Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 24 and March 31. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
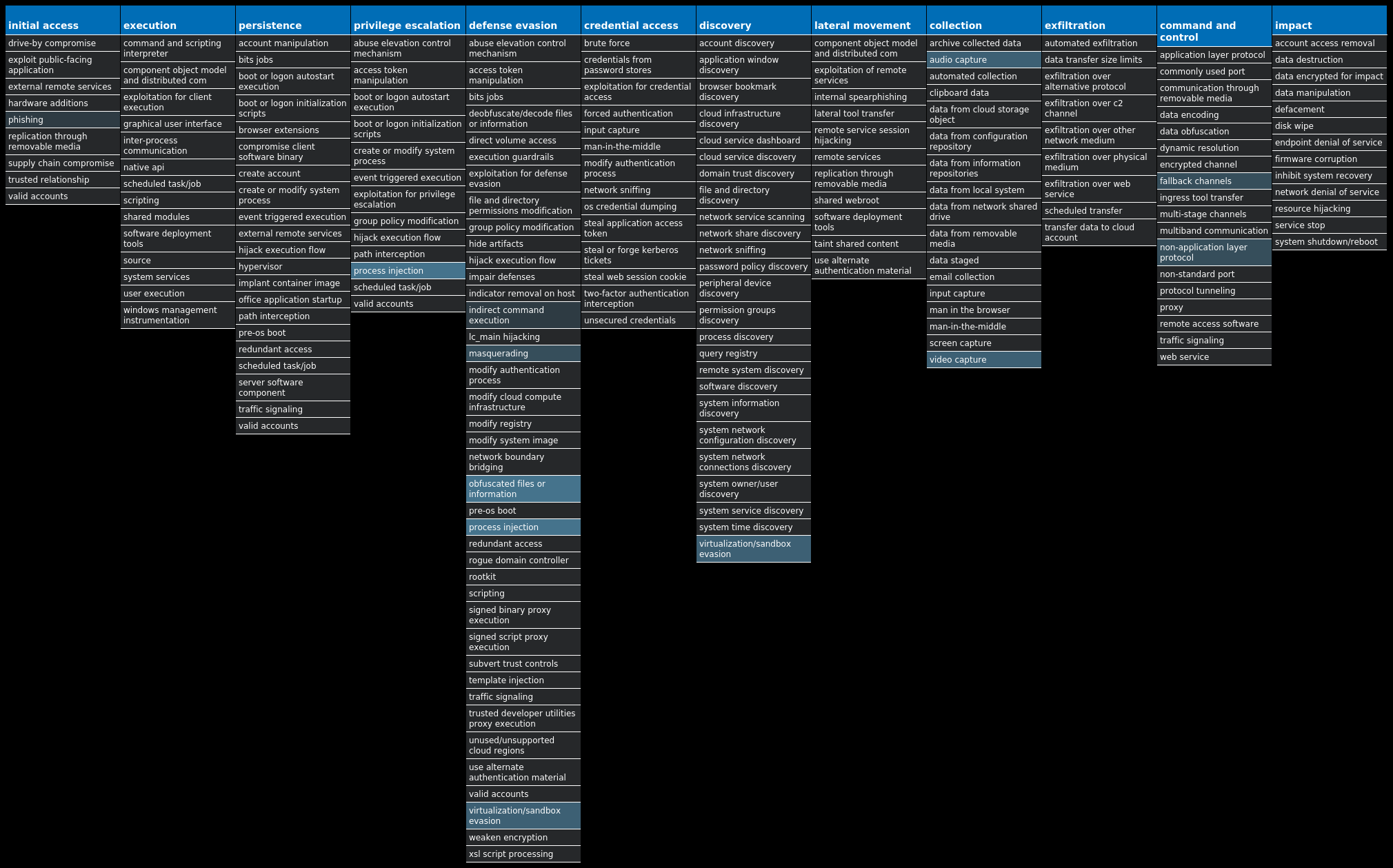
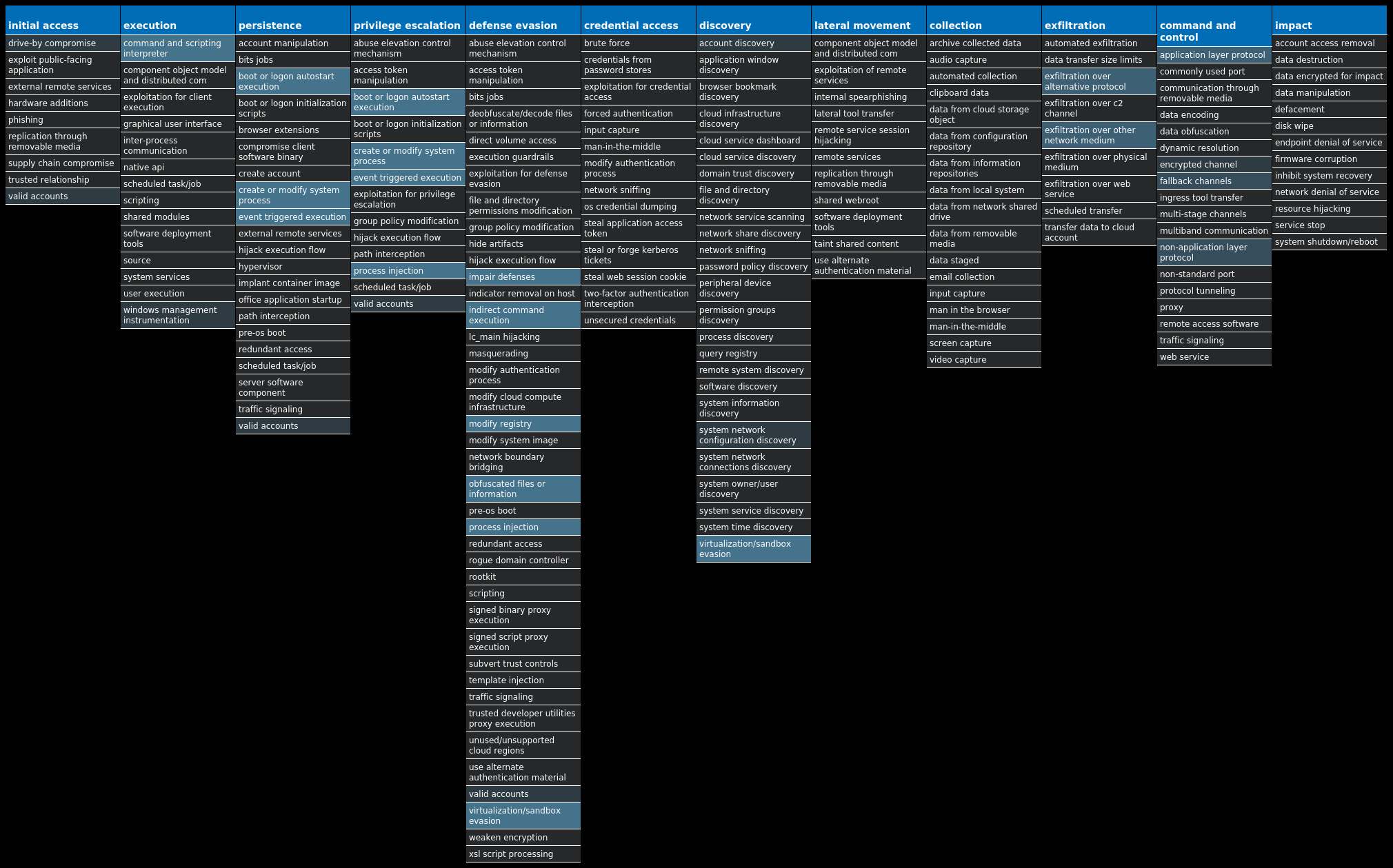
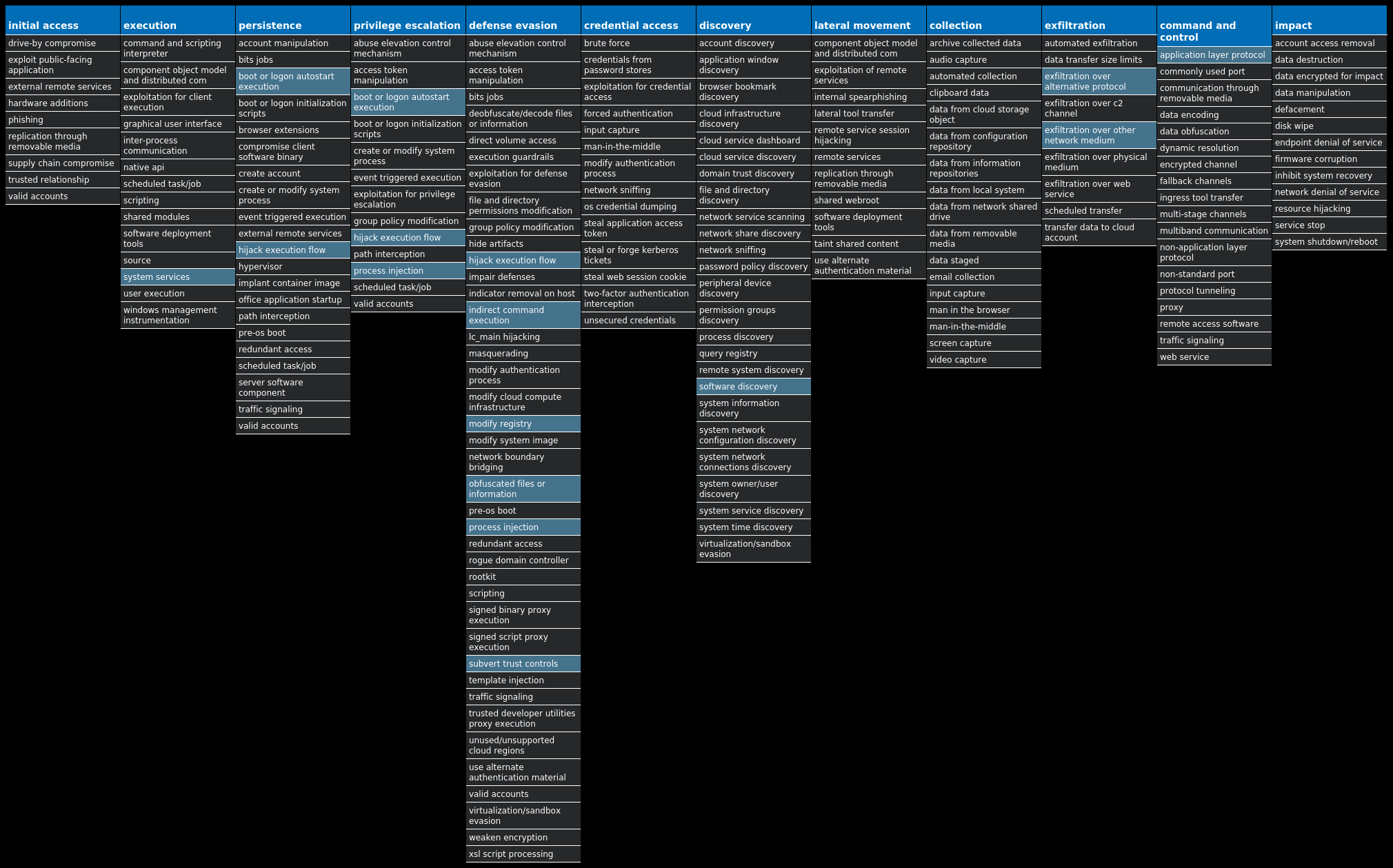
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Ransomware.TeslaCrypt-9994144-1 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Ransomware.Cerber-9994145-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Dropper.Tofsee-9994178-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control. Win.Dropper.Formbook-9994385-0 Dropper Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard. Win.Dropper.Kovter-9994588-1 Dropper Kovter is known for its fileless persistence mechanism. This family of malware creates several malicious registry entries that store its malicious code. Kovter can reinfect a system, even if the file system has been cleaned of the infection. The malware traditionally spreads ransomware and click-fraud malware. Win.Dropper.TinyBanker-9994341-1 Dropper TinyBanker, also known as Zusy or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information. Win.Dropper.Emotet-9994401-0 Dropper Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Dropper.Fareit-9994421-1 Dropper The Fareit trojan is an information stealer with the functionality to download and install other malware. Win.Dropper.DarkComet-9994524-1 Dropper DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. This malware can download files from a user's machine and contains mechanisms for persistence and hiding, along with the ability to send back usernames and passwords from the infected system.
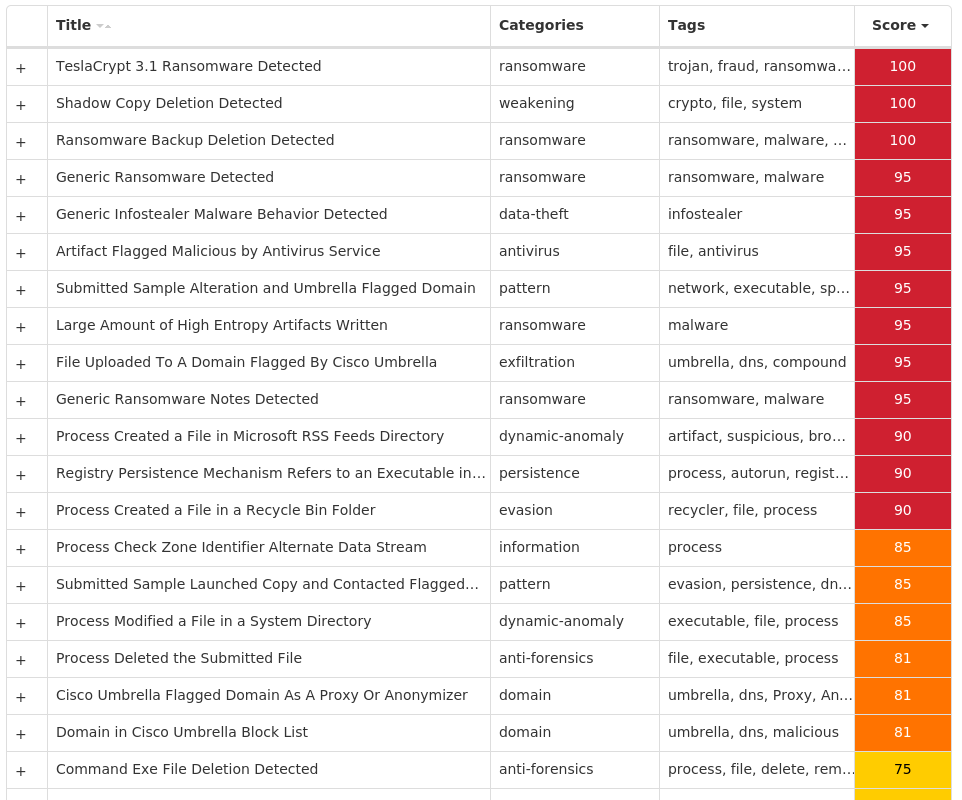
Threat Breakdown Win.Ransomware.TeslaCrypt-9994144-1 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKCU>\SOFTWARE\XXXSYS17 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: v23-deadbeef 17 <HKCU>\SOFTWARE\XXXSYS Value Name: ID 17 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>17 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 17
Mutexes Occurrences z_a_skh495ldfsgjl293534517
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 34[.]102[.]136[.]18017 172[.]67[.]137[.]13710 104[.]21[.]30[.]14110 172[.]67[.]172[.]2507 104[.]21[.]62[.]1657
Domain Names contacted by malware. Does not indicate maliciousness Occurrences mhomeusa[.]com17 internationalists[.]org17 csopedro[.]org17 fmc[.]org[.]in17 jecit[.]ac[.]in17
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\ka.txt17 %ProgramFiles%\7-Zip\Lang\kaa.txt17 %ProgramFiles%\7-Zip\Lang\kab.txt17 %ProgramFiles%\7-Zip\Lang\kk.txt17 %ProgramFiles%\7-Zip\Lang\ko.txt17 %ProgramFiles%\7-Zip\Lang\ku-ckb.txt17 %ProgramFiles%\7-Zip\Lang\ku.txt17 %ProgramFiles%\7-Zip\Lang\ky.txt17 %ProgramFiles%\7-Zip\Lang\lij.txt17 %ProgramFiles%\7-Zip\Lang\lt.txt17 %ProgramFiles%\7-Zip\Lang\lv.txt17 %ProgramFiles%\7-Zip\Lang\mk.txt17 %ProgramFiles%\7-Zip\Lang\mn.txt17 %ProgramFiles%\7-Zip\Lang\mng.txt17 %ProgramFiles%\7-Zip\Lang\mng2.txt17 %ProgramFiles%\7-Zip\Lang\mr.txt17 %ProgramFiles%\7-Zip\Lang\ms.txt17 %ProgramFiles%\7-Zip\Lang\nb.txt17 %ProgramFiles%\7-Zip\Lang\ne.txt17 %ProgramFiles%\7-Zip\Lang\nl.txt17 %ProgramFiles%\7-Zip\Lang\nn.txt17 %ProgramFiles%\7-Zip\Lang\pa-in.txt17 %ProgramFiles%\7-Zip\Lang\pl.txt17 %ProgramFiles%\7-Zip\Lang\ps.txt17 %ProgramFiles%\7-Zip\Lang\pt-br.txt17
*See JSON for more IOCs
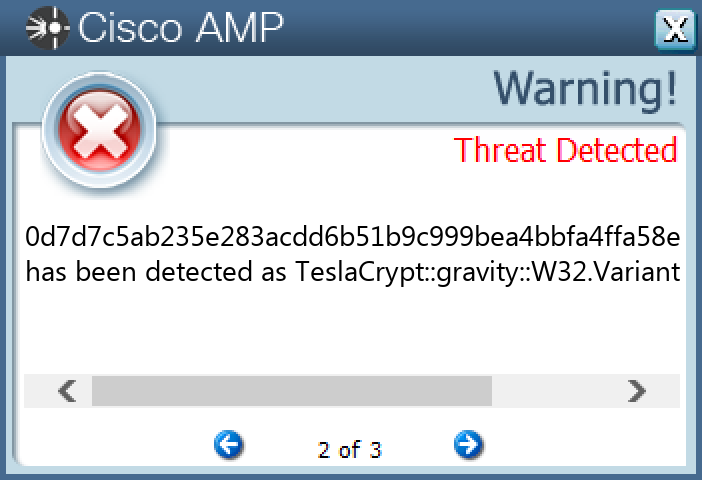
File Hashes 0d7d7c5ab235e283acdd6b51b9c999bea4bbfa4ffa58e03ba65a9908d391b20c1c84a83693148026c1c56d2bf1bbc42fc00b9c7391d86b46e0cbdf1c1b8205c71eedbe6ece9bfb7d1f4fb736a3ddd1274360fb932c5ecb1e843bea94c472761e35b2c9e1152704b48beff52488f94769213c0329117f4dd0a0a8e3781b63bdf43e55219fdf3b431fac2055cd3d3fe1df5cf8584688caeedefb42e4840e7e8e8245e7d31d51548b8e319ed3efe76c0a4a76ebbfe5db77d20cd4278e1ff53b40bf49cfb2ad073c9c3c54994b4d755e68b6bbf1c28ec226982a141a8645653e6965575aa40fddba7556541259211b0e65736592e615e60b8b258476e12e61c2950f69db0ecd9fb224db188edf645dfe37c192d06ff24ecf3d9da6c8fbc81b981a0d75740399485a04493a4c07432c8753368baec315e42394752428519147b811ab7a00e458f6cb3da91da97f2109188c3a70147aa6f22b1e884dbb81c9c78103ec8020bb9feda720adbe902cef6a807e7763d14c605cdcc0974e854d23cedc7d9c8243c174d73ae24698c901170463ac966c6e1996d45a480f6b1b11d726f54721a51ddcf639a4b80286119568577bcd1067e1be514c48d25c774da2a34fabc9c7a5fec2ff19af3099052f37a9b57b28edffcb6ab71778a6e3228cb020cde07972d911ab5357f13ead71c6cf653ac309ea2f04c4bec995bfbb54dfae3185cbaef7f401aa6387cf4860afe6a6c7c7d7d539c2d8ecff234a50e8ab6e5513ba620871
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
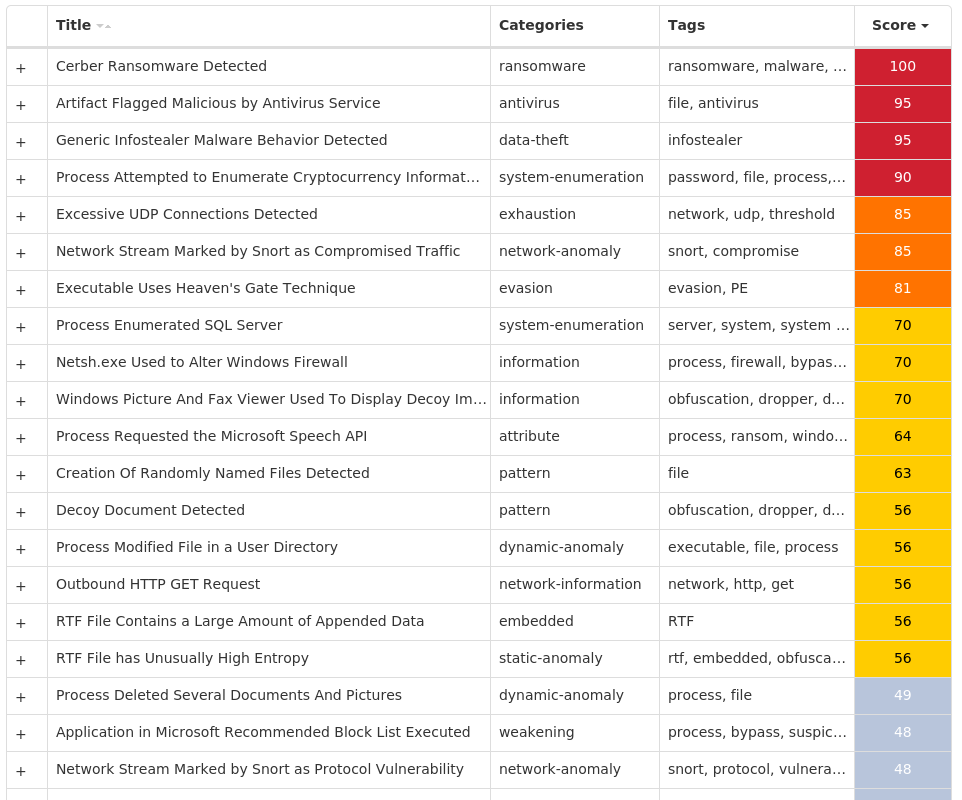
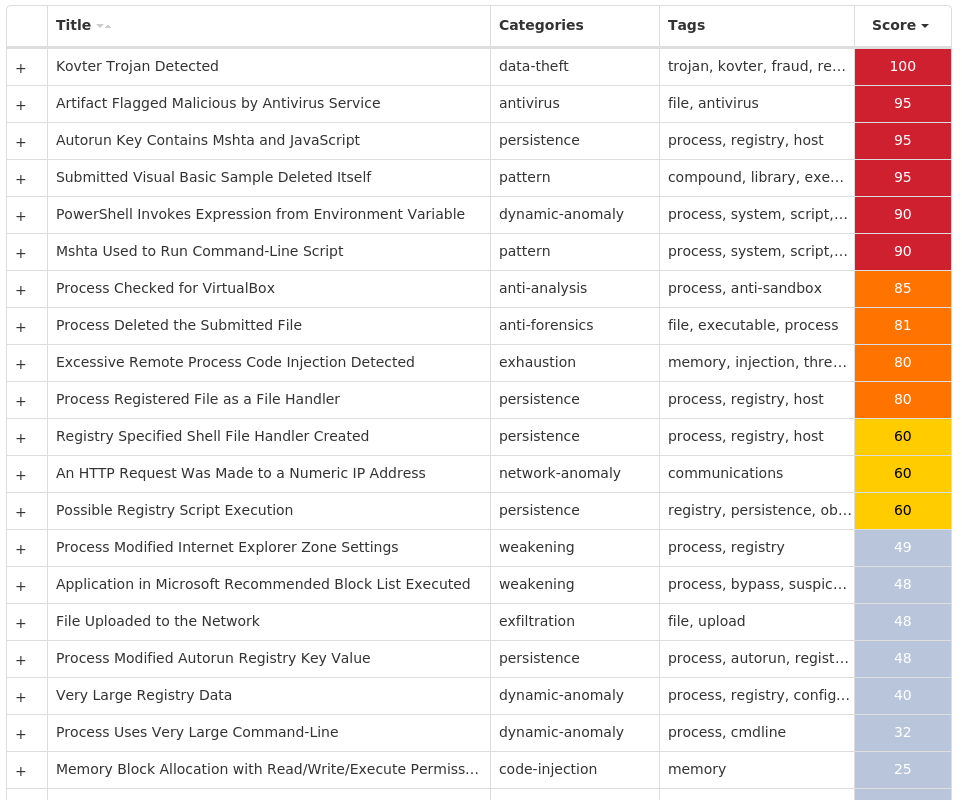
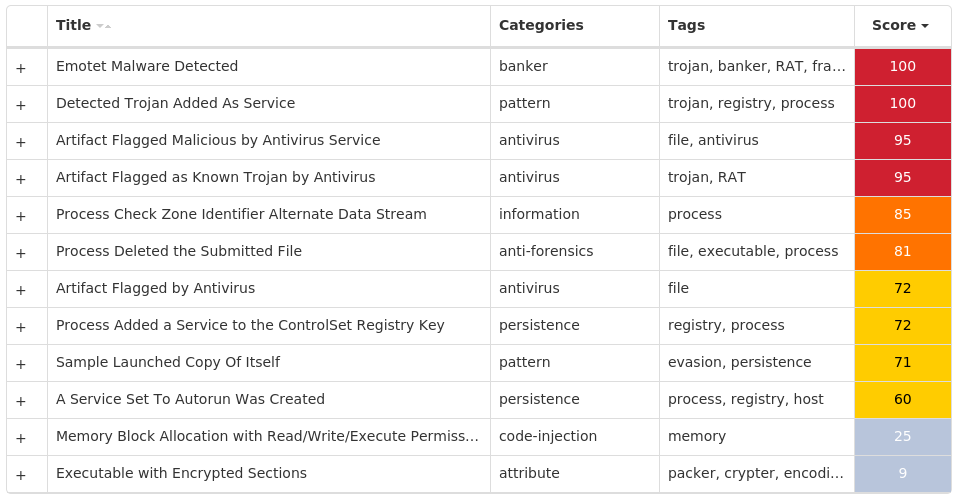
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9994145-0 Indicators of Compromise IOCs collected from dynamic analysis of 270 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL Value Name: NodeSlots 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL Value Name: MRUListEx 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\\1 Value Name: MRUListEx 2 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\\1\0 Value Name: MRUListEx 2 <HKCU>\SOFTWARE\MICROSOFT\DIRECT3D Value Name: Name 1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}270
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]202[.]64[.]0/27270 149[.]202[.]122[.]0/27270 149[.]202[.]248[.]0/22270 178[.]128[.]255[.]179202 172[.]66[.]42[.]238103 172[.]66[.]41[.]1899 104[.]20[.]21[.]25194 104[.]20[.]20[.]25193 172[.]67[.]2[.]8883
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com270 bitaps[.]com202 chain[.]so202 btc[.]blockr[.]io202 hjhqmbxyinislkkt[.]1j9r76[.]top68
Files and or directories created Occurrences %TEMP%\d19ab989270 %TEMP%\d19ab989\4710.tmp270 %TEMP%\d19ab989\a35f.tmp270 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat270 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp270 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp270 <dir>\_READ_THI$_FILE_<random, matching [A-F0-9]{4,8}>_.hta270 <dir>\_READ_THI$_FILE_<random, matching [A-F0-9]{4,8}>_.txt270 <dir>\_READ_THI$_FILE_<random, matching [A-F0-9]{4,8}>_.jpeg270
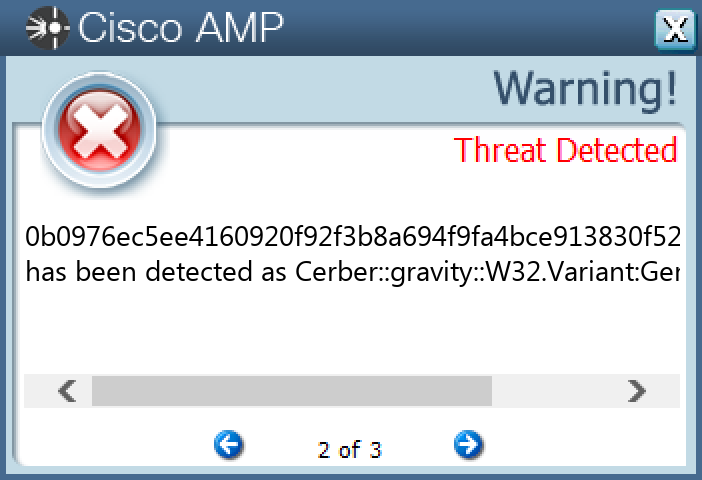
File Hashes 00b2a9bc73d10c724220de847c99f8756dcc86a245bd3b4e0f995510656f788f00c7a7771f1f91494ead2115edc791ca35af078b929f91b408b9f11006cf83b50181a14708d21ce9ed344d796561e1359528949b1b09dbdc6ad9bad98988dfad02444554961bc3b4ba3a6c8e2e85266cac482acdc0d6e2777187ef746ca1aacc02cb2d24044d09e98c92869e78844f8b1a598410acf7573a5b5ea0f0714fff6903b3e35f1183d76c14f9d8fbdf17b87b4e0334483e1a51f465fc97de6d607c4503f719cc549c461a71c1d8f7889792d2f54ef571f8082abd8cdb00613d913d0e04e8daa018dca72480648ab5a8c9de4491921e3250fa5a1cdf9ddea234dd1d8105bca297ce941c298c72004a3e9b6567053e740967040e635b3ba3f3fa03d6260833239e1520b5c9980f4c096f1081164501563df78dfcf3b710f4a203b53286086166e0e02f55dd55f88dd6c974d3ea173db043f019c406e71e1882170ff1dd088c4bfac4fec6b1a436613ac926e56d9535eca28f582ecb1bb9e80c8796ebbd08c7f732210c4937cb948e29e2d222e915fb6d254a7ea6ee5838560dc734728c0a33fe6dec023f8a23080a63292ae48bd0df5e650f95834f6f9d6481347526c10b0976ec5ee4160920f92f3b8a694f9fa4bce913830f528d899b9387ddacf5940b7f32eaa6873c4802aa6d52fba60bb9d9121b3901d271fc4766d451f34009ad0c07020e2cba9d84d45e0014618d42d85dd13c274aa80d8cefa961f9748ef8750da012fc6f89c175ca4693e89c576a43195818f1becefbf281e6d822d0bd19950de70bd123d23b51d29279e8b3b6c13028b0a119d5eb4356e35111c7f2a533ea0f0131f7938c6e69dd178fd43b3ffbd29615054c8841c5e44a022ff4f096c8f10f2a33db939580a739ddc4fa7cceaa29720305645b9b830d3f54555e8479caad114f9dab0eb8023b81dd818503eac74386634900ab2b47b6768254d6424b3b4e11b048fc725ceece2e24c5854c034abe891346af56e68b8d7ca4fabb6fc183e511c097a24e5eb0258824c2a5f7c31583249028dfde0762bc058a93946ae34bb211d27031aa8515af44fe76345881d5c3fca5f44429187d592cba786f14a72800
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-9994178-0 Indicators of Compromise IOCs collected from dynamic analysis of 84 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 193[.]233[.]20[.]3184
Files and or directories created Occurrences %LOCALAPPDATA%\Yandex84 %LOCALAPPDATA%\Yandex\YaAddon84
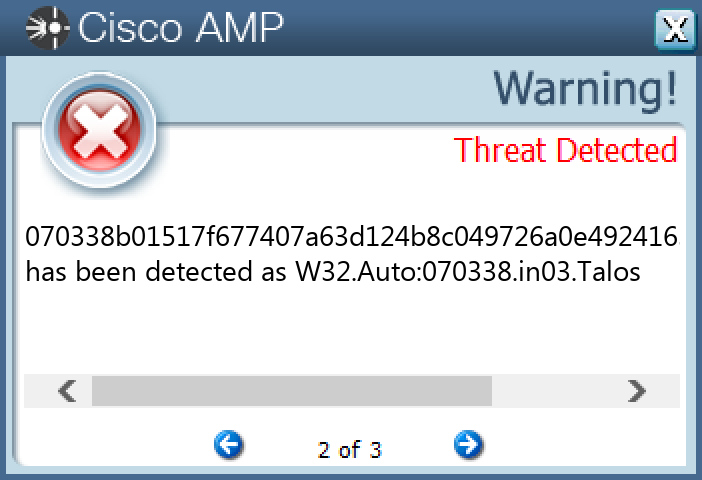
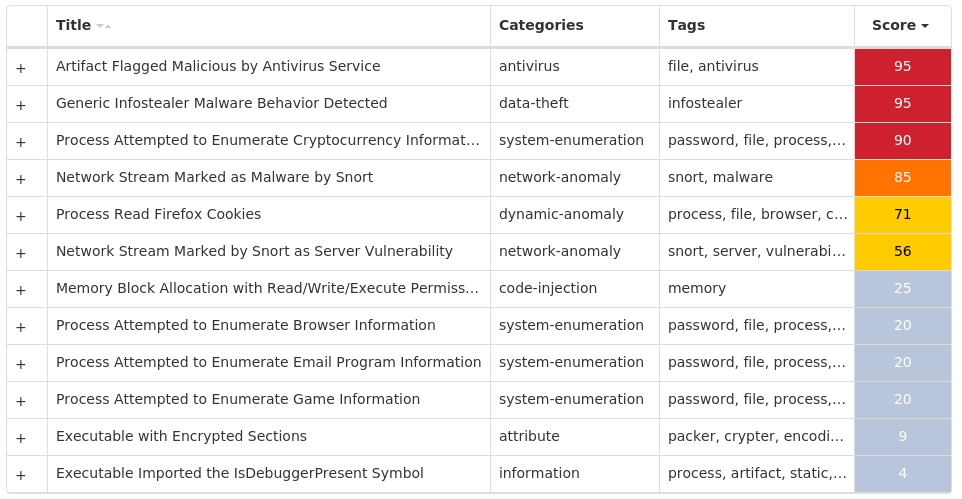
File Hashes 0470c3c5b735b2c1b5b07a833941ef7e9ac9fc8333c12750b88252b7a9d8876b070338b01517f677407a63d124b8c049726a0e492416353bf50fa6ed7b20a0c70e843a71040bf57a24197afd129c26ca5065db2bbc0e3540626199f129b4ccd717369e3c91a3461e439832e1912b984c4e0bc1526ce48f6c2a7937565e00179319208e193ccd5d6a10153d8d3a3f9075846ba42ec42f27a915857edc19f5dbcf1be4e71e0c832208b940e817cf2489fcc904a2cc8bde5e12f85796039001e5d81eb5a9d34f001ece2d934d6759b92e57e3aceca91d93d76b86b423126bf29f8a32c082e92a74b3ef0c29663cac017adcdb99fa86c92d75b95b67260480d1f261349108a8623e59e3baee540b25a123a20c338b70a2a910da5900bb77e4619d213e1f8463cc20fdbce750170e1031074c1ec3f90482c2f05d55874d8510b039f840e48e71e057fa7159cc542572b2f54c25b2e7b43773eae757fd9f58cad303ef437cfd2d9e2097f1bf9498be0df782dc03617eaf47d6f0daa5addf5bbbce9a9e478ac6974c3766ee57e79ce003746f6b66b43cfc4c41cacca4ca0c78c9f6cc324ace3dd384423c110374abc61995c48618cb445c031ccdf6fd30cff5658968cc4cb3253cb09d4765129b3379abae653a36da1db27b3dfc864606687523900cb14db03abd586331ffe27b89bf781ff665675a8d81259984c5a58e0a39e449b4174f38c1bfa2a03d4e8b15ee2b3b85abbc667cf26394f8eb99e8217b3b3611ed254f6fe789af662e534743301d78f6b99baf0db39a542ea863e04511b99e4e261b541ee37ecc69c60dca2c48e0e7990e2c7855cd709157896cc92e677d8484217c543b84ef95aaf61436fc96073079a9ecfad60e55e77fc344f158d8426813dc375a1a019c8d099f5ba8a1a00e3ddca09f846db3af7e85f0312ca33df6cca6894a5bc939edc308a59117f64c60b0897994a81d0d647b467a02558c31af281431f3601a19783f711defe03791f2b6b628d7488528ebe1d66b20e460d468ca888eeb691fd63aa95063cdeeb6e0b8c4b8be80713bebadd51fae4d9cb1de8d6509b2aa726fef5283dd616e36f64ea50a8afc33726265ed60574f796546b3c0d30b4df8
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Indicators of Compromise IOCs collected from dynamic analysis of 28 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.IMAADPCM Value Name: fdwSupport 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.IMAADPCM Value Name: cFormatTags 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.IMAADPCM Value Name: aFormatTagCache 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.IMAADPCM Value Name: cFilterTags 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSG711 Value Name: fdwSupport 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSG711 Value Name: cFormatTags 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSG711 Value Name: aFormatTagCache 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSG711 Value Name: cFilterTags 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSGSM610 Value Name: fdwSupport 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSGSM610 Value Name: cFormatTags 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSGSM610 Value Name: aFormatTagCache 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\AUDIOCOMPRESSIONMANAGER\DRIVERCACHE\MSACM.MSGSM610 Value Name: cFilterTags 12
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]214[.]22[.]20812
Files and or directories created Occurrences %LOCALAPPDATA%\SbmsftwVp23 %LOCALAPPDATA%\SbmsftwVp\taskhost32.exe9 %LOCALAPPDATA%\SbmsftwVp\system32.exe8 %LOCALAPPDATA%\SbmsftwVp\Space.o9k6 %LOCALAPPDATA%\SbmsftwVp\pcons.o9k6 %LOCALAPPDATA%\SbmsftwVp\prova.o9k5 %LOCALAPPDATA%\SbmsftwVp\chrome.exe5 %LOCALAPPDATA%\SbmsftwVp\sc.o9k2 %LOCALAPPDATA%\SbmsftwVp\chrome32.exe1 %LOCALAPPDATA%\SbmsftwVp\pcons.au31 %LOCALAPPDATA%\SbmsftwVp\Usertemp.txt1 %LOCALAPPDATA%\SbmsftwVp\Istat Febbraio 2019.zip1 %LOCALAPPDATA%\SbmsftwVp\Usertemp.jpeg1
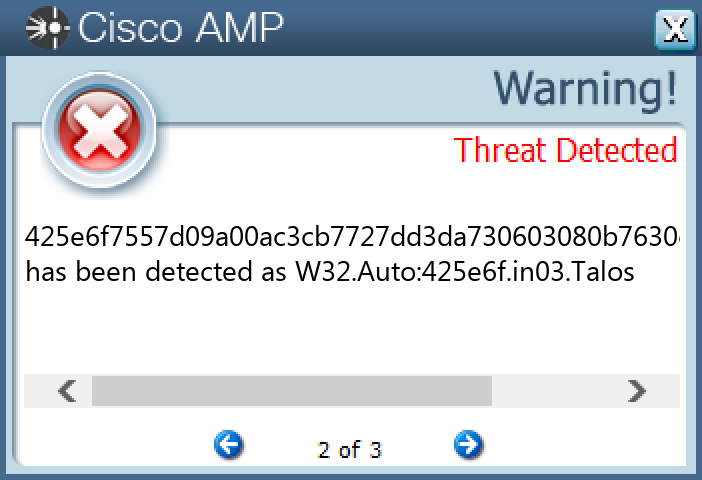
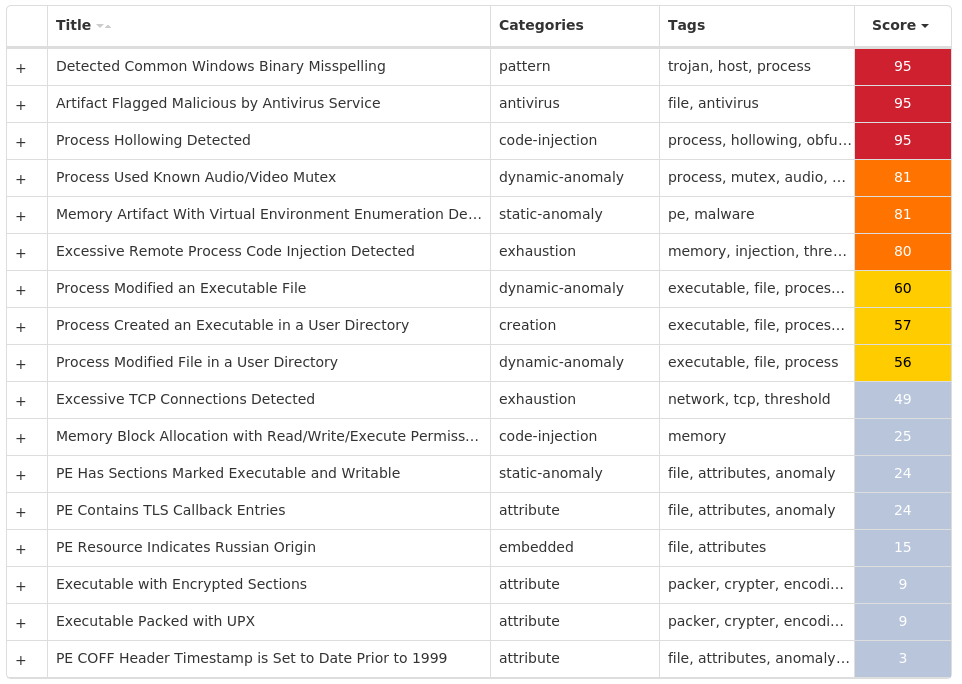
File Hashes 013fa0a93b28f8b58b2ba0009fc127a8928ec7fb8d9985b31caae3c99f41b0ca0860f64fe287c02077b8345dc0b2b8b62b65f24cf4acd660e34c1f5e0ab2094810f484b167e53ac7d1ef580b7db909029043e3c84ffe6ff8f9ebe61f3f05a1d012fde2a7b8717082f257b389eda1b8a6cd99e300755daacaa4f2cc1f9433a22c13f3049b1b31a8a8a37cef64f1eb56e0a33dae9e59793a438dc2c693ebc380af13f668c4dcbf3056829a1429ebe500c77c8c97d8f8a6c2136371cca3fca3f4501a00c3e800f895618776eef85c292d242931af16504fe0867e032441967f077a1f6e4f8a970816e178d3cc15b970c1e124d91ff49de09bf37158ea64499484e321238f4dc280260c83300a79ef7b8835b5984886ab74f0f112f5bd7e8113cd7c2b4df32209f34e7adadc69c2ea1e3f810b4f9f5e89705f047dd54aa97020c1362b6bae898a46d6b10fda70b3ce23e6c4b53c3f1ccd59c2c848b1d6b7ab68dbf52c44b9a7fcbec0ef6f5251dd628591dff7dacf4a8a2108c41c4b5d7e134ccec03a3dfd35e5746024dbddff2519744cd86188516cccb0632ed8c1483ed1bc8d48425e6f7557d09a00ac3cb7727dd3da730603080b7630c5313d5014b631e5b74e438c3344a14bda9737b01d88332759365671c3f32e913347939880bc2c630ba84eeda267847e114344ffdf4dff447e2b03fa58defd3af1d787e9b05c2e12be3e603641f8a14199a2d850f9eb6c3e987ae10472c1b1f4296a046245184a33990965e2243e22224c73e8ce43f16a2906fdc7818acf8f12d56f104c9f19ee88c2ec7137f1f56dbc98cbe68c211ca6743417dd01cb81d7cd772e36b2785d61acce2a7987e2e41a89e067688c26129a44575063e371aaf91fb27954c10711334bfbcd801c703b5540fc3d95b54c79951990c6d53f49c0175e4216f0e0019e04c51f6698732b1197ffce108241b175b8104c36e40e8b191d9f9d6104702e144a079c67a4499806ed8d92e212733ec8605e1028d94a1b2b82bcc98776d42ad6e27bb9bba469a0197cdab036e7d93a9da9ec9113a78b9e58ce024fa15078879a0035244da614a8dc837ccb52330bd6cd4f5732dbaff6cc94bb8ff1ca738feff50cfb0fe6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kovter-9994588-1 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DisableOSUpgrade 20 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE Value Name: ReservationsAllowed 20 <HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1 Value Name: 96f717b3 20 <HKCU>\SOFTWARE\3A91C13AB1 Value Name: 96f717b3 20 <HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1 Value Name: 656f27d6 20 <HKCU>\SOFTWARE\3A91C13AB1 Value Name: 656f27d6 20 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN20 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE20 <HKCU>\SOFTWARE\3A91C13AB120 <HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB120 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE20 <HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1 Value Name: 01b2a448 12 <HKCU>\SOFTWARE\3A91C13AB1 Value Name: 01b2a448 12 <HKLM>\SOFTWARE\WOW6432NODE\B1941377BA1C30B46D652 <HKLM>\SOFTWARE\WOW6432NODE\BOPM5S2 <HKLM>\SOFTWARE\WOW6432NODE\B1941377BA1C30B46D65 Value Name: FD99B600636C23EE61F 2 <HKLM>\SOFTWARE\WOW6432NODE\BOPM5S Value Name: ugLIgu 2 <HKLM>\SOFTWARE\WOW6432NODE\BOPM5S Value Name: b9yMBZ0 2 <HKCR>\BGWJJ9Q2 <HKCR>\BGWJJ9Q\SHELL2 <HKCR>\BGWJJ9Q\SHELL\OPEN2 <HKCR>\BGWJJ9Q\SHELL\OPEN\COMMAND2 <HKCR>\.KDPZPKZ042 <HKCR>\BGWJJ9Q\SHELL\OPEN\COMMAND2 <HKCR>\.KDPZPKZ042
Mutexes Occurrences EA4EC370D1E573DA20 A83BAA13F950654C20 Global\7A7146875A8CDE1E20 B3E8F6F86CDD9D8B20
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 25[.]184[.]178[.]2092 65[.]61[.]21[.]1262 33[.]59[.]53[.]752 148[.]95[.]103[.]1572 208[.]83[.]179[.]1772 216[.]141[.]67[.]2212 33[.]9[.]30[.]1782 214[.]113[.]157[.]332 128[.]196[.]44[.]1892 106[.]167[.]173[.]1072 124[.]79[.]107[.]1722 78[.]178[.]65[.]242 43[.]210[.]195[.]2002 29[.]196[.]11[.]2082 123[.]75[.]123[.]1822 208[.]102[.]210[.]1012 193[.]94[.]77[.]2532 172[.]49[.]78[.]212 8[.]47[.]183[.]572 108[.]7[.]213[.]2432 145[.]55[.]254[.]1532 184[.]181[.]140[.]892 34[.]32[.]121[.]512 115[.]68[.]254[.]1112 159[.]177[.]136[.]2052
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z0-9]{3,7}'>20 %LOCALAPPDATA%\wega\Kp45cE.kdpzPkz042 %LOCALAPPDATA%\hori\SwPObjKl.Nlb2FsB771 %LOCALAPPDATA%\ogehu\Fparl.SKiGlq1 %LOCALAPPDATA%\vamu\w5nuC6.WGTurLb1 %LOCALAPPDATA%\ajogy\qGuhM3.GTfDMEKB1 %LOCALAPPDATA%\uxyda\b5AtmVw.x5QJb1 %LOCALAPPDATA%\cezihu\xQCDfCA.2MaJY8E2C1 %LOCALAPPDATA%\vife\cX83.5f908v1 %LOCALAPPDATA%\oqukot\B6Jj.9dBlAf1 %LOCALAPPDATA%\ejahu\AXBlFqTI.g8zXYu1 %LOCALAPPDATA%\ihar\QeVvU.1bLWpC71 %LOCALAPPDATA%\venivi\qwYoqIq.Ebz3M1 %LOCALAPPDATA%\ozul\2ZQDlBeW.fDMBBQqb1 %LOCALAPPDATA%\jazy\pyBDe3A.bVyh1t1 %LOCALAPPDATA%\itoxan\9SqRjetq.xI40Zyq241 %LOCALAPPDATA%\ilet\9G3Co.vEXWb4JxN1 %LOCALAPPDATA%\ubil\lTWPpC.foeSI81b1 %LOCALAPPDATA%\uryfip\083ieXW5.S3s2vE1 %LOCALAPPDATA%\apejer\xNSKBdUF.Wk2F8ZHc1
File Hashes 05b59f2d2f563bec3929440f1934a0e38368e2d2a9846a04c4e23097f72a4bb21345a0c98f9346ad900072aaeba96b760d26fc4b7e8ed89950fcf41ea8340c6524c2154b70a3ce56ccf1e42a6ee993a6e76c31ed6b4560bc7ca0247c05ccd6f641a82b412860774b20bf9562b453737d83f8eed41a54b87718580b38c53ff42642029c42a98766c0ced24f34376fc46c64bf91e81f4d4a446eb883d2cec24d6360941f0456a5def136eb637a846a0d05d6f917729faa2c015347137bc3adfd976ceb7ec11282ed100bbd6d155ac6950f312ff35882bf57ce6382a3e28deca1dd7e98d8fe61e2414e89a6f8d40a7f4b2565367768e726b91cb32410e7386e97868492e74830e9524e07ddb11891b7c13bb88f2d0531241c878a39f3e9d509a4ac84eee3d947706aa43cd9166b753162f807654c16fa4a956198c22f0fd37141968ec2235e1542206870f1176428ef361fb1e40a2f27b18a70a8bd97c6811a68b0b93995d399154fc03b78501998173db0286b89bca3d1f25589a50100208f05adb9d086647099a1290d07eae291d976c2ee9783c1129ae529ee08b55184302b7dbd1d4e24da7f0e753ecdfab3764c5ac0953c7746a67af82845435a8c3ad29c0dbd2f685746355f614886a16466a57bd2058532b537a1f7293161b4e9f0af9ed7c96ae9fc37071f091a7756331129930741f2c7e3452390f9f948107f181385e5da7f437578196e4312b752fdadedc3f5c94654d6dfb3efe6cd9a01241405a8e1ece7a983dd9e1d0fe4fd1b766f3b130ec35eb885d351ea224b2051bc08c45323f014cc63389f1ef11379e783e0e36477741aa22bebac5addbea73ce19eaa6d63fcba15982a854e57b6d4f65404de3ece75e38b8d4b671e67394961ec22fa6d65
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
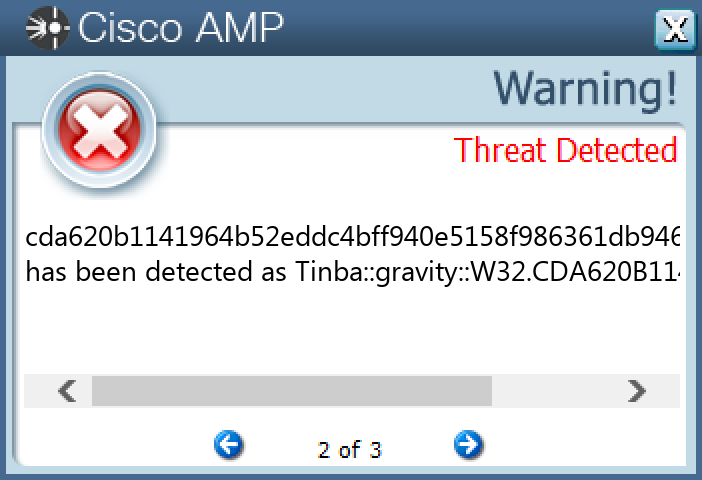
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TinyBanker-9994341-1 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: DA81EF4C 15
Mutexes Occurrences DA81EF4C15
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]google[.]com1 insamertojertoq[.]cc1
Files and or directories created Occurrences %HOMEPATH%\AppData\LocalLow\DA81EF4C15 %APPDATA%\DA81EF4C15 %APPDATA%\DA81EF4C\bin.exe15
File Hashes 01f5c62a2fc27a2b82ce42c823ef956b65571a8f4691cb662fcf3731760e608c167919de0c9d3bd508e9018bafbb029113740a28b4885c0ffc0b2e2d9119cebd1d5c53442df1c48bd18dd95753e74dbb226d42642301d078a359af04ece859581f70cbd79386ba8b4a13d9057be77762d55e5b9dd9f8874cdab4bc65abab5e4d309f2be8022f4083f03730628d40032e5c404d5e9bc088cacf5bb2c3d99df9d85c74d0399e10b4c6e76e4853c202eed2f2e1855661e64ee3731f2eb4fc3db6376a9b98c034e17154a69737e655f7dcfc07de0be68f2547e32b29cc36a5fe5f866bf18453b330e349516a4ece2841ea72e904dff6facc0f905a2150fcb626b8fd6c0596e9d5a209a13e3c1a17b01d28273b0ec680df9004fbe27ab2bf2f3fcddd88bd0c5645eb63caea334084e3031d066d712edc64884f8626886ffce9ad7e27c461e50c6da421b2db71c6198a5661d25948e1c29911c2827d794799b57faad0cda620b1141964b52eddc4bff940e5158f986361db94631ed0f0816a76c7f35ddbc82464eb2e12a89f1bf17b17506bb3fe9e4c514c230f7082ea517af8ab10dadeb0de847b202a1bf0b53c86d921847e82df971c6e5d5cc0c6a06b7f311e5668e7b73464492ff2674a94d95f6805e57bf2cdb2228aa58e6d05bcd713f2331029
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
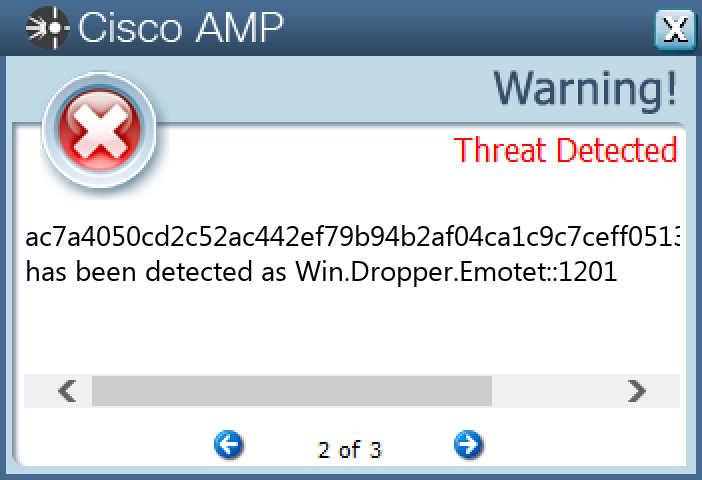
Screenshots of Detection Secure Endpoint Secure Malware Analytics Umbrella MITRE ATT&CK Win.Dropper.Emotet-9994401-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: Type 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: Start 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: ErrorControl 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: ImagePath 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: DisplayName 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: WOW64 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: ObjectName 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM Value Name: Description 18 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPECSYSTEM18
Mutexes Occurrences Global\I98B68E3C18 Global\M98B68E3C18 MC8D2645C18 <random, matching [a-zA-Z0-9]{5,9}>18
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 82[.]211[.]30[.]20212 119[.]59[.]124[.]16312 37[.]97[.]135[.]8212 69[.]45[.]19[.]25112 217[.]13[.]106[.]1612 37[.]187[.]57[.]5712 193[.]169[.]54[.]126 80[.]82[.]115[.]1646 71[.]244[.]60[.]2316 84[.]200[.]208[.]986
File Hashes 01593a61dbce3e76fc877e41431e50d3b4be87624d90a9775506d4bd71d2760a0b27f786515e584d7d9be20bdb257cf7d530c04a50d1d6794e740b5f73a57acb0ff608f42d1dd85c3f37da7036029364df52deb8f299ef80693fa8410f27088014364e6d3b68bd897229beb3cfc403a97619159cd53eb743112e3e1aef41d91c34812e948f6ce6f5fda8bb18b075e1ebe7edd54db906b51eb27e2578d837201b3a7f15244ba98d41b5ff3e8923257a32c8c6e67708a156eda7e5cbb3ab44d34c47f6b6f2a25fd83e38ddd870f534da9c54a5ffda8904b46f4bdc10429fc3fd8e4d94ae394d3807f3825d4c98e146bcbc17dd60adfdf1518911b4c400b46d77585325f15a05b95eaefa9855f12413efeb3ecc339a41d3147676ec520db4d08fed722786cb4c08c942596925e8da8a18cd829067c6714b951fa128311812c24b6a7b0167a29632a92652aabe3b8eafbf98cb15e0dab643bfbc0256a77be76942587ef2a1f72aa702765b9c71b1a1de8db472650c02ae15eb70270b80f3c02f0db585fbacca424b9c58cf9ab6feeb3497d15529e6560b33a66f7f4c0458c80d52279349ce2527350b9c71a2b55ede69016bd463be73c019130fcb2790903f5abd0d967733f0c45d0e19b53236d014f40543715e58d9e9958efd0a07723aeaa5c572ac7a4050cd2c52ac442ef79b94b2af04ca1c9c7ceff05133c62fdd109907bc2de1132e32300dd6d0c780cf91906e641d04dce598ee5d3ef7c6d4a70713d07132fc10181166fcf7253033da27bf25c1df2ea717704403331537768f231066c150ffab3385e090744bb39a48f3cf1518363d17a91e24eb8c437ec96fc4dcd39487
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
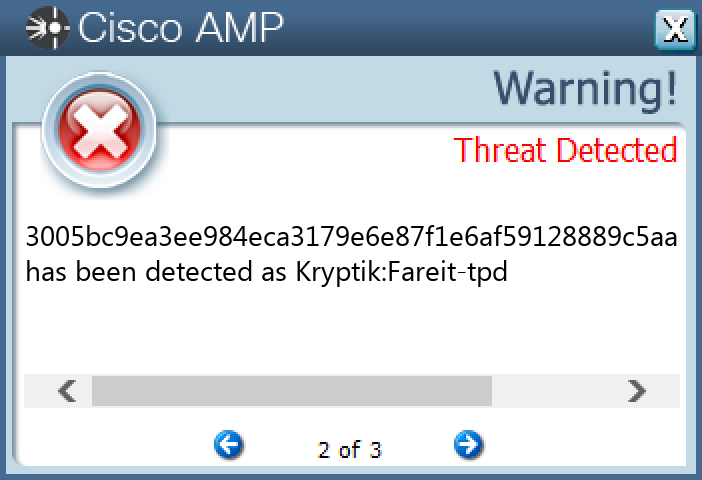
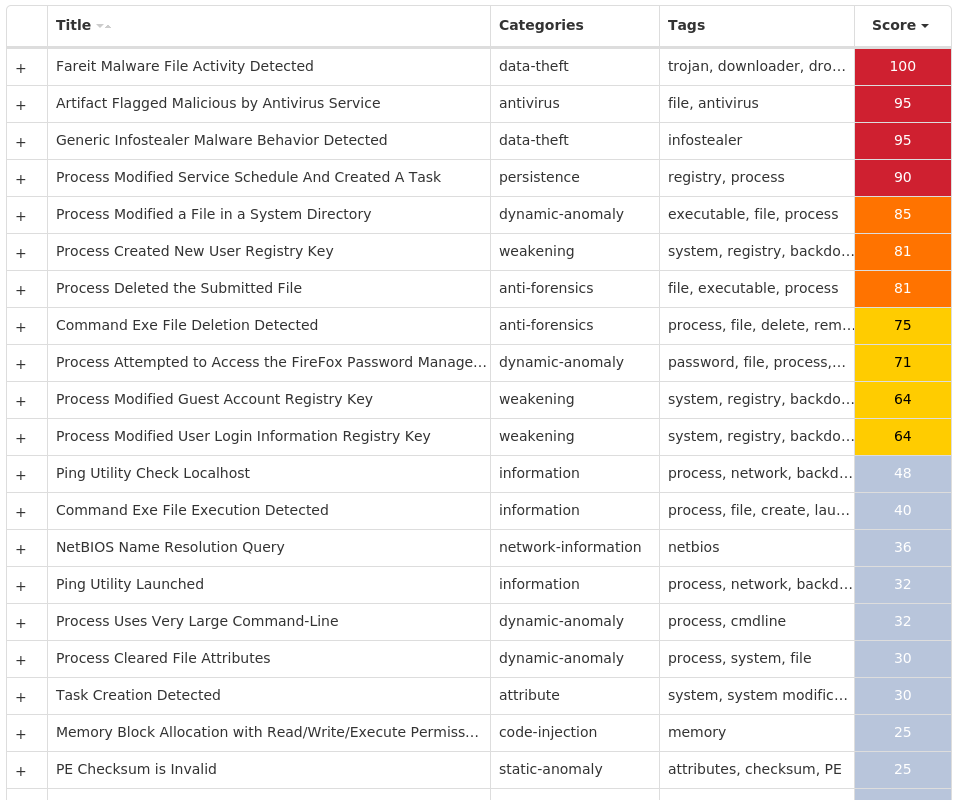
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Fareit-9994421-1 Indicators of Compromise IOCs collected from dynamic analysis of 22 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE Value Name: NextAtJobId 22 <HKCU>\SOFTWARE\WINRAR22 <HKCU>\SOFTWARE\WINRAR Value Name: HWID 22 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 22 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 22 <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 22 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\\SIGNATURES Value Name: At1.job 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\\SIGNATURES Value Name: At1.job.fp 1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences splwiu[.]info22 slepoz[.]info22
Files and or directories created Occurrences %System32%\Tasks\At122 %SystemRoot%\Tasks\At1.job22 %System32%\drivers\etc\hosts.sam22 %System32%\drivers\etc\tmp.tmp22 %TEMP%\1272824692aq2 %TEMP%\1272825253aq2 %TEMP%\1272824536aq1 %TEMP%\1272824926aq1 %TEMP%\1272822757aq1 %TEMP%\1272824661aq1 %TEMP%\1272823491aq1 %TEMP%\1272824083aq1 %TEMP%\1272822445aq1 %TEMP%\1272822461aq1 %TEMP%\1272822289aq1 %TEMP%\1272822945aq1 %TEMP%\1272832414aq1 %TEMP%\1272825768aq1 %TEMP%\1272822804aq1 %TEMP%\1272824395aq1 %TEMP%\1272822835aq1 %TEMP%\1272825955aq1 %TEMP%\1272826392aq1 %TEMP%\1272826891aq1
File Hashes 06d493c3c386cc9b4a79bf6210c1524f2a68096262666213e7941fc09fba692d10dcb4196b851ee45e194f39d321a873c6d5c17b146e129ff8c231506e7e135716b8f159ccc693e8602b31eb7e04f47d2db91ca37848df223388915478e8990b174ae749aa2e208acad6c027d3977d0c22d6b17045ba72ee8f707695d5cdbe851b97e18edea5050fc61daf4c599ba25529c0a96382468d2463cb2bb1f74f404b200435f84a6648abb8a55ff866373bbf3a190e76e2e60ff66e77360bb303c2ec3005bc9ea3ee984eca3179e6e87f1e6af59128889c5aa11d91b36b0ff62c00d24306980b56c70ee90d09e346efa9c4014ab4802ecc30c2c2f300cc410484a0704508a96887fbfdf1d89bbf15bf1574da9a4d96abc51676848023f6ae4b5e090f47c486a892f16b4244ada411669b9d785da83d71e2cf7bbc3e1192683cb59e684c96c23ece92a8ab414394a0a04402972145bce768012bb006d4622d9e46cc764ecf1bcae86f6a571312f5e0f2fb2387e66312c06976920daa74e9247f7fa6b15d611d8d139e50505c9ff71c08b3fa06824da478c5331db70e568c358b7c603662905eb2afc58013d38a4700d67b8607e6fdf30c68de86a50173bbfd9a870c5b987a723c2d4c604367b28950eb7c70852c47346637123aa3f84a5d120912b583b942e291b9b446c7940bbe8e31a8bda034337c49839ecaeb4bb03715ea8abc4eb96194cf2dd05d226496c04a6a1307d703c3017c1a733655d4e14916668b5dddd736fc9cc5c87b1ce6f9addf8cdf6c19a2ccbe7a4b733efa9f06bfa237d8527ad96cb7c1c8330b6ebaceb4025799156250450bdc1175b3a6916278ddde7186fae72269954fc113b52ac7be95229ad26322635621ecdf5431e3ee4bb1a6daf95fec5350e05ebe06c6246144e6456ae40294a5f738ee0006b4291919103b6a360cf7e6866e63a3ffb4e3da8979a74f8c7013cad913275998ddab388353d6b8e6ed
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkComet-9994524-1 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: Policies 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: Policies 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 13 <HKCU>\SOFTWARE\REMOTE Value Name: NewIdentification 13 <HKCU>\SOFTWARE\REMOTE Value Name: NewGroup 13 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN13 <HKCU>\SOFTWARE\REMOTE13 <HKCU>\SOFTWARE\REMOTE Value Name: FirstExecution 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{4KB410KP-K47X-F1OS-P28S-4EM4PML0P85S}12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{4KB410KP-K47X-F1OS-P28S-4EM4PML0P85S} Value Name: StubPath 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{QUESH2FS-EW8G-217P-W5KA-61WH6D6G0SHH}1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{QUESH2FS-EW8G-217P-W5KA-61WH6D6G0SHH} Value Name: StubPath 1
Mutexes Occurrences Administrator513 DGUH4X41T1IOR412 DGUH4X41T1IOR4Administrator1512 DGUH4X41T1IOR4_RESTART12 DGUH4X41T1IOR4_SAIR12 0T13YCQ10SV7R01 0T13YCQ10SV7R0Administrator151 0T13YCQ10SV7R0_RESTART1 0T13YCQ10SV7R0_SAIR1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dfuso[.]zapto[.]org12 koort[.]zapto[.]org1
Files and or directories created Occurrences %TEMP%\Administrator713 %TEMP%\Administrator813 %APPDATA%\Administratorv1.18.0 - Trial versionlog.dat13 %TEMP%\Administrator2.txt13 %SystemRoot%\SysWOW64\install13 %SystemRoot%\SysWOW64\install\server.exe13
File Hashes 1737a47c7c99e14900e7c0c50634d6c2d501b3791d3378023dd7c98cdd4a20921dc73c05eba96649d459e39f33678f6ef6b80068f1497fbdac3c0851f367d6b223fcef1c2aa3aaa06fba04edd246f3d540ba33dfcb48190c2ce68eed3b10488c28db39898aa31ff39a363061f3a1185d3d9048ae43279f4db24806fb9091342d32141021a611a0e52a74f81e2757b91369c5b90f23b63c3446afd0413492d8555e27228a51e84b26e0075049b3fe4da31805894ddbe3b5fa11a5782f804dc34e7ac698b31b4350f8b330fb85af049cd5d0ec35dc0272445c3eab61a67f0ae18e8c33791c2fad6489ac0d30ab28682b07c1603e5cce0e0fcafca6513149a852dcb523f3a0bbdb732742d9c34538b40a23613c46a425568f4e0d92ce35a3da7ea7d531098fe1e0c6e1c6e0aac2248d8e316462dfc52bbf1e551833d4721fd3176bea9d1028dadc79eadf9eadf728d6c999fa429c05bffebbdfce34d4cf6c0b68f3f863ec84969fbf861b13999d5d1a271864edf9f54d43412ecd79c1220ea6433efabc2eee42dc5af4e7aa7c97e7f97bbb2b8d81b47c4272ced6d35653f956ea81
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK