9267a8dad234a6d5e3c2f086497948baaa8d7088daeff4ee3c75b676599dfc4f2f2ee3530bbf86dcba3a380ceaf8ab241de0f83ab5629195cca95f9b79b39c7d91cb601b56b7cd4bdf3cc30dc0ba851273b33d6a5ecbeddaccc505d81001d80c66cb7b003e9f7b4605557a981c003301d07500180d3e3b813
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
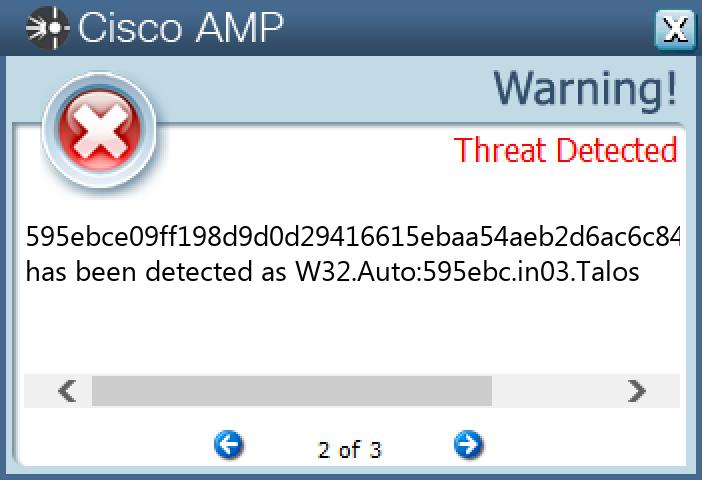
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Expiro-9992651-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Mutexes Occurrences Global\Multiarch.m0yv-98b68e3c311dcc78-inf23 Global\Multiarch.m0yv-98b68e3c311dcc78493cd690-b20
Files and or directories created Occurrences %TEMP%\FXSSVCDebugLogFile.txt23 %TEMP%\FXSTIFFDebugLogFile.txt23 %APPDATA%\98b68e3c311dcc78.bin20 %System32%\alg.exe1
File Hashes 0368919fe82d5f16749986e2ff7f0817f8dd8547ec9dcc6a2acad45b3a0071080e7153cbde0d2904de4381abbcacbc1b3d36cf73fb64f2a2fb52d4d2667a469317324ad4952b971f99f2a1f6bf797ccfe869e87e2f03ab6498cbd16c213bc00a191a1b046b3e6b739e7b4e2aa8f17a39ac5b115b7a1aee70f33d1cb1f4b067de1a68b21345fb819861a8da9f99f89af90d7f70c92bdb8bc63a830c14f523ff7423e8f2741f52c4eb812491e4648155f56ffc7b83a1d489e1c7e60f545134ab942d4e34cba87f45c358e591c40e9650742e7e27b4c9c757d32e942b296dee8a3d2e981c607f33fcd0bfae11711442c3b06e8e918bf64fdabed7d7dd06a577cc843781e971f6ed27177f2e7dd72294d8393a14a25f38d4a88250978cc55c6bd4b3595ebce09ff198d9d0d29416615ebaa54aeb2d6ac6c84c636bc18bc7926975bd5c71ca9de35ba3192240d1ab4b26f87e098c3403e789410ba937a29dca796bf1605640b61ae770c1155f116a4b520ba1e58f9f85f3b3df06fd1c3cc86e88790c8169d89c0afb1c60e10496a1fcf15781da300deb8d77123c9241e4cd2127183d85e37e39ce4e04daddaa5fe09cba3fac0cc6573b1577786b90ef1d675cc1a5a18a5283bc8fe9bda0e51126fff99820c25a837b668d2c491fb7ac4be3115b4bc99085523c8866e3eb913b4fbbf6a529dd5c8568a8b41a1701d0b643a9a02faef4a1ff6b73eb8059a372c699764f4251ca1b6645d0dd4e2e9f03eabc2c518c605fa51a8fa2dac31b208e41e8b33e465d8403a4443e51289f76a772a32d011c7f55b6d2770601ba50d9e74ef3b6e52e623472775a648d54774cd686dc9c6a1744f6b9b68dfe8533f769ca5008c5226be3def020823f10acfe00a1e741baedb4fe8bba38f434f80918dfcb8625e70eabdfe75628295fc3b99d8c56c8002fd0d7a43dc7ddc112ff722f5c28cd6d9265b451492e177f1b65f887f4918c7c85f4f4c147e4205529c2944abc592b00f987fe9607351627e029ae0e764ec1eabc640e9a39
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Ursu-9993206-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Mutexes Occurrences Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb75 Global\405f0aa1-c411-11ed-9660-00151757fb541
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 120[.]254[.]246[.]2/311 120[.]254[.]246[.]4/301 120[.]254[.]246[.]8/291 120[.]254[.]246[.]16/281 120[.]254[.]246[.]32/271 120[.]254[.]246[.]64/261 120[.]254[.]246[.]128/271 120[.]254[.]246[.]160/301 175[.]26[.]247[.]11 175[.]26[.]247[.]1801 175[.]26[.]247[.]2/311 175[.]26[.]247[.]4/301 175[.]26[.]247[.]8/291 175[.]26[.]247[.]16/281 175[.]26[.]247[.]32/271 175[.]26[.]247[.]64/261 175[.]26[.]247[.]128/271 175[.]26[.]247[.]160/281 175[.]26[.]247[.]176/301 121[.]179[.]217[.]11 121[.]179[.]217[.]2/311 121[.]179[.]217[.]4/301 121[.]179[.]217[.]8/291 121[.]179[.]217[.]16/281 121[.]179[.]217[.]32/271
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.CIPHER._AES.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.CIPHER._ARC4.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.CIPHER._DES.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.CIPHER._DES3.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.HASH._MD4.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.HASH._SHA256.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.RANDOM.OSRNG.WINRANDOM.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.UTIL._COUNTER.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.UTIL.STRXOR.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MICROSOFT.VC90.CRT.MANIFEST7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_HASHLIB.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_SOCKET.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_SSL.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\BZ2.PYD7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\II.EXE.MANIFEST7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCM90.DLL7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCP90.DLL7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCR90.DLL7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\PYTHON27.DLL7 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\PYWINTYPES27.DLL6 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\SELECT.PYD6 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\UNICODEDATA.PYD6 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\WIN32API.PYD6 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\WIN32PIPE.PYD6 %SystemRoot%\temp\m.ps15
*See JSON for more IOCs
File Hashes 0812d7585fa86a7b44771542d081456e9f604f1681ddebf9ccb030f928831a2a20983670981b721ba966513505f85169ccd8f5a8a8f5eda24385eacd84b2c34b20afbd232fc7840d6697d0096b2c058f5afdc00f36ab710822a6b7bdf26754e42fb126435f9559b4e22763e65b80c9815feb0e773e8870223ddfe9ee9e2e30a533a0b0eb31e2c161393101eb307e1f78587e0ea218e5e6b15b5edaf42c6ebaf63c692ef3256190fb845503d5cede33752bc53168d06f2ce3e2409718f9db311740e113847461dee589567b0a3613a5af4898e9aff023d532c2b415574d31c1b860b6d7664598e6a988d9389e6359838be966dfa54859d5cb1453cbc9b126ed7d76d9a482d149770fcfde8f69924db6bbf3439cff7859fe5b85073a219e880b6781e305bf5e9cf02f6698916b87279dafebda418c27bc095cc2e76be3bba7ae3e
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.njRAT-9993044-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 1 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 1 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}1
Mutexes Occurrences Global\10ce2141-c380-11ed-9660-0015177eda001 Global\122748a1-c380-11ed-9660-0015174353321
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]21[.]2001 104[.]77[.]236[.]1631 104[.]106[.]239[.]831
Domain Names contacted by malware. Does not indicate maliciousness Occurrences go[.]microsoft[.]com1 www[.]bing[.]com1 learn[.]microsoft[.]com1
File Hashes 030a6b3c97d78dcf19cddaa56b9165aca07c7edc2e2fe20cf6b86ab6e69fd2c70d91427189819eca8df5f972b86c34ea1a5843299dce10c5f73acbea6f3f07170eb69ecc13d46ddbc01560ba72d09854500533734595f235266157f334c87e7d164a4cdbfe7162772a75a91c49e9e89ee24ab57cf051169c76ca4d0b198caef81663196132f20b428e3f9beb0cba128e552be30bf1f5677ea69ece8abe4639651af57ca8bf6eef70b75d59de7d69b647f9b95f0591bc3b2e8adca1d33bb3024221e8bdbd188c62a86f88f3890e16d697b640b92ee73be8cc28727294b488519e23b98927a89ec4c226a72d5befe4810fa571ba51813c4f773a6cecc1ca4dfa062f306b32f0042b3758c4ce40332d298a1e1a7d0acdf8fe08472cade082e35e4931dc7dd2b37a39a8c1d8498783b9cd706bc65e9cbe301e60d613641dace1853d3412bd03d47e49c49aaf9045d2097e472e4cef20b8dc898eceff334e4d49443537901c8304910f76ea8bfead184754c2555f5fbcb5111f78c0796d5e15cb56e841b7ba20a6df8d264a91f199587c294d13875552264c8b514518ed30a4a085eb45a306e503fea7eaed91350d5ef2a2b493348a6389fd8305c2a8e78a4d9cda6451f4cb7ad0f142626615e0255a43c23cecf7e6c5d4e017342fd29910d0ea832352282cd59742a9b1ed4d14749660cab3b4354a9cc759dfbce88744ea7fc05e6556be94415da328b46f93544135c826d4c7c64b90dfd77f619dba35dbb37db77f570f3bb75222f6321ea67082f66868e81addf33f3be8d992405da9d0298000105d66001cce3d271cd04da046f98c8bef59cc7ecb8f0c38e56286e3b8e4902d265da60a89e95890861d24c04a7d6357a1886e9189d8d5730a74ef90487d72adc96025a61b34bd1a49884e4837f326348930c4a038b18ed8149eab5a69cac668c07136de7871922418b93b424899d27b936ced37a21d0d1f68f25d6e2d005c14d4726764a541aaeefec88d6324716d41b5b659863487a5ee688fdfa8513e1676c5739768eb609ffbbd3d27dd27325480031ba0a02e7b6cf741ba2b1173e4b3b20783e3dd77f13be64e3245f7ff00cd330cff616cca5435d4f21a09d270e7908525
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkKomet-9992898-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: WindowsUpdate 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: WindowsCenter 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: Policies 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: Policies 2 <HKCU>\SOFTWARE\XTREMERAT1 <HKCU>\SOFTWARE\WINDOWS1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B5OJ4L45-IEYJ-5QW6-B8W5-588P2B6V06M7}1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: SearchInstrumentation 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: msnmsgr 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{B5OJ4L45-IEYJ-5QW6-B8W5-588P2B6V06M7} Value Name: StubPath 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{P001VBYY-IAR1-8I81-VBAD-21LQ82453K22}1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: KeyWindows 1 <HKCU>\SOFTWARE\SNSERVER1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: KeyWindows 1 <HKCU>\SOFTWARE\SNSERVER Value Name: FirstExecution 1 <HKCU>\SOFTWARE\SNSERVER Value Name: NewIdentification 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{13UUEGCR-1KL1-48G2-S4E1-35H16U3U0CEF}1 <HKCU>\SOFTWARE\XTREMERAT Value Name: Mutex 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{P001VBYY-IAR1-8I81-VBAD-21LQ82453K22} Value Name: StubPath 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Key Registrer 1 <HKCU>\SOFTWARE\WINDOWS Value Name: FirstExecution 1 <HKCU>\SOFTWARE\WINDOWS Value Name: NewIdentification 1 <HKCU>\SOFTWARE\WINDOWS Value Name: NewGroup 1
Mutexes Occurrences _x_X_BLOCKMOUSE_X_x_3 _x_X_PASSWORDLIST_X_x_3 _x_X_UPDATE_X_x_3 ***MUTEX***2 ***MUTEX***_SAIR2 6O060IBVE63W7K1 Global\b3004101-c2ef-11ed-9660-001517b2b8ea1 ¡¡¡¡¡¡¡¡¡¡009999996660XXXXXX1 6O060IBVE63W7K_PERSIST1 ¡¡¡¡¡¡¡¡¡¡009999996660XXXXXXPERSIST1 6O060IBVE63W7K_SAIR1 ¡¡¡¡¡¡¡¡¡¡009999996660XXXXXXEXIT1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences domo123[.]no-ip[.]org2 fkzkedim[.]redirectme[.]net1 drkufhsdlifuvsdr[.]redirectme[.]net1
Files and or directories created Occurrences %TEMP%\XX--XX--XX.txt3 %TEMP%\UuU.uUu3 %TEMP%\XxX.xXx3 %APPDATA%\logs.dat2 %APPDATA%\cglogs.dat1 %SystemRoot%\SysWOW64\system321 %SystemRoot%\SysWOW64\Windows1 %SystemRoot%\SysWOW64\Isass.exe1 %SystemRoot%\SysWOW64\update.exe1 %APPDATA%\Microsoft\Windows\¡¡¡¡¡¡¡¡¡¡009999996660XXXXXX.dat1 %SystemRoot%\SysWOW64\Windows\update.exe1 %SystemRoot%\SysWOW64\system32\Isass.exe1
File Hashes 09c627a80feb17bdd1c691f08304bf3c0919f1d3649b3737e5e73ebfc6cb7a7e103a4c883a3e5cc1d26dc9e7b23515193897996328f9bda2f27f58ffaf21af4922d0086aad6339e4c70a5d1a8a52fdfe156be7a9ffd86570a6b71aaaaa71a56b352e169bdbb62dbee2403fbb6be19cfb5bb31d9be24aa71aaa8c597fbfb1923d733766323a2a60cc5f1e125d3f10dd1dd5fd435556f8931b93c6e444371b75847de1fed73d6386b7e6a8f0ddf3f2fe09f41c177a75dd3196871488b6e47110b4841b33cd462ebc256e13bc2ea1e0b7f5ce0caf4a92508f41f0bb5250805e2620886c390b9c6b0ed823c3281d90a2888419ada09bf425dbab5e136676fafd053aac0e95e4b26b3123a9254c67f847a58d2a7c76f1b86a4f695890e3e452f727a8b869f621ada391282aa15ad7ed33c9500f10be50e8d510daccfe9a4fbdd0878dbf6df03ede9cf7c85f49321221af2764fccf4a7ba41c938f6e3a284ecd1ec148df8e322d932dcfb9d562f2867cd07f24fbdb0fea5234567c5bd2aeb1179e739ae59fb24214fe51cebf80fed4ad5833ce896c06c5e5e8aa10eb468ec1a08d3af3ed7b55eeeb4428a084836790e97511f627c5f34d40b22647c680ef58f67eae70f5291f52a036f0c6af479557baea52adaf2375a8c0de4d5a5ca074256c287b32
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK